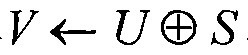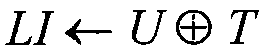Generation and verification method for visual digital identity of article
A digital identity and identity verification technology, applied in the direction of user identity/authority verification, etc., can solve problems such as sub-exponential time solutions not found
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0090] The characteristic of the visual digital identity method based on lightweight digital signature is that it adopts asymmetric verification technology, which is fundamentally different from traditional symmetric verification methods such as handwritten signature or round red seal.
[0091] The method uses two keys, one key can only be privately owned by the unit, and is used for generating the visible digital identity, and the other key can be publicly placed on the server, and is used for the verification of the visible digital identity. In this way, it is ensured that the visible digital identity is inimitable and thus the associated item is also unforgeable.
[0092] A pair of private key and public key is prepared by the item production or distribution unit, and the public key is uploaded to the verification server of the unified platform. Of course, the private key must be kept by the person in charge of the unit or its designated agent, and must not be leaked.
[00...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com