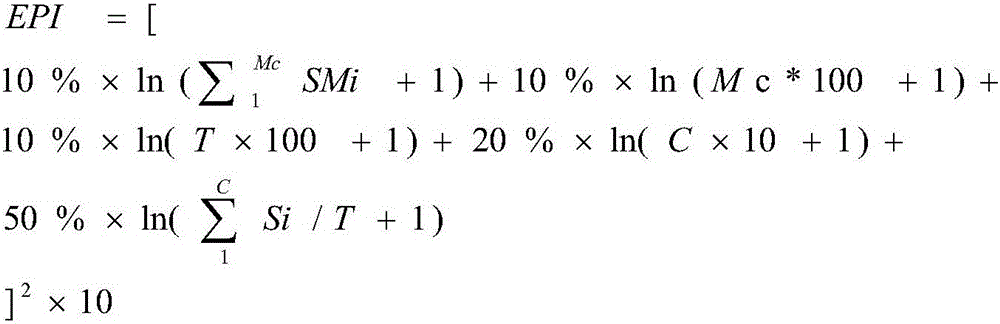Patents
Literature
46 results about "Event propagation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
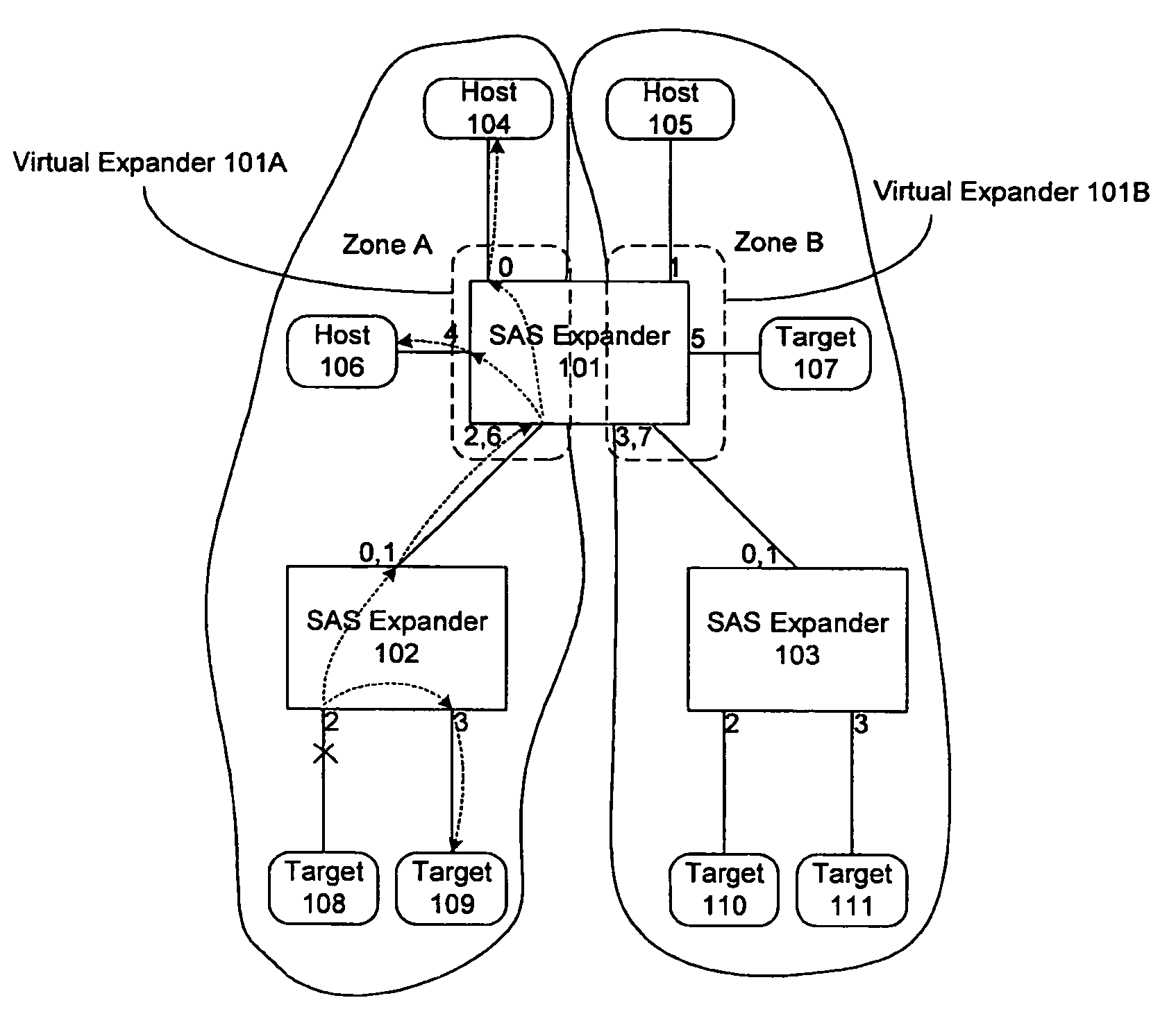
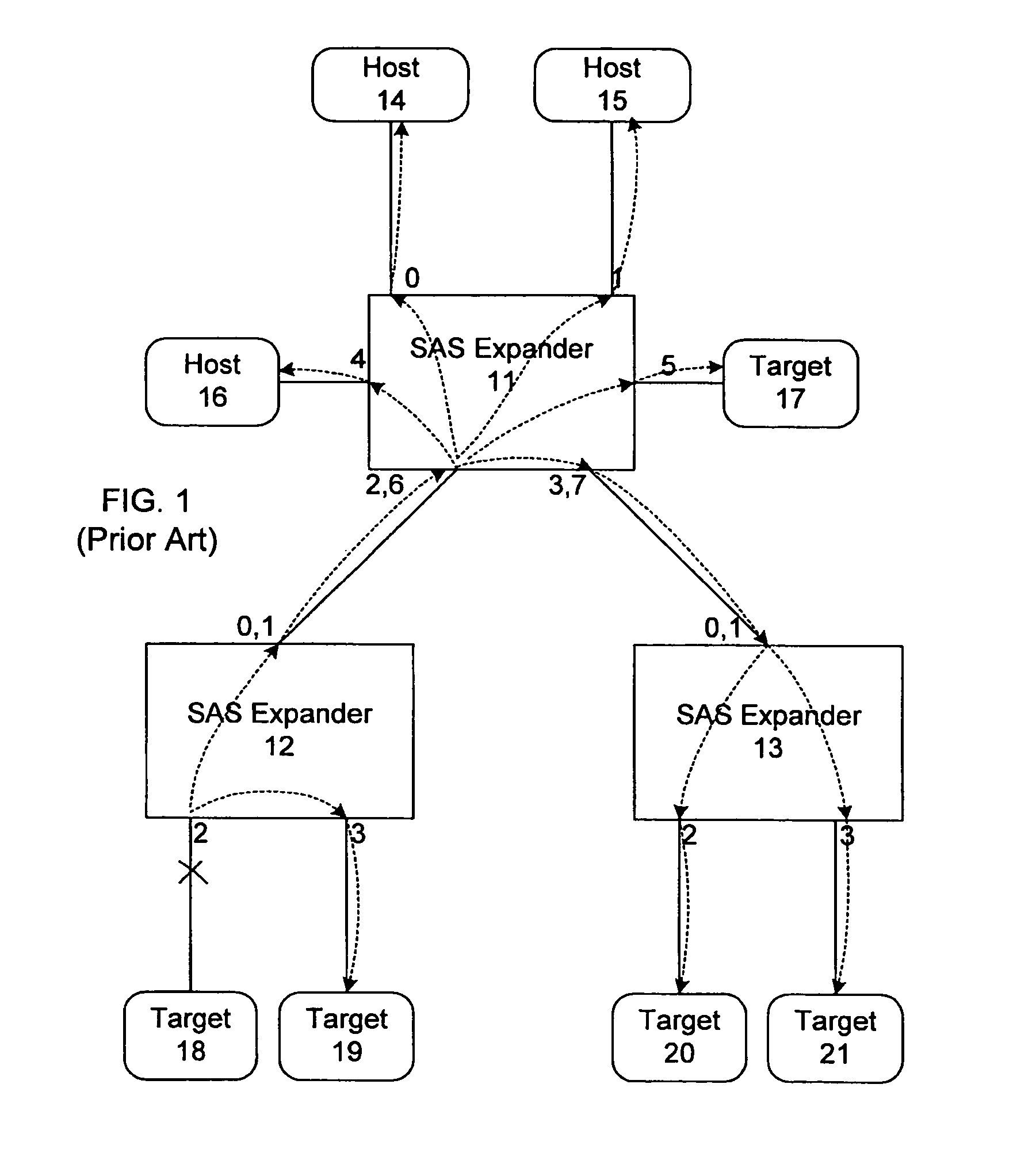
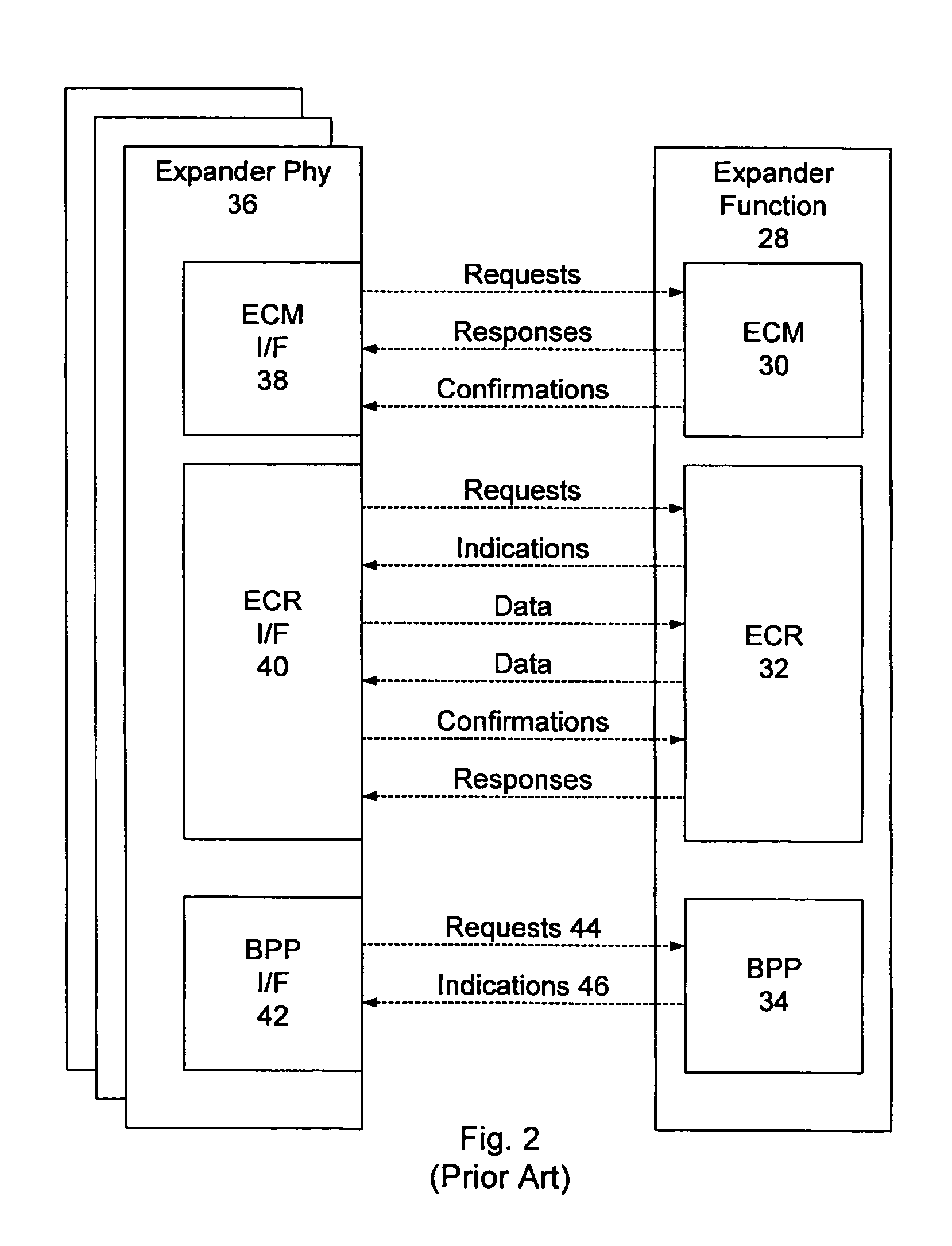
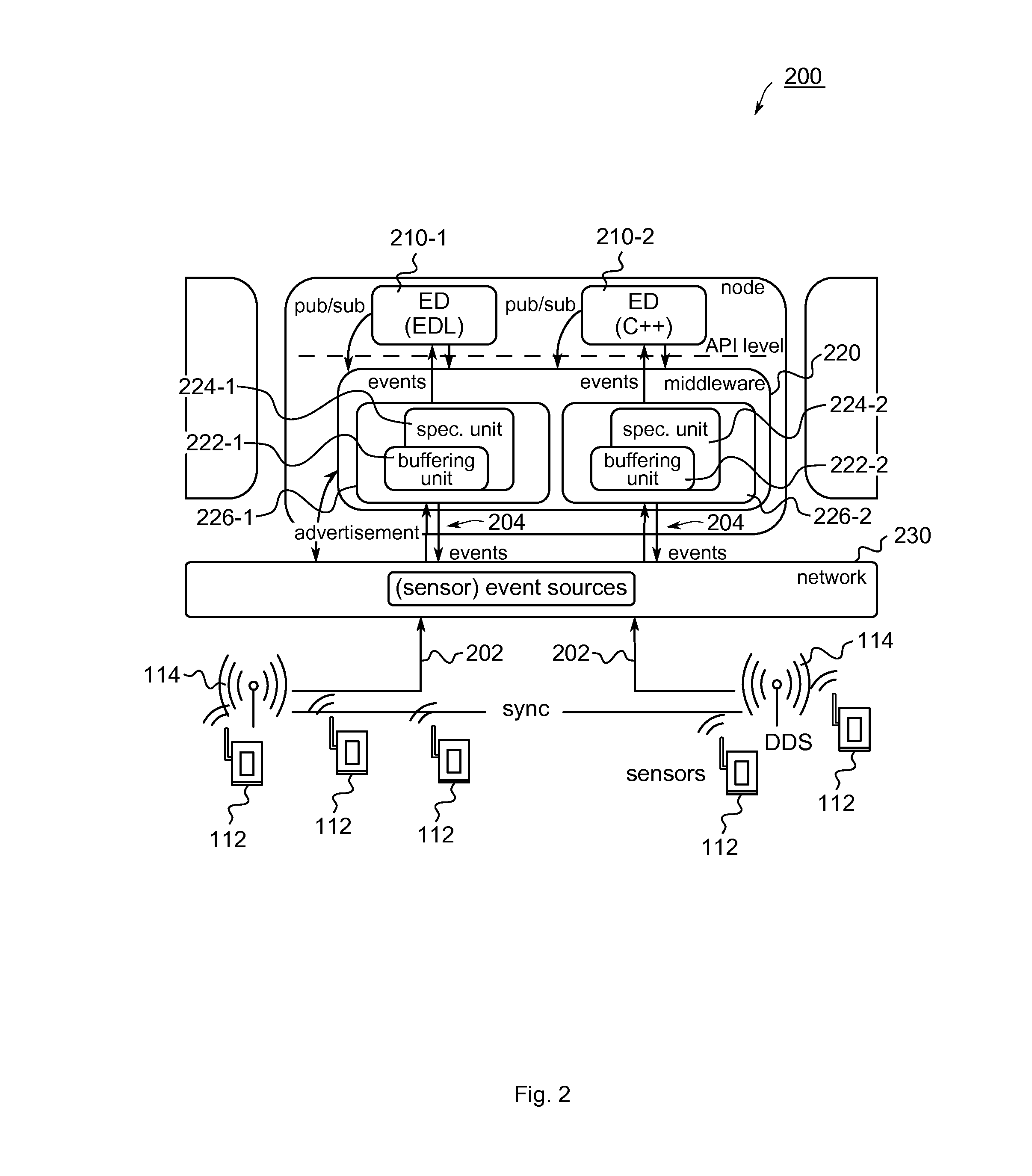
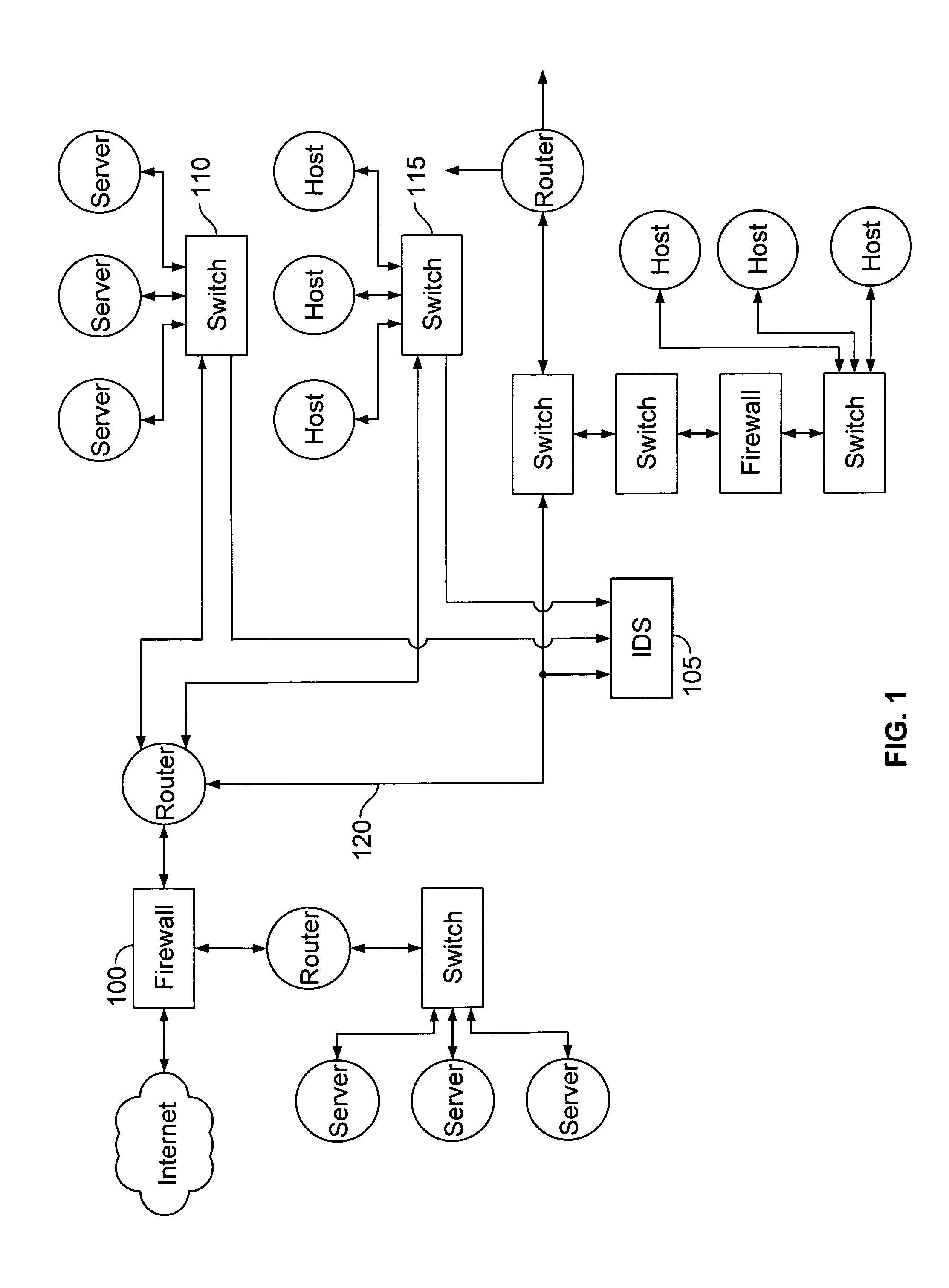
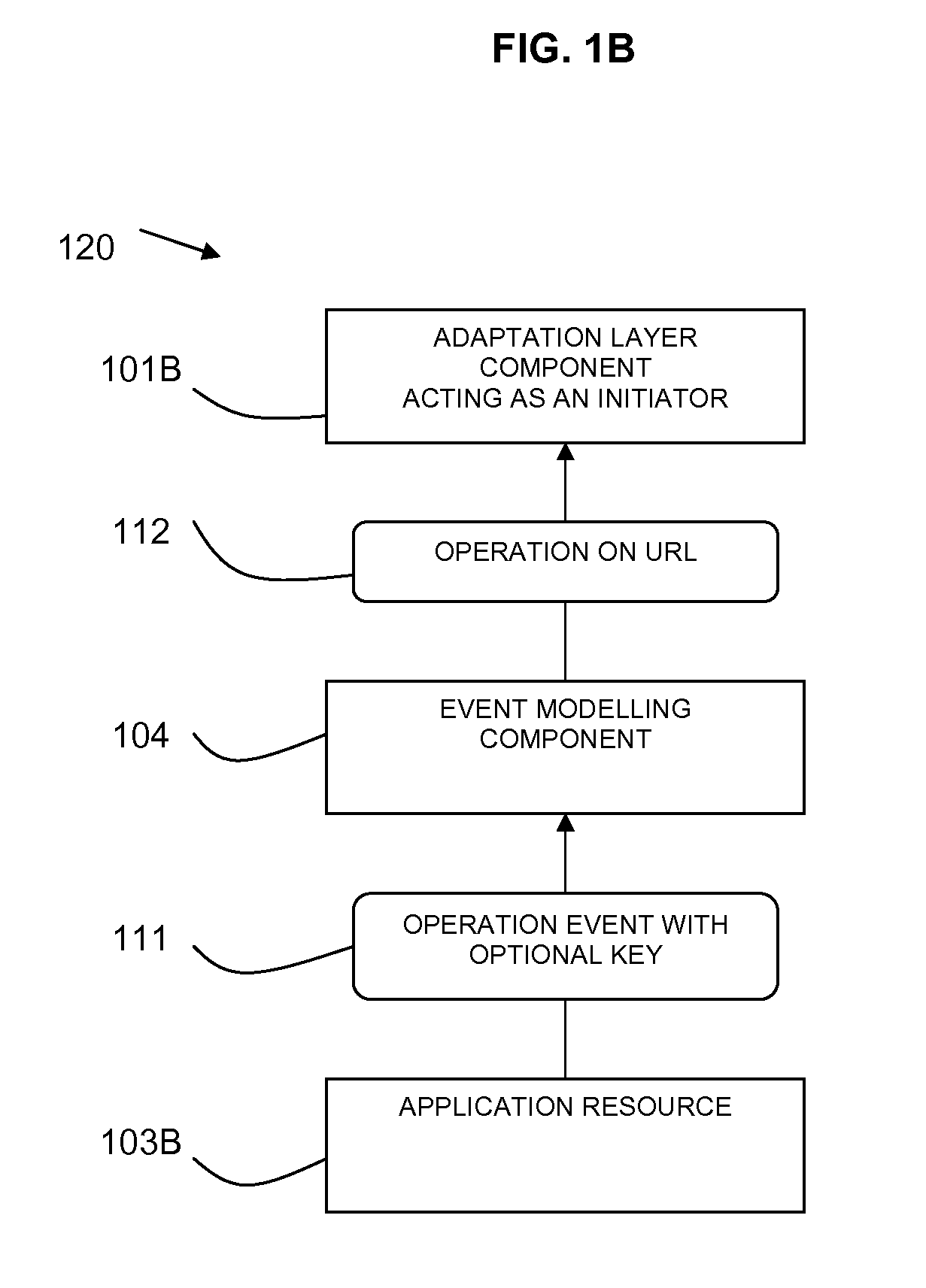
Method and apparatus for broadcast primitive filtering in SAS
ActiveUS8116226B1Data switching by path configurationMultiple digital computer combinationsTraffic capacityEvent propagation
Broadcast primitive filtering in a SAS expander using virtual domains. The virtual domains can be non-overlapping or overlapping logical subsets of the physical topology, or a logical construct based on the membership of a device within a group. Broadcast event propagation is handled in accordance with predetermined policies associated with the virtual domains. These policies can, for example, include limiting the broadcast traffic within the boundaries of the logical zones defined by the subsets, or routing the broadcast events in accordance with access policies, or privileges, associated with the group.
