Method and system for detecting network security threat based on trusted business flow
A technology for network security and threat detection, applied in the field of network information security, can solve the problems of low false positive rate and anti-kill efficiency, high false positive rate of defense system, and many loopholes, etc., to improve the degree of intervention and perception, and high anti-kill efficiency. , the effect of low false alarm rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
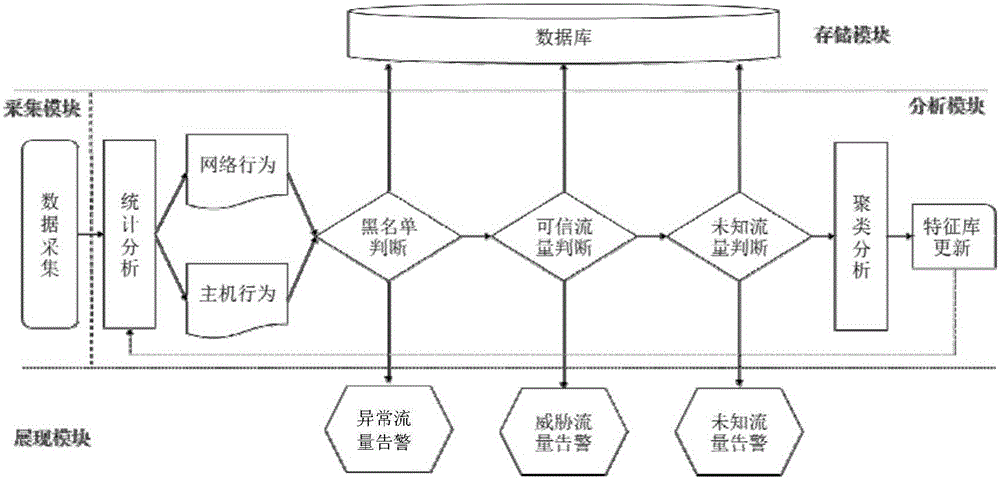
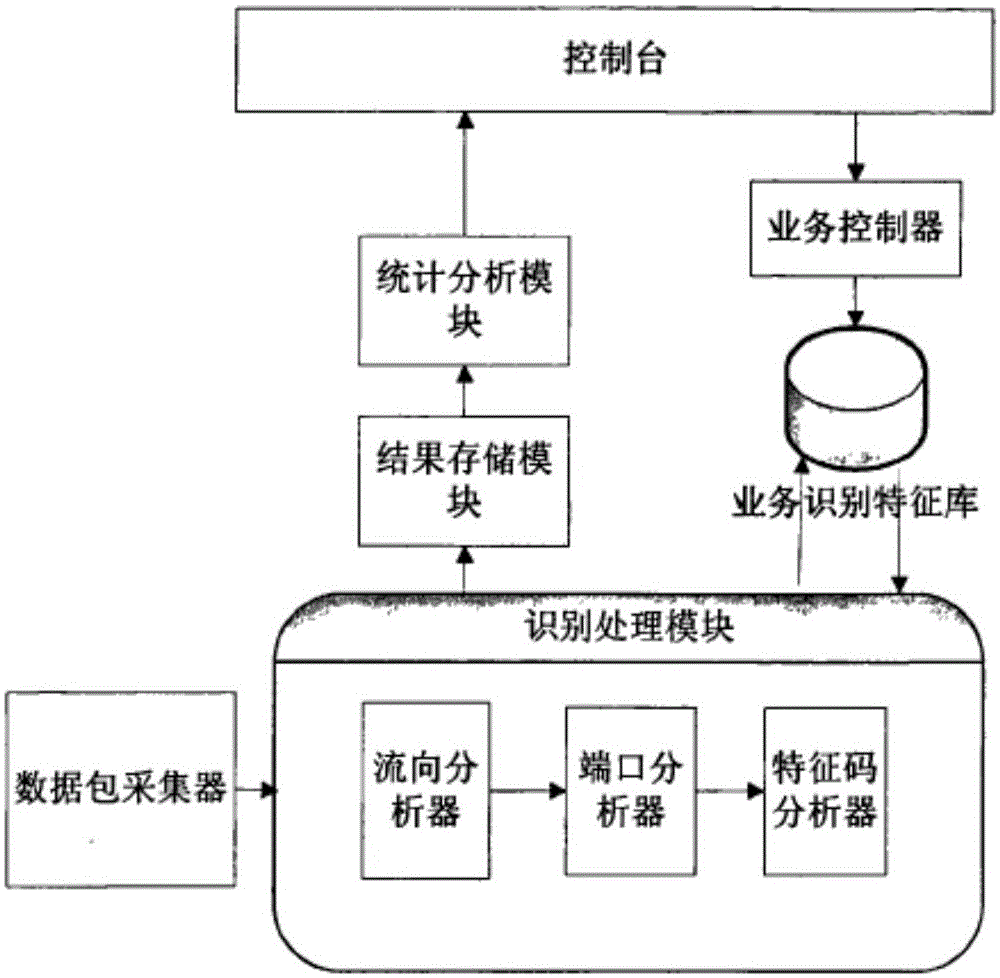
[0032] The present invention provides a network security threat detection method and system based on a trusted service flow. By real-time monitoring and characteristic analysis of the actual flow in the service system and the "trusted service flow", the network system can be discovered and found in time. Abnormal network behavior and host behavior, so as to achieve the purpose of timely detection of security threats.
[0033] Among them, abnormal network behavior and host behavior include: using an incorrect identity, at an incorrect time, in an incorrect location (through incorrect channels), and performing incorrect operations on unauthorized resources in an incorrect manner .
[0034] Trusted business flow is to monitor the business traffic in daily work, sample the behavior of the system or users, calculate the collected samples, and obtain a series of parameter variables to describe these behaviors, thus sorting out The minimum network access relationship that satisfies norma...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com