Attribute-based multi-keyword ciphertext retrieval method under background of multiple data owners
A technology for data owners and owners, applied in the field of cryptography, can solve problems such as multiple data owner scenarios that have not been considered, and achieve fine-grained access control, reduce burden, and ensure keyword privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
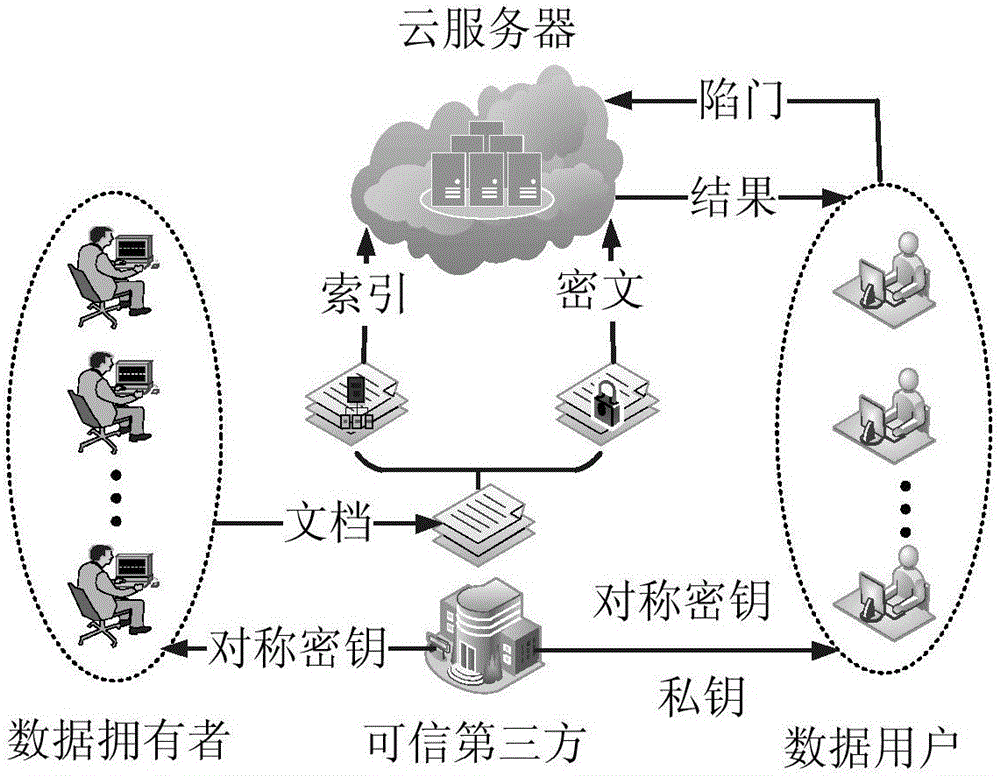
[0026] refer to figure 1 , the present invention takes the personal health record PHR storage system as an example, the actual scene includes four entities: a trusted third party TTS, a cloud server CSP, multiple data owners DO and data users DU. Trusted third-party TTS generates public key pk, private key sk and symmetric key Φ; cloud server CSP is used to store data ciphertext; multiple data owners DO, such as patients are responsible for encrypting documents and creating indexes; data users DU, such as Physicians can search the ciphertext.