Owner:MICROSEMI SOLUTIONS (US) INC
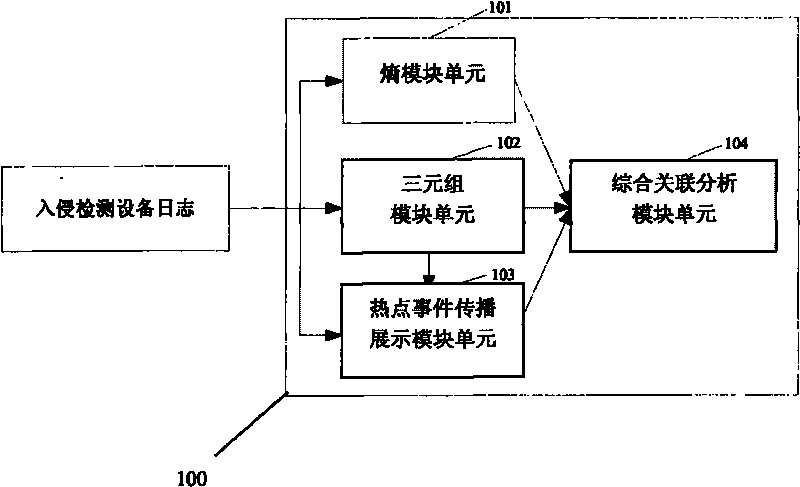
Association analysis method and system for massive logs
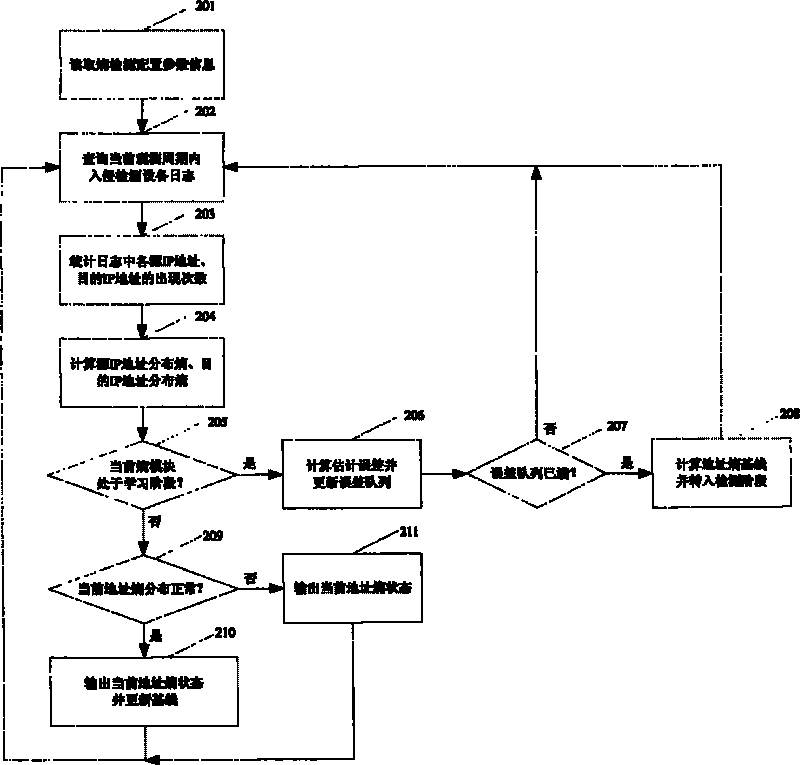
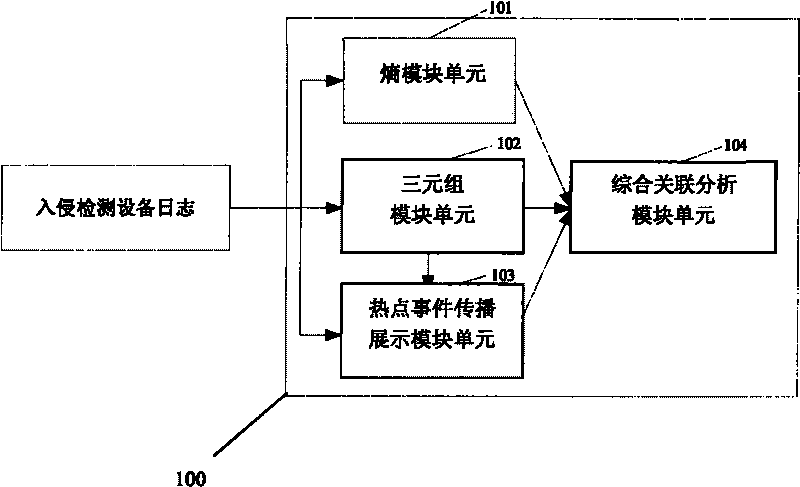
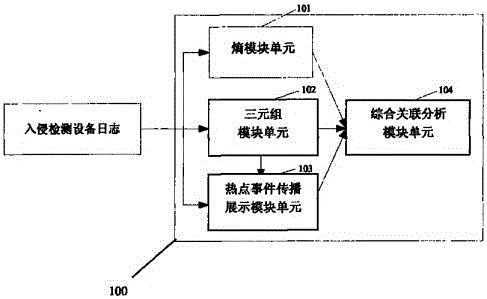
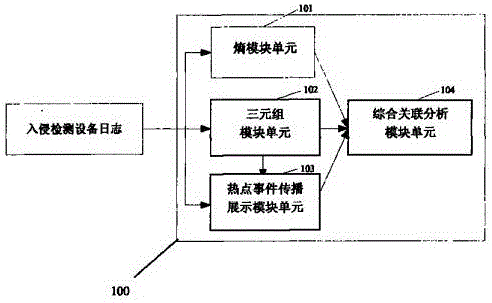
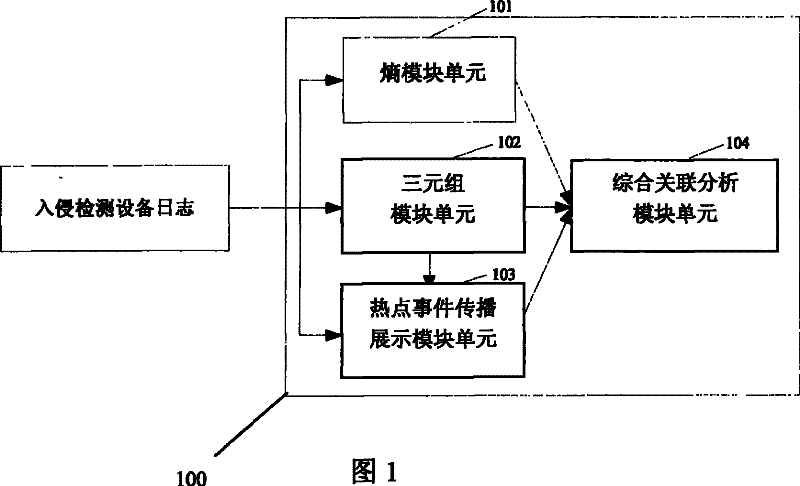
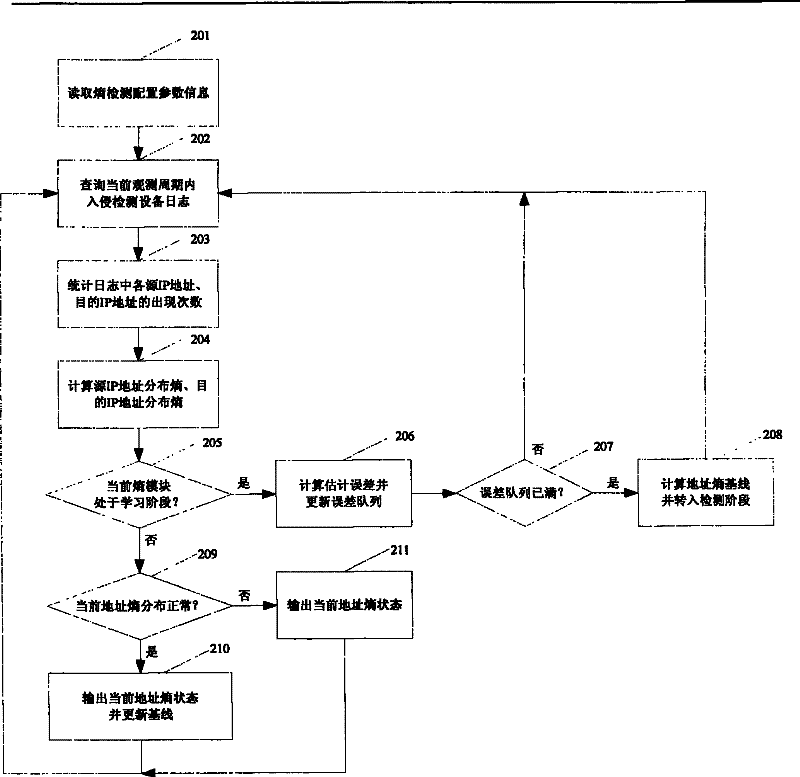
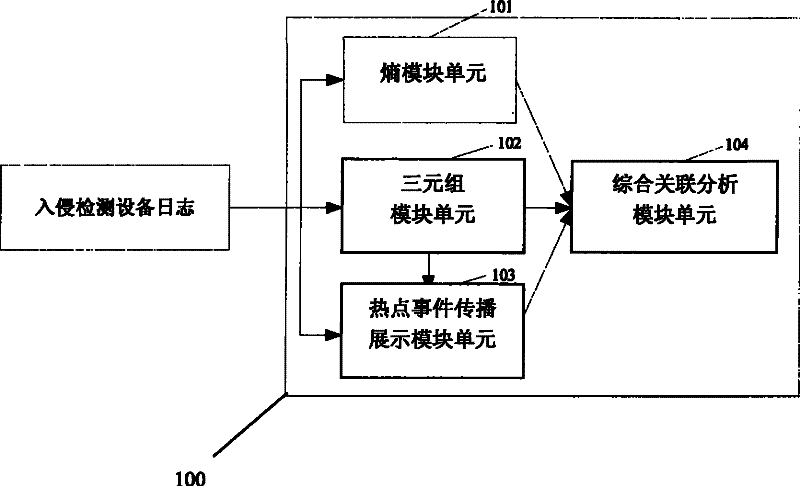
The invention discloses an association analysis method and an association analysis system for massive logs to evaluate the current network security condition and describe the attack condition which is paid most attention currently according to the massive logs generated by an intrusion detecting device. The method comprises the following steps: acquiring the logs of the intrusion detecting device, and judging whether a large-scale network security event exists or not by calculating the distribution condition of source addresses and destination addresses of the logs of the intrusion detecting device; merging the logs of the intrusion detecting device according to the source addresses, the destination addresses and event types, and detecting and reporting abnormal addresses and hot events; counting and displaying a propagation process of the hot events in a specific time period through graphics; and associating output results, and giving comprehensive evaluation on the current network security condition. The system comprises an entropy module unit, a triple module unit, a hot event propagation display module unit, and a comprehensive association analysis module unit.
Owner:BEIJING VENUS INFORMATION TECH +3
Apparatus, method and computer program for processing out-of-order events
ActiveUS20150363245A1Late detectionParticular environment based servicesInterprogram communicationEvent propagationOccurrence time
Embodiments relate to a concept for ordering events of an event stream, comprising out-of-order events, for an event detector, wherein the events have associated thereto individual event occurrence times (ei·ts) and individual event propagation delays up to a maximum delay of K time units. Event received from the event stream are provided to an event buffer. Received events in the event buffer are ordered according their respective occurrence times to obtain ordered events. An ordered event (ei) having an event occurrence time ei·ts is speculatively forwarded from the event buffer to the event detector at an earliest time instant clk, such that ei·ts+α*K≦clk, wherein α denotes a speculation quantity with 0<α<1.
Owner:FRAUNHOFER GESELLSCHAFT ZUR FOERDERUNG DER ANGEWANDTEN FORSCHUNG EV
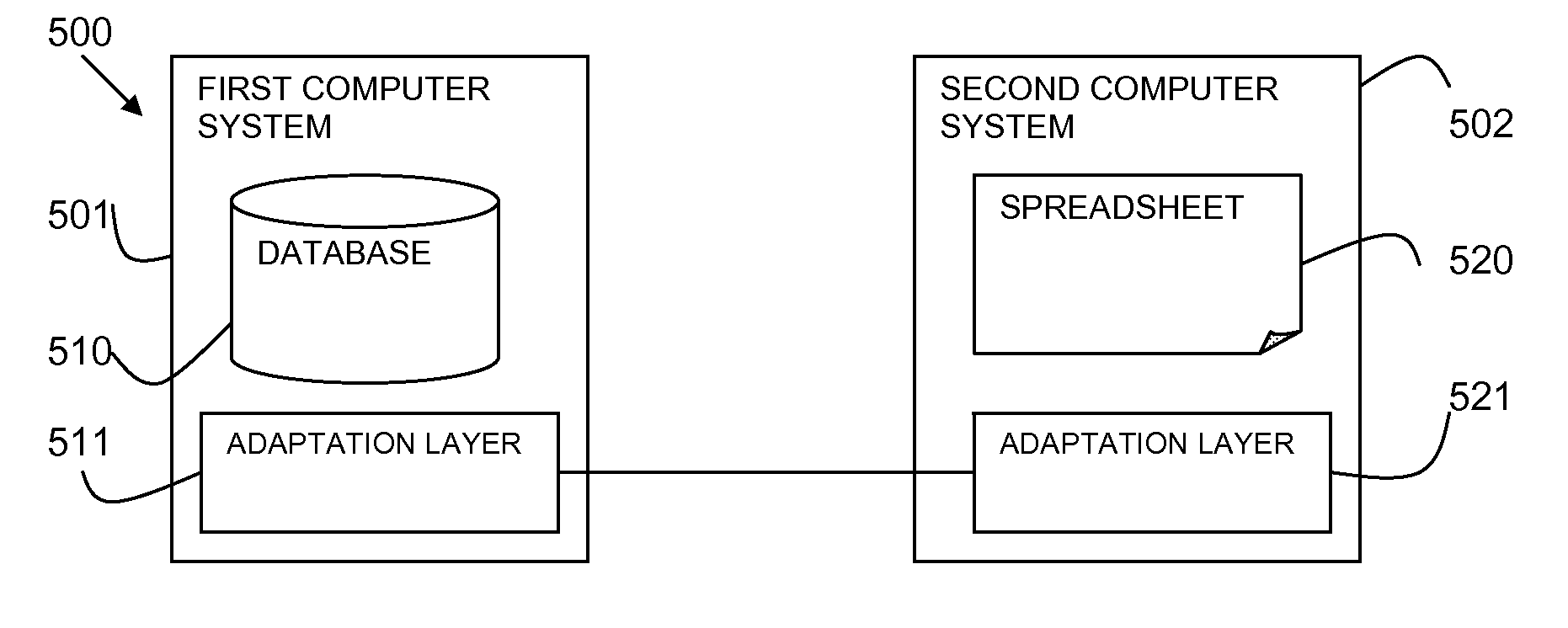
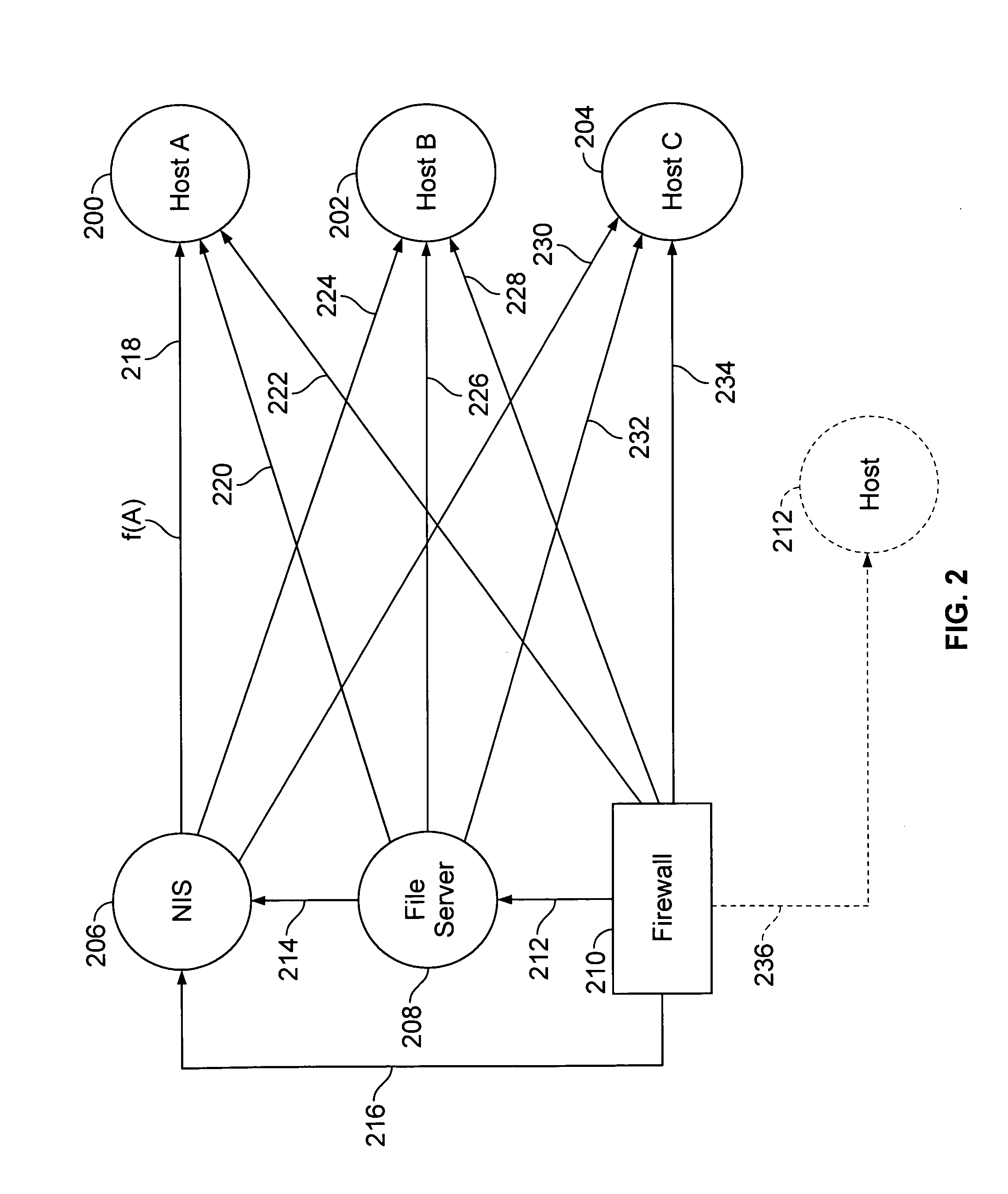
Synchronization of data between systems
ActiveUS20120221522A1Digital data processing detailsDatabase distribution/replicationData resourcesEvent propagation
Owner:IBM CORP
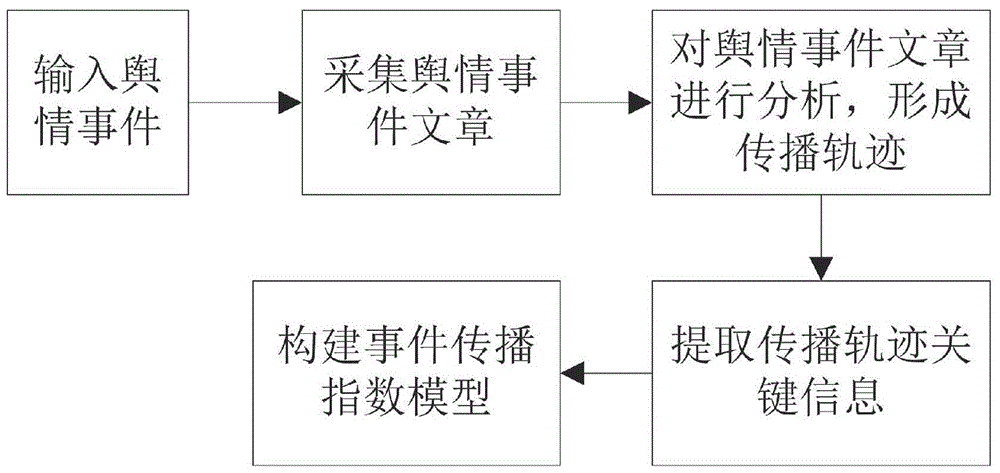
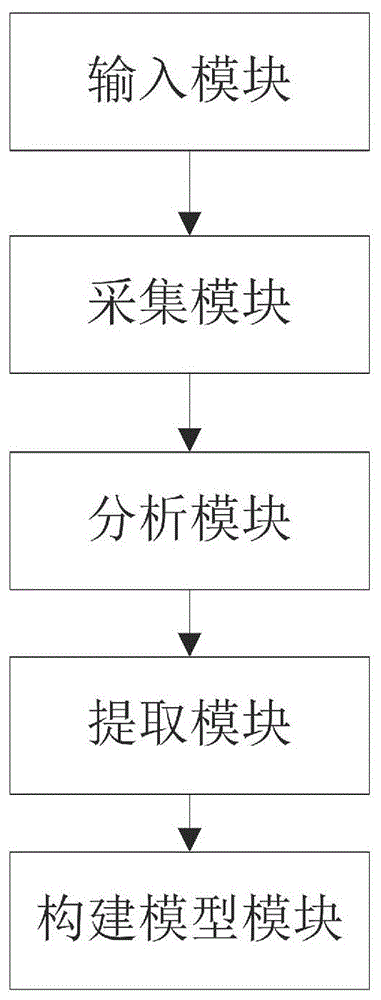
Acquiring method and system for propagation indexes of internet public opinion events
ActiveCN106776841AWeb data indexingSpecial data processing applicationsThe InternetEvent propagation
The invention provides an acquiring method for propagation indexes of internet public opinion events. The acquiring method comprises steps as follows: 1, inputting the public opinion events; 2, collecting related public opinion articles grabbing the public opinion events from each medium source and storing the public opinion articles in a public opinion event analysis library; 3, analyzing all the public opinion articles about the public opinion events, sorting all medium-sourced articles in the order of publishing time of the articles to form a public opinion event propagation track, and meanwhile, performing single-article propagation index calculation on each article; 4, extracting public opinion event propagation track key information by the aid of the article propagation indexes; 5, constructing a final model by use of the public opinion event propagation track key information. With the adoption of the method, a more precise model is adopted, and the development trend of the public opinion events in the whole life cycle from generation, development, outburst, peak, weakening to end can be better reflected.
