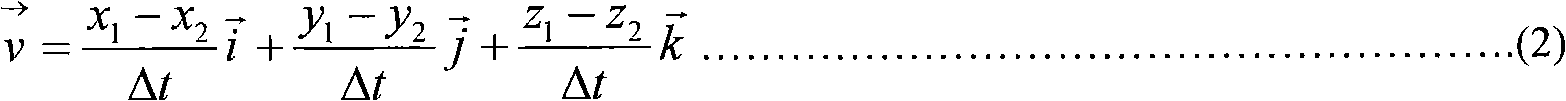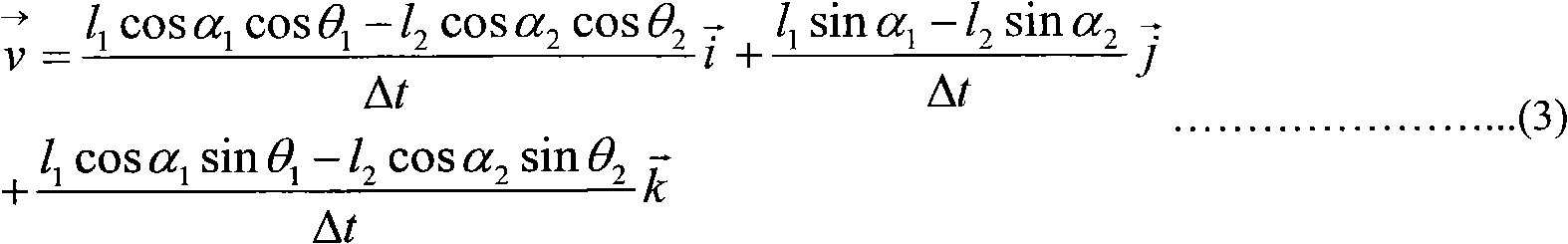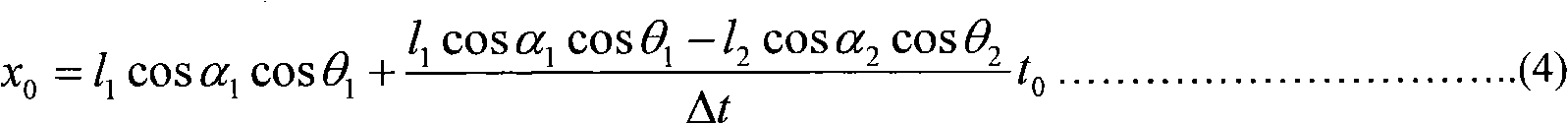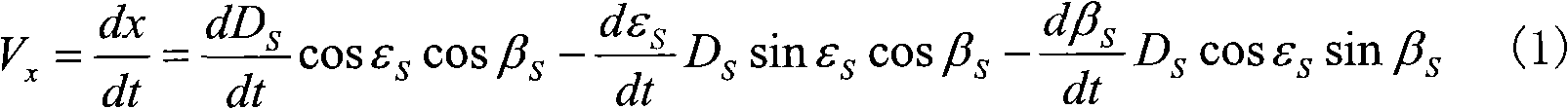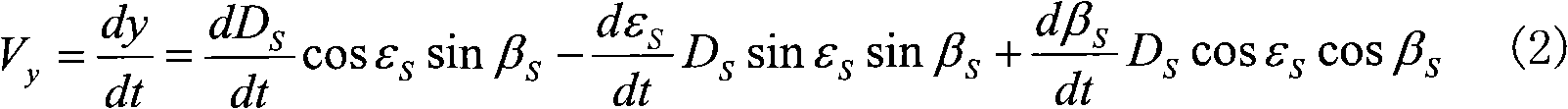Patents
Literature
238 results about "Intercept method" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The intercept method, also known as Marcq St. Hilaire method, is an astronomical navigation method of calculating an observer's position on earth. It was originally called the azimuth intercept method because the process involves drawing a line which intercepts the azimuth line. This name was shortened to intercept method and the intercept distance was shortened to 'intercept'.
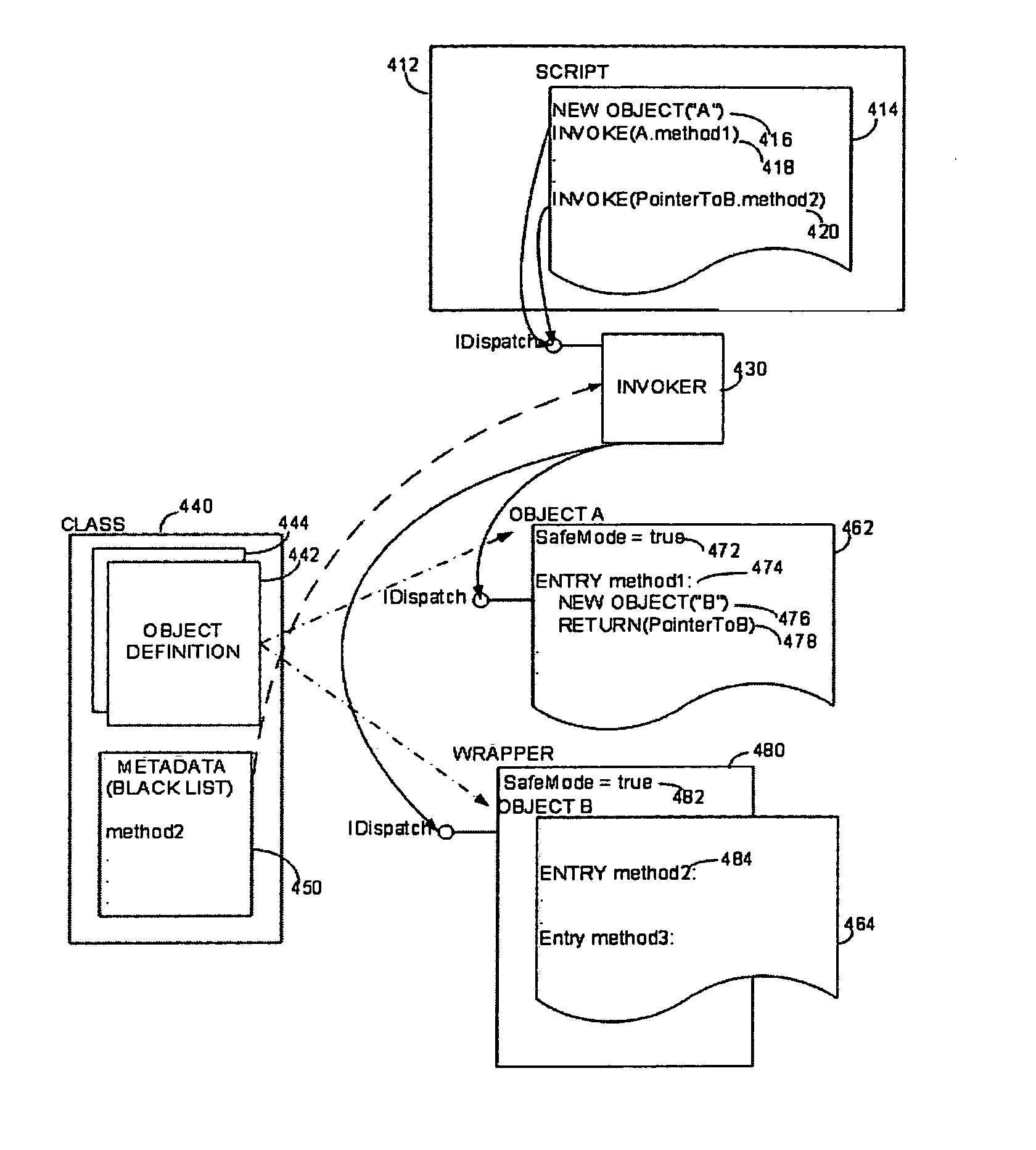
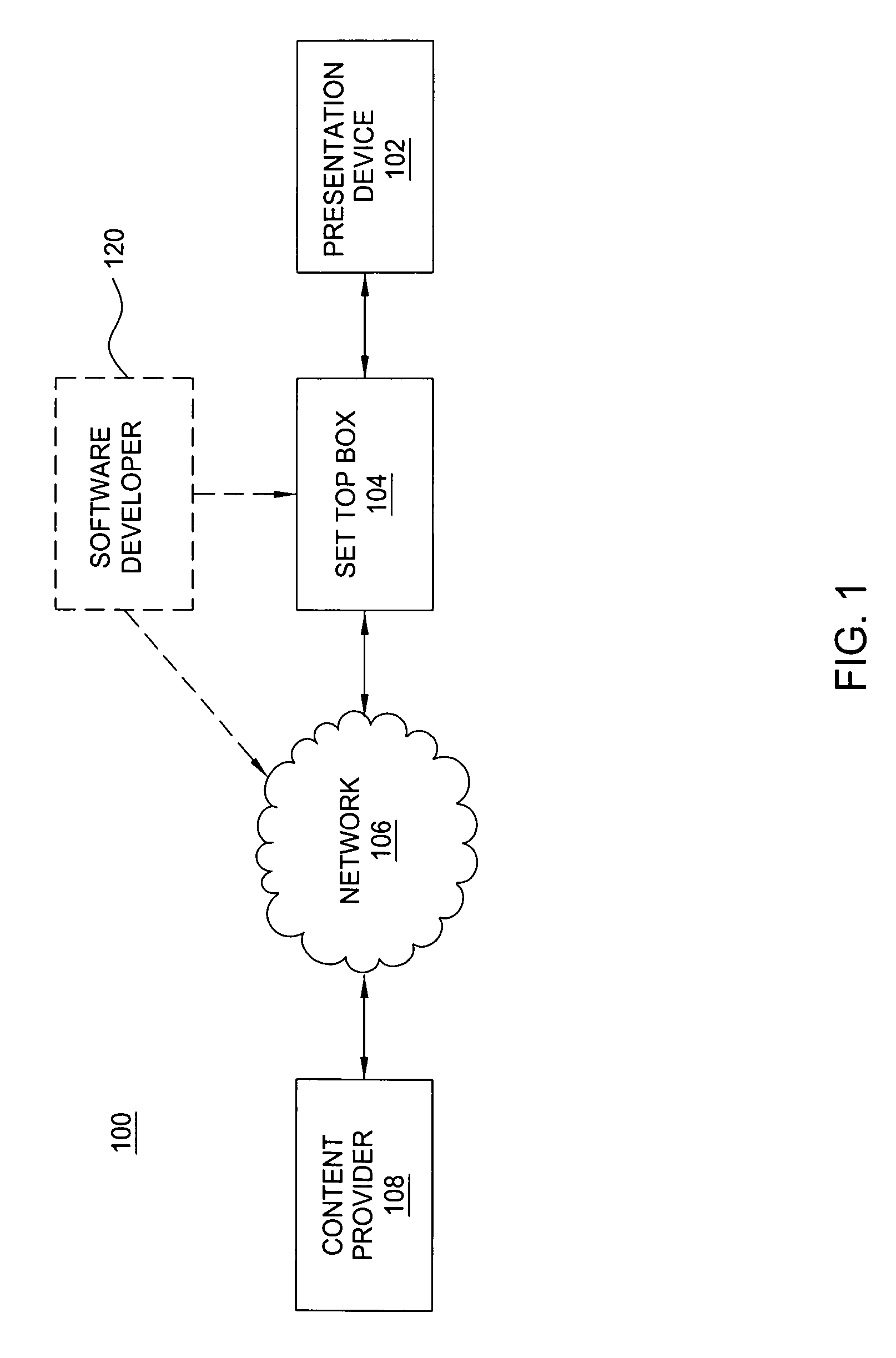
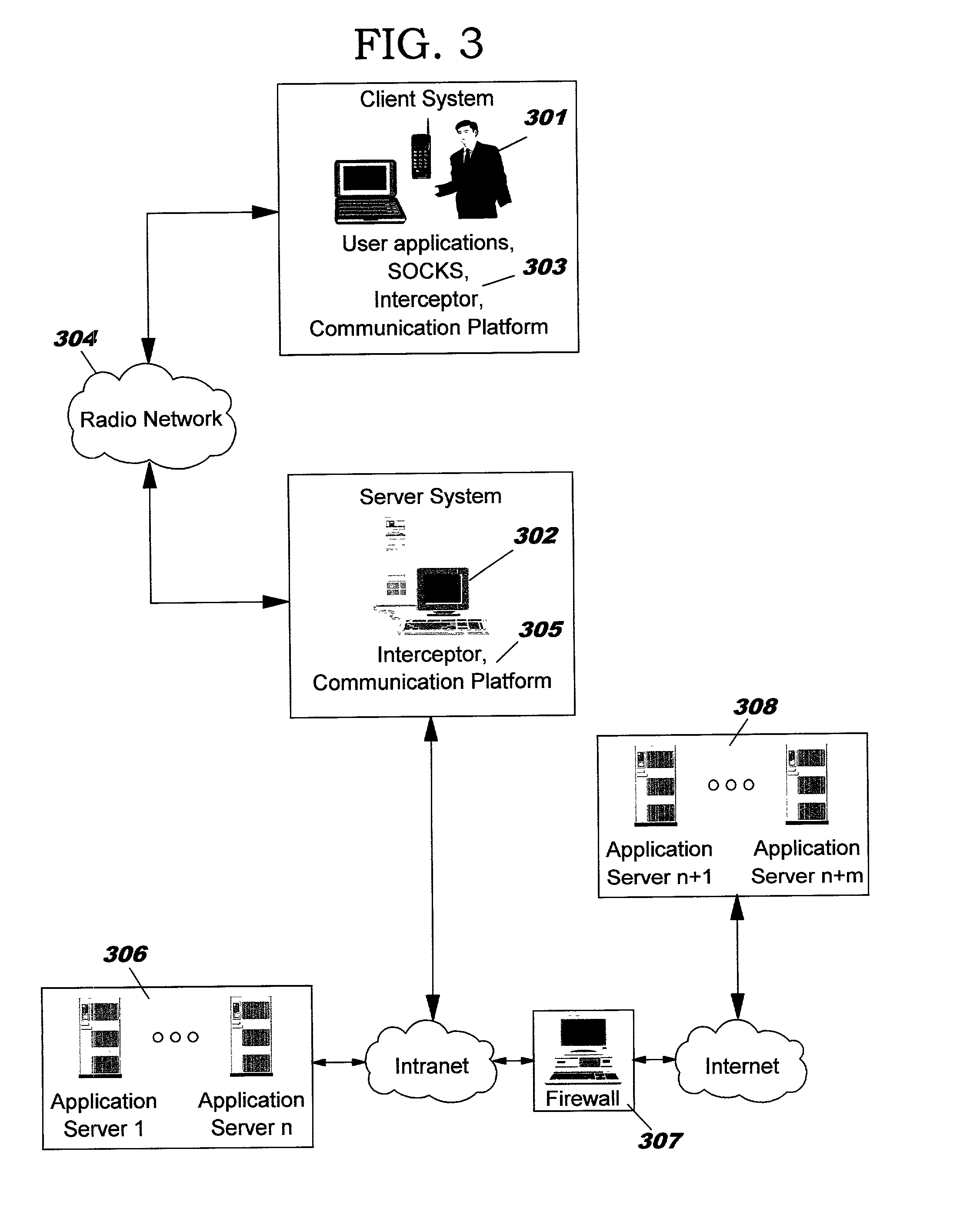
Software system with controlled access to objects
ActiveUS20070199000A1Easy to useImprove developmentSpecific access rightsProgram control using stored programsSoftware systemWhitelist
A computer system configured to intercept method calls placed on an object. By intercepting method calls, processing may be performed on a method call-by-method call basis. As part of the processing, metadata for an object is consulted to partition the methods for that object into subsets. The processing performed in response to any specific method call may be based on the subset to which the method belongs. The type of metadata may depend on the desired operation of the computer system. Metadata representing a white list or black list may be used in a computer system that implements a security zone that allows access to methods deemed to be safe or to deny access to methods deemed to be unsafe. In a performance monitoring system, metadata may identify methods to be logged or methods for which execution cost are to be measured. Values returned by a method call may also be processed when the method calls are intercepted. The returned value may be wrapped with a wrapper that holds data useful in implementing a security zone or for performing other processing.
