Patents
Literature
39results about How to "The transmission process is safe and reliable" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
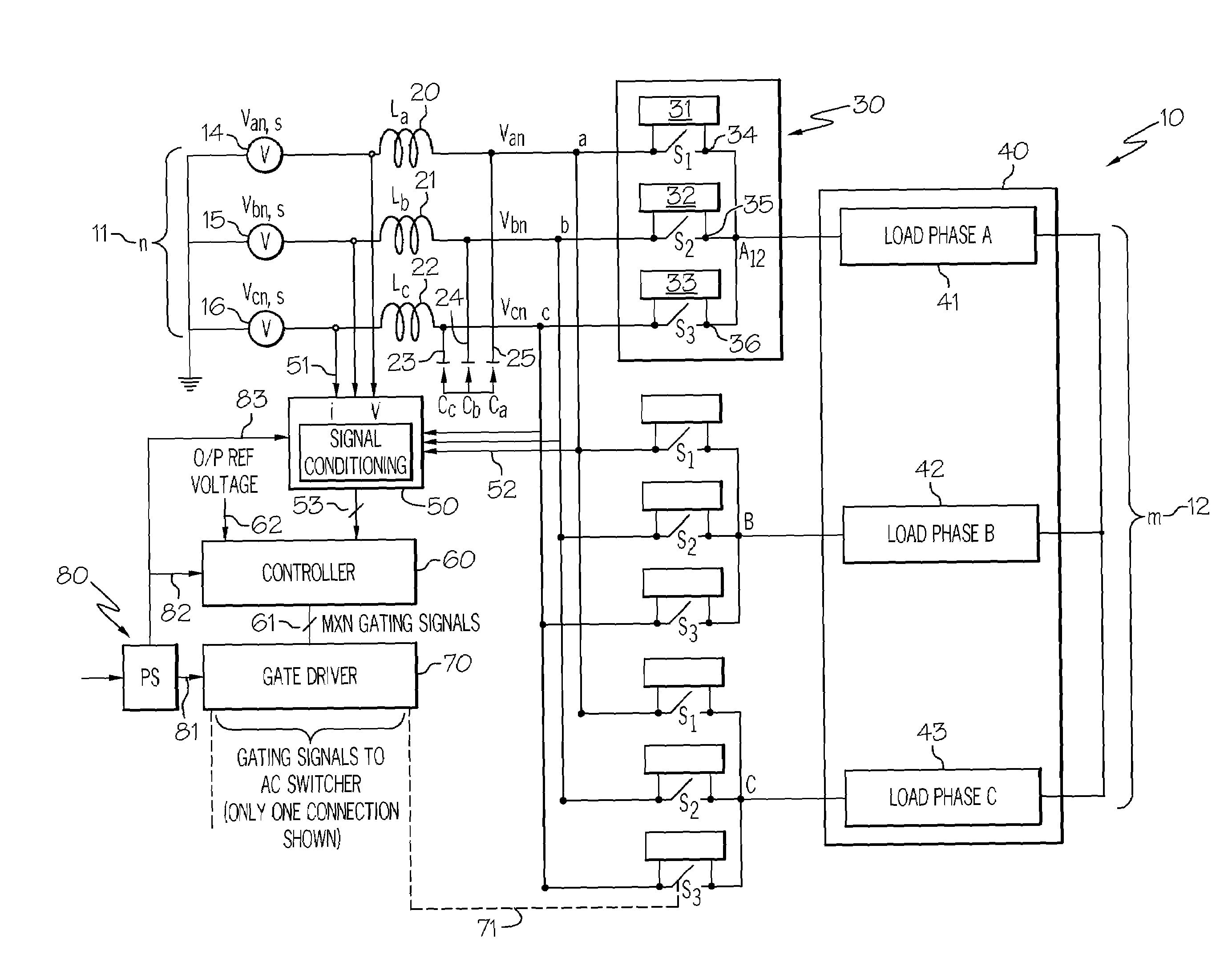
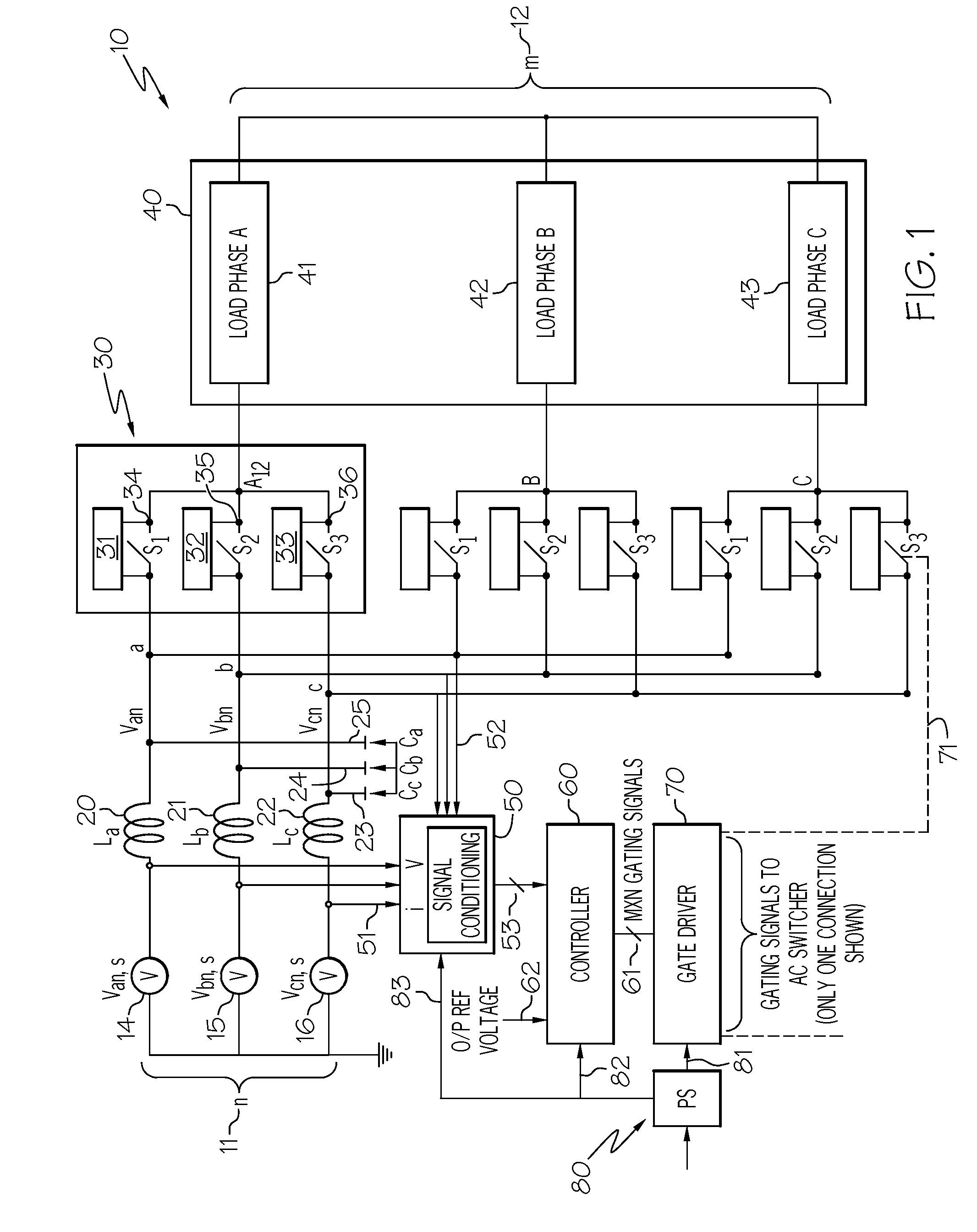
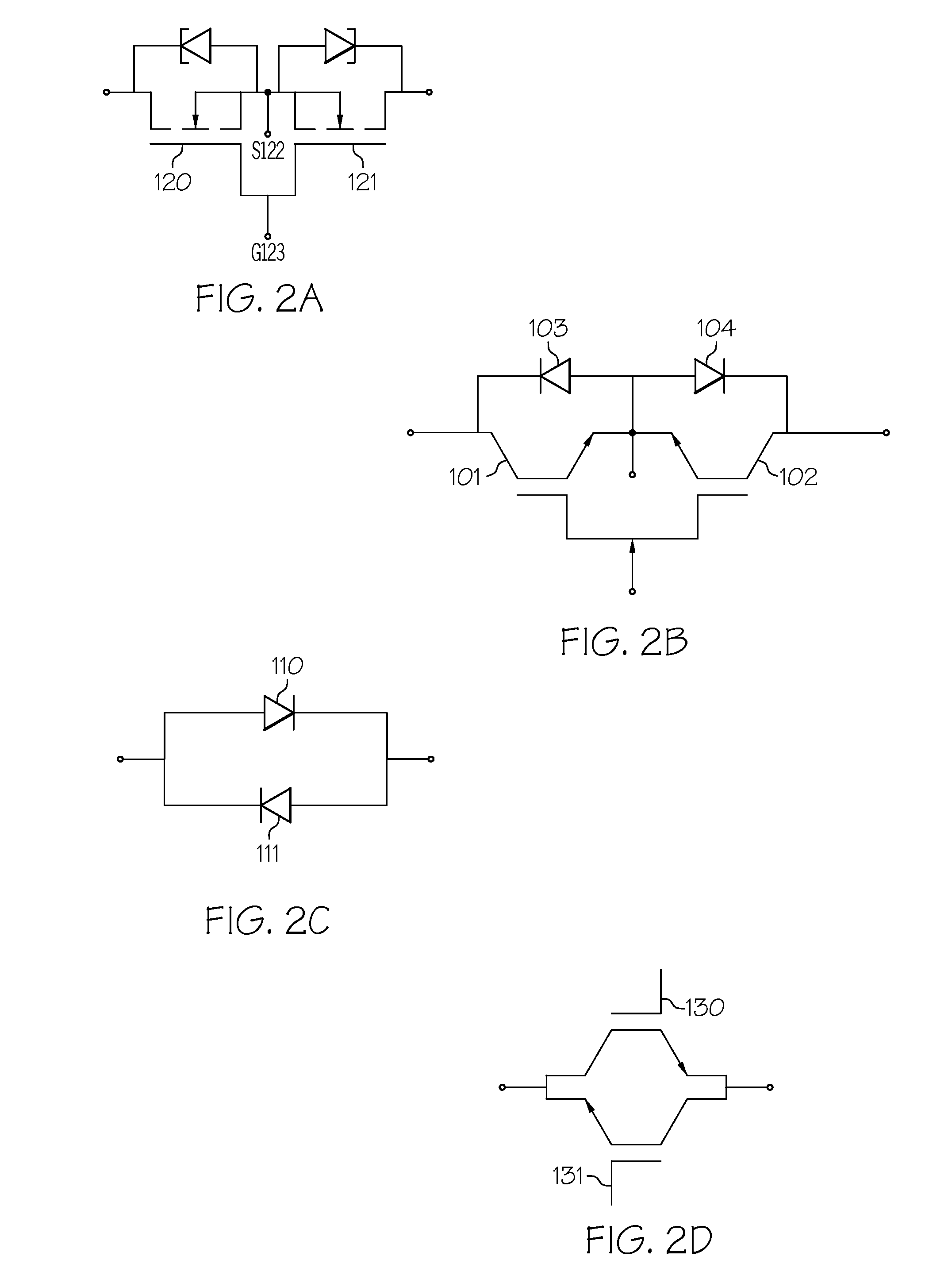
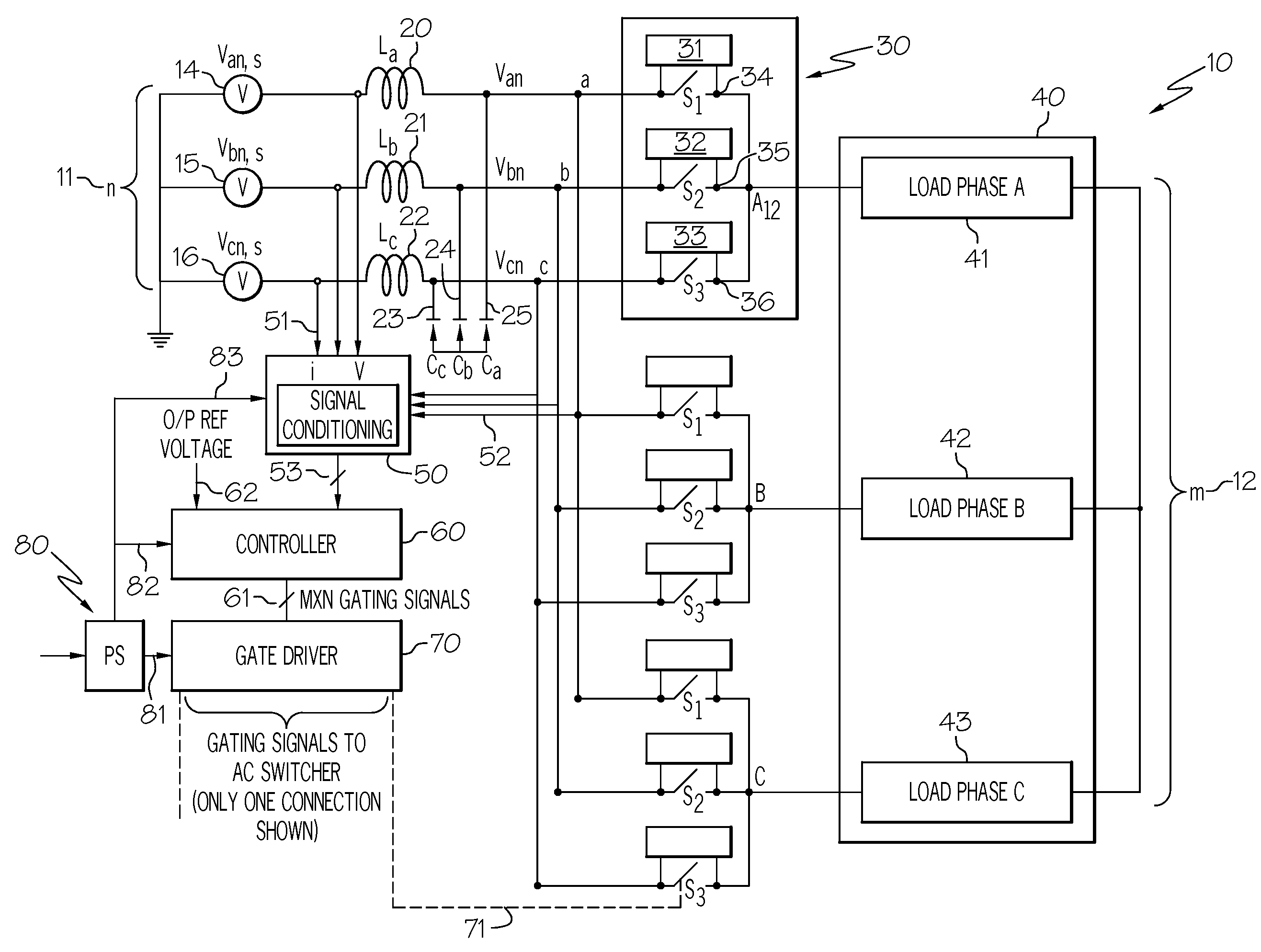
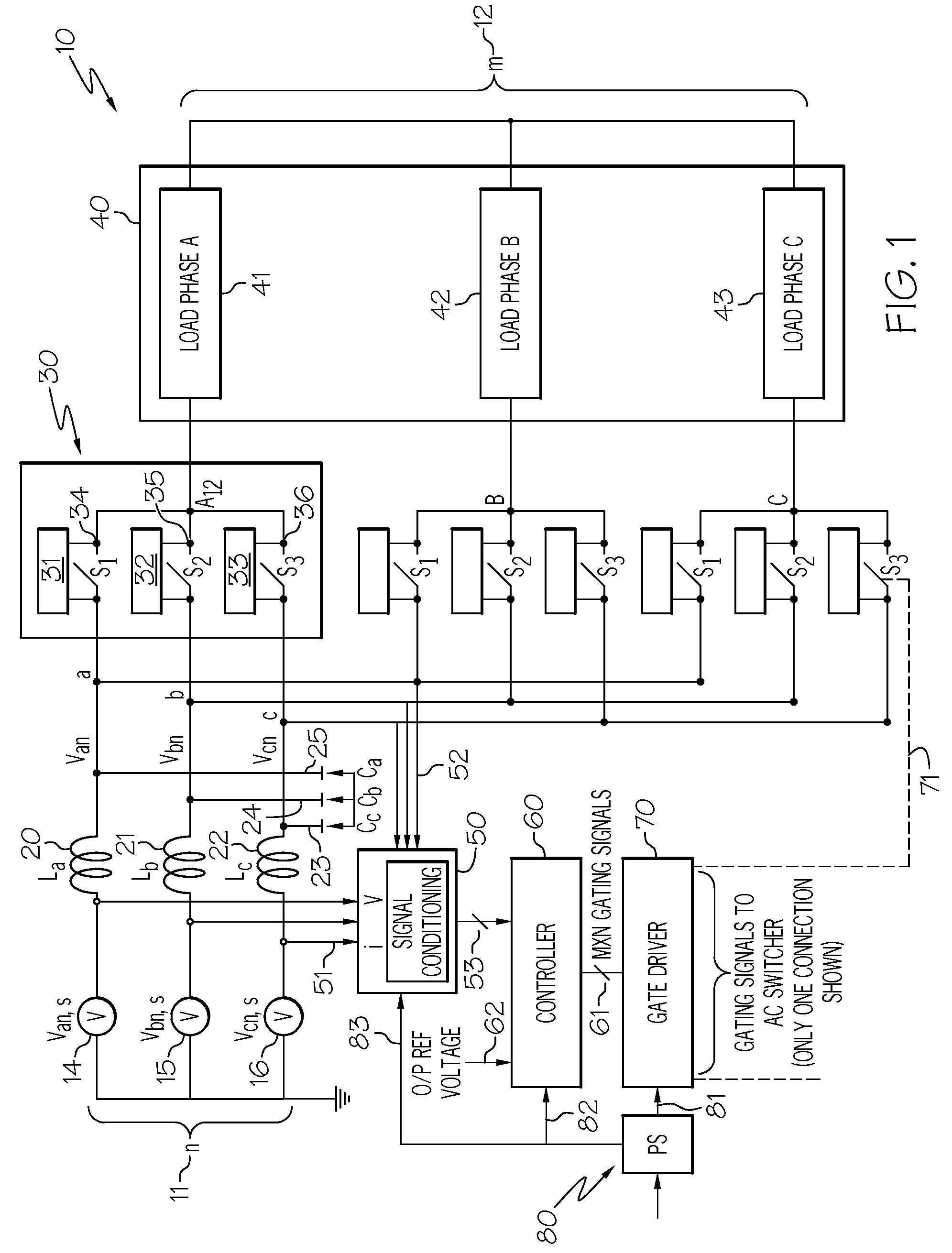
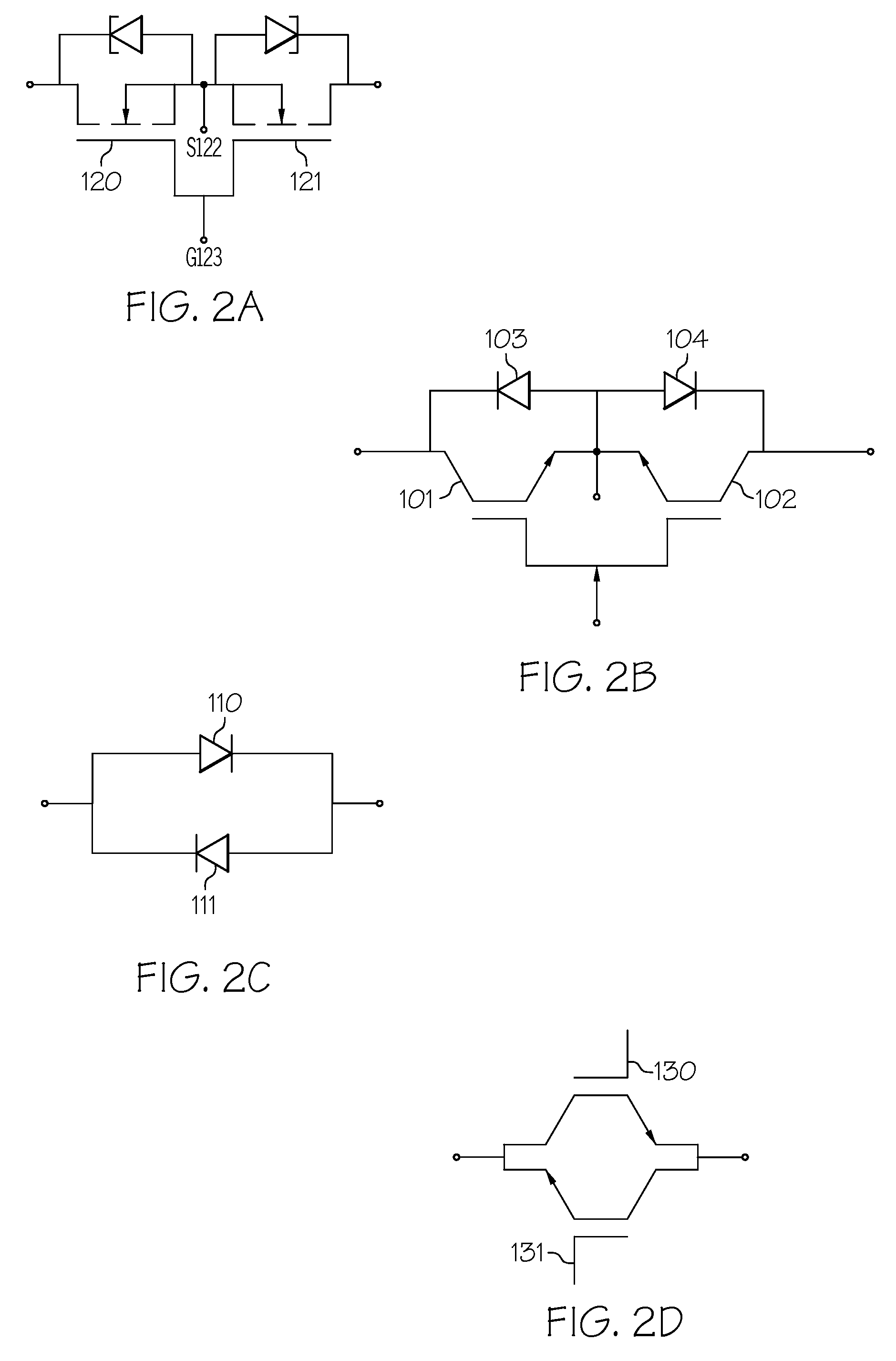
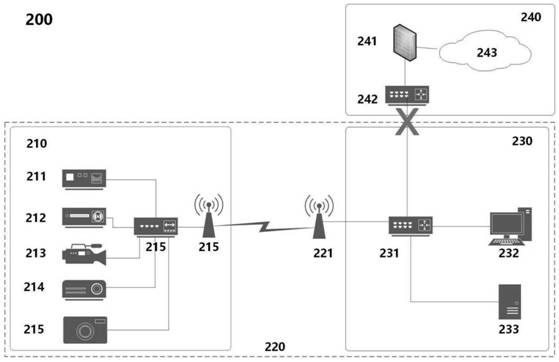
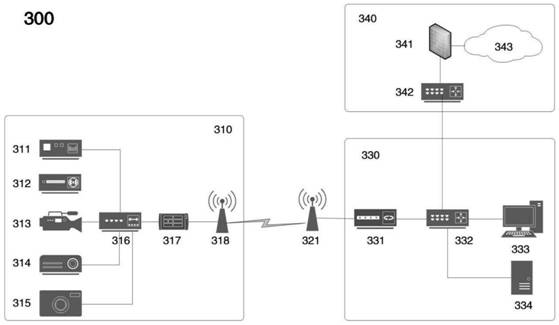
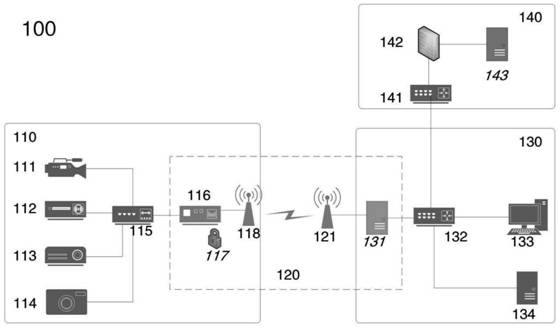
Advanced matrix converter and method for operation
InactiveUS20080285314A1Requires minimizationThe transmission process is safe and reliableConversion with intermediate conversion to dcEmergency protective circuit arrangementsMatrix convertersTime delays
A matrix converter may be provided with AC switches that comprise bi-directional sets of semiconductor switches that are gated with a common gating link. A low loss diode-bridge based snubber may facilitate introduction of time delay between sequential operations of the bi-directional set of semiconductor switches. The matrix converter may be operated in a three-phase mode with only one gating signals for each AC switch, in contrast to prior-art matrix converters which may require use multiple gating signals for each AC switch.