Owner:FUJIAN YIRONG INFORMATION TECH +3
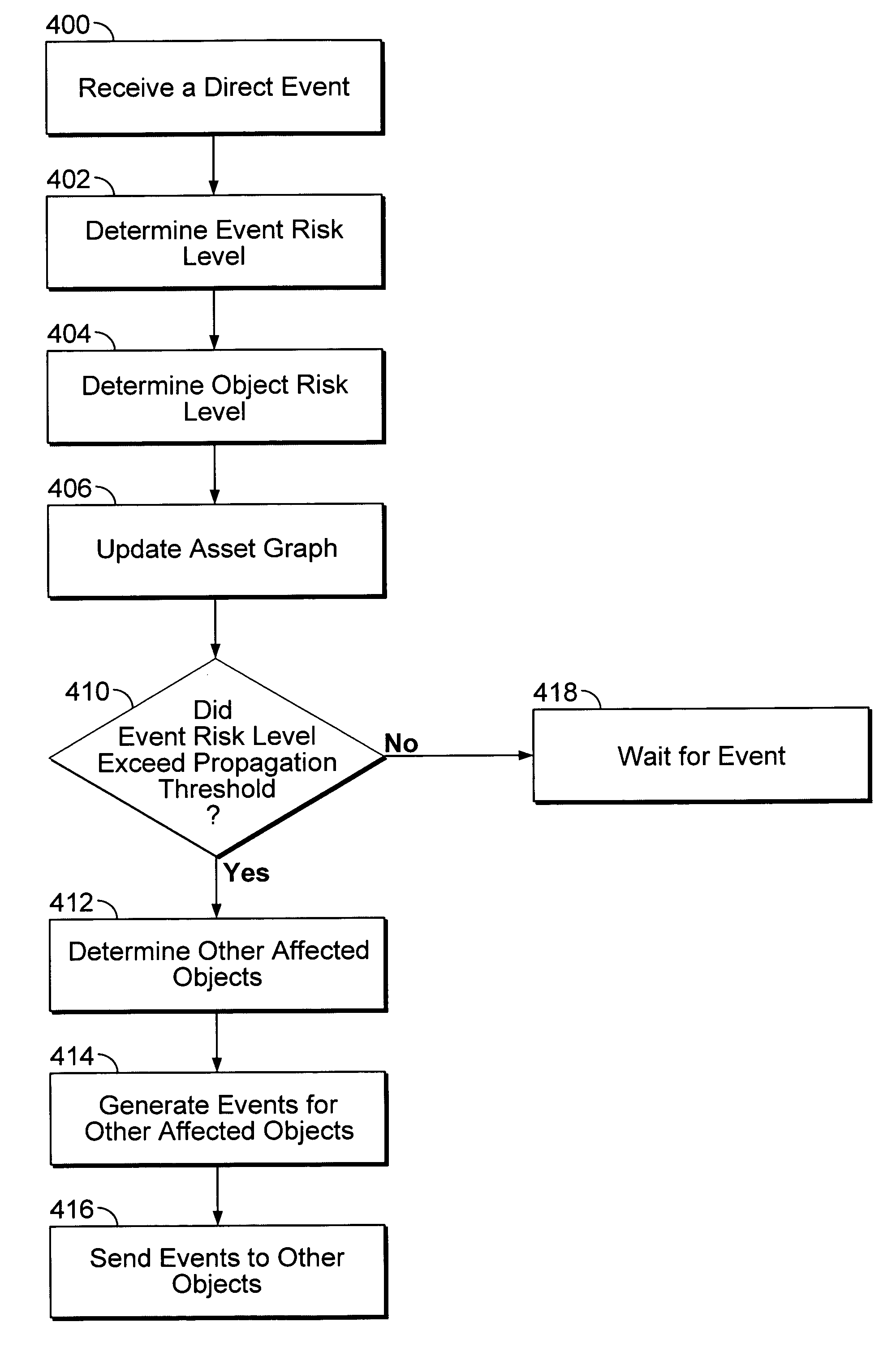
Network risk analysis
A system and method are disclosed for analyzing security risks in a computer network. The system constructs asset relationships among a plurality of objects in the computer network and receives an event associated with a selected object, where the event has an event risk level. The system also propagates the event to objects related to the selected object if the event risk level exceeds a propagation threshold.
Owner:CA TECH INC
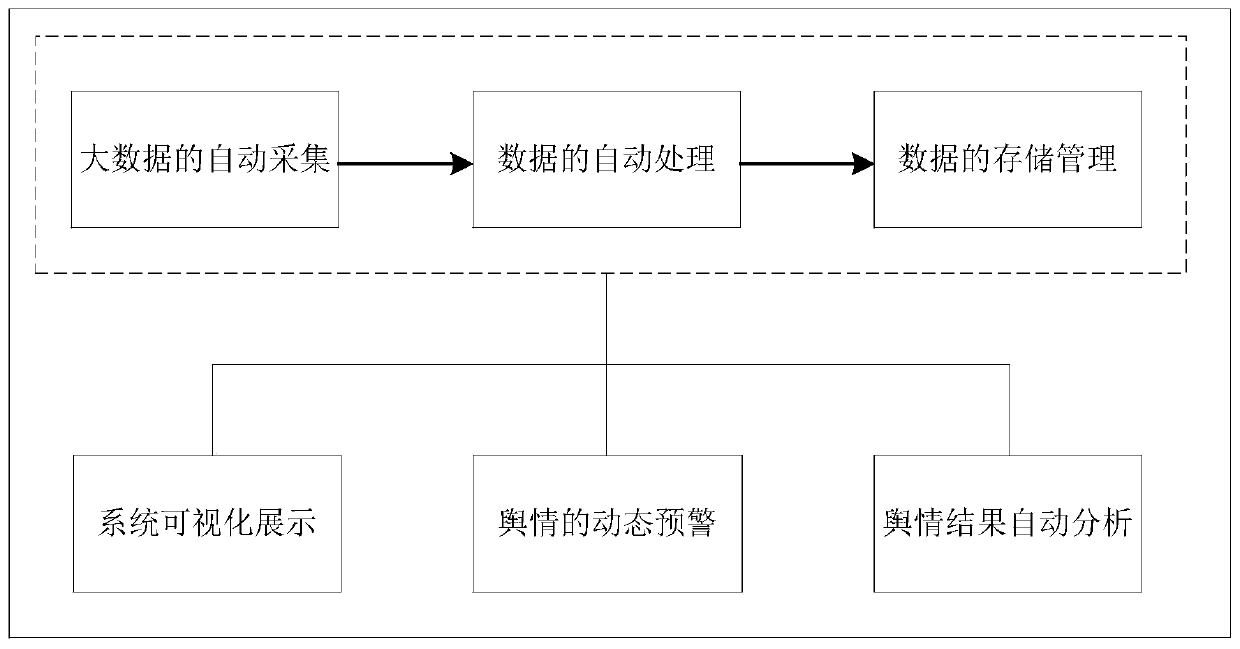
Urban inland inundation public opinion monitoring and early warning method based on big data
The invention discloses an urban inland inundation public opinion monitoring and early warning method based on big data. The method comprises five levels of data acquisition, data processing, public opinion analysis, visual display and system management. The method comprises the following steps: firstly, performing structured processing on collected public opinion big data related to urban inlandinundation, and analyzing an urban inland inundation event popularity index trend, an inland inundation whole-network information source proportion, keyword clustering, viewpoint deviation of netizensto inland inundation events, inland inundation event propagation nodes and the like; the system provides rainfall monitoring, rain condition tracking, waterlogging point display, traffic route guidance and other application services, and visualized display is carried out through a client, a display screen, a mobile terminal and other modes. The system establishes multi-level user management authority, realizes dynamic monitoring and early warning of urban inland inundation public opinions, responds quickly, and provides efficient information service and decision support for managers and social people.
Owner:XIAN UNIV OF TECH
Network attack analysis method
The invention discloses a network attack analysis method. Through the method, the current network attack condition can be evaluated and the attack situation deserving most attention currently can be described according to a huge amount of logs produced by an intrusion detection system. The method comprises the following steps: acquiring the logs of an intrusion detection system, and judging whether there is a large-scale network attack event by calculating the distribution of the source addresses and destination addresses of the logs of the intrusion detection system; merging the logs of the intrusion detection system according to three parameters, namely, source address, destination address and event type, and detecting and reporting abnormal addresses and hot events; making a statistical analysis of and displaying the propagation process of the hot events in a specified period of time; and associating the output results, and presenting a comprehensive evaluation of the current network attack condition. The system comprises an entropy module unit, a triple module unit, a hot event propagation display module unit, and a comprehensive association analysis module unit.
Owner:LIUZHOU LONGHUI TECH
A social network rumor identification method based on feature aggregation
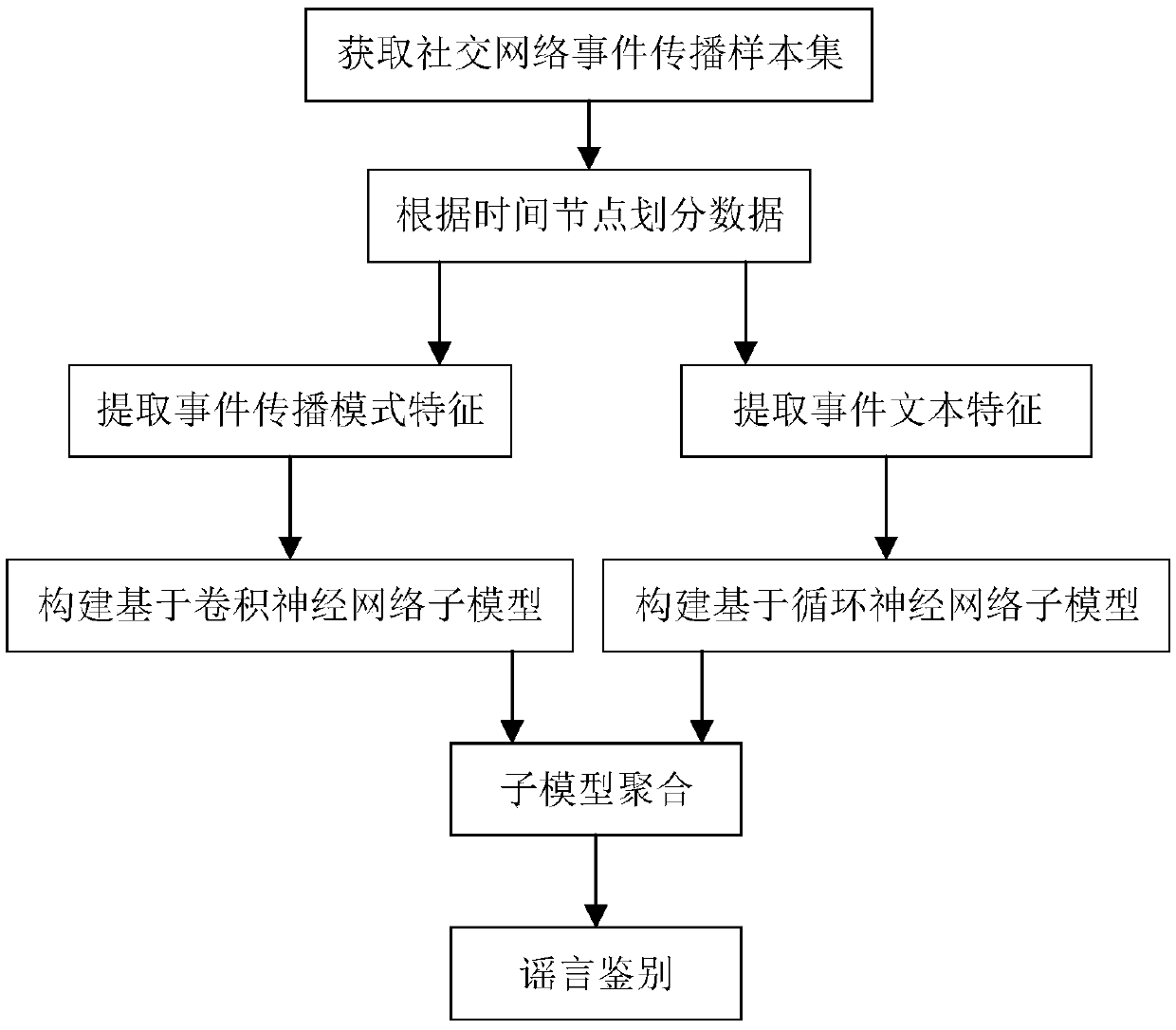
ActiveCN109685153ASolve the problem that it is difficult to deal with heterogeneous informationSolve problems that are difficult to feed into machine learning modelsData processing applicationsCharacter and pattern recognitionStudy methodsData quality
The invention discloses a social network rumor identification method based on feature aggregation, and the method comprises the steps: designing time sequence propagation mode features acceptable by adeep neural network and time sequence text features, constructing a rumor detection model by using a feature aggregation technology, and carrying out the final detection and early detection of a rumor. The problem that propagation mode characteristics of social network event propagation are difficult to serve as machine learning model input is solved, the propagation mode characteristics do not depend on characteristic engineering and field knowledge, the influence of various factors in the actual propagation process is comprehensively embodied, and the method can be effectively applied to different rumor identification scenes; The defect that the quality of feature data is reduced due to huge difference of the number of messages contained in different samples is avoided, the problem thata single model is difficult to deal with heterogeneous information in a traditional machine learning method is solved, and compared with an existing rumor identification method, the accuracy is obviously improved.