Owner:MICROSOFT TECH LICENSING LLC
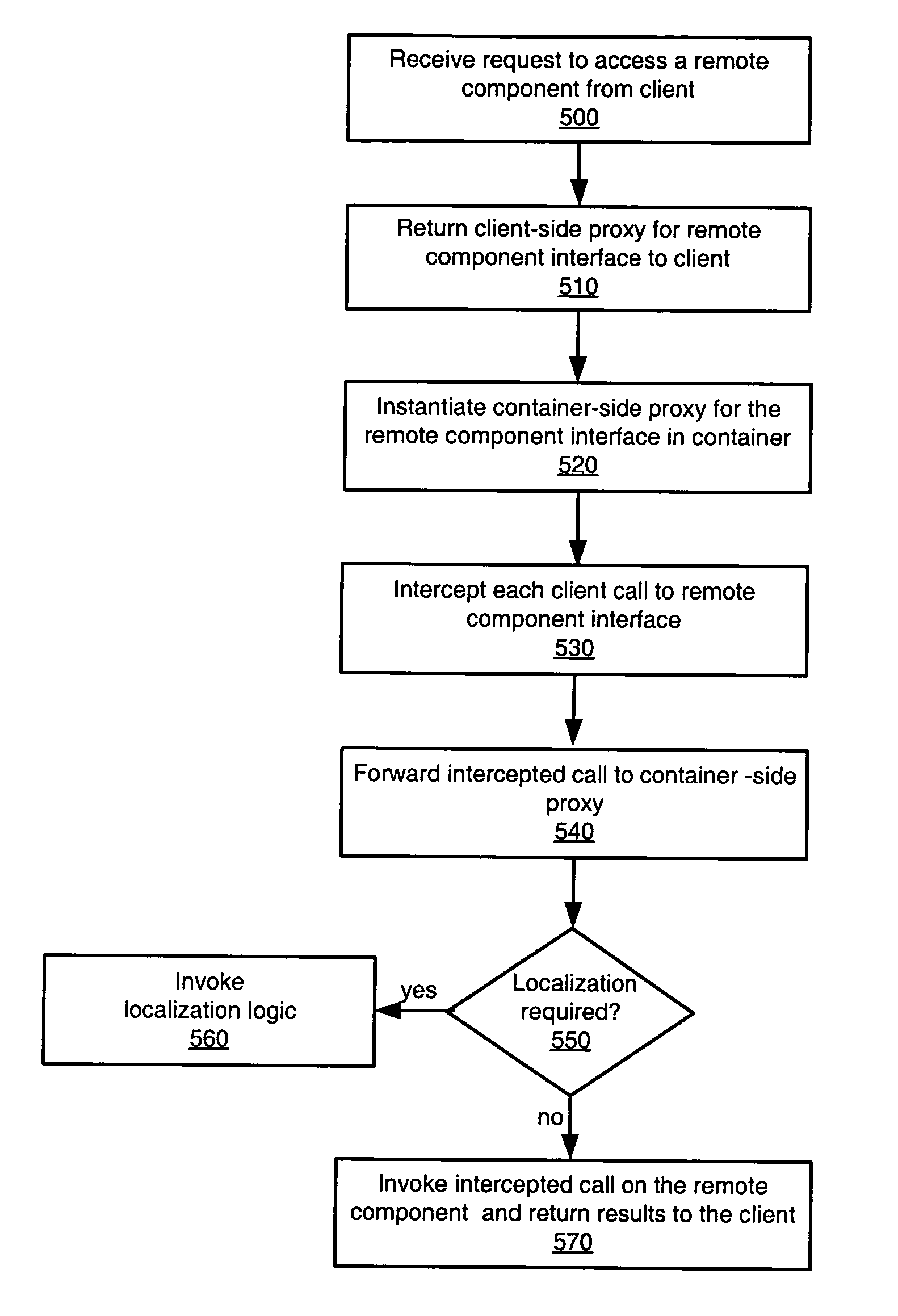
Application internationalization using dynamic proxies
An application that was not internationalized when coded may be internationalized through the addition of interception and localization logic and tables without modification of the original application logic. The interception logic may be configured to intercept calls to an application component and invoke localization logic in response to an intercepted call to the application component. The interception logic may use dynamic proxies to intercept method calls from a client component to an application component both before and after the execution of the method. The interception logic may use JAVA reflection to determine whether input parameters or return values associated with the method call are localizable. The application component logic may operate on data stored in a primary database table in which the data is represented in the system default locale.