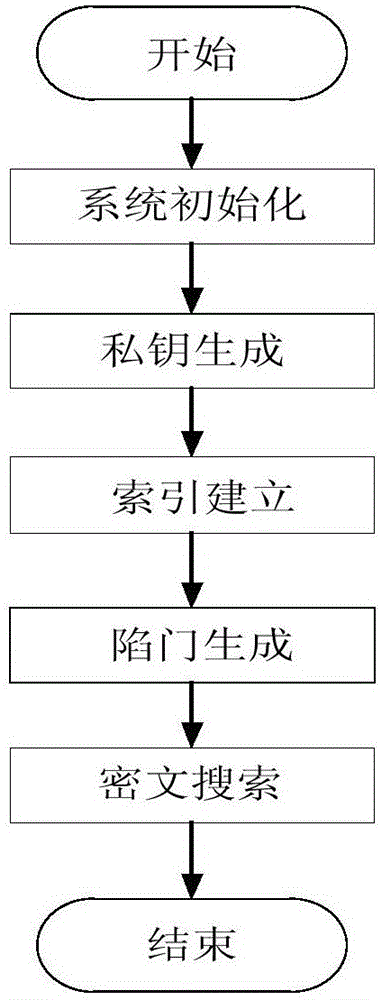
[0027] refer to figure 2 , the present invention is based on attribute-based multi-keyword ciphertext retrieval under the background of multi-data owners, and its implementation steps include the following:
[0028] Step 1, system initialization
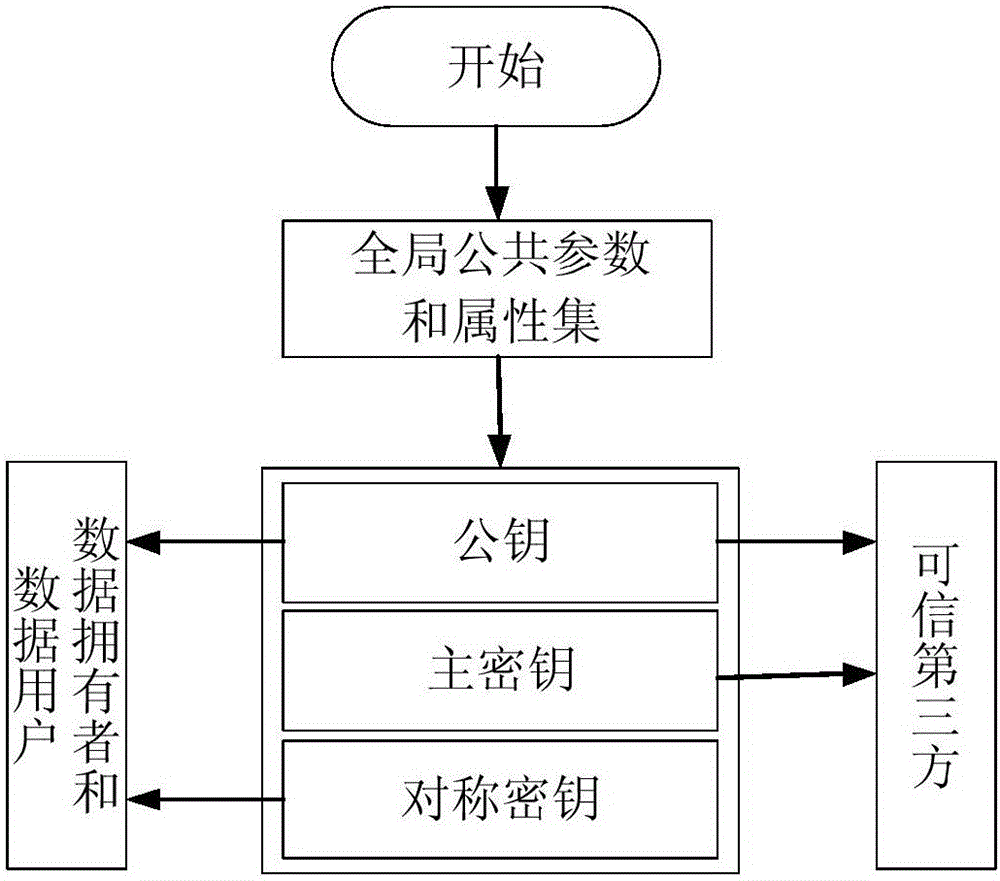
[0029] refer to image 3 , the specific implementation of this step is as follows:
[0030] (1a) The third-party trusted server TTS calculates the public key pk=(G 1 ,G 2 ,e,h 1 ,h 2...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com