Owner:WUHAN UNIV
Method for transferring data between modules by utilizing event mechanism in flex
InactiveCN101599029AEasy to handleEliminate dependenciesInterprogram communicationEvent propagationDatabase
The invention provides a method for transferring data between modules of a flex application program, which comprises the steps of utilizing an event propagation mechanism of the flex to encapsulate the data into a customized event, and then transferring the event carrying the data from a source module to a target module and separating the data which is contained in the event from the target module for the target module to use, thereby achieving the purpose of transferring the data between the modules. The method has simple operation and easy maintenance, and eliminates the dependence between the modules. Because the event propagation mechanism of the flex is utilized by the method, the data transferring efficiency is high, and errors do not easily occur.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
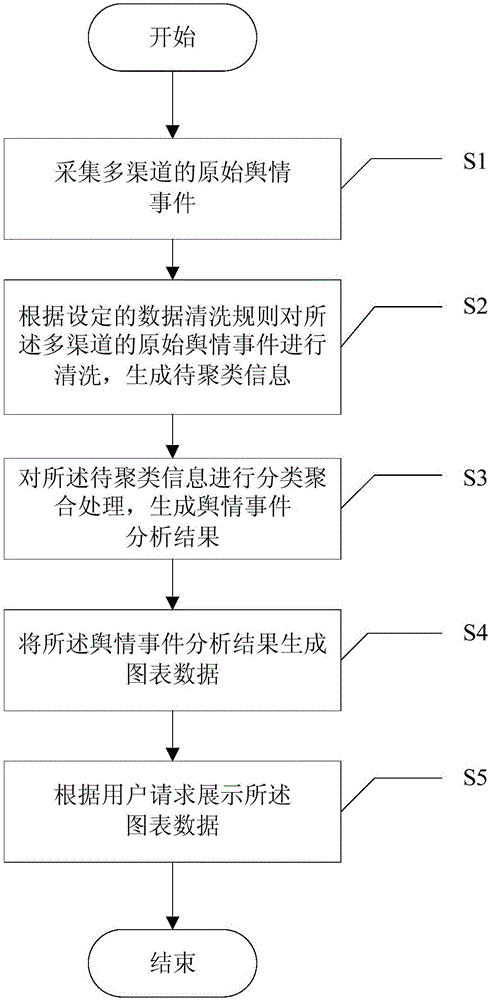
Data analysis method and apparatus
ActiveCN106557558AThe analysis result is accurateThe results of the analysis are comprehensiveSpecial data processing applicationsAnalysis methodEvent propagation
The invention provides a data analysis method and apparatus. The data analysis method comprises the steps of collecting multi-channel original public sentiment events; according to a set data cleansing rule, cleansing the multi-channel original public sentiment events to generate to-be-clustered information; performing classification polymerization processing on the to-be-clustered information to generate a public sentiment event analysis result; generating the public sentiment event analysis result into graph data; and showing the graph data according to requirement of a user. By adoption of the data analysis method and apparatus disclosed by the invention, the polymerization efficiency of effective public sentiment events is greatly improved, and the problem of more abundant information and single analysis channel in the conventional public sentiment event analysis method is solved; in addition, the invention also provides a public sentiment event service for realizing all-around showing of the development process and trend of the public sentiment events to form a complete public sentiment event propagation path, so that a more accurate and more all-around public sentiment event analysis result is provided for the user; and therefore, social situation can be mastered in time, hidden dangers can be found, hidden risks can be recognized, and forceful data support is provided.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
Key node selection method in network public opinion information propagation
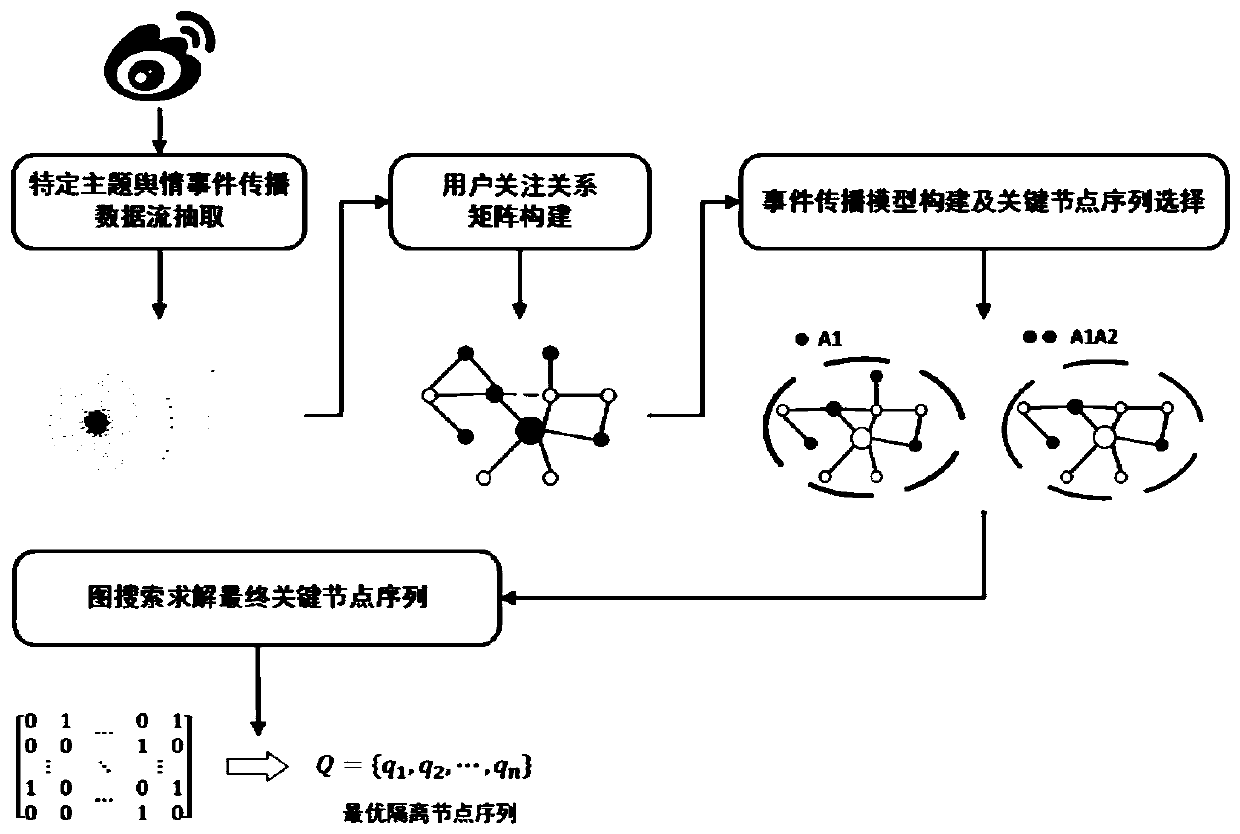
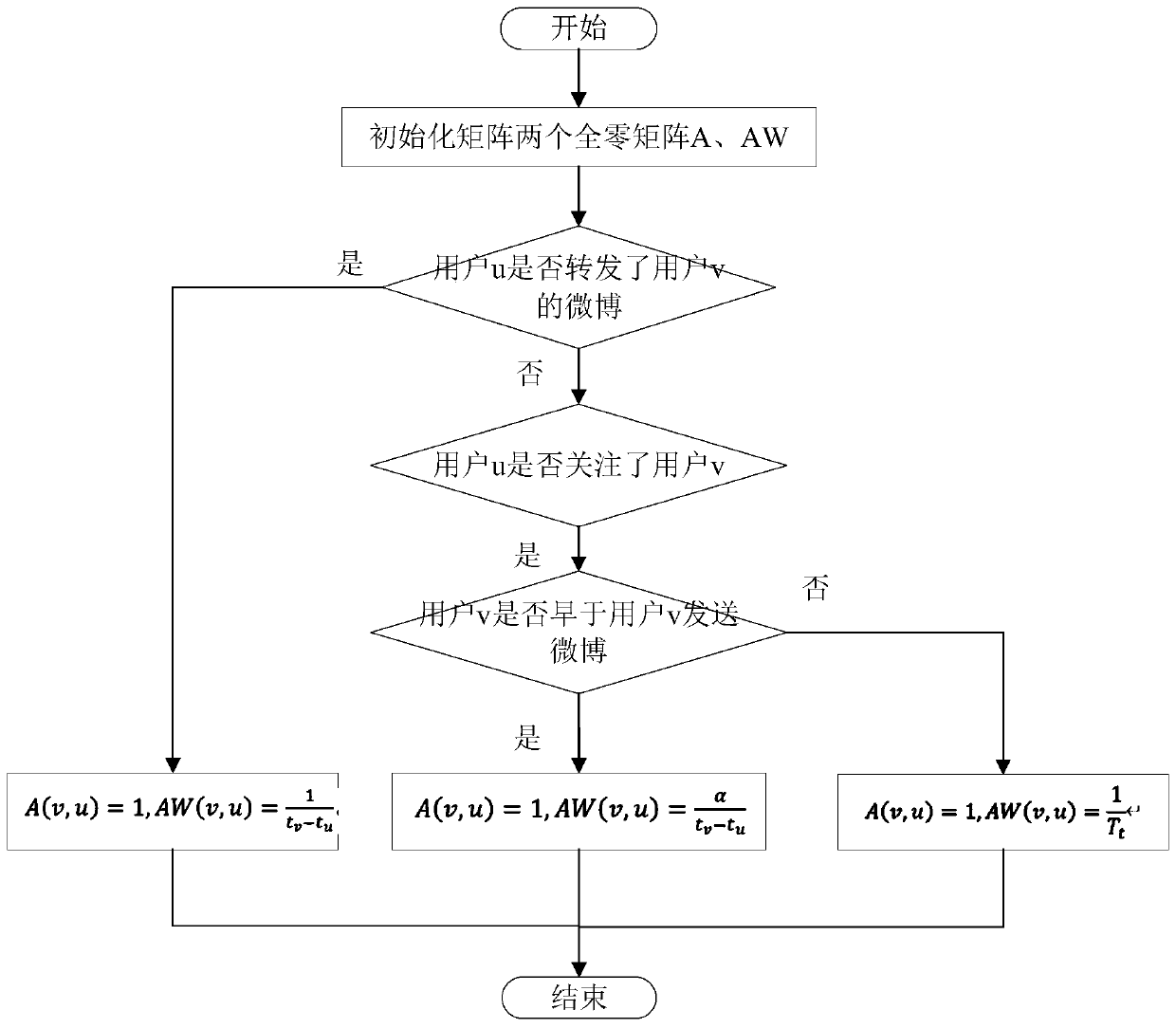
ActiveCN111222029ASmall averageIncreased cost-benefit ratioData processing applicationsWeb data indexingInformation propagationGreedy algorithm
The invention discloses a key node selection method in network public opinion information propagation. The method comprises the following steps: 1) collecting public opinion event propagation flow data under a specific theme from a real social network; 2) modeling the propagation process of the single microblog message by adopting an infectious disease model and accurately estimating the propagation influence of the single microblog message; 3) in order to solve the problem of high algorithm time complexity due to excessive users, reducing the number of seeds by adopting a heuristic method from the perspective of network structure characteristics, introducing the concept of isolation efficiency, and selecting a node with the highest isolation efficiency in each simulation process by adopting a greedy algorithm to add into a key node set; 4) solving the problem of simulation randomness by adopting a depth-first algorithm in directed graph search, and obtaining a group of key node sets in an information propagation process. according to the invention, the structural characteristics of a network and dynamic characteristics of information propagation are comprehensively considered in akey node selection process in network public opinion information propagation, so the method is more suitable for an actual application scene.
Owner:XI AN JIAOTONG UNIV
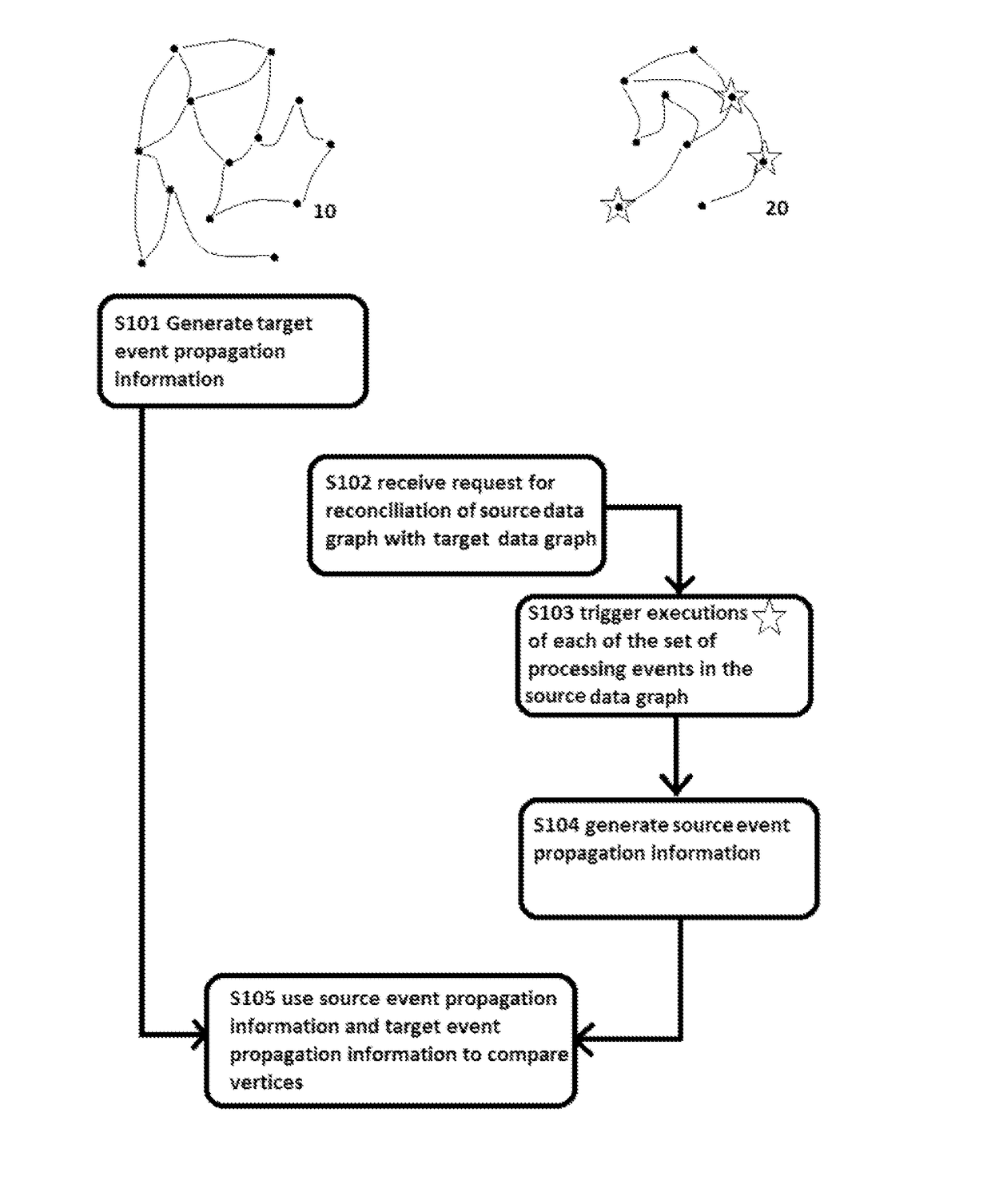
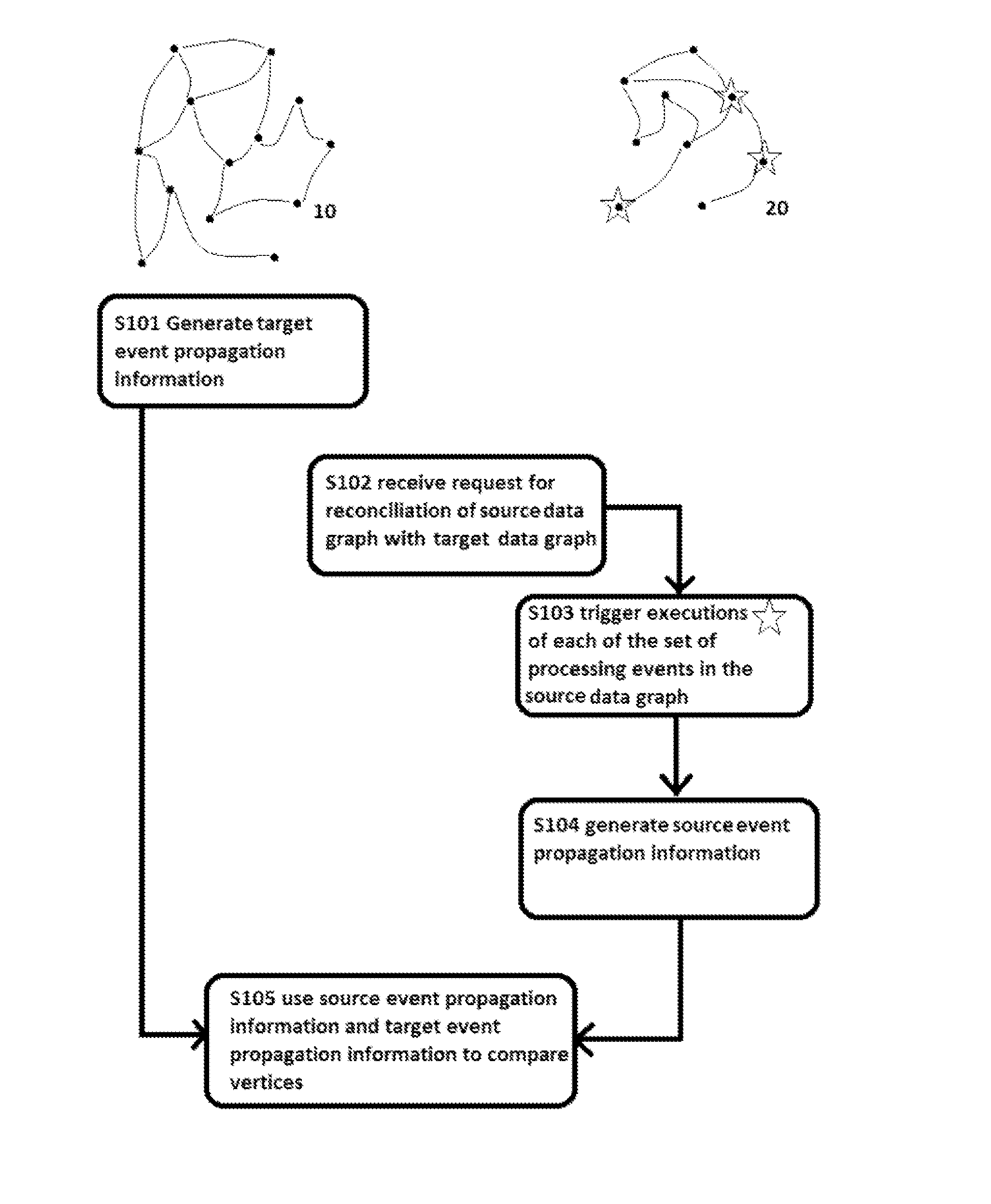
Method, Controller, Program, and Data Storage System for Performing Reconciliation Processing
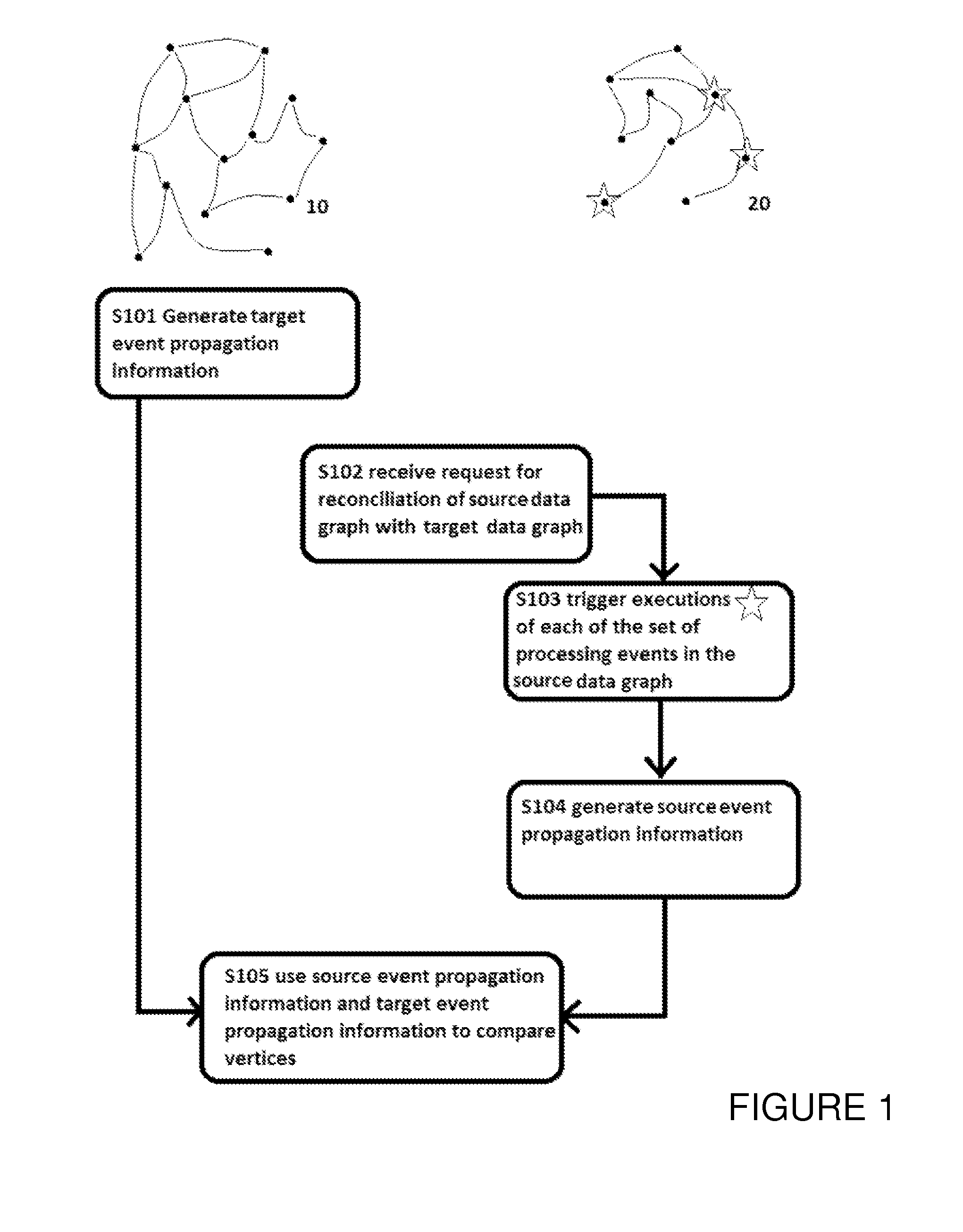
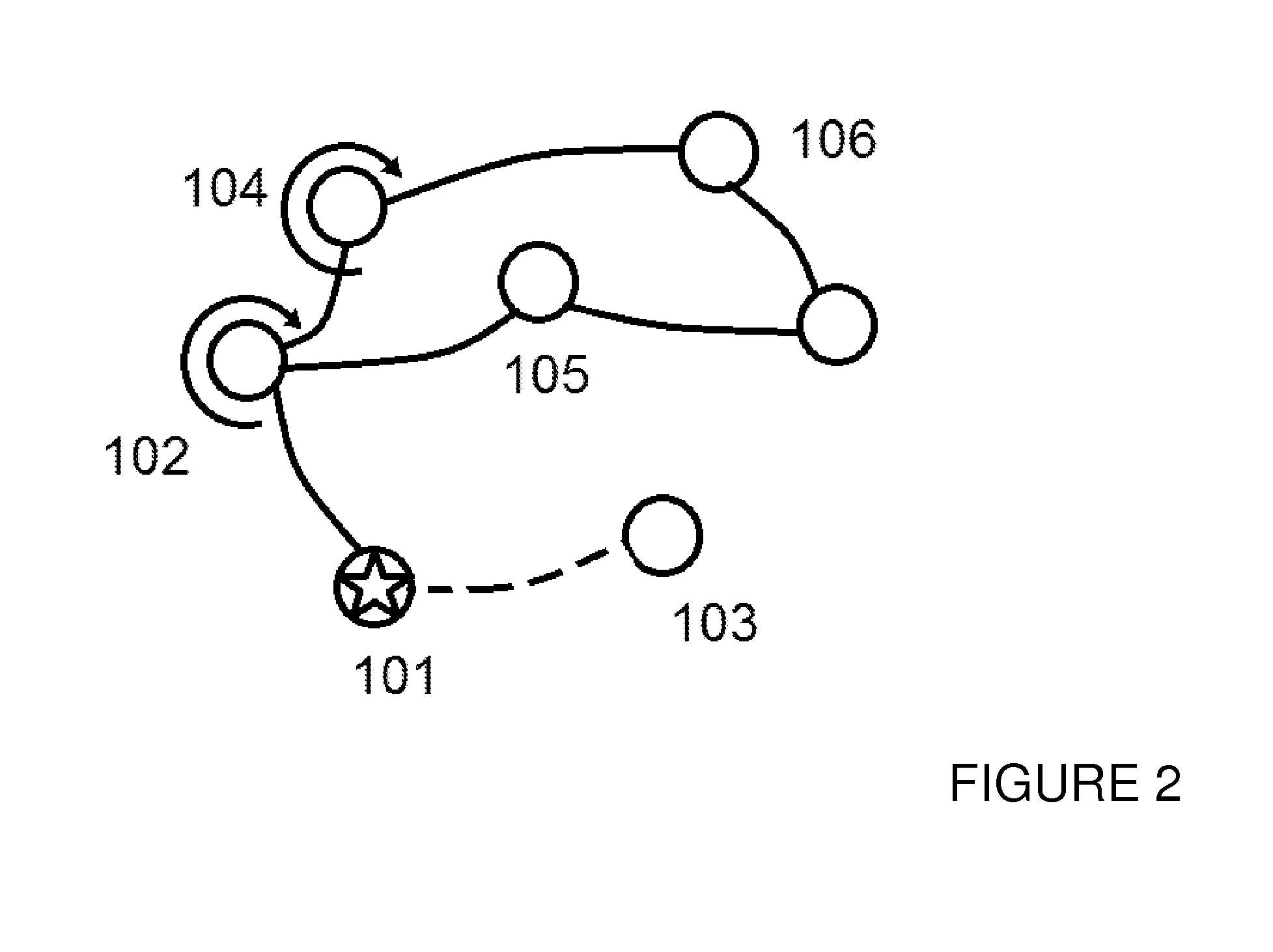
InactiveUS20170177737A9Reduce processing burdenReconciling the data graphsKnowledge representationSpecial data processing applicationsPropagation patternAlgorithm
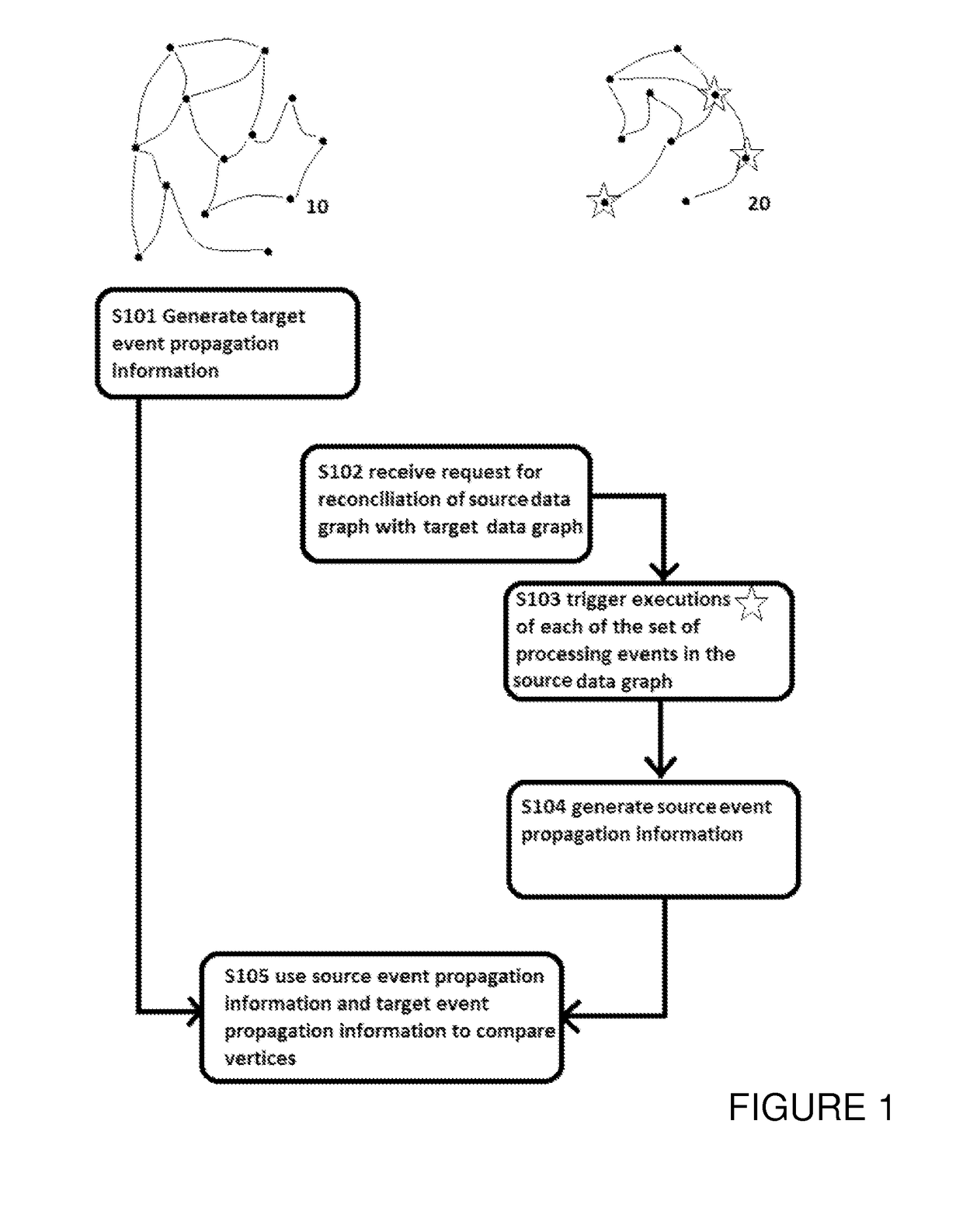
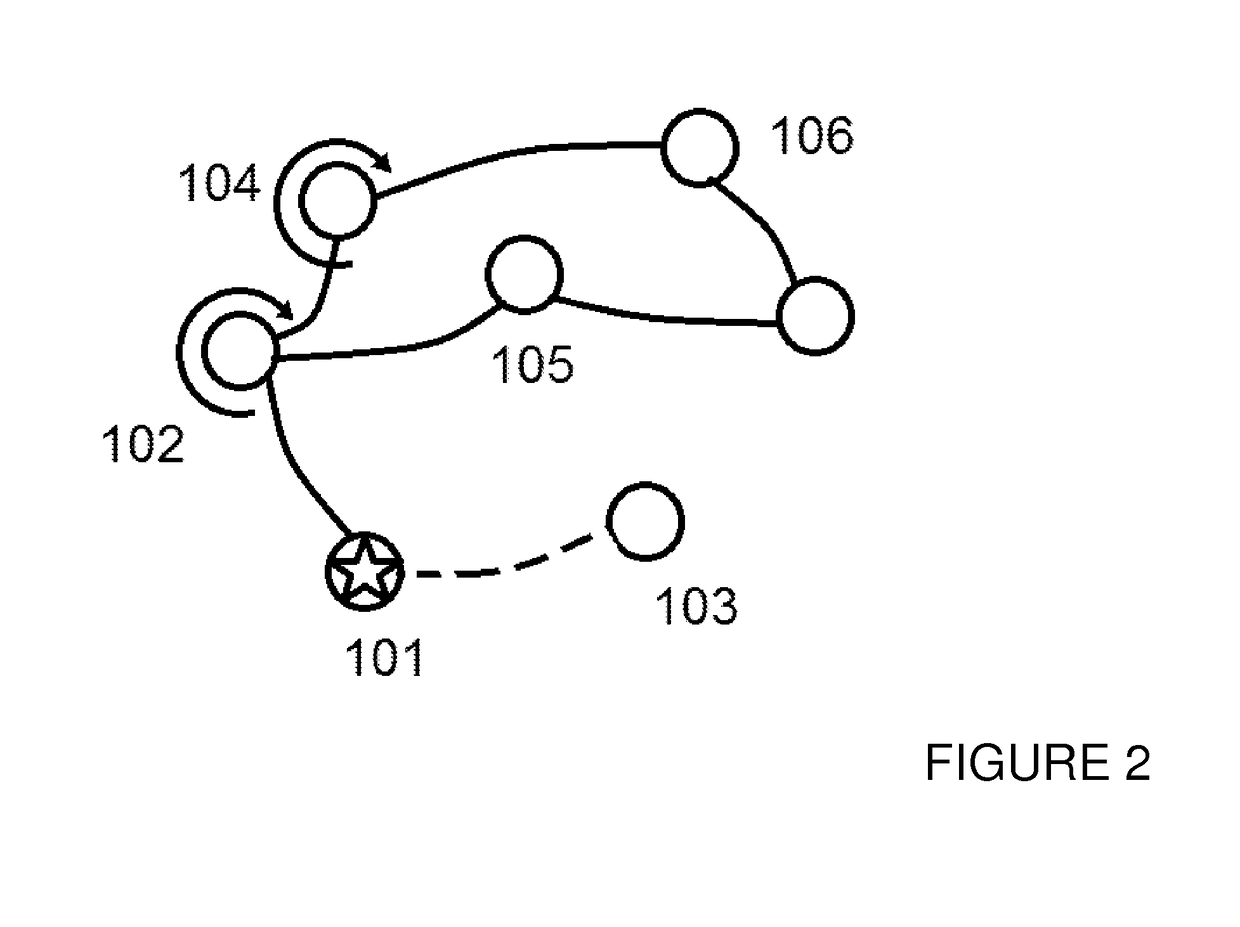
A method for reconciling a source data graph with a target data graph, the source graph and the target graph each comprising: and a interconnections, the interconnections each connecting two vertices from and representing a relationship between the connected vertices. The method comprises: generating target event propagation information representing the propagation pattern of executions of each of a set of processing events in the target graph; receiving a request to reconcile the source and graph, and in response to the request, triggering the executions of each of the set in the source graph; generating source event propagation information representing the pattern of each of the executions triggered in the source graph; and using the target event propagation information and the source event propagation information to assess the similarity of pairs of vertices comprising one vertex from each of the source graph and the target graph.