Owner:SUN MICROSYSTEMS INC
Method and system for monitoring and intercepting sensitive behaviour of Android software
ActiveCN103198255AIntegrity guaranteedGuaranteed availabilityPlatform integrity maintainanceInternet privacyInter-process communication
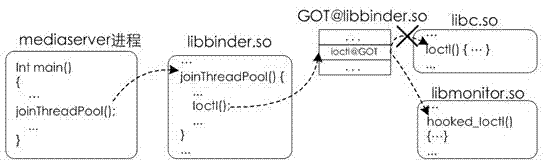
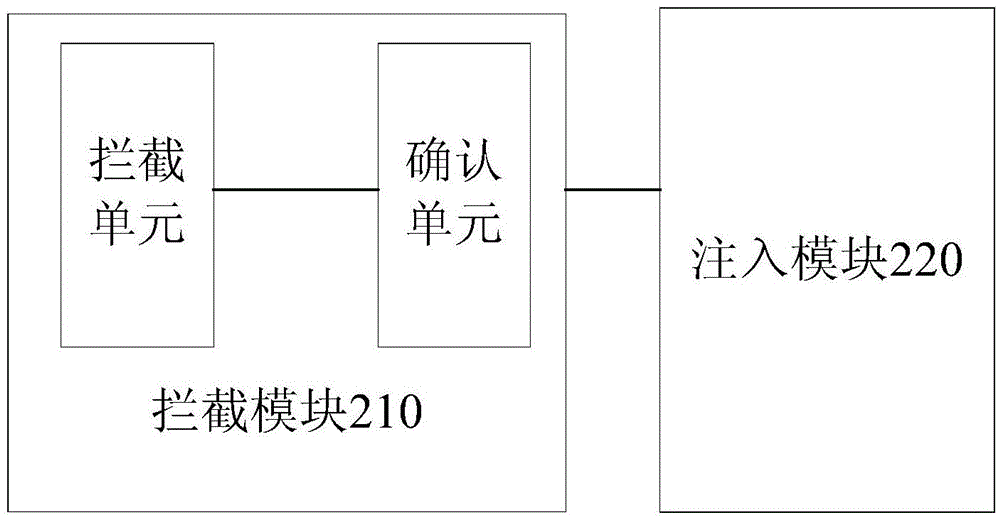
The invention belongs to the technical field of security of intelligent mobile phones, relates to a security reinforce method of an Android system and particularly relates to a method and a system for monitoring and intercepting sensitive behaviour of Android software. The method for monitoring and intercepting the sensitive behaviour of the Android software is used for monitoring and intercepting the sensitive behaviour of the Android software during operation, wherein the monitoring and intercepting method is based on a Binder inter-process communication mechanism of the Android system. The monitoring and intercepting system comprises an injector module, a monitor module, an intercepting rule managing module and a user interaction module. According to the method and the system, the system is not required to be modified, the sensitive behaviour of the software can be monitored accurately in real time, the sensitive behaviour can be intercepted according to the requirements of users, and infringement of the privacy and the property security of users by malicious software can be found out and prevented timely.
Owner:WUHAN UNIV
Intercept method and intercept device for homepage advertisements and browser
ActiveCN103605688AImprove loading efficiencyImprove efficiencyAdvertisementsText processingSoftware engineeringWeb page