Owner:HONEYWELL INT INC
Advanced matrix converter and method for operation
InactiveUS7848121B2Requires minimizationThe transmission process is safe and reliableConversion with intermediate conversion to dcEmergency protective circuit arrangementsMatrix convertersTime delays
A matrix converter may be provided with AC switches that comprise bi-directional sets of semiconductor switches that are gated with a common gating link. A low loss diode-bridge based snubber may facilitate introduction of time delay between sequential operations of the bi-directional set of semiconductor switches. The matrix converter may be operated in a three-phase mode with only one gating signals for each AC switch, in contrast to prior-art matrix converters which may require use multiple gating signals for each AC switch.
Owner:HONEYWELL INT INC
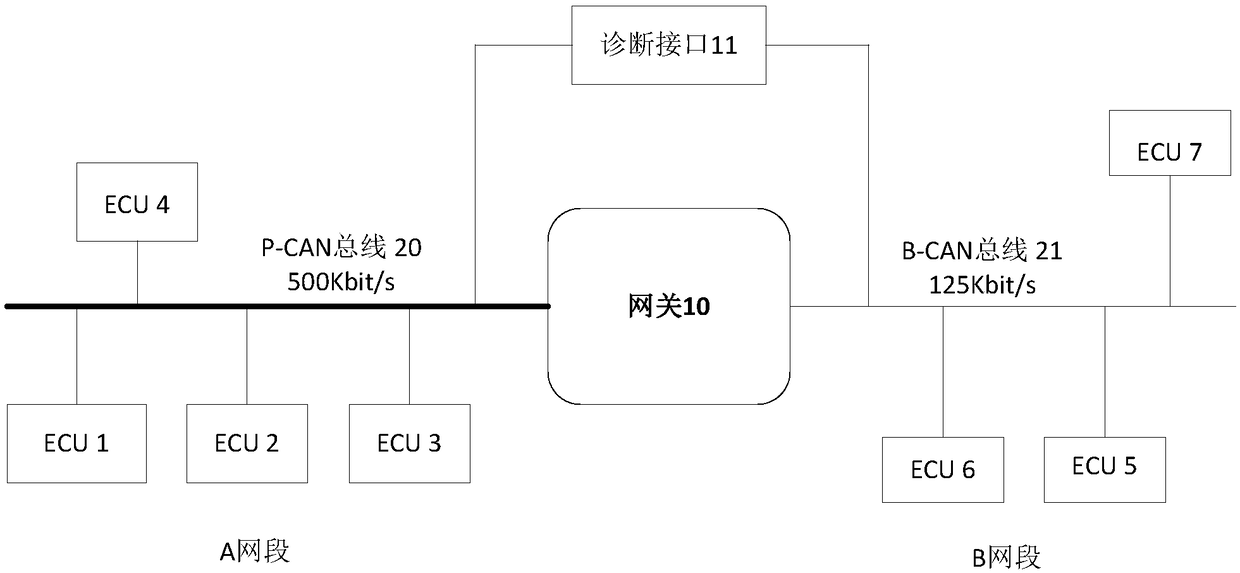
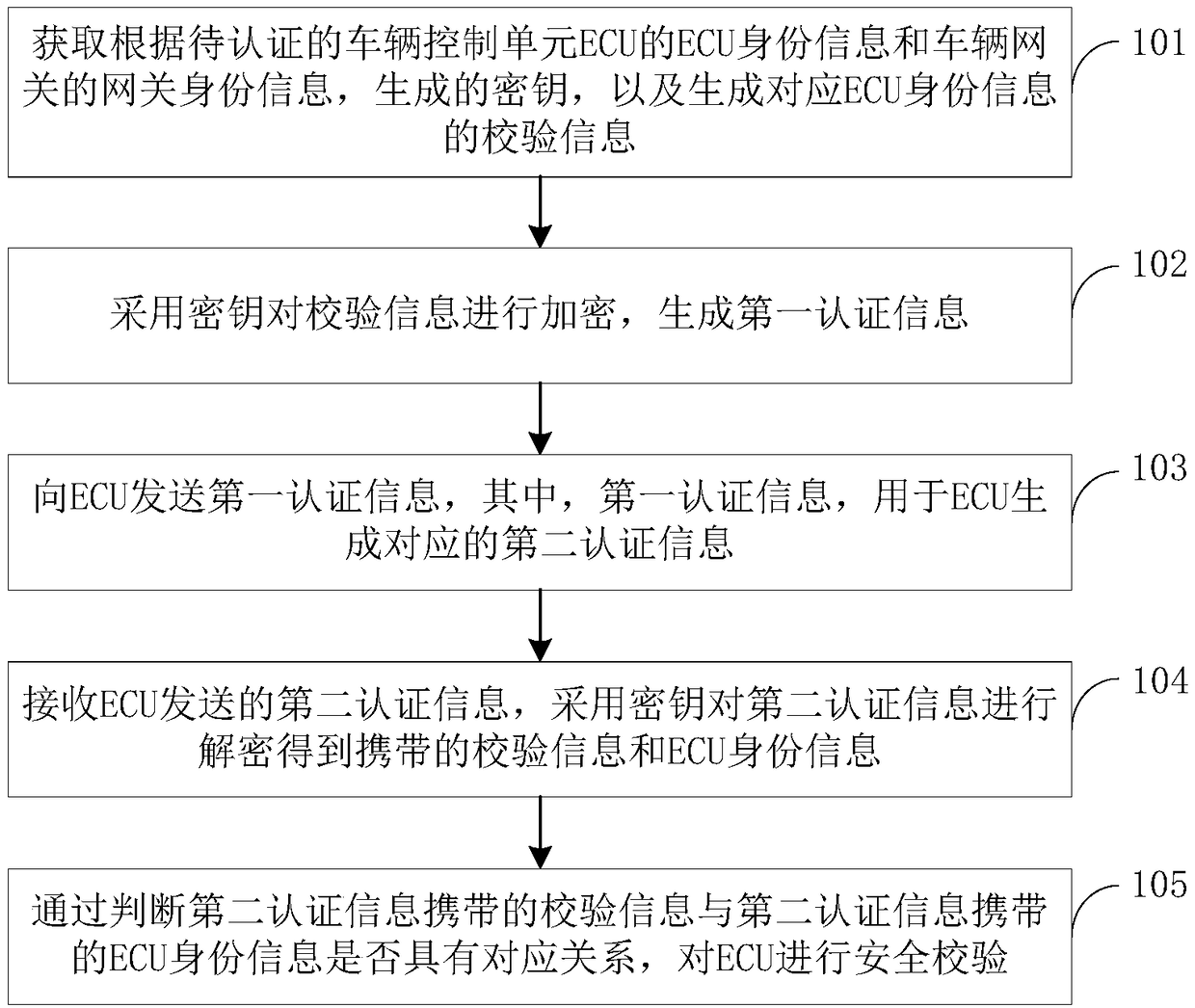
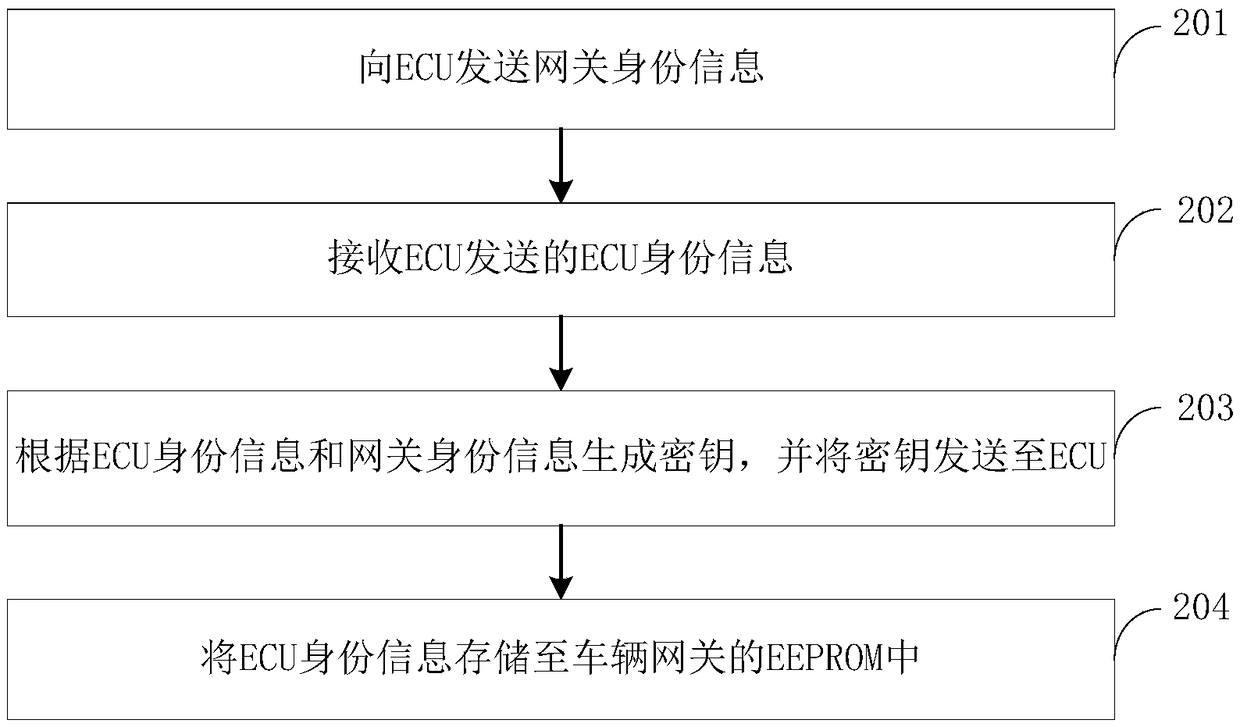
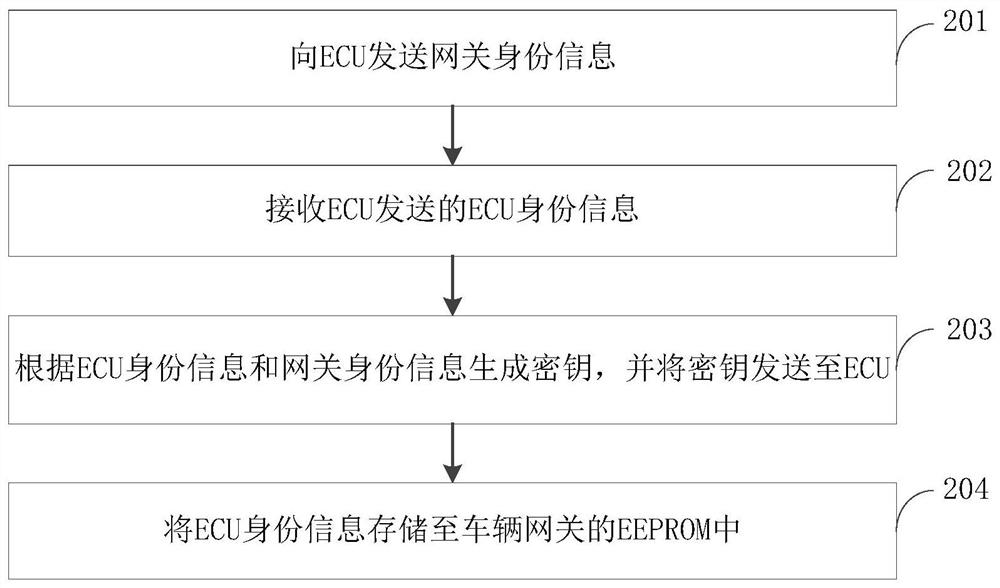
Safety control method, device and computer equipment
ActiveCN109257374AThe transmission process is safe and reliableRealize legitimacy verificationBus networksComputer equipmentTransfer procedure
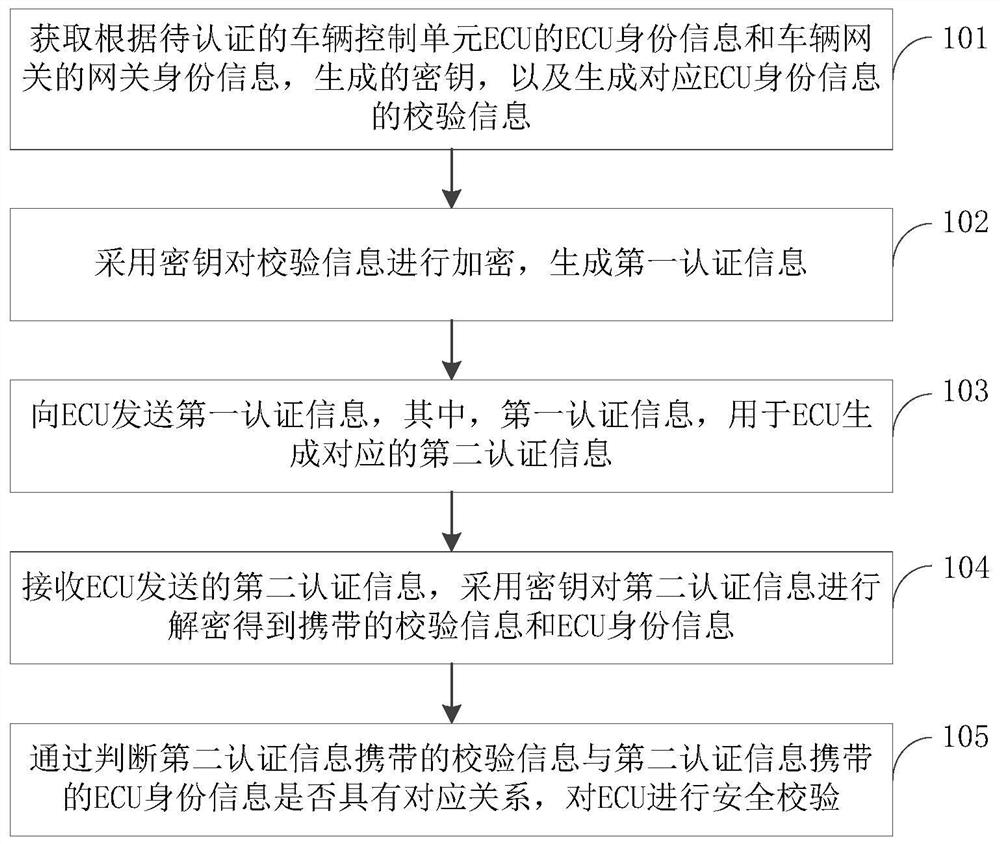
The invention provides asafety control method, a device and a computer equipment, wherein the method comprises: obtaining a key generated according to ECU identity information of a vehicle control unit ECU to be authenticated and gateway identity information of a vehicle gateway, and generating check information corresponding to the ECU identity information;a key is used to encrypt the verification information to generate the first authentication information;receiving second authentication information generated based on the first authentication information transmitted by the ECU;the second authentication information is decrypted by using a key to obtain the carried check information and the ECU identity information;by judging whether the decrypted check information and the ECU identity information have a corresponding relationship, the ECU is verified securely. The gateway verifies each ECU securely with different verifying information and encrypts with different keys when transmittingthe verifying information, which makes the transmission process more secure, realizes the ECU security verification and ensures the communication security.
Owner:APOLLO INTELLIGENT CONNECTIVITY (BEIJING) TECH CO LTD
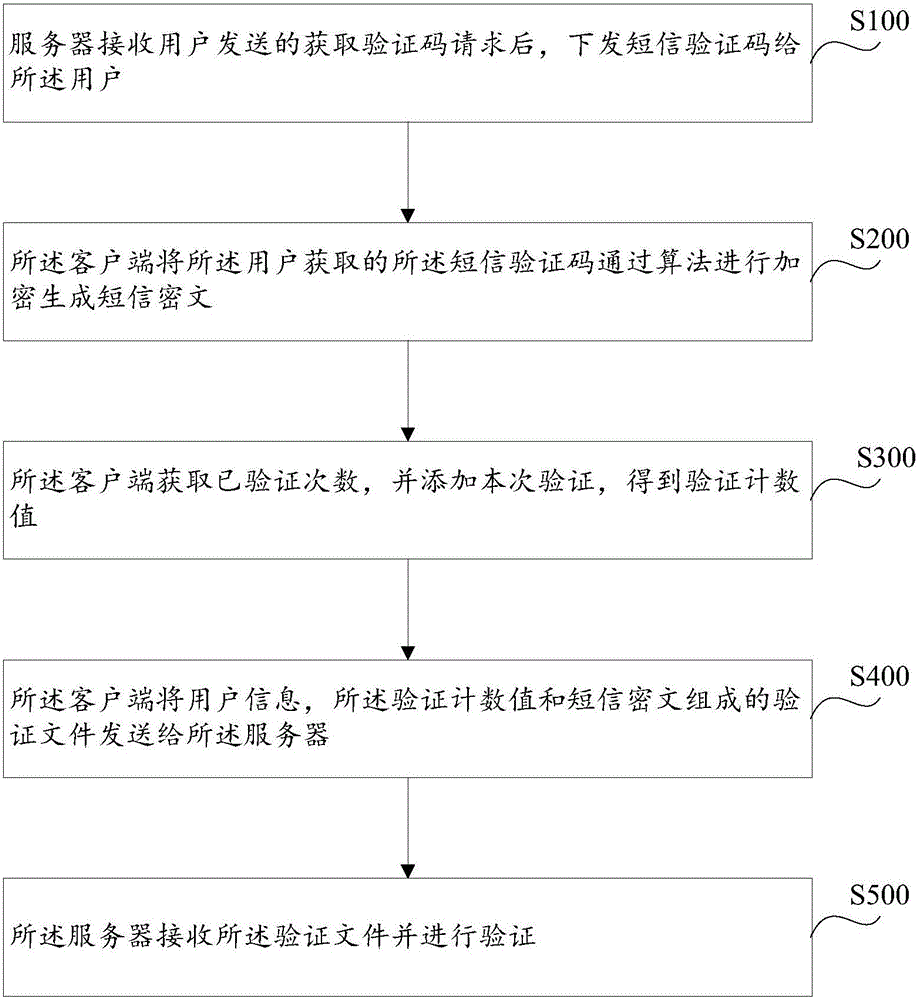
Authentication method and system of verification code security reinforcement
InactiveCN106713327AImprove securityImprove experienceMessaging/mailboxes/announcementsTransmissionTransceiverCiphertext
The invention discloses an authentication method of verification code security reinforcement. The method comprises the following steps: after a server receives a verification code acquisition request sent by a user, the server releases a short message verification code to the user; a client encrypts the short message verification code obtained by the user by using a pre-stored algorithm to generate short message ciphertext; the client obtains verification times and adds the present verification to obtain a verification counting value; the client sends a verification file composed of user information, the verification counting value and the short message ciphertext to the server; and the server receives and verifies the verification file. In addition, the invention further provides an authentication system of verification code security reinforcement. The system comprises a server and a client connected with the server, the client comprises a first information transceiver module, an encryption plug-in, a statistical module and a control module, and the control module is separately connected with the first information transceiver module, the encryption plug-in and the statistical module. By adoption of the authentication method and system disclosed by the invention, the authentication security of the verification code is greatly improved without affecting the user experience, and the user experience is improved.
