Patents
Literature
81results about How to "Attempt have been hampered" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
System and method for the detection and termination of fraudulent services
InactiveUS7512221B2High error rateMaximize throughputUnauthorised/fraudulent call preventionEavesdropping prevention circuitsComputer networkFinancial transaction
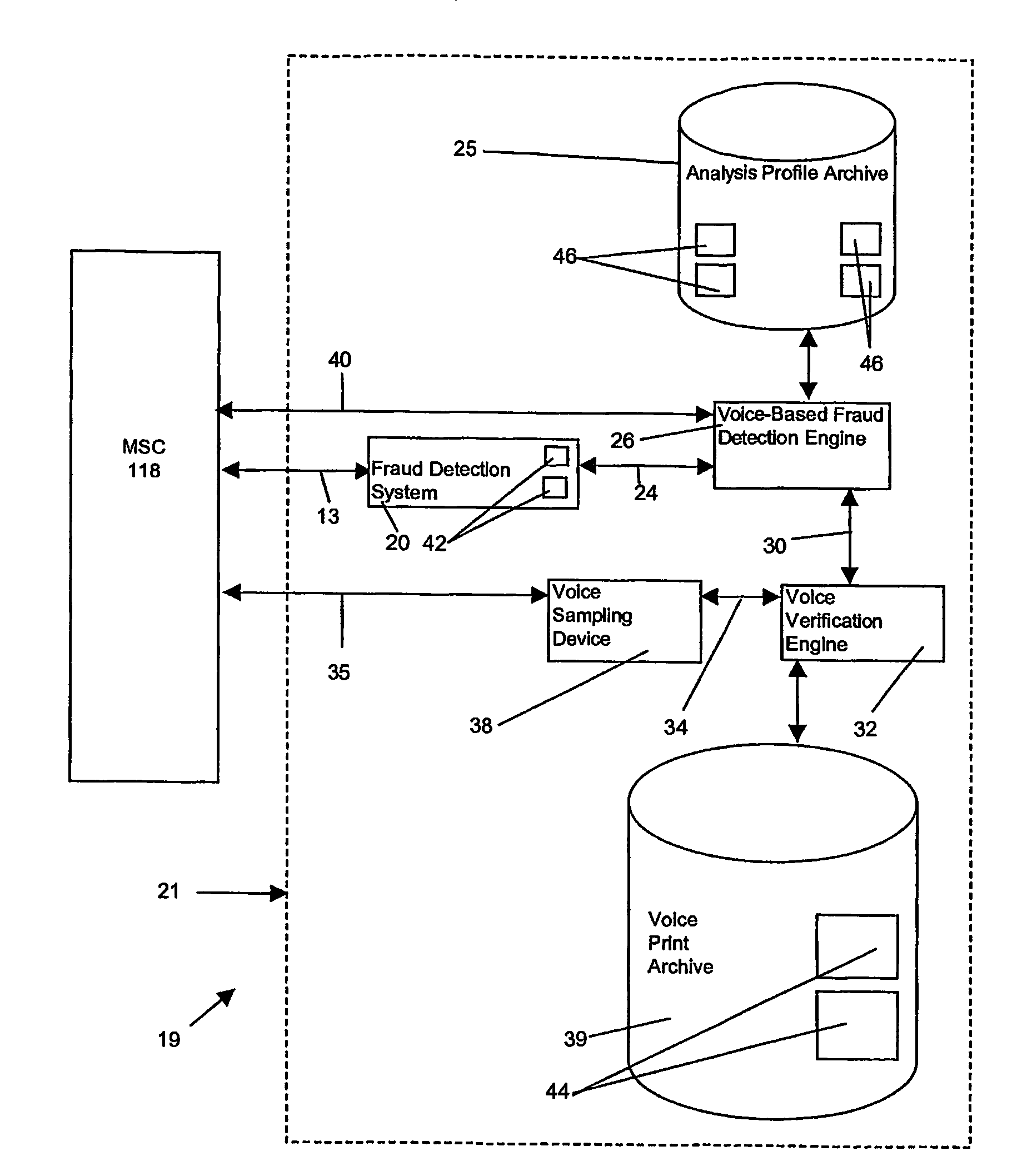
A system is disclosed for the automatic detection of fraudulent activity on a transaction network, for which each transaction over the network has an associated identifier. In one embodiment, the system includes voice comparison means for comparing a first sampled voice of a user of a first transaction with a subsequently sampled voice of a user of a subsequent transaction having an identical identifier to that of the first transaction. Control means in the form of a voice-based fraud detection engine is provided for determining, from said comparison, a profile of user usage that is representative of a total number of different users of the associated identifier. In a preferred embodiment, the system also includes voice sampling means for sampling a voice of the user of the first transaction to generate a first voice sample.
Owner:CEREBRUS SOLUTIONS LTD
Electromechanical cylinder lock
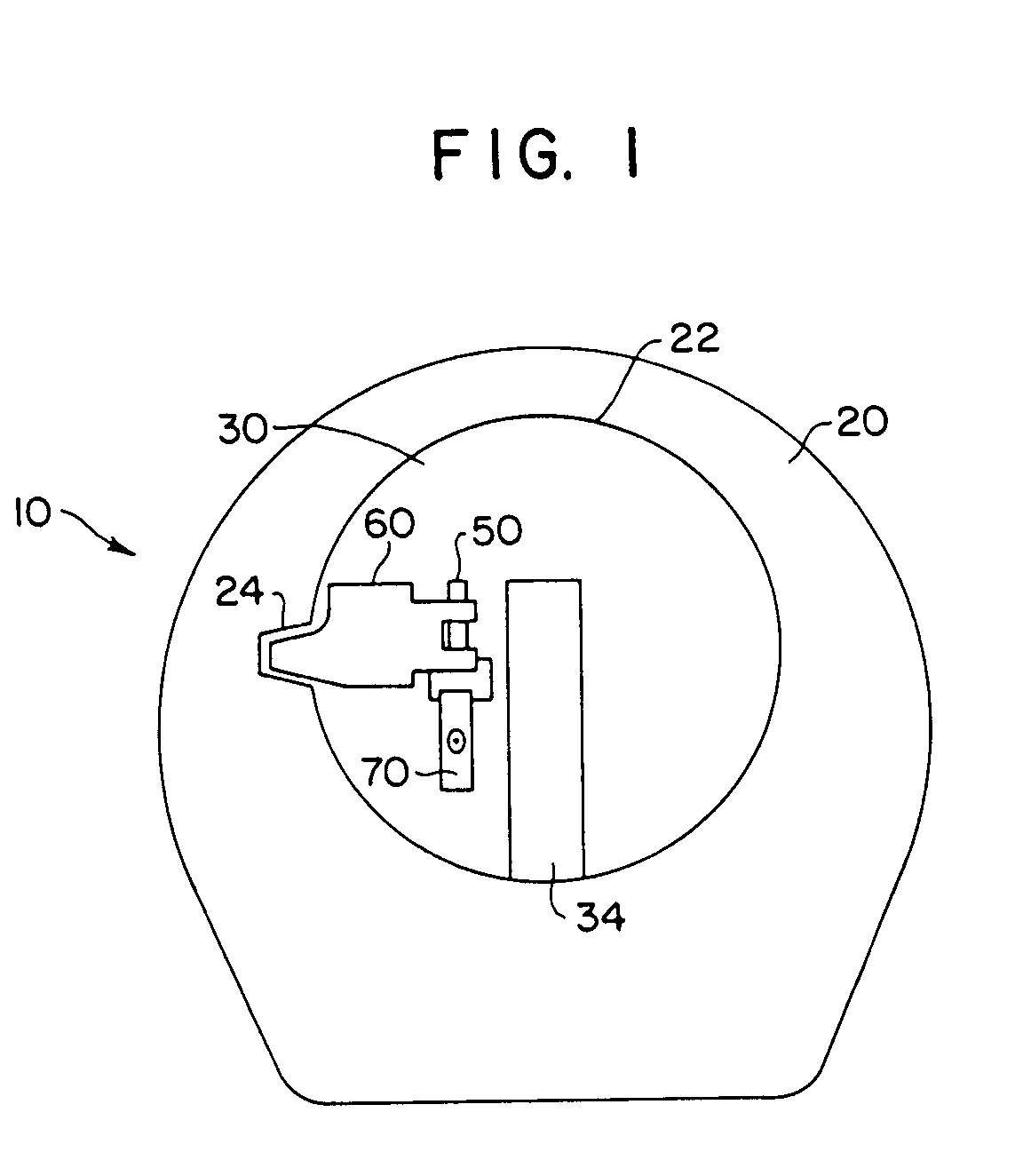
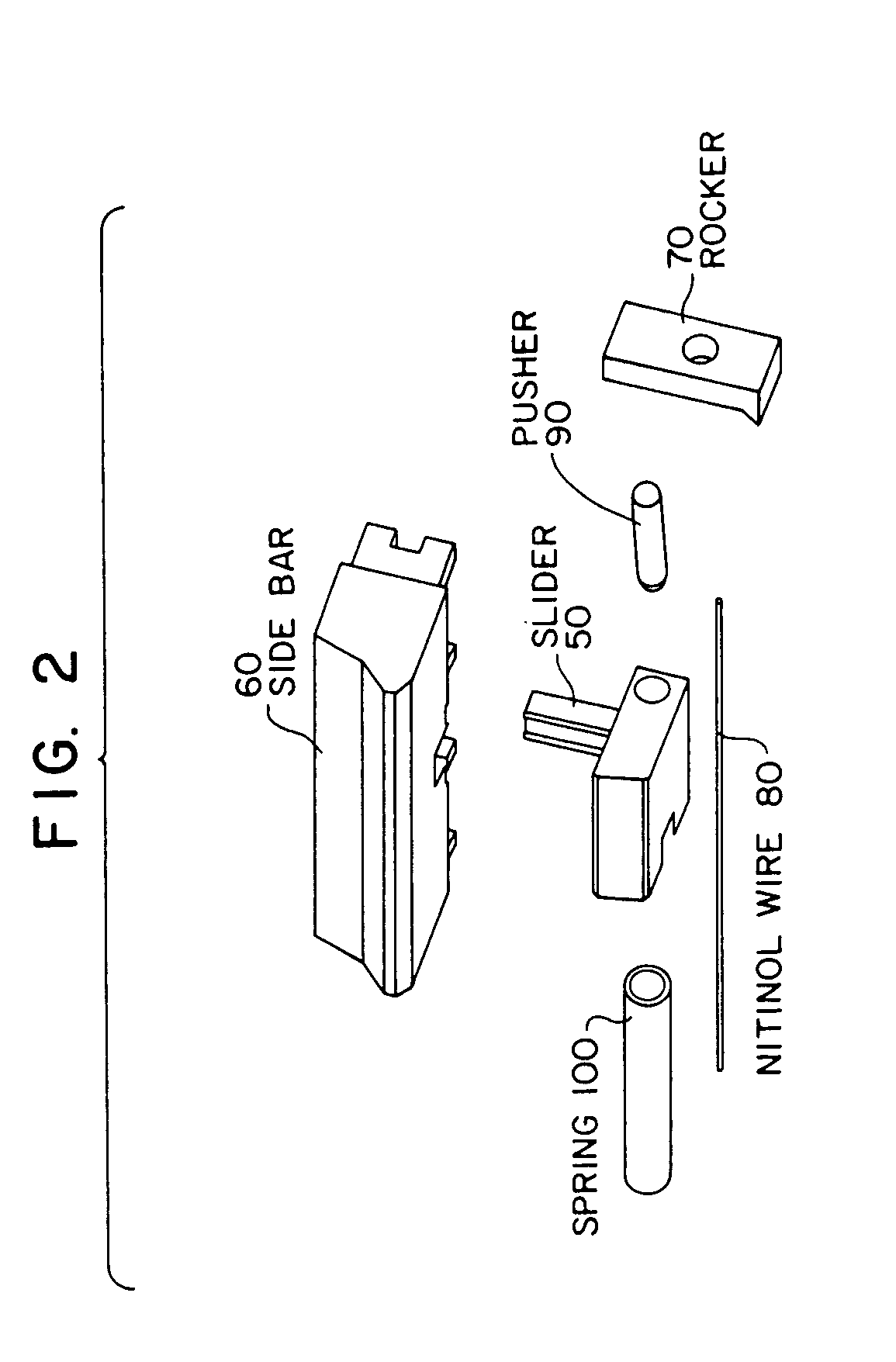
InactiveUS7690231B1Good flexibilityAttempt have been hamperedShaftsNon-mechanical controlsEngineeringMechanical engineering
An electromechanical cylinder lock includes an outer lock shell and a rotatable lock barrel located therein which is controlled by dual locking features. A side bar or fence selectively blocks and permits rotation of the barrel with respect to the shell in response to insertion of a key into a keyway in the barrel. A slider bar is movable between a blocking position in which the side bar is prevented from permitting rotation of the barrel, and an unblocking position in which the side bar permits rotation of the barrel. Alternately, a blocking mechanism is provided to block motion of tumbler pins in the cylinder lock. A shape memory alloy actuator, such as a wire made of NITINOL disposed in the barrel is activated by an electric current in response to determination by an electronic control device whether an attempt to open the lock is authorized. Thermal interlock protection from external heating of the lock is also provided.
Owner:ASSA ABLOY HIGH SECURITY GRP INC
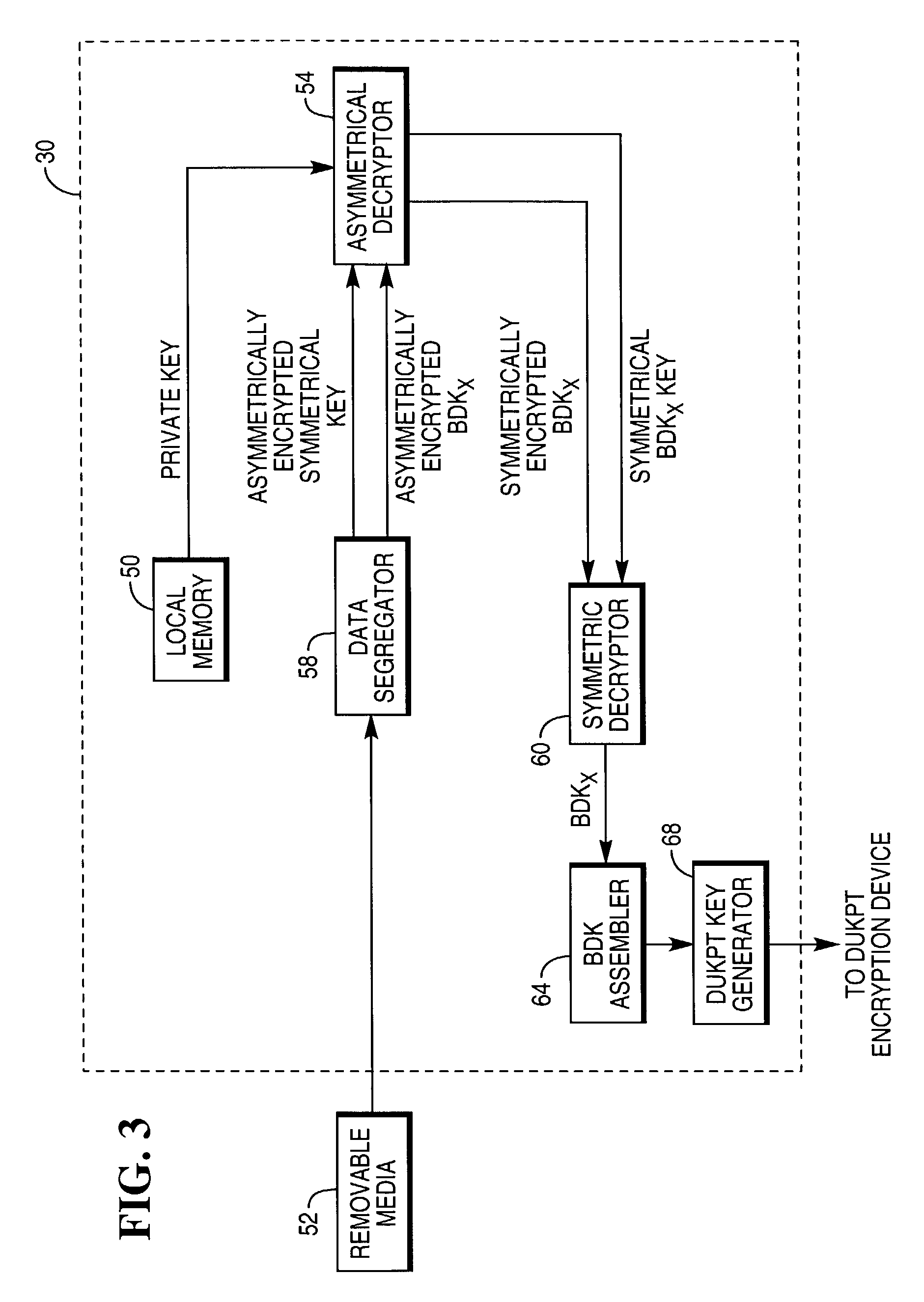
System and method for securing a base derivation key for use in injection of derived unique key per transaction devices
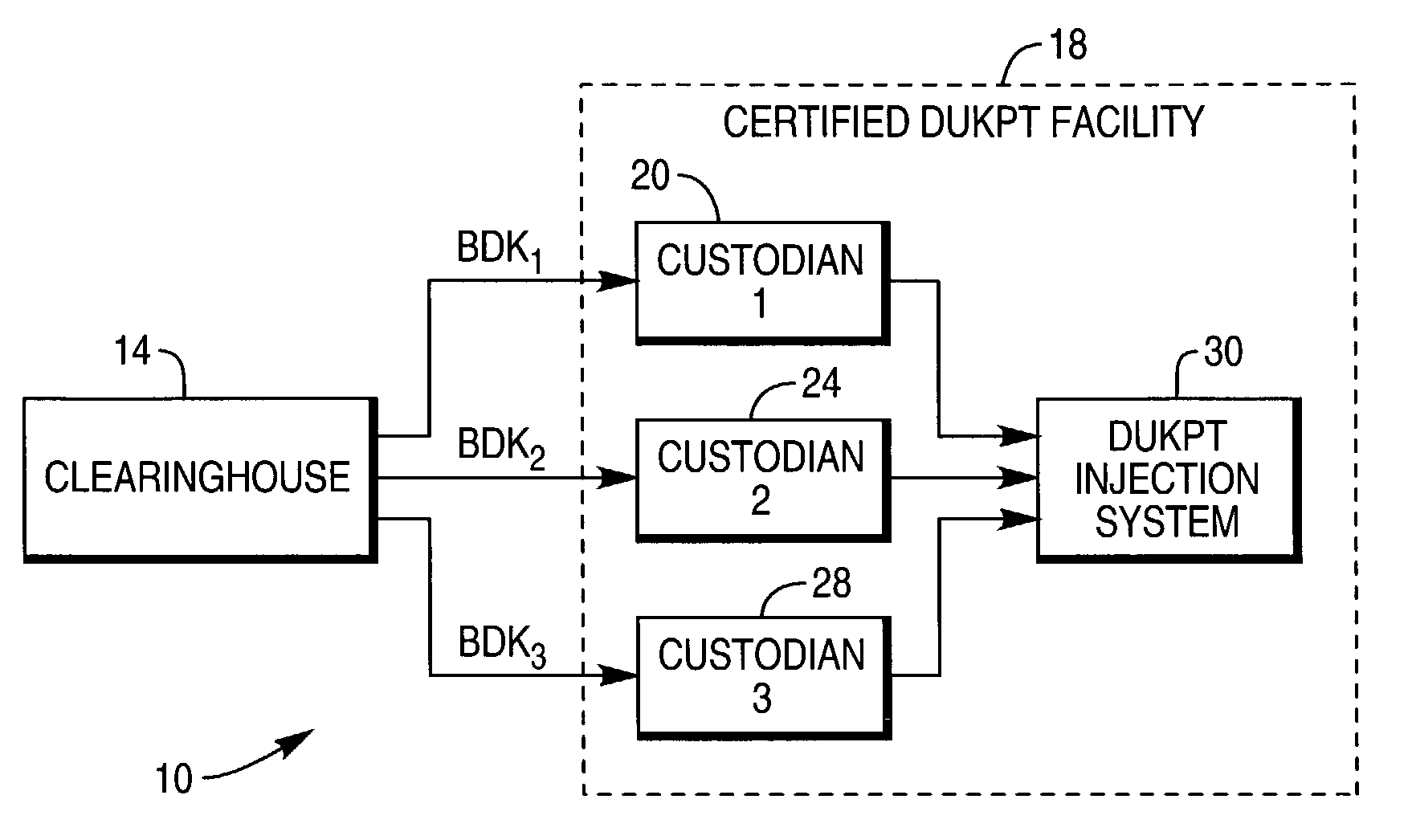
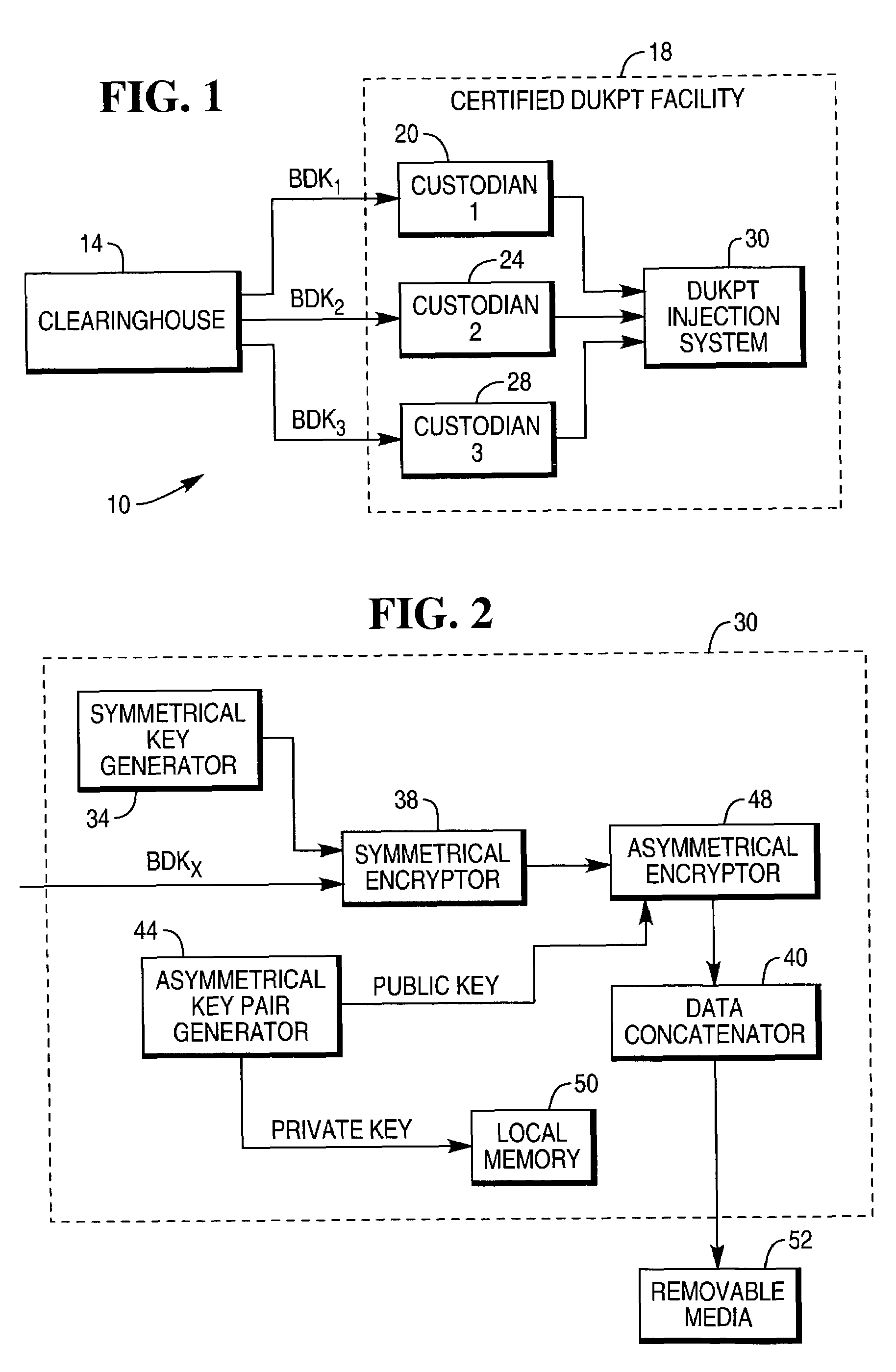
InactiveUS7548621B1Safe storageAttempt have been hamperedPublic key for secure communicationUnauthorized memory use protectionNon symmetricKey generator
A system that secures a Base Derivation Key (BDK) in a facility for injecting Derived Unique Key Per Transaction (DUKPT) devices uses software for securing the BDK rather than a Tamper Resistant Security Module (TRSM). The system comprises a symmetrical key generator, a symmetric encryption device, a concatenating device, an asymmetrical key pair generator, and an asymmetrical encryption device. The symmetrical key generator randomly generates an encryption key for a symmetrical encryption method. The symmetrical key is provided to the symmetric encryption device for encrypting a segment of a BDK with a symmetrical key. The asymmetrical encryption device uses the public key of a randomly generated private / public key pair generated by the asymmetrical key pair generator to asymmetrically encrypt the symmetrically encrypted BDK segment and the symmetrical key. The public key is then destroyed and the private key is stored on the computer.