The invention discloses an intercept method and an intercept device for homepage advertisements and a browser. The intercept method includes: receiving a first loading request of a current homepage by adopting an inner core of a first browser on a browser side; starting an inner core of a second browser when the current homepage is judged to be applicable to being loaded by adopting the inner core of the second browser; adopting the inner core of the first browser to generate a second loading request of the current homepage when the inner core of the second browser is monitored to request to load the current homepage; finding homepage elements needed to be intercepted in the current homepage by adopting a preset first judgment rule; intercepting the homepage elements by adopting the inner core of the second browser during finding. Poor practicability caused by non-universality of the intercepting rule and randomness of advertisement intercepting in switching of the inner cores in the multi-core browser is avoided, and the intercept method is high in practicability, system resource occupancy after the advertisement intercepting is reduced, and homepage loading efficiency is improved.
Owner:BEIJING QIHOO TECH CO LTD
Transparent and sub-classable proxies
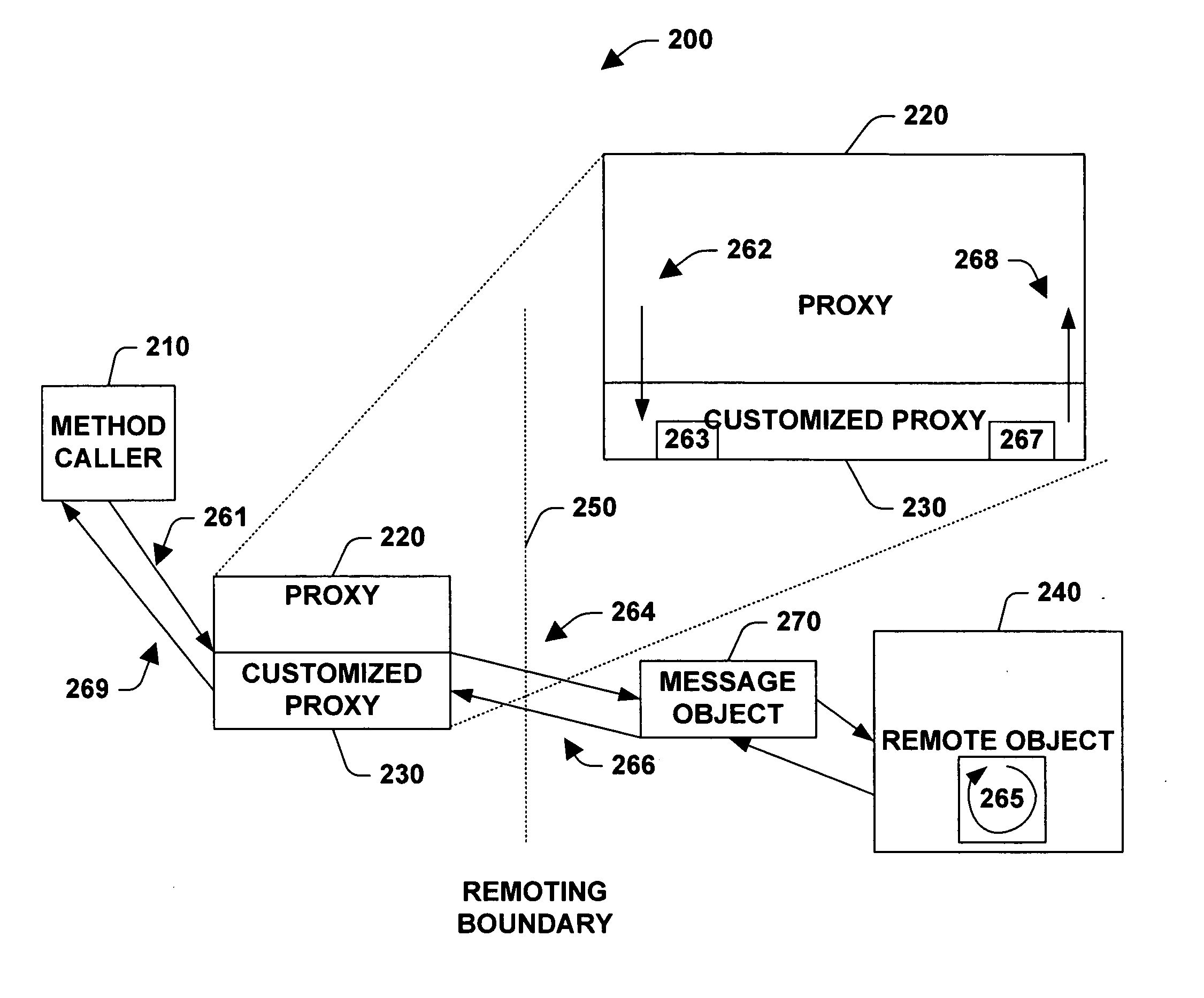
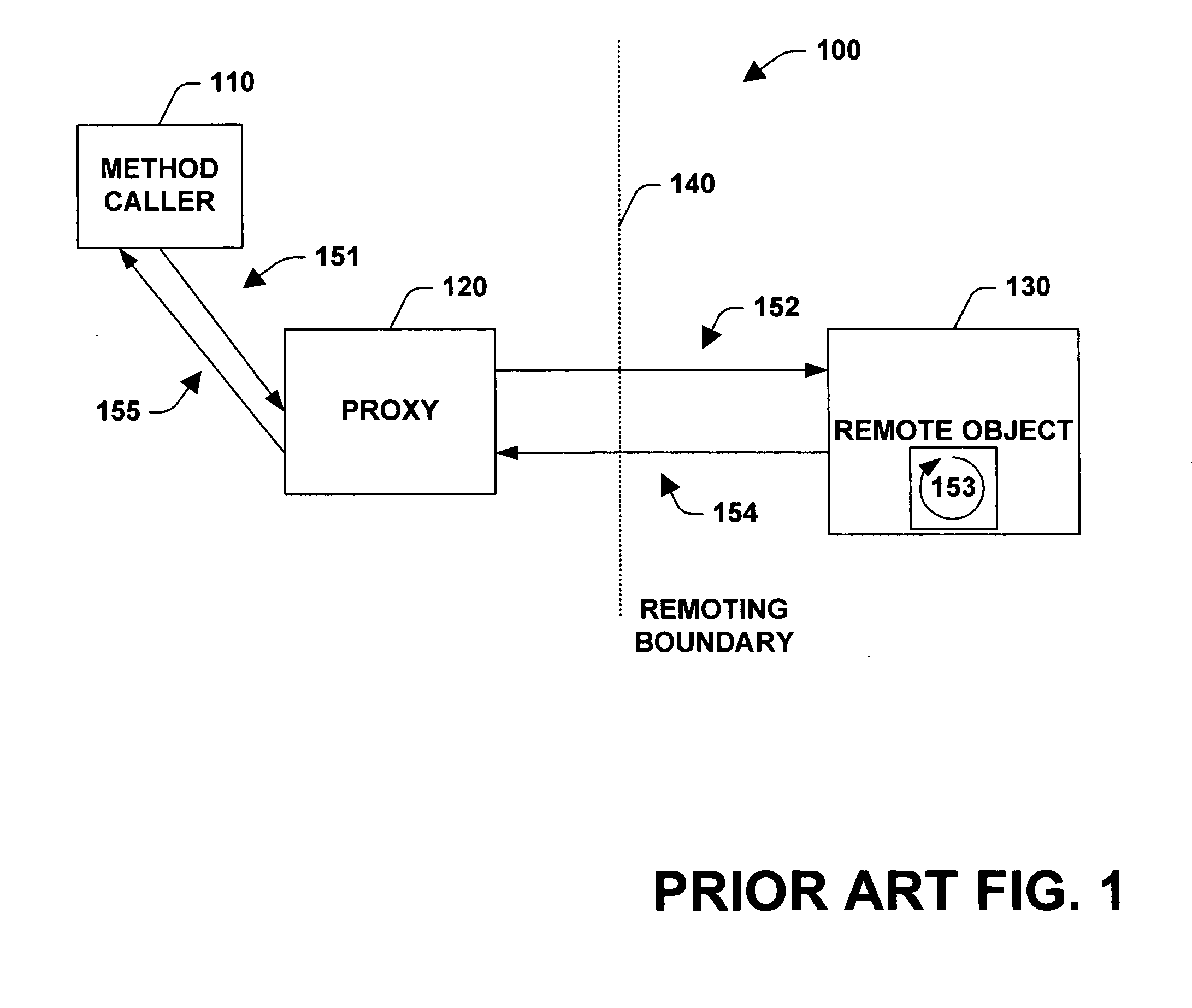
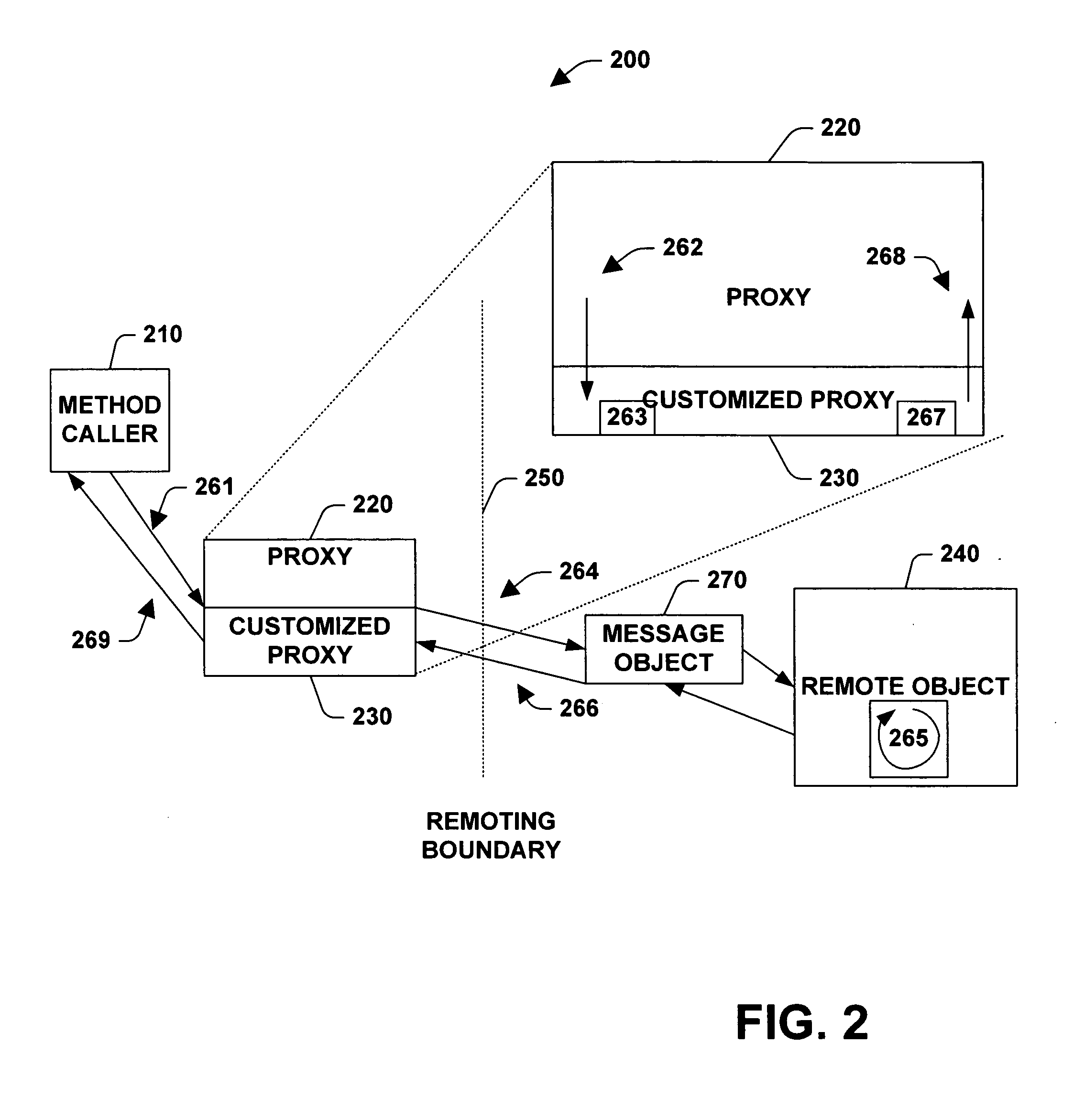
InactiveUS20050268309A1Function increaseReduce decreaseMultiprogramming arrangementsMultiple digital computer combinationsProgramming languageIntercept method
A system and method for interacting with an object is provided. The system includes a method call interceptor that intercepts a method call made on an object and that routes the method call to a proxy. The method call interceptor is accessible to application code. The system also includes an application code generic proxy that after overriding a base class invocation method can receive intercepted method calls, can invoke methods on the object that the proxy images, can receive results from the object that the proxy images and can pass results to the entity that generated the intercepted method call.