Owner:SHANGHAI PEOPLENET SECURITY TECH
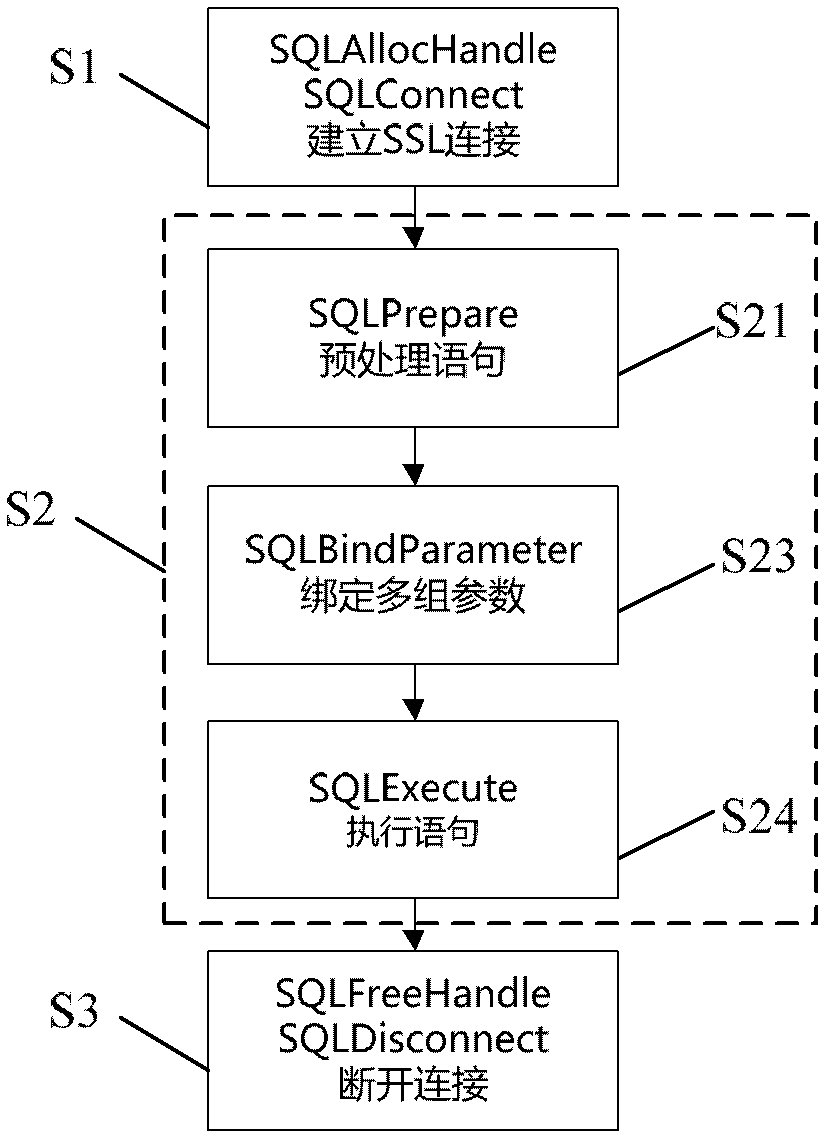
Method for updating data of database in batch mode based on communication protocol
ActiveCN102521409AThe transmission process is safe and reliableReduce the number of interactionsTransmissionSpecial data processing applicationsClient-sideSQL
The invention discloses a method for updating data of a database in batch mode based on communication protocols, which includes the following steps: step S1, security socket layer (SSL) connection is built between a client and a server; step S2, the client is communicated with the database server in interactive mode to complete batch updating of the data; and step S3, the SSL connection between the client and the database server is broken. In the step S2, a PreparedStatement object is stated through preprocessing of structured query language (SQL) statement and used for enabling the generated SQL statement to be preserved in the server in the process of execution of the SQL statement at the first time, and then sends required data to the SQL statement continually. The method adopts a once-transmission batch updating mode to all data, and facilitates pressure remission of the database server caused by batch updating of the data at the client.
Owner:北京人大金仓信息技术股份有限公司
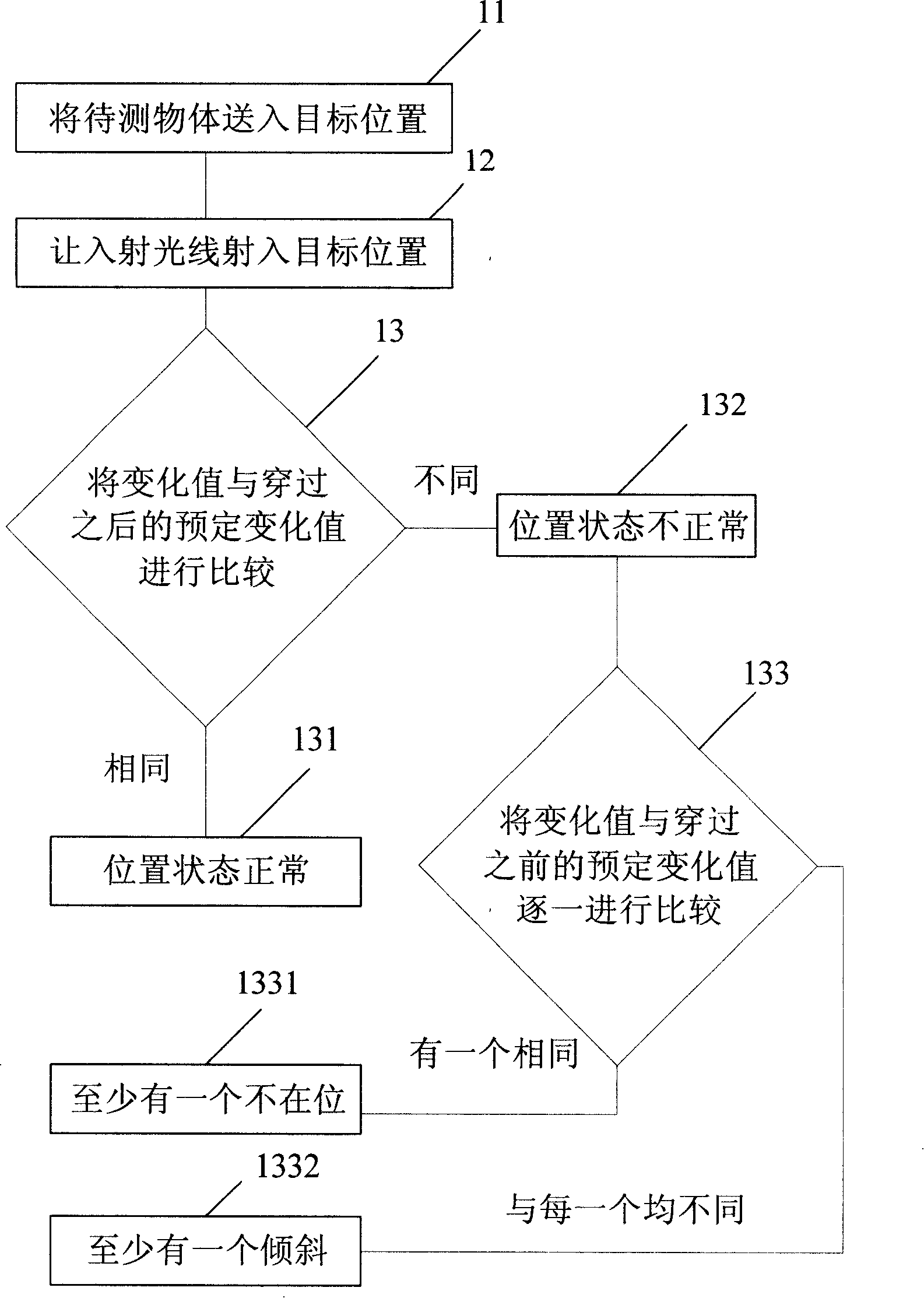
Method for on-position detecting a light-permeable object and device for detecting
InactiveCN101202237AThe transmission process is safe and reliableRealize detectionSemiconductor/solid-state device testing/measurementOptical detectionTransfer procedureComputational physics
Owner:BEIJING NAURA MICROELECTRONICS EQUIP CO LTD
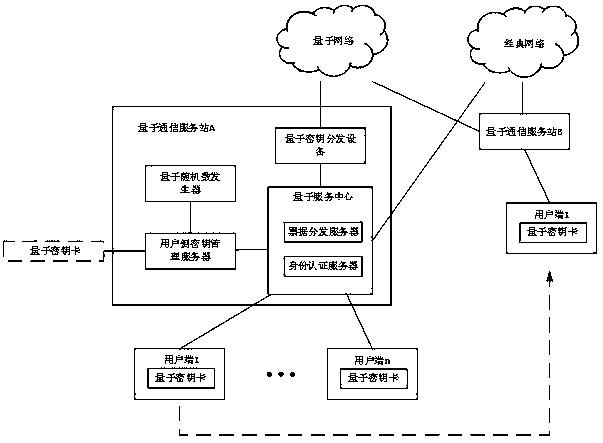
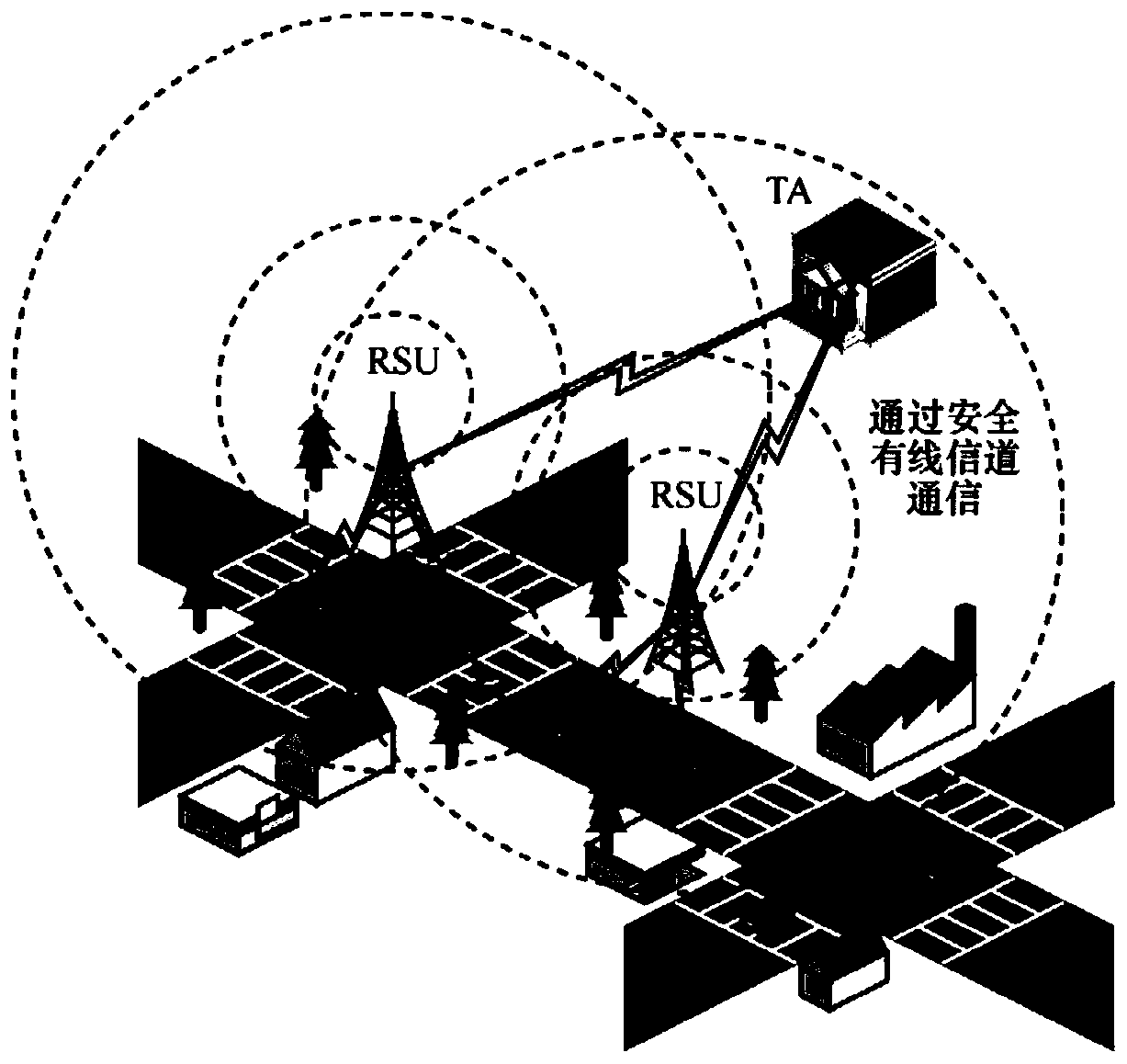
Quantum communication service station key agreement system and method based on secret sharing and timestamps
ActiveCN110932870AAvoid crackingImprove securityKey distribution for secure communicationUser identity/authority verificationAttackEngineering
The invention discloses a quantum communication service station key negotiation system and method based on secret sharing and timestamps. The system comprises a client A, a client B and a quantum communication service station, the clients and the quantum communication service stations use the secret key cards to store public keys and private keys, the quantum communication service stations and thequantum secret key cards carry out secret sharing on the clients, only current components stored in the secret key cards are hidden in a false mode, and safety is greatly improved. According to the method, the offset is used at the same time, so that the transmission process is safer, the characteristic of quantum computing resistance is achieved, the calculated amount of the encryption mode is smaller than that of a common encryption mode, therefore, the situation that the common encryption mode is used for resisting attacks of a quantum computer is avoided, and the equipment burden of all parties is reduced.
Owner:南京如般量子科技有限公司 +1
Intelligent robot inspection system for transformer substation and access operation method thereof
ActiveCN112102516AAvoid accessImplement encrypted storageChecking time patrolsClosed circuit television systemsData streamSmart substation
The invention relates to an intelligent robot inspection system for a transformer substation, and an access operation method thereof. The system comprises a terminal security reinforcement unit, a security authentication transmission proxy server and a security authentication encryption platform, wherein the terminal security reinforcement unit is installed on an inspection robot industrial personal computer; the security authentication transmission proxy server is deployed between an AP in an intelligent substation and a main control room router, and the security authentication encryption platform is deployed in an information intranet. By installing the terminal security reinforcing unit in the industrial personal computer of the inspection robot, security certification access of the inspection robot and security protection of data are realized. The security capability provided by the terminal security reinforcement unit comprises digital certificate application, data encryption anddecryption, secret key storage protection and terminal state monitoring, encryption and decryption of data streams can be flexibly configured according to needs, and the security of the substation intelligent robot inspection system is improved.
Owner:ELECTRIC POWER RESEARCH INSTITUTE OF STATE GRID SHANDONG ELECTRIC POWER COMPANY +1
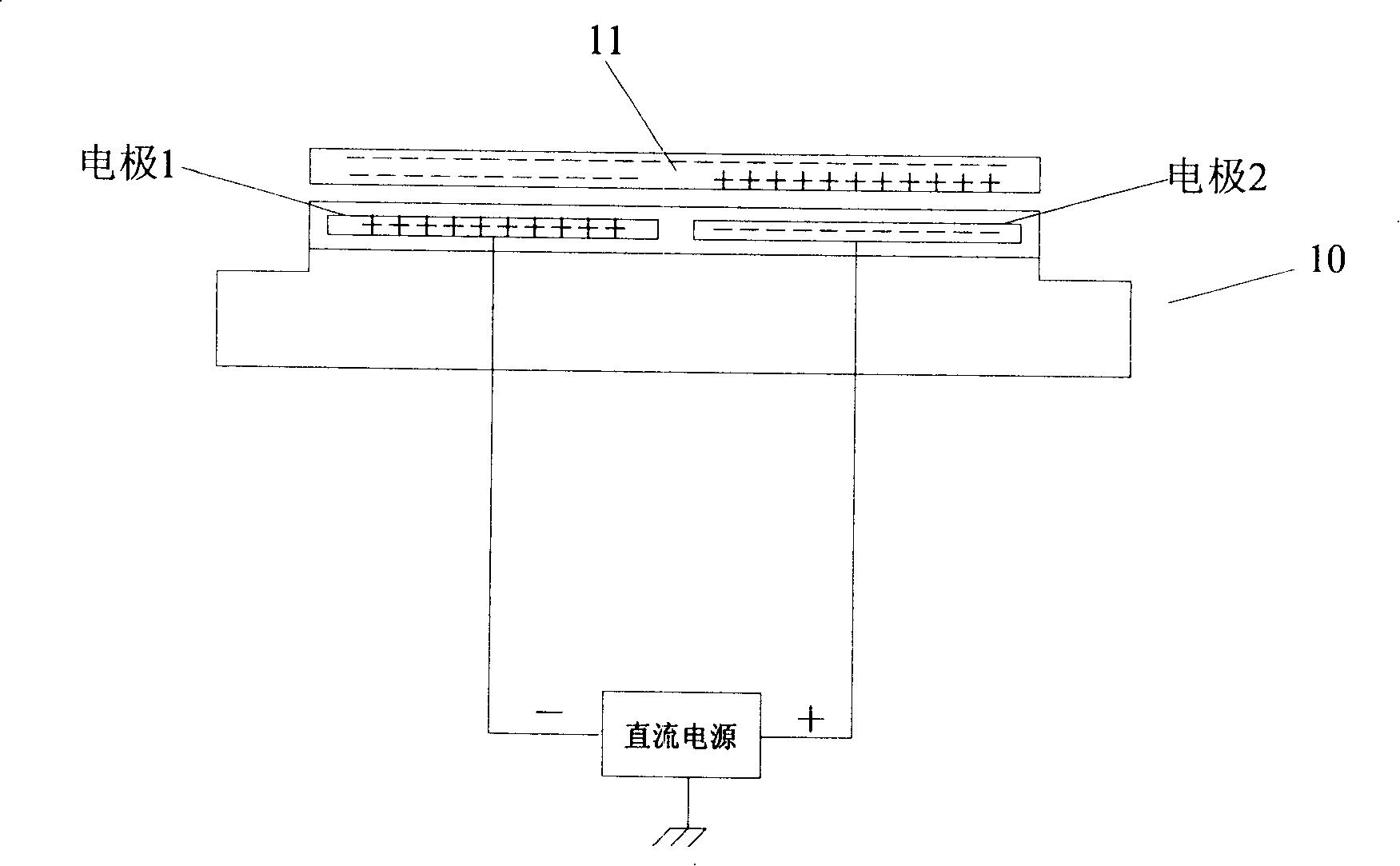
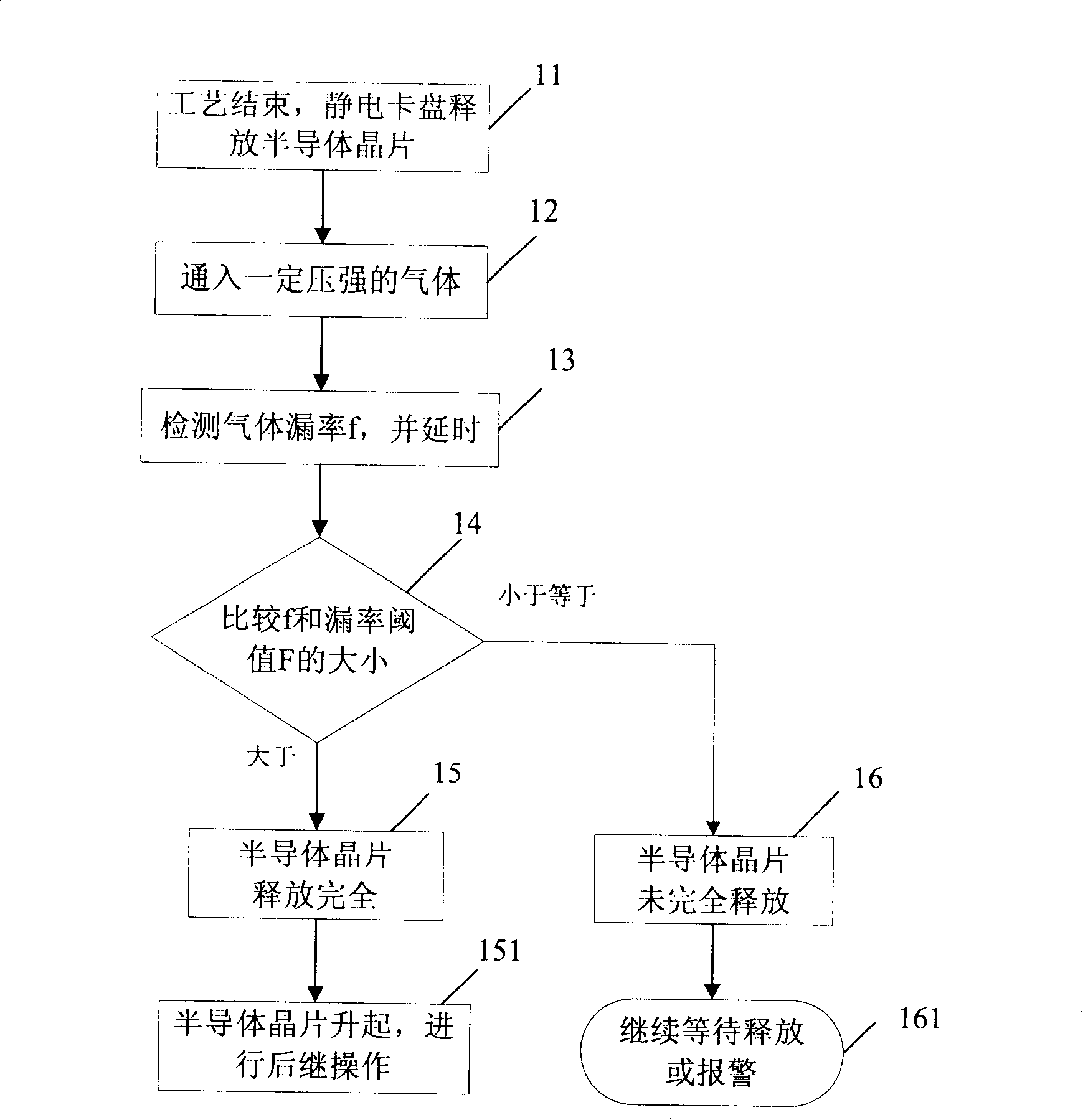
Method for detecting releasing degree of semiconductor chip from electrostatic chuck
ActiveCN101221892APrevent jumpingAvoid displacementSemiconductor/solid-state device testing/measurementSemiconductor/solid-state device manufacturingSemiconductor chipEngineering
The invention provides a method for detecting the degree of the release of a semi-conductor chip from an electrostatic chuck, which in details comprises the following steps of: passing air between the semi-conductor chip and the electrostatic chuck and comparing the rate of the detected air leakage with the set threshold value of leakage rate so as to judge the degree of the release of the semi-conductor chip. With the detection method, the degree of the release of the semi-conductor chip from the electrostatic chuck can be judged effectively so as to conduct corresponding operation according to the degree of the release, which avoids the jump or displacement of the semi-conductor chip, reduces the accident rate and ensures the safety and reliability of the semi-conductor chip during transmission.