Owner:FUJITSU LTD
Method for performing two-dimensional graphic layer drawing and event handling by using Qt
ActiveCN106815029ASimplify the drawing processSpecific program execution arrangementsGraphicsOverlap zone
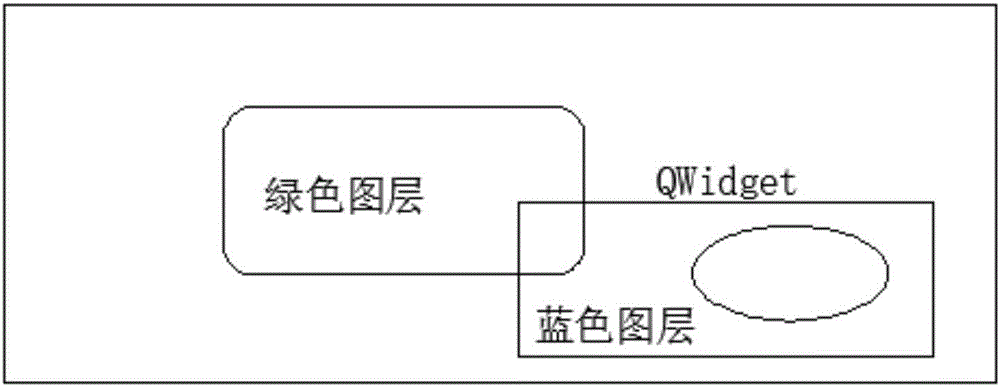
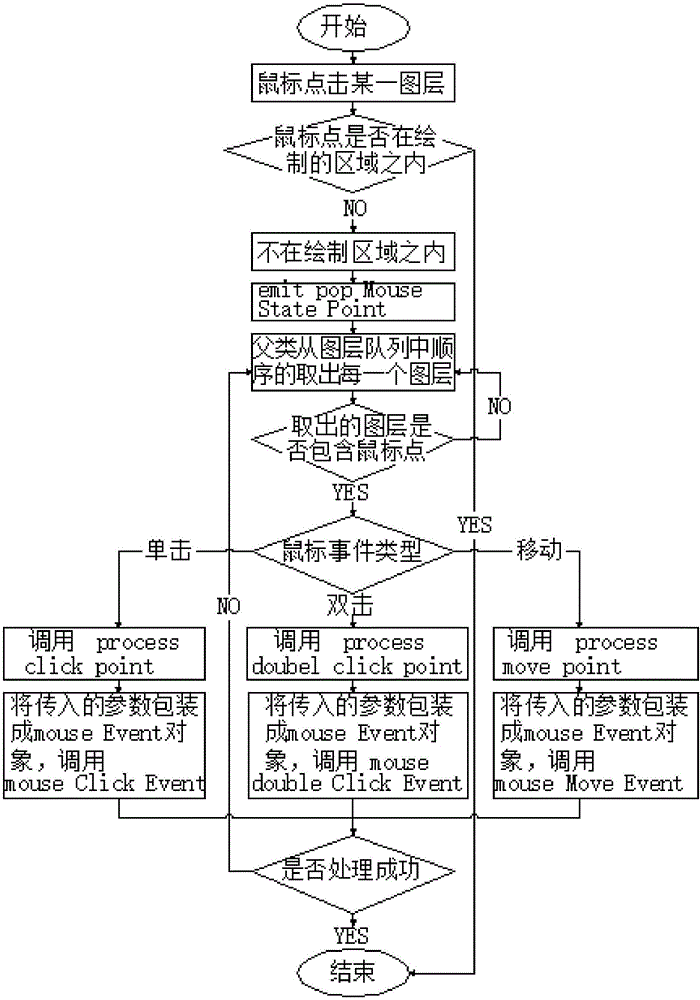
The invention discloses a method for performing two-dimensional graphic layer drawing and event handling by using Qt. The method extracts out different basic graphic drawing conditions and combines with gesture operation, and the drawing process is simplified. State management is conducted on the drawn graphic layer. When multiple graphics having overlapped zones are drawn, coordinate mapping is conducted on selection points firstly, conversion from a global coordinate system to a graphic layer internal coordinate system is achieved, then the selection points are reversely transmitted to graphic layers according to a queue creating sequence, different position relation judging algorithms are automatically called according to the types of the graphic layers, and finally state switching is achieved. In addition, state tracking conducted on produced system events is supported, inter-layer transfer of the produced events is performed, whether the events are needed to be processed or not is judged by the graphic layers till the events are processed or neglected, and state tracking is completed at the moment. The problems of the complicated Qt two-dimensional graphic layer drawing process and non-penetrating event propagation are effectively solved by adopting the method.
Owner:南京仁谷防务科技有限公司
Status synchronization system and its method
Synch state method includes acquiring the first service state edition identification code stored in the first electronic device local buffer cache space; obtaining the second service state edition identification code stored in each second electronic device by inquiring a plurality of second electronic devices; judge whether each second service sate edition identification code is older than the first service state edition identification code; when the second service sate edition identification code is older than the first service state edition identification code, transmit the forward update request to the second electronic device stored with older second service state edition identification code and facilitate the second electronic device start upward examination procedure to update the older second service state edition identification code. The first and the second service state identification code are generated by the third electronic device service. The first, second and third electronic device form a tree structure of event propagation. The third electronic device is positioned on the root node of the tree structure. The first and the second electronic device are positioned on the leaf node of the tree structure.
Owner:BENQ CORP
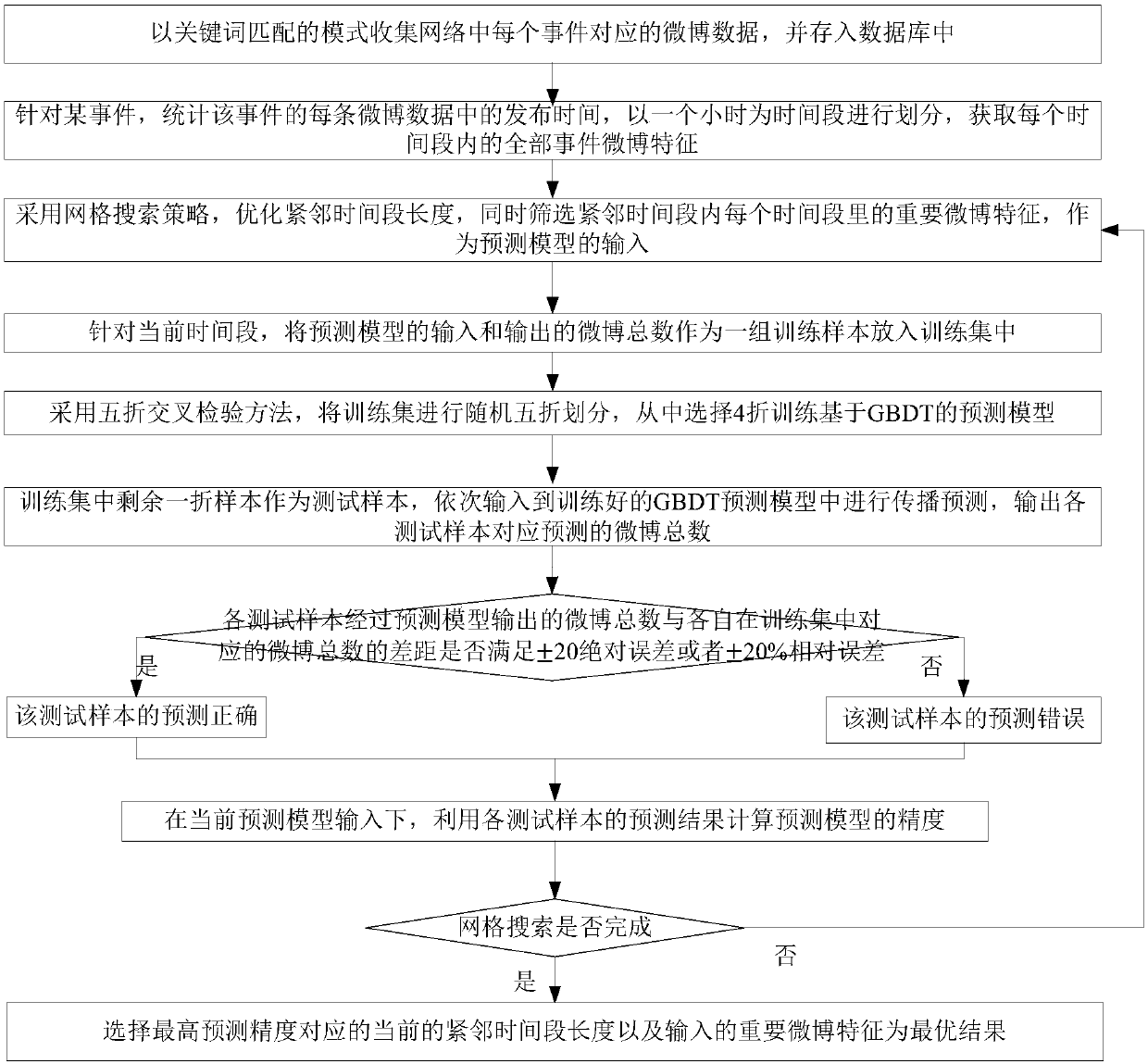
Weibo event information propagation continuous dynamic prediction method
ActiveCN107784387ASupport early warningSupport interventionsForecastingSpecial data processing applicationsData dredgingIntervention measures
The invention discloses a Weibo event information propagation continuous dynamic prediction method, and belongs to the data mining field. The method comprises the following steps: aiming at Sina Weibo, attempting to predict the weibo total quantity of the next phase on the basis of currently given propagation information; hourly dividing event propagation, using the propagation characteristics inthe time period from the event generation to the current moment to predict the event weibo propagation total quantity in the next hour according to a GBDT model, wherein the weibo propagation characteristics include weibo quantity, participation numbers and weibo emotions. The optimal time period length and weibo characteristics are combined in the prediction model, and selected through comprehensively considering each characteristic contribution degree and correlation, thus effectively improving the model prediction precision, enabling the average model precision to exceed 70%, reducing computing complexity, avoiding useless computing, and effectively supporting early warning and intervention measures aiming at the event.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT
User mining method and device in event propagation process
InactiveCN106126740ASolve the problem of not being able to mine important users for specific eventsWeb data indexingSpecial data processing applicationsData miningEvent propagation
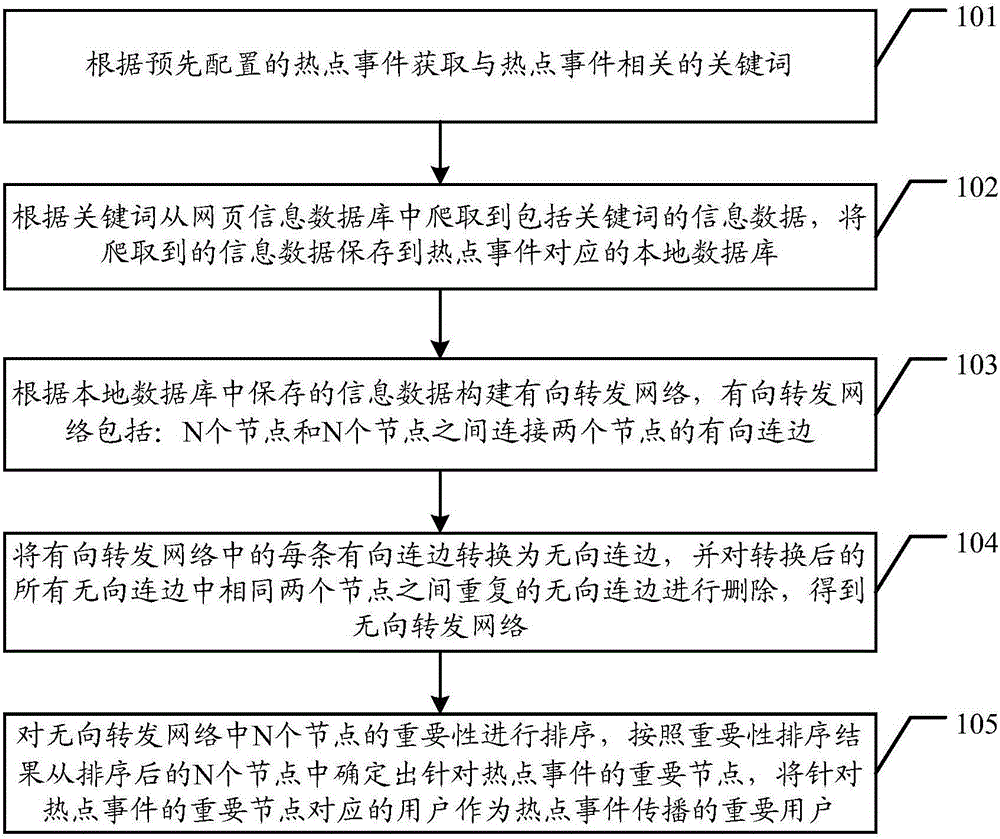
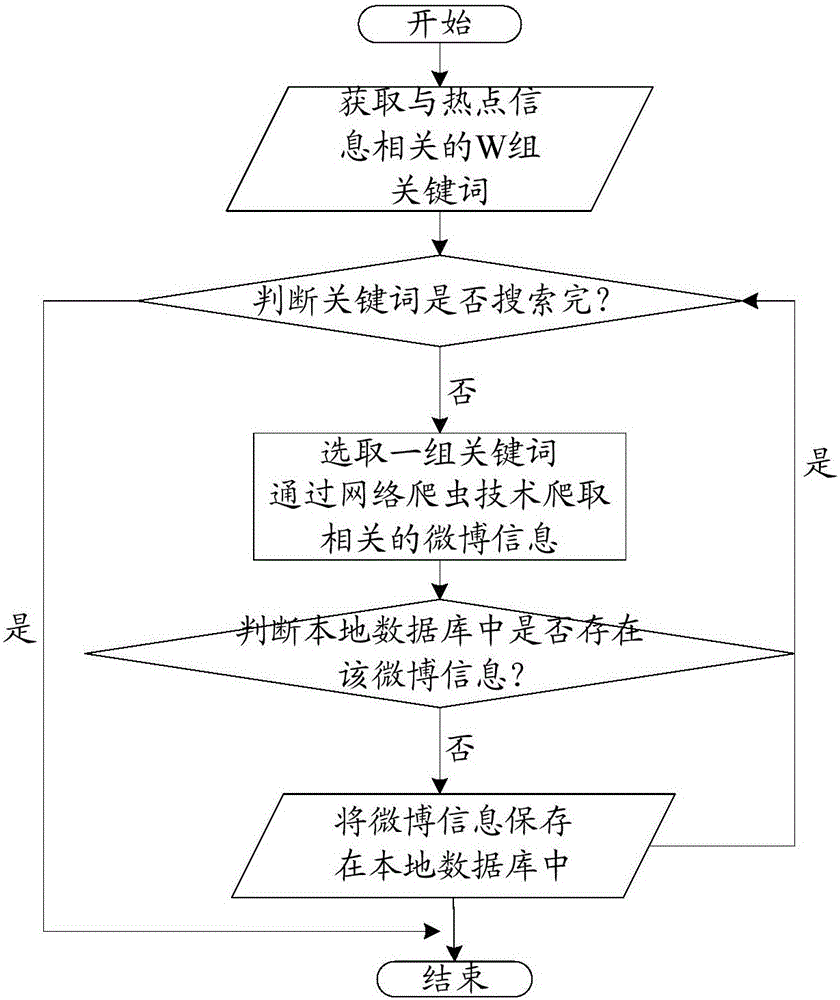
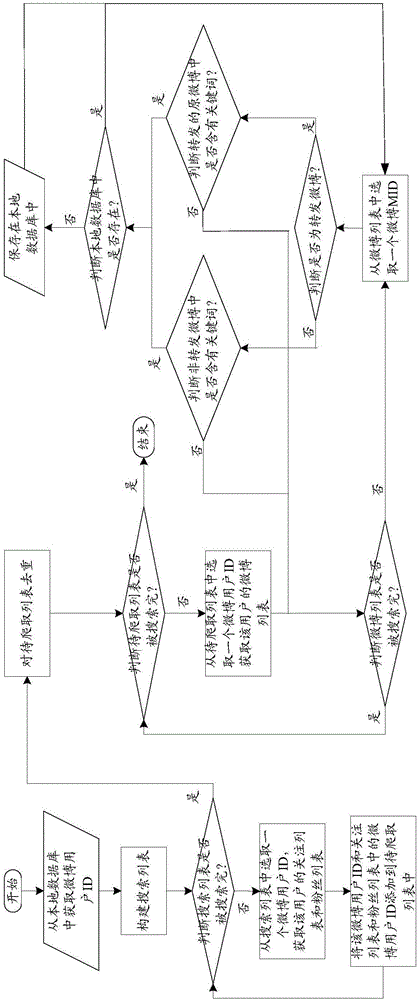
The invention discloses a user mining method and device in an event propagation process, which can be used for mining important users during a hot event propagation process. The method includes: configuring an aimed hot event; establishing a keyword associated with the hot event according to the hot event; crawling information data including the keyword from a webpage information database according to the keyword; and saving the crawled information data in a local database corresponding to the hot event. In this way, the local database can be established from the webpage information database according to the hot event, the local database can establish a directed forward network, and an undirected forward network can be obtained through undirected treatment of the network; and the established undirected forward network is selected according to a certain hot event, and then the important users of hot event propagation can be determined through an importance sequence of nodes.
