Safety responsibility identifying method of video content for integration of three networks
A video content and three-network integration technology, applied in selective content distribution, image communication, electrical components, etc., can solve the problems that the responsible party cannot be traced, the responsible party cannot be confirmed, and the triple-network integration environment has not been found.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
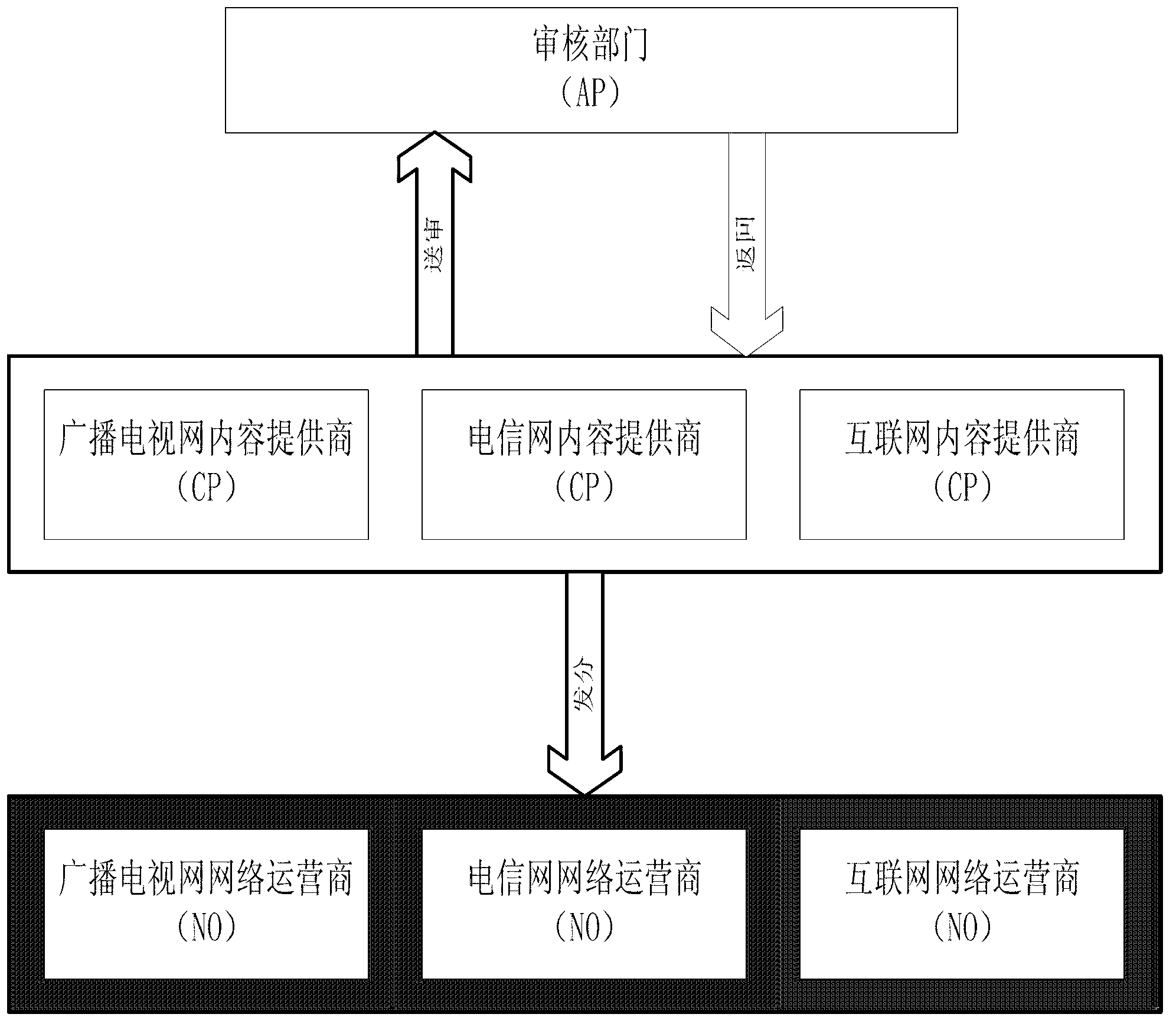
[0117] In the embodiment of the present invention, three nodes are deployed, which are respectively a content provider (Content Provider, referred to as CP), an audit department (Audit Provider, referred to as AP) and a network operator (Network Operator, referred to as NO). A video content security responsibility identification system is deployed on each node. In this embodiment, the computer is "DELL computer, Intel(R) Core(TM) i5-2400CPU3.10GHz3.10GHz, 4.00GB memory, 1T hard disk". Adopt VC++ programming to realize.