Owner:NCR CORP
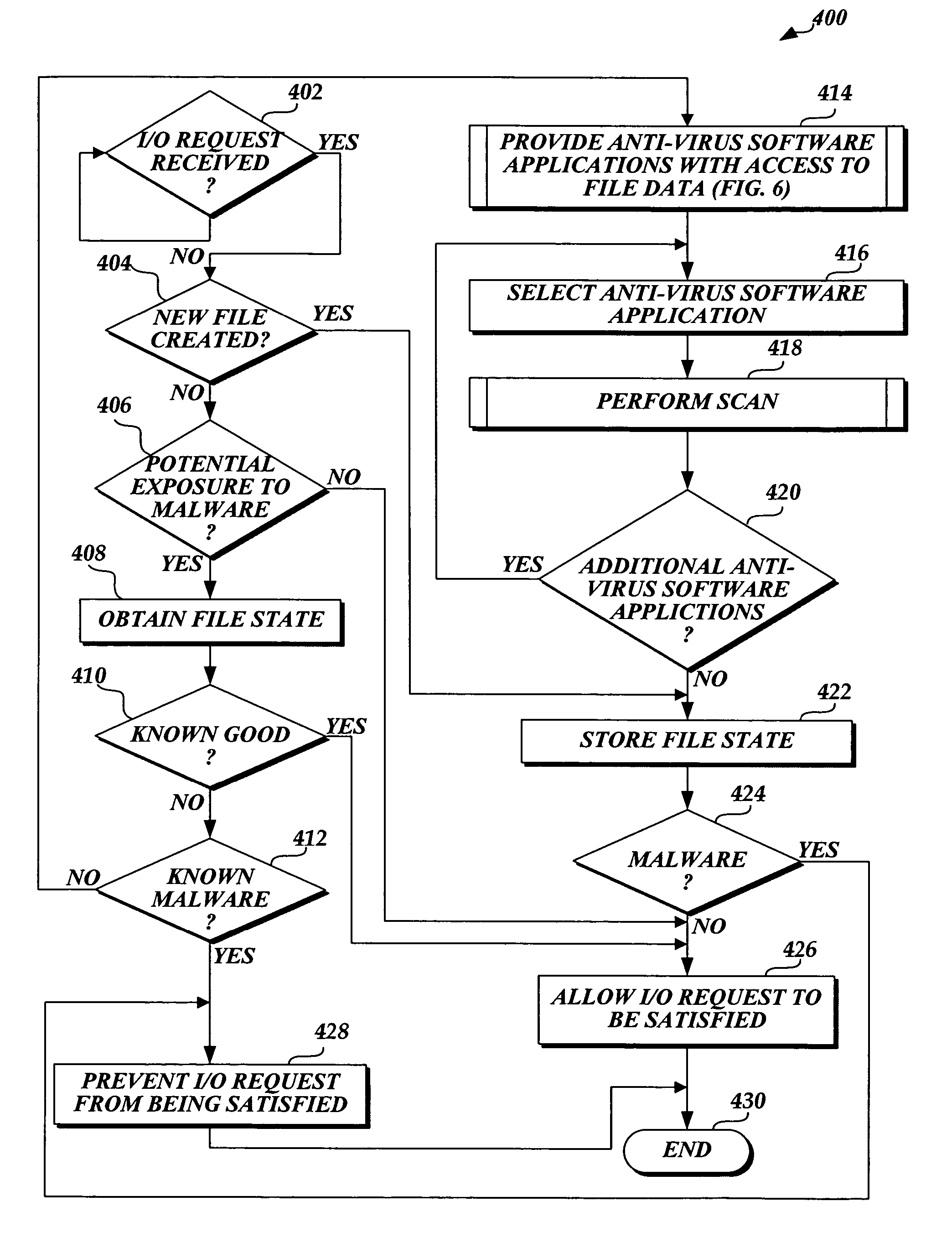
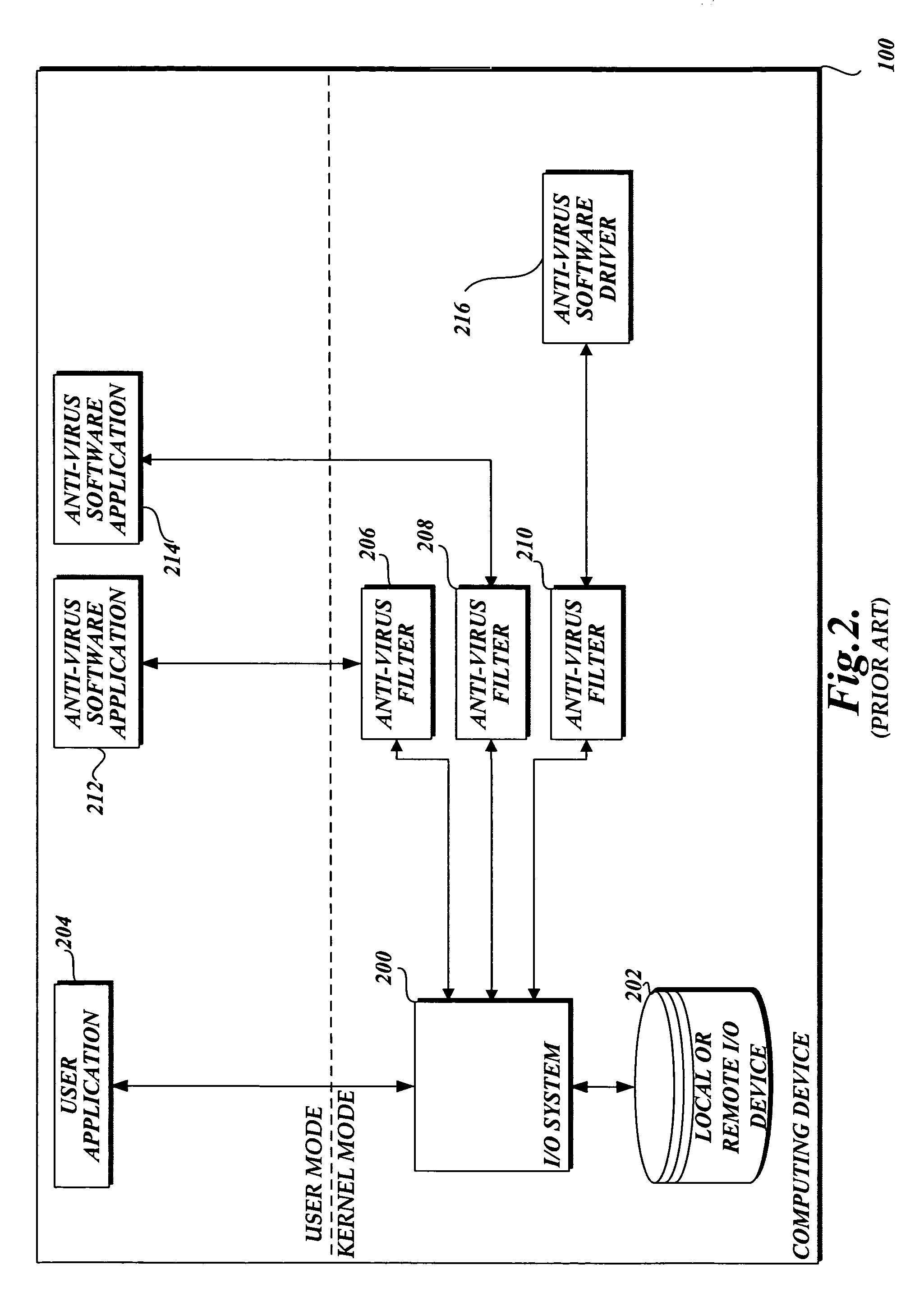
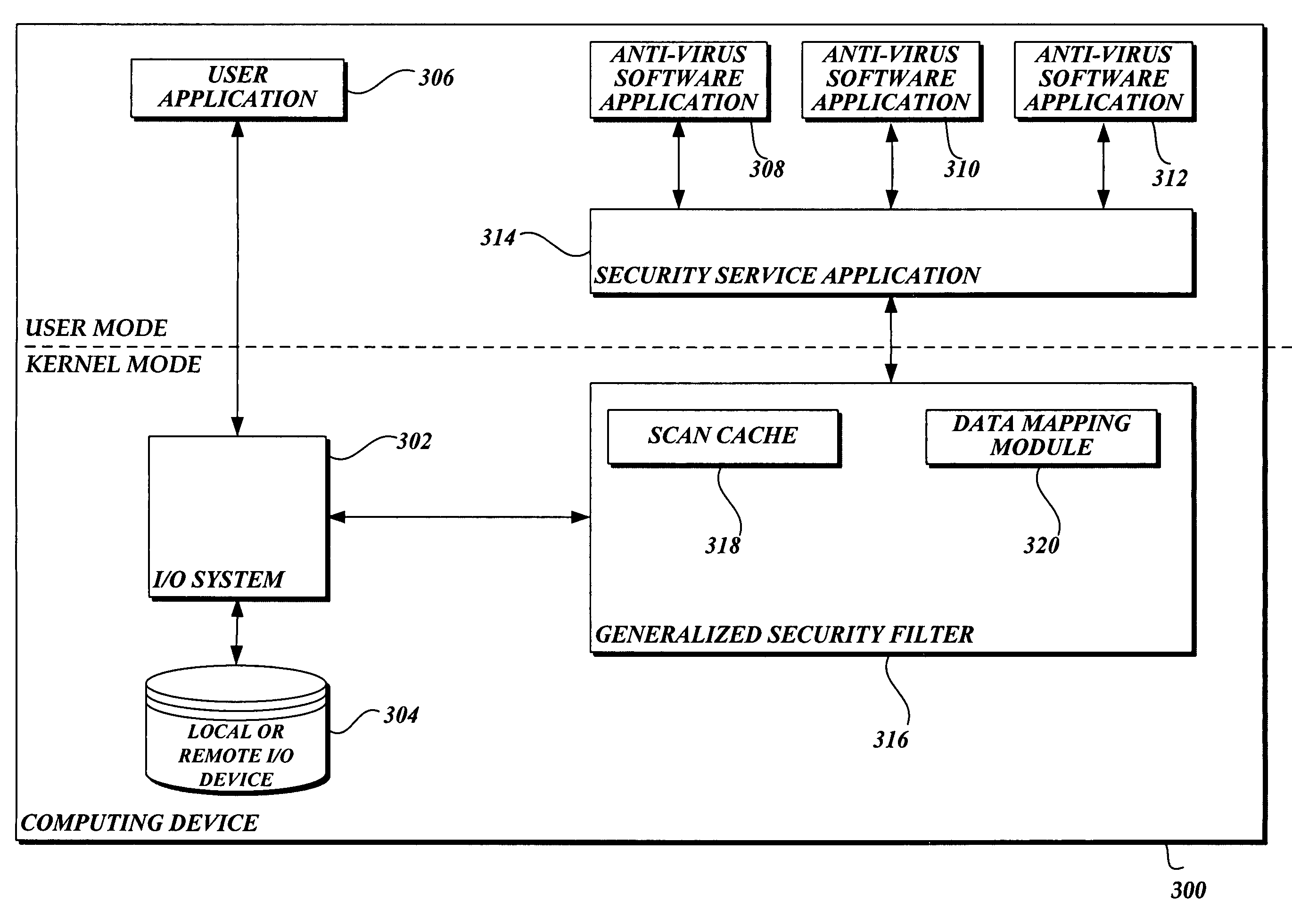
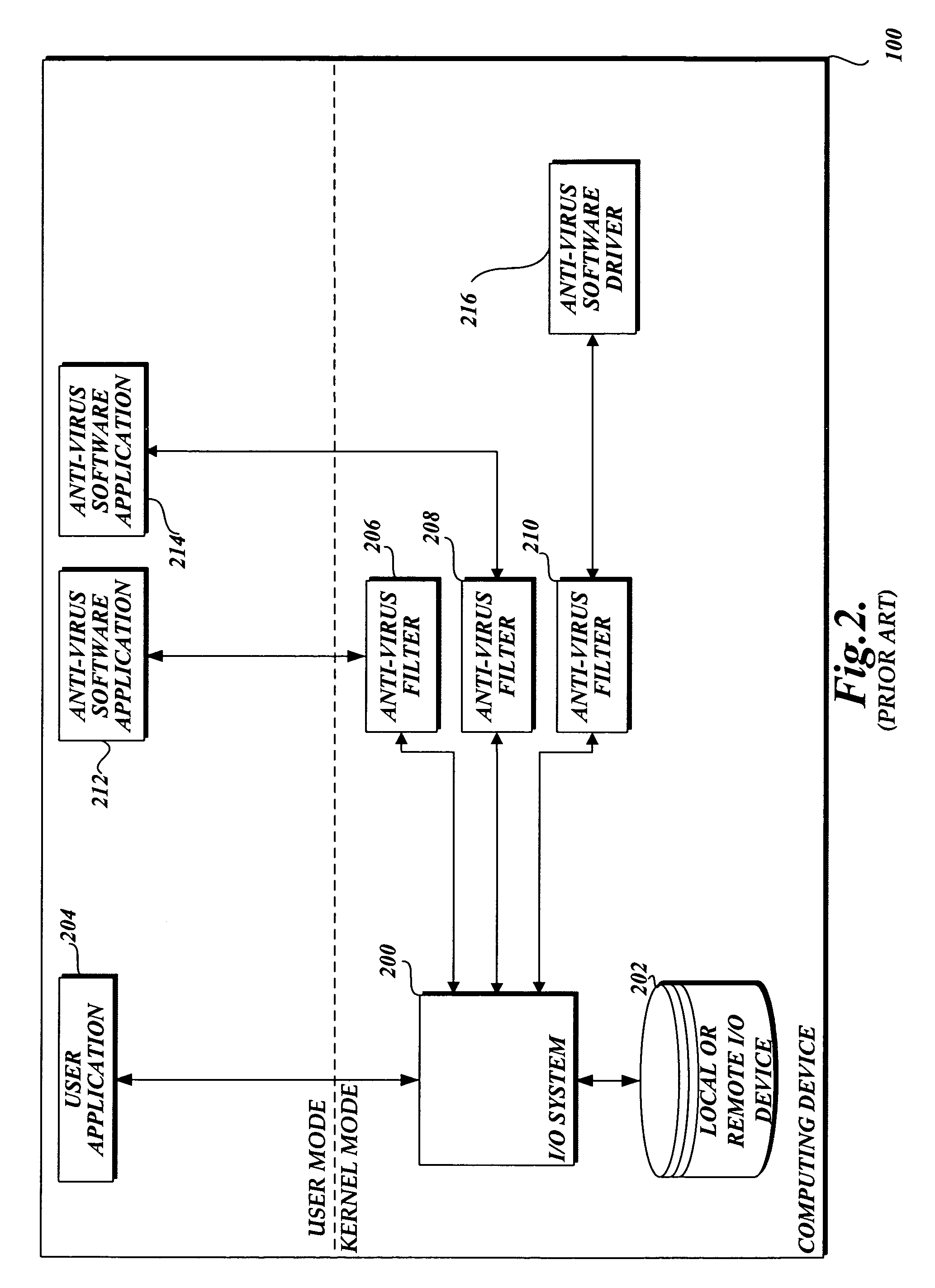
System and method of allowing user mode applications with access to file data
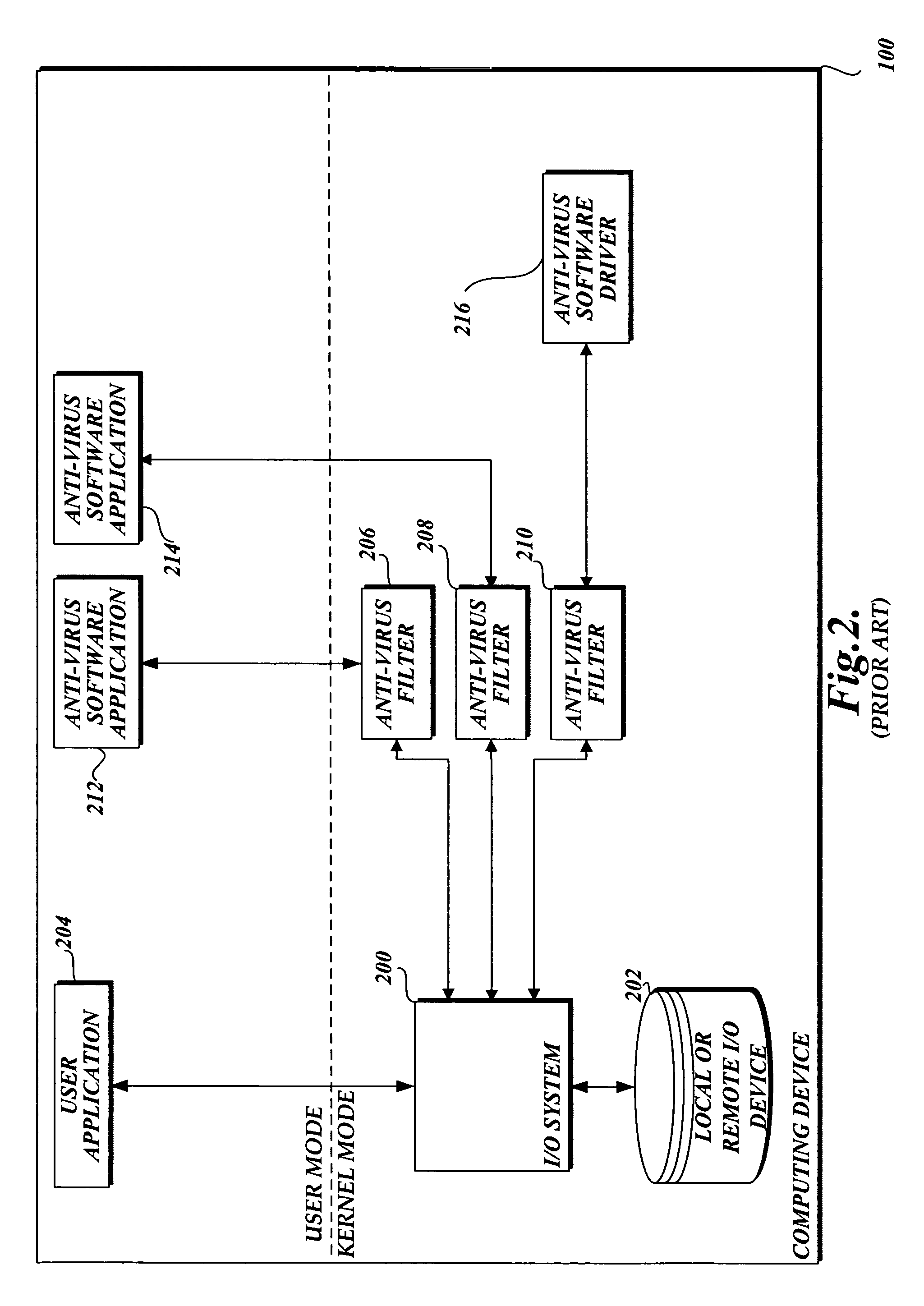
InactiveUS20060101263A1Attempt have been hamperedIncrease speedDigital data processing detailsAnalogue secracy/subscription systemsMalwareApplication software
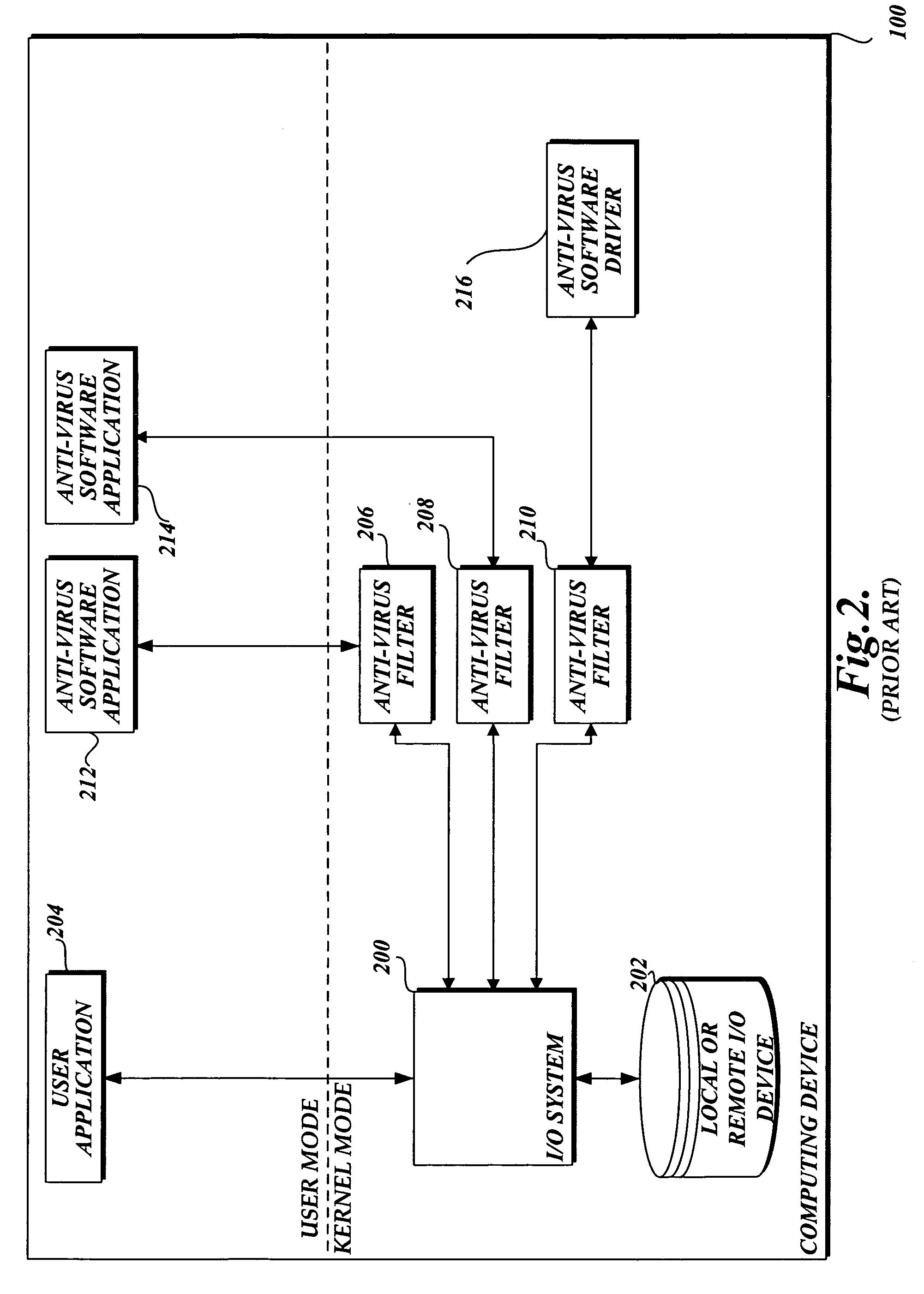
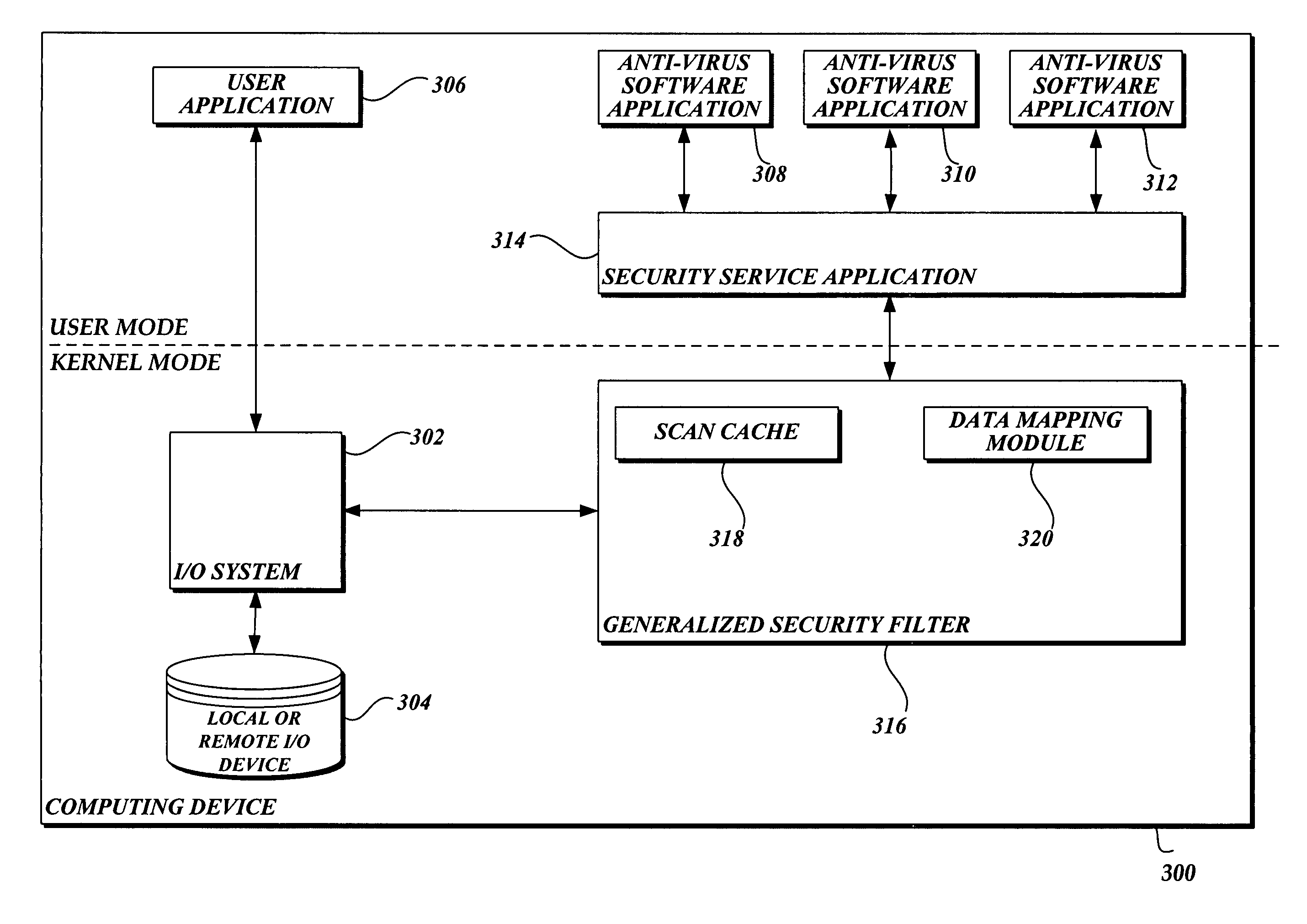
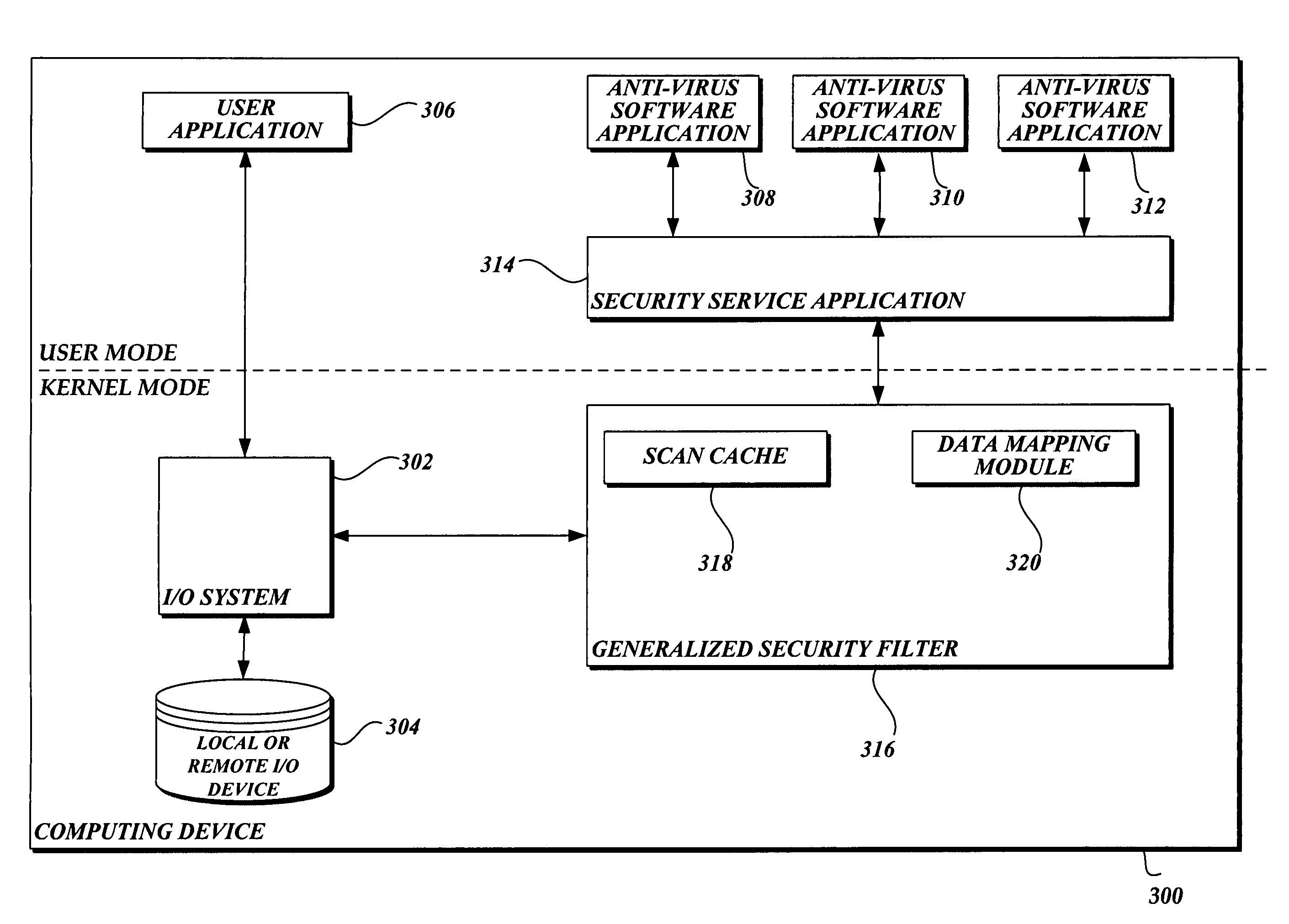
In accordance with this invention, a system, method, and computer-readable medium that aggregates the knowledge base of a plurality of antivirus software applications are provided. User mode applications, such as antivirus software applications, gain access to file system operations through a common information model, which obviates the need for antivirus software vendors to create kernel mode filters. When file system operations are available to antivirus software applications, the present invention may cause each antivirus software application installed on a computing device to perform a scan to determine if the data is malware.
Owner:MICROSOFT TECH LICENSING LLC
Aggregation of the knowledge base of antivirus software
InactiveUS7765400B2Attempt have been hamperedIncrease speedData processing applicationsMemory loss protectionFile systemMalware
Owner:MICROSOFT TECH LICENSING LLC
System and method of aggregating the knowledge base of antivirus software applications
InactiveUS7765410B2Attempt have been hamperedIncrease speedMemory loss protectionDigital data processing detailsFile systemApplication software
In accordance with this invention, a system, method, and computer-readable medium that aggregates the knowledge base of a plurality of antivirus software applications are provided. User mode applications, such as antivirus software applications, gain access to file system operations through a common information model, which obviates the need for antivirus software vendors to create kernel mode filters. When file system operations are available to antivirus software applications, the present invention may cause each antivirus software application installed on a computing device to perform a scan to determine if the data is malware.
Owner:MICROSOFT TECH LICENSING LLC
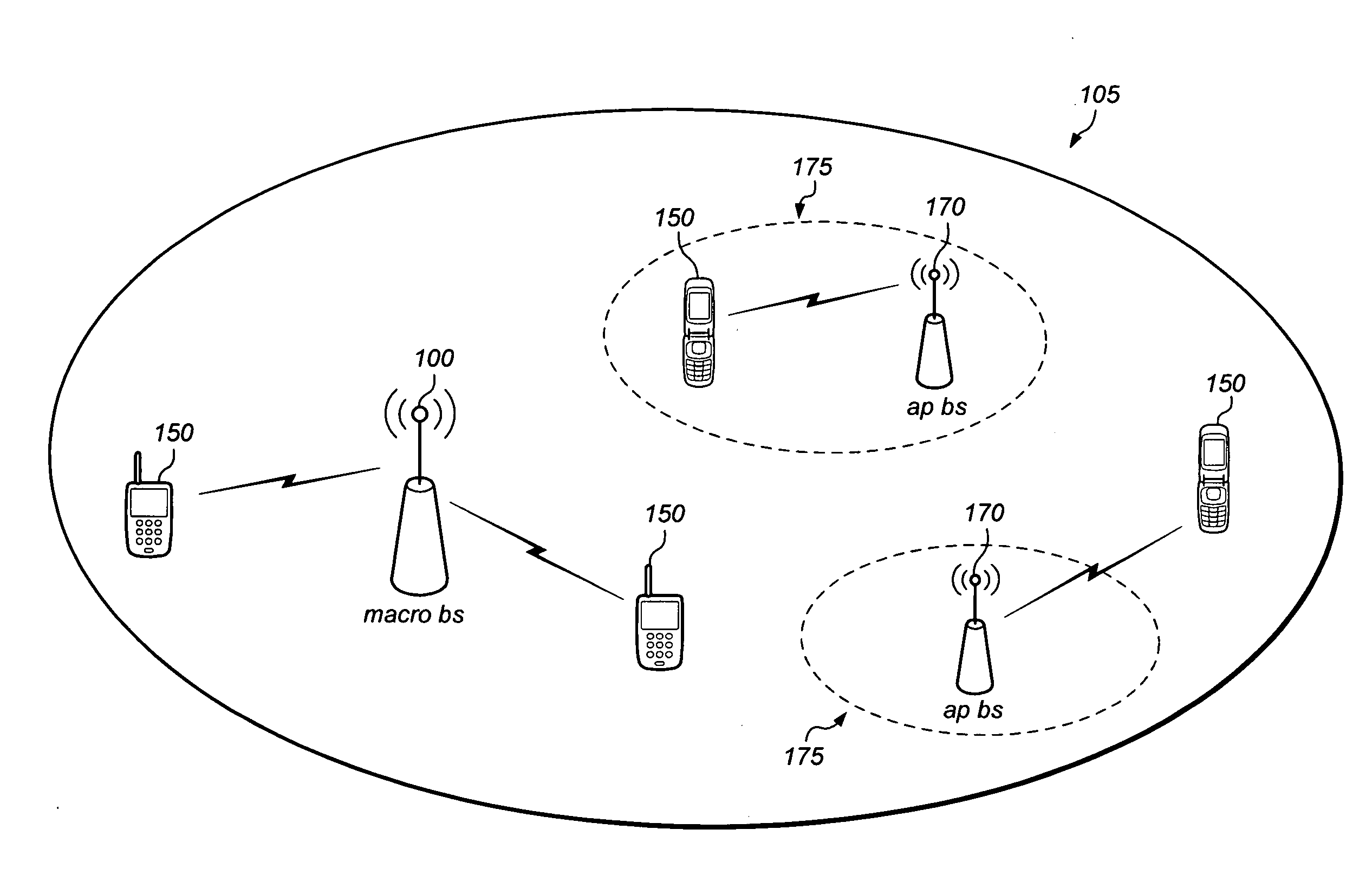
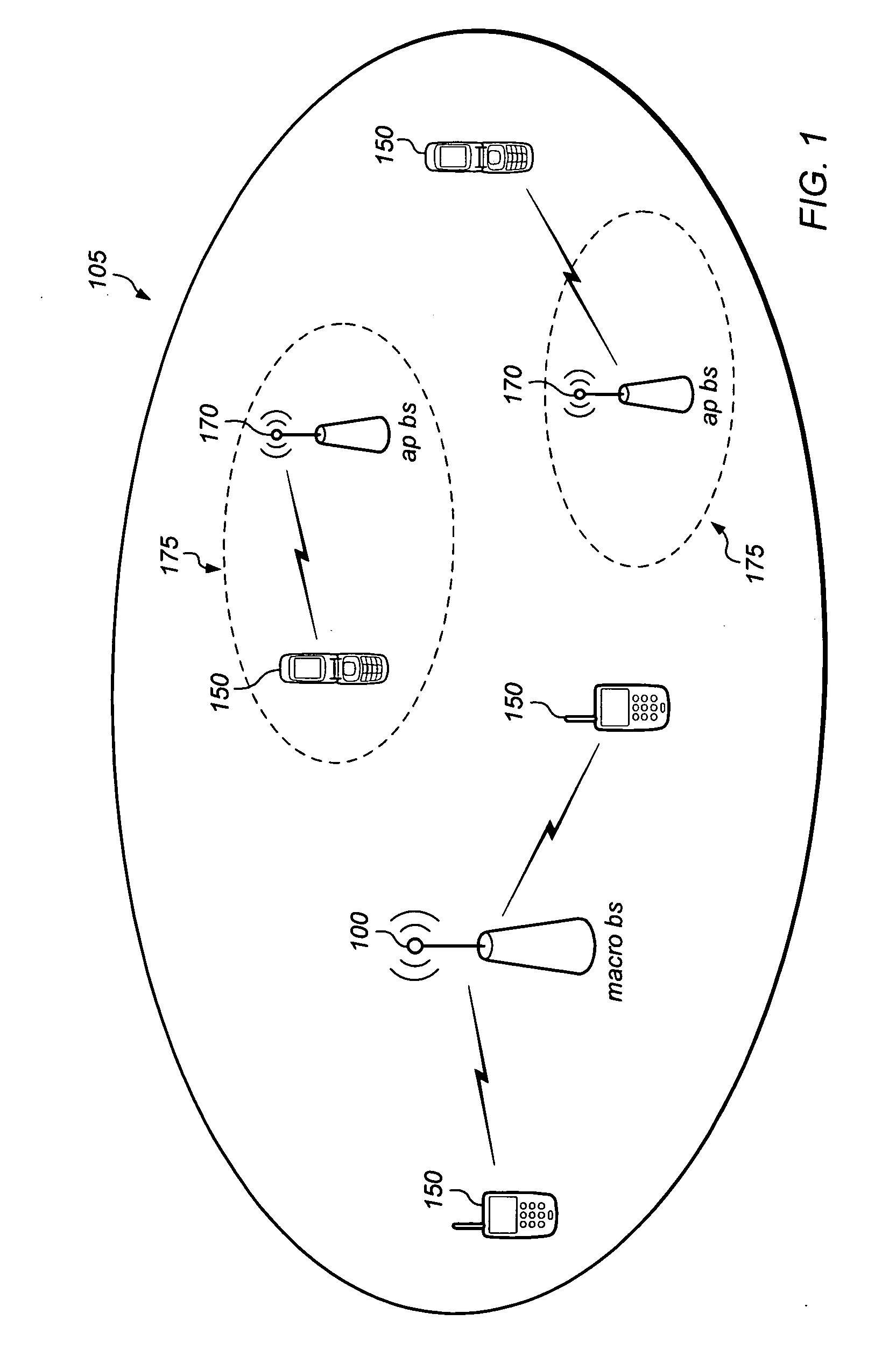
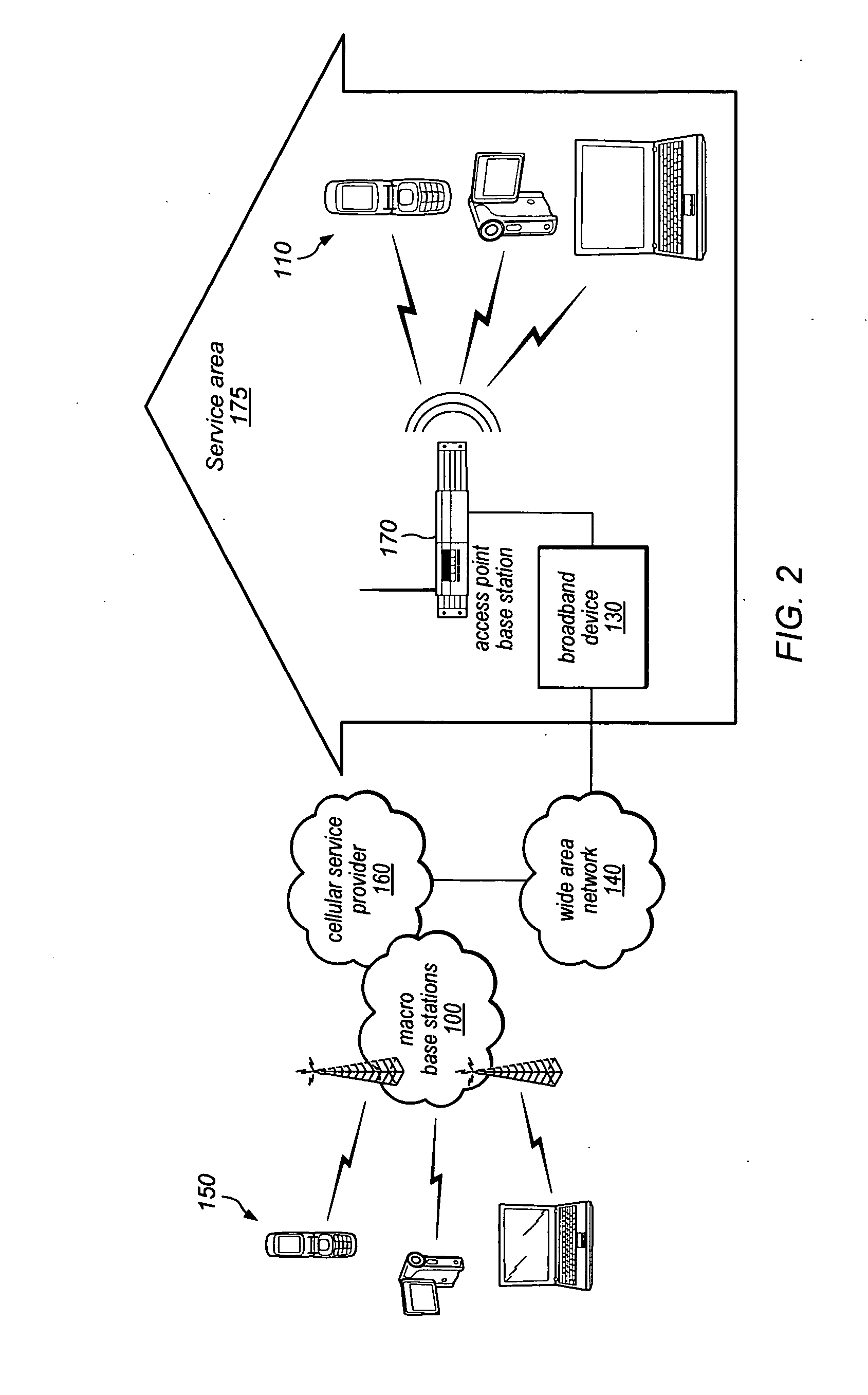
Localized silence area for mobile devices
ActiveUS20090298475A1Reduce eliminateAttempt have been hamperedAssess restrictionSubstation equipmentTelecommunications linkDirect communication
A system and method for creating a localized silence area. A mobile device may be registered with an access point base station. Any direct communication links from the mobile device to any other base stations may be removed. An indication may be given to the mobile device that the mobile device is in a localized silence zone. The indication may include a request that the mobile device operate in a silent mode, information about making outgoing calls, information about receiving incoming calls, or a combination of these. Procedures for incoming voice calls to the mobile device may be different for different priority levels.
