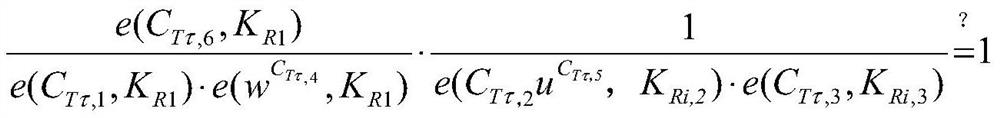Friend recommendation system based on hidden strategy attribute-based encryption and method thereof
An attribute-based encryption and friend recommendation technology, which is applied in the field of social network privacy protection, can solve data privacy leakage and other problems, and achieve the effect of reducing decryption costs and information encryption costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0039] The purpose of this embodiment is to provide a friend recommendation system based on hidden policy attribute-based encryption.
[0040] A friend recommendation system based on hidden strategy attribute base encryption, including:
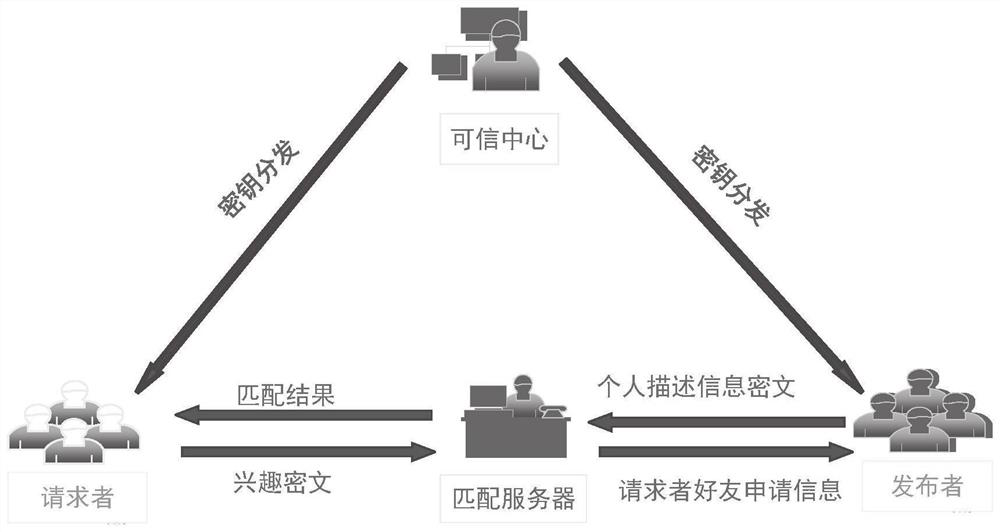
[0041] The trusted center is configured to provide registration services for issuers and requesters, and to distribute keys;
[0042] The matching server is configured to receive and store the publisher's self-description ciphertext and the requester's interest ciphertext; analyze whether the publisher's self-description information matches the requester's interest, and recommend friends according to the matching result;
[0043]The publisher is configured to encrypt its self-description information according to the requester's interest policy, and send its self-description ciphertext to the matching server; at the same time, add corresponding tag attributes to its self-description so that interested requesters can receive To the publisher's...
Embodiment 2
[0080] The purpose of this embodiment is to provide a friend recommendation method based on hidden policy attribute-based encryption.
[0081] like figure 2 As shown, it is a flow chart of a friend recommendation method based on hidden policy attribute-based encryption provided by the present disclosure, and the steps include:
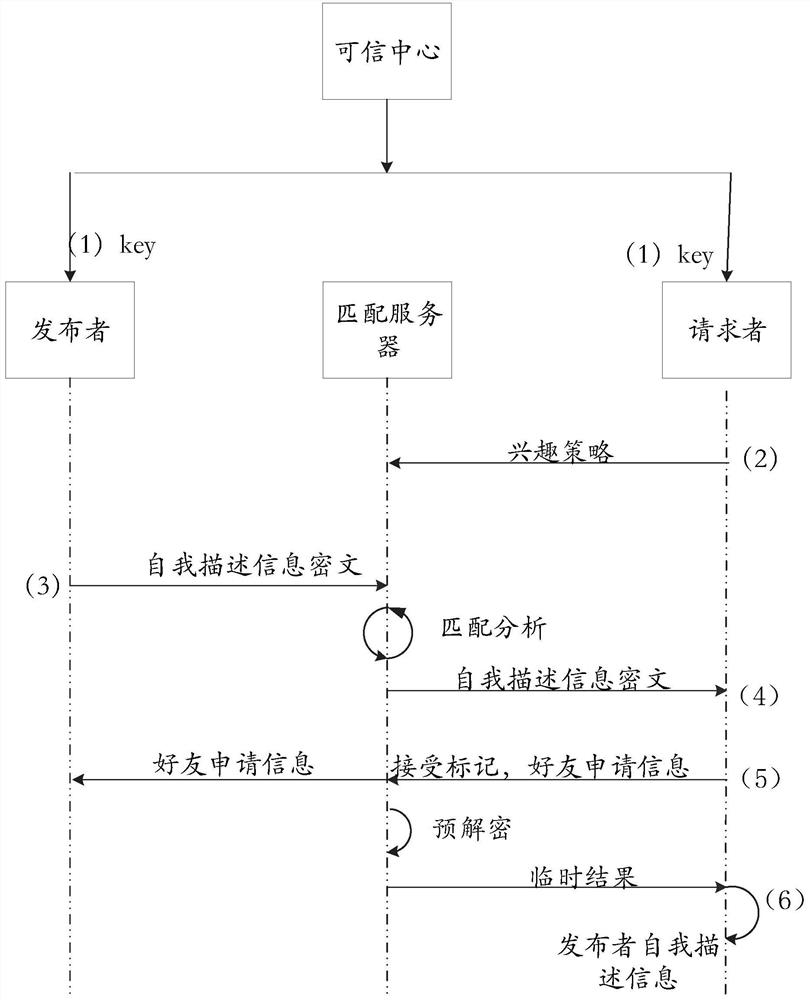
[0082] Step 1: In the initialization phase, the trusted center generates the public key PK and the system master key SK, the organization registers the issuer and the requester, and generates an interest attribute key for the requester;
[0083] Step 2: The matching server collects the requester's interest ciphertext;
[0084] Step 3: The publisher encrypts the personal information ciphertext and sends it together with his self-describing ciphertext policy, and sends the self-describing tag key to the matching server;
[0085] Step 4: The matching server analyzes the interest ciphertext obtained from the requester and the publisher's self-descriptio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com