Account theft risk identification method and device and prevention and control system
A risk identification and account number technology, which is applied in the field of network security, can solve the problems of insufficient ability to distinguish the risk of theft, identification errors, and unsatisfactory overall effects, etc., and achieve the effect of improving the ability to distinguish the risk of theft, enhance the ability and stability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
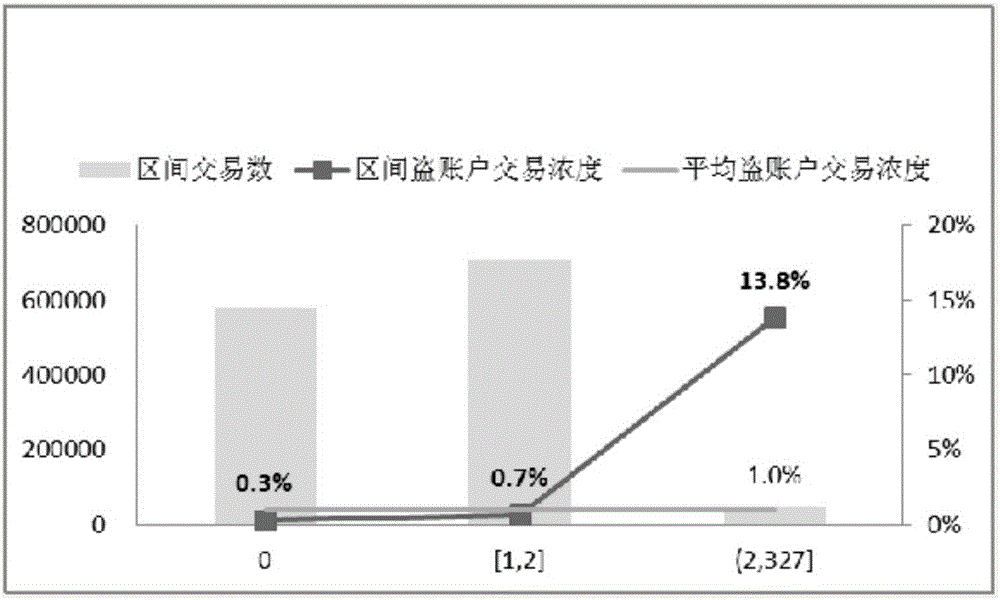
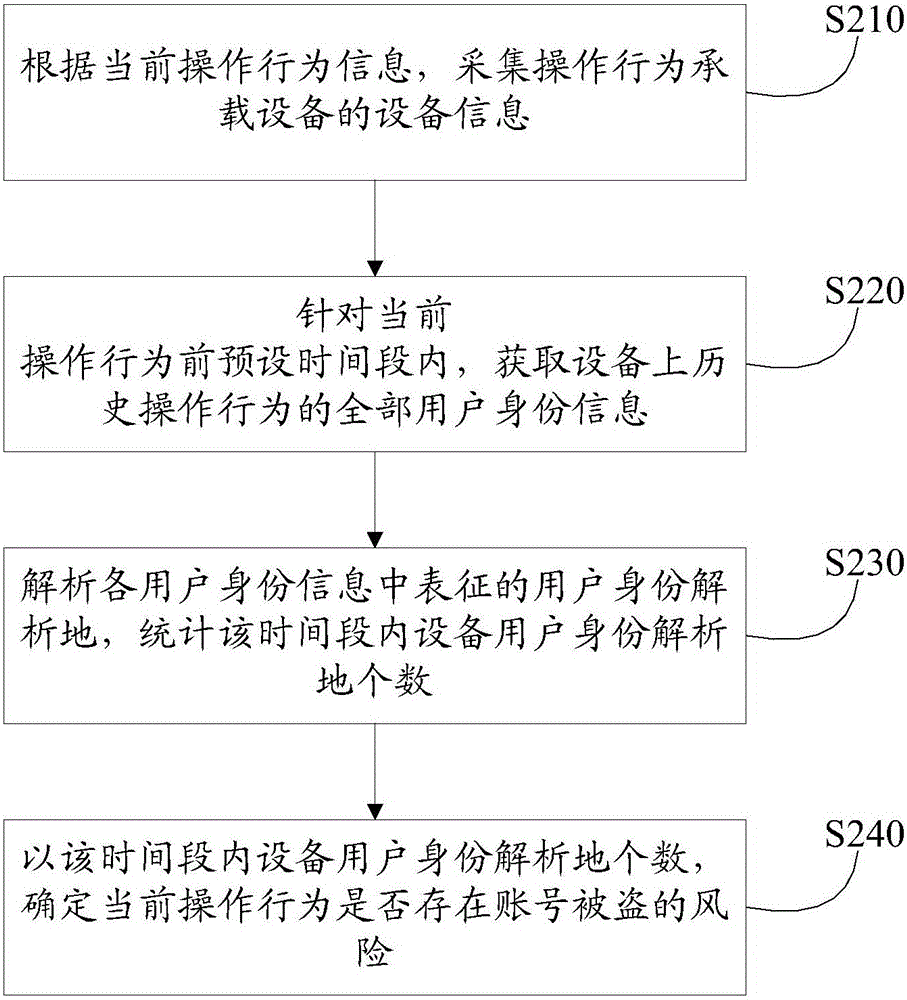
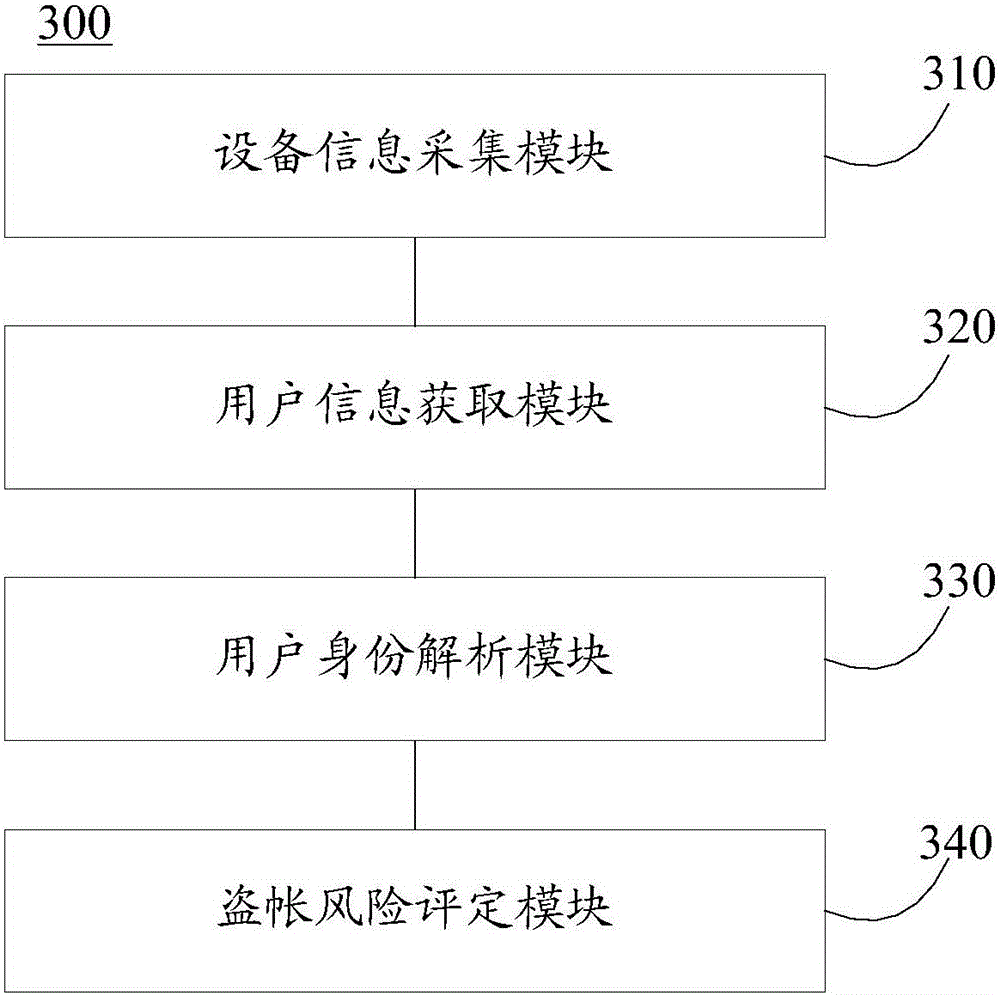
[0053] In the following embodiments of the present application, input variables such as the number of device user identities resolved within a period of time before the current operation behavior are introduced into the risk scoring model to improve the ability of model variables to distinguish risks. This scheme needs to establish a risk scoring model based on data mining technology. The main modeling steps include determining research objectives, determining data sources, extracting samples, data exploration, model development and model verification, etc. The focus of this application is to provide the scoring model Build suitable input variables. Since the scoring model itself is not the main focus of this application, other details of the modeling will not be described. For details, please refer to the known prior art.
[0054] In order to construct suitable variables, the inventor of the present application collected massive data of users' operation behavior on a certain ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com