Owner:IPCOMM +1
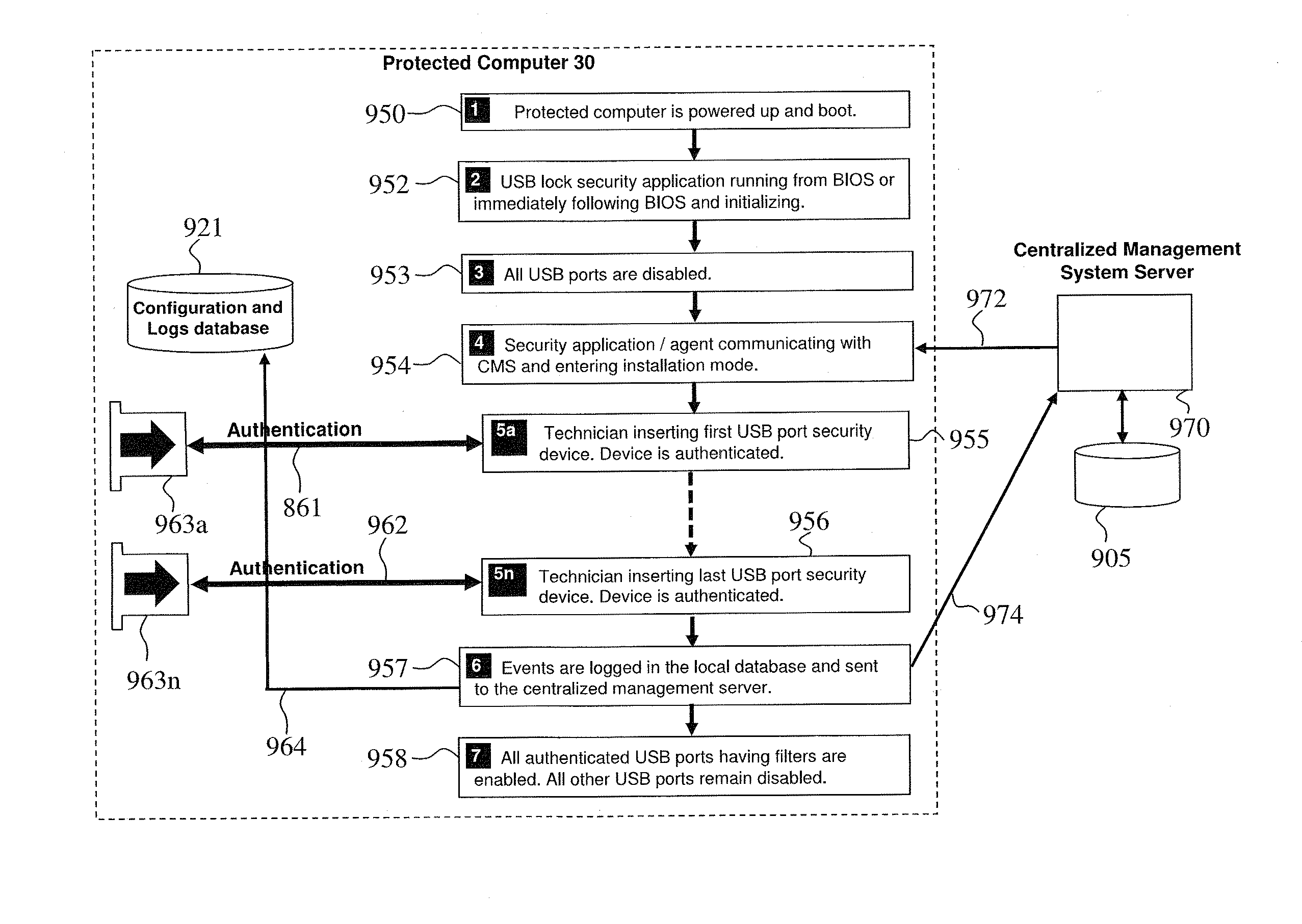
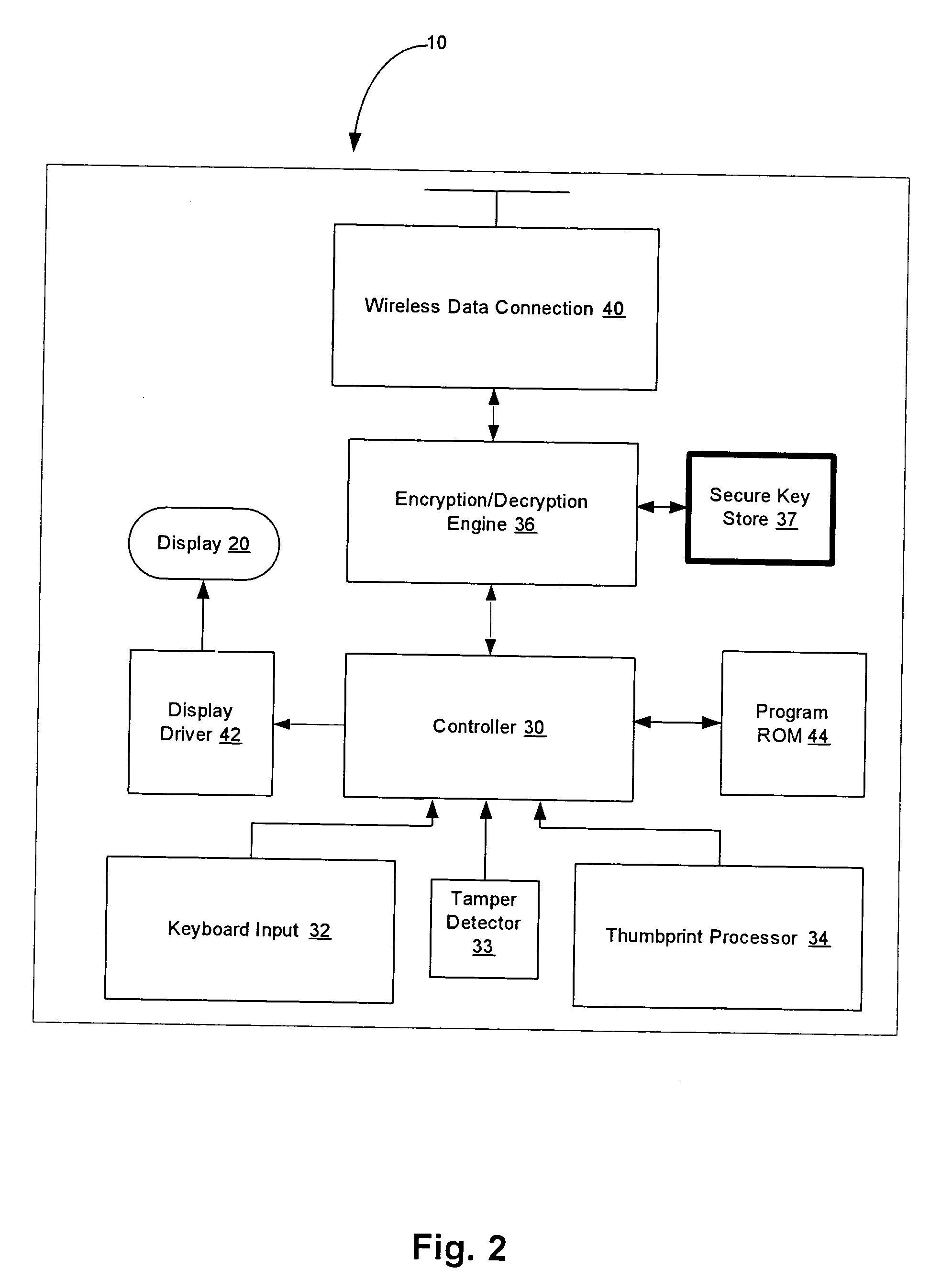
USB security device, apparatus, method and system
ActiveUS20160196454A1Improve information securityAttempt have been hamperedDigital data processing detailsCoupling device detailsEngineeringSelf locking
Methods, devices and system for enhancing computer information security by physically blocking unused USB ports with self-locking devices, or by providing USB port self-locking device with internal circuitry that qualifies and secures user peripheral device attached to the computer, and by continuously communicating with a management software application that provides real-time monitoring and warnings when any USB self-locking device is being removed or tampered. The self-locking devices use a spring loaded teeth in the USB plug that lock into tab spaces in the USB jack. Visual indicator provides positive assurance when all ports are secure. Each self-locking devices include a security circuit which is uniquely paired with the protected port. Some self-locking devices include data filters that only enable connecting authorized peripheral devices.
Owner:HIGH SEC LABS LTD
Method of controlling a function of a device and system for detecting the presence of a living being
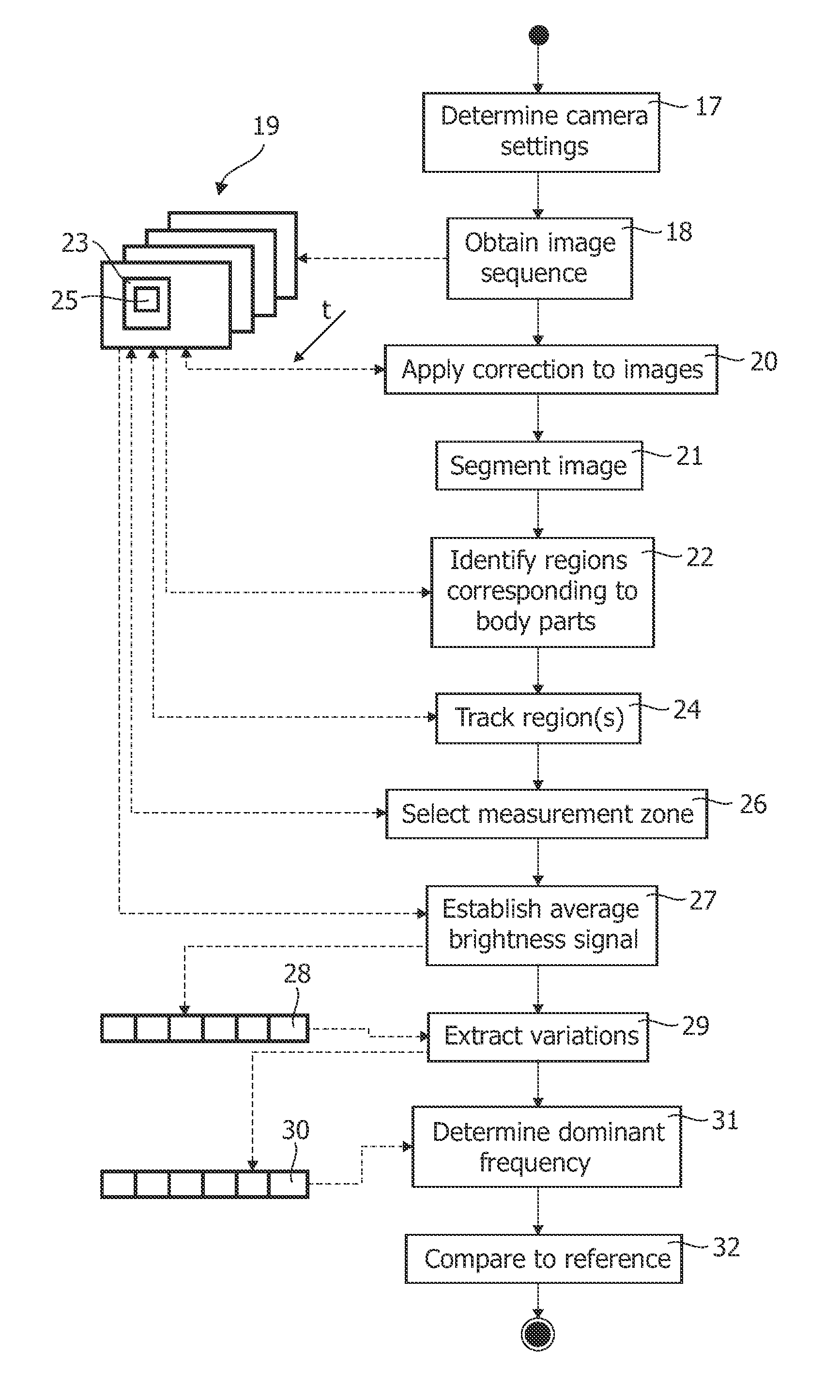
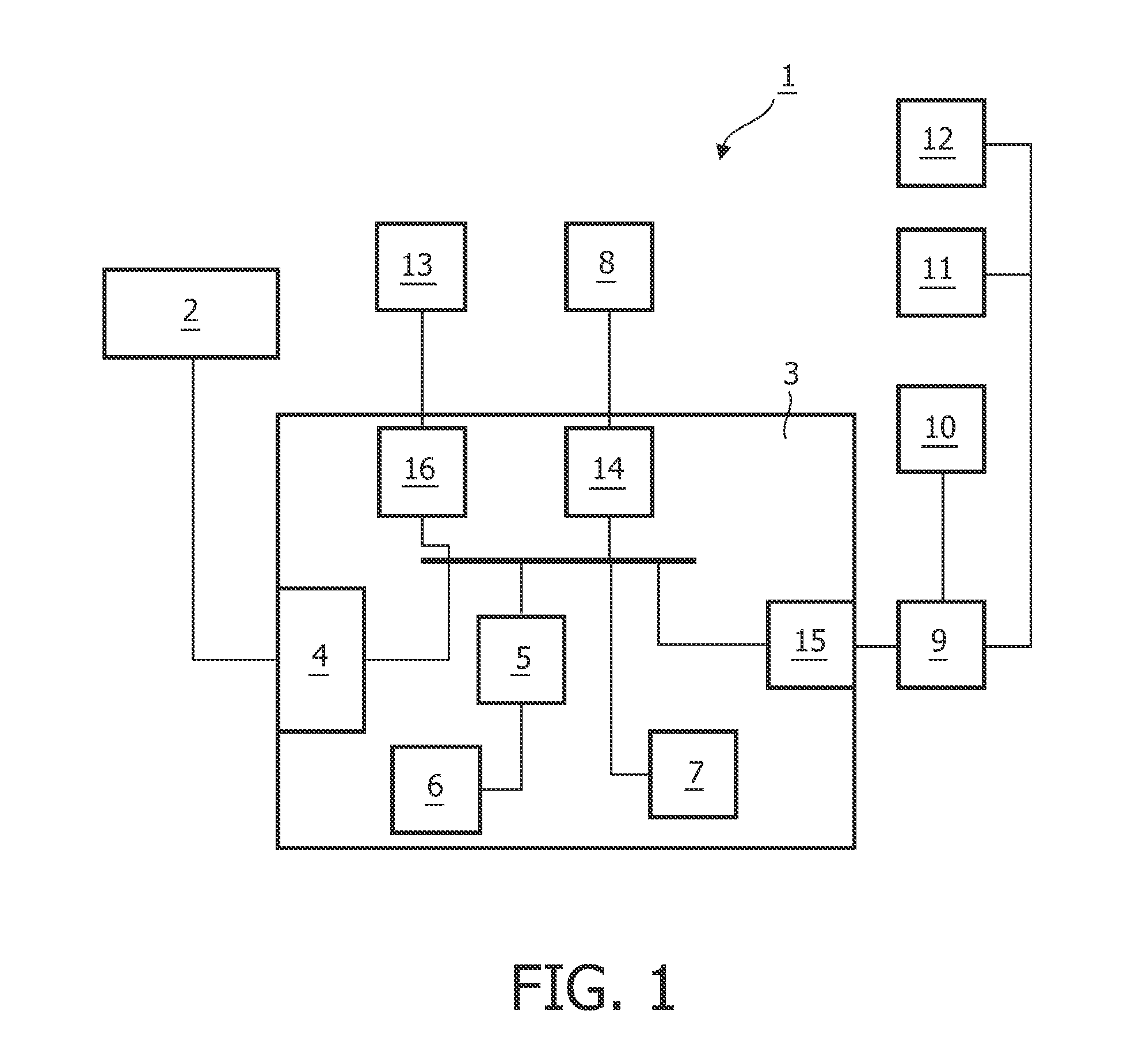
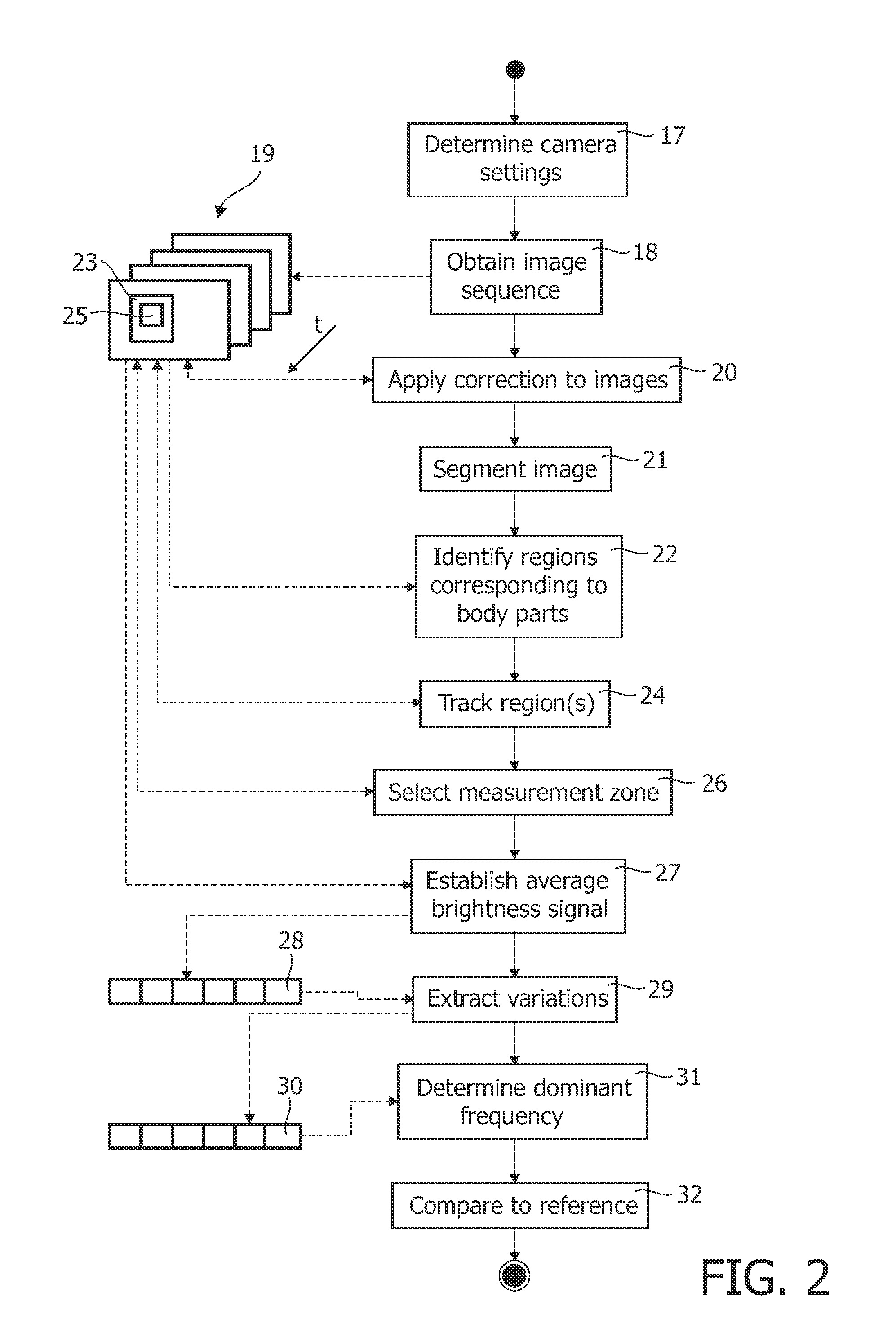
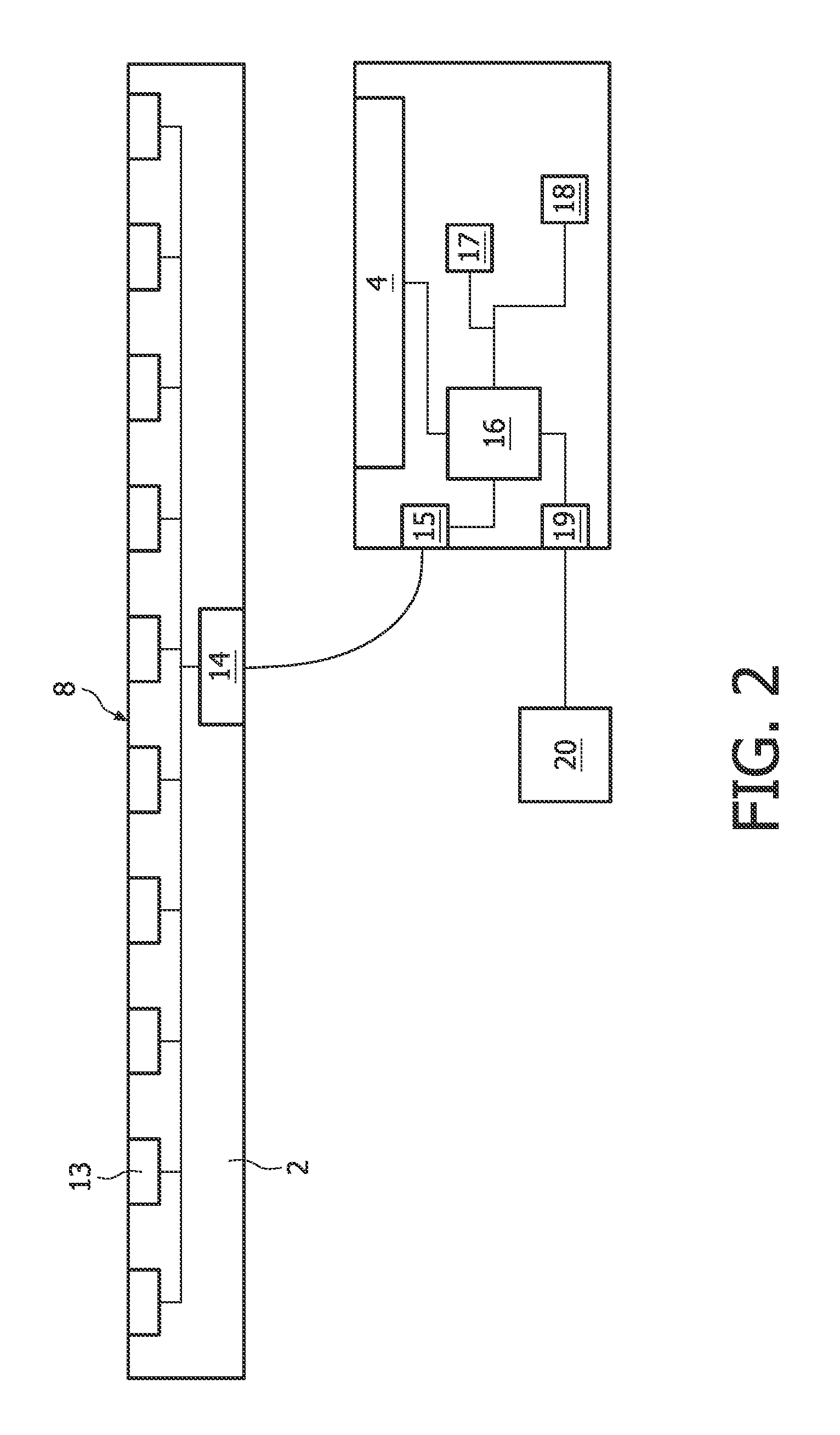
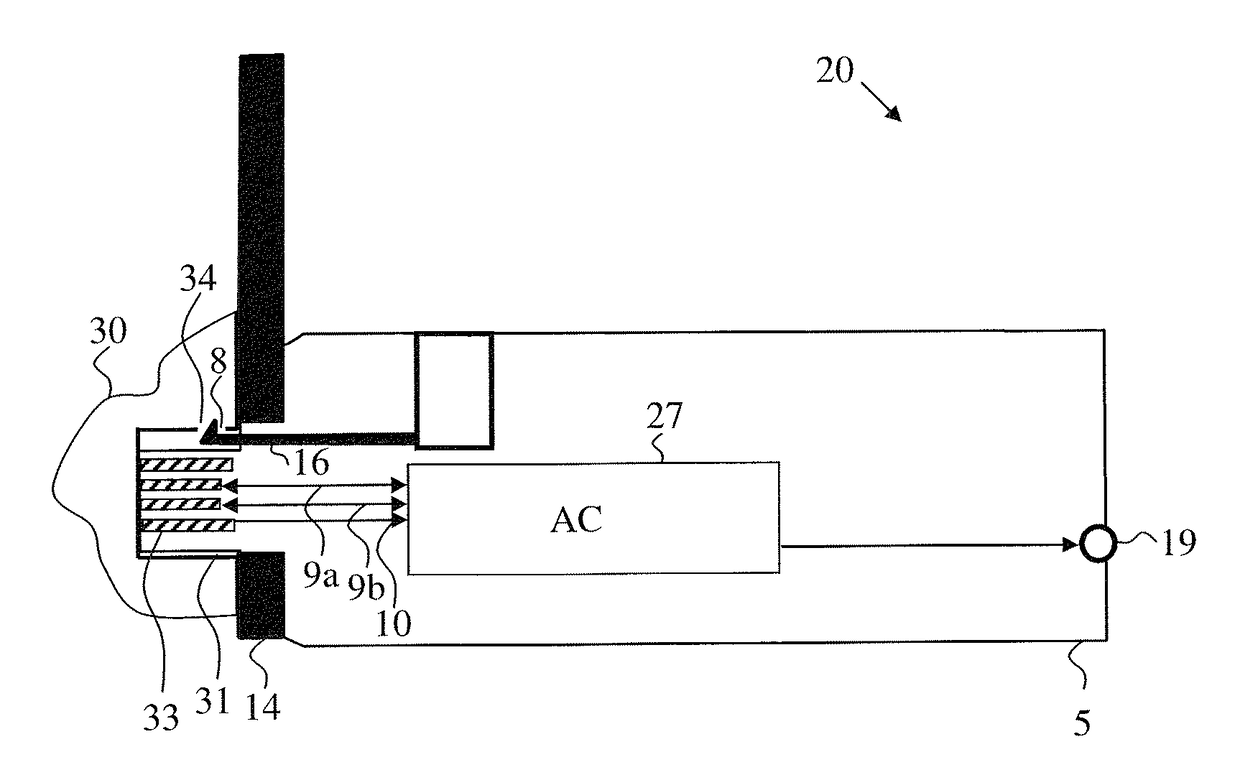
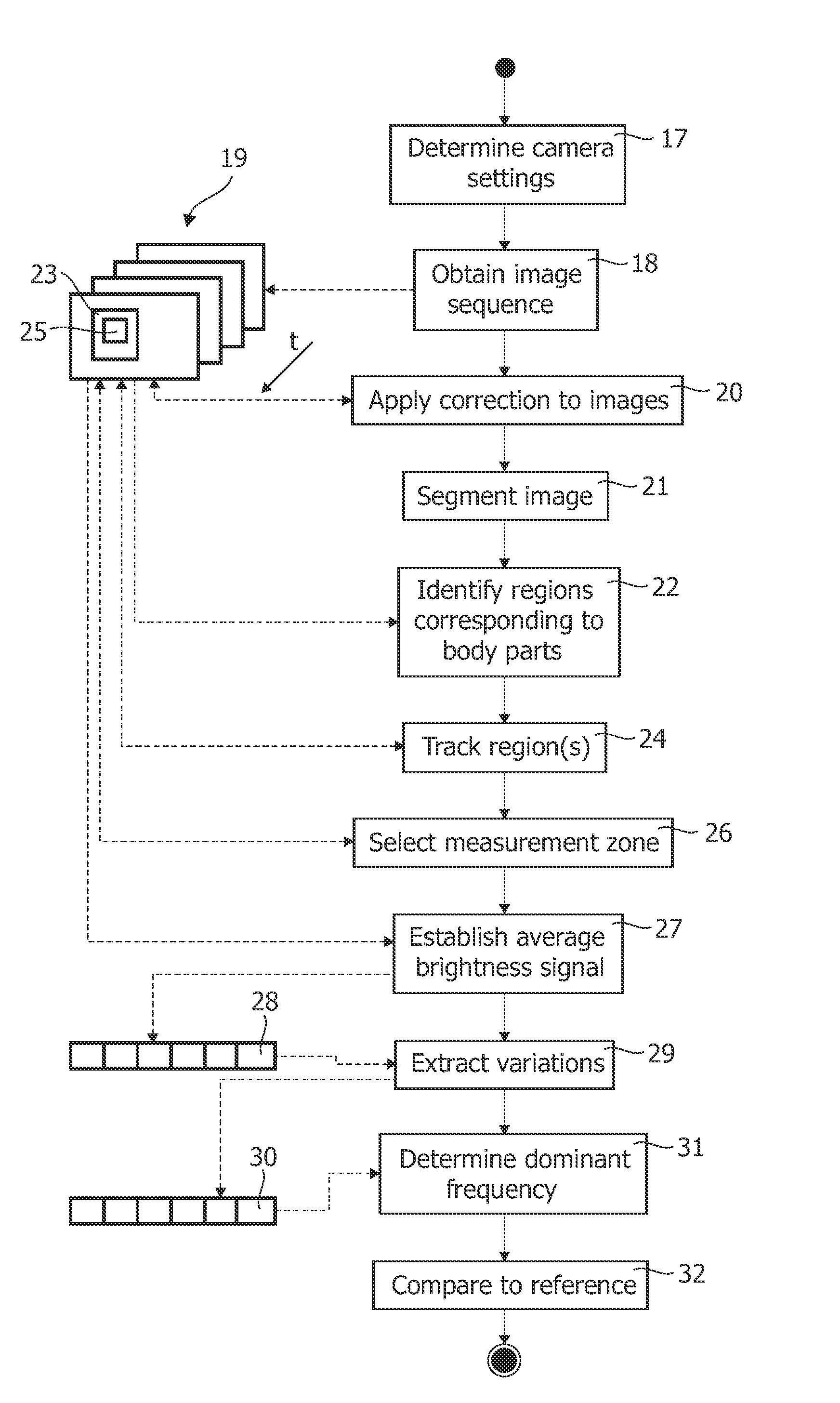
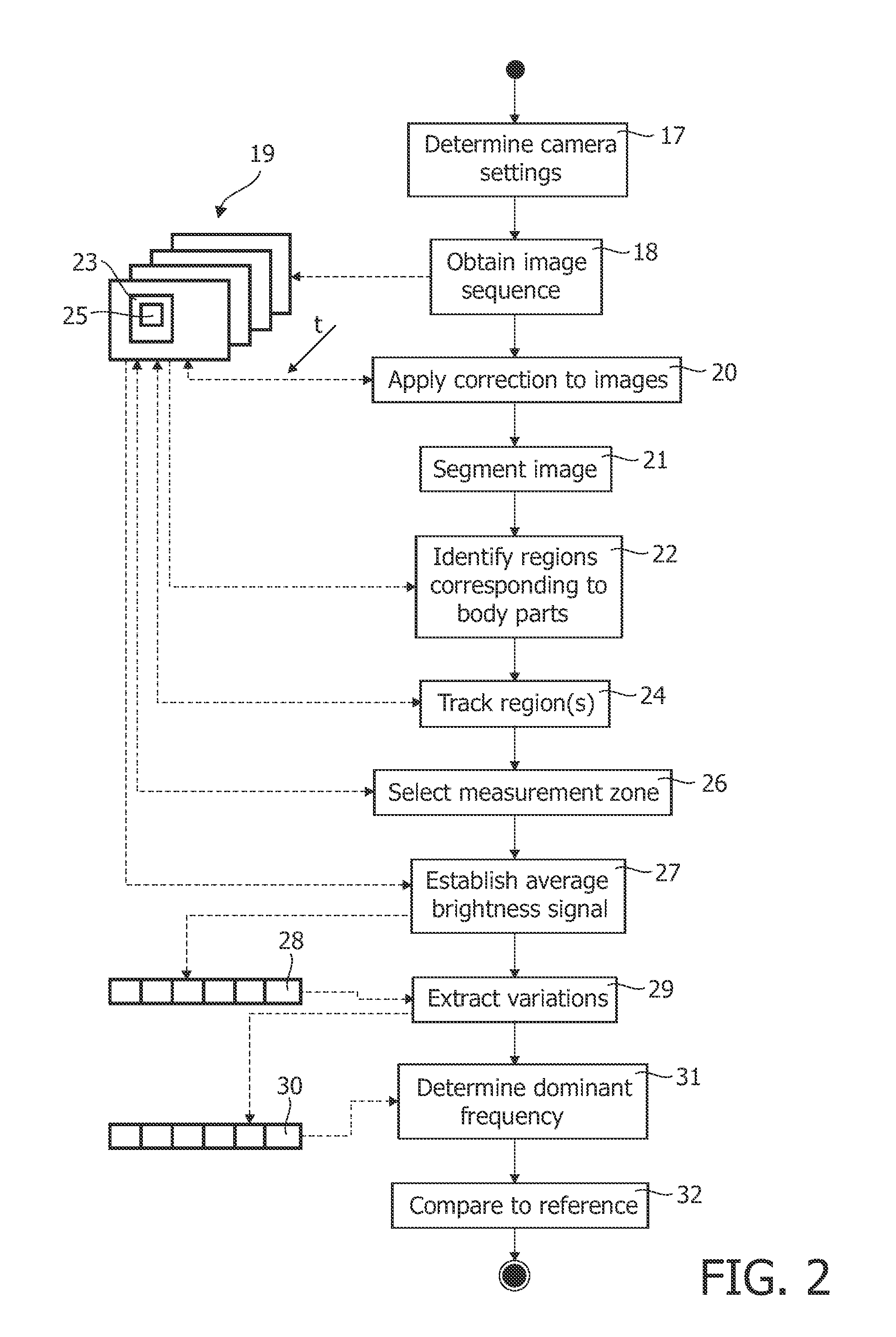
InactiveUS20110311143A1Improve signal-to-noise ratioSufficient degree of accuracyImage enhancementImage analysisFrequency spectrumFrequency matching
A method of controlling a function of a device, includes obtaining a sequence (19;34;48) of digital images taken at consecutive points in time. At least one measurement zone (25) including a plurality of image points is selected. For at least one measurement zone (25), a signal (30;41;55) representative of at least variations in a time-varying value of a combination of pixel values at least a number of the image points is obtained and at least one characteristic of the signal (30;41;55) within at least a range of interest of its spectrum relative to comparison data is determined. The determination comprises at least one of: (i) determining whether the signal (30;41;55) has a spectrum with a local maximum at a frequency matching a comparison frequency to a certain accuracy; and (ii) determining whether at least a certain frequency component of the signal (30;41;55) is in phase with a comparison signal to a certain accuracy. The function is controlled in dependence on whether the determination is positive.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Musical composition system and method of controlling a generation of a musical composition
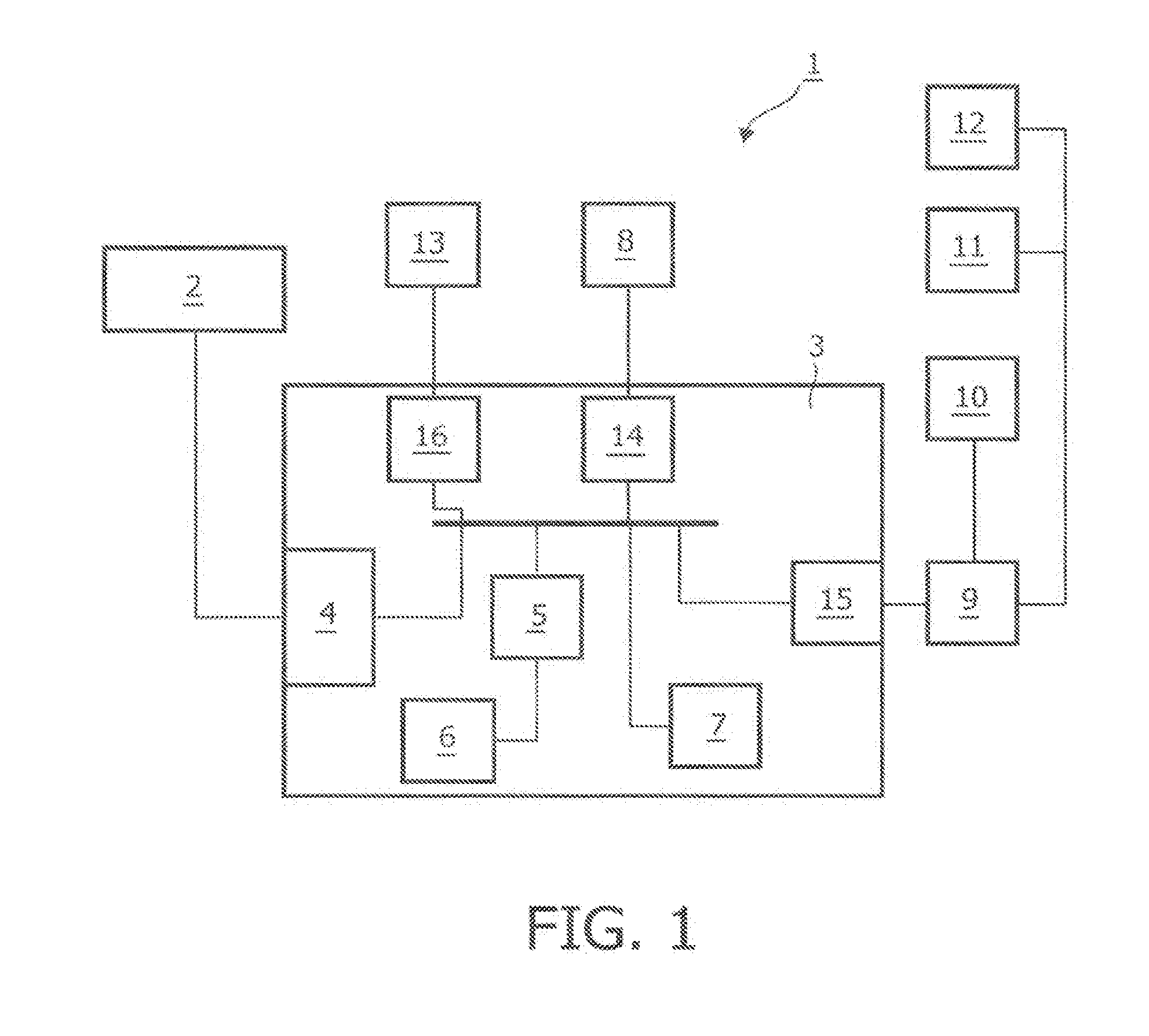
InactiveUS20100043625A1Attempt have been hamperedCustomised easilyElectrophonic musical instrumentsReproductionSpatial ordering
A musical composition system, includes a plurality of tokens (5-7) of visibly distinct types, each representing aspects of at least a fragment of a musical composition, wherein the tokens are configured for placement by at least one user in a spatial configuration; a system for determining respective locations and types of an assembly of tokens (5-7) placed in a spatial configuration by the user(s); a system (13-16;44-46) for translating a spatial ordering of the tokens (5-7) in the spatial configuration into a temporal ordering; a system (13,18,40;44-46) for translating the types of the tokens (5-7) into respective aspects of at least a fragment of a musical composition; and a system (13,18-20;44-46) for generating at least one signal representing a synthesis of the respective aspects of fragments of a musical composition in accordance with the temporal ordering, the signals being suitable for audible reproduction. It is arranged to detect or prevent at least an attempted placement of a token of a certain type at a position in the spatial ordering violating any of at least one constraint associated with the certain type.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Method of controlling a function of a device and system for detecting the presence of a living being
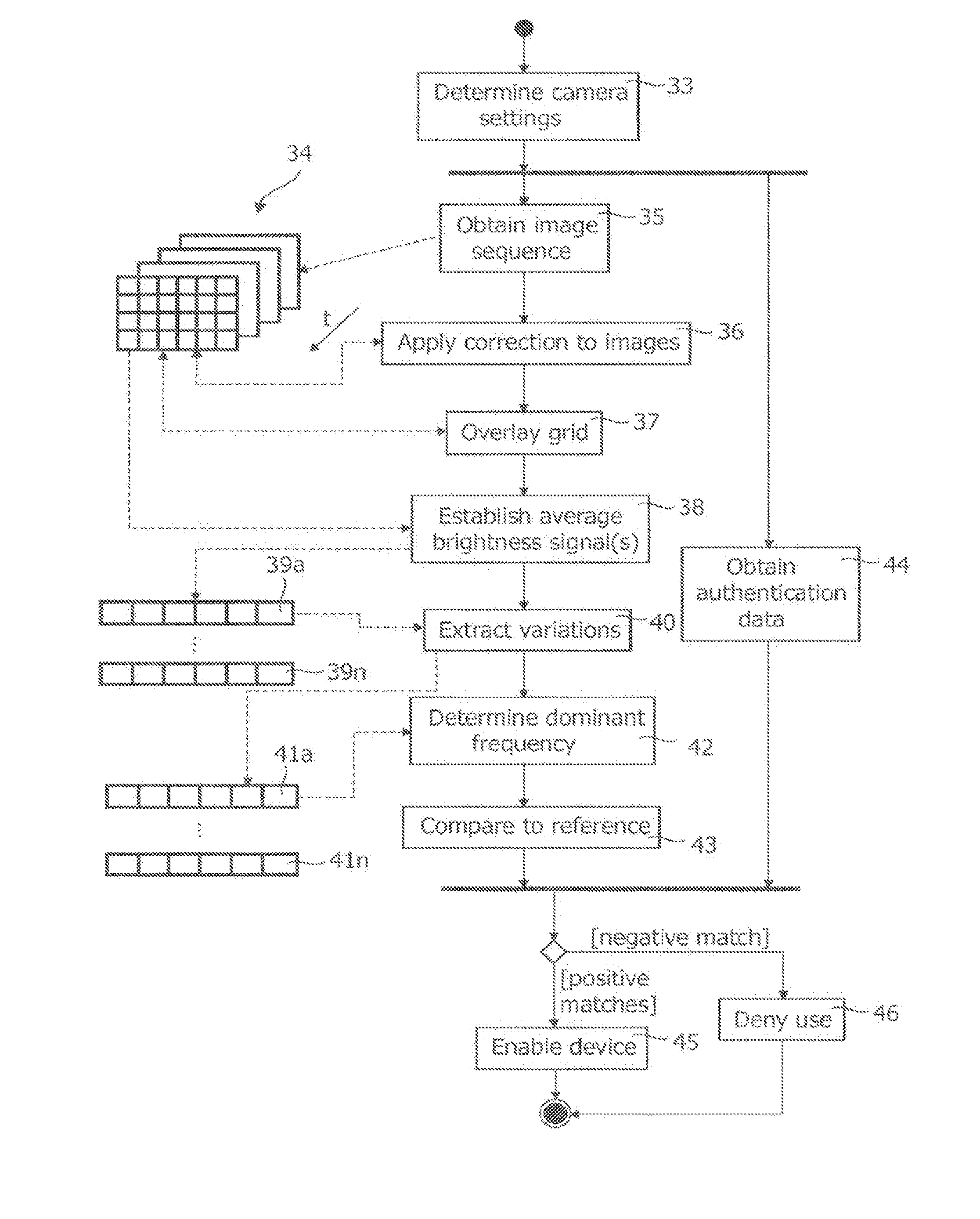
InactiveUS20140023235A1Improve signal-to-noise ratioSufficient degree of accuracyImage enhancementImage analysisFrequency spectrumFrequency matching
A method of controlling a function of a device, includes obtaining a sequence (19;34;48) of digital images taken at consecutive points in time. At least one measurement zone (25) including a plurality of image points is selected. For at least one measurement zone (25), a signal (30;41;55) representative of at least variations in a time-varying value of a combination of pixel values at at least a number of the image points is obtained and at least one characteristic of the signal (30;41;55) within at least a range of interest of its spectrum relative to comparison data is determined. The determination comprises at least one of:(i) determining whether the signal (30;41;55) has a spectrum with a local maximum at a frequency matching a comparison frequency to a certain accuracy; and(ii) determining whether at least a certain frequency component of the signal (30;41;55) is in phase with a comparison signal to a certain accuracy. The function is controlled in dependence on whether the determination is positive.
