User identity authentication method, third-party authentication platform and operator authentication platform
A technology of user identity authentication and authentication platform, applied in the direction of user identity/authority verification, etc., can solve problems such as security risks and economic losses, and achieve the effect of ensuring security, improving authentication level, and strengthening authentication services.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
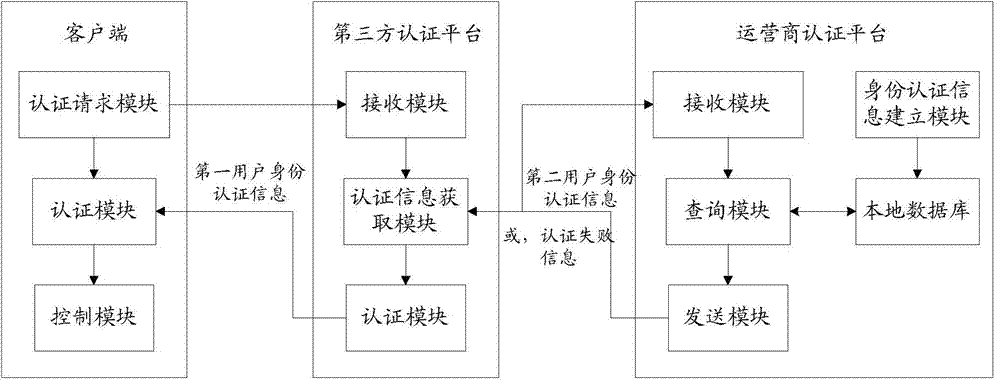
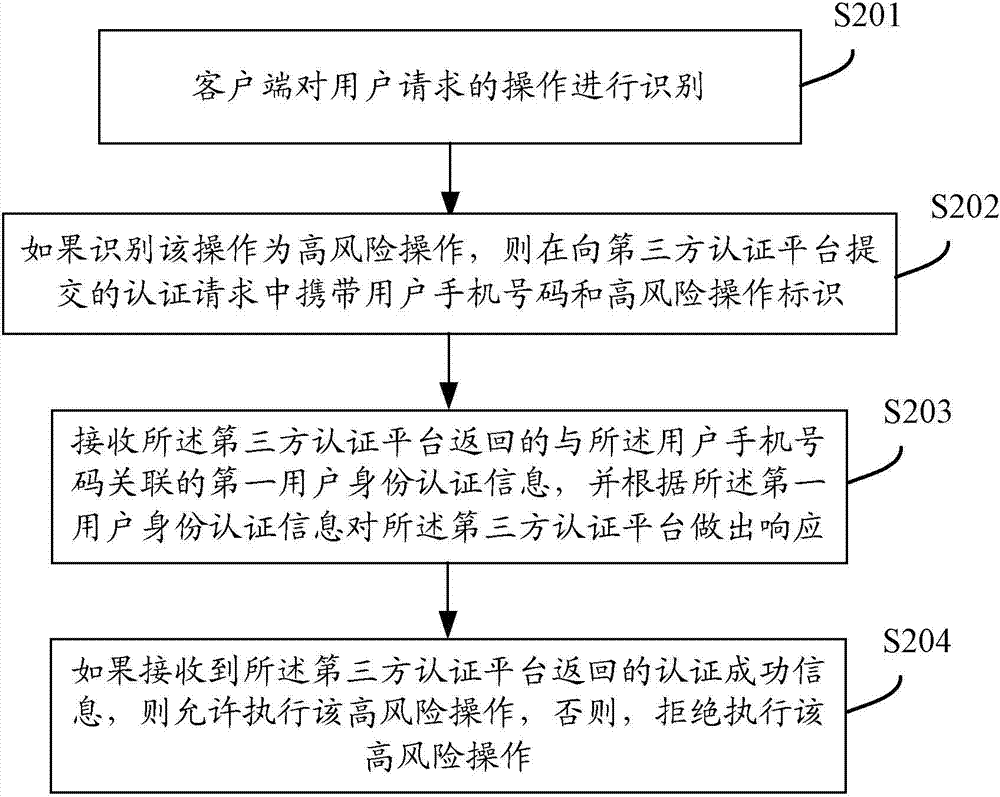
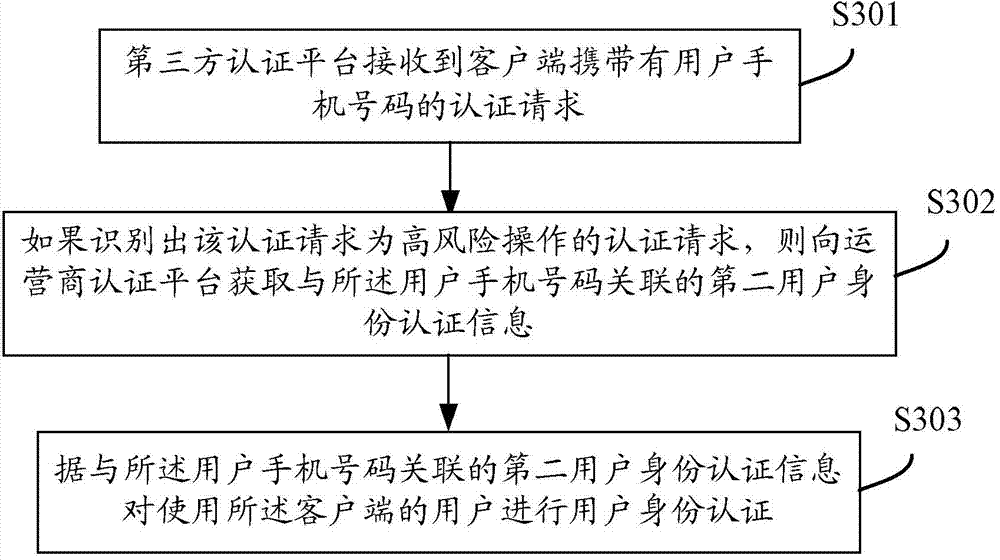
[0051] User identity credential - mobile phone and real user are two-level concepts, which can be expressed by "user-owned" and "user-known". "Owned by the user" is a superficial attribute of the user. For example, a mobile phone is an item owned by the user, which is easy to be forged and replaced; "Known by the user" is a deep-level attribute of the user, which is difficult to forge and can represent the real identity of the user. The current authentication methods centered on mobile identity are owned by the third-party application authentication platform to verify users, that is, the mobile phone number + password + SMS verification scheme is used to complete high-risk operations such as mobile payment and transfer. After entering the spyware, the attacker can crack the user's ownership only by stealing the mobile phone verification code, and obtain extremely high permissions, such as modifying the payment password, canceling the payment binding certificate, and logging into ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com