Owner:BEIJING NAURA MICROELECTRONICS EQUIP CO LTD
Intelligent safe power utilization monitoring system integrated with Internet-of-things technology
InactiveCN112511655AImprove securitySmooth transmissionMeasurement devicesParticular environment based servicesPrivate networkThe Internet
The invention discloses an intelligent safe power utilization monitoring system integrated with an Internet-of-things technology. The intelligent safe power utilization monitoring system comprises anintelligent host module, a multi-service gateway module and an Internet-of-things platform, the intelligent host module is connected with a device to be monitored, collects electrical safety data of the device to be monitored in real time, and generates an alarm for abnormal information. The multi-service gateway module is connected with the intelligent host module, encrypts the electrical appliance safety data, converts the encrypted electrical safety data through a protocol and transmits the encrypted electrical safety data to the Internet-of-things platform; and the Internet-of-things platform acquires information in the multi-service gateway module, and performs integrated control and data support for applications of upper-layer services. According to the system, a power service private network frequency wireless communication network is adopted to provide full network coverage for power generation enterprises, and the transmission process is more stable, efficient and safer; in addition, the Internet-of-things platform realizes descriptive-diagnostic-predictive-guidance type full-cycle power utilization safety supervision by uninterruptedly storing, analyzing, mining and utilizing the data, so that the safety of a power utilization system is greatly improved.
Owner:BEIJING HUADIAN TIANREN ELECTRIC POWER CONTROL TECH
Anti-quantum computing Internet of Vehicles system based on secret sharing and mobile terminal and authentication method thereof
ActiveCN111212400AImprove securityWon't leakParticular environment based servicesIn-vehicle communicationThird partyComputer network
The invention discloses an anti-quantum computing Internet of Vehicles system based on secret sharing and a mobile terminal and an authentication method thereof. The system comprises a plurality of mobile terminals, a third-party trust mechanism, vehicle keys, vehicle-mounted units and roadside units. The vehicle keys and the vehicle-mounted units are arranged on a plurality of vehicles. The roadside units are used for transmitting messages of the vehicle-mounted units and the third-party trust mechanism. The mobile terminals and the vehicle-mounted units are paired in a one-to-one mode, and the vehicle-mounted units authenticate the mobile terminals. By arranging the mobile terminal, the safety of the vehicle-mounted unit to the driver authentication process is enhanced in the authentication of the vehicle-mounted unit to the mobile terminal. A signature based on ID cryptography is adopted for a transmitted message, an ID is changed into a form of a public key random number, secret sharing is adopted, and a secret is added into the signature message, so that an actual signature message cannot be obtained by an enemy, and a digital signature has very high quantum-resistant computing security. The offset is used, so that the transmission process is safer, and meanwhile, the equipment burden is reduced.
Owner:南京如般量子科技有限公司 +1
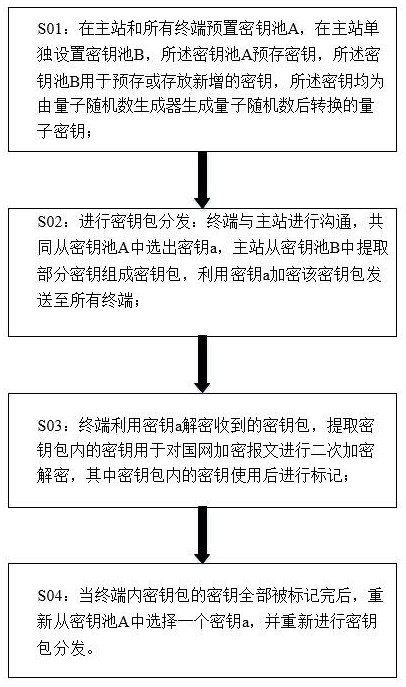
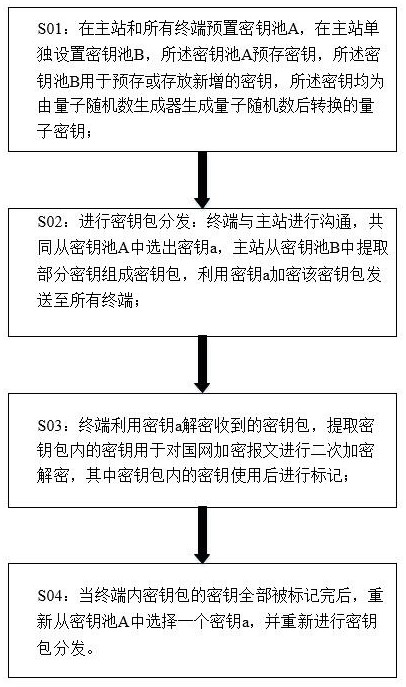
Power distribution automation information encryption method based on quantum reinforcement
ActiveCN113037486AMature and reliable technologyThe transmission process is safe and reliableKey distribution for secure communicationMaster stationEngineering
The invention discloses a distribution automation information encryption method based on quantum reinforcement, and the method comprises the steps: presetting a key pool A in a master station and all terminals, independently setting a key pool B in the master station, pre-storing a key in the key pool A, pre-storing or storing a newly added key in the key pool B, and storing the newly added key in the key pool B, wherein the keys are quantum keys converted after quantum random numbers are generated by a quantum random number generator; distributing key packets: the terminals communicate with the master station, the terminals and the master station jointly select a key a from the key pool A, the master station extracts part of keys from the key pool B to form a key packet, and the key packet is encrypted by using the key a and sent to all the terminals; the terminal decrypting the received key packet by using the key a, extracting the key in the key packet for performing secondary encryption and decryption on the state grid encrypted message, and marking the key in the key packet after being used; and after all the keys of the key packet in the terminal are marked, a key a being selected from the key pool A again, and key packet distribution being performed again.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER CO LTD HANGZHOU POWER SUPPLY CO
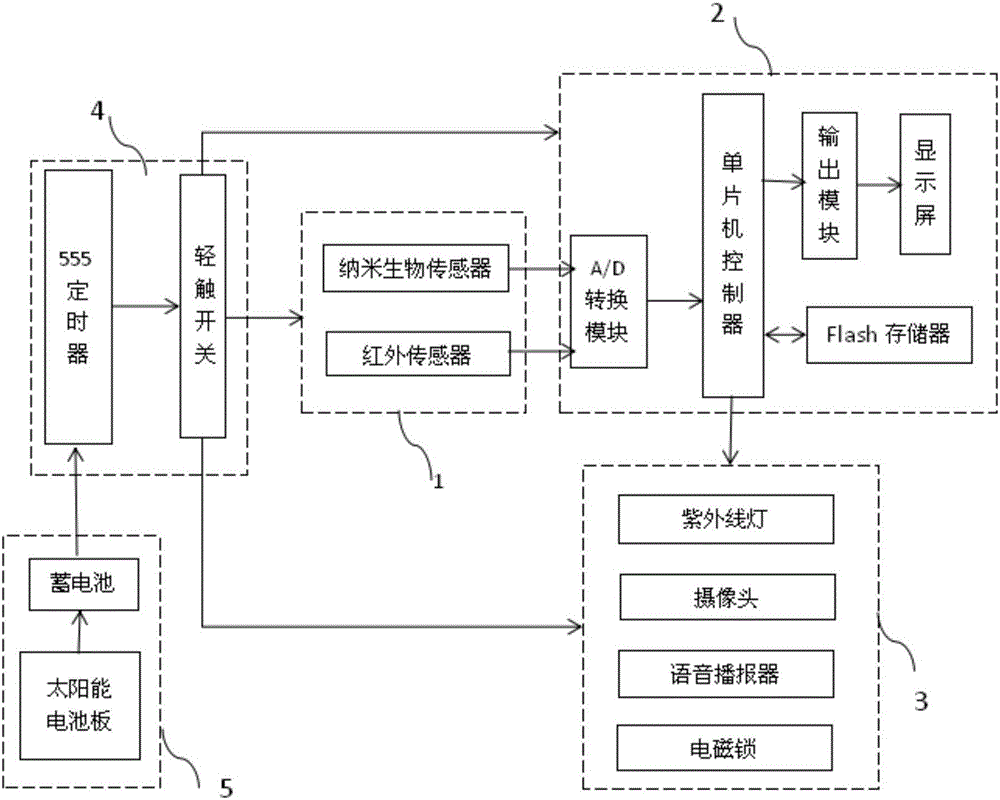
Ultraviolet disinfecting system for operating room
InactiveCN106512037AEasy to useReasonable designLavatory sanitoryRadiationInformation processingMicrocontroller
The invention belongs to the field of medical disinfection, and discloses an ultraviolet disinfecting system for an operating room. The ultraviolet disinfecting system comprises an information acquisition unit, an information processing unit, an implementing unit, a timed starting unit and a power supply unit, wherein the information acquisition unit comprises a nano biosensor and a human body proximity sensor; the information acquisition unit is connected to the information processing unit; the information processing unit comprises a single chip controller which is connected to the information acquisition unit, a display screen which is connected to the single chip controller and a Flash memory; the implementing unit comprises an ultraviolet lamp, a camera, a voice broadcast device and an electromagnetic lock; the implementing unit and the single chip controller are connected; the timed starting unit comprises a 555 timer which is connected to the power supply unit and a touch switch which is connected to the 555 timer; and the power supply unit is electrically connected to the information acquisition unit, the information processing unit and the implementing unit by virtue of the timed starting unit. With the application of the ultraviolet disinfecting system provided by the invention, the environment of the operating room can be monitored in real time and comprehensive and effective disinfection can be automatically conducted, so that the labor intensity of cleaning personnel is reduced.
Owner:GUANGXI UNIV
Quantum secret communication system and method based on secret sharing and asymmetric cryptography
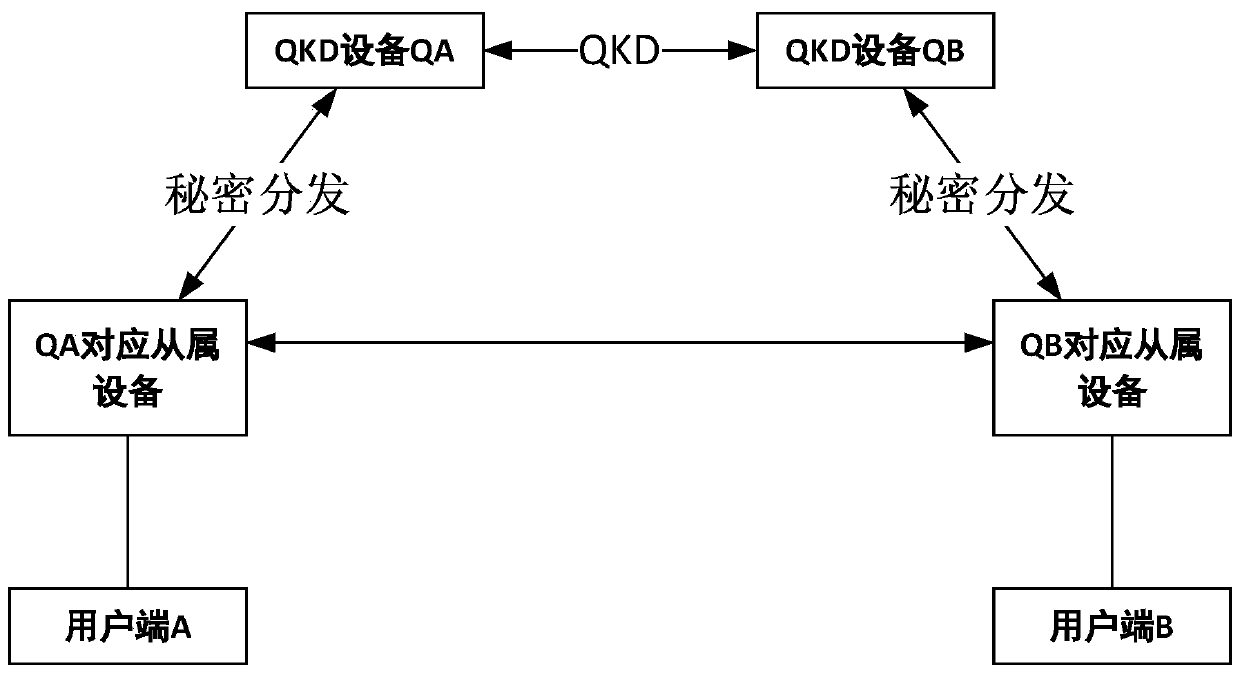
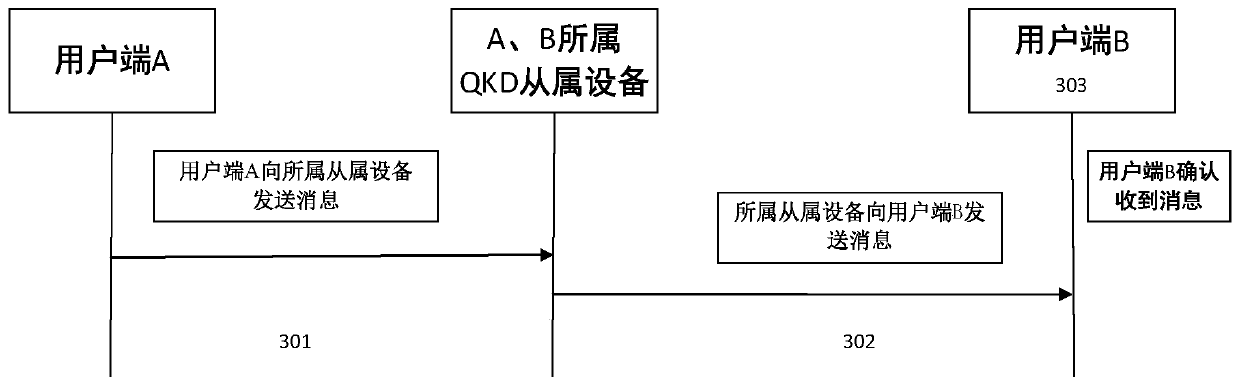
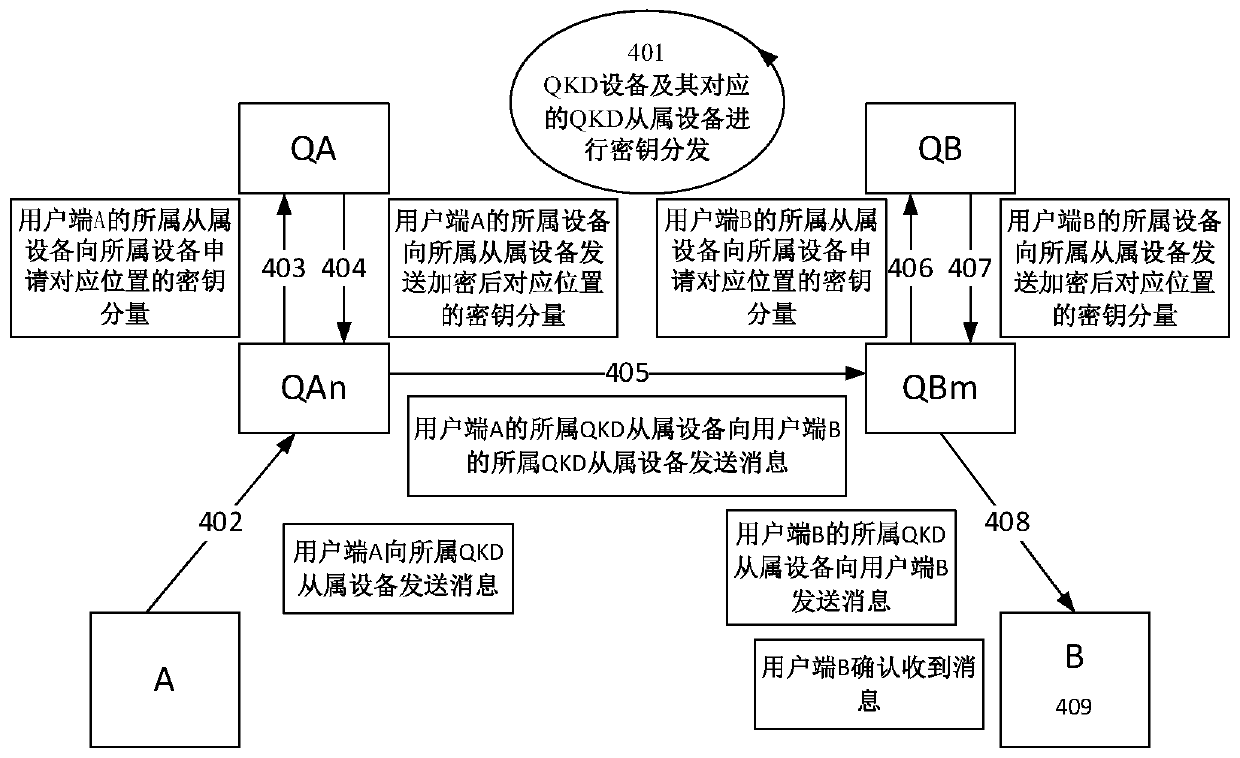
ActiveCN111314083AImprove securityImprove the ability of key serviceKey distribution for secure communicationUser identity/authority verificationKey (cryptography)Communications system
The invention discloses a quantum secret communication system and method based on secret sharing and asymmetric cryptography. The method is used for secret communication between user sides through QKDequipment. The QKD device generates a secret key based on the QKD or the true random number generator, secret sharing of the generated secret key between the QKD device and the QKD slave device is achieved through a symmetric secret key pool between the QKD device and the QKD slave device, and offset calculation is introduced in the communication process for encryption. According to the method, secret sharing is carried out on the QKD symmetric key pool, so that the possibility that the key is stolen is greatly reduced, and the safety of the QKD key is effectively improved. A single QKD device is provided with a plurality of slave devices, so that the capacity of the QKD device for providing key service and the system stability are improved. The offset is used for encrypting the data, andother parties cannot crack the data protected by the offset, so that the method has the characteristic of quantum computing resistance.
