Network security correlation analysis method based on complex event processing
A complex event processing and network security technology, applied in the field of network security correlation analysis based on complex event processing, can solve the problems of complex, unfavorable network security conditions, and low execution efficiency, and achieve the effect of processing protection and early warning
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
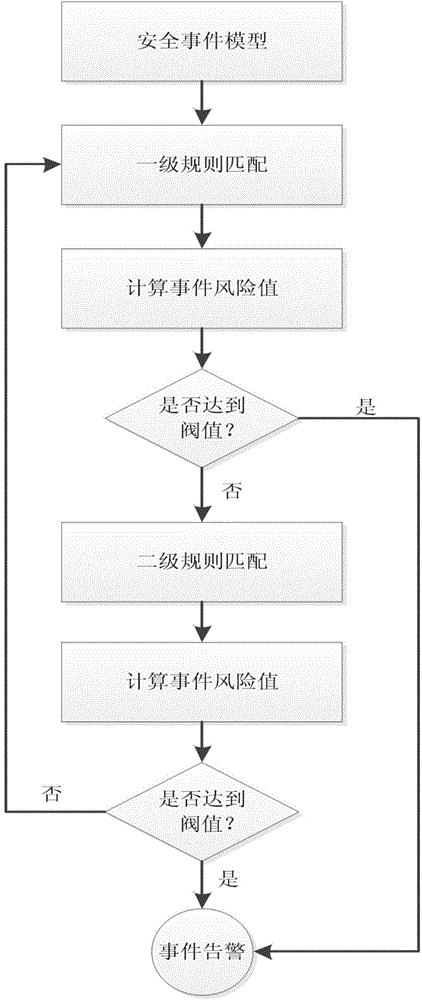
[0024] The preferred embodiments will be described in detail below in conjunction with the flow charts. It should be emphasized that the following descriptions are only illustrative, not intended to limit the scope of the present invention and its application.
[0025] Step 1: Carry out unified format conversion for network security events through the security event model.
[0026] Cybersecurity events come from a variety of sources and in different formats. Before performing correlation analysis, a unified format conversion for various security events can facilitate subsequent calculations.
[0027] The event model used here includes four attributes, namely E_Identifier, E_Attribute, Restraint, Risk, where E_Identifier is a set of related identifiers that are convenient for distinguishing events, and E_Identifier={E_N, E_ID, E_Type}, where E_N represents the event name, E_ID is a unique identification code that distinguishes different events and is universal globally. E_Type...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com