[0118] The specific implementation plan is:
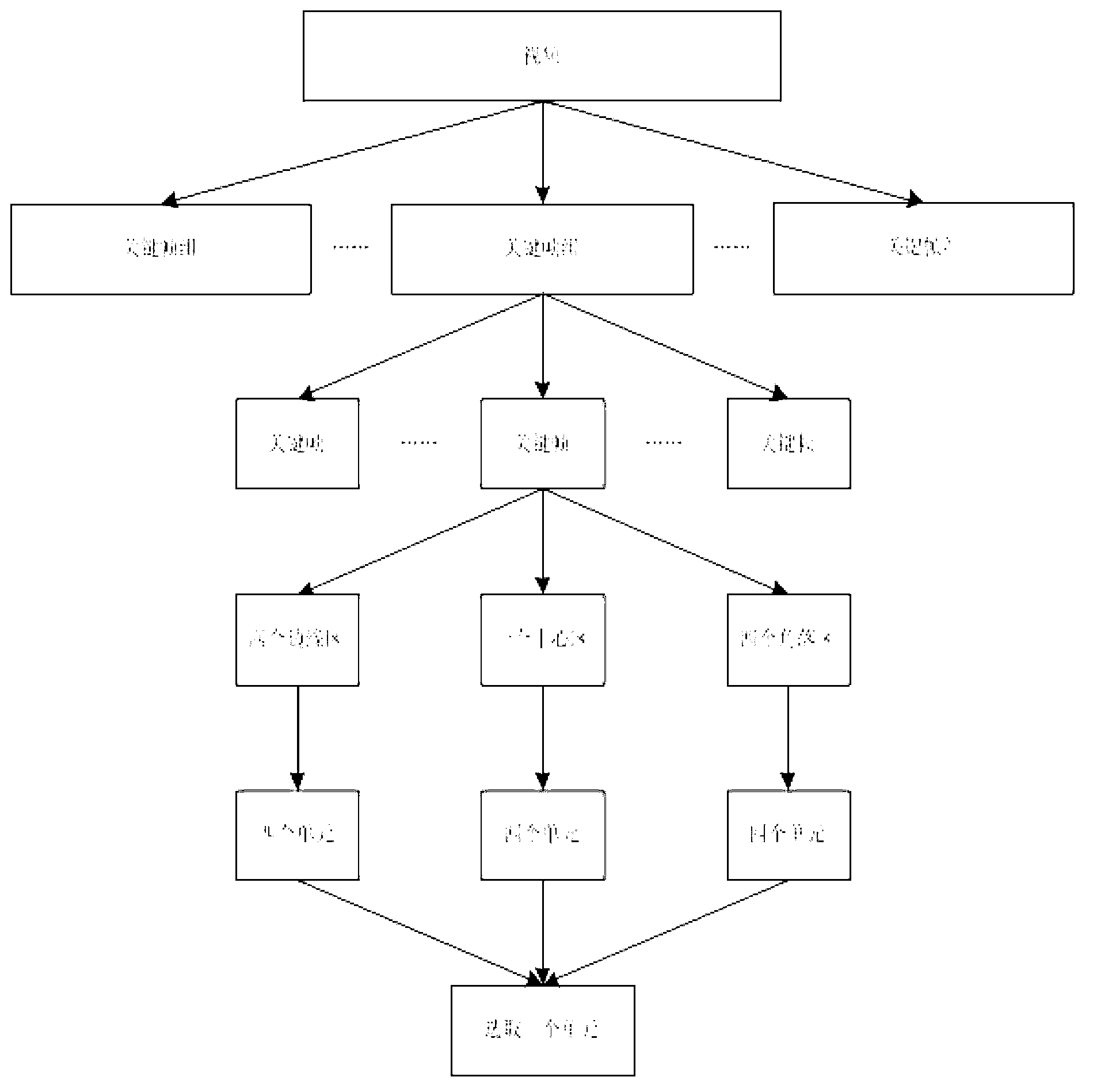
[0119] The whole system is mainly divided into two major processes, namely, the review and distribution process of video content and the responsibility determination process in case of disputes. The review and distribution process is that the CP in the three networks uploads the produced video content to a unified AP for review. After the review is passed, the AP returns the content to the CP, and the CP then dis...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com