Owner:MICROSOFT TECH LICENSING LLC
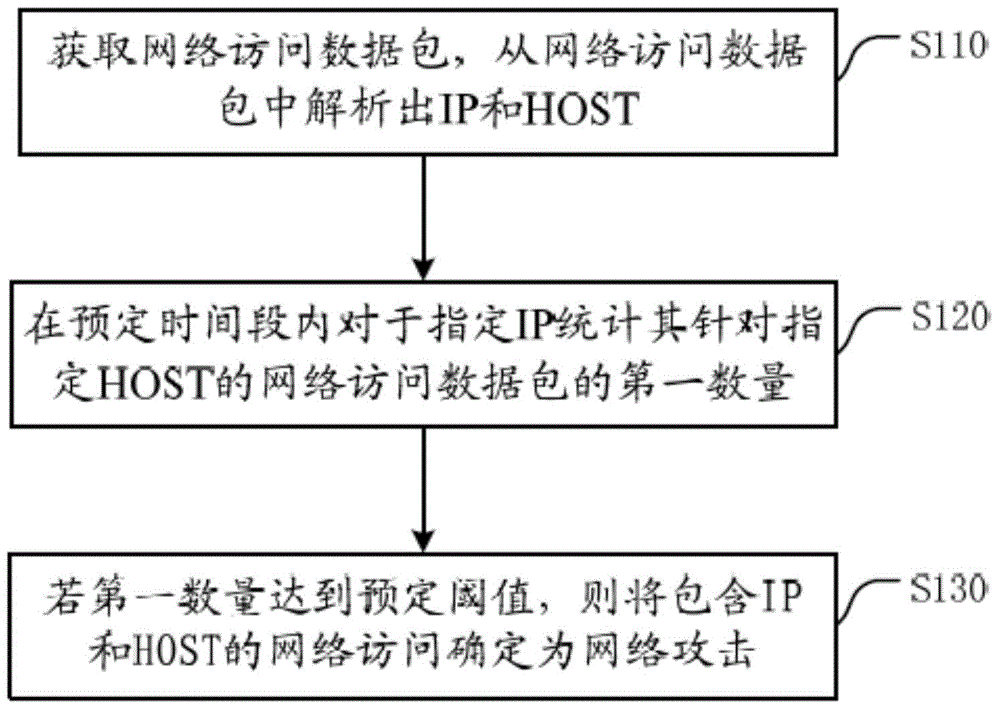
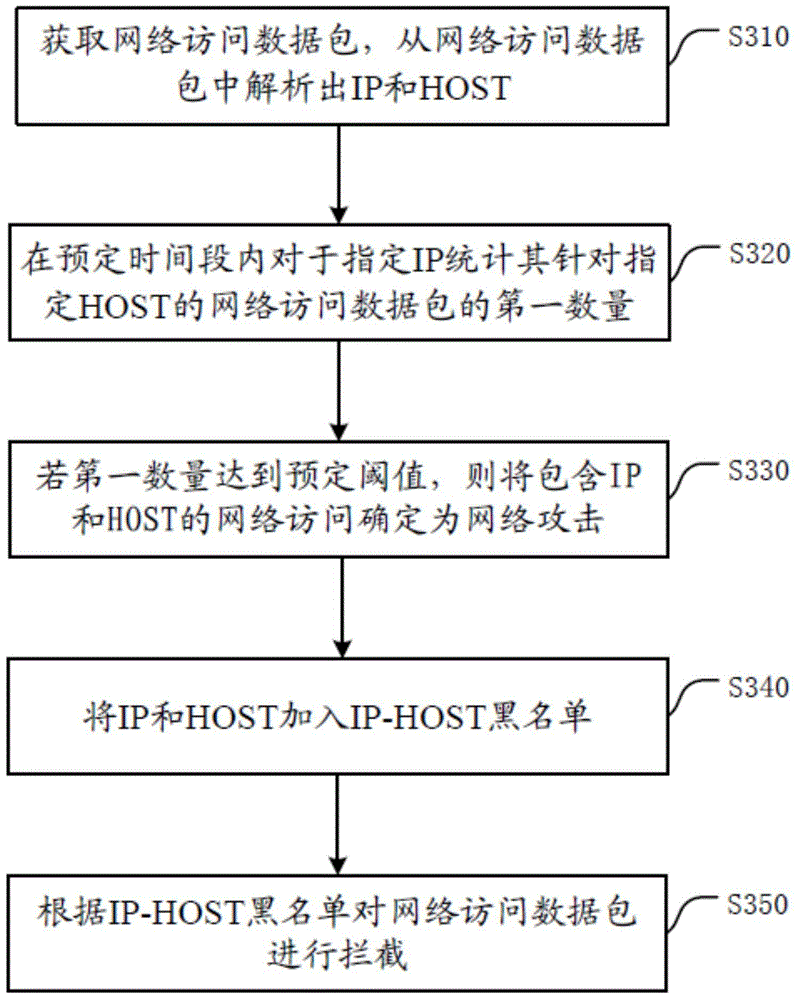
Attack detection method and device based on IP and HOST
InactiveCN104468554AResolve normal access requestsTroubleshoot technical issues with normal access requestsTransmissionDomain nameNetwork packet
The invention discloses an attack detection method and device based on an IP and a HOST, and an attack intercepting method and device based on the IP and the HOST. The attack detection method based on the IP and the HOST comprises the following steps that a network access data packet is obtained, the IP and the HOST are analyzed out of the network access data packet, wherein the IP is a source IP address of the network access data packet, and the HOST is a target website domain name of the network access data packet; statistics is carried out on the first number of the network access data packet of the specified IP on the specified HOST within a preset time period; if the first number reaches a preset threshold value, the network access including the IP and the HOST is determined as a network attack. Therefore, according to the technical scheme, network access data packets sent when a single host of the specified IP or part of hosts of a local area network carry out network access on remaining internet servers corresponding to the HOST cannot be wrongly intercepted.