Owner:HANGZHOU NORMAL UNIVERSITY
Propagation influence evaluation method for comprehensively calculating events
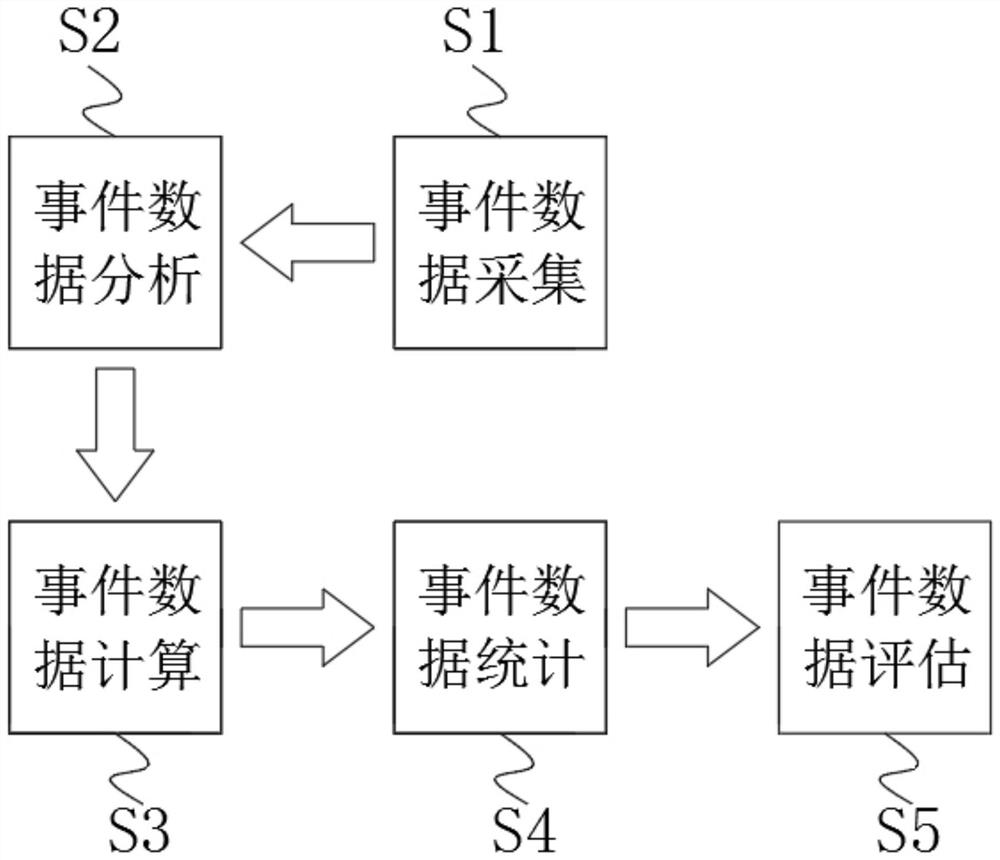
PendingCN112035603AHigh precisionAccurate removalSemantic analysisText database queryingWeb siteSocial media
The invention discloses a propagation influence evaluation method for comprehensively calculating events, which comprises the following steps of: S1, event data acquisition: firstly, acquiring data related to a specific event in a social media website by using the website of social media and taking a keyword of the specific event as query content, and counting the acquired related data; the invention relates to the technical field of internet propagation. According to the propagation influence evaluation method for the comprehensive calculation event, the user data of which the like number andthe forwarding number exceed the threshold values are independently classified, the event data of which the historical like number and the historical forwarding number are calculated by utilizing theuser data of which the like number and the forwarding number exceed the threshold values, and statistical post-evaluation is carried out in cooperation with the user data; according to the method, malicious assessed user data can be effectively eliminated, the spreading influence of the event can be assessed by comprehensively calculating the event, the basis and reference of hotspot event assessment are provided, and the accuracy of the assessment method for comprehensively calculating the spreading influence of the event is greatly improved.
Owner:北京宏博知微科技有限公司
Cross-platform dissemination trend evaluation and grading method based on specific events
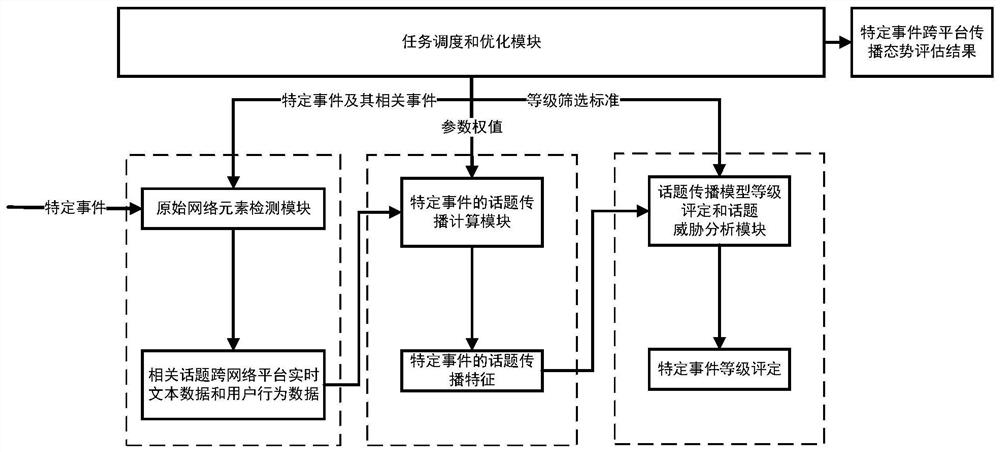
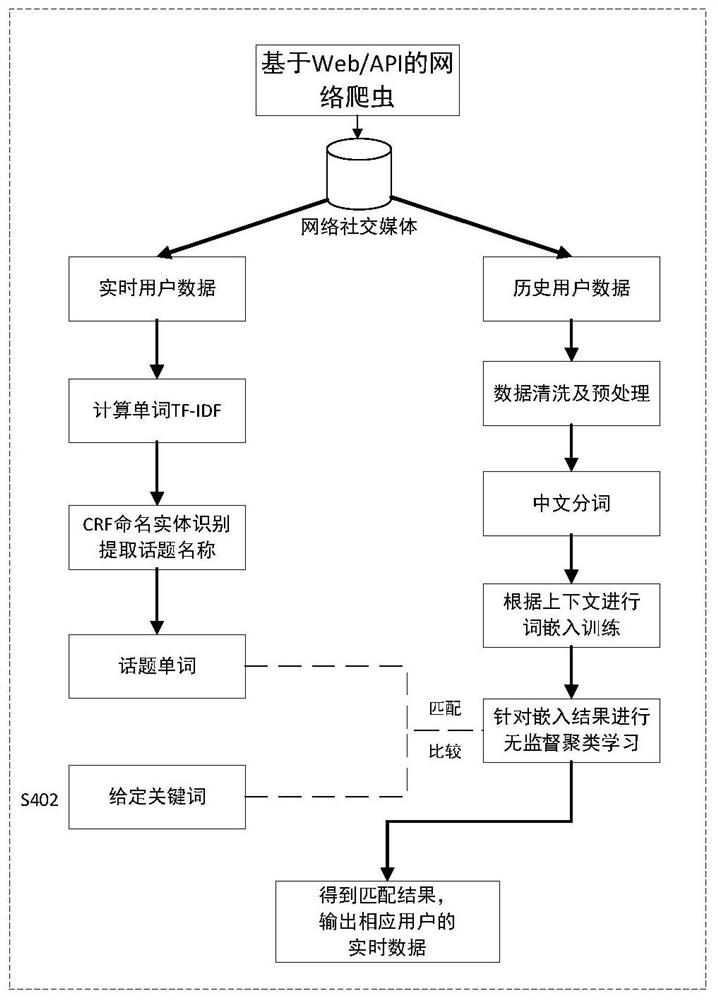
ActiveCN111949848AEasy to detectRealization of graded assessmentWeb data indexingNatural language data processingEngineeringData mining
The invention relates to a cross-platform dissemination trend evaluation and grading method based on specific events, and belongs to the field of network information. The cross-platform disseminationtrend evaluation and grading method based on the specific event specifically comprises four functional modules, namely an original network element detection module, a topic propagation calculation module of the specific event, a grade evaluation and threat analysis module of topic dissemination model parameters, and a task scheduling and optimization module. The problem that a dissemination trendevaluation and grading method of events is not considered in the prior art is solved, a quantitative evaluation method for specific event dissemination situations and a grading means with discrimination are provided, an information system framework is established, and cross-platform dissemination trend evaluation and grading of the specific events are realized. The subsequent monitoring work is guided according to the cross-platform dissemination trend evaluation of the specific events, so that the judgment capability on the emergency or influence degree of event dissemination is effectively improved, and the actual work is guided.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT
Method, Controller, Program, and Data Storage System for Performing Reconciliation Processing
InactiveUS20160171121A1Reduce processing overheadReduce processing burdenDigital data processing detailsKnowledge representationData graphAlgorithm
A method for reconciling a source data graph with a target data graph, the source graph and the target graph each comprising: and a interconnections, the interconnections each connecting two vertices from and representing a relationship between the connected vertices. The method comprises: generating target event propagation information representing the propagation pattern of executions of each of a set of processing events in the target graph; receiving a request to reconcile the source and graph, and in response to the request, triggering the executions of each of the set in the source graph; generating source event propagation information representing the pattern of each of the executions triggered in the source graph; and using the target event propagation information and the source event propagation information to assess the similarity of pairs of vertices comprising one vertex from each of the source graph and the target graph.
Owner:FUJITSU LTD
Synchronization of data between systems
InactiveUS9047358B2Digital data processing detailsDatabase distribution/replicationData synchronizationData system
Owner:INT BUSINESS MASCH CORP
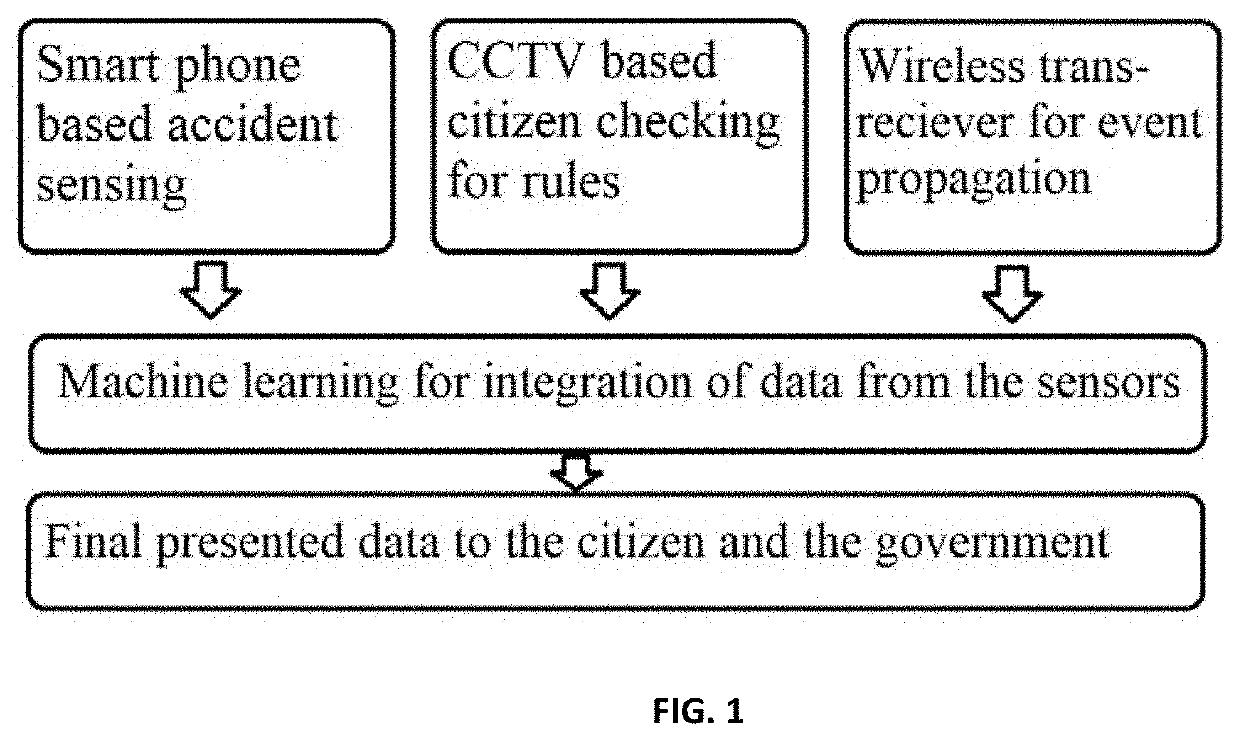
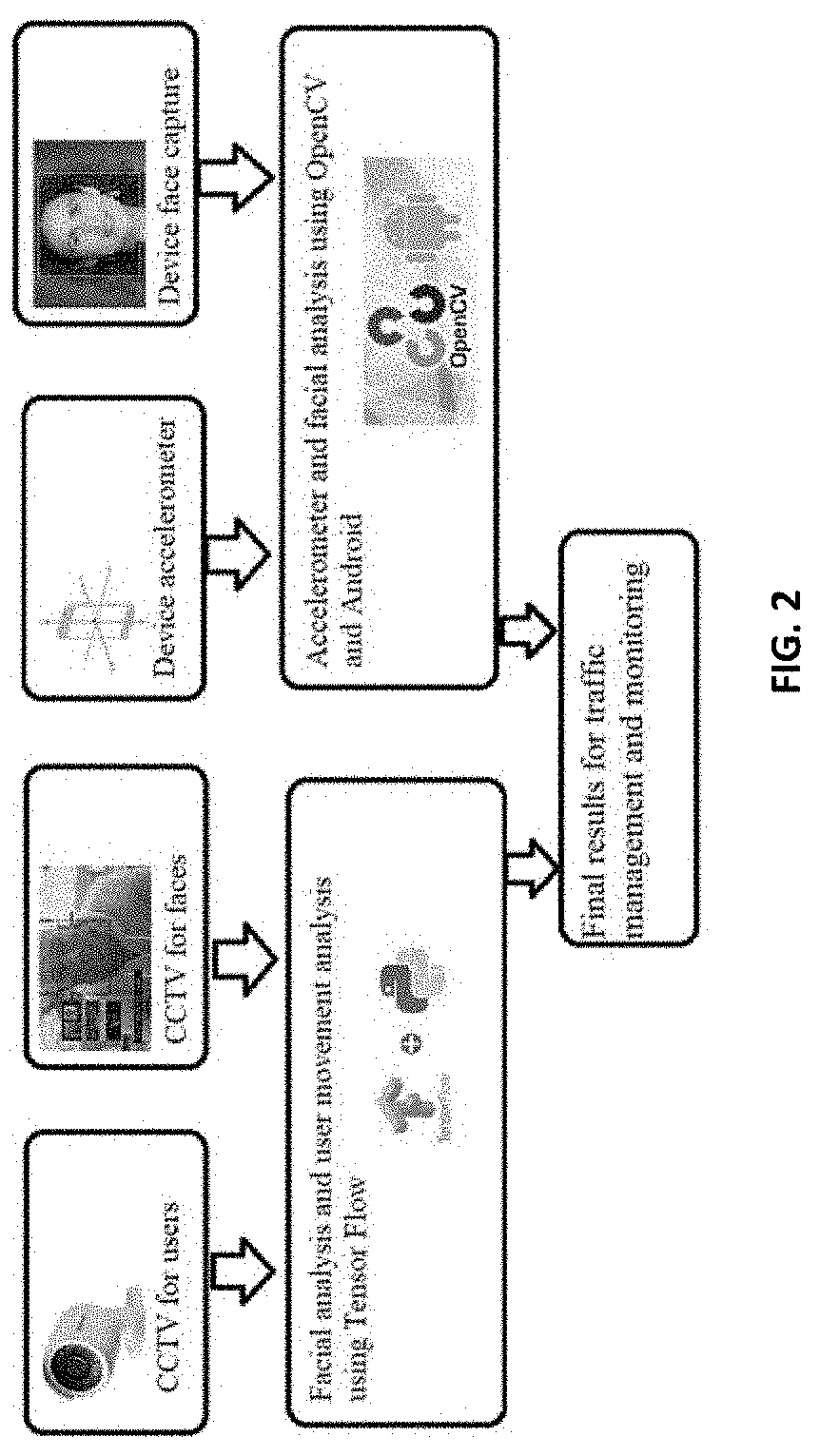
Tracking and alerting traffic management system using IoT for smart city
ActiveUS20210134146A1Improve traffic efficiencySimple structureControl with pedestrian guidance indicatorCharacter and pattern recognitionInternet privacySmart city
Tracking and alerting Traffic management system using IoT for smart city to determine a social distance or norms violation between a plurality of communicative pairs, each of the image have plurality of communicative pairs including two communicating entities participating in a corresponding one or more of the communicative acts, the system comprising: CCTV for captured User's data i.e User movements, facial data, Smartphone data in case of accident detection; wireless trans-receiver for event propagation and sending the data to database; Sensor for getting the data of smart phones based on GPS system specially in case of accidental case; processor having CNN technology for analyzing and reverting data to control room based and configured to determine the pairwise social distancing based on particular behavior like movement and stopping or falling; hardware for storing data captured based on classification and analyzed parameters; machine learning for integration of data received from processor or sensors for visualization and processing final data to the citizens or to governments for monitoring and sending data to alarming sensor for non instructive alert if violations of social distancing norms.
