Server, terminal and authority management and permission method
A technology of rights management and server, applied in the fields of license, server, terminal and rights management, to achieve the effect of improving use efficiency, improving user experience and improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
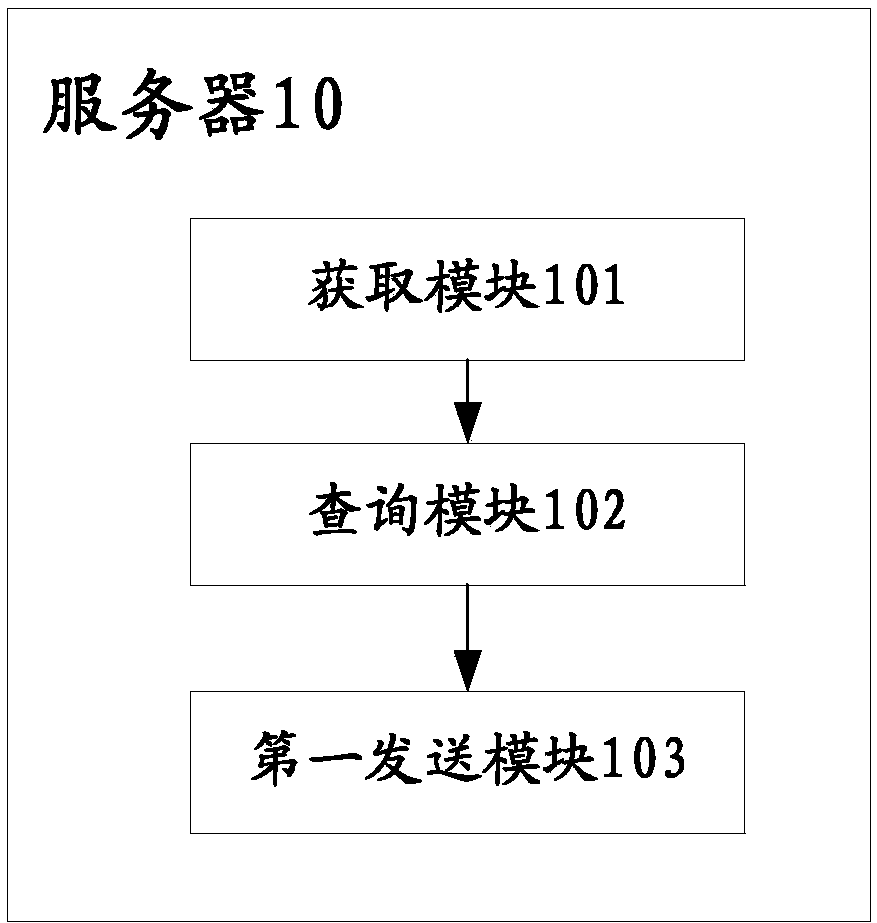
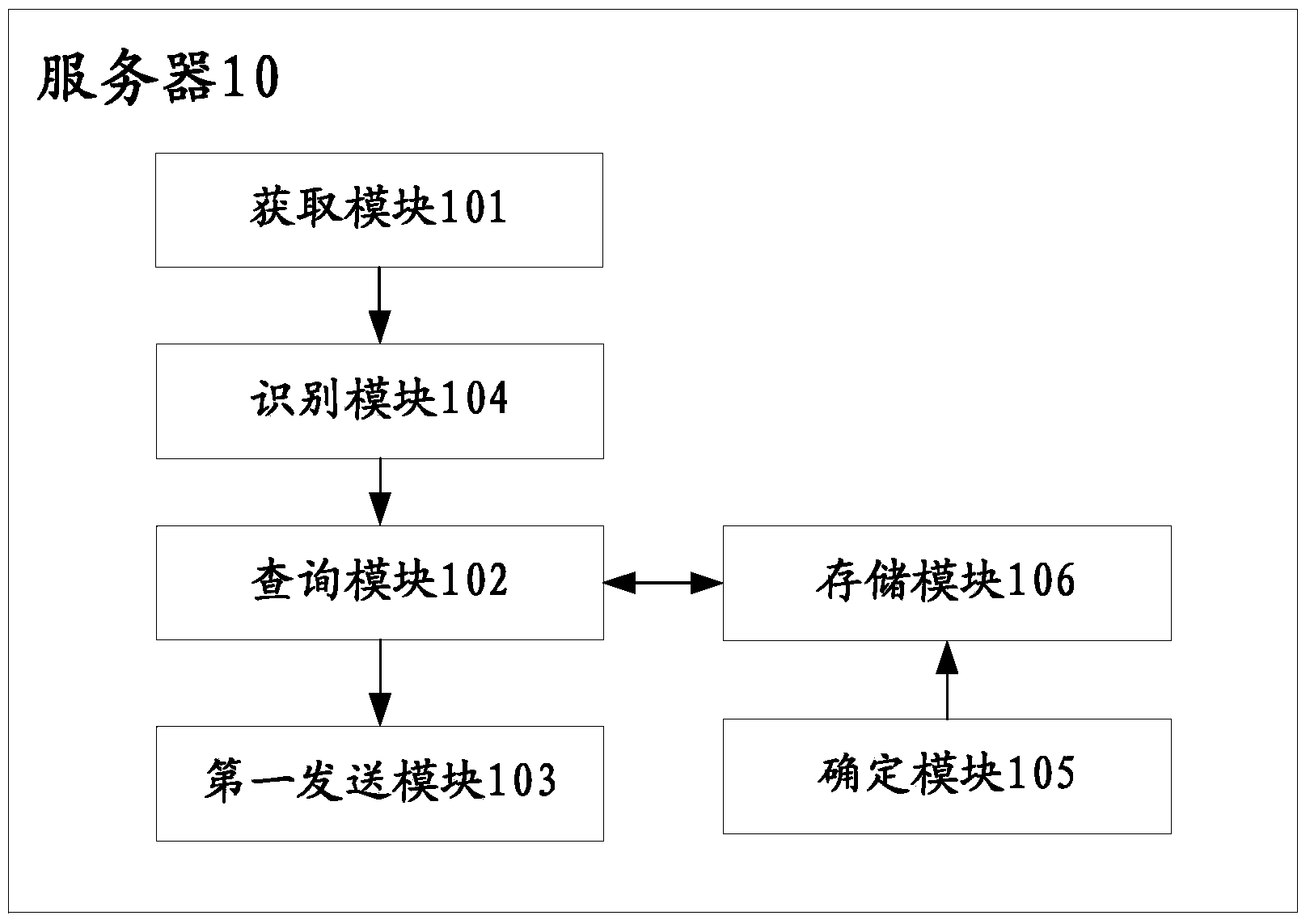
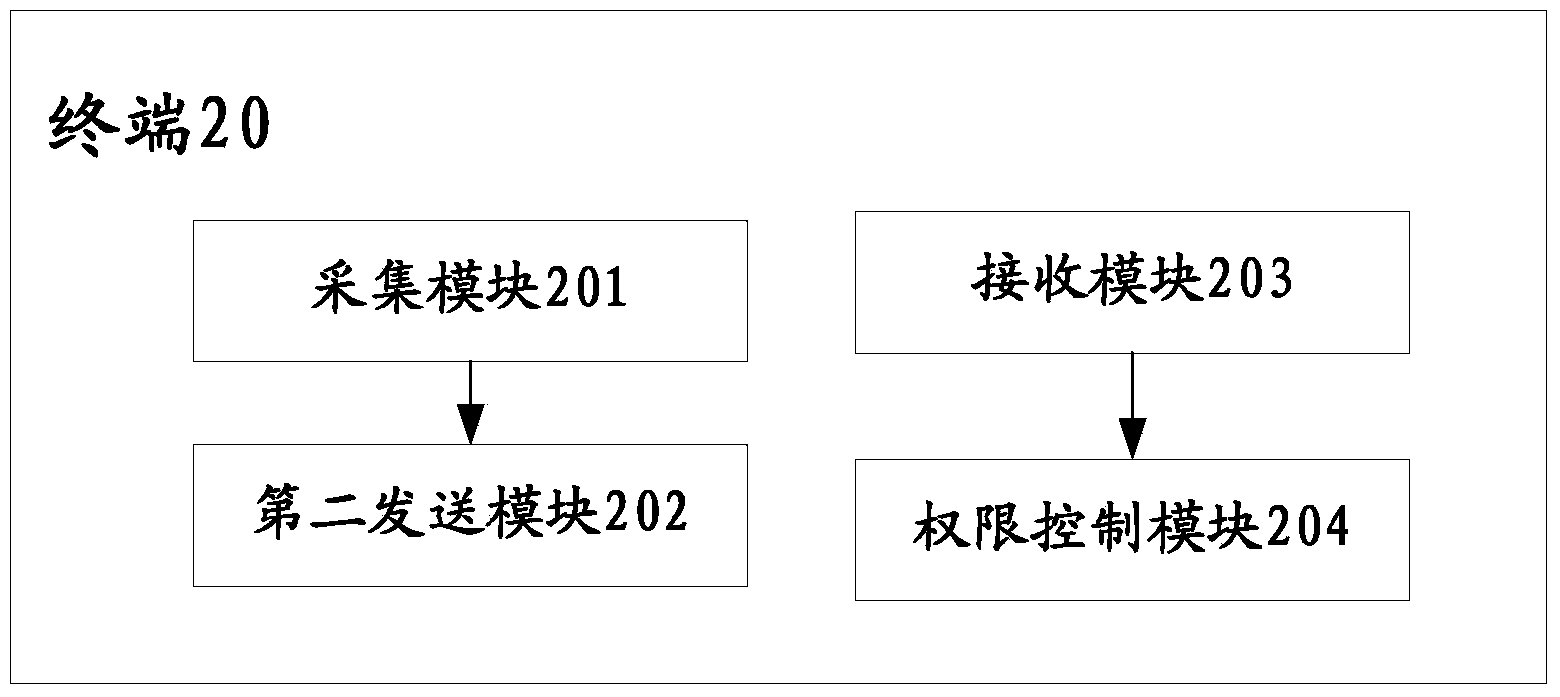
[0052]The general idea of the present invention is: by extracting the identification information of the application programs that need to be limited in authority, and uploading the identification information to the server, the server will query according to the information stored in itself or in other servers, and obtain the corresponding information. The reasonable permission policy of the application program, so as to limit the permission of the corresponding application program according to the reasonable permission policy. However, in this application, the reasonable permission policy obtained from the server can be in various ways, and the better ones can be the following two. One is the permission policy after removing the unnecessary permissions of the corresponding application program, that is, the permission in the permission policy It is the permission that the application program can operate; a prohibition permission policy that prohibits the corresponding applicat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com