Owner:BEIJING QIHOO TECH CO LTD +1
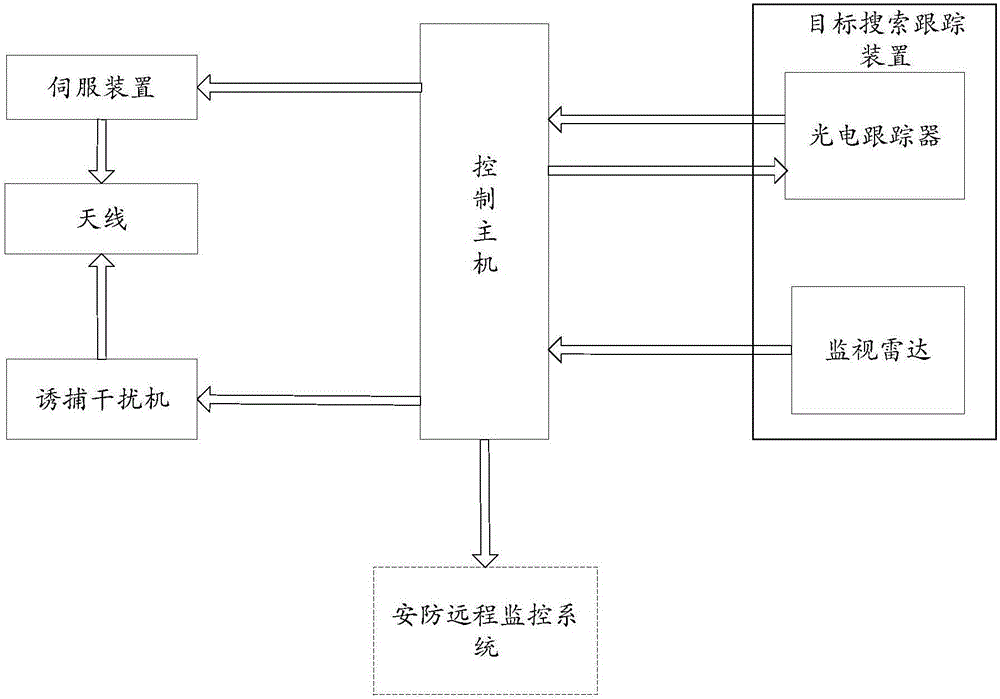
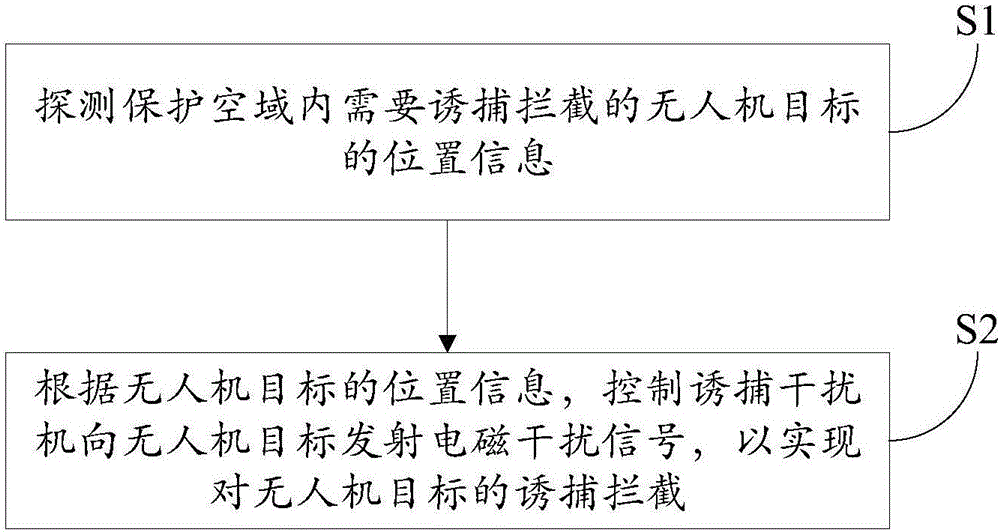
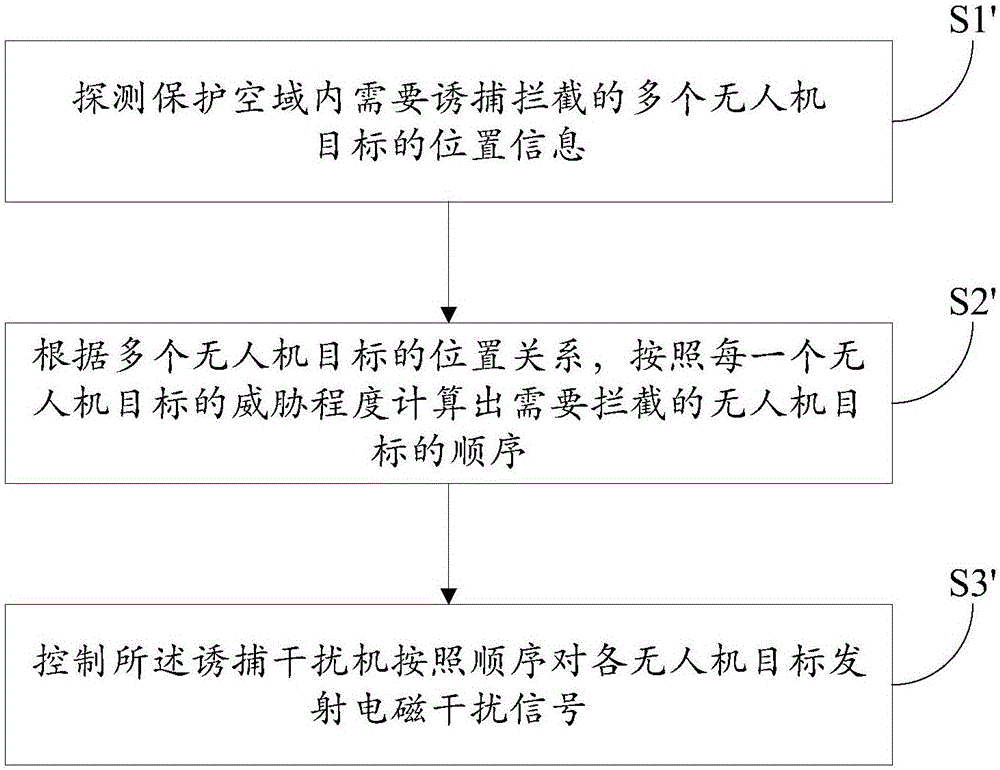
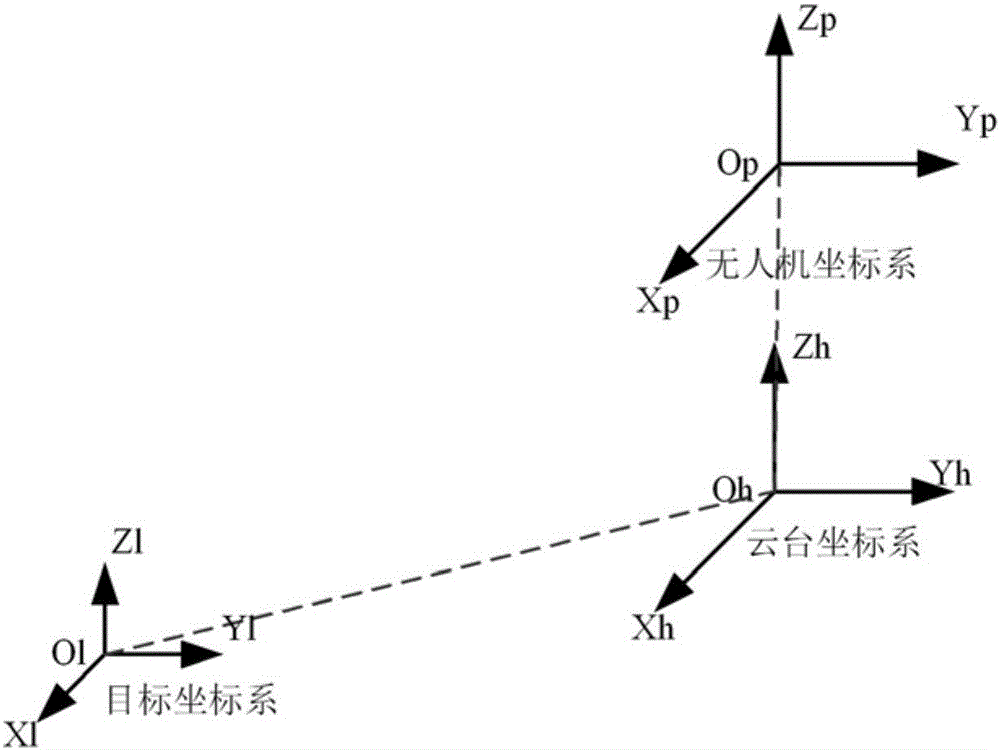
Unmanned aerial vehicle trapping interception system based on electromagnetic interference and trapping interception method thereof
InactiveCN106569511ARealize decoy interceptionRealize soft killing, trapping and interceptionControl using feedbackSatellite radio beaconingTrappingElectromagnetic interference
The invention discloses an unmanned aerial vehicle trapping interception system based on electromagnetic interference and a trapping interception method thereof. The trapping interception system comprises a control host, a target searching tracking device and a trapping jammer. The target searching tracking device is used for detecting position information of a suspicious target in a protection airspace and video information and sending to the control host. The control host is used for determining whether the suspicious target is an unmanned aerial vehicle target according to the video information. If the suspicious target is the unmanned aerial vehicle target, according to the position information of the unmanned aerial vehicle target, the trapping jammer is controlled to emit an electromagnetic interference signal to the unmanned aerial vehicle target so as to realize trapping interception to the unmanned aerial vehicle target. In the invention, through using the electromagnetic interference signal, the trapping interception to the unmanned aerial vehicle is realized and soft killing trapping interception of the unmanned aerial vehicle is realized too. New defense means are provided for relieving a security threat caused by a low, slow and small unmanned aerial vehicle. And a secondary damage caused through using a traditional interception net, a laser and other hard killing interception modes is avoided.