Owner:KONINKLJIJKE PHILIPS NV
Method and system for manufacturing a hearing device with a customized feature set
InactiveUS20100067711A1Minimize storage spaceBetter meetingMicrophonesCharacter and pattern recognitionFeature setHearing apparatus
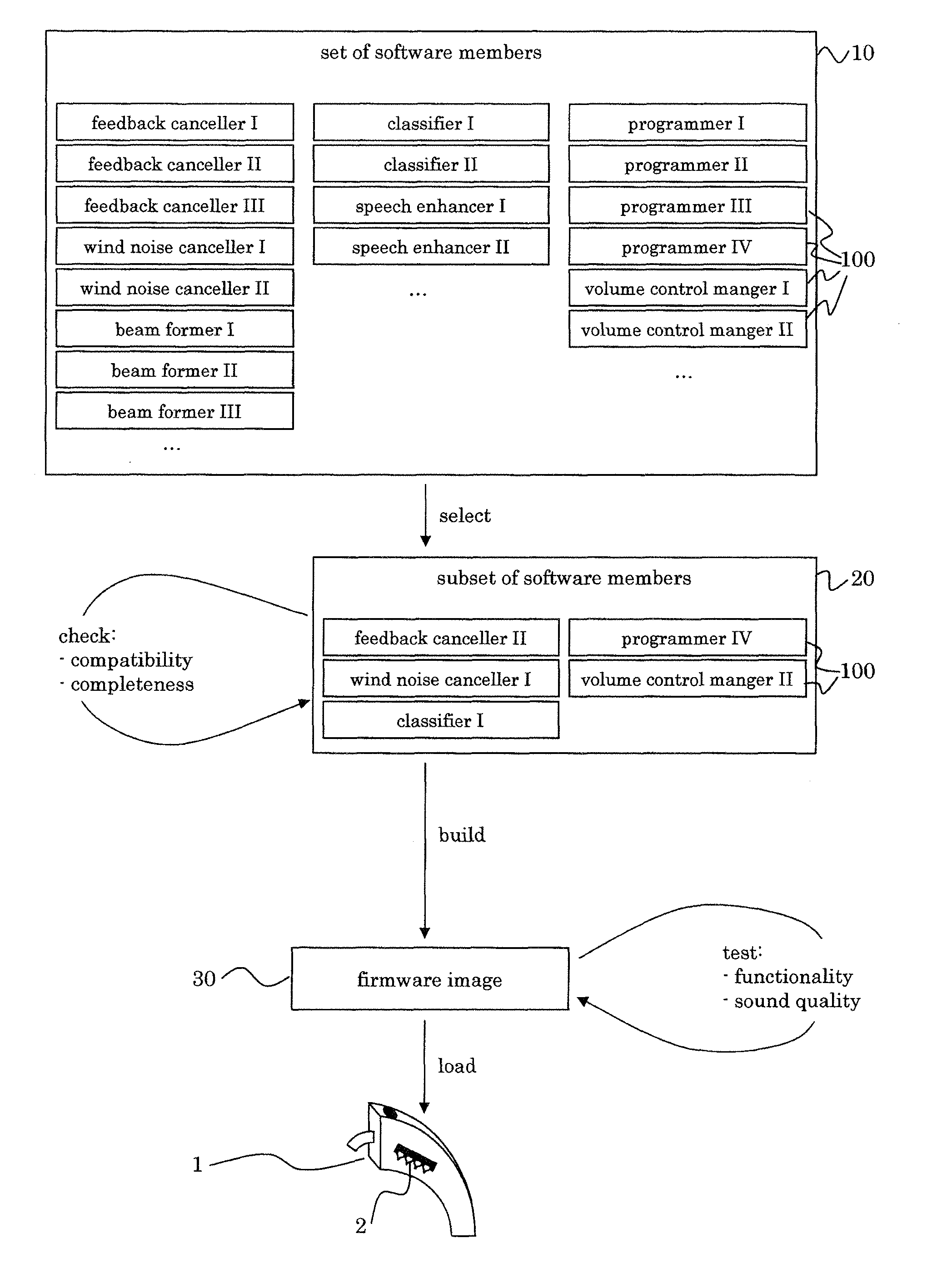
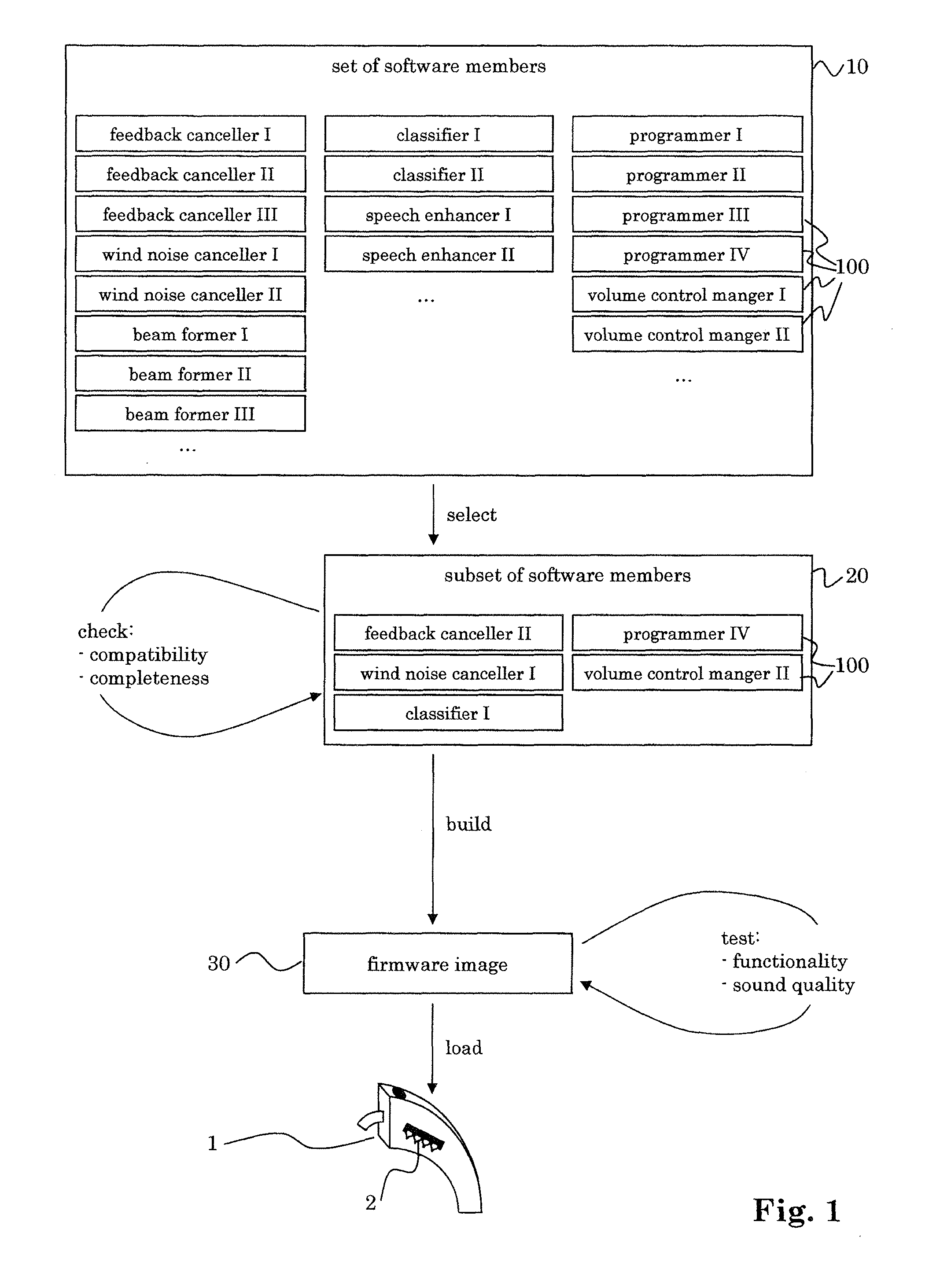
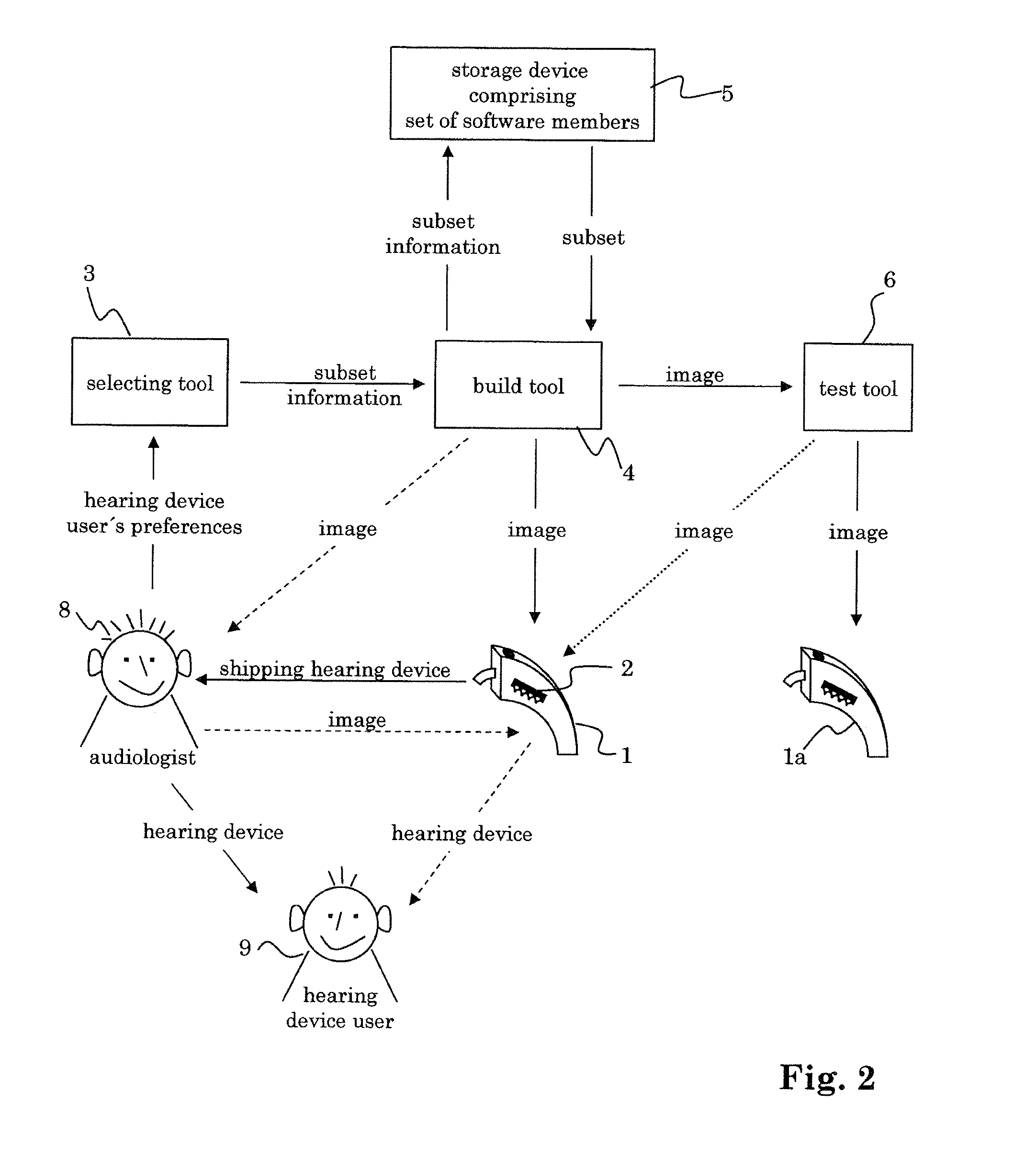
The method for manufacturing a hearing device, which hearing device includes at least one programmable processor, includes the steps of a) providing a set of software members, b) selecting a subset of said set, and c) creating an image of said subset, which is executable in said at least one processor. This allows to select from a large set of software members only those, which are suitable for a specific user. The system for manufacturing a hearing device in dependence of individual preferences of a user of said hearing device, which hearing device includes at least one programmable processor, includes a selecting tool allowing to select a subset of software members from a set of software members, and a build tool for creating an image of said subset of software members, wherein said image is executable in said at least one processor.
Owner:PHONAK
System and method of allowing user mode applications with access to file data
InactiveUS7478237B2Attempt have been hamperedIncrease speedDigital data processing detailsUser identity/authority verificationFile systemApplication software
In accordance with this invention, a system, method, and computer-readable medium that aggregates the knowledge base of a plurality of antivirus software applications are provided. User mode applications, such as antivirus software applications, gain access to file system operations through a common information model, which obviates the need for antivirus software vendors to create kernel mode filters. When file system operations are available to antivirus software applications, the present invention may cause each antivirus software application installed on a computing device to perform a scan to determine if the data is malware.
Owner:MICROSOFT TECH LICENSING LLC
Method and system for facilitating transactions
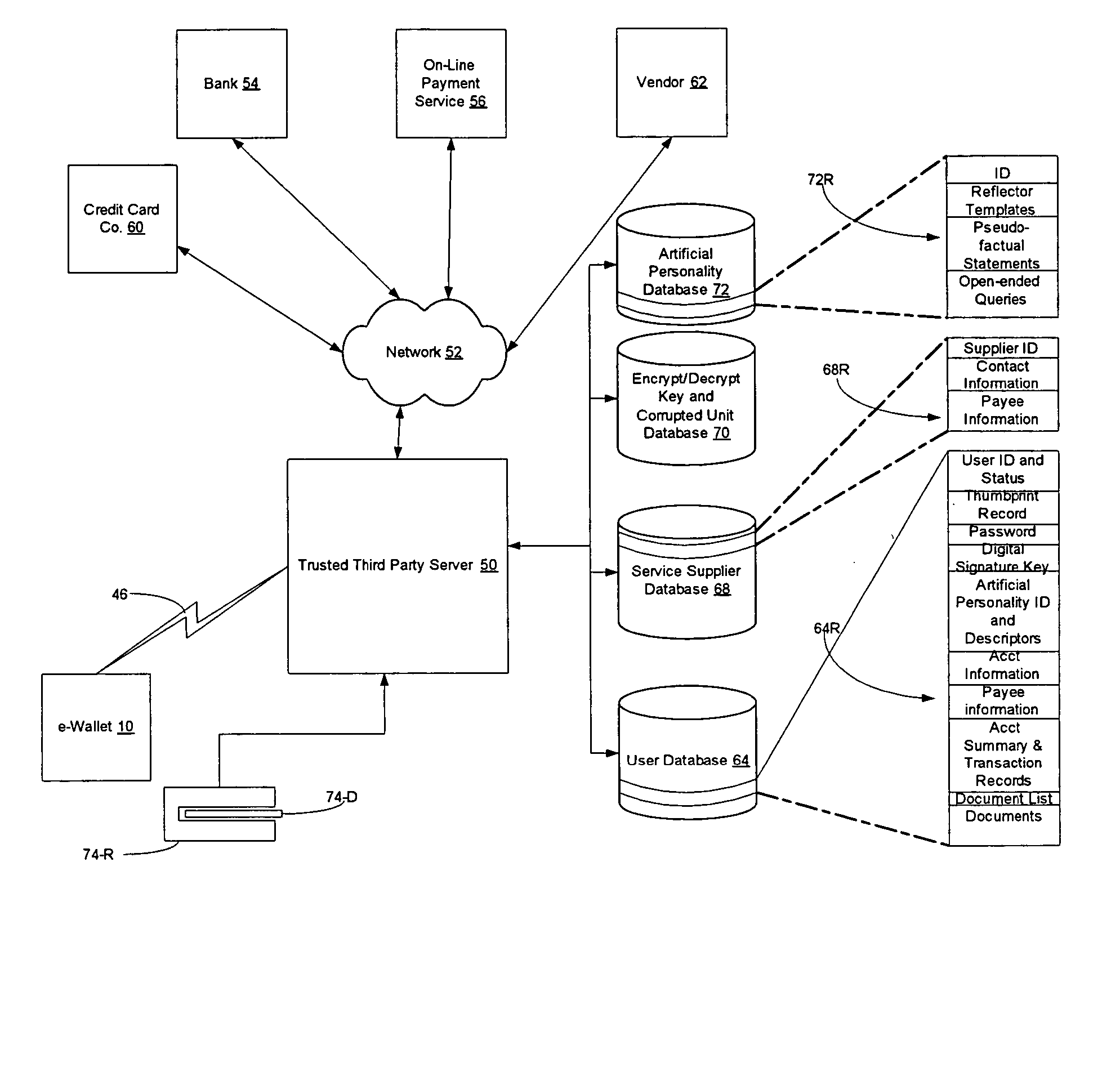
InactiveUS20050131839A1High costAttempt have been hamperedDigital data processing detailsUnauthorized memory use protectionThird partyInternet privacy
A system for facilitating a transaction between a first party and a second party is controlled by a trusted third party system and is programmed to carry out the method by receiving the first party's instructions for fulfilling at least a part of the first party's obligations in said transaction. The system communicates with the second party and provides the second party with perceptible assurance that the second party is in communication with a trusted third party system through the system. The system transmits information to the second party to provide assurance that the first party's instructions have been or will be fulfilled. Thus trust in the third party is transferred to the first party and the second party can trust that the first party's obligations have been or will be fulfilled.
