Method for protecting safety of account number cipher
A password security and account number technology, applied in the field of account password security protection, can solve problems such as low reliability, high cost of use, easy loss, etc., and achieve the effect of high reliability, low cost, and enhanced authentication strength
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
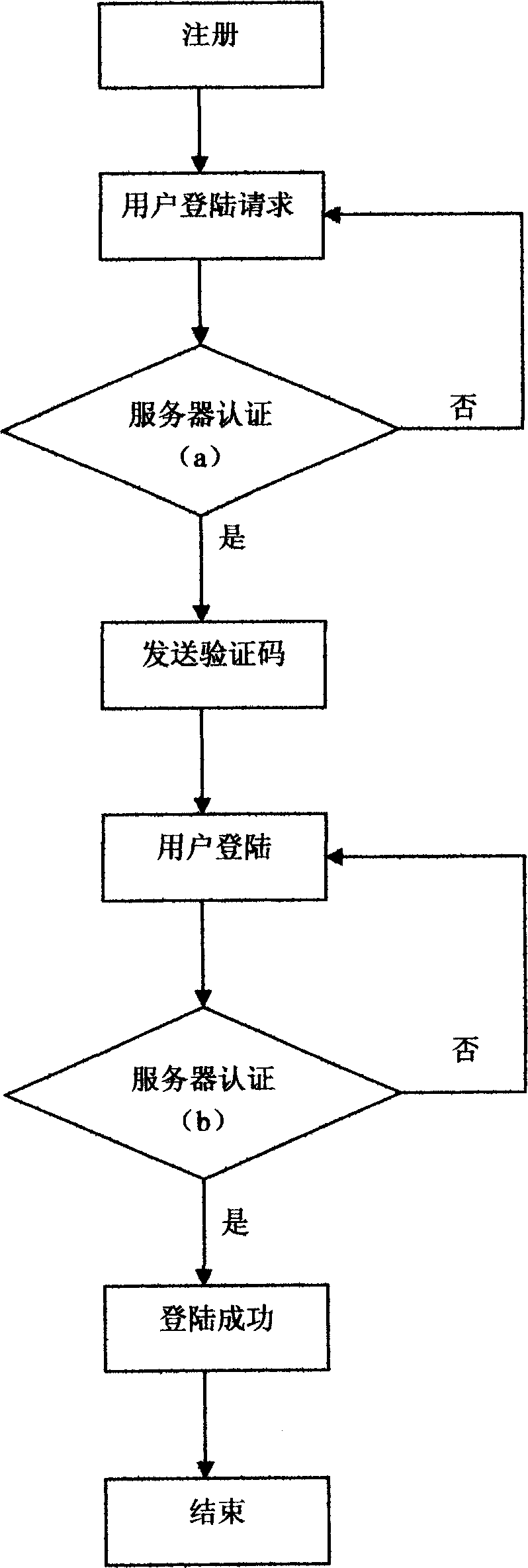
[0017] The following describes the operation process of the method of the present invention in conjunction with the accompanying drawings:
[0018] The user needs to submit the user's account name and mobile phone number to the registration authentication server system, and the system binds the user's account name and mobile phone number to each other; when logging in, the user submits his account name to the system's SMS platform through the SMS gateway in the form of mobile phone SMS when logging in. And indicate to the system whether there is a time limit; after receiving the user’s login request, the system SMS platform extracts the account name and user’s mobile phone number in the user’s SMS, and forwards them to the system authentication server. The authentication server receives the account name and user’s mobile phone. After the number is retrieved in the database of the system authentication server, if the account name and mobile phone number in the user login request ma...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com