Owner:BEIJING INST OF RADIO MEASUREMENT
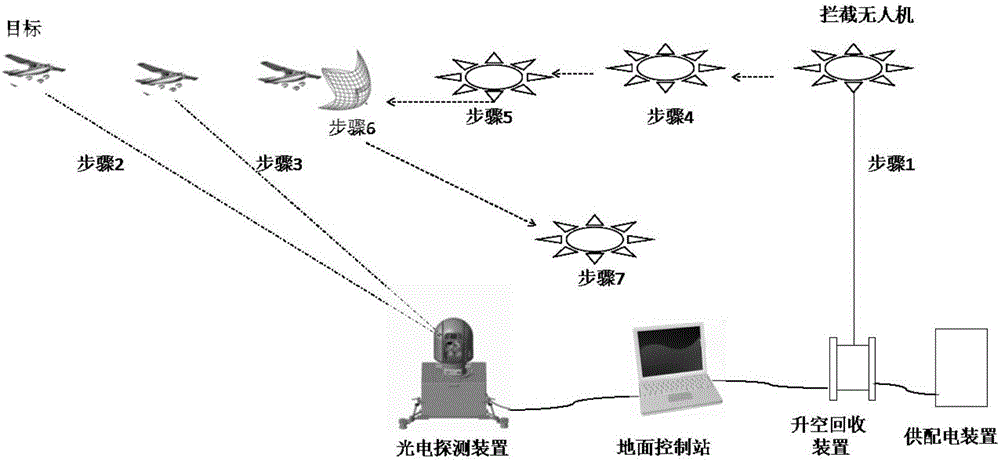
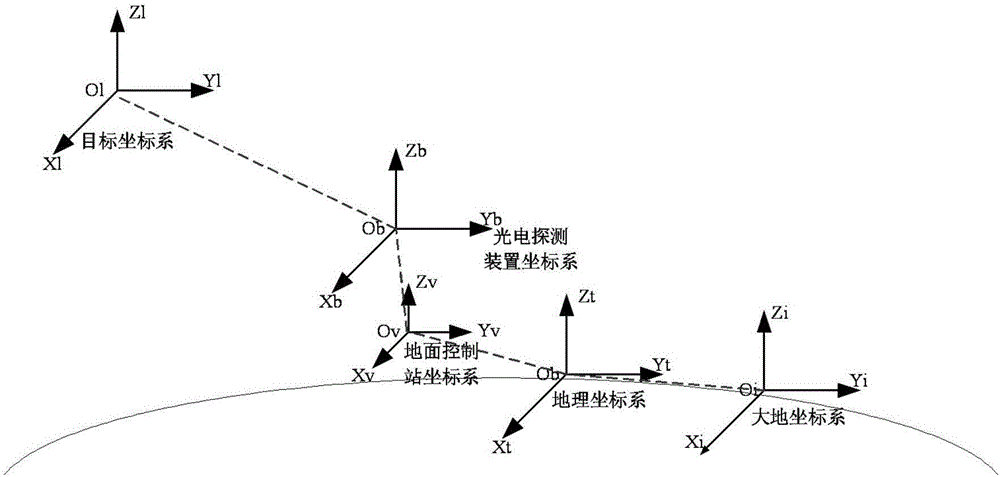
Guidance unmanned aerial vehicle net cast interception method for "low-altitude, slow-speed and small" target
ActiveCN106444829AIncrease intercept distanceHigh precisionSatellite radio beaconingPosition/course control in three dimensionsUncrewed vehicleComputer science
The invention relates to a guidance unmanned aerial vehicle net cast interception method for a "low-altitude, slow-speed and small" target. The guidance unmanned aerial vehicle net cast interception method comprises the steps that an unmanned aerial vehicle is set as the standby state; a ground control station determines a threat target and controls photoelectric detection equipment to perform dynamic tracking on the threat target; the ground control station acquires the location of the threat target and transmits a flight instruction to the unmanned aerial vehicle; and the unmanned aerial vehicle enters the maneuvering flight mode and reaches the area near the target. When the distance between the unmanned aerial vehicle and the target is less than a first threshold, the unmanned aerial vehicle is controlled to accurately approximate the target through a visual guidance device and a distance measurement device. When the distance between the unmanned aerial vehicle and the target is less than a second threshold, a net cast device is automatically triggered to emit an interception net to wind the target to fall off and finally the unmanned aerial vehicle returns. With application of the method, the net cast device is automatically triggered to intercept the target according to the relative location information between the unmanned aerial vehicle and the target so that the interception precision and the degree of automation can be effectively enhanced.
Owner:BEIJING MECHANICAL EQUIP INST