Owner:MESHRAM KUNDAN
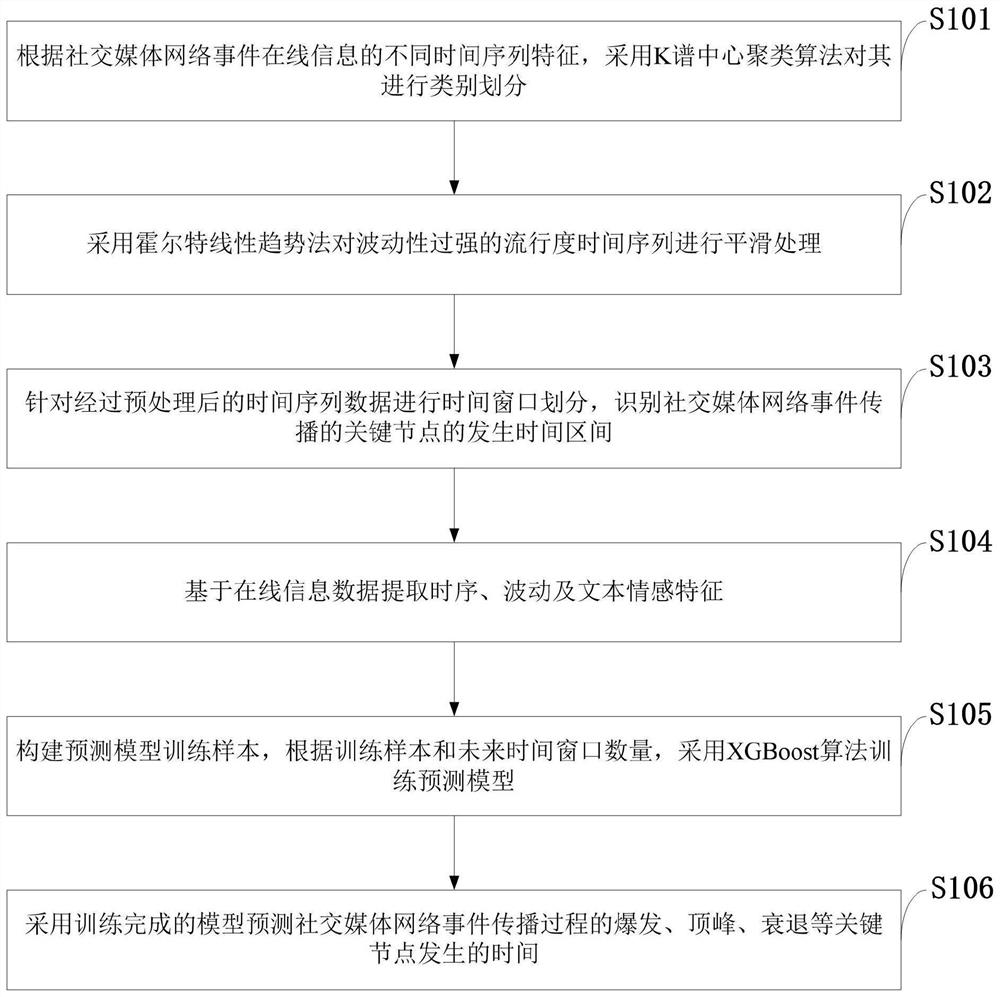
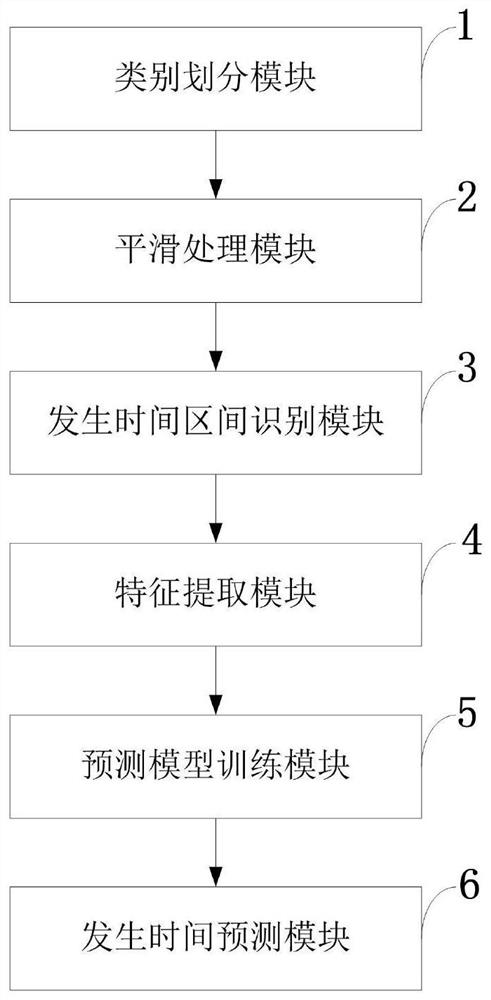
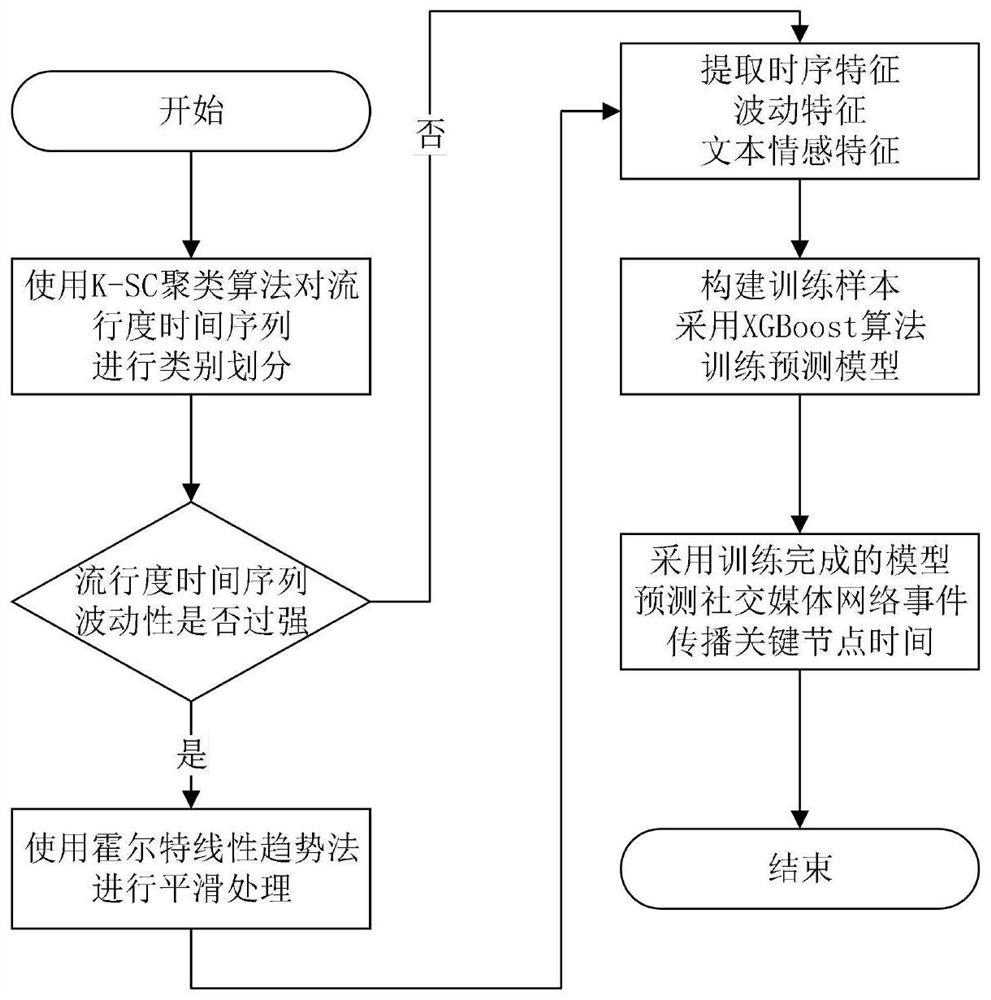
Social media network event propagation key time prediction method, system, and medium
PendingCN112418269AGrasp the communication trendAccurate classificationMultimedia data queryingForecastingInformation propagationSocial media network
The invention belongs to the technical field of online information propagation prediction, and discloses a social media network event propagation key time prediction method, a system, and a medium. The method comprises the steps: carrying out the classification according to different time sequence features of social media network event online information; carrying out smoothing processing on the popularity time sequence with too strong volatility by adopting a Hort linear trend method; recognizing a time interval in which a key node propagated by the preprocessed social media network event occurs; carrying out time window division on the preprocessed time series data, and extracting time series, fluctuation and text emotion features based on online information data; constructing a prediction model training sample, and training a prediction model by adopting an XGBoost algorithm according to the training sample and the number of future time windows; and predicting the occurrence time ofthe key nodes in the event propagation process of the social media network by adopting the trained model. The method can effectively predict the occurrence time of the key node in the event propagation process of the social media network.
Owner:XIDIAN UNIV +1
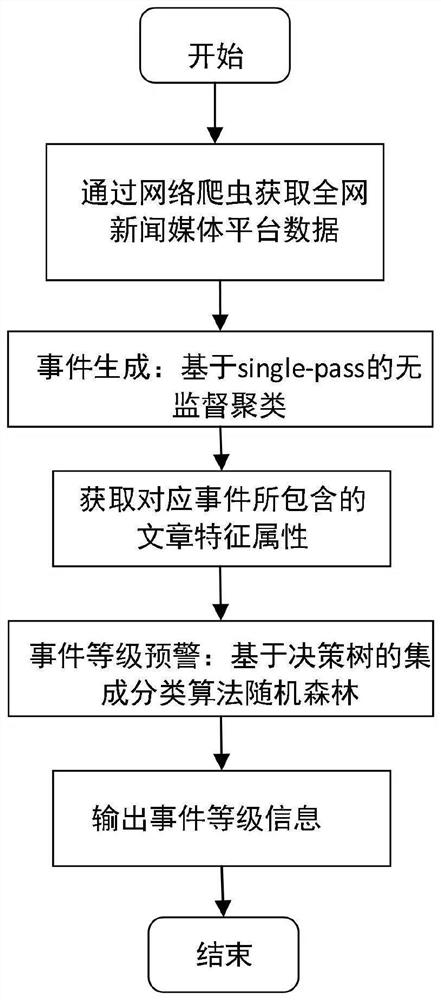
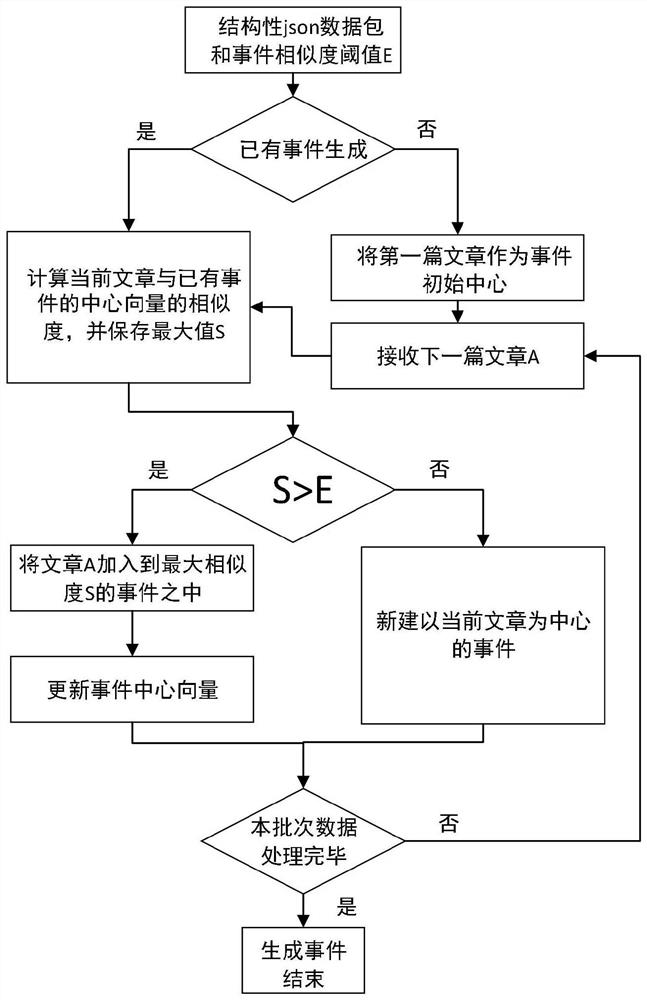
Internet public opinion event automatic early warning system based on event propagation characteristics
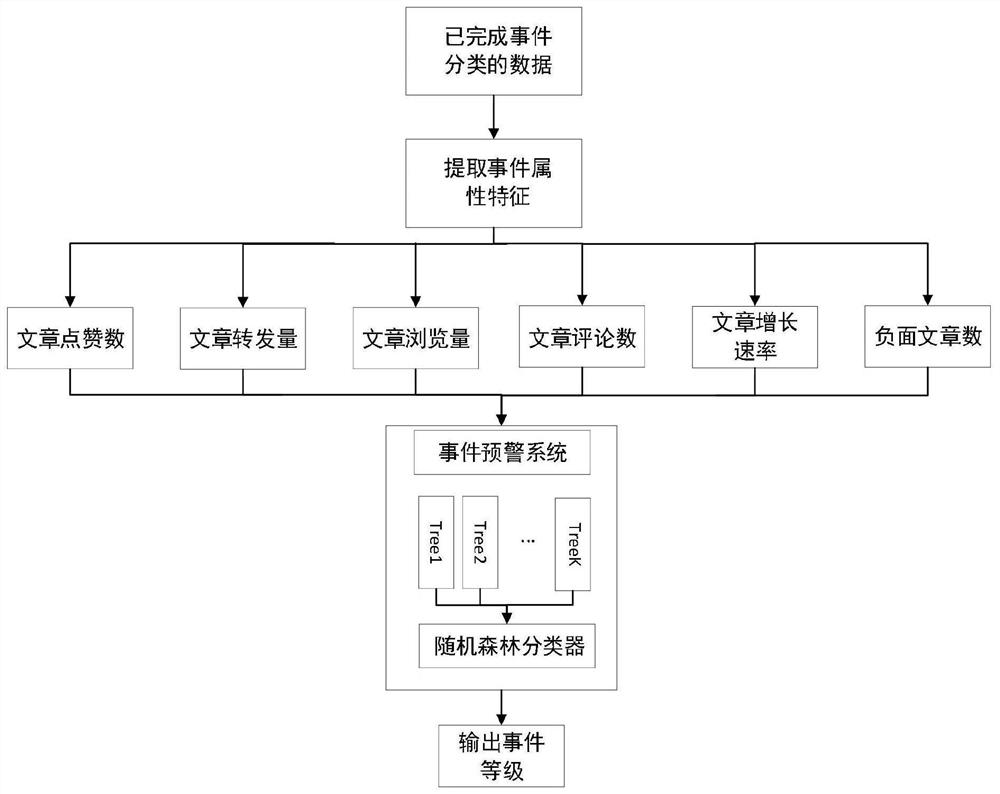
The invention relates to an internet public opinion event automatic early warning system based on event propagation characteristics, which comprises a data acquisition module, a data preprocessing module, an event forming module, a characteristic capturing module and a decision making module which are connected in sequence, the data acquisition module obtains news message data of all media platforms of the whole network through a crawler system, carries out primary processing and outputs a basic data result to the data preprocessing module, and the data preprocessing module cleans disordered data in various formats from the whole network. The event forming module obtains information from the data preprocessing module, carries out event forming processing, carries out feature collection on a formed event and outputs features describing event attributes to the decision making module; and the decision-making module carries out decision-making processing according to the characteristics describing the event attributes and finds the most suitable decision-making module parameters through multiple experiments, so that the automatic public opinion event early warning function is completed in real time with the maximum accuracy.
