An asymmetric group key negotiation method based on permissioninformation exchange
A group key negotiation and information exchange technology, which is applied in the field of asymmetric group key negotiation, can solve the problem of inability to exchange group information with access rights
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
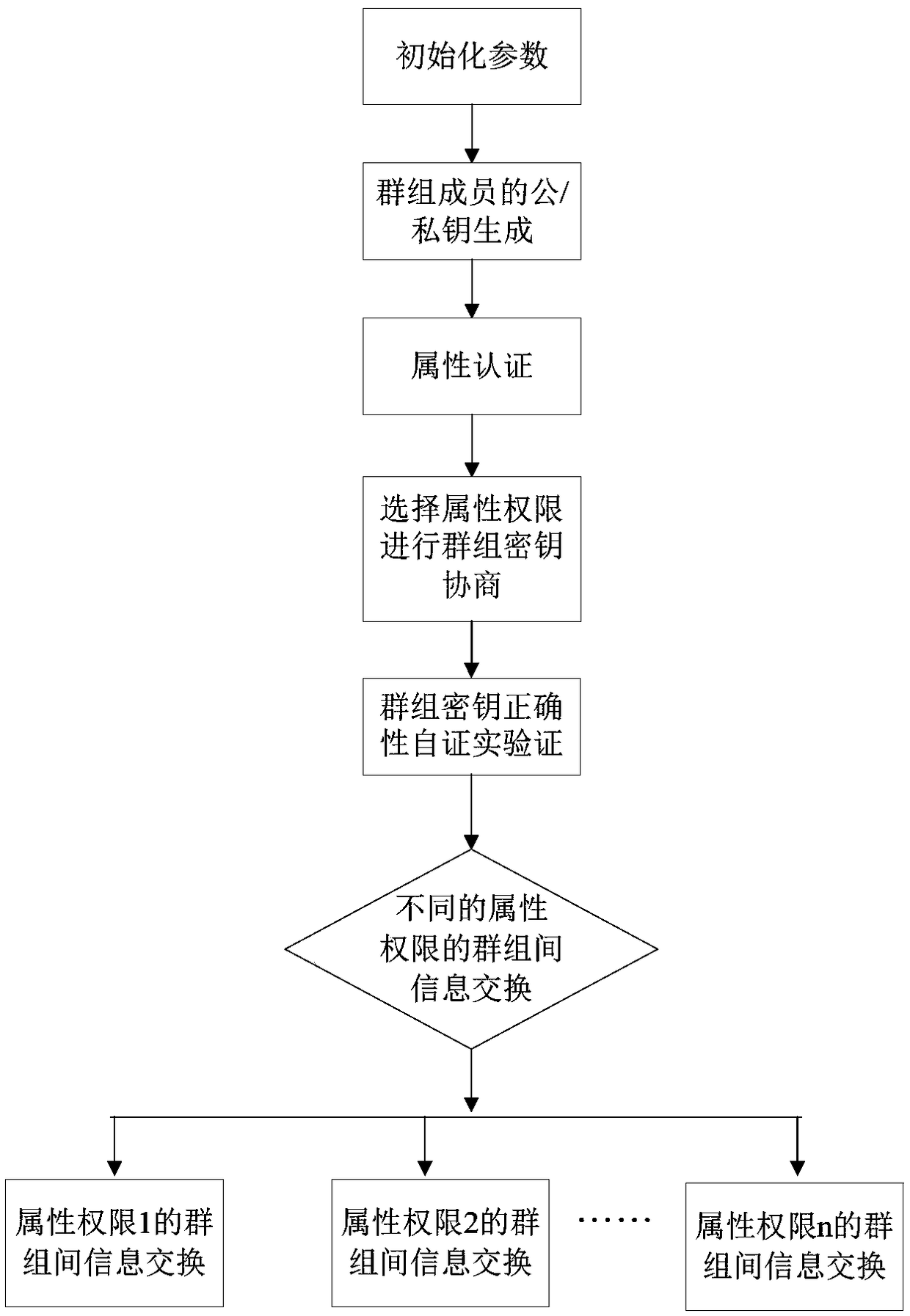
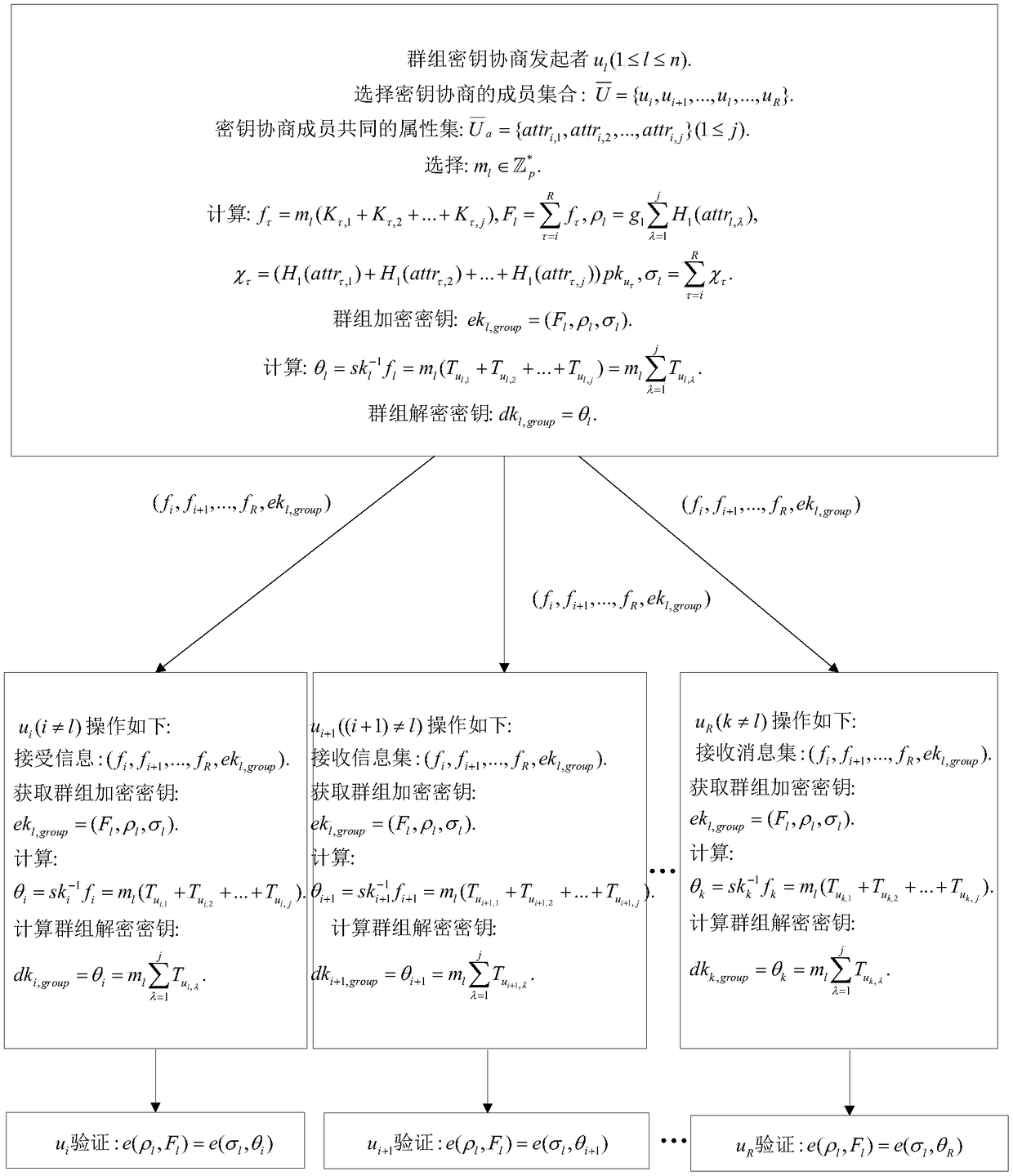
[0051] like figure 1 As shown, an asymmetric group key agreement based on authority information exchange, the steps are as follows: ①The members participating in the group key agreement first initialize the parameters, and then generate their own public / private key pairs; ②The terminal Each member registers and authenticates through the attributes they have, and obtains the group authority key parameters of the corresponding attributes; ③The group key negotiation sender selects the attribute authority that can be shared with the attribute corresponding to the attribute according to the confidentiality of its broadcast message Group authority key parameters and broadcast these parameters; ④After receiving the broadcast from the initiator of the key negotiation, the remaining members calculate and analyze their own key parameters with these group authority keys, and calculate the group key; ⑤Group encryption After the key negotiating members calculate the group key, they each ve...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com