Owner:PITNEY BOWES INC
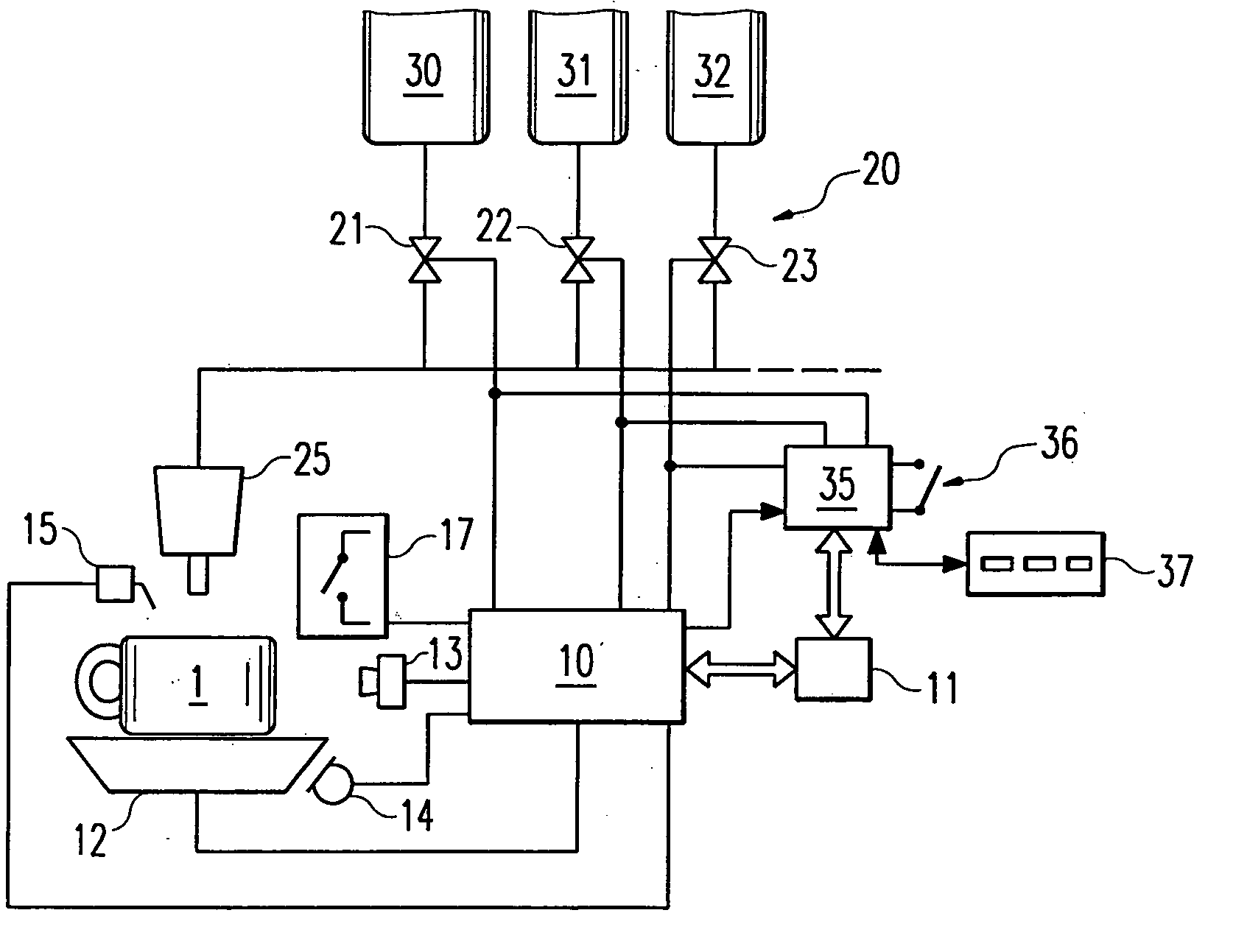
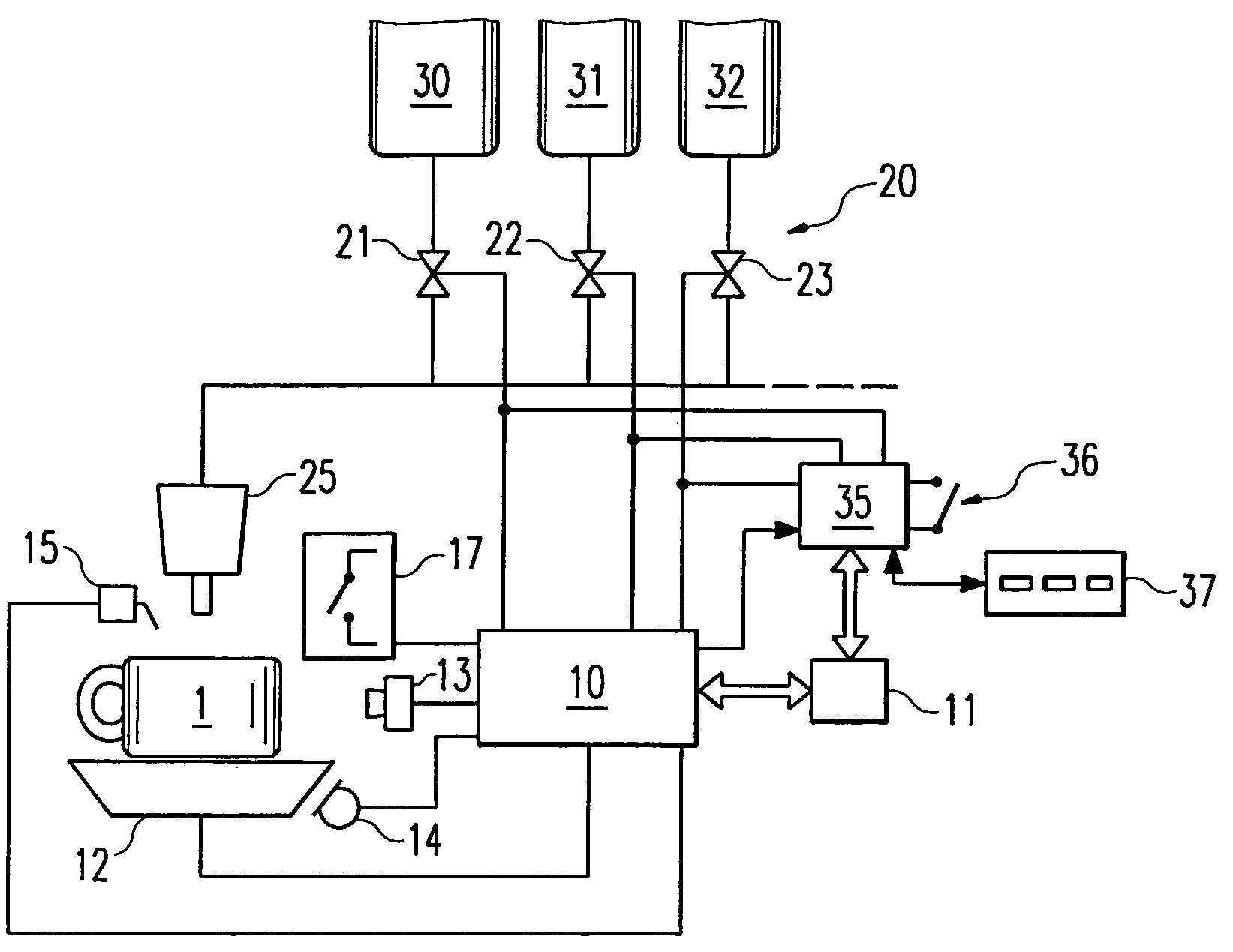
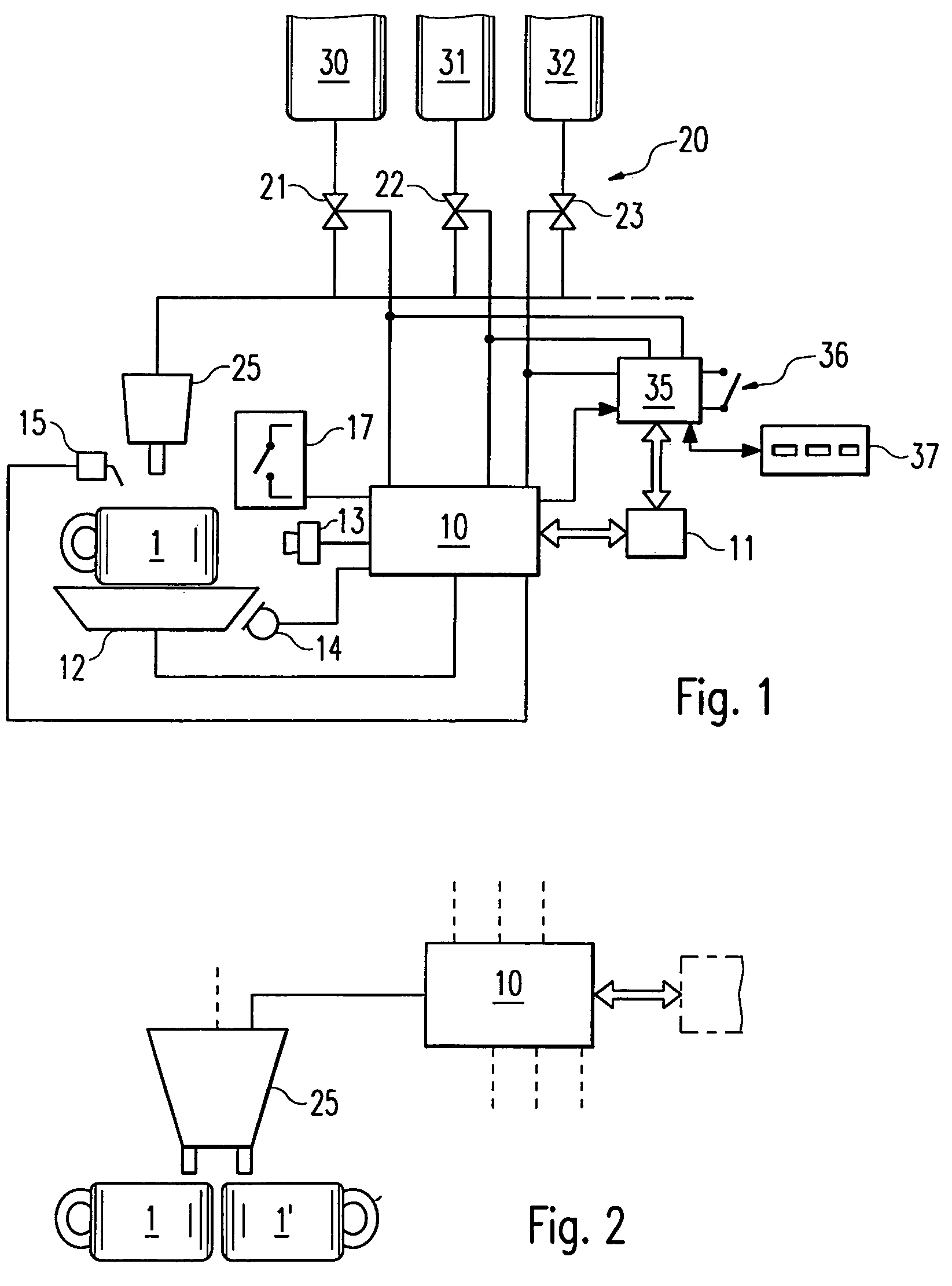
Dispensing device for drinks
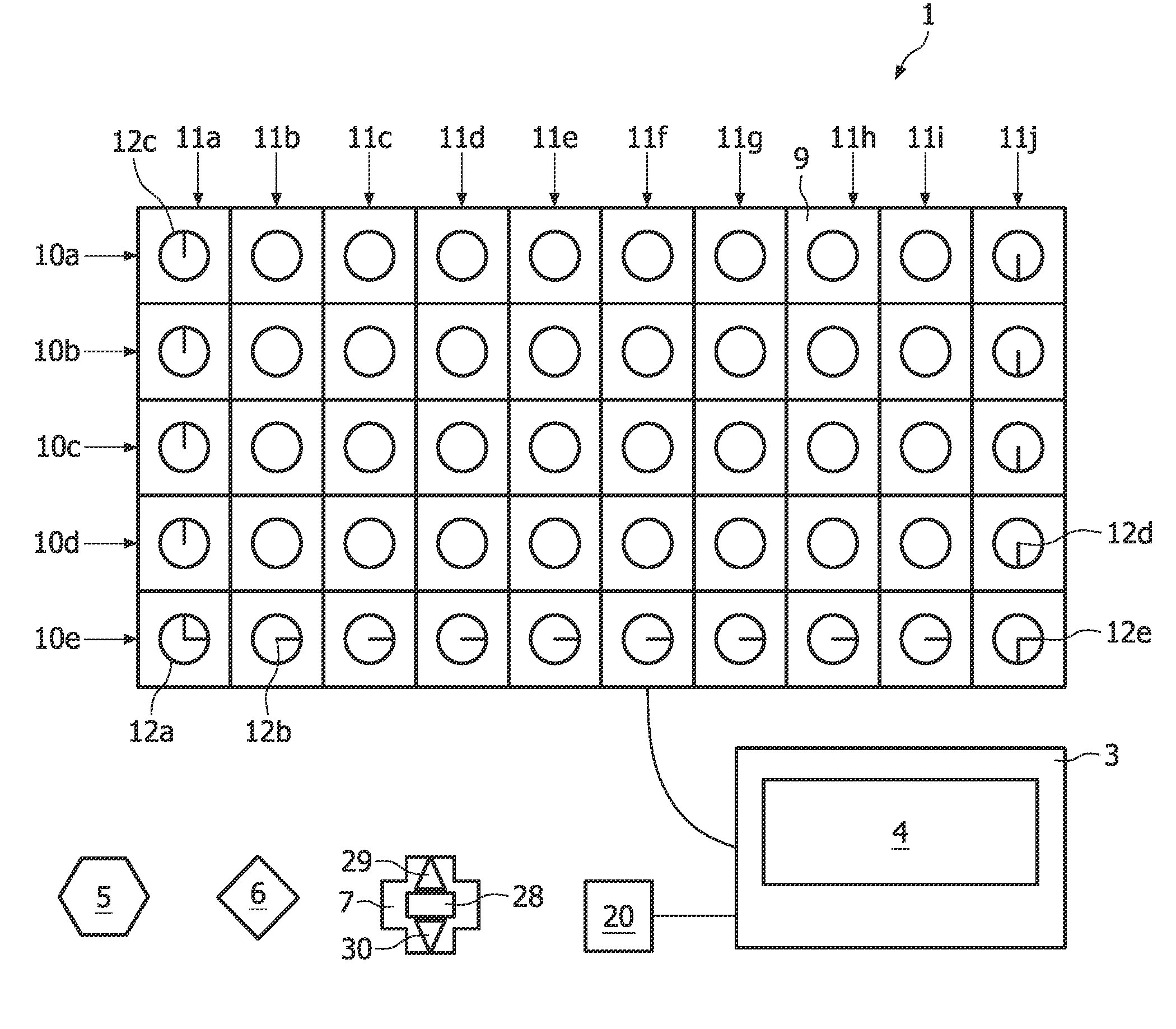
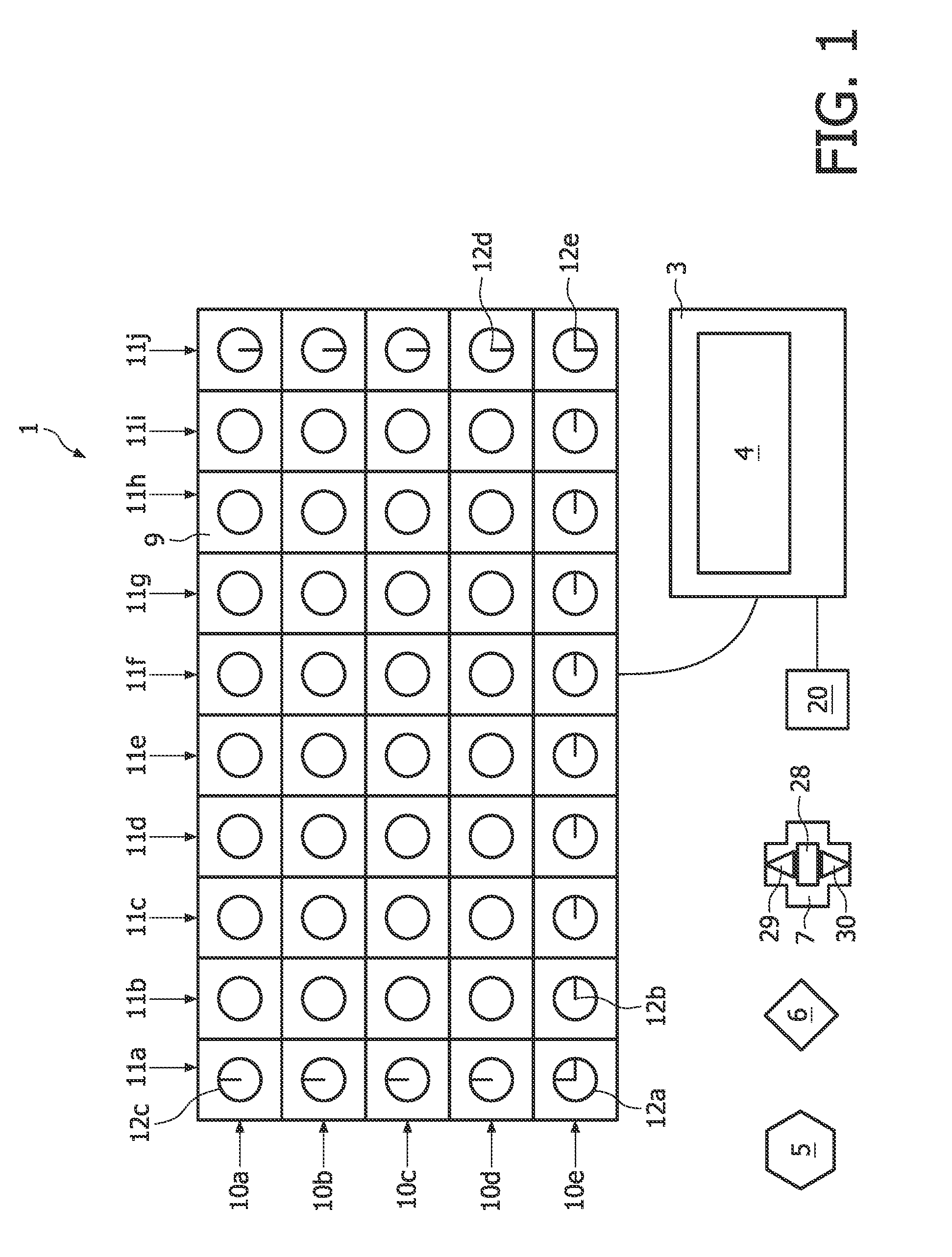
InactiveUS20060123994A1Attempt have been hamperedImprove reliabilityBarrels/casks fillingBeverage vesselsSoft drinkBiomedical engineering
The invention relates to dispensing devices for drinks or similar dosable liquid foodstuffs, e.g. coffee, milk or soft drinks, comprising manually actuatable selector switches for determining the type and quantity of the foodstuff to be dispensed. The aim of the invention is to simplify the use of one such dispensing device. To this end, said device is provided with an identification device (10) for identifying different types of containers (1) for receiving the foodstuff with subsequent consumption from the container, and for emitting an identification signal describing the container. The dispensing device is also provided with a valve device (20) which, on the basis of the identification signal, connects at least one of a plurality of supply devices (30 to 32) for supplying a defined foodstuff or a mixture of defined foodstuffs by means of a filling device (25), and fills the container (1) with a pre-determined quantity of the defined foodstuff or the mixture thereof. Said arrangement enables the customer to determine the amount of foodstuff to be contained in the container, by the selection of the container, thus simplifying the operation of the dispensing device.
Owner:FRANKE TECH & TRADEMARK LTD
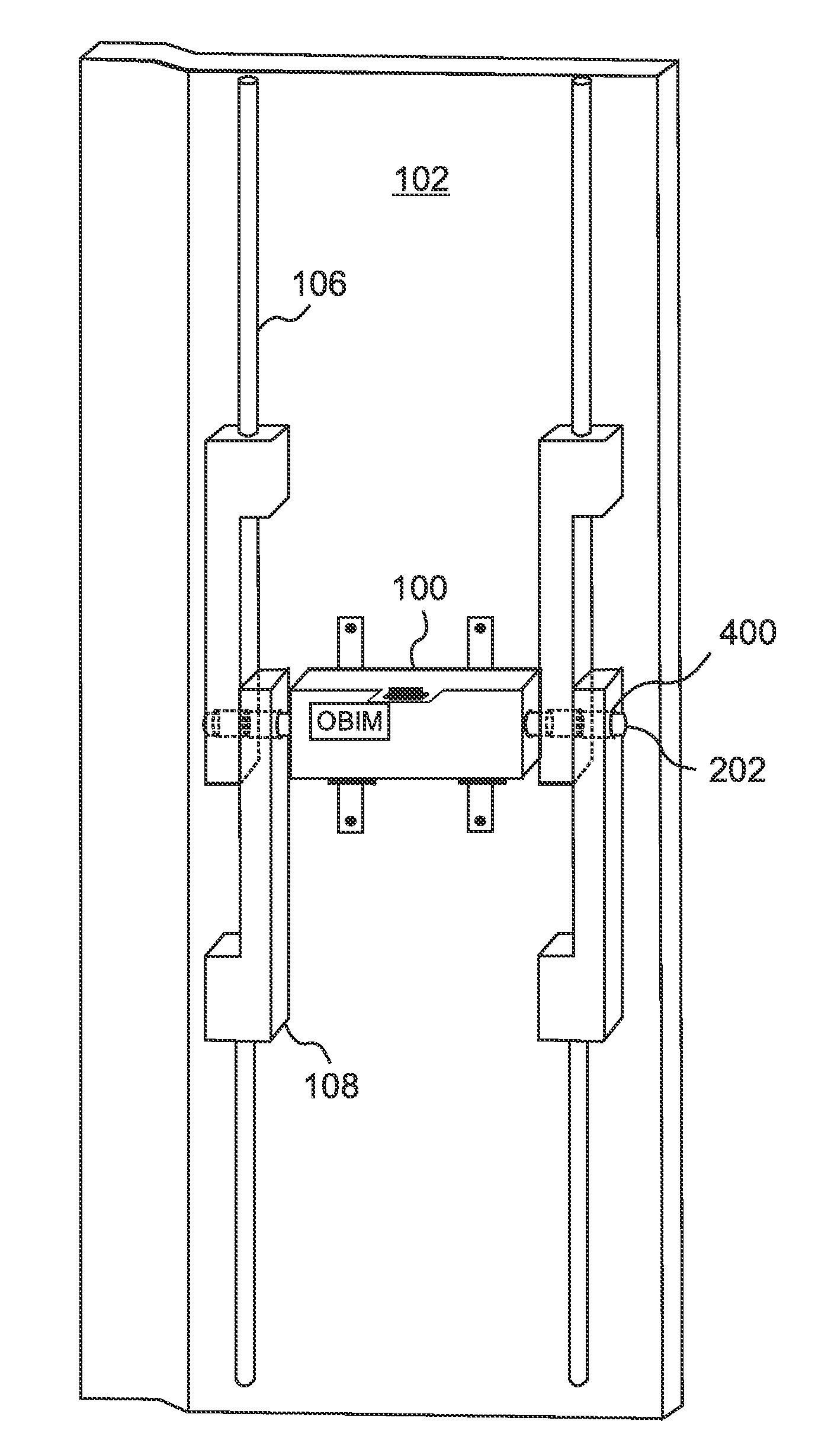
System and method for secure shipment of high-value cargo
ActiveUS20100257904A1Improve securityPrevent openingElectric signal transmission systemsDigital data processing detailsDouble blindLocking mechanism
A system for protecting high-value cargo enclosed in a container, while maintaining the container indistinguishable from similar low value shipments, includes an onboard identity module (OBIM) cooperative with an internal locking mechanism (ILM), both of which are externally undetectable. The OBIM can secure the ILM and prevent the container from being opened until a properly encoded unlocking signal from a Security Management System (SMS) is wirelessly received by the OBIM. The unlocking signal can be a composite including a plurality of species of wireless signals such as different frequencies of AM and FM encoded RF and acoustic signals, transmitted simultaneously and / or at specified intervals. In embodiments the OBIM enables remote tracking of the container, and in some embodiments the tracking is double-blind, whereby a Master Number (MN) recorded in shipping documents is associated with a “Random Number” (RN) used for tracking, the association being known only to the SMS.
Owner:PERFORMANCE PARTNERS
Apparatus and method for performing speculative reads from a scan control unit using FIFO buffer units
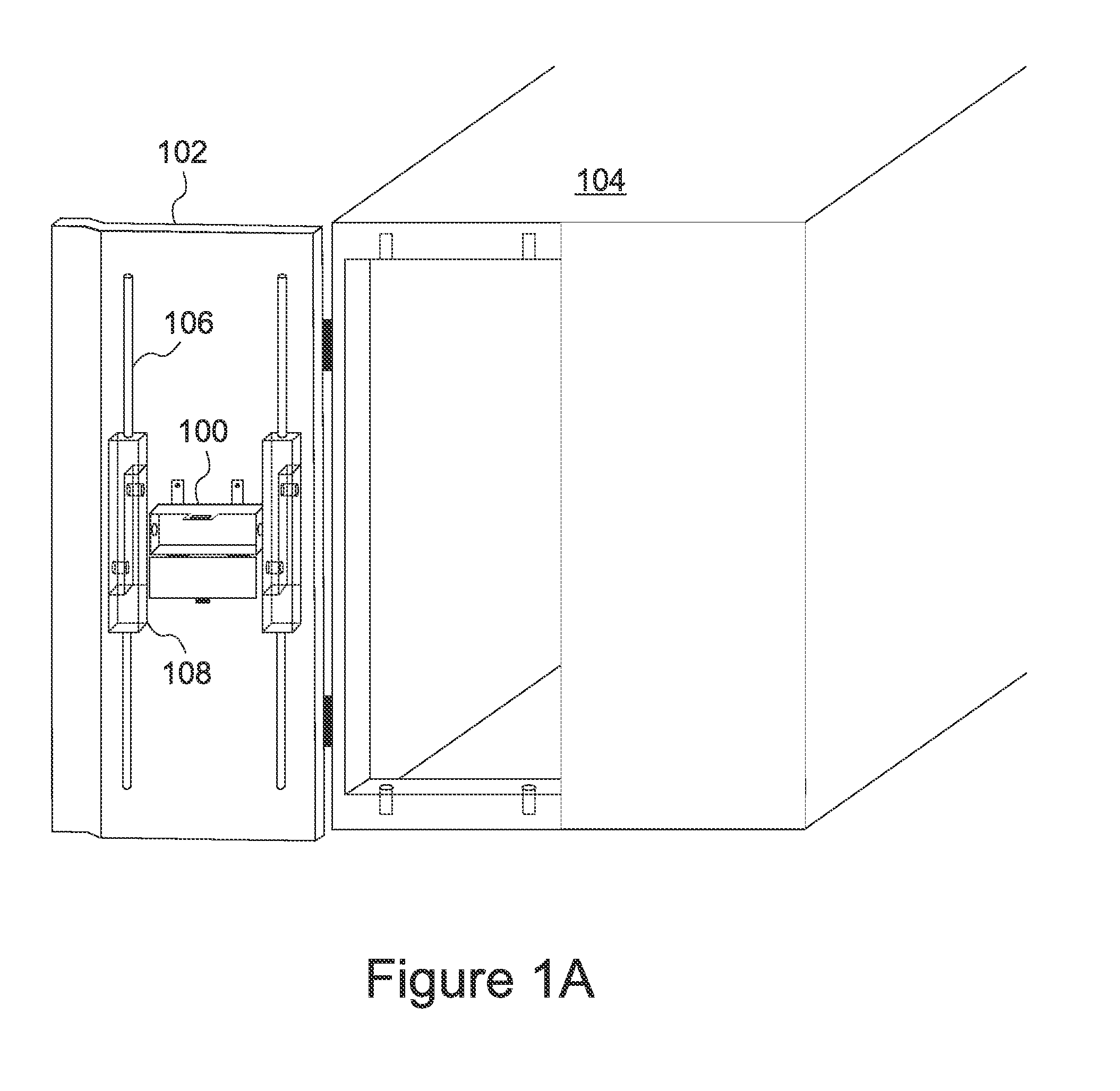
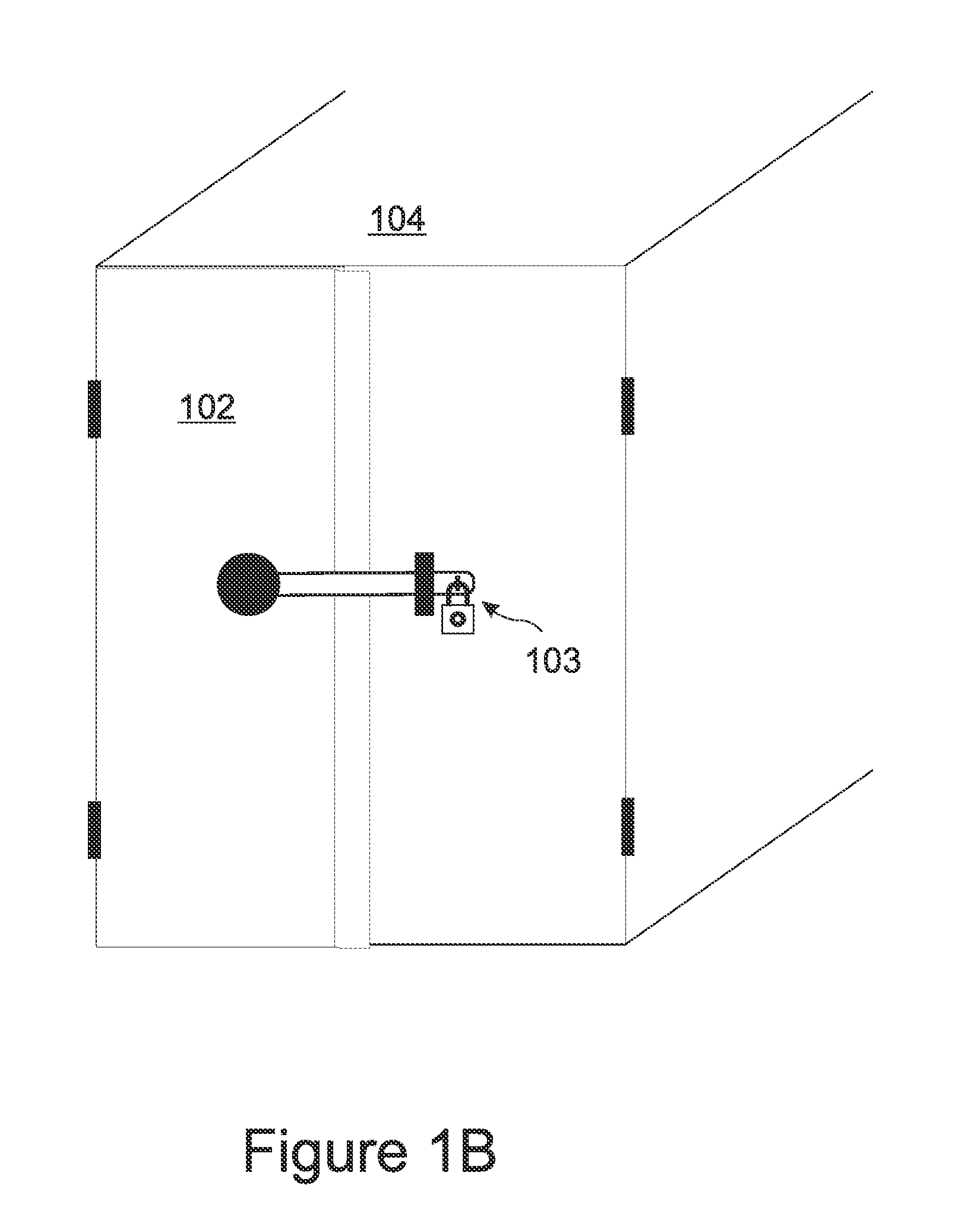
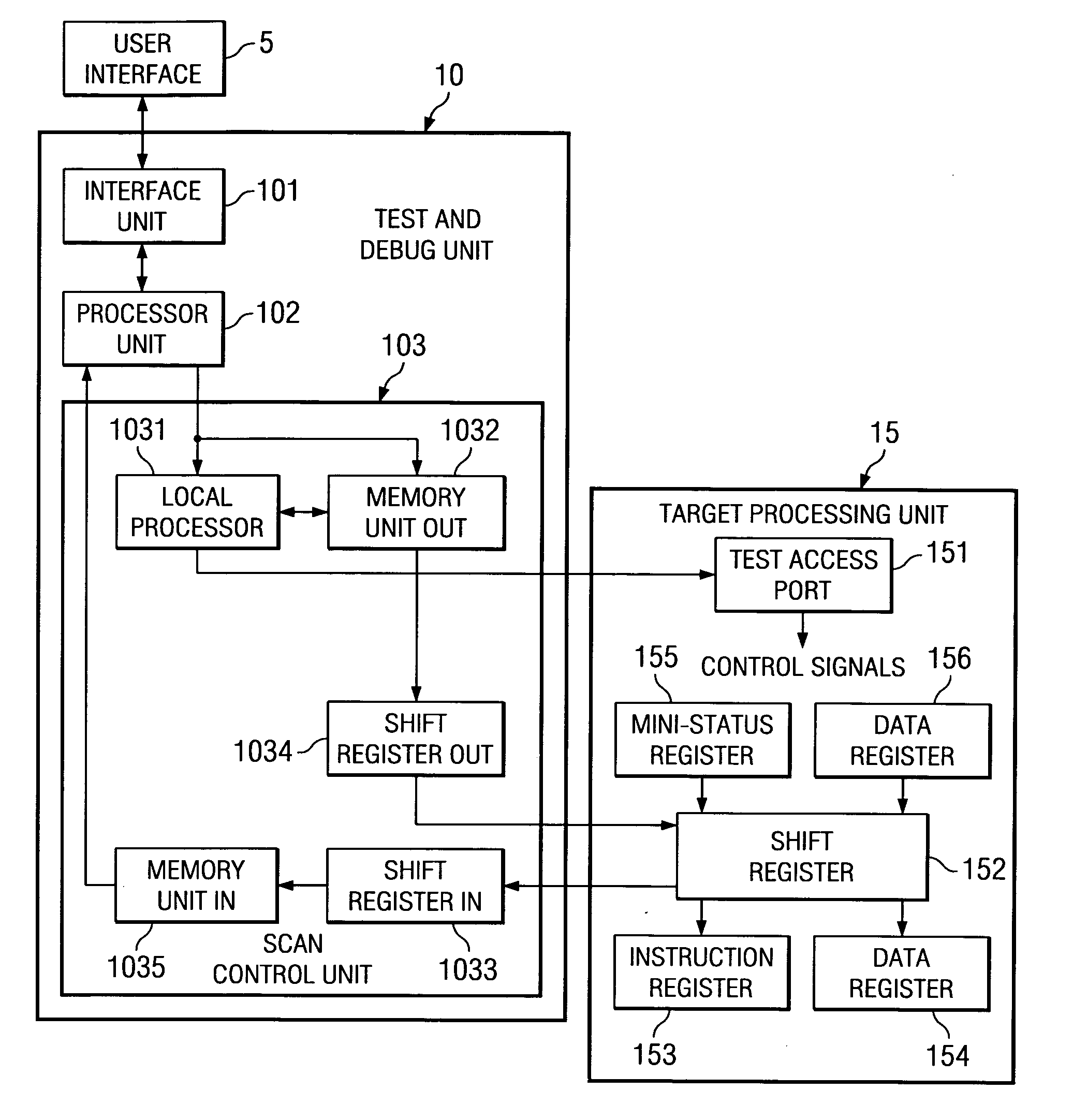
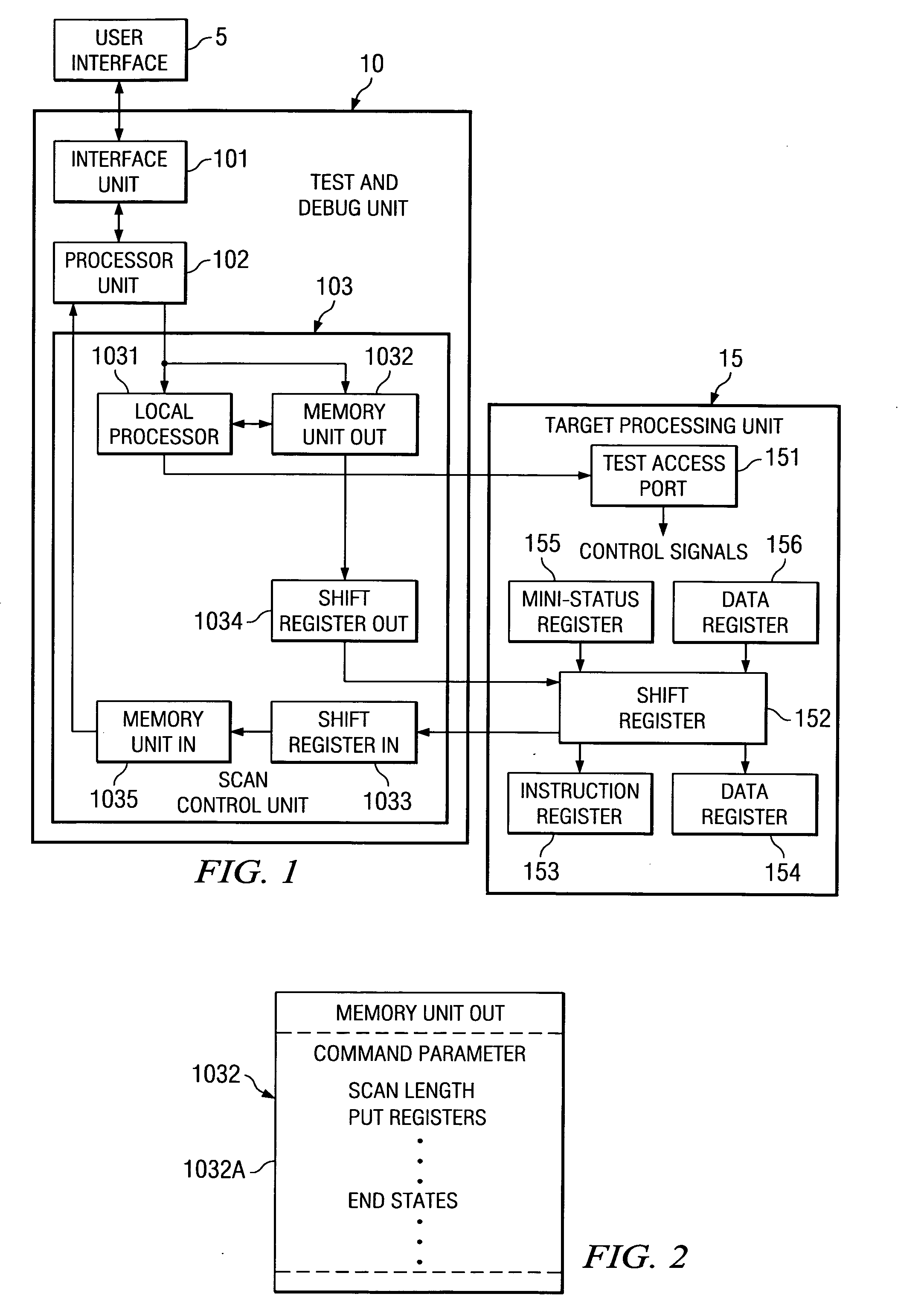
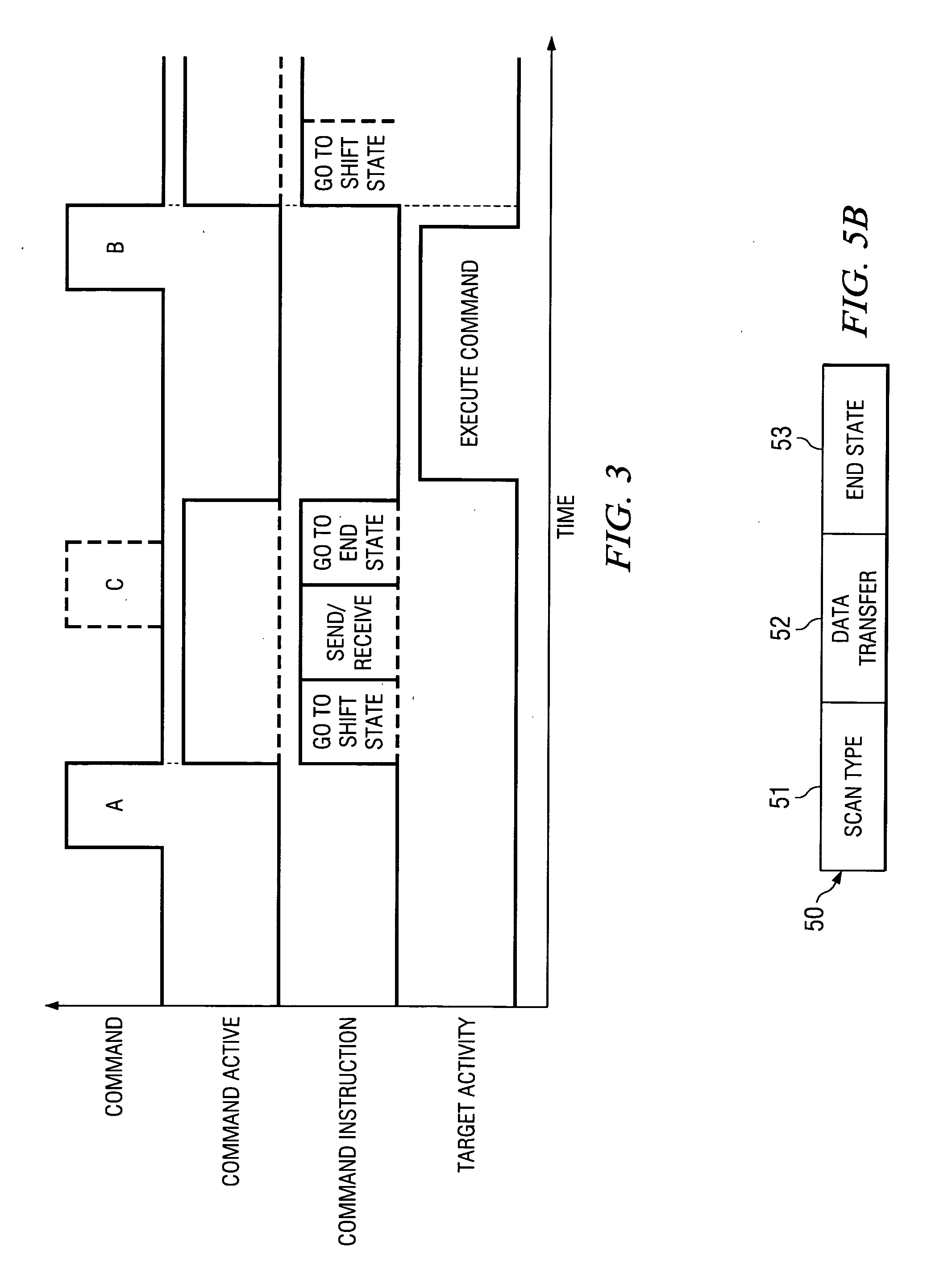
ActiveUS20050120269A1Attempt have been hamperedError detection/correctionComputer hardwareTransfer mode
In a JTAG test and debug environment, the signal groups may have a variable length, a fixed length of a combination of both fixed and variable signal groups to be transferred to the target processor. To implement the three types of data transfers, the storage unit associated with the scan control unit includes two types of storage locations, fixed signal length storage locations and variable length storage locations. The software can select the mode of data transfer and this selection is provided to the scan controller by a command.
