Method and system for monitoring network behavior data, risk monitoring method and risk monitoring system
A monitoring system and data technology, applied in the field of computer network, can solve the problems of unmonitoring, untimely monitoring, lagging, etc., and achieve the effect of reducing manual intervention, improving timeliness, and improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
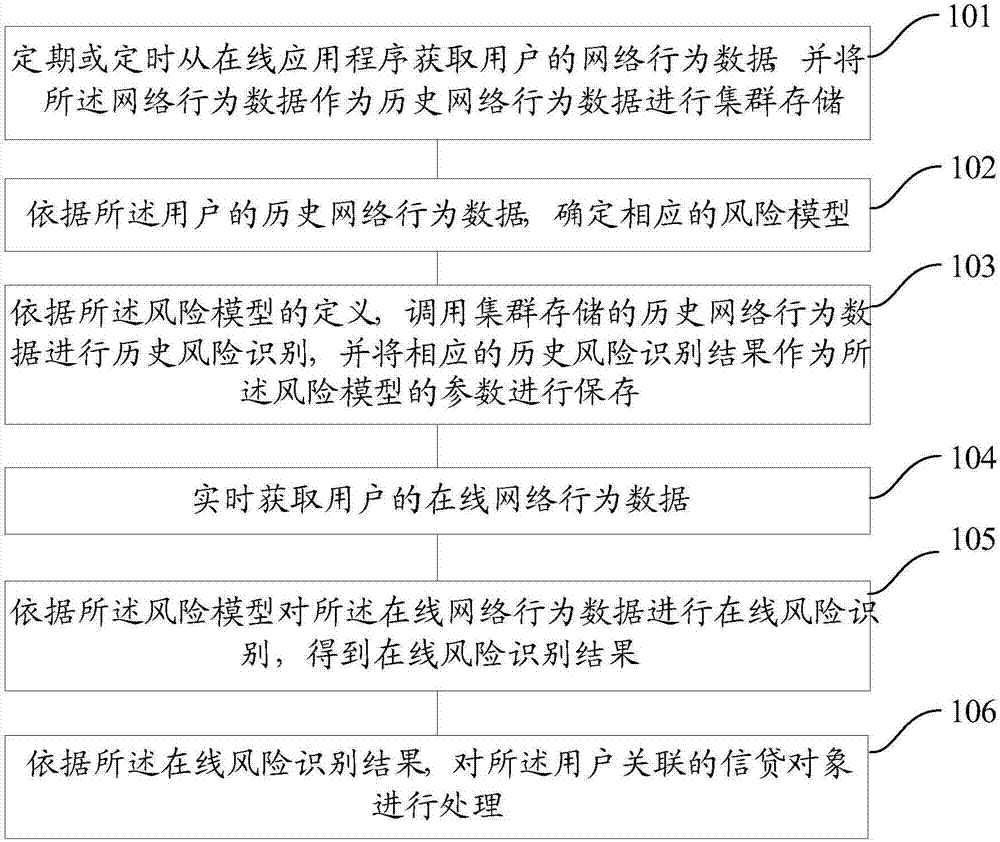
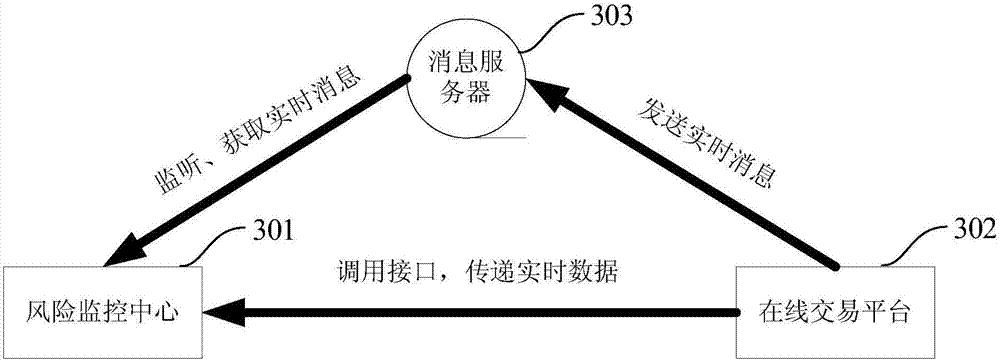
[0066] In order to make the above objects, features and advantages of the present application more obvious and comprehensible, the present application will be further described in detail below in conjunction with the accompanying drawings and specific implementation methods.
[0067] The existing monitoring methods for corporate credit or personal credit card credit risk cannot obtain timely and sufficient user information. For example, only the financial report provided by the company is collected before the loan application, and the corporate financial monthly report is collected regularly every month after the loan application ; Another example is to only collect the identity certificate provided by the individual user before applying for a credit card, and calculate the total monthly consumption amount of the individual user after applying for a loan. Based on the above reasons, the prior art can only perform post-loan and static monitoring, which has the disadvantages of u...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com