Owner:SHANGHAI JIAO TONG UNIV
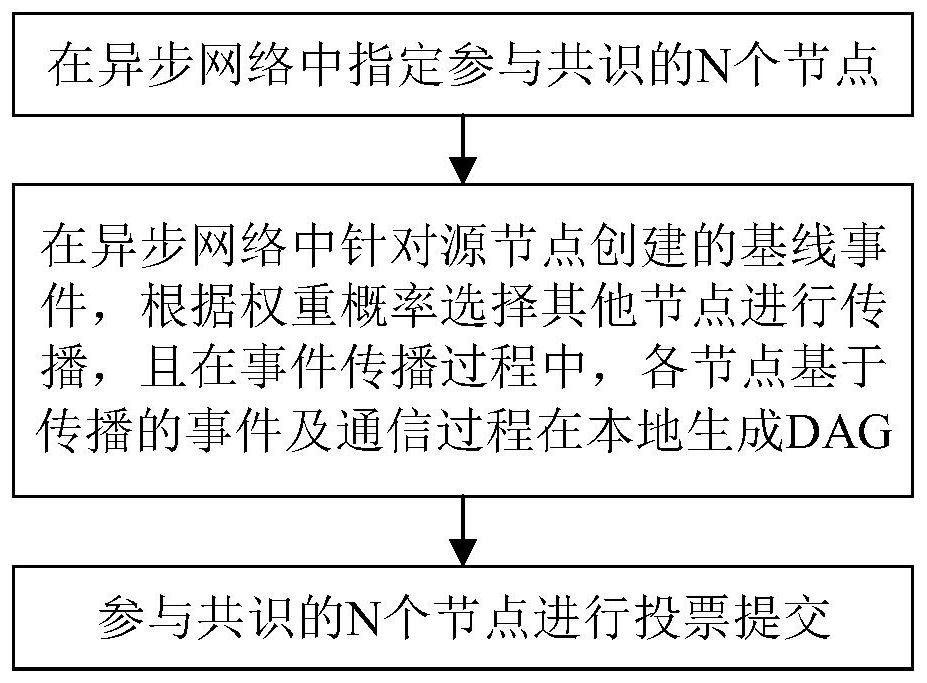
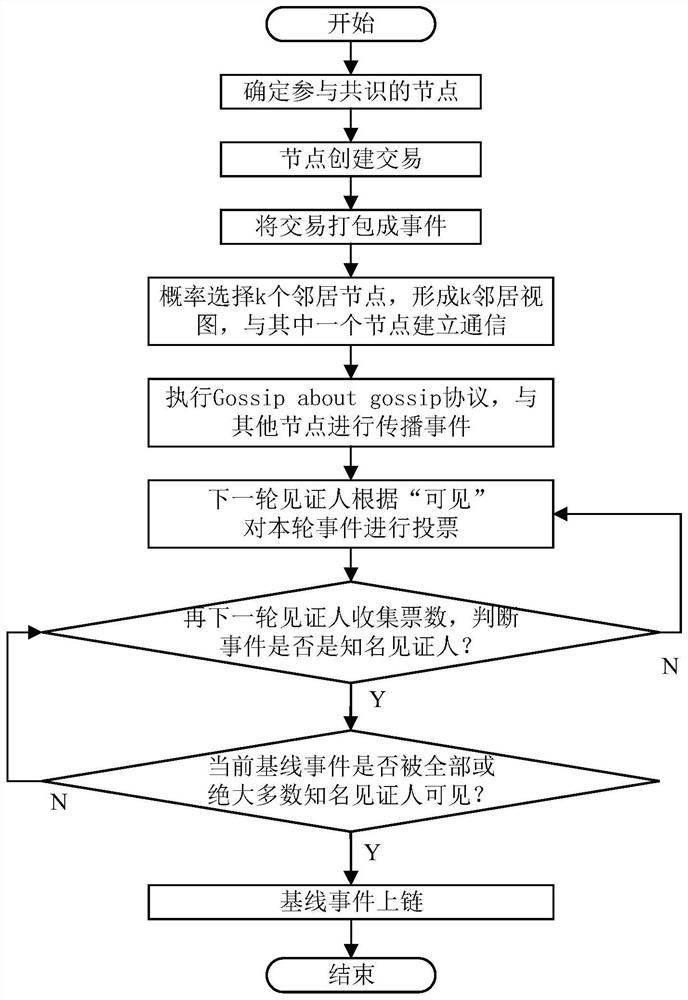
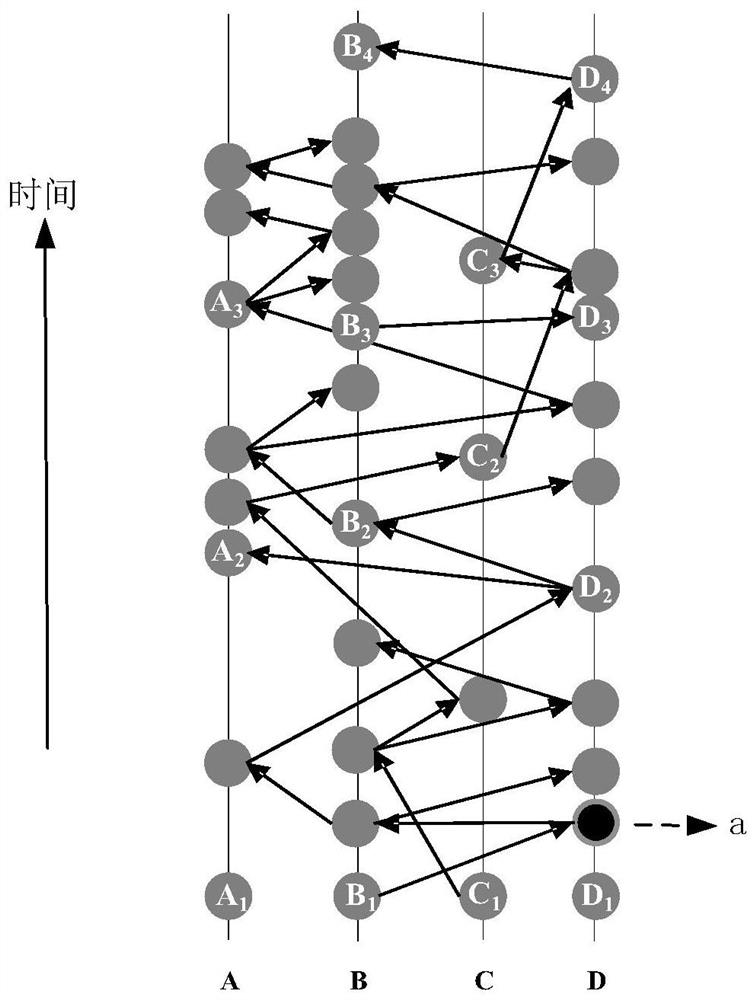
Asynchronous Byzantine consensus method and system based on DAG
PendingCN113923217AHigh degree of decentralizationEnsure fairnessSecuring communicationProtocol authorisationAsynchronous networkNetwork communication
Owner:NAT UNIV OF DEFENSE TECH
Network attack analysis system
InactiveCN106302382AEasy to judgeReasonable responseData switching networksNetwork attackEvent propagation
The invention discloses a network attack analysis system, which comprises an entropy module unit, a triple module unit, a hot event propagation display module unit and a comprehensive association analysis module unit, wherein the entropy module unit reads logs of an intrusion detection system, computes entropy distribution values of source addresses and destination addresses, judges whether a large-scale network security event exists or not and outputs a judging result to the comprehensive association analysis module unit; and the triple module unit reads the logs of the intrusion detection system, merges the logs of the intrusion detection system, and detects and reports abnormal addresses or hot events. According to the analysis system disclosed by the invention, through computing the entropy distribution values of the source addresses and the destination addresses of the logs of the intrusion detection system, the large-scale network security event capable of causing the abnormal address distribution, such as network scanning and distributed denial of service attacks, can be detected.
Owner:LIUZHOU LONGHUI TECH
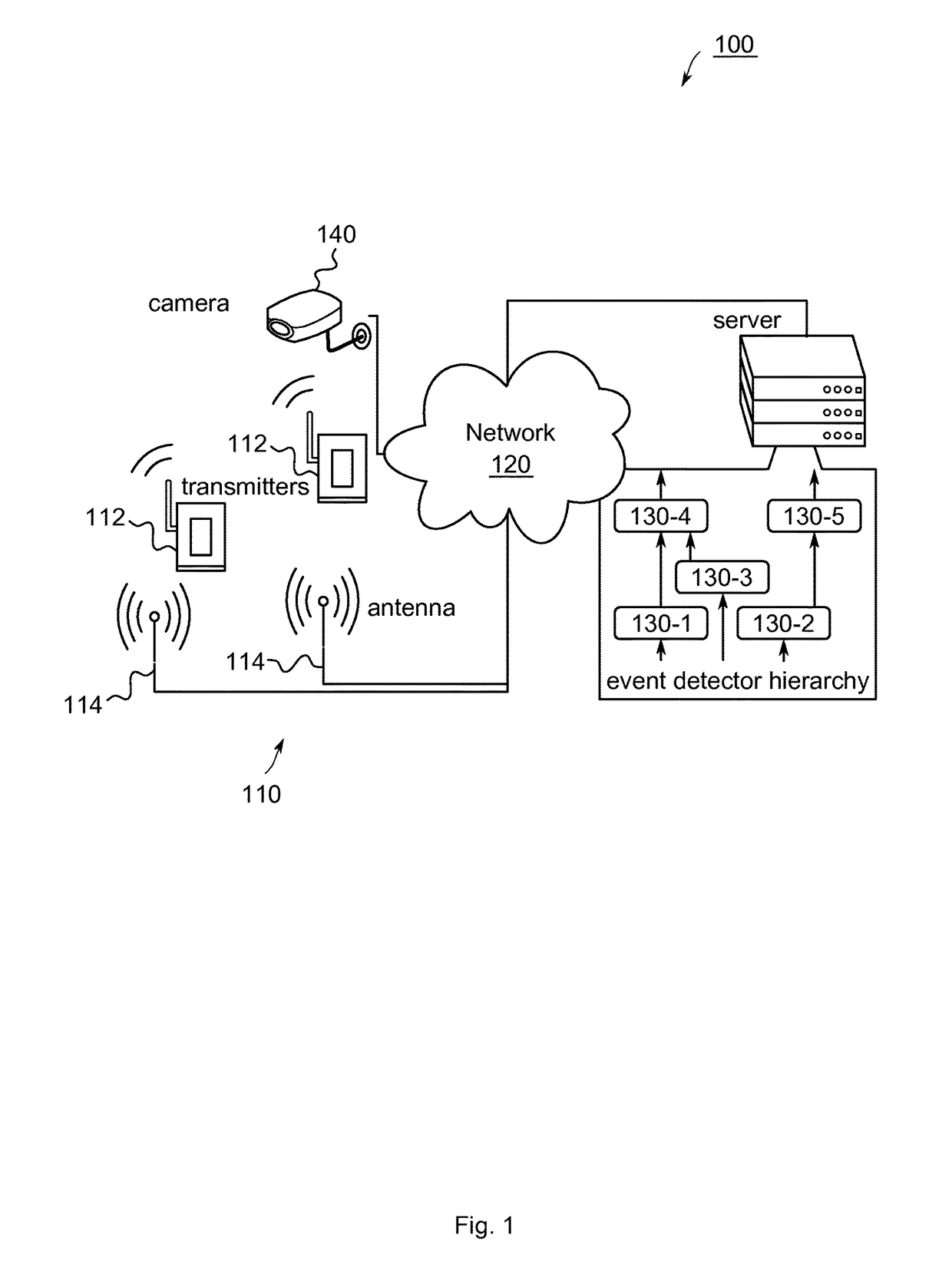
A method and system for correlation analysis of massive logs
InactiveCN101741633BEasy to judgeReasonable responseData switching networksEvent typeCorrelation analysis
The invention discloses a massive log association analysis method and system, which realizes evaluating the current network security status and describing the current attack situation that should be paid most attention to based on the massive logs generated by the intrusion detection equipment. The method includes: obtaining the log of the intrusion detection device, and judging whether there is a large-scale network security event by calculating the distribution status of the source address and the destination address of the log of the intrusion detection device; Intrusion detection device logs are merged to detect and report abnormal addresses and hotspot events; statistics and graphics display the propagation process of hotspot events within a specified time period; correlate the above output results to give a comprehensive evaluation of the current network security status. The system includes an entropy module unit, a triple module unit, a hot event propagation display module unit, and a comprehensive correlation analysis module unit.
Owner:BEIJING VENUS INFORMATION TECH +3
Apparatus, method and computer program for processing out-of-order events
ActiveUS9678811B2Late detectionDigital data information retrievalParticular environment based servicesMaximum latencyParallel computing
Embodiments relate to a concept for ordering events of an event stream, comprising out-of-order events, for an event detector, wherein the events have associated thereto individual event occurrence times (ei·ts) and individual event propagation delays up to a maximum delay of K time units. Event received from the event stream are provided to an event buffer. Received events in the event buffer are ordered according their respective occurrence times to obtain ordered events. An ordered event (ei) having an event occurrence time ei·ts is speculatively forwarded from the event buffer to the event detector at an earliest time instant clk, such that ei·ts+α*K≦clk, wherein α denotes a speculation quantity with 0<α<1.
Owner:FRAUNHOFER GESELLSCHAFT ZUR FOERDERUNG DER ANGEWANDTEN FORSCHUNG EV
Method, device and equipment for simulating network event propagation
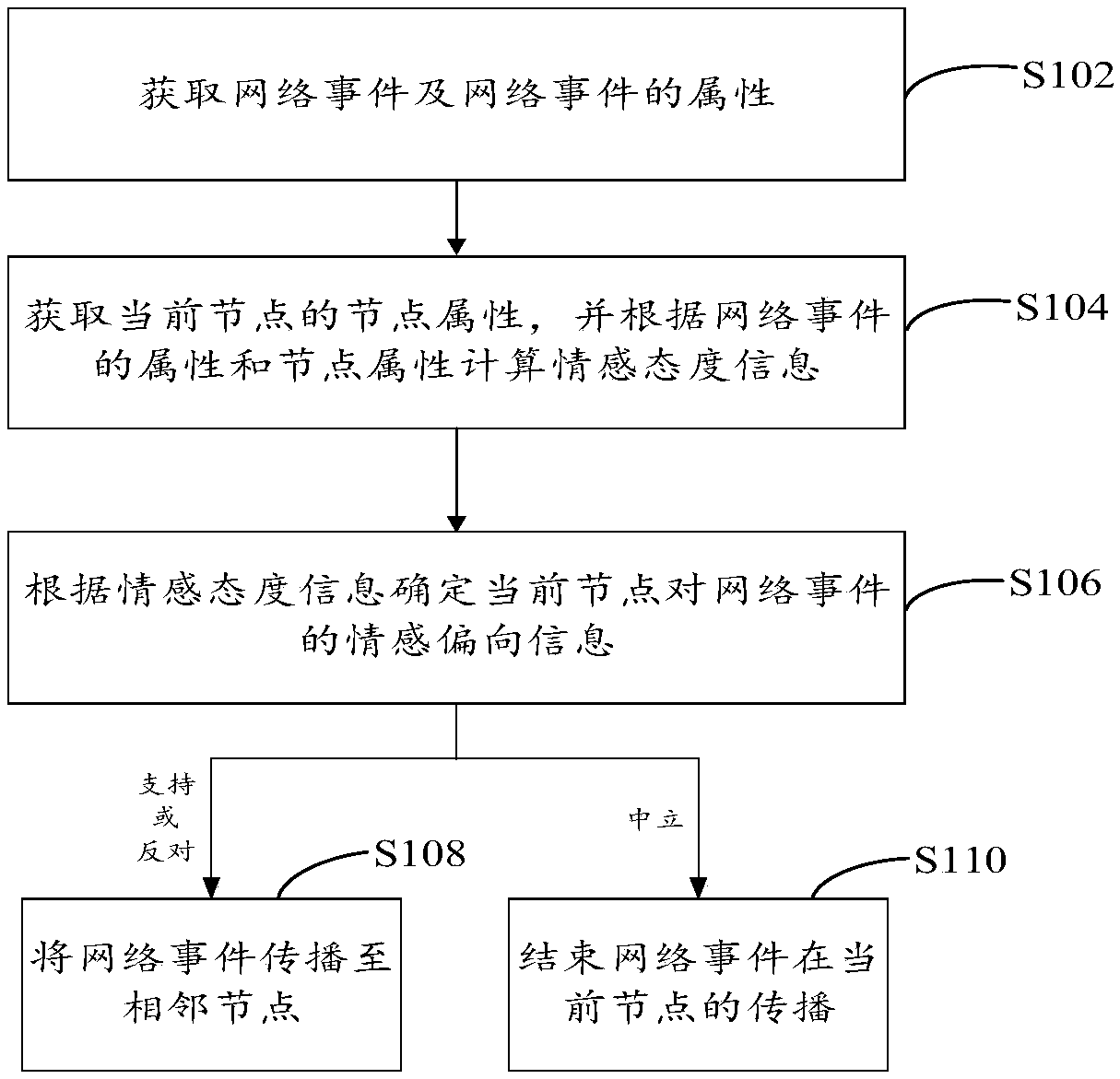
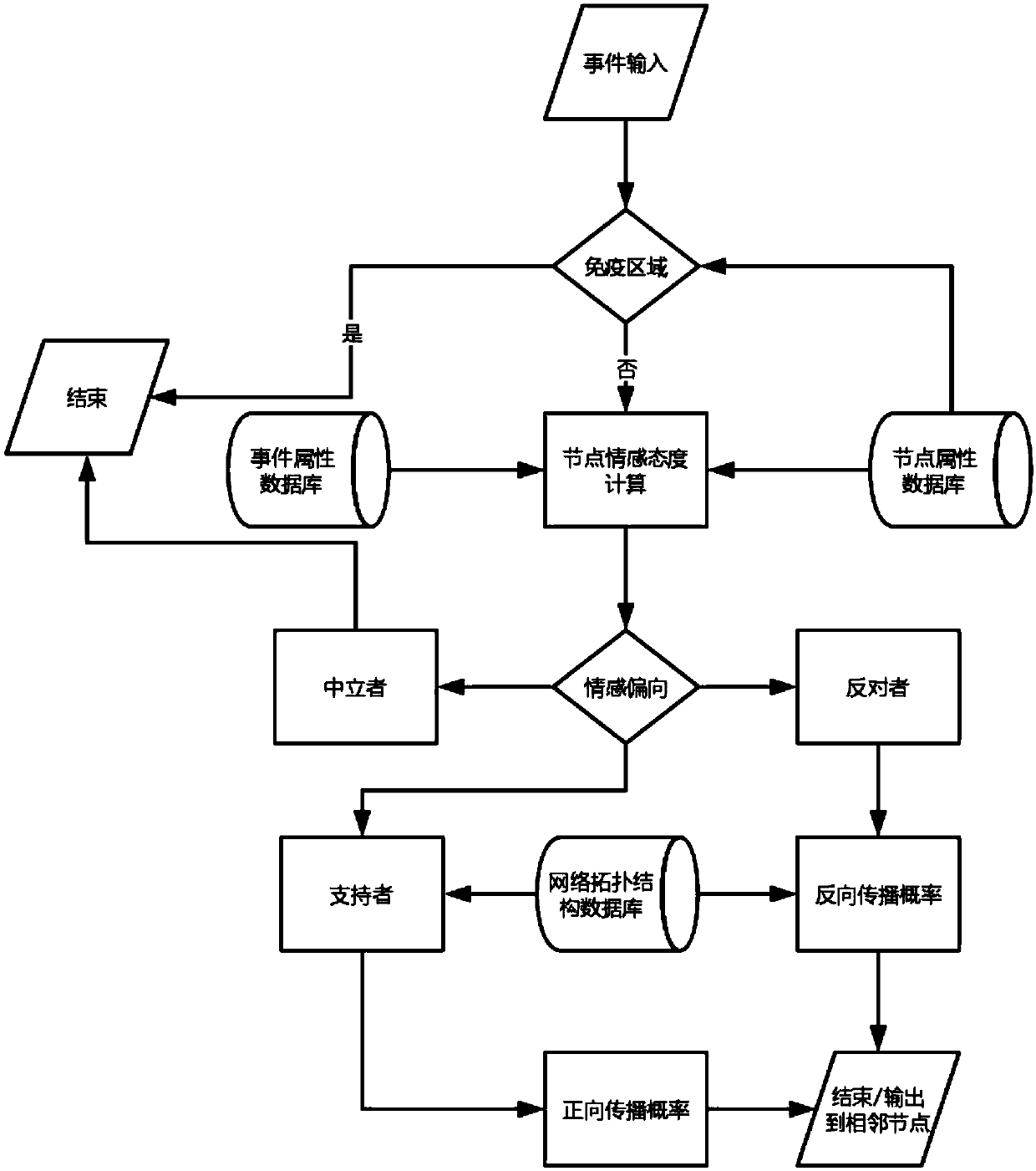
ActiveCN109657139AImprove accuracySuitable for applicationData processing applicationsDigital data information retrievalInformation propagationEvent propagation
The invention provides a simulation method, device and equipment for network event propagation, and relates to the technical field of computers, and the method comprises the steps: obtaining a networkevent and the attribute of the network event; Wherein the attributes at least comprise one of the following attributes: time, type or theme; Obtaining the node attribute of the current node, and calculating emotion attitude information according to the attribute and the node attribute of the network event and the historical emotion attitude information of the previous node; Determining emotionalbias information of the current node to the network event according to the emotional attitude information; Wherein the emotion deviation information is any one of the following information: support, anti-alignment or neutrality; If the emotion deviation information is supported or inversely aligned, the network event is propagated to an adjacent node; And if the emotion deviation information is neutral, ending the propagation of the network event at the current node. According to the method, the emotional attitude information is calculated, so that the accuracy of information propagation process simulation is improved, and the method is more suitable for practical application.
Owner:PEKING UNIV
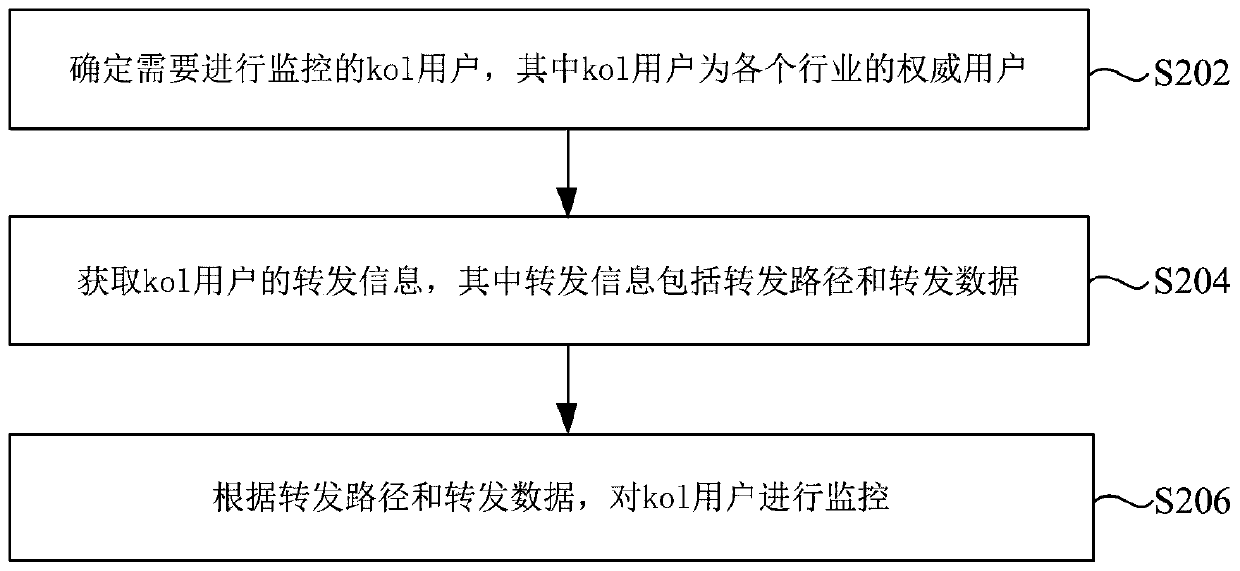
Method and device for monitoring kol account and storage medium
PendingCN110704289AImprove the ability to predict the effect of communicationHardware monitoringResourcesUser needsComputer network
The invention discloses a method and a device for monitoring a kol account and a storage medium. The method comprises: determining a kol user needing to be monitored, and the kol user being an authoritative user of each industry; acquiring forwarding information of the kol user, wherein the forwarding information comprises a forwarding path and forwarding data; and monitoring the kol user according to the forwarding path and the forwarding data. The technical problems that in the prior art, a means for monitoring propagation of a kol user is lacked, the event propagation effect pre-judging capacity is affected, and then public opinion events cannot be found in time are solved.
Owner:数熙科技(北京)有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com