Owner:TEXAS INSTR INC
Hypervisor-based virtual machine isolation apparatus and method
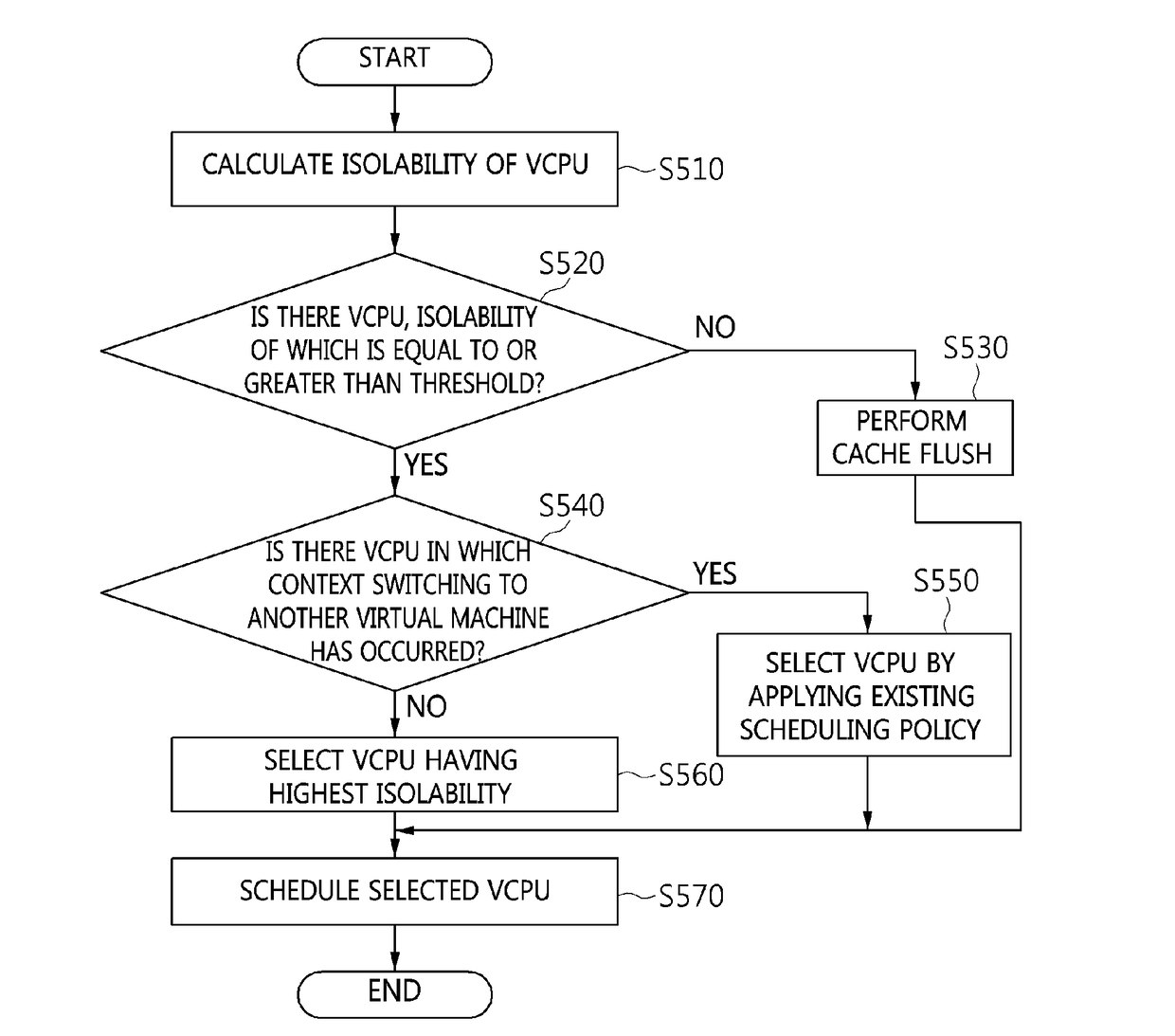
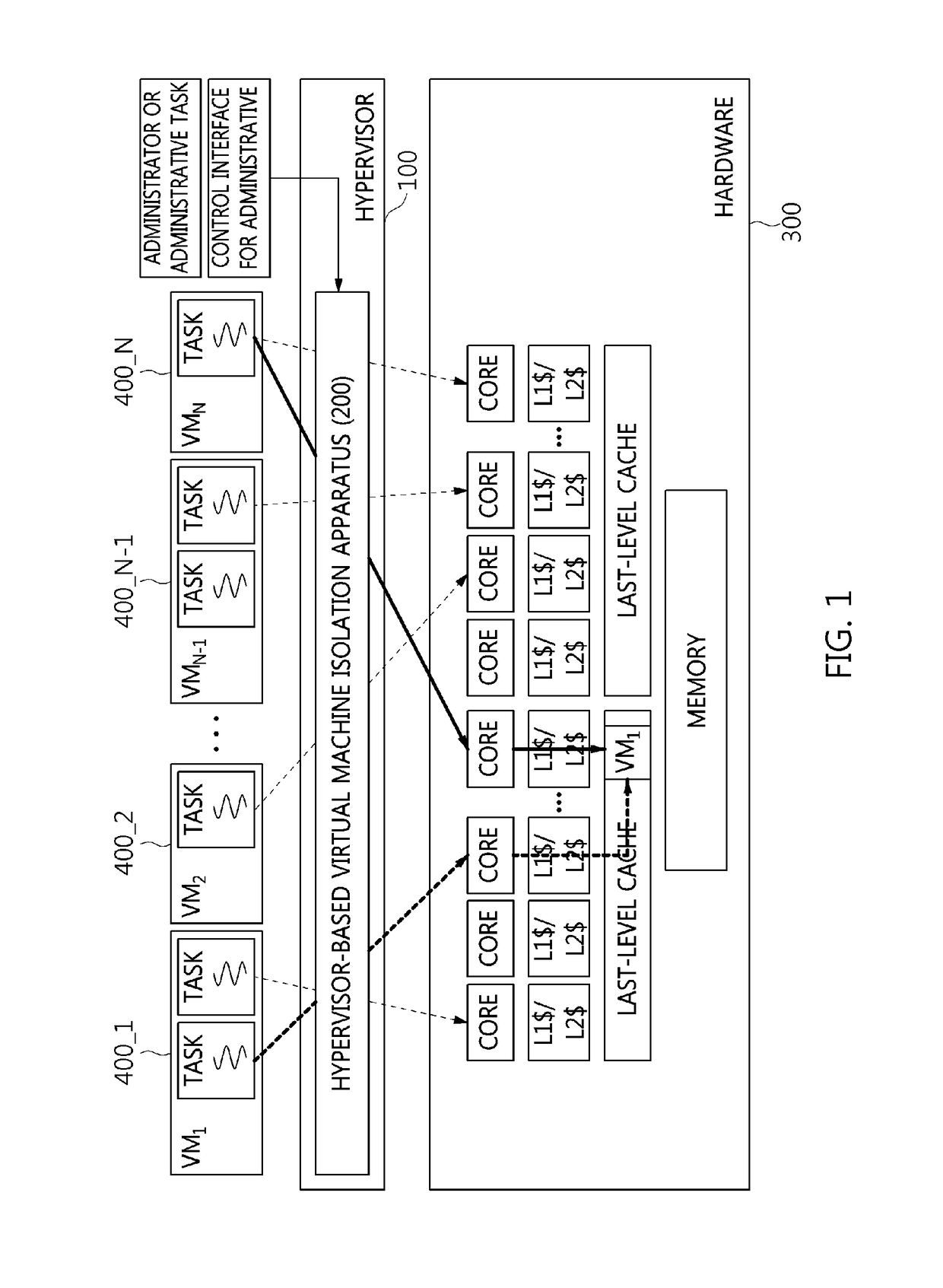
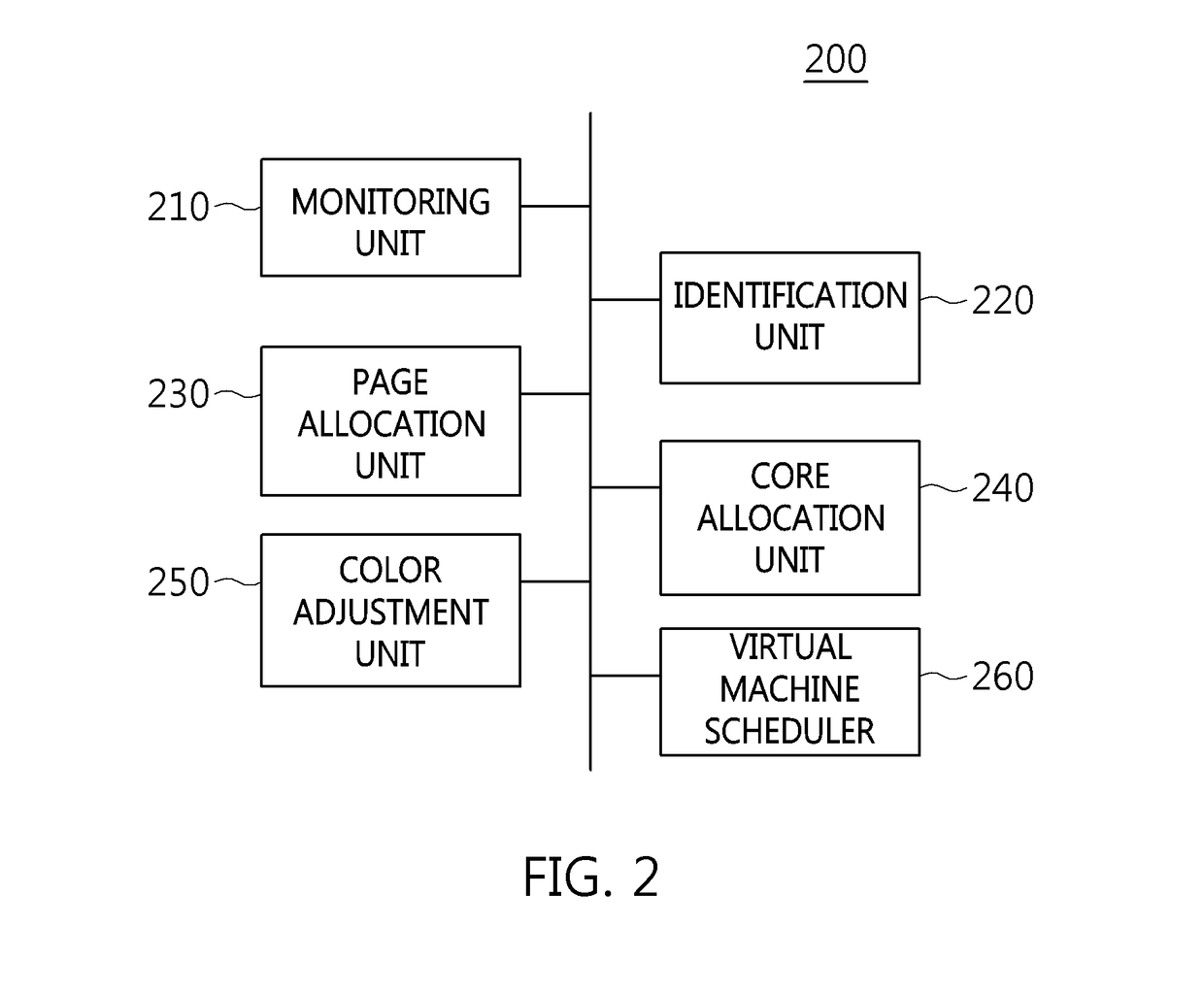
ActiveUS20180300182A1Attempt have been hamperedLoad minimizationResource allocationPlatform integrity maintainanceVirtual machinePage frame
A hypervisor-based virtual machine isolation apparatus and method. The hypervisor-based virtual machine isolation method performed by the hypervisor-based virtual machine isolation apparatus includes when a hypervisor starts to run virtual machines, allocating one or more colors to each of the virtual machines, allocating a page frame corresponding to the allocated colors to the corresponding virtual machine, allocating an accessible core depending on the colors of the virtual machine, and performing isolation between virtual machines corresponding to an identical color by changing a temporal / spatial scheduling order between the virtual machines corresponding to the identical color.
Owner:ELECTRONICS & TELECOMM RES INST
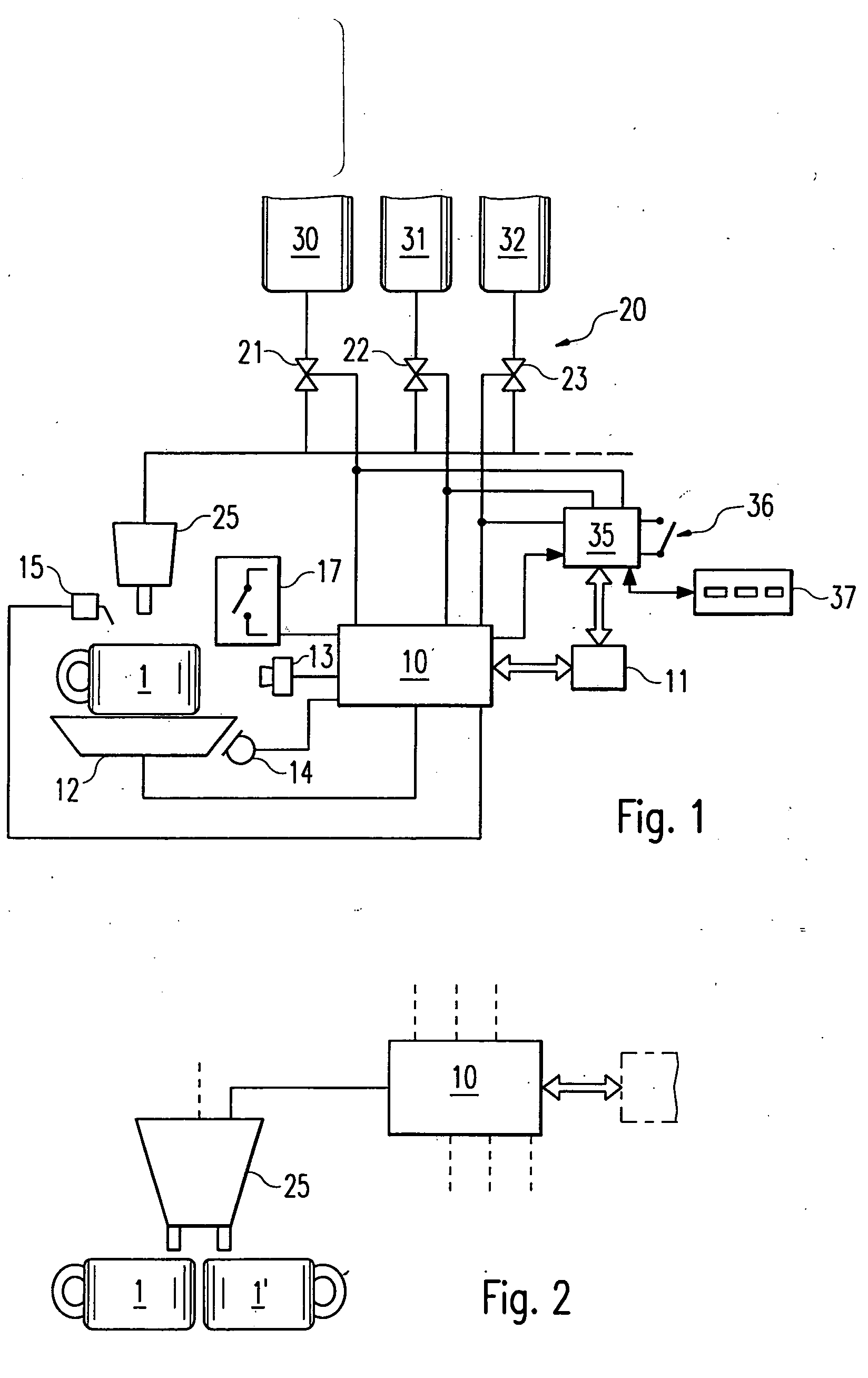
Dispensing device for drinks
InactiveUS7637205B2Improve reliabilityAttempt have been hamperedBarrels/casks fillingBeverage vesselsIdentification deviceBiomedical engineering
The invention relates to dispensing devices for drinks or similar dosable liquid foodstuffs, e.g. coffee, milk or soft drinks, comprising manually actuatable selector switches for determining the type and quantity of the foodstuff to be dispensed. The aim of the invention is to simplify the use of one such dispensing device. To this end, said device is provided with an identification device for identifying different types of containers for receiving the foodstuff with subsequent consumption from the container, and for emitting an identification signal describing the container. The dispensing device is also provided with a valve device which, on the basis of the identification signal, connects at least one of a plurality of supply devices for supplying a defined foodstuff or a mixture of defined foodstuffs by means of a filling device, and fills the container with a predetermined quantity of the defined foodstuff or the mixture thereof. Said arrangement enables the customer to determine the amount of foodstuff to be contained in the container, by the selection of the container, thus simplifying the operation of the dispensing device.
Owner:FRANKE TECH & TRADEMARK LTD
Self-locking USB protection pug device having LED to securely protect USB jack
ActiveUS9734358B2Improve information securityAttempt have been hamperedComputer periphery connectorsInternal/peripheral component protectionEngineeringSelf locking
Owner:HIGH SEC LABS LTD
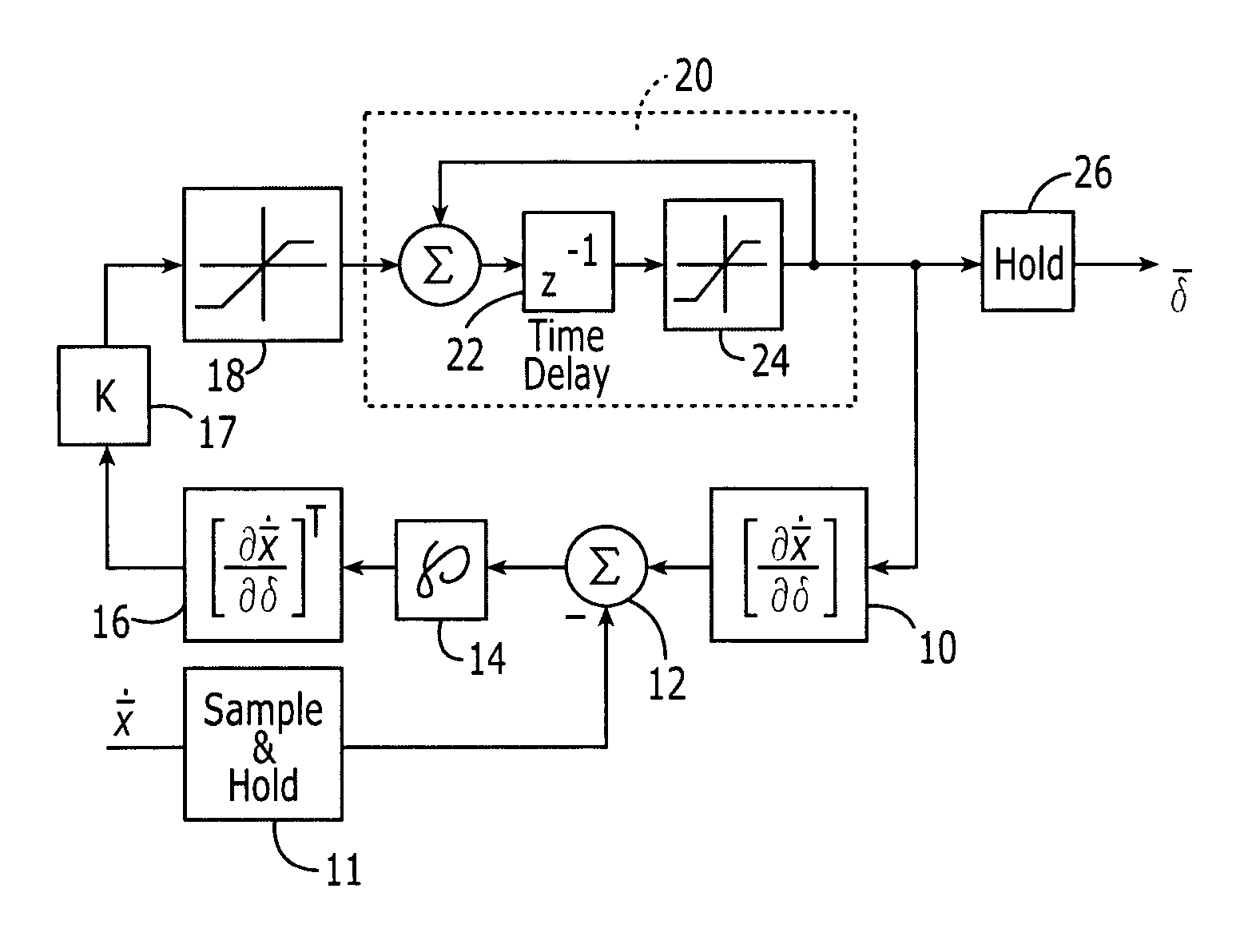
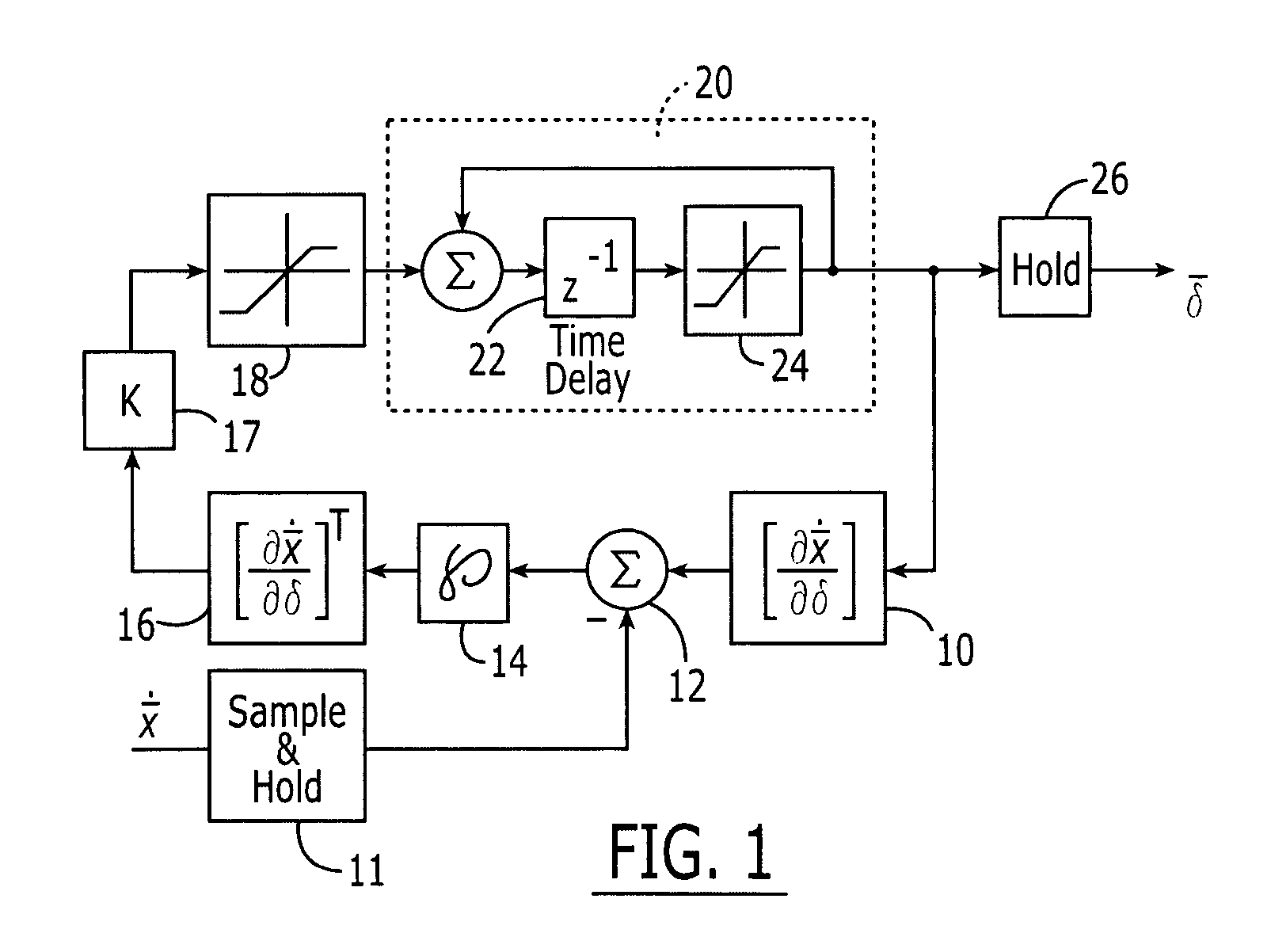
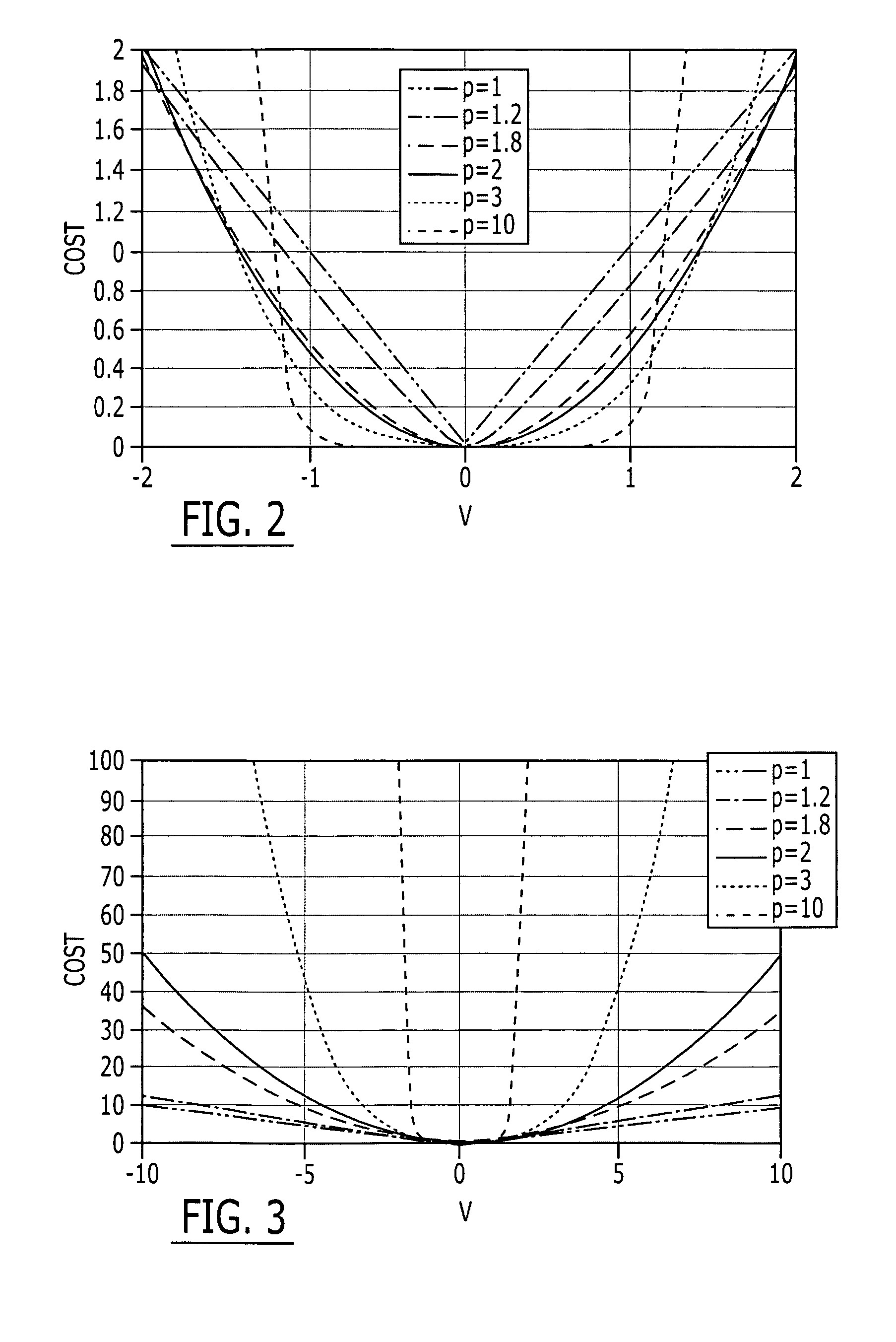
Method and computer program product for controlling the control effectors of an aerodynamic vehicle
InactiveUS7255306B2Improve efficiencyAppropriate weightAircraft stabilisationActuated automaticallyTemporal changeControl signal
A method and computer program product are provided for controlling the control effectors of an aerodynamic vehicle including, for example, the respective positions of nozzles and aerodynamic surfaces, to affect a desired change in the time rate of change of the system state vector. The method initially determines differences between anticipated changes in the states of the aerodynamic vehicle based upon the current state of each control effector, and desired state changes. These differences may be weighted based upon a predetermined criteria, such as the importance of the respective states and / or the weight to be attributed to outliers. The differences between the anticipated and desired state changes are converted to the corresponding rates of change of the control effectors. Control signals are then issued to the control effectors to affect the desired change in the time rate of change of the system state vector.
