Network invading event risk evaluating method and system
A technology of risk assessment and network intrusion, applied in the direction of transmission system, digital transmission system, data exchange network, etc., can solve the problem of no provision, achieve the effect of reducing false alarm rate, increasing use value, and improving accuracy rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
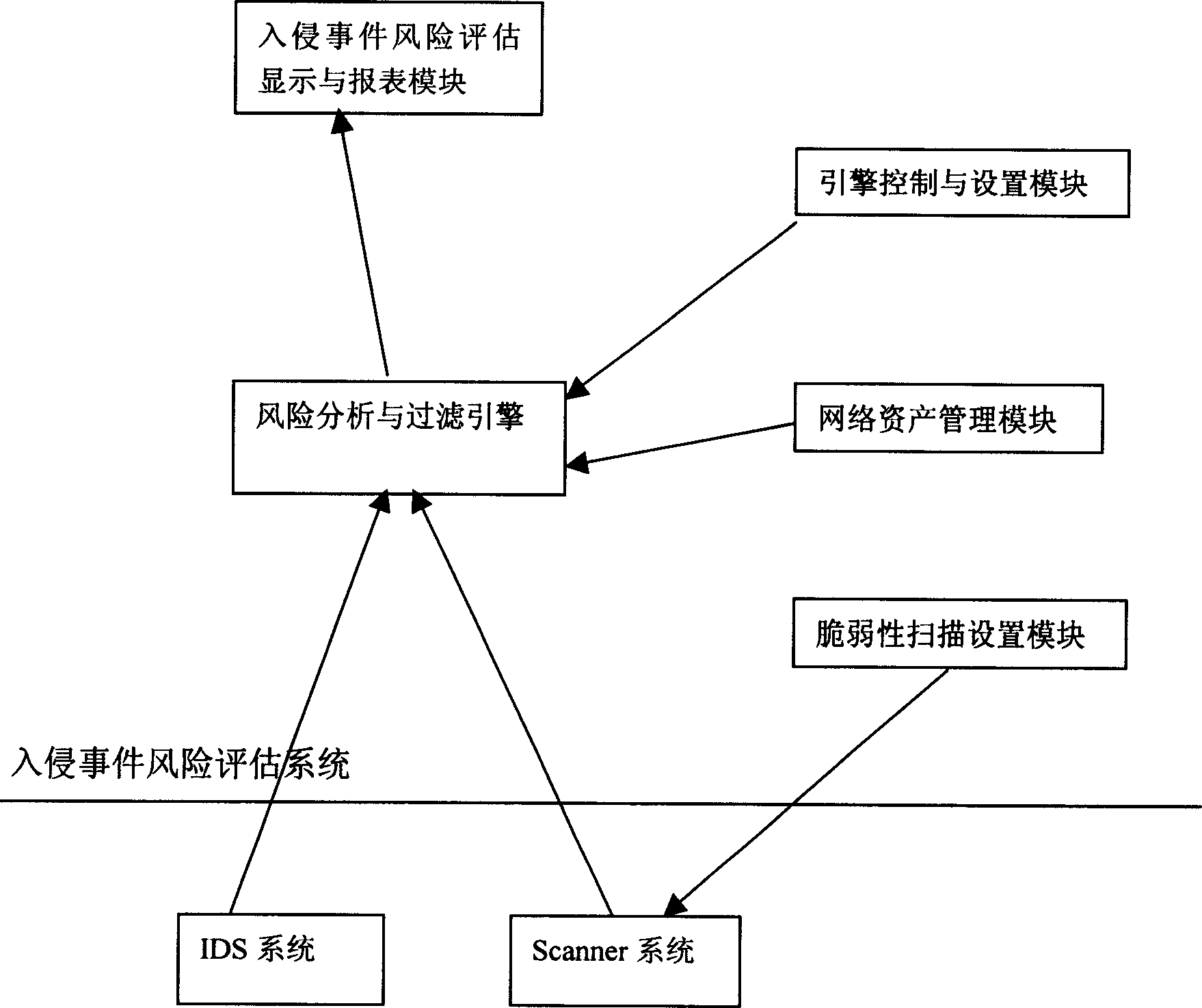
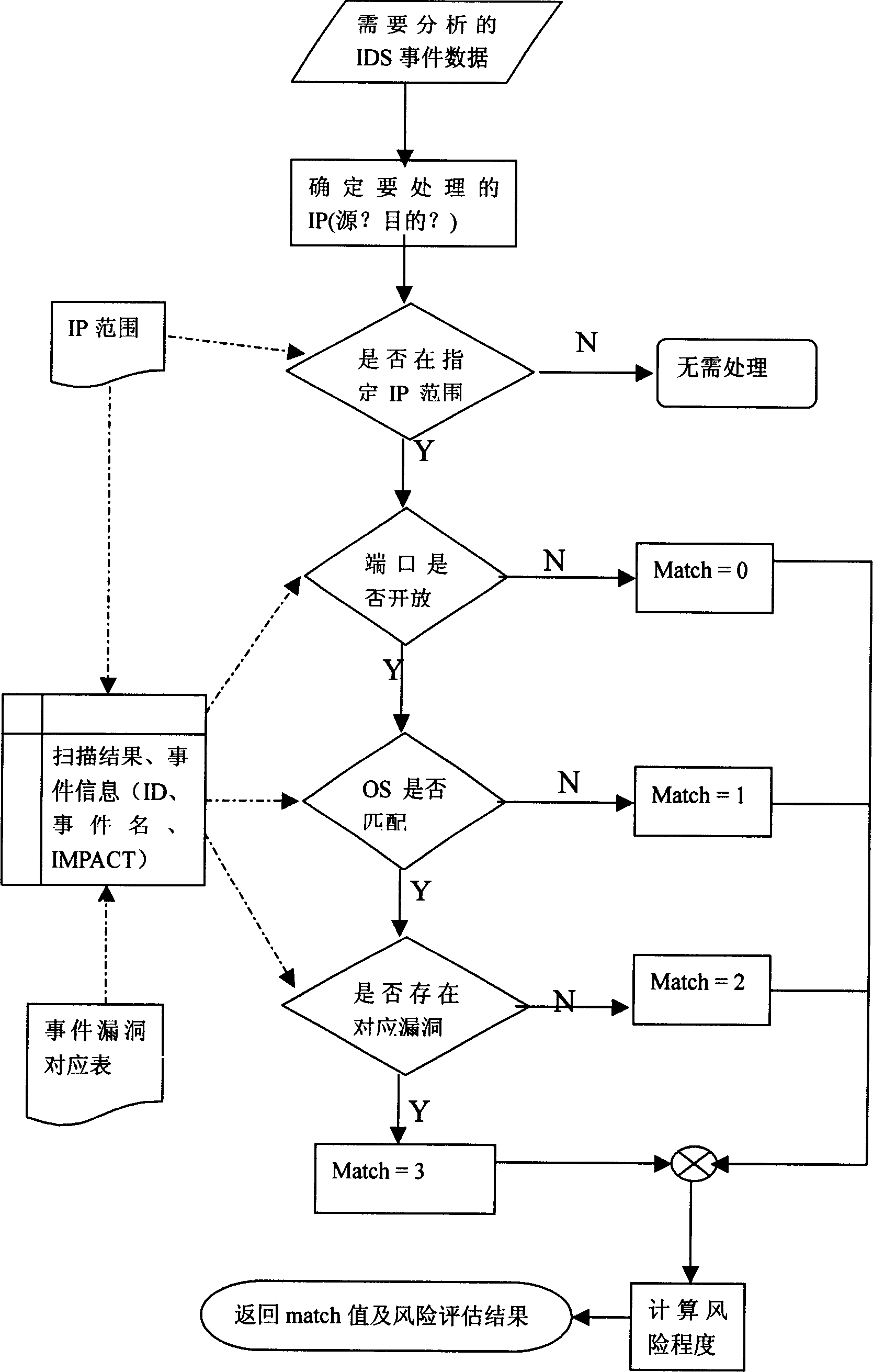
[0028] For the software implementation structure of the behavior-related event description language, see the attached figure 2 . This system works on IDS and SCANNER. It mainly uses the results reported by IDS and SCANNER to analyze, eliminate false positive events, and carry out risk assessment on effective events.
[0029] After the engine is started, it will regularly obtain the latest vulnerability scan results of all IPs based on the specified IP range, and its data structure is as follows:
[0030] typedef struct
[0031] {
[0032] / / Specify the ID of the IP range scanning task
[0033] DWORD dwTID;
[0034] / / Scan task dwTID scan completion time, used to calibrate whether it is the latest result
[0035] time_t tCurrentTime;
[0036] / / Scan result of scan task dwTID
[0037] map map_ScanLog;
[0038] / / Calibrate whether the scan result is in use
[0039] LONG nSLCounter;
[0040]}MapScanLog;
[0041] Among them, map_ScanLog associates and sorts the scanning ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com