Owner:南京如般量子科技有限公司 +1
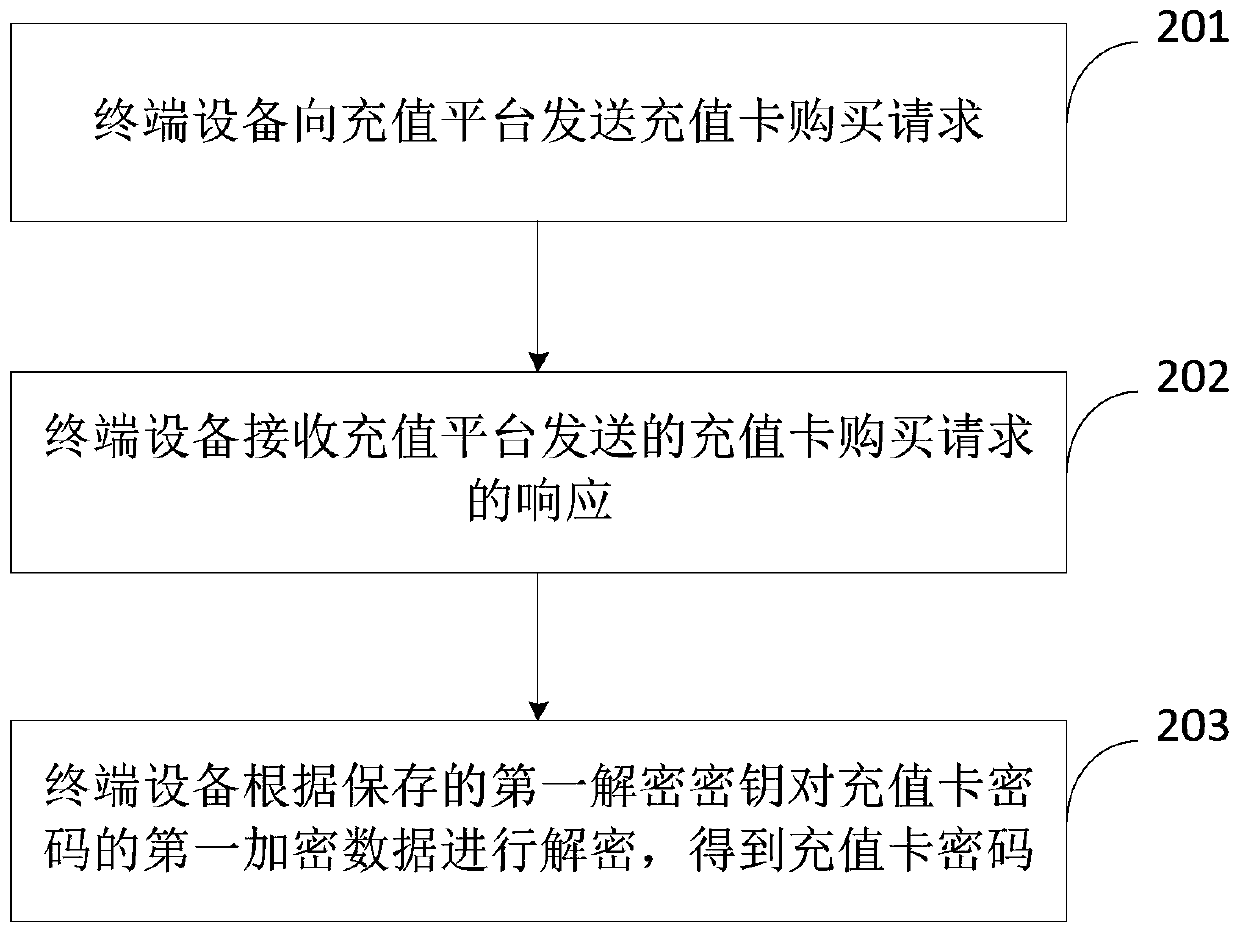
Recharging card information encryption method and device, terminal equipment and recharging platform
ActiveCN111127000AThe transmission process is safe and reliableAvoid property damagePayment protocolsPasswordTerminal equipment
The invention provides a rechargeable card information encryption method and device, terminal equipment and a recharging platform. The method comprises the following steps: after sending a rechargeable card purchase request by the terminal equipment, the recharging platform encrypts a password of a recharging card by using a first encryption key to acquire first encrypted data, the first encrypteddata is sent to the terminal equipment; and the terminal equipment decrypts the first encrypted data of the rechargeable card password according to the stored first decryption key to acquire the password of the rechargeable card. During the process of purchasing the rechargeable card, according to the method, the password of the rechargeable card is encrypted, so that the password of the rechargeable card is transmitted in the form of the first encrypted data, even if an illegal user steals the first encrypted data, the password of the rechargeable card cannot be obtained, the password transmission process is safer and more reliable, and property loss of the user or an operator is avoided.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
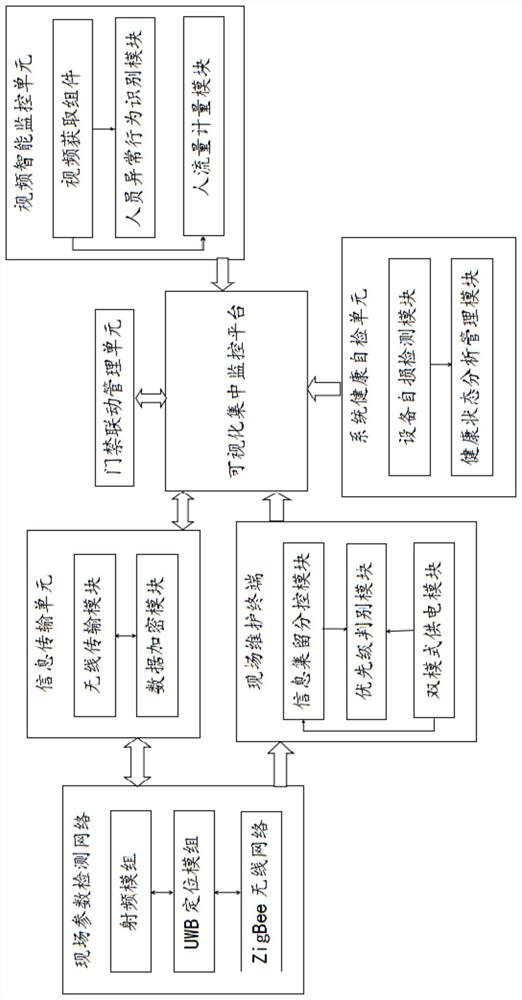
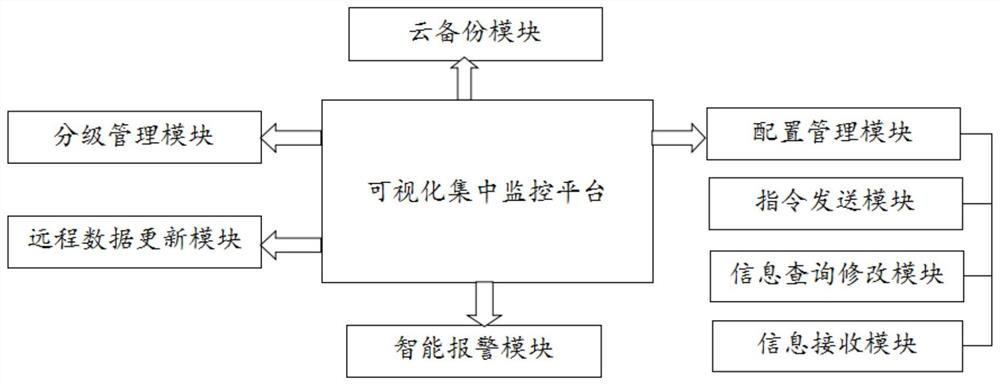
Security and protection monitoring system based on Internet of Things
ActiveCN112187940AAutomatic updateOptimize layoutMeasurement devicesParticular environment based servicesVideo monitoringThe Internet
The invention provides a security and protection monitoring system based on the Internet of Things. The security and protection monitoring system comprises a field parameter detection network, a system health self-checking unit, an intelligent video monitoring unit, an information transmission unit, a field maintenance terminal and a visual centralized monitoring platform. The field parameter detection network is used for forming a front-end environment information and article and personnel position information detection network; the system health self-checking unit is used for carrying out periodic self-checking on the system and forming a self-checking report; the intelligent video monitoring unit is used for monitoring personnel access at an entrance, pedestrian flow in a specific areaand abnormal behaviors of personnel; the information transmission unit is used for transmitting detection data and control instructions; the field maintenance terminal comprises an information collection sub-control module, a priority discrimination module and a dual-mode supply module; and the visual centralized monitoring platform is used for receiving the detection data and carrying out visualmanagement. According to the invention, layout can be simpler and more convenient, data can be automatically updated, a transmission process is safer, and management efficiency is higher.
Owner:浙江安防职业技术学院
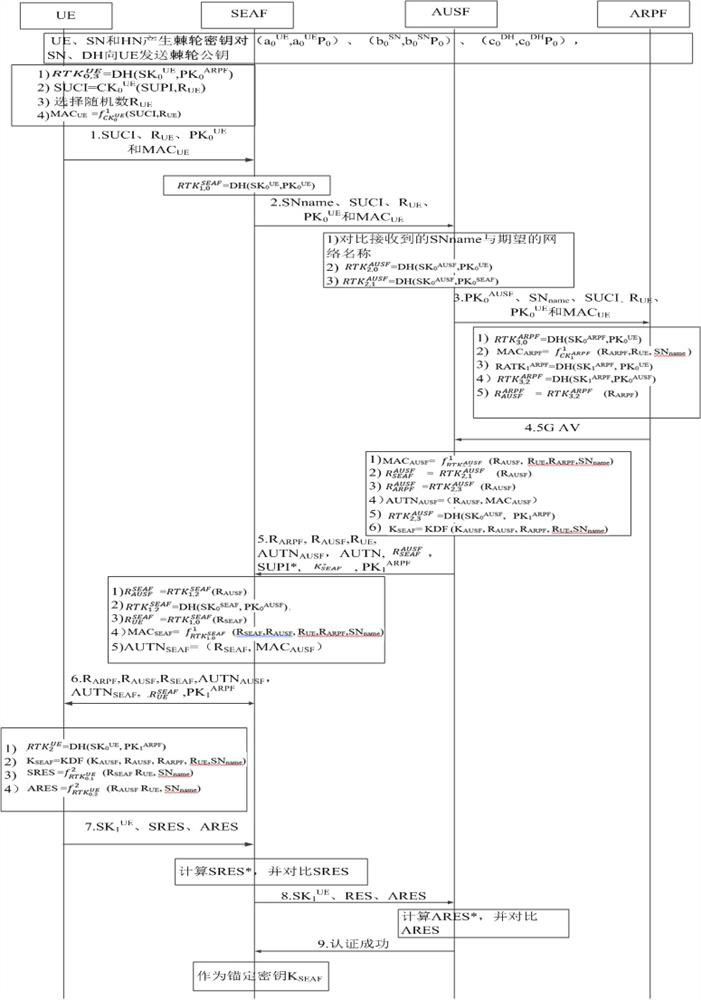
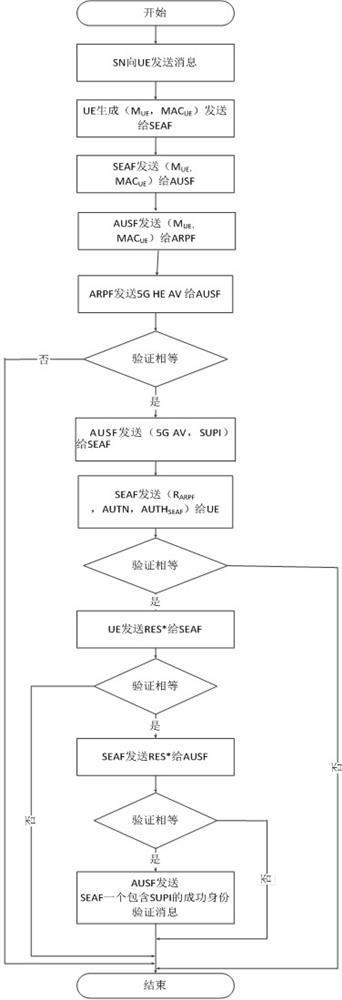
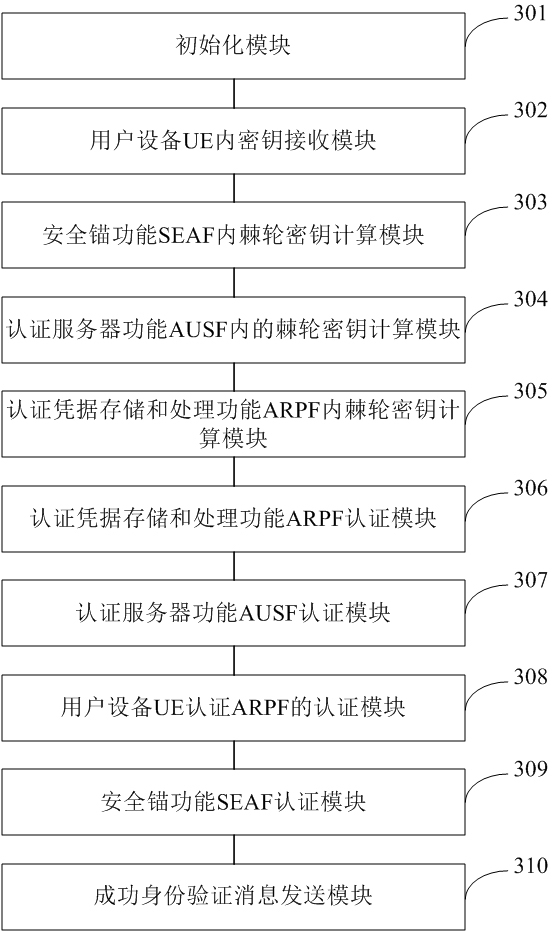
5G network authentication method and system based on DH ratchet algorithm
ActiveCN112399407AGuaranteed confidentialityThe transmission process is safe and reliableEncryption apparatus with shift registers/memoriesSecurity arrangementWeb authenticationAlgorithm
The invention relates to a 5G network authentication method and system based on a DH ratchet algorithm. The method comprises the steps that user equipment encrypts identity information through a ratchet wheel secret key and sends the identity information to a server for verification, and the confidentiality of the identity information is guaranteed; ratchet key pairs are generated for each entityin a 5G network, so that each entity encrypts transmission information through a ratchet key of the entity when transmitting information, information safety is guaranteed, mutual verification betweenthe entities is guaranteed by generating respective identity tokens of the entities, and counterfeit attacks are avoided. Through ratchet wheel stepping, each entity generates different ratchet wheelsecret keys in the session process, so that each session is encrypted by using different ratchet wheel secret keys, and the message transmission process is safer; the session key in 5G is generated through the ratchet wheel key instead of the shared key K, so that the security problem caused by leakage of the shared key K is solved.
Owner:北京电信易通信息技术股份有限公司
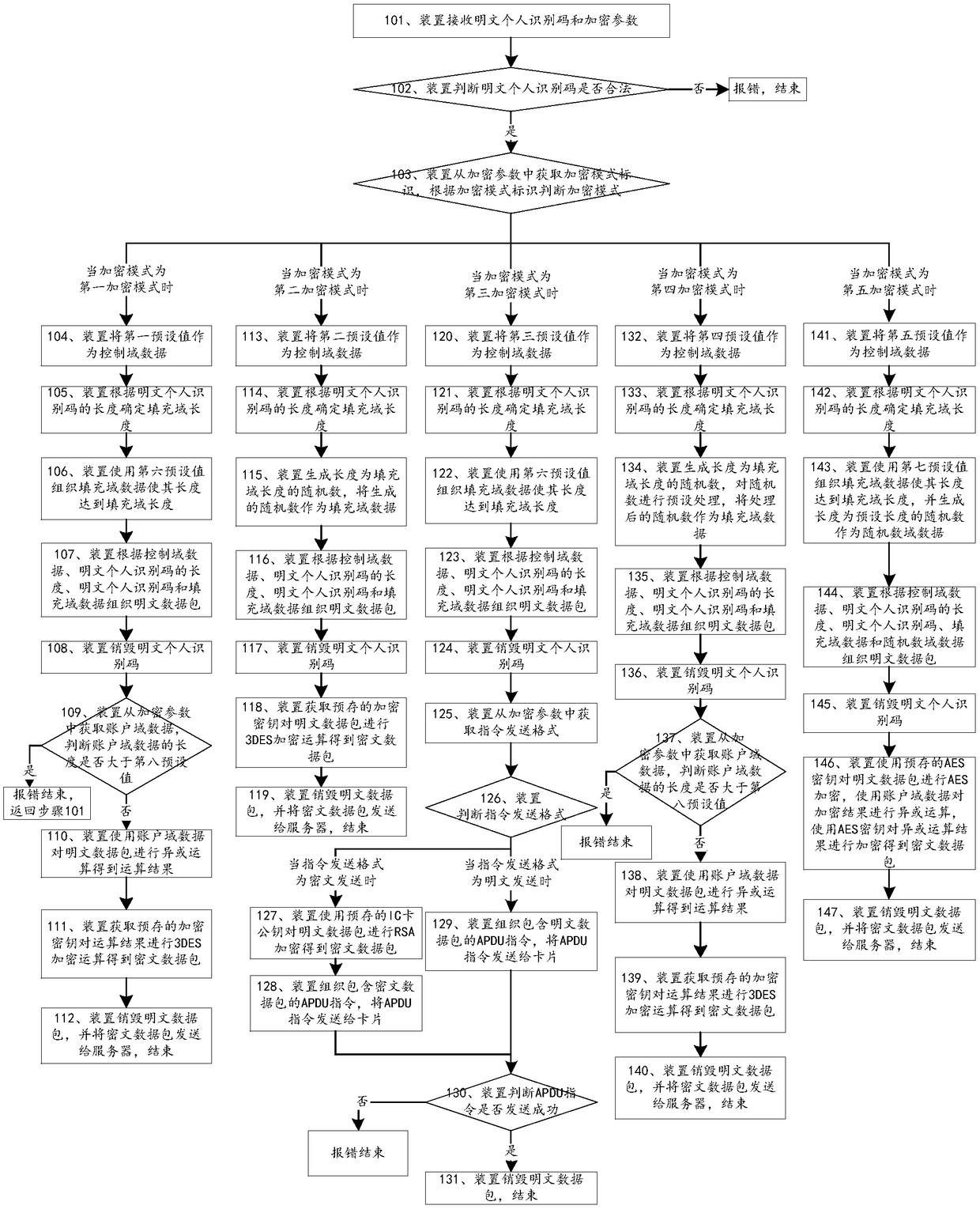
Method and device for protecting personal identification code
InactiveCN108718317APrevent leakageThe transmission process is safe and reliableUser identity/authority verificationPlaintextPersonal identification number
The invention relates to the field of information safety, in particular to a method and device for protecting a personal identification code. The method comprises the steps that the device receives the plaintext personal identification code and determines an encryption mode, when the encryption mode is a first encryption mode, a sixth preset value is used for organizing filling domain data, according to control domain data, the plaintext personal identification code and the filling domain data, a plaintext data package is organized, account domain data in an encryption parameter is used for conducting first preset processing on the plaintext data package, and a prestored encryption key is used for encrypting a processing result to obtain a plaintext data package; the plaintext data packageis sent to a server; when the encryption mode is a second encryption mode, a random number is generated and used as filling domain data, according to the control domain data, the plaintext personal identification code and the filling domain data, a plaintext data package is organized, and a prestored encryption key is used for encrypting the plaintext data package to obtain a ciphertext data package; the ciphertext data package is sent to the server, and accordingly the personal identification code is safer during transmission.
Owner:FEITIAN TECHNOLOGIES
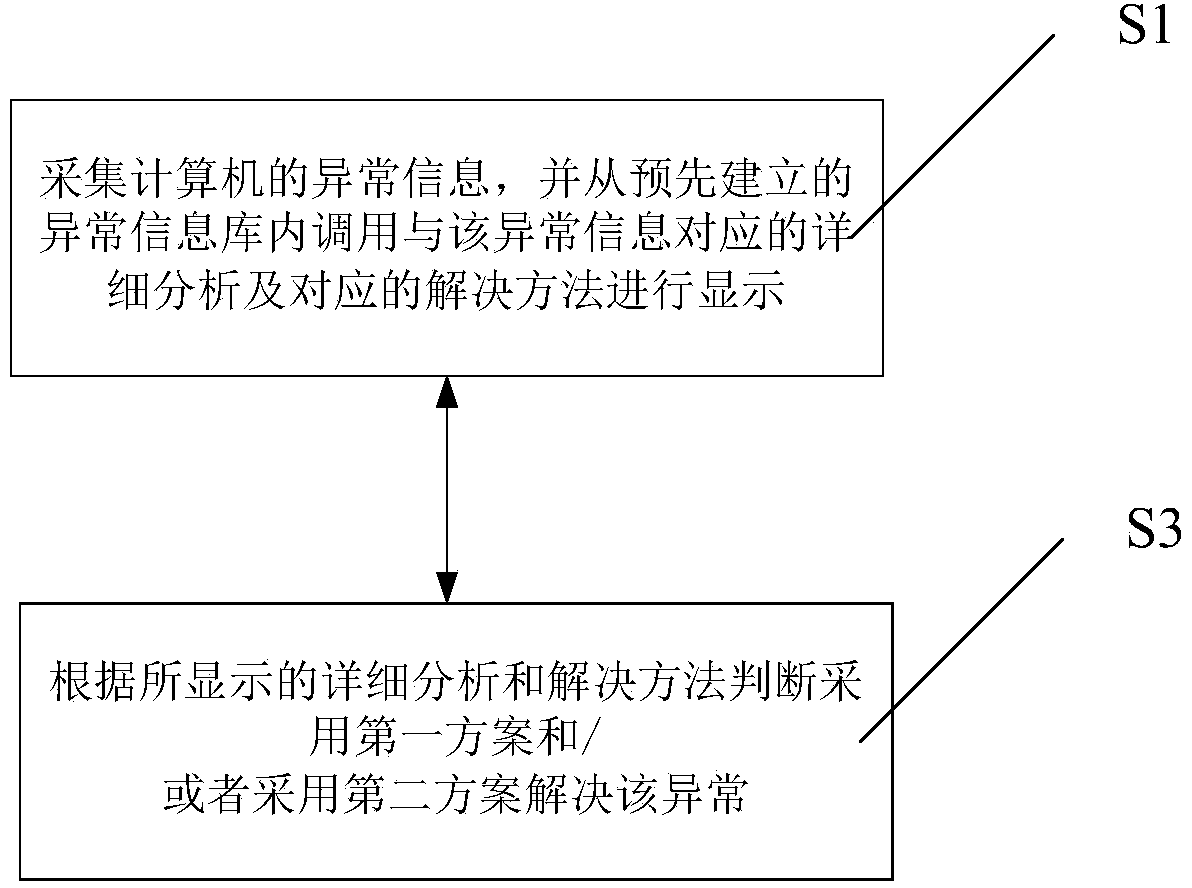
Method and system for maintaining computer
InactiveCN104268066AGood serviceReliable serviceHardware monitoringTransmissionInformation repositoryHuman power
The invention discloses a method and a system for maintaining a computer. The method for maintaining the computer includes the followings steps performed when an abnormal problem occurs in the computer, which are respectively: S1, collecting abnormal information of the computer, invoking detailed analysis and solutions, corresponding to the abnormal information, from an abnormal information database built in advance, and displaying the detailed analysis and the solutions; S2, judging whether a first scheme and / or a second scheme can be used to solve the abnormal problem according to the detailed analysis and the solutions, which are displayed. The first scheme includes: solving the abnormal problem through the computer according to the displayed solutions, and the second scheme includes: uploading the displayed detailed analysis to a manufacturer of the computer. According to the method for maintaining the computer, the different solutions for solving the abnormal problem are selected by collecting the abnormal information, and therefore a large amount of labor and material cost is saved, and quick, convenient and timely and reliable services are provided to a user.
Owner:STATE GRID CORP OF CHINA +1
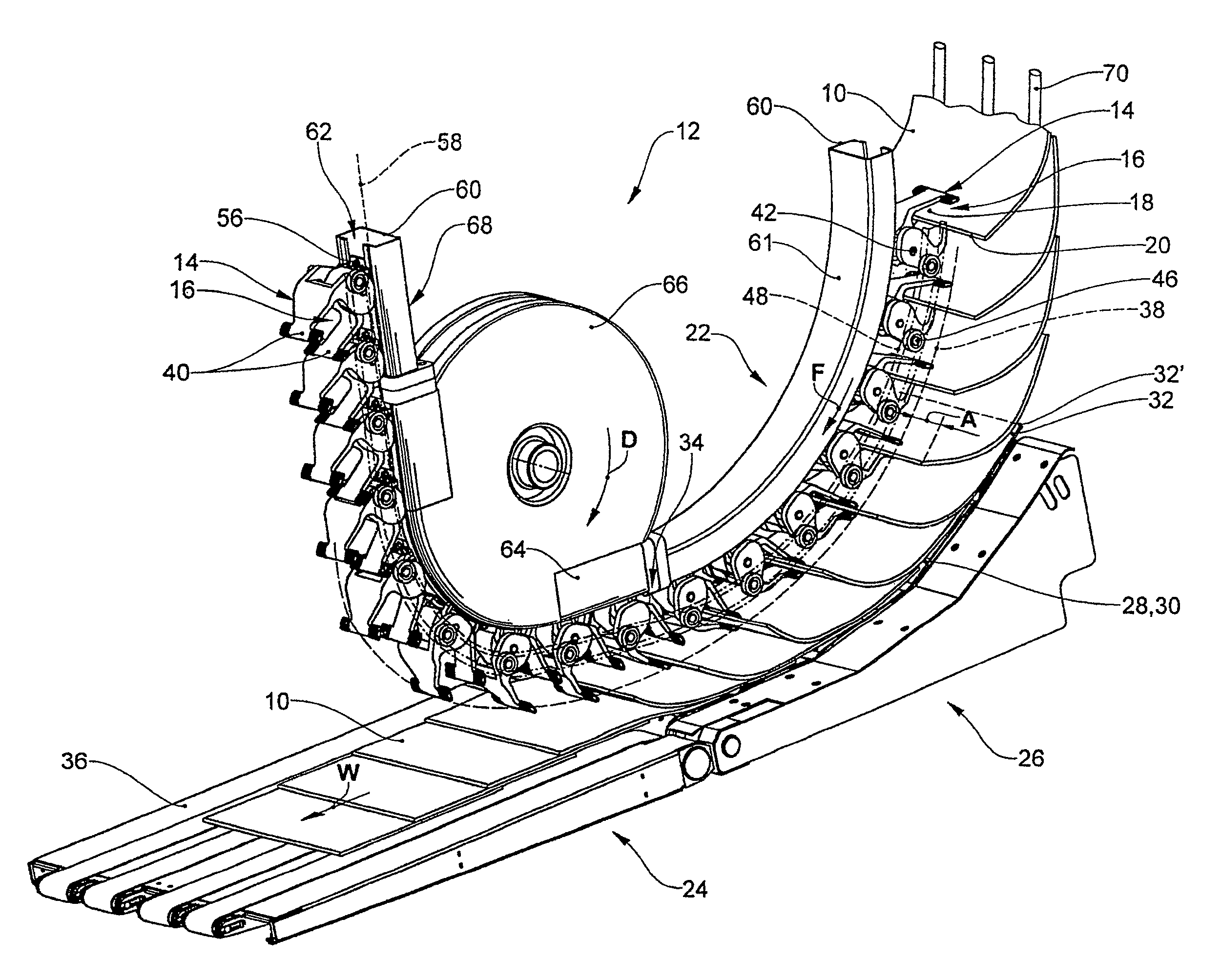
Apparatus and method for transporting flexible, planar products
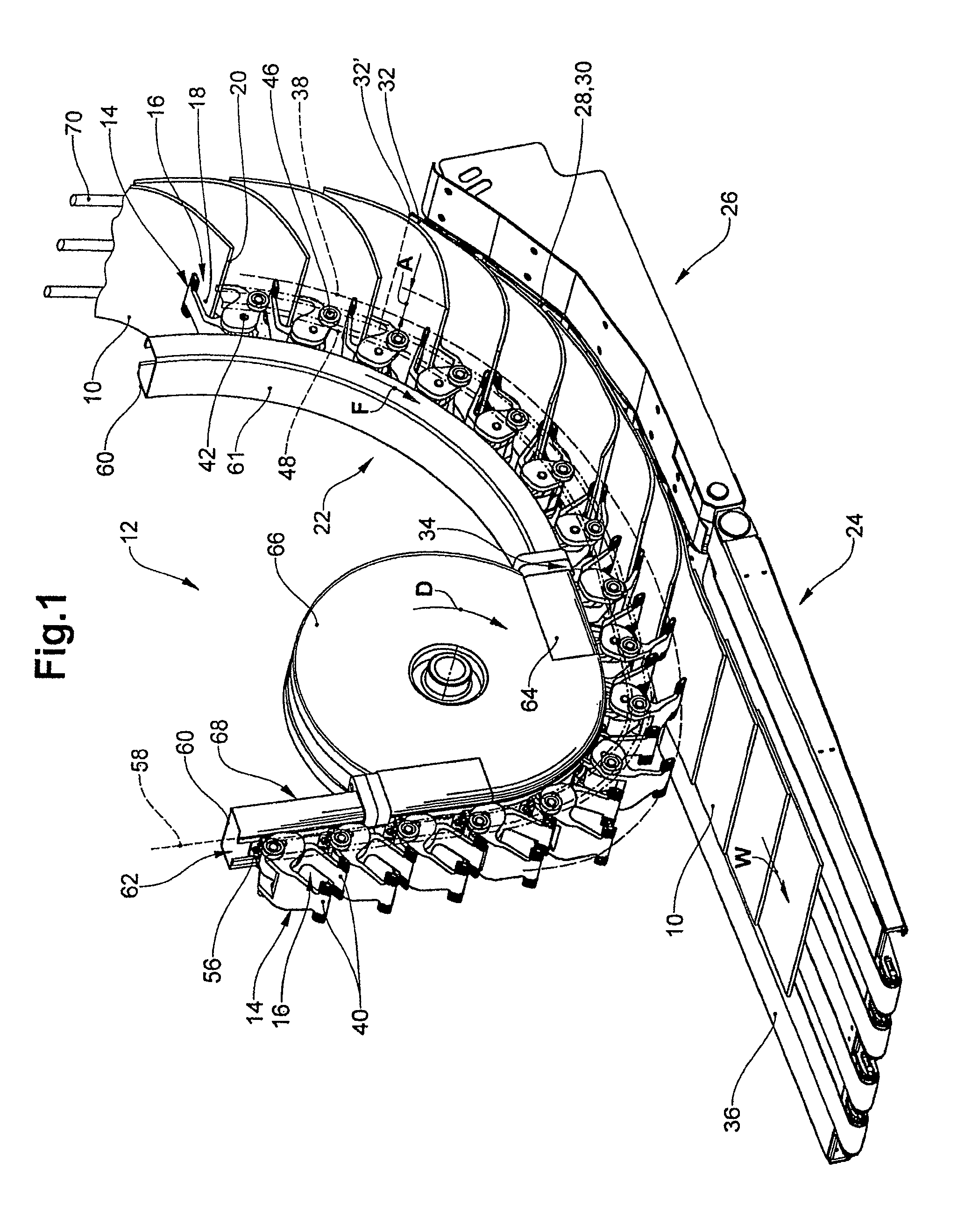
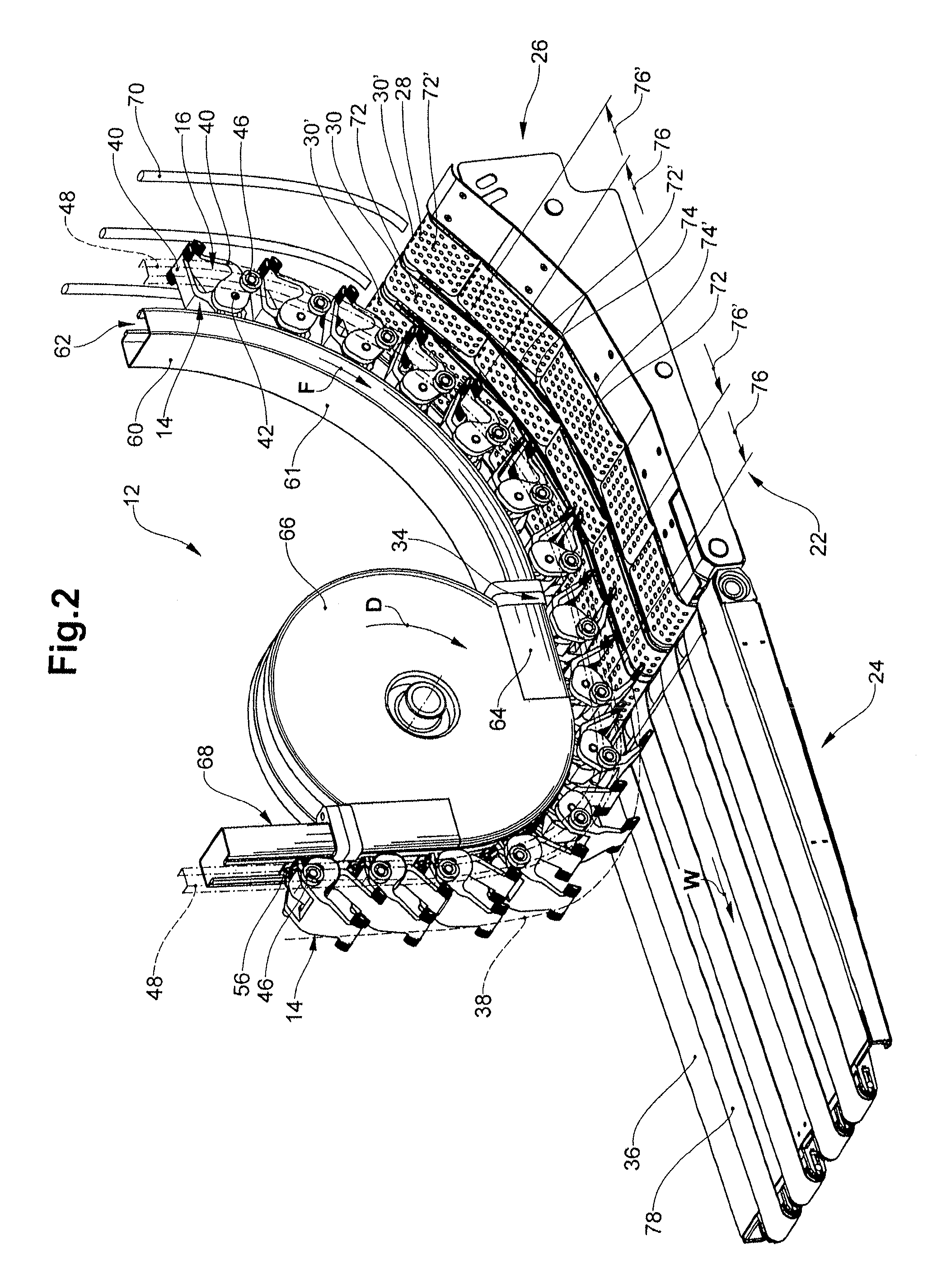
InactiveUS8550460B2The transmission process is safe and reliableFunction indicatorsArticle feedersEngineeringHigh velocity
Printed products (10) are conveyed to a transfer portion (22) by means of the grippers (14) of the gripper conveyor (12). The vacuum belt conveyor (26) suctions with its active strand (28) the respective end region (32) of the printed products (10), after which, close to the end of the (34) of the transfer portion (22), the grippers (14) respectively release the printed products (10). The motional path (38) of the gripper jaws (16) runs in the transfer portion (22) in the shape of an arc. The active strand (28) of the vacuum belt conveyor (26) runs in the transfer portion (22) at an approximately constant distance to the motional path (38). In the case of large processing capacities and correspondingly high velocities, a reliably secure, positionally stable transfer of the printed products (10) from the gripper conveyor (12) to the vacuum belt conveyor (26) is thereby ensured.
Owner:FERAG AG
Database cluster data migration method and system
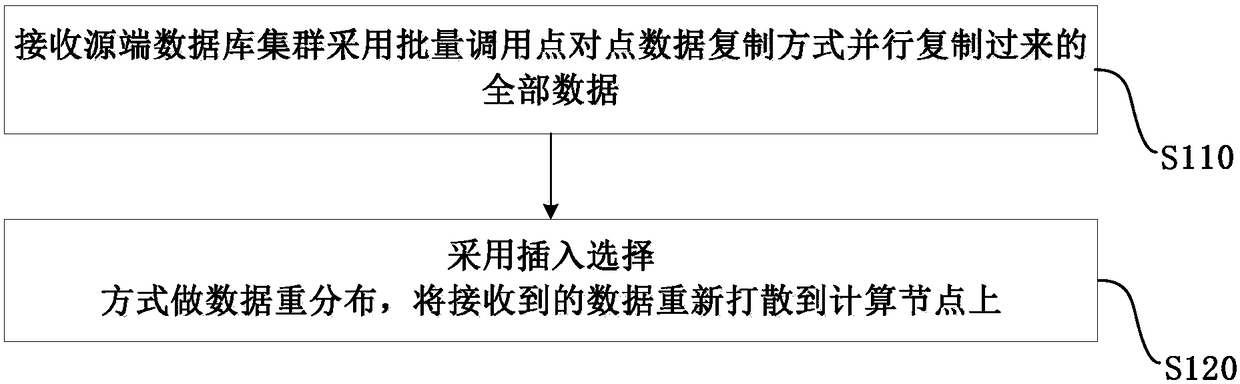
InactiveCN108268542AReduce resource consumptionThe transmission process is safe and reliableDatabase distribution/replicationSpecial data processing applicationsData migrationPoint data
The invention relates to a database cluster data migration method and system. The method comprises the steps of receiving all data copied in parallel in a batch call point-to-point data copy mode by asource end database cluster; and performing data redistribution in an insert select mode, and re-scattering the received data to computing nodes. According to the method and the system, a destinationend database cluster performs the data redistribution in the insert select mode directly in a database after the data is copied in parallel, so that the security and performance of data extraction, transmission and loading are greatly improved, the data migration time is greatly shortened, and the influence on businesses is reduced.
Owner:HANDAN BRANCH OF CHINA MOBILE GRP HEBEI COMPANYLIMITED +1
Sterile liquid cross-level transmission device and pharmaceutical workshop
PendingCN108910101AAvoid cross contaminationEasy to usePipeline systemsLiquid materialTransfer procedureEngineering
The invention provides a sterile liquid cross-level transmission device and a pharmaceutical workshop. The sterile liquid cross-level transmission device comprises a casing pipe, fastening chucks, valve bodies and a disposable liquid transferring bag. The casing pipe is used for being installed between walls of different clean areas. The fastening chucks are arranged at the two ends of the casingpipe. The valve bodies can be arranged on the fastening chucks. The end portions of the casing pipe can be sealed through the valve bodies. The disposable liquid transferring bag comprises a bag bodyand a liquid transmission pipe, one end of the liquid transmission pipe penetrates out of a bag opening of the bag body, the other end of the liquid transmission pipe penetrates out of the surface ofthe bag body, and the bag body can be arranged on the fastening chucks. The pharmaceutical workshop at least comprises a B-level clean area, a C-level clean area and an air return passageway, whereinthe sterile liquid cross-level transmission device is arranged between the B-level clean area and the C-level clean area. The sterile liquid cross-level transmission device has the beneficial effectsthat usage is simple, cost is low, and the sterile liquid transmission process is safe and reliable.