Owner:THE BOEING CO
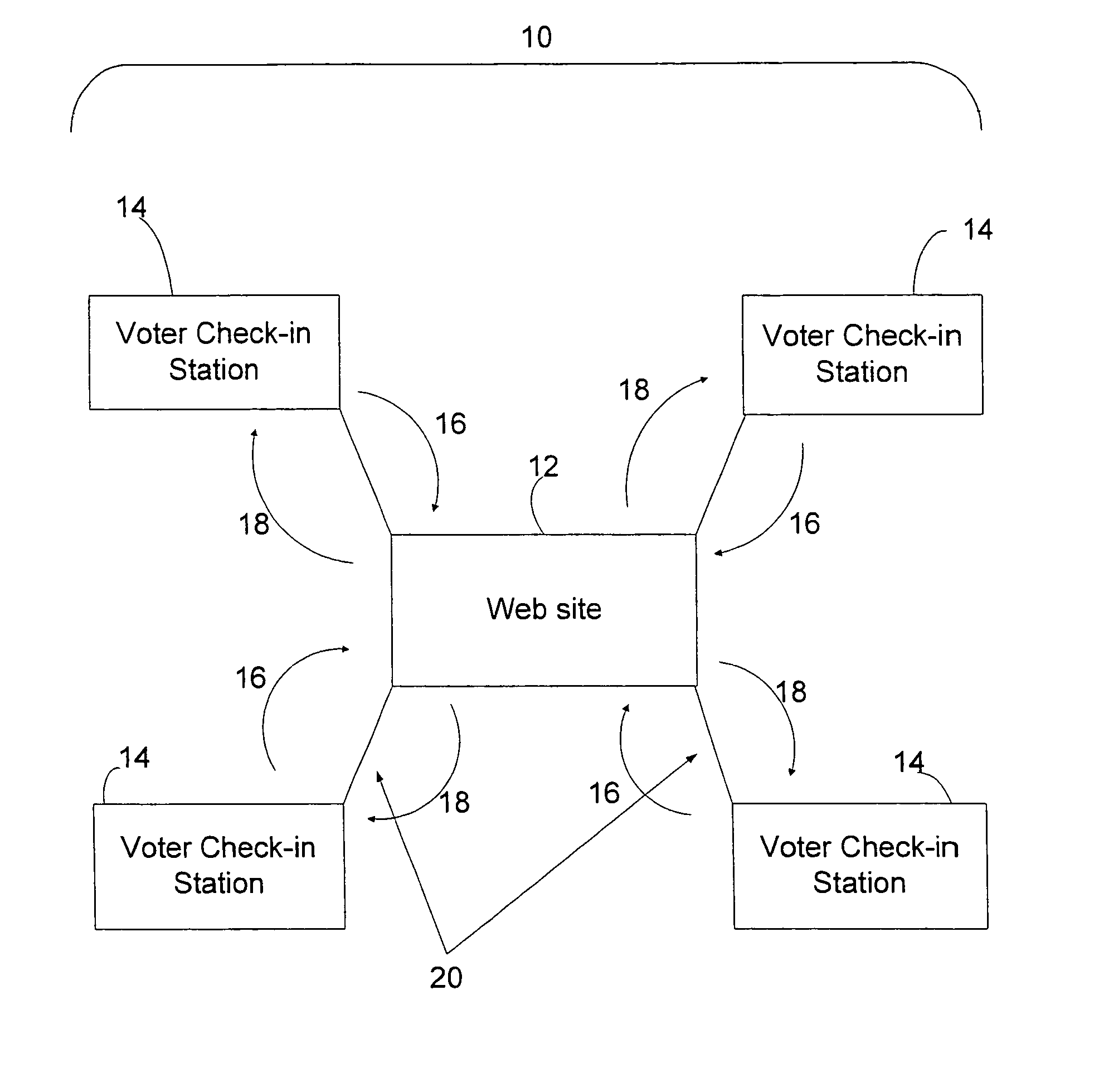
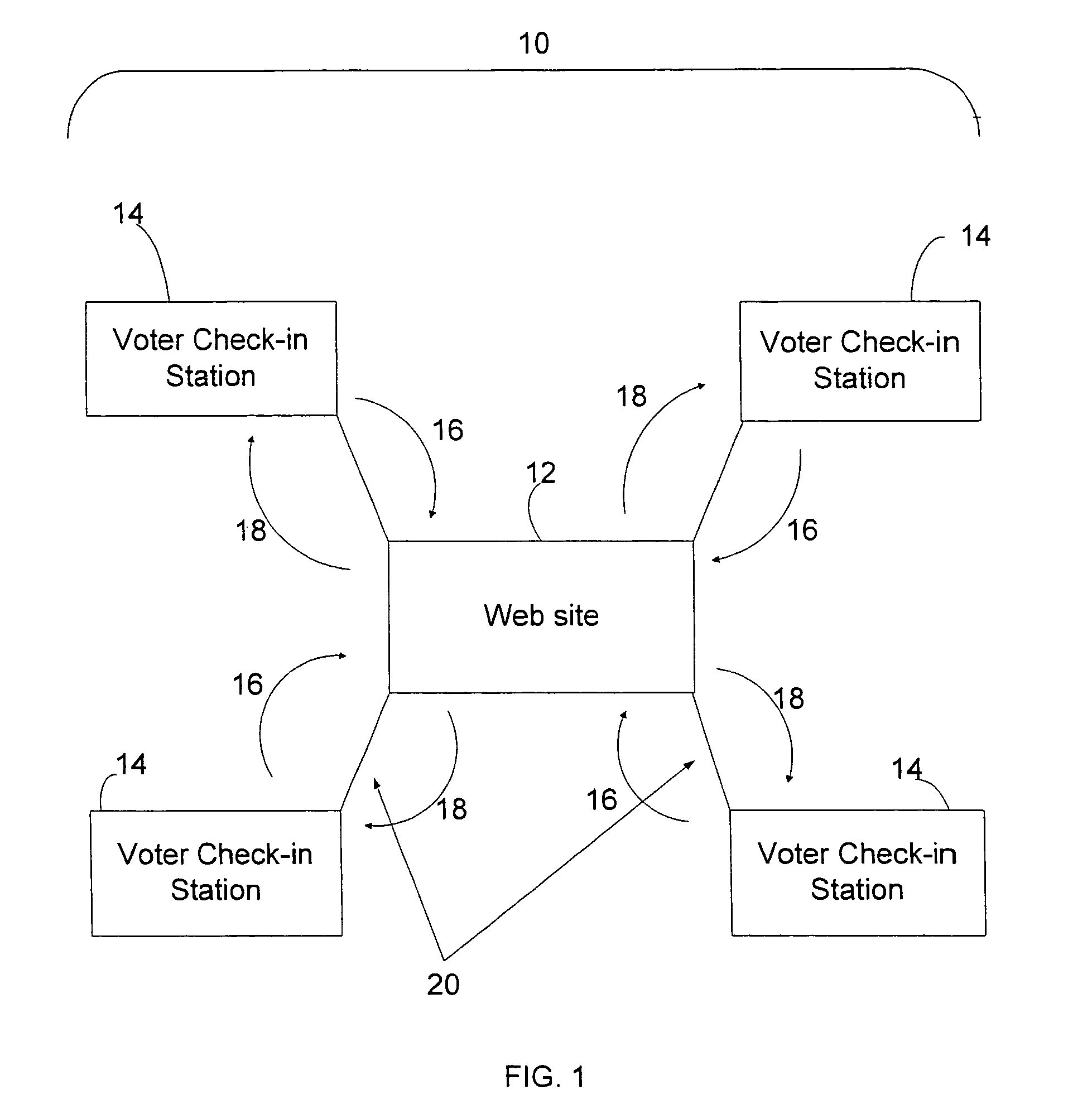
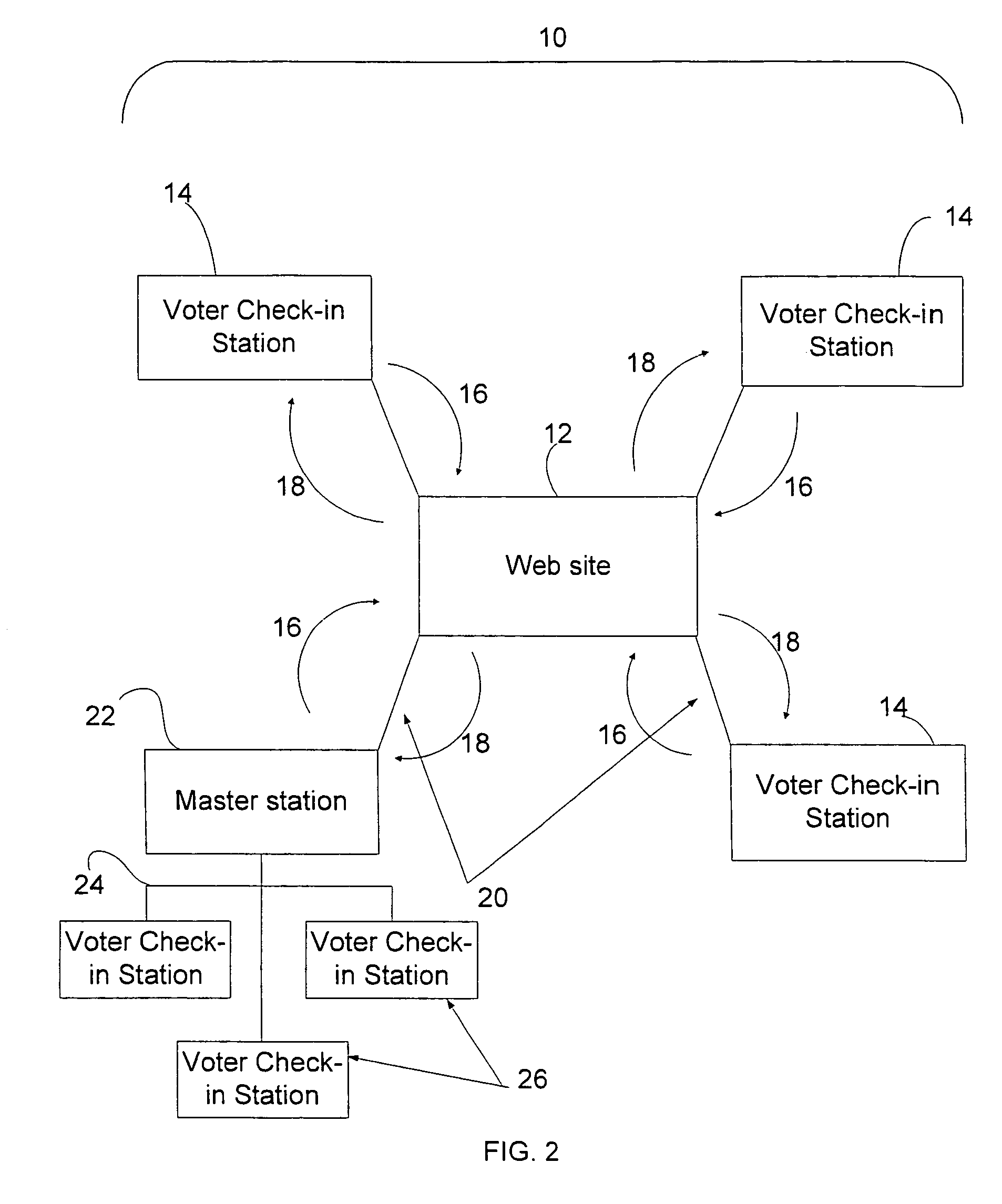
Electronic poll register system for elections
ActiveUS7497377B2Reduce quality problemsAttempt have been hamperedVoting apparatusCo-operative working arrangementsWeb siteSystem usage
Owner:WATSON DAVID
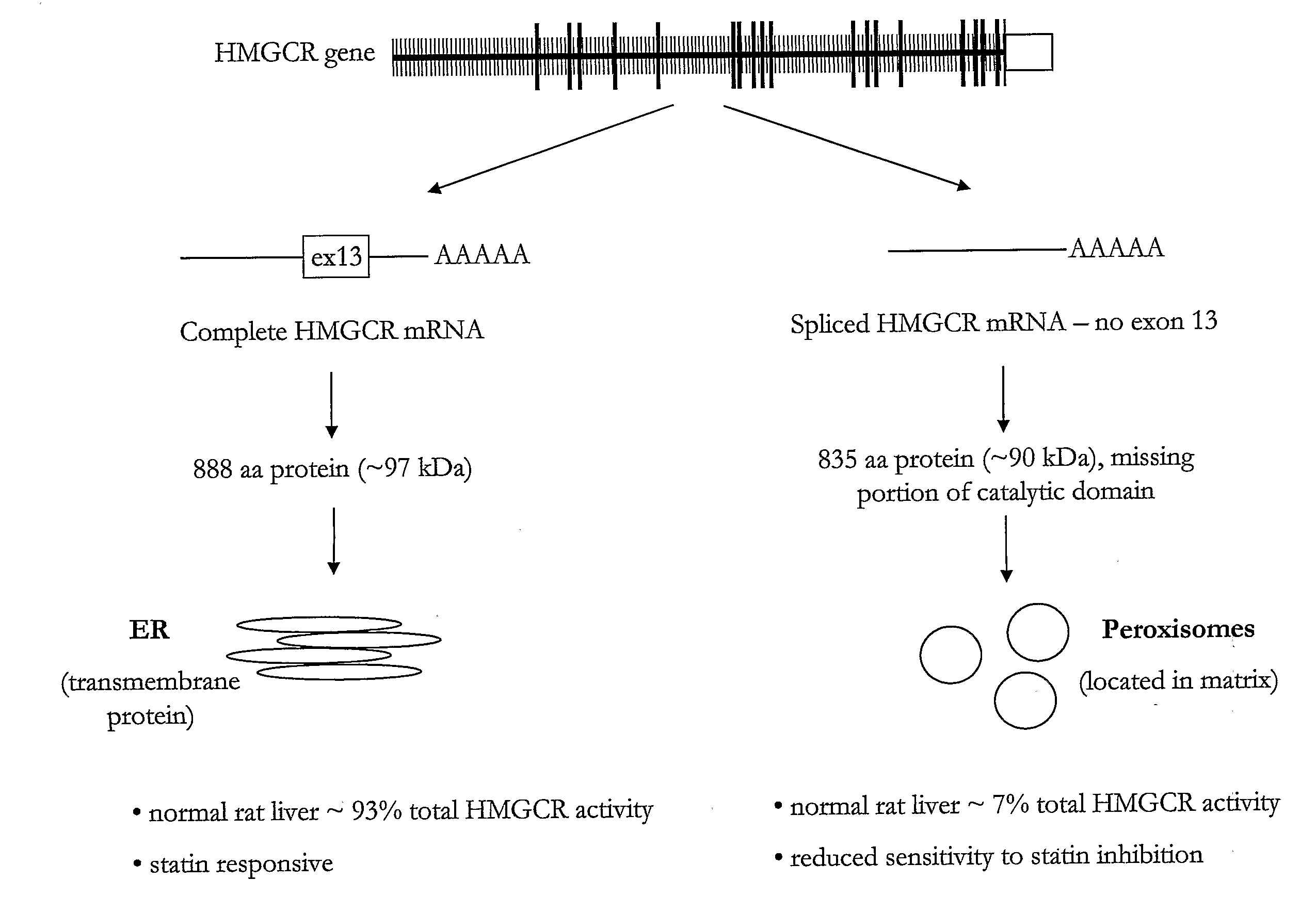
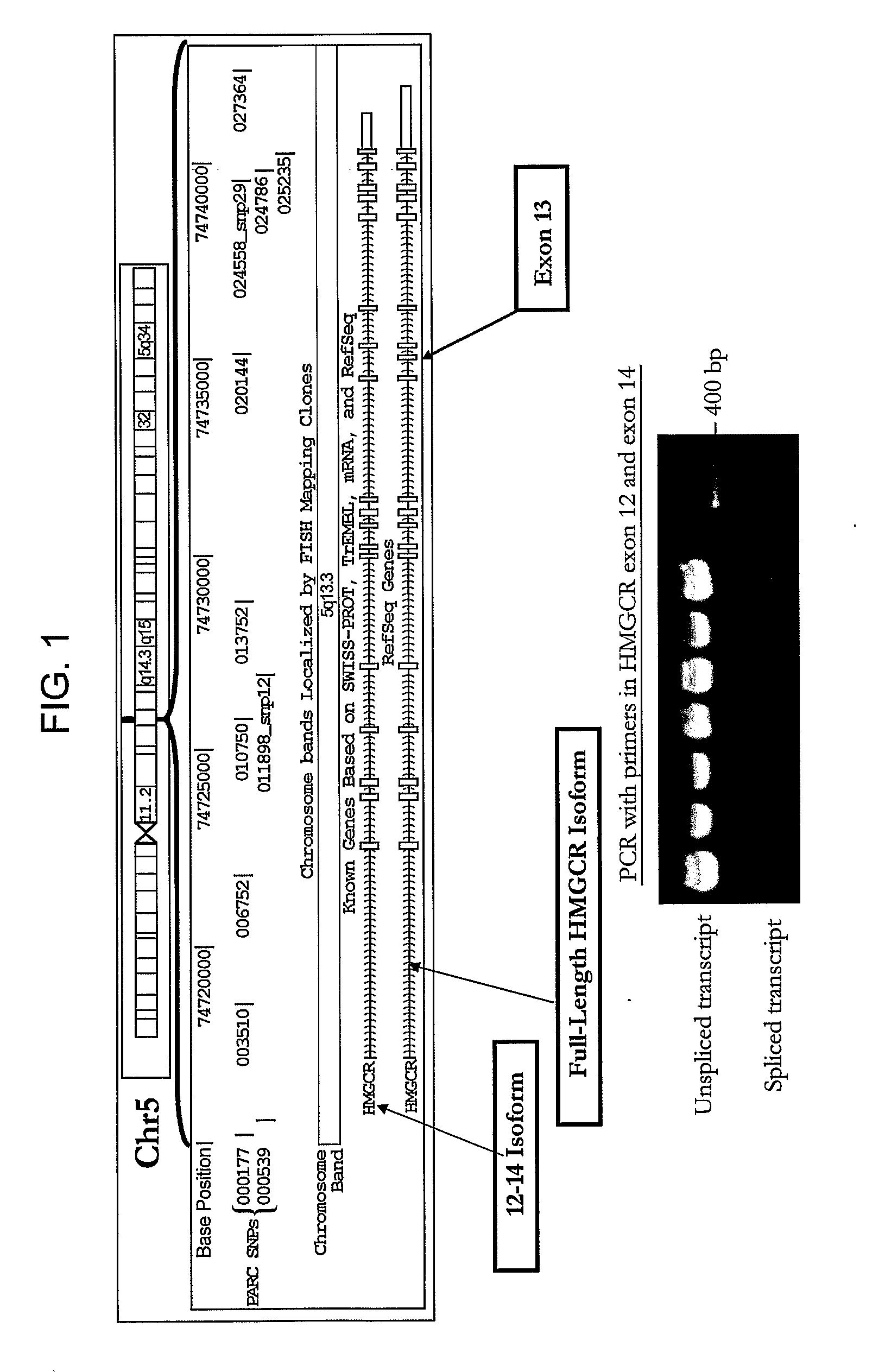
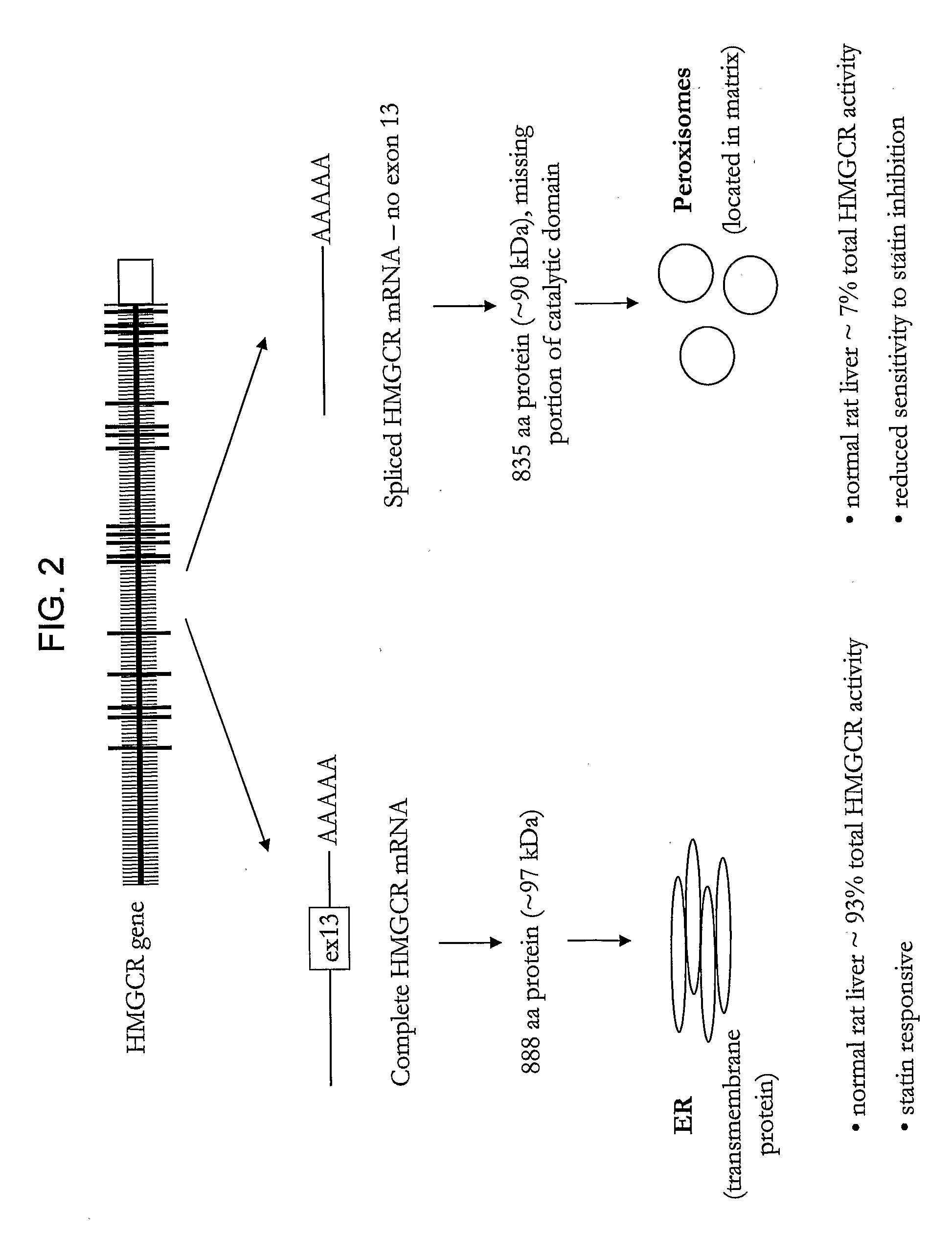
Hmgcr isoforms in Prediction of Efficacy and Identification of Cholesterol-Modulating Compounds
ActiveUS20080293054A1Good choiceIncrease doseMicrobiological testing/measurementBiological testingCholesterolGenetics
The present invention provides methods for assessing a subject's responsiveness to a HMGCR inhibitor therapy, and selection of a HMGCR inhibitor therapy based upon such methods. The invention further provides methods for identifying agents that modulate HMGCR activity, e.g., through modulating HMGCR mRNA splicing, while avoiding elevation of the statin-resistant isoform of HMGCR.
Owner:CHILDREN S HOSPITAL &RES CENT AT OAKLAN
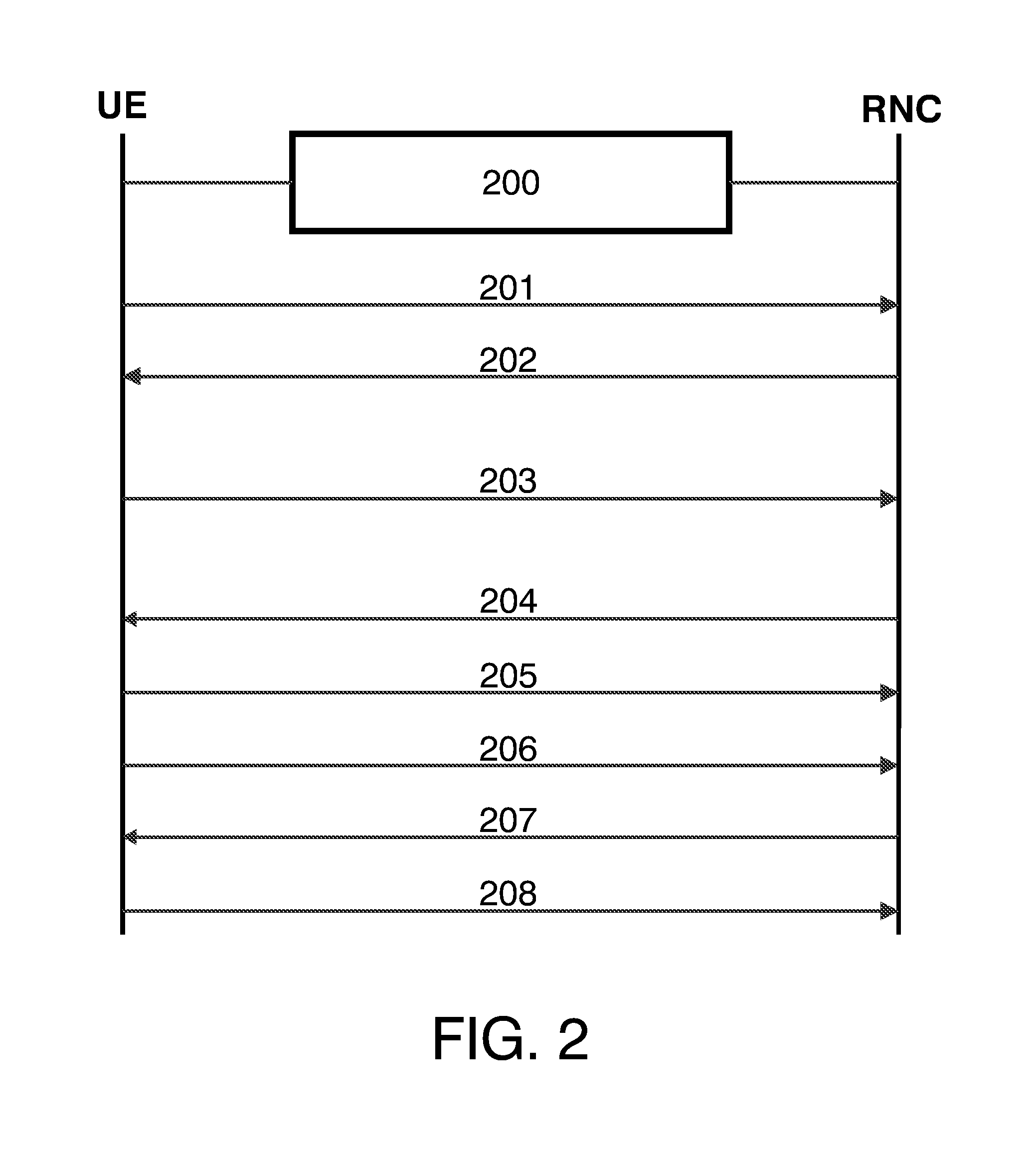
Method and Network Entity for Active Set Update in Wide Area Mobile Networks
InactiveUS20120113797A1Poor voice qualityLess G coverageSite diversityError preventionWide areaDiversity scheme
The described method provides a Network Controller (e.g., RNC) with an active set update procedure for application when activating STTD in the 3G networks. To avoid any call drop due to misalignments between the respective transmission diversity mode configurations of cells and the presence / absence of support for transmission diversity in user terminals, STTD mode is deactivated, in cases where the terminal is rejecting the Active Set Update message due to ‘invalid configuration’. The misalignments between the respective transmission diversity mode configurations may arise in a number of scenarios: handover from a cell with STTD deactivated to a cell with STTD activated, handover from a cell with STTD activated to a cell with STTD deactivated, or handover between cells with STTD activated. In all cases the solution consists of indicating to the UE the STTD Off configuration to obtain a success active set update procedure irrespective of the true configuration status.
Owner:VODAFONE GRP PLC
Method of controlling a function of a device and system for detecting the presence of a living being
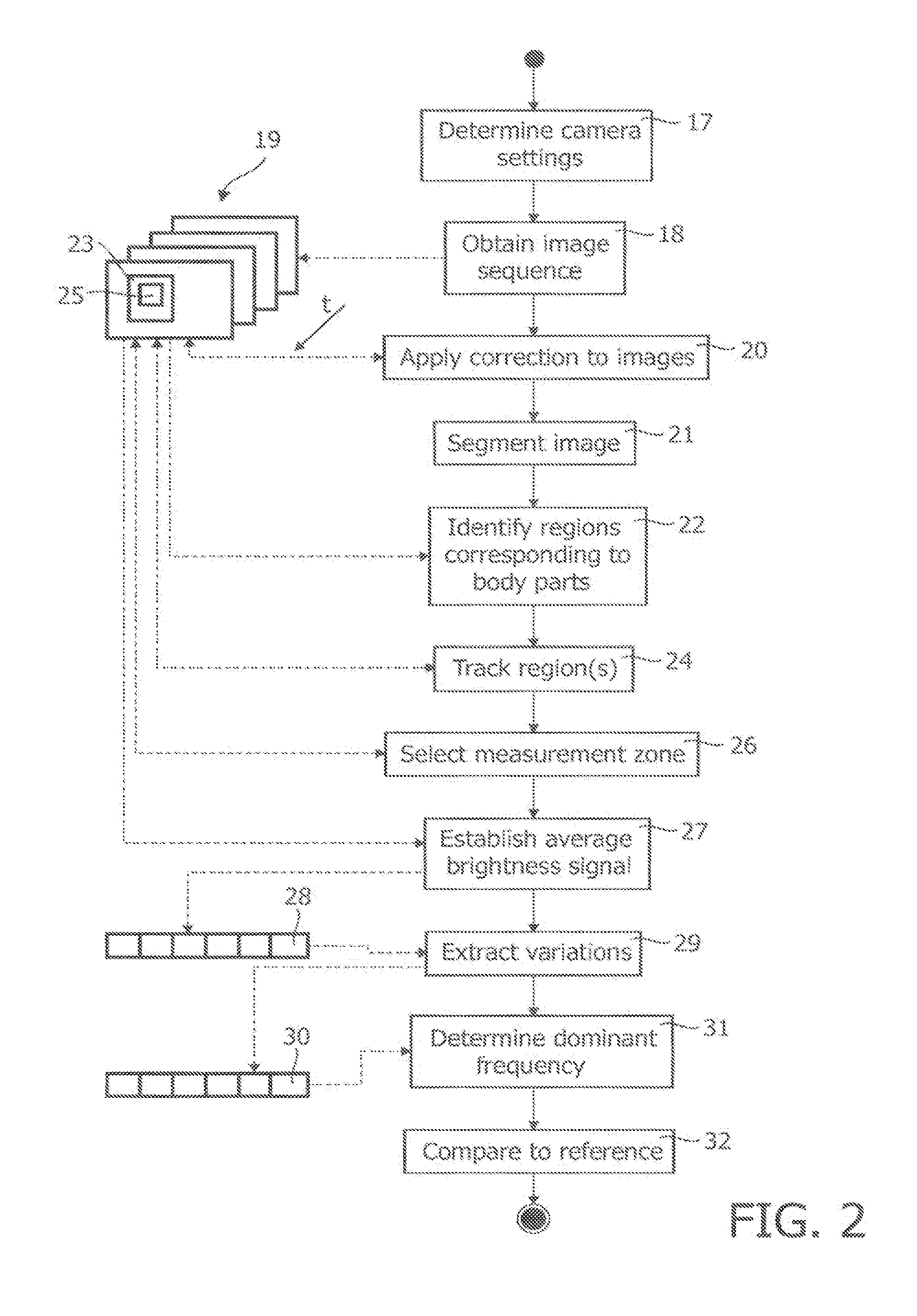
InactiveUS8542878B2Improve signal-to-noise ratioSufficient degree of accuracyImage enhancementImage analysisFrequency spectrumComputer vision
A method of controlling a function of a device, includes obtaining a sequence (19;34;48) of digital images taken at consecutive points in time. At least one measurement zone (25) including a plurality of image points is selected. For at least one measurement zone (25), a signal (30;41;55) representative of at least variations in a time-varying value of a combination of pixel values at at least a number of the image points is obtained and at least one characteristic of the signal (30;41;55) within at least a range of interest of its spectrum relative to comparison data is determined. The determination comprises at least one of: (i) determining whether the signal (30;41;55) has a spectrum with a local maximum at a frequency matching a comparison frequency to a certain accuracy; and (ii) determining whether at least a certain frequency component of the signal (30;41;55) is in phase with a comparison signal to a certain accuracy. The function is controlled in dependence on whether the determination is positive.
