Authentication method and system of verification code security reinforcement
An authentication method and authentication system technology, applied in transmission systems, messages/mailboxes/announcements, electrical components, etc., can solve the problems of fraudulent use of SMS verification codes, damage to legitimate user rights and interests, etc., to enhance security, avoid batch cracking, The effect of high user experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
[0100] Embodiment two of the method of the present invention, as figure 2 shown, including steps:
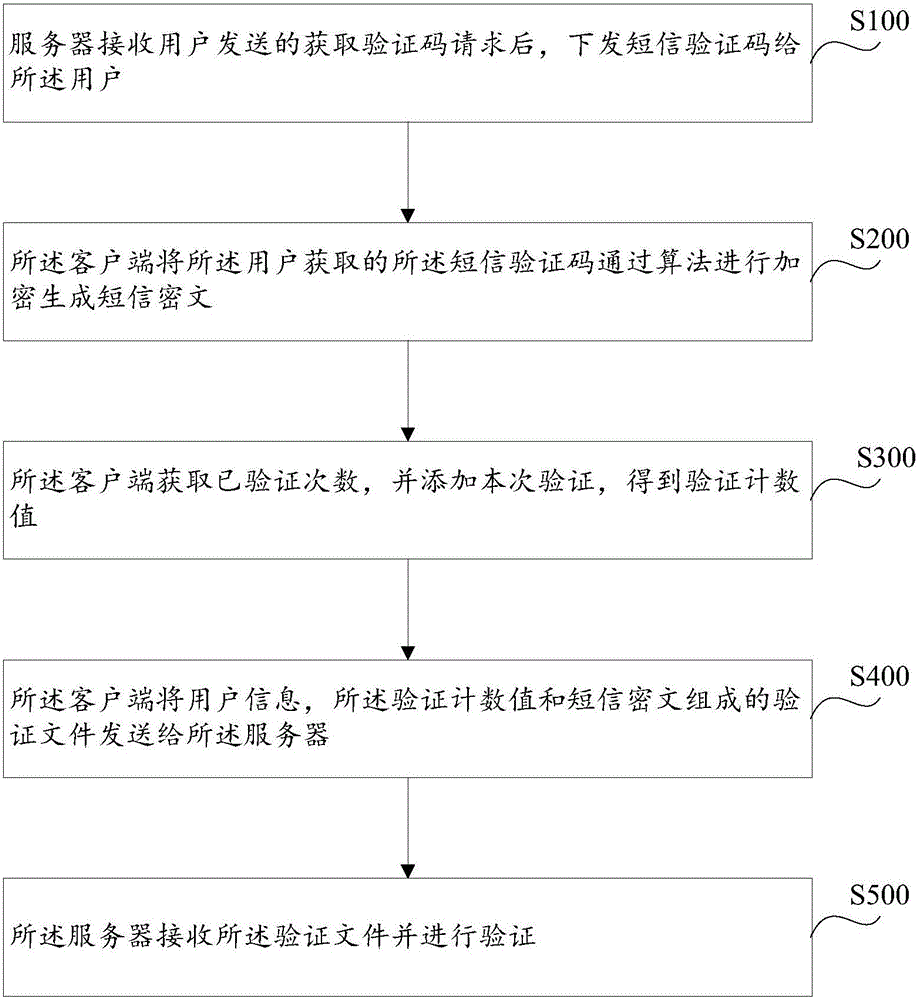
[0101] After receiving the verification code request sent by the user, the S100 server sends a text message verification code to the user;
[0102] S200, the client encrypts the short message verification code obtained by the user through an algorithm to generate a short message ciphertext;
[0103] S300, the client obtains the number of times of verification, and adds this verification to obtain the verification count value;
[0104] S350, the client encrypts the verification count value to generate a count ciphertext;
[0105] S410, the client sends a verification file consisting of user information, client identification information, the counting ciphertext, and SMS ciphertext to the server;
[0106] S500 The server receives the verification file and performs verification.
[0107] This embodiment adopts the method of encrypting the verification code and the number of time...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com