Owner:珠海西格膜生物技术有限公司
A distributed platform file and content distribution method and system
ActiveCN104580158BImprove transmission efficiencyThe transmission process is safe and reliableEncryption apparatus with shift registers/memoriesContent distributionData center
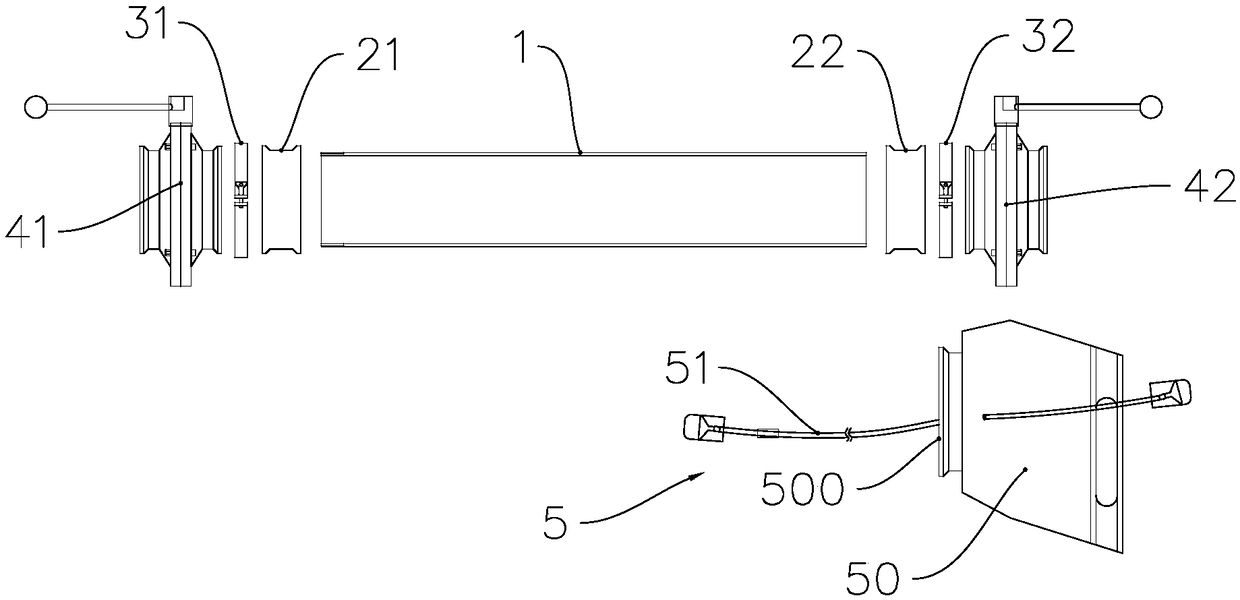
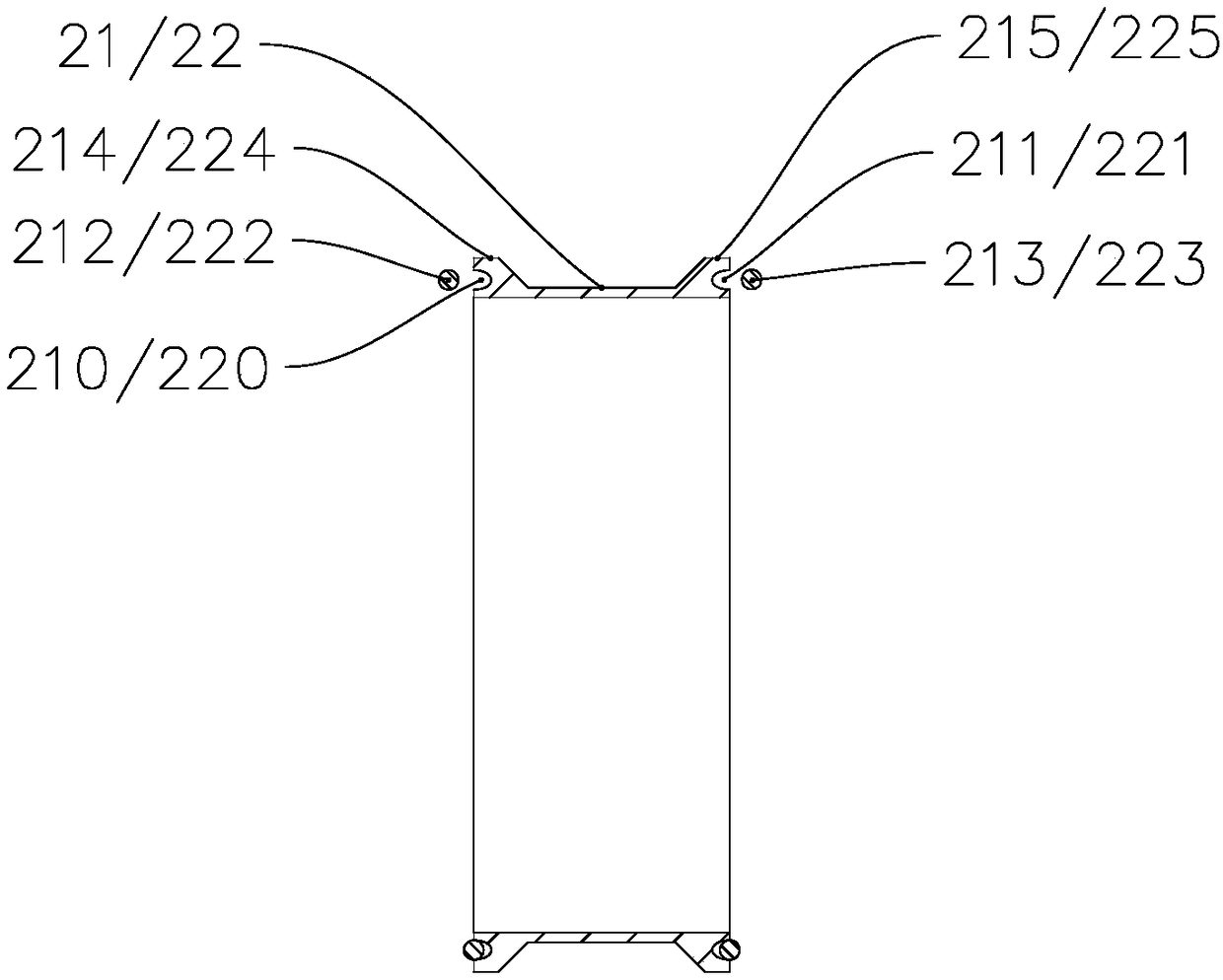
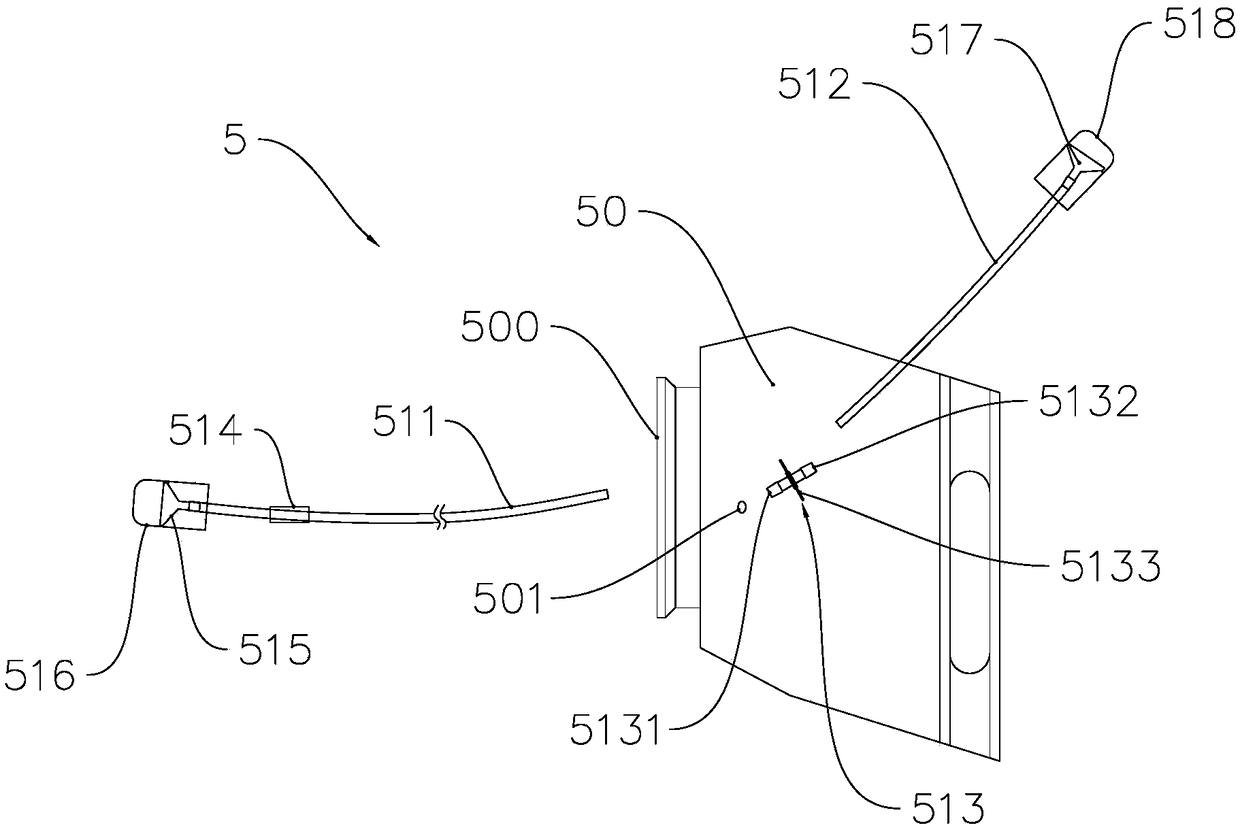
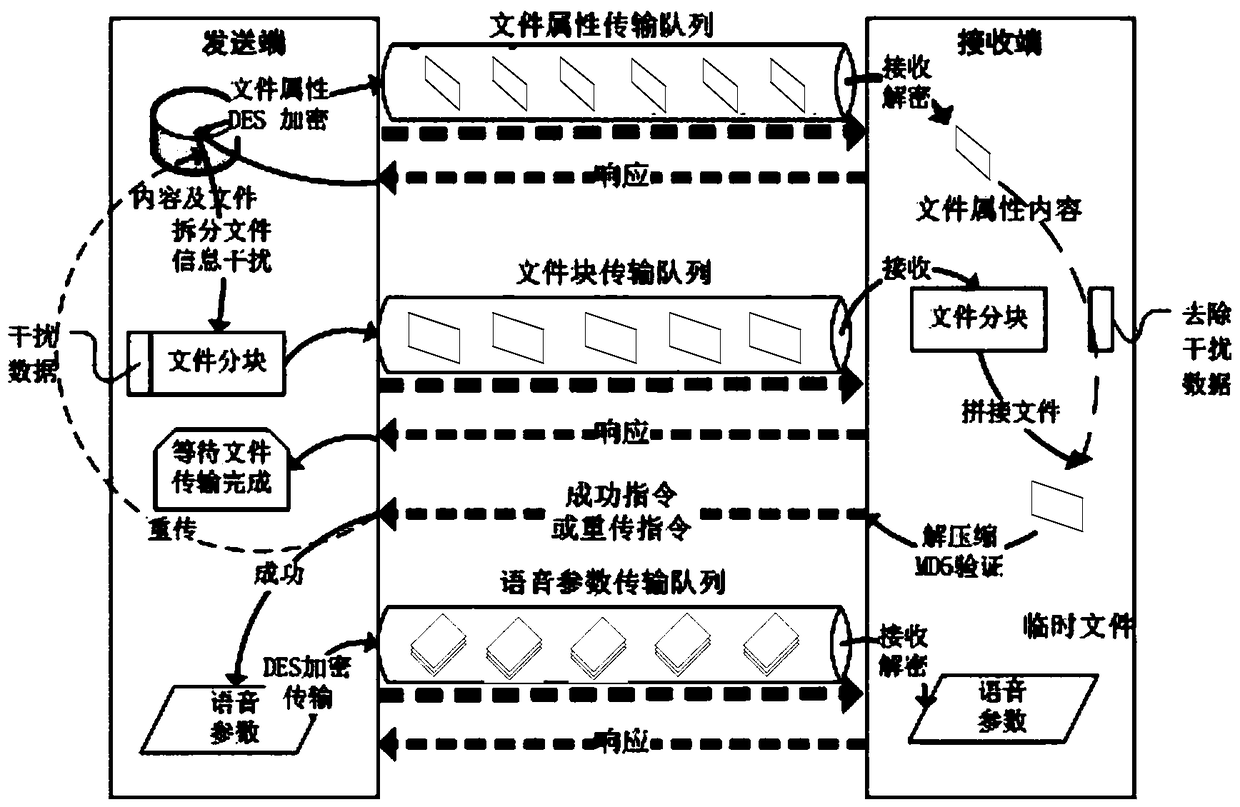
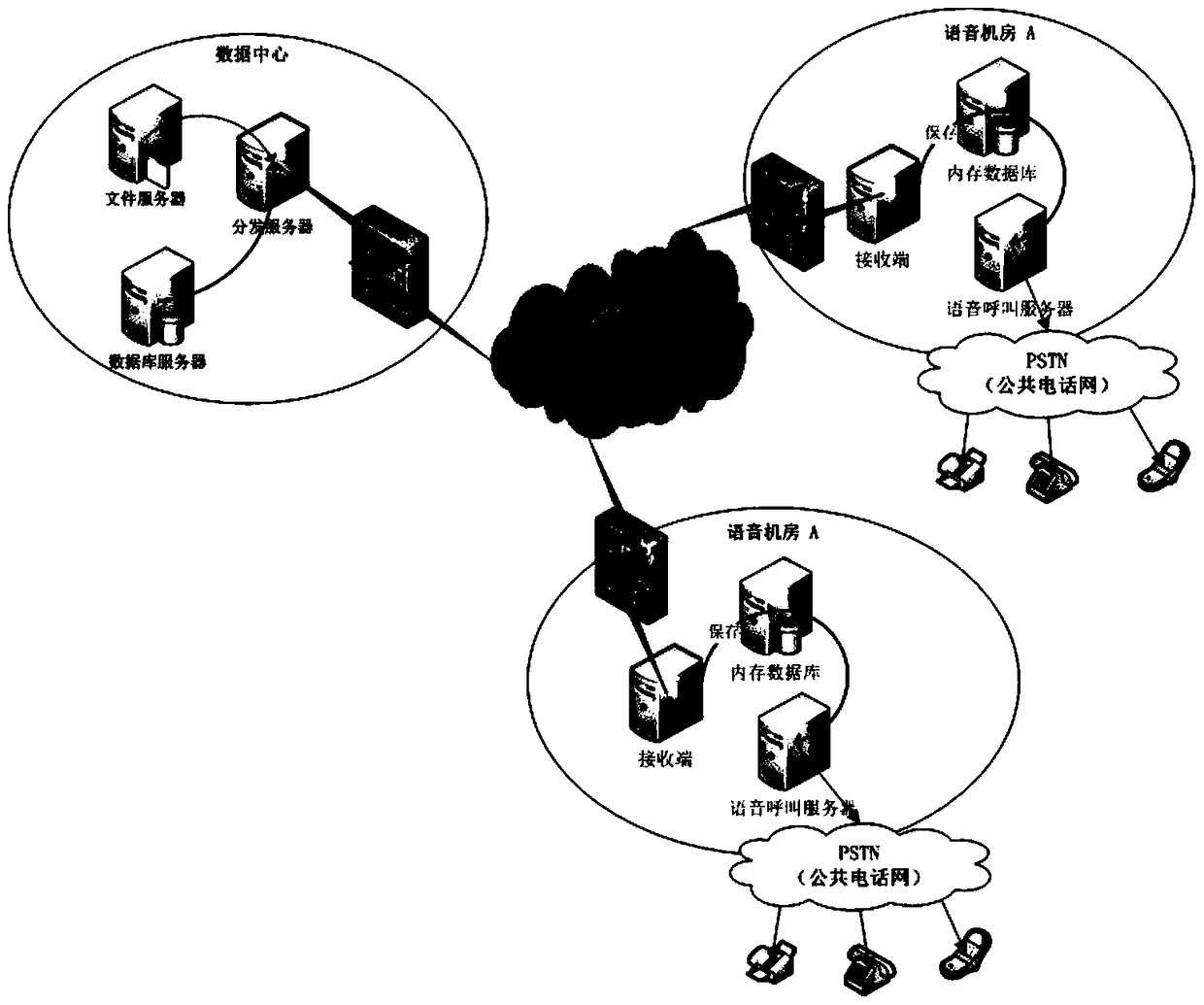
The invention discloses a method and system for distributing files and contents on a distributed platform. The method specifically includes: establishing a link connection between a sending end of a data center and each receiving end of a voice playback end, and establishing an independent transmission link for each connection link. Each transmission queue is allocated with multiple transmission threads; the sender points the voice task to the corresponding transmission link according to the type of the voice task; the sender divides the voice task file into file attribute content and file stream data, through The transmission links are sent to the receiving end respectively; after the receiving end verifies the validity of the file stream data with reference to the file attribute content, the sending end serializes the parameter content of the voice call and then encrypts and transmits it to the receiving end. The technical scheme of the invention realizes one-to-many distributed transmission, effectively improves the transmission efficiency, and makes the transmission process more secure.
Owner:V COM FUJIAN INFORMATION TECH CO LTD
Secure computer platform supporting software batch remote updating
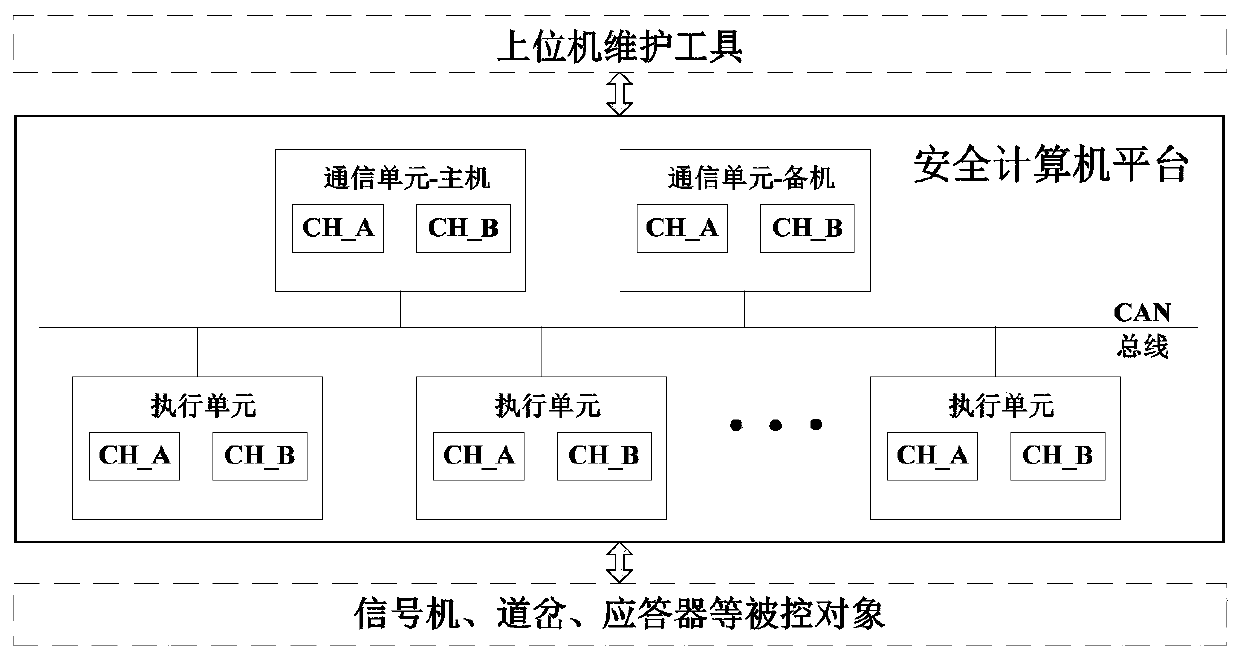
PendingCN111273919ADoes not affect safety outputThe transmission process is safe and reliableVersion controlSoftware deploymentCommunication unitEngineering
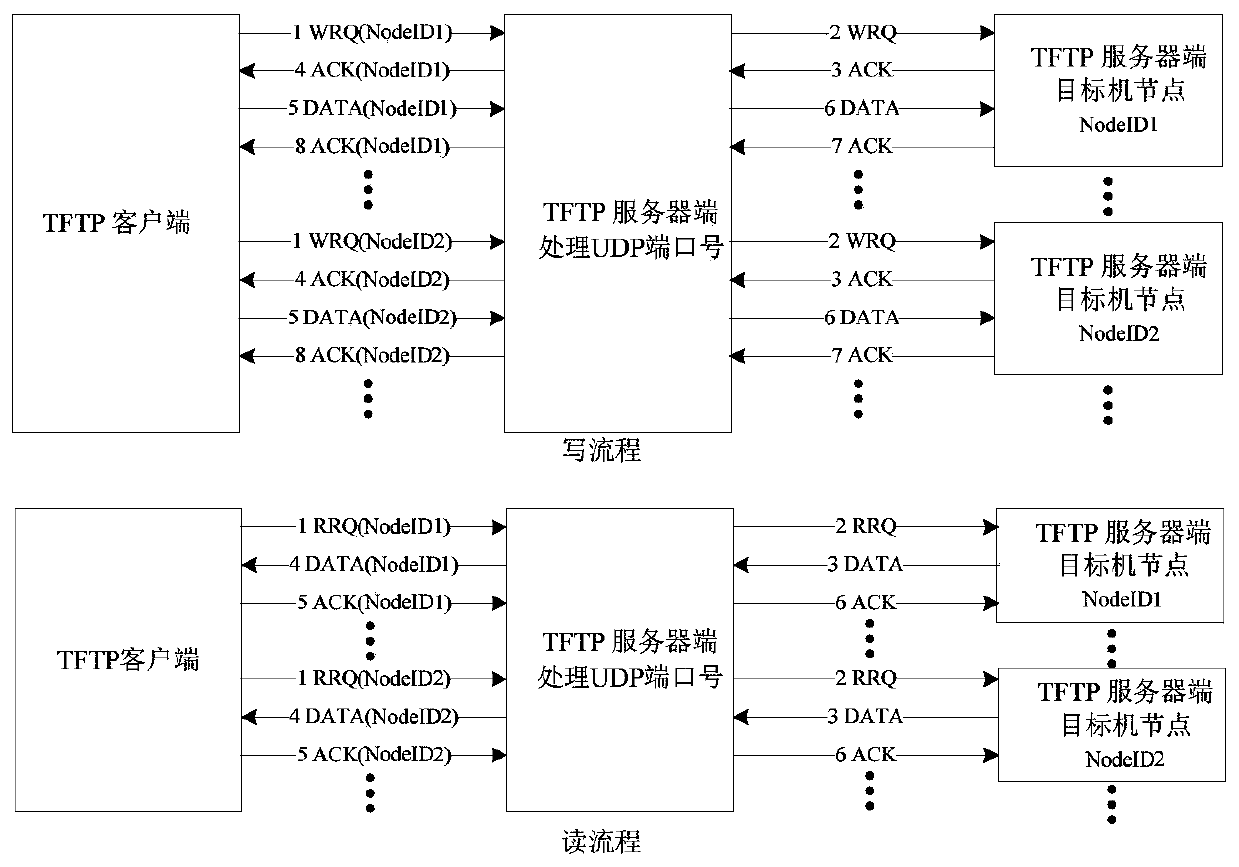
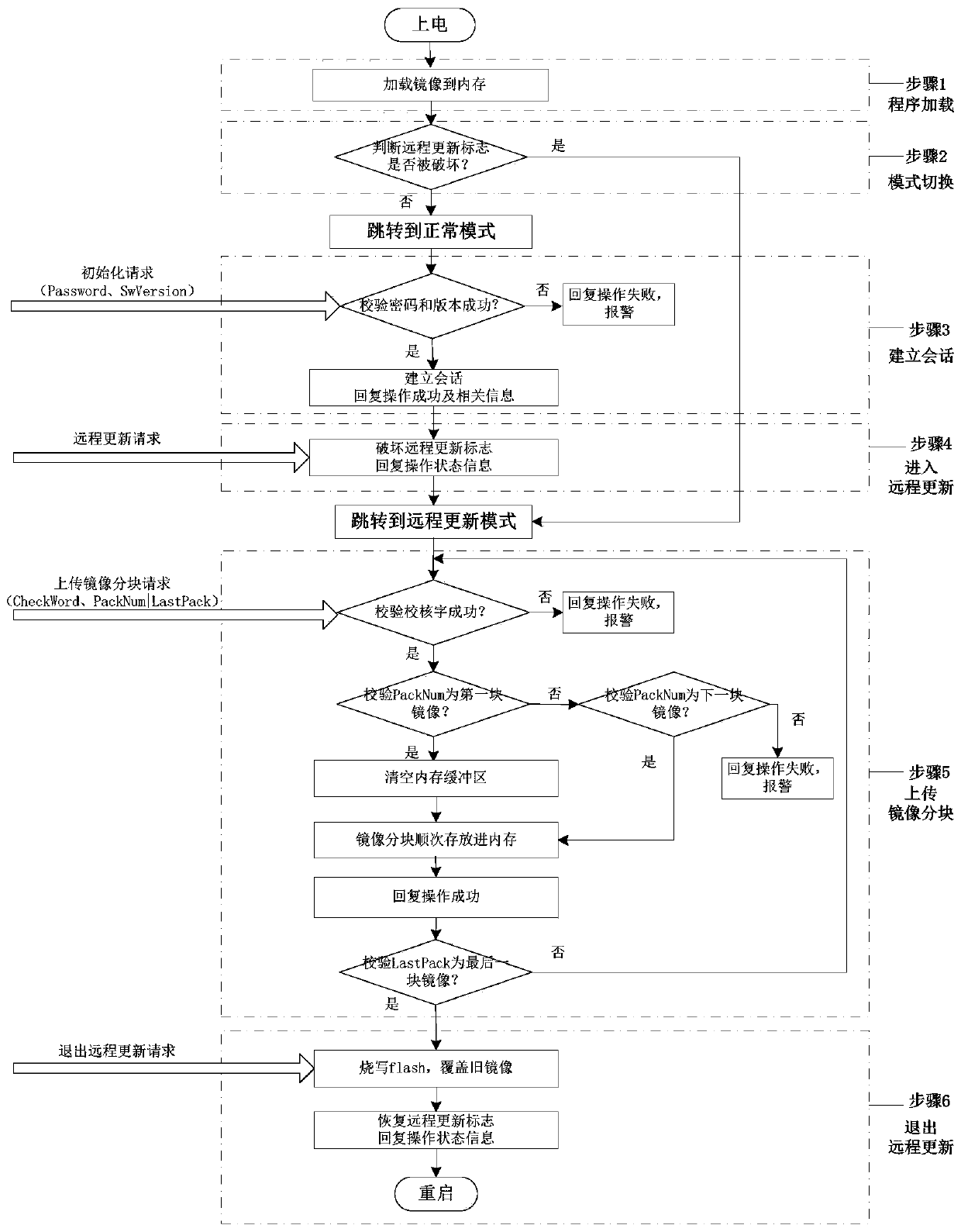
The invention relates to a safe computer platform supporting software batch remote updating. The platform is connected with an upper computer maintenance tool, the safety computer platform comprises acommunication unit and an execution unit, the upper computer maintenance tool is connected with the communication unit, the communication unit controls a controlled object through the execution unit,and the safety computer platform further comprises a communication forwarding part and an online updating part. The communication forwarding part is arranged in a communication unit of the security computer platform and is used for interacting information with an upper computer maintenance tool and forwarding the information to a corresponding target machine; the online updating part is arrangedin each target machine and used for batch parallel remote updating of the multiple target machines, and it is guaranteed that the updating process is safe and reliable. Compared with the prior art, the method has the advantages that the target machines can be remotely updated in parallel in batches, the updating process is safe and reliable, and reuploading and version rollback are supported.
Owner:CASCO SIGNAL
Method suitable for remotely connecting database in intranet environment
InactiveCN113645267AThe transmission process is safe and reliableSolve the problem of being unable to connect to the database remotelyDatabase queryingTransmissionData operationsEngineering
The invention discloses a method suitable for remotely connecting a database in an intranet environment. The method comprises the following steps: 1) establishing connection between a client and a server; 2) sending a request; 3) querying data according to the request; 4) the server responding; 5) the client obtaining data; and 6) operating data. The invention belongs to the technical field of network transmission, particularly relates to a method suitable for remotely connecting a database in an intranet environment, solves the problem that a MySQL database cannot be remotely connected in the intranet environment, and is simple in protocol, simple and convenient in code implementation, high in communication speed, allowed to transmit various data and capable of saving transmission time.
Owner:济南朗宁电力科技有限公司
A blockchain-based multimodal transport data exchange system and method
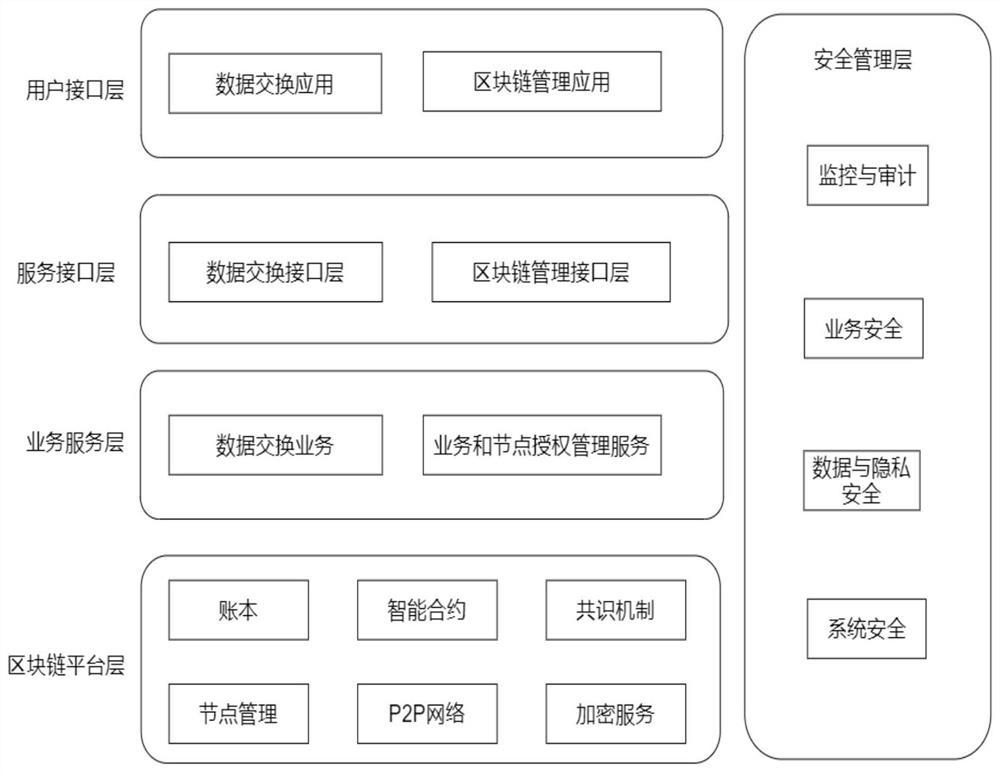
ActiveCN113556393BImprove synchronization efficiencyReduce accessUser identity/authority verificationData synchronizationEngineering
The invention discloses a blockchain-based multimodal transport data exchange system and method, belonging to the technical field of multimodal transport data exchange, comprising: a user interface layer; a service interface layer; a business service layer; and a blockchain platform layer. The blockchain platform layer is connected to the service interface layer and the business service layer, and is used to provide data storage, processing, and encryption for the business service layer, and to enable users to share data; security management Layer; the blockchain-based multimodal transport data exchange system and method utilizes the distributed ledger in the blockchain platform layer to achieve data synchronization between different data exchange subjects, and when a node fails, the exchange data cannot be received When the fault occurs, other nodes on the blockchain work normally; when the faulty node recovers, the data will be automatically synchronized to the local ledger of the node, so that there is no need to consider the issue of data reissue and the amount of reissue.
Owner:JIANGSU TRANS UNION INFORMATION
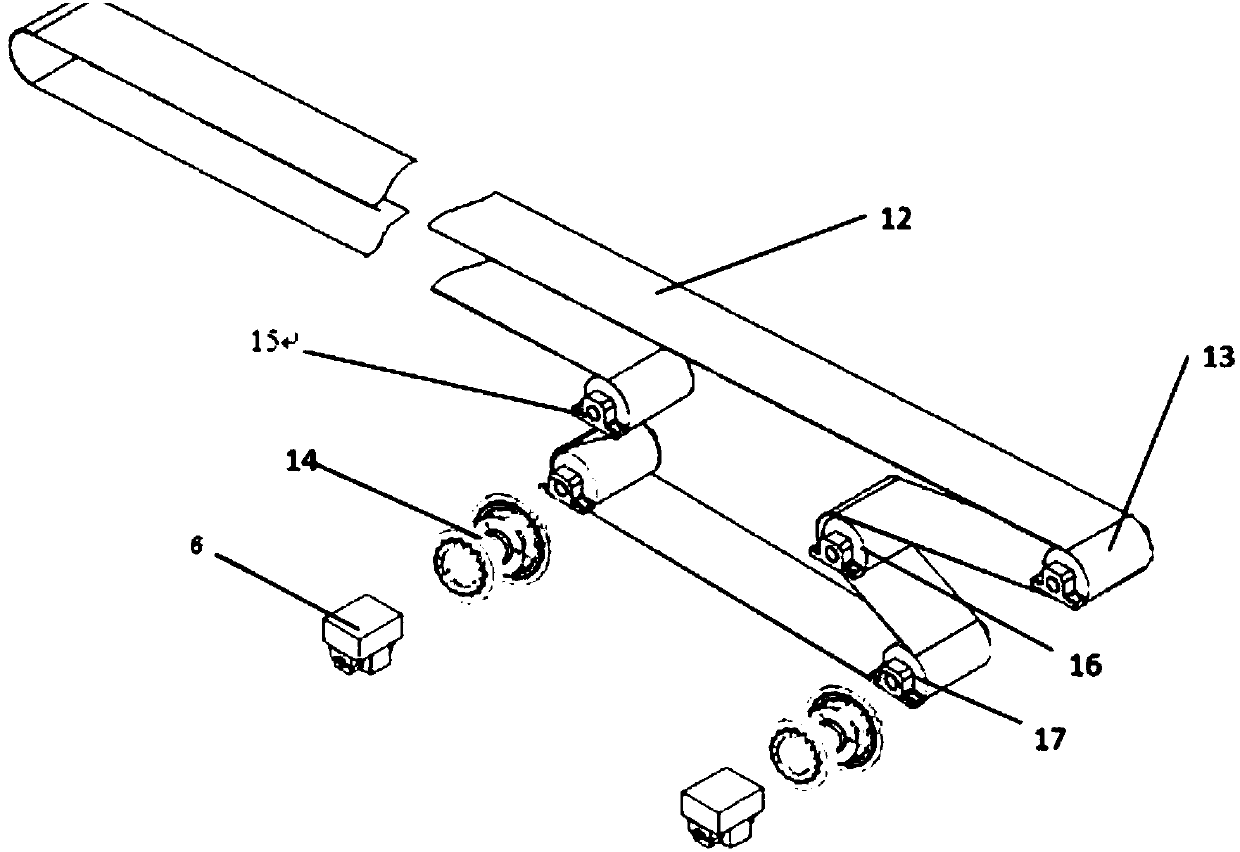
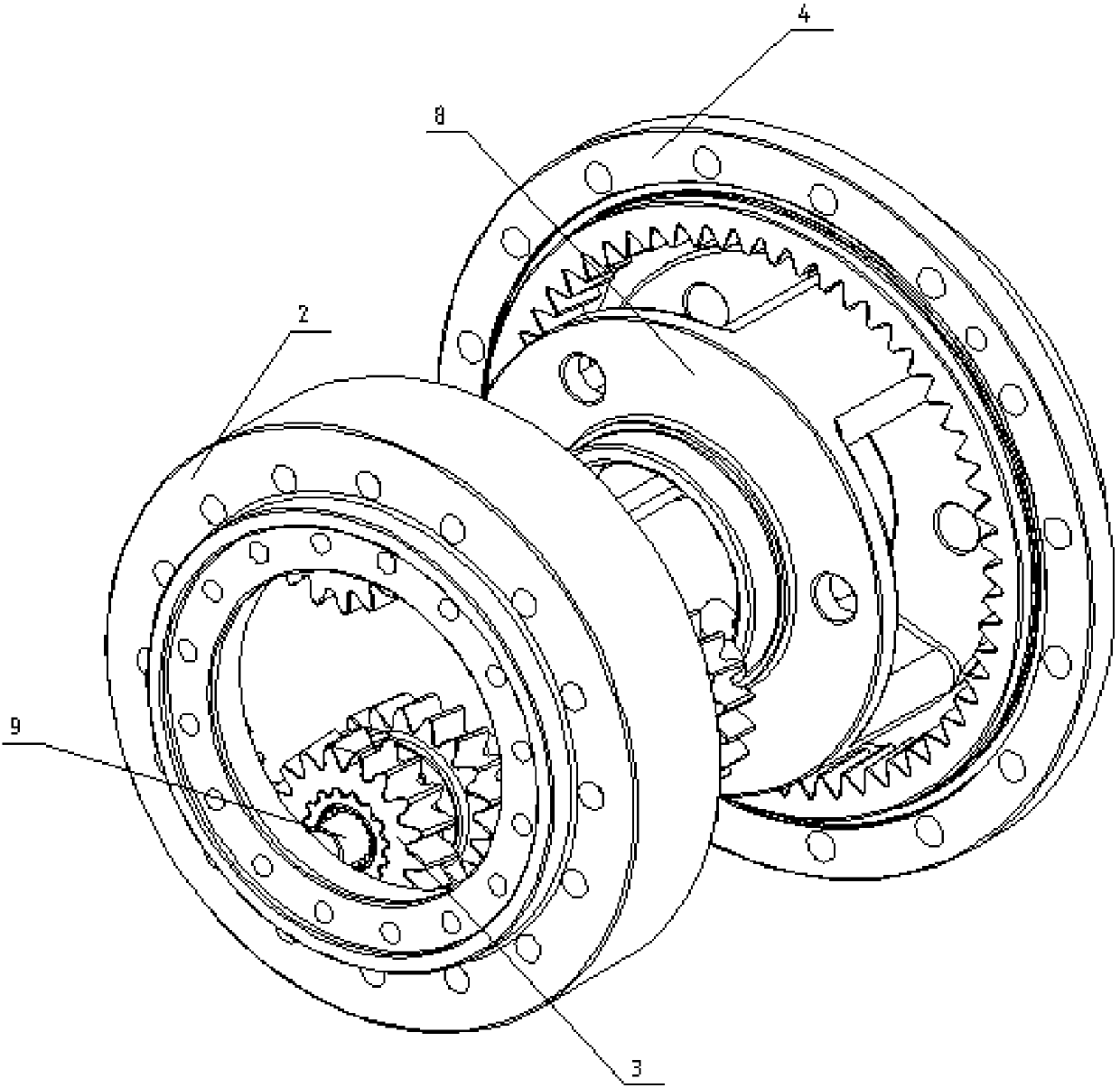
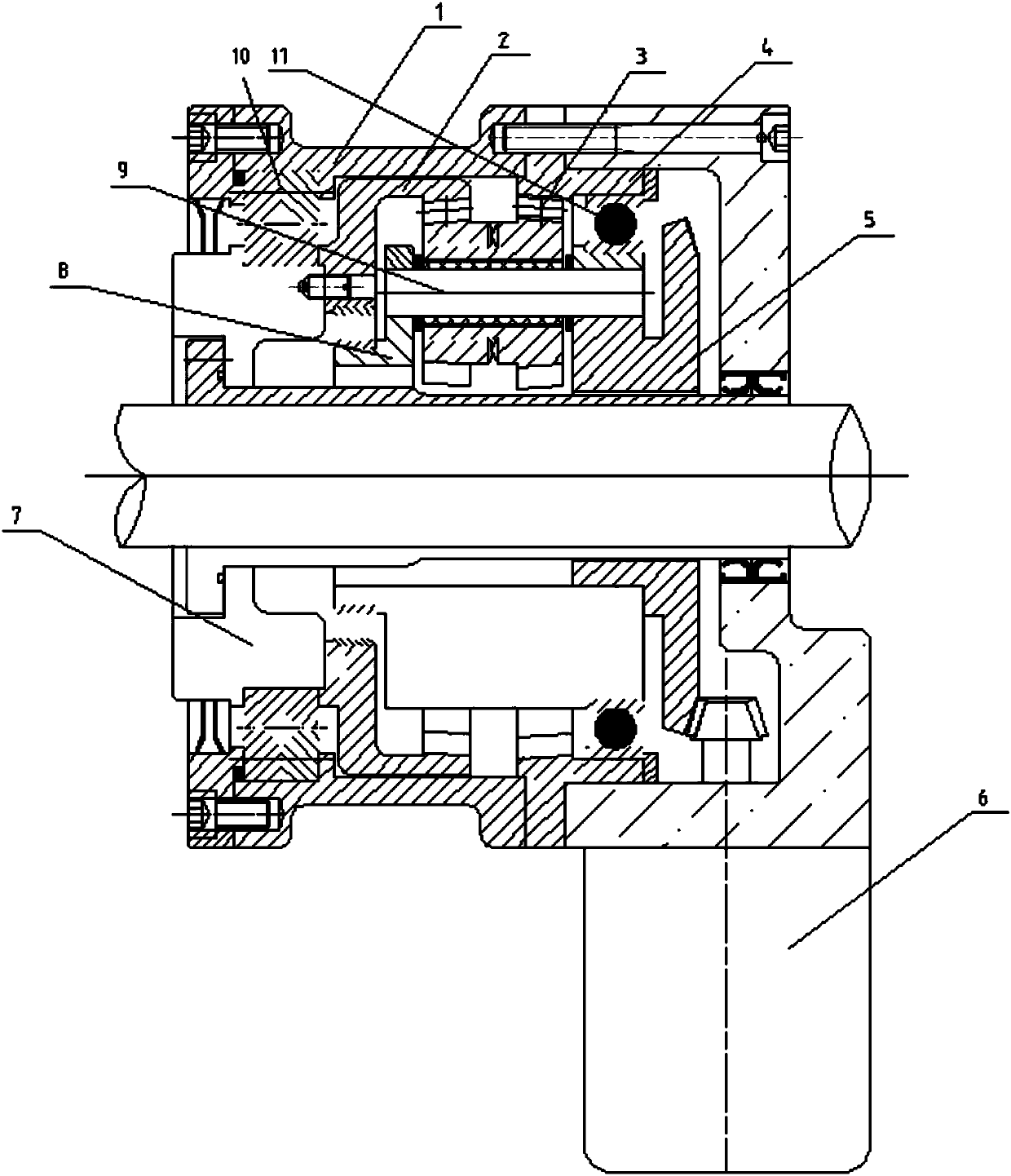
Bulk conveyor adopting variable-thickness planetary gearbox
PendingCN108033211AReliable speed controlImprove power densityConveyorsGearingVariable thicknessDrive motor
The invention relates to the field of bulk conveying, in particular to a bulk conveyor adopting a variable-thickness planetary gearbox. The bulk conveyor comprises a conveyor belt, a plurality of drive rollers, the variable-thickness planetary gearbox and a drive motor, wherein the conveyor belt is wound and distributed on the drive rollers; one end of each drive roller is equipped with a rotary drive device; the drive rollers are connected with the variable-thickness planetary gearbox through the rotary drive devices; the input end of the variable-thickness planetary gearbox is connected witha drive motor; the variable-thickness planetary gearbox comprises a first-stage transmission chain, a planet carrier, a planetary pin, double variable-thickness planetary gears, a first variable-thickness gear ring, a second variable-thickness gear ring, a housing assembly and an output shaft, wherein the first variable-thickness gear ring is connected with the output shaft as an output end; andthe output shaft is connected with the rotary drive devices on the drive rollers. The bulk conveyor adopts a non-solar-wheel drive mode, guarantees a small gap and a small return difference of outputand optimizes the structure; and conveying speed of the conveyor is more stable.
Owner:BEVELOID ROBOT JOINT TECHSHANGHAI CO LTD
Distributed micro-power system
InactiveCN108736473AThe transmission process is safe and reliableEasy to analyze and calculateSingle network parallel feeding arrangementsSystems intergating technologiesMicrocontrollerComputer module
The invention discloses a distributed micro-power system. The distributed micro-power system comprises a receiving module, a digital module, a monitoring module, a closing module, a power electronic inversion module, an energy storage module, a microcontroller, a rectification module, a display module, a recording module and a comprehensive module; the receiving module is connected with the digital module; the digital module is connected with the monitoring module; the digital module is connected with the closing module; the monitoring module is connected with the display module; the closing module is connected with the power electronic inversion module; the power electronic inversion module is connected with the energy storage module; the energy storage module is connected with the microcontroller; the microcontroller is connected with the rectification module; the microcontroller is connected with the display module; the display module is connected with the recording module; and therecording module is connected with the comprehensive module. The distributed micro-power system is convenient to use, and the received signals are monitored in real time, so that professional workerscan carry out analysis and research conveniently.
Owner:浙江博通信息技术有限公司
Safety control method, device and computer equipment
ActiveCN109257374BRealize legitimacy verificationEnsure safetyBus networksCommunications securityEngineering
The present invention proposes a security control method, device and computer equipment, wherein the method includes: acquiring a key generated according to the ECU identity information of the vehicle control unit ECU to be authenticated and the gateway identity information of the vehicle gateway, and generating the corresponding ECU identity information The verification information is encrypted with the key to generate the first verification information, and the second verification information generated based on the first verification information sent by the ECU is received, and the second verification information is decrypted with the key to obtain the carried verification information. The verification information and ECU identity information, by judging whether the verification information obtained by decryption has a corresponding relationship with the ECU identity information, the security verification of the ECU is performed. In each verification, the gateway uses different verification information for each ECU to perform security verification. At the same time, when the verification information is transmitted, it is encrypted with different keys, which makes the transmission process more secure, realizes the security verification of the ECU, and ensures the communication security.
Owner:APOLLO INTELLIGENT CONNECTIVITY (BEIJING) TECH CO LTD
A distribution automation information encryption method based on quantum hardening
ActiveCN113037486BMature and reliable technologyThe transmission process is safe and reliableKey distribution for secure communicationMaster stationEncryption decryption
The invention discloses a distribution automation information encryption method based on quantum reinforcement, which includes: presetting a key pool A at the main station and all terminals, separately setting a key pool B at the main station, and the key pool A pre-stores encryption key, the key pool B is used to pre-store or store newly added keys, and the keys are all quantum keys converted after quantum random numbers are generated by the quantum random number generator; key package distribution is carried out: terminals and The master station communicates and jointly selects the key a from the key pool A, and the master station extracts part of the key from the key pool B to form a key package, encrypts the key package with the key a and sends it to all terminals; the terminal Use the key a to decrypt the received key bag, and extract the key in the key bag for secondary encryption and decryption of the State Grid encrypted message, where the key in the key bag is marked after use; when the terminal After all the keys of the key package are marked, select a key a from the key pool A again, and distribute the key package again.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER CO LTD HANGZHOU POWER SUPPLY CO
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com