Owner:KONINK PHILIPS ELECTRONICS NV
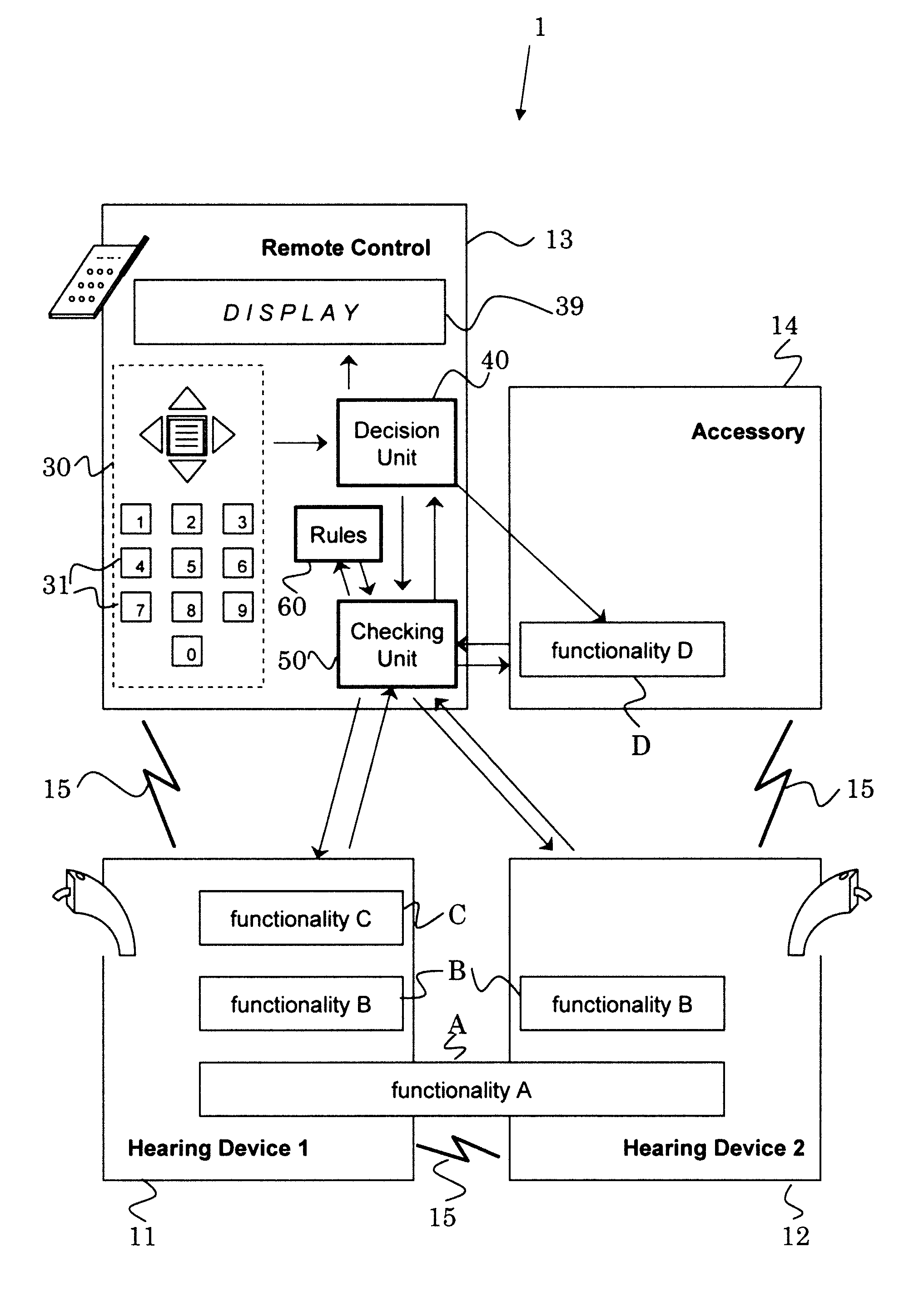
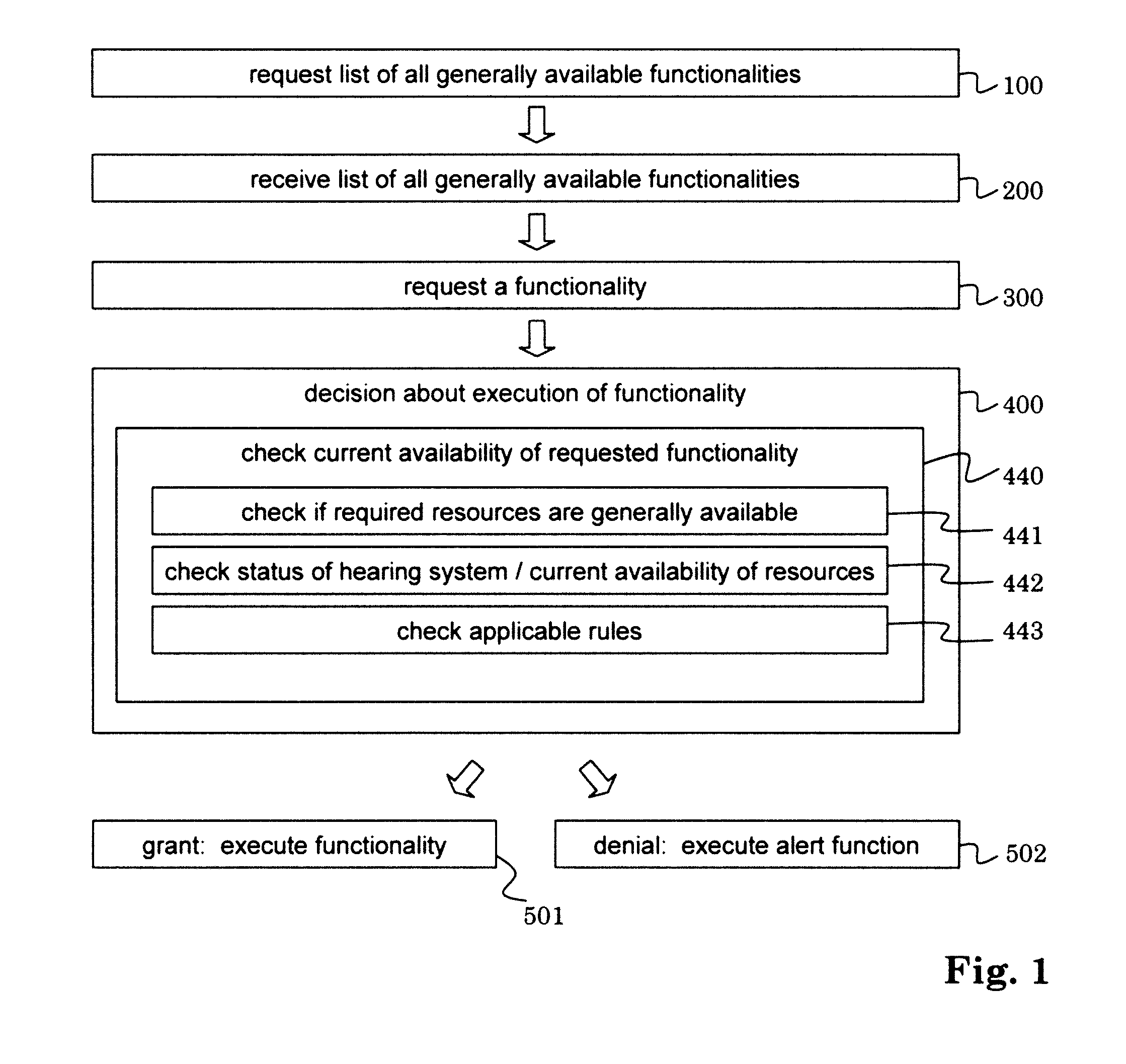
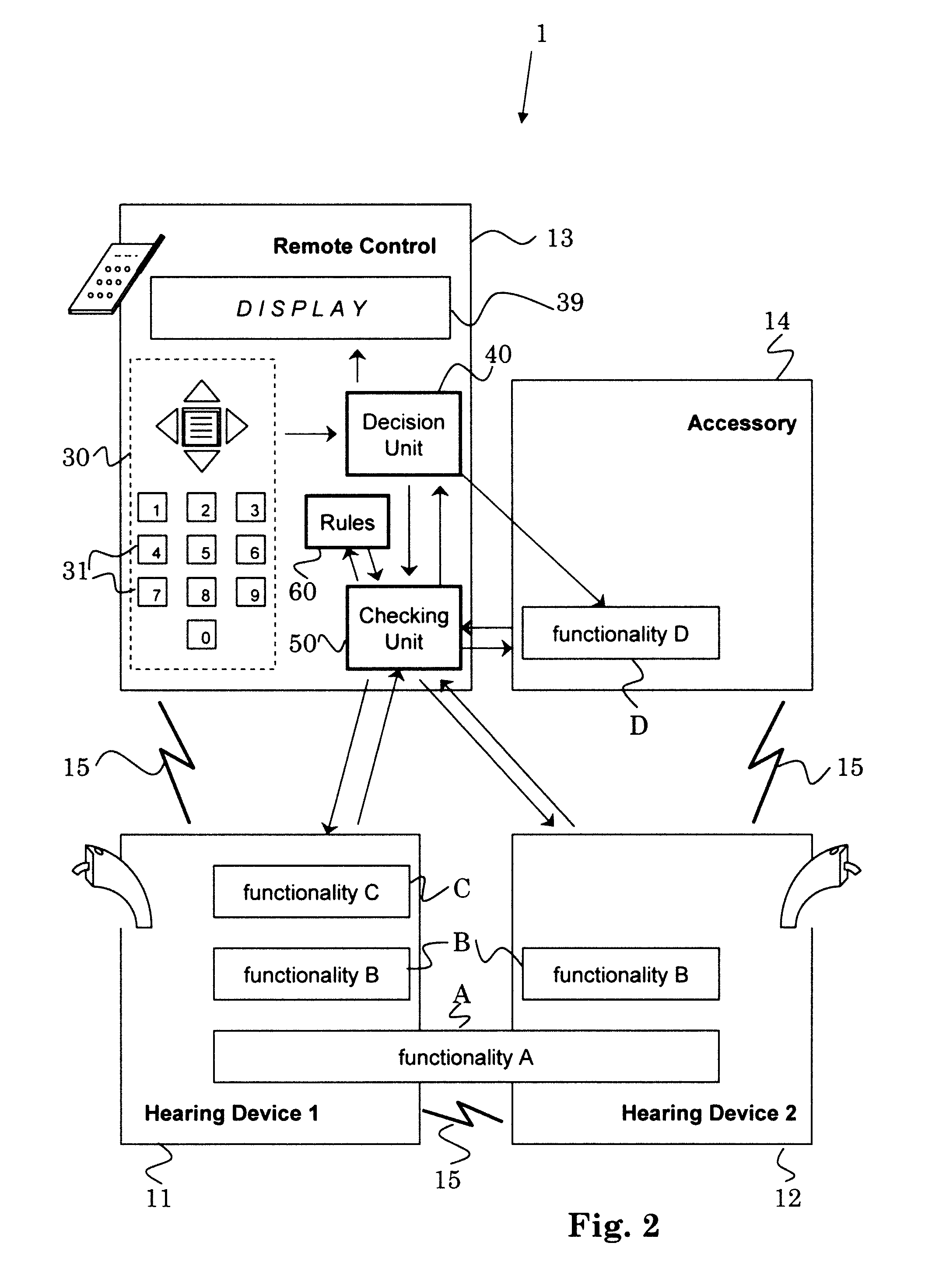
Hearing system and method for operating the same
ActiveUS20110129106A1Less energyKeep for a long timeSets with customised acoustic characteristicsAuditory systemComputer science
The method for operating a hearing system comprises the steps ofa) requesting (300) said hearing system to execute a functionality; andb) deciding (400) whether or not to execute the requested functionality.It preferably comprises the steps ofc) checking (440) the current availability of the requested functionality;wherein the decision of step b) depends on the so-obtained current availability of the requested functionality, andd) executing the requested functionality, only if the requested functionality is currently available in said hearing system.The hearing system comprises at least one decision unit adapted to deciding whether or not to execute functionalities the hearing system is requested to execute.The invention can make it possible to form hearing systems from a wide range of devices.
Owner:SONOVA AG
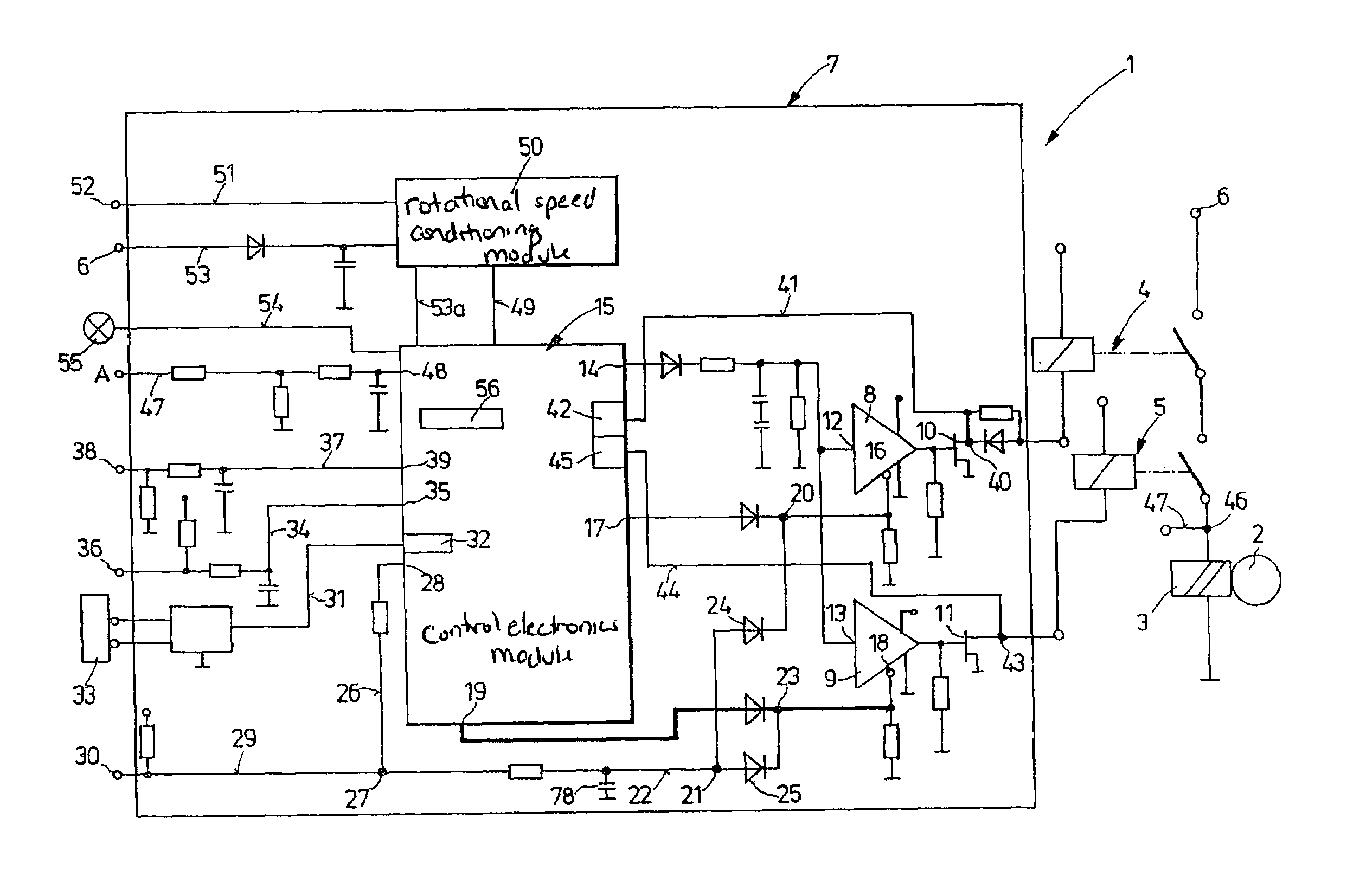
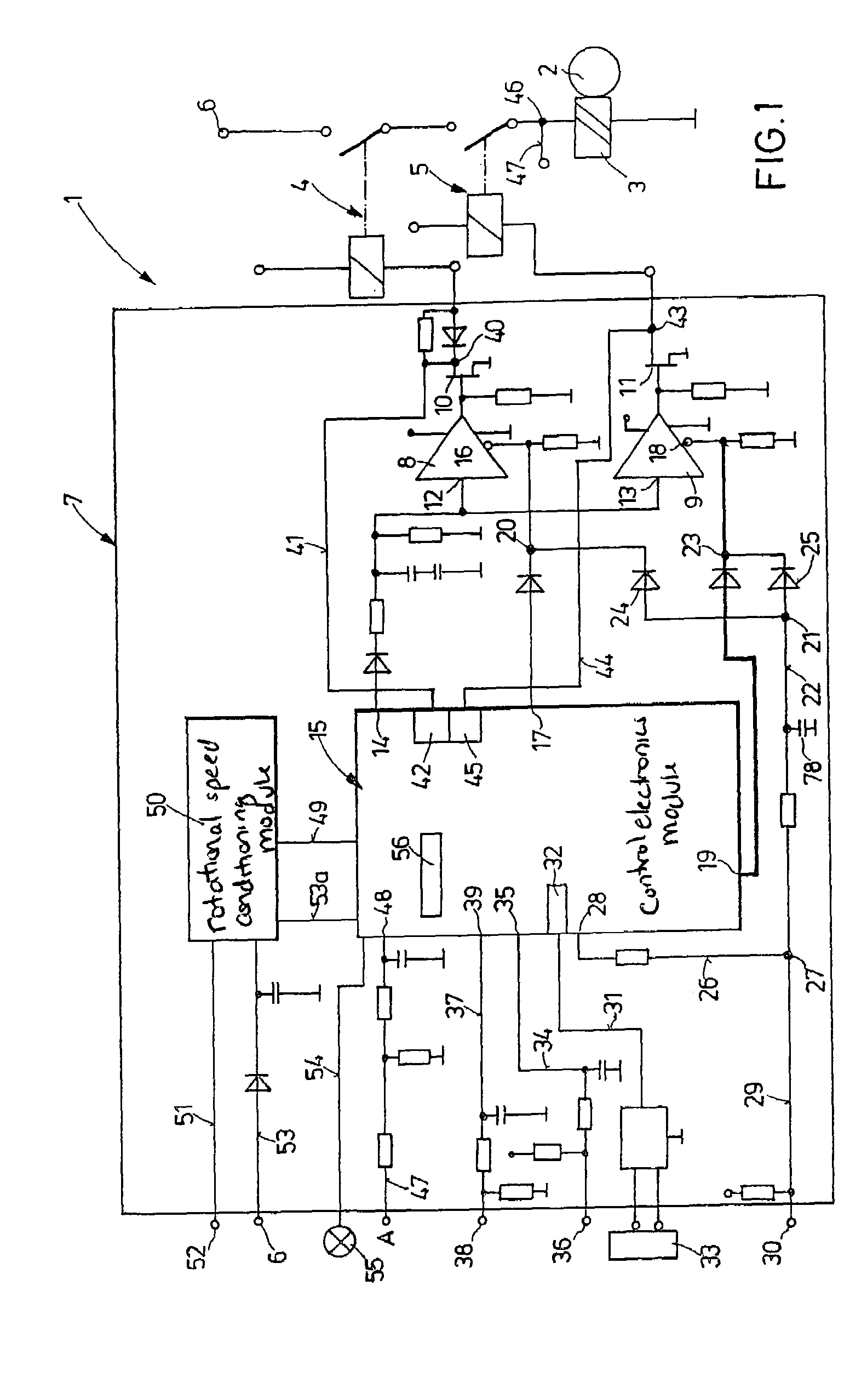
Starter device for an internal combustion engine as well as a method for starting an internal combustion engine
InactiveUS7156063B2Detection securityAttempt have been hamperedEngine controllersElectric motor startersPower flowControl electronics
A starting device for an internal combustion engine includes a switching control device for controlling a starter motor. At least one power switching module connects the starter motor to a voltage source and is activated via an assigned control line. A control electronics is provided for controlling the at least one power switching module. A release device which records the power flow of the internal combustion engine makes available, as a function of the running of the internal combustion engine, a release signal for the release of the activating switching procedure by the at least one control line. The release device includes a first release switching channel that works independently of the control electronics and a second release switching channel that cooperates with control electronics. These are set up in such a way that an initiation of the activating switching procedure takes place only during the simultaneous release switching setting of the two release switching channels. A diagnosis device of the switching control device, at the ending of making available the release signal for the activating switching procedure by the release device, records the release switching setting of the first release switching channel. This makes possible the monitoring of the function of the first release switching channel, which increases the safety of the starting procedure. A method utilizing the components described for starting an internal combustion engine is also described.
Owner:ROBERT BOSCH GMBH
Performance of multi-processor computer systems
ActiveUS20130055270A1Improve performance and scalabilityEfficiently performedDigital computer detailsMultiprogramming arrangementsReal-time computingProcess information
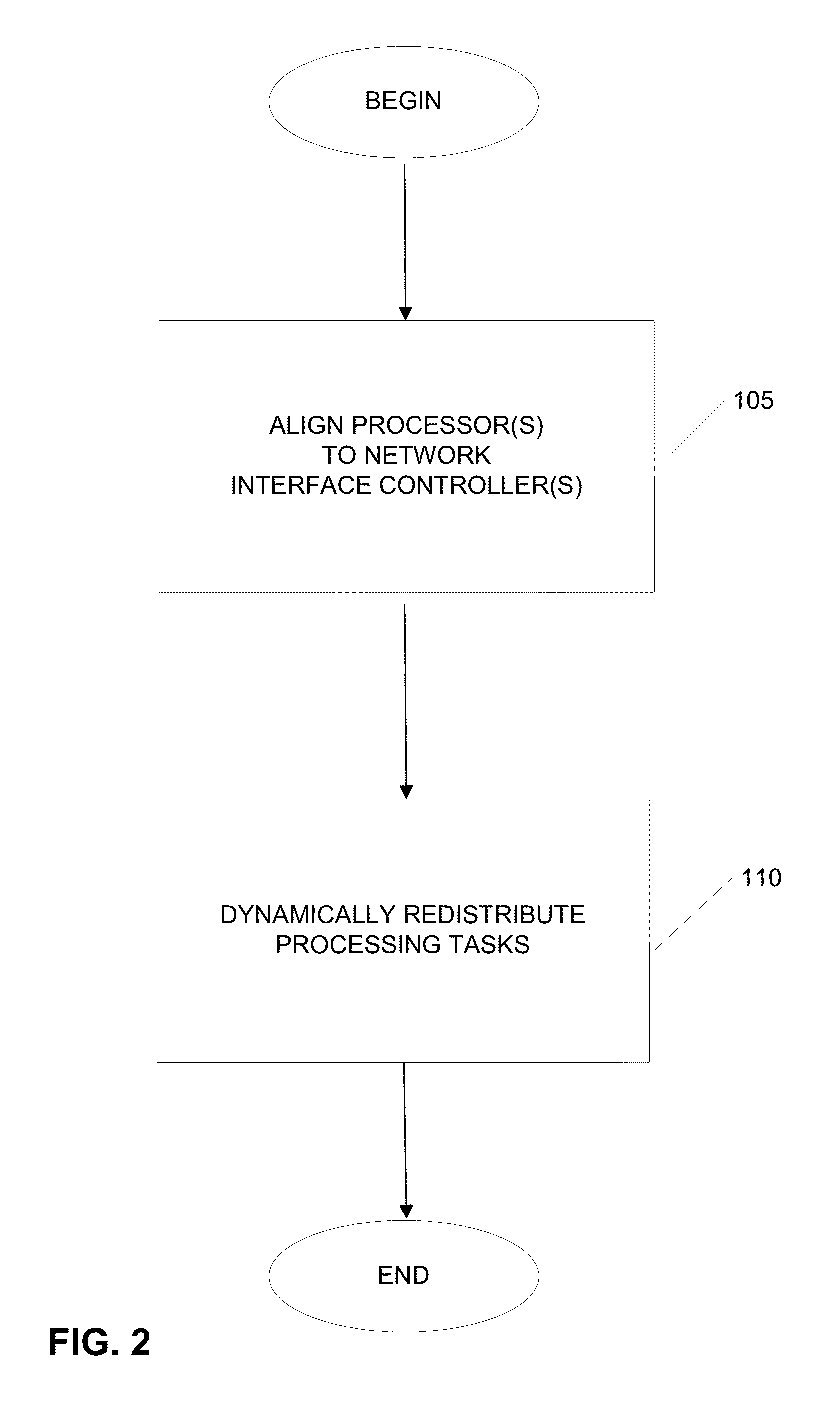
Embodiments of the invention may improve the performance of multi-processor systems in processing information received via a network. For example, some embodiments may enable configuration of a system such that information received is distributed among multiple processors for efficient processing. A user may select from among multiple configuration options, each configuration option being associated with a particular mode of processing information received. By selecting a configuration option, the user may specify how information received is processed to capitalize on the system's characteristics, such as by aligning processors on the system with certain NICs. As such, the processor(s) aligned with a NIC may perform networking-related tasks associated with information received by that NIC. If initial alignment causes one or more processors to become over-burdened, processing tasks may be dynamically re-distributed to other processors.
Owner:MICROSOFT TECH LICENSING LLC
Game of Chance Utilizing Wheels with Parlay and Progressive Jackpot Options
InactiveUS20110159942A1Attempt have been hamperedRewarding gaming experienceApparatus for meter-controlled dispensingVideo gamesHuman–computer interactionRandom event
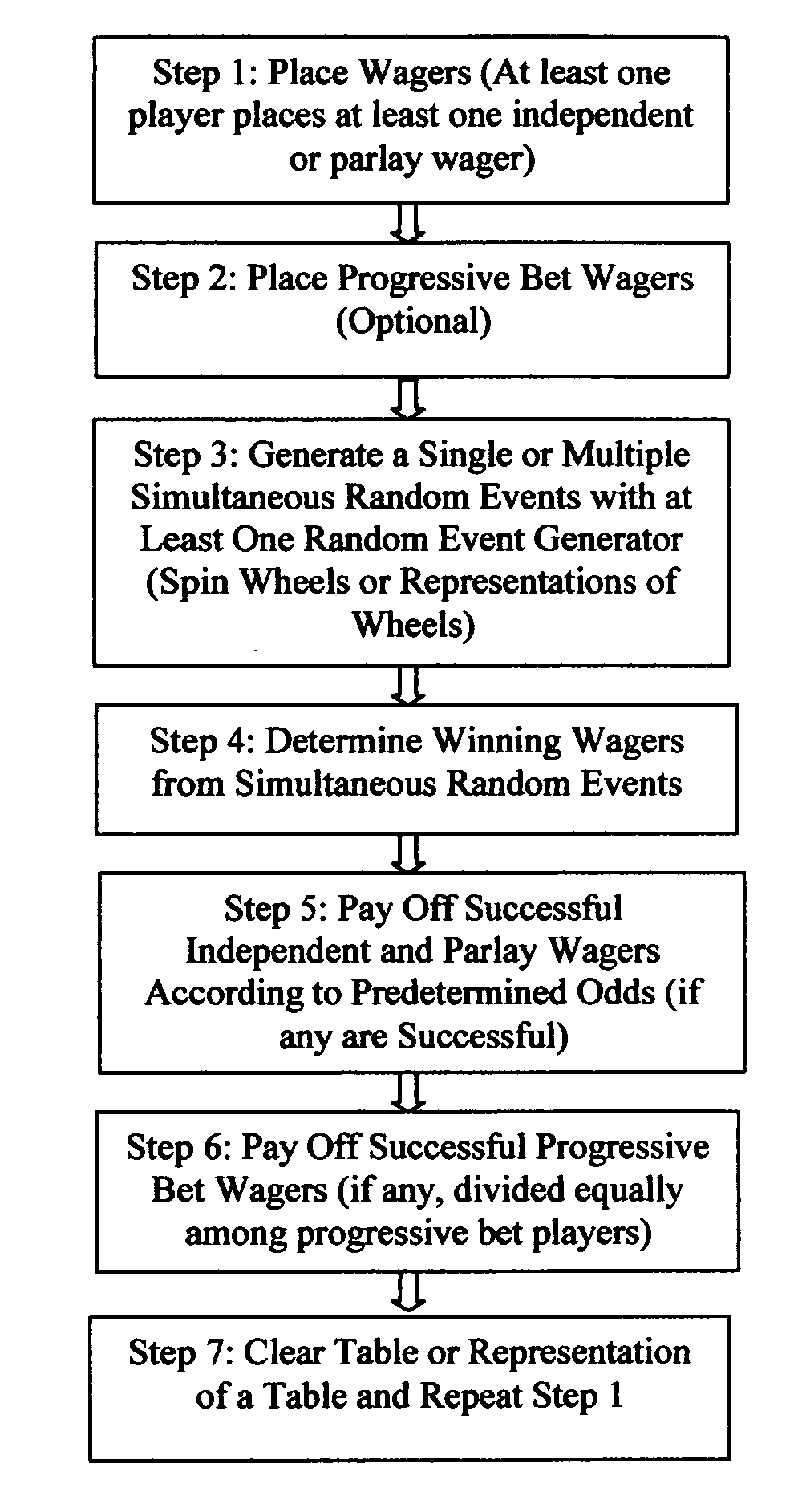
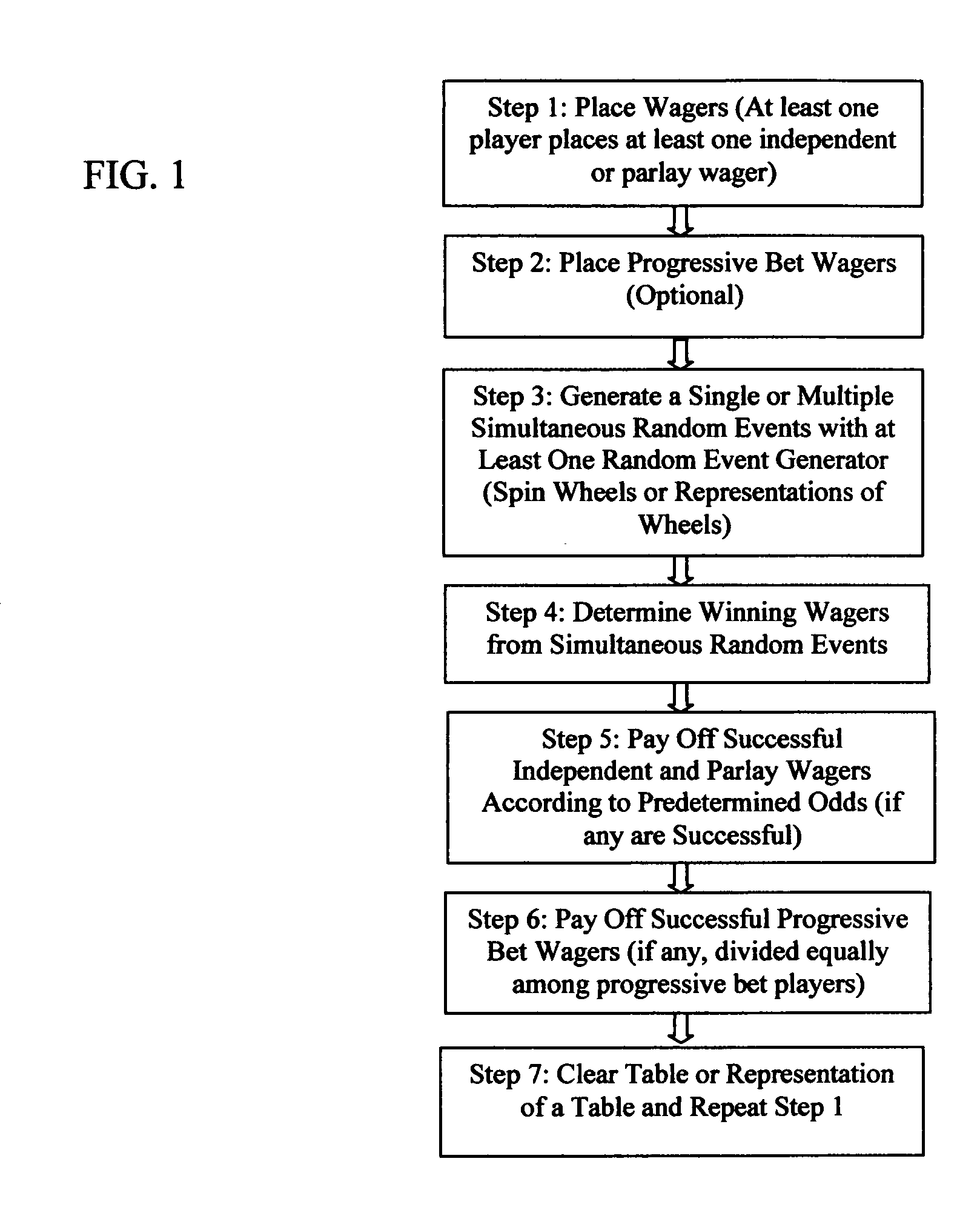
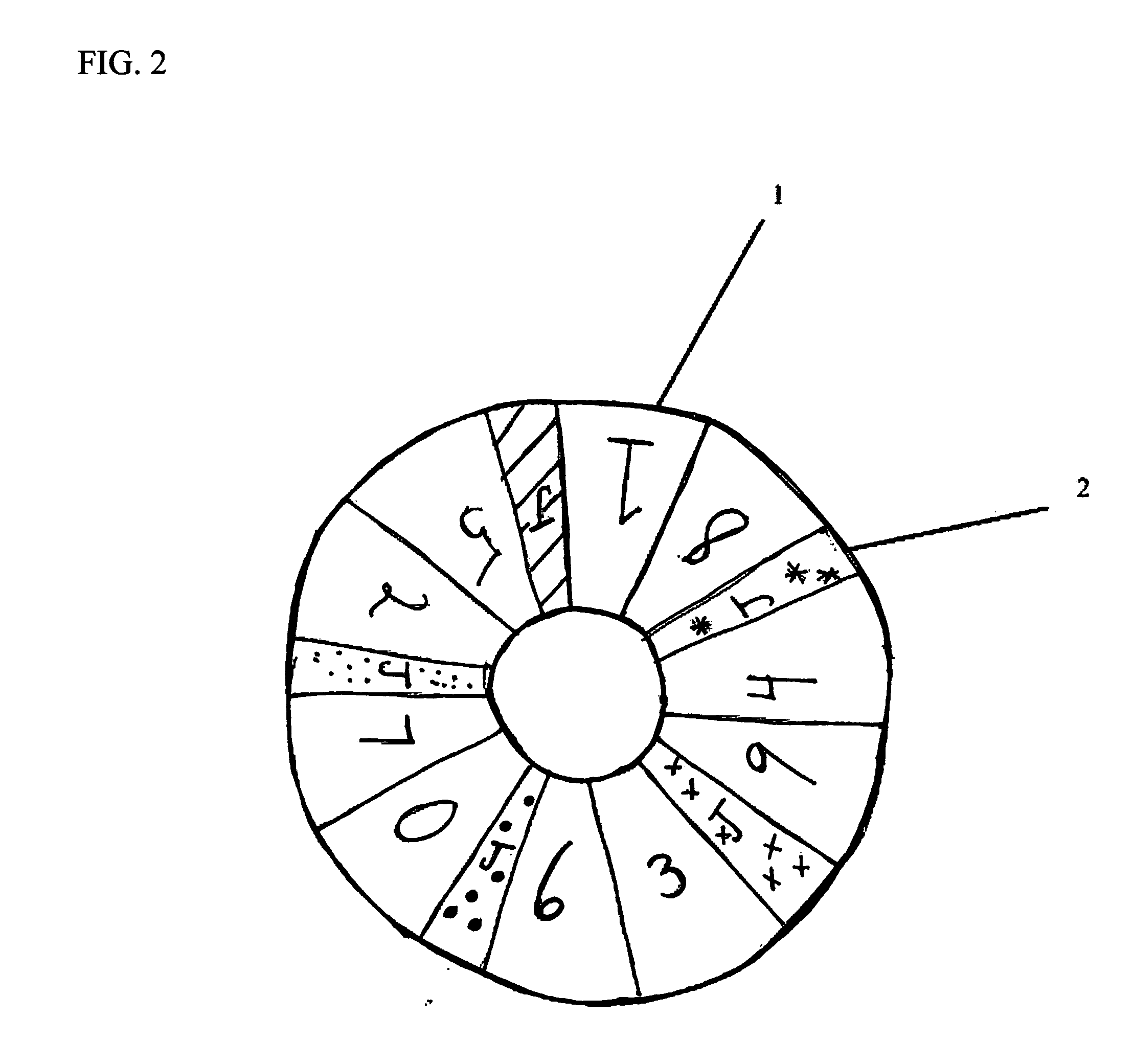
A game of chance and a method of playing a game of chance with a unique format and innovative wagering options, including parlay and progressive betting. At least one player must place at least one bet for the game to commence. Wagers can be placed on one event or multiple random events occurring simultaneously. Winning payouts are calculated based on the odds of the single event or the cumulative odds of multiple simultaneous events. The progressive bet can only be placed if another wager is simultaneously made, and is paid out as a separate bet. Once commenced, the game incorporates a plurality of random event generators to generate outcomes, which are paid out depending on predetermined payout odds. This game and method would be well suited for casinos in table, hybrid or electronic formats. This game could be played as a board game, a video game or a machine game.
Owner:CRAM JARED
Electronic lock for safes
ActiveUS20180066453A1Lower requirementMore robust to malicious attemptsNon-mechanical controlsConverting sensor output opticallyEngineeringPlunger
An electronic lock with an electronic sensing arrangement to accurately sense relative positions of a bolt which mechanically locks a door, such as a door of an electronic drop safe, and to also sense an electronically controlled plunger which locks the bolt in place. The arrangement provides a mechanism for sensing a variety of mechanical malfunctions, as well as, potential fraud or tampering situations.
Owner:ELLENBY TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com