Association analysis method and system for massive logs
A correlation analysis and log technology, applied in the field of information security, can solve problems such as difficult network security conditions, difficulty in understanding system security threats, and security managers spending time on processing useless information.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] Specific embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings.
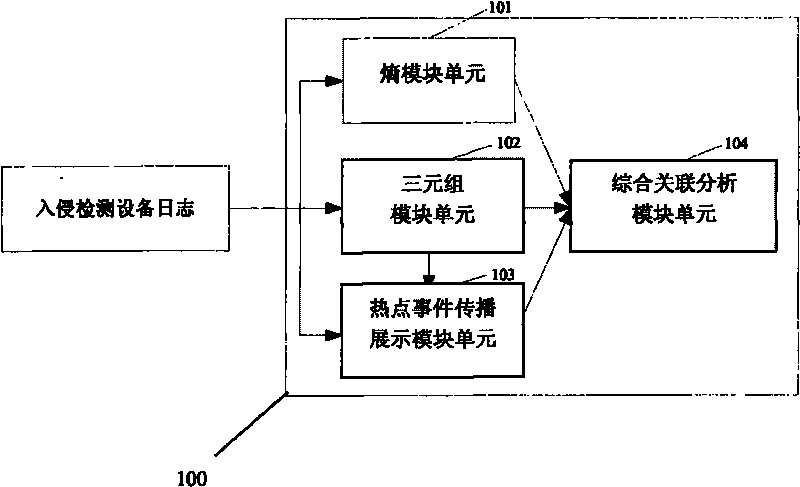
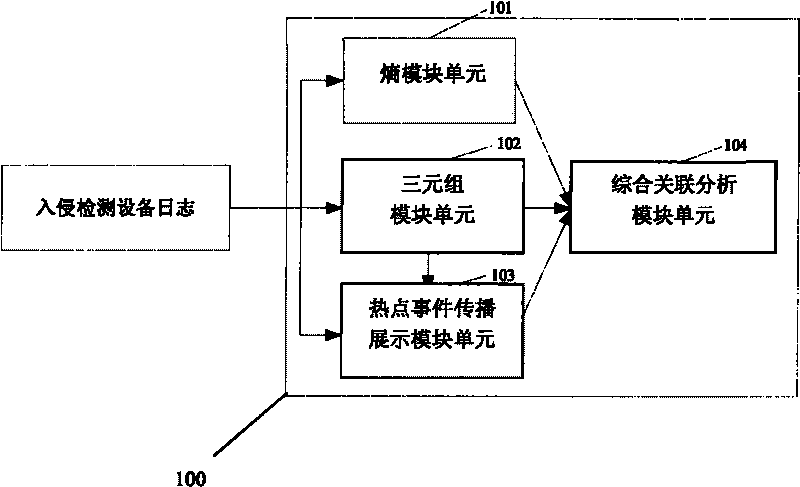
[0042] figure 1 is a schematic structural diagram of a massive log association analysis system according to an embodiment of the present invention. The massive log correlation analysis system 100 according to this embodiment includes an entropy module unit 101 , a triple module unit 102 , a hot event propagation display module unit 103 , and a comprehensive correlation analysis module unit 104 .
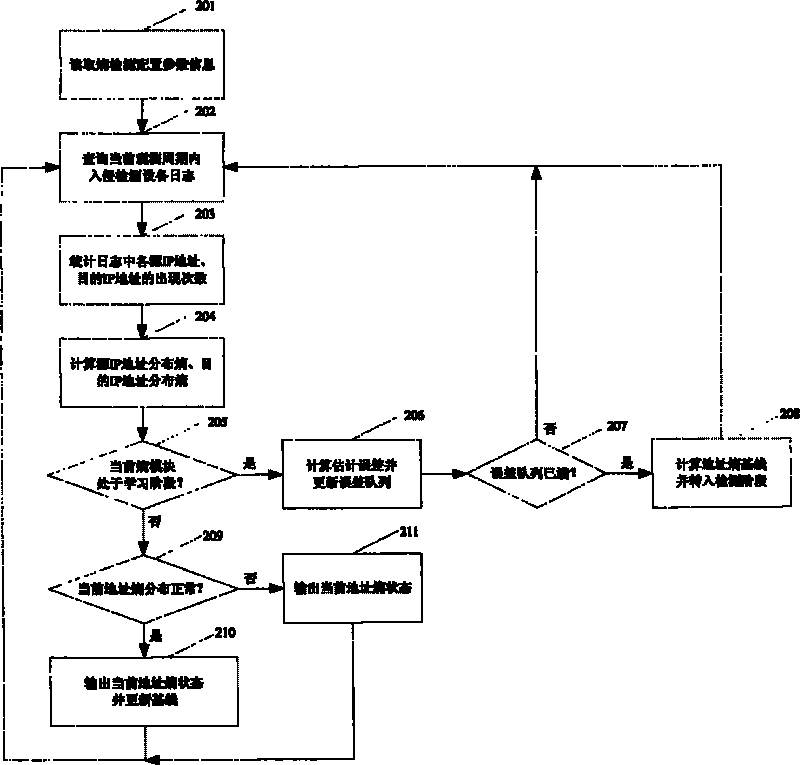
[0043] The entropy module unit 101 is used to read the intrusion detection device log within a specified time period, then calculate the entropy distribution value of the source address and destination address of the intrusion detection device log, judge whether there is a large-scale network security event, and then provide comprehensive correlation analysis The module unit 104 outputs the judgment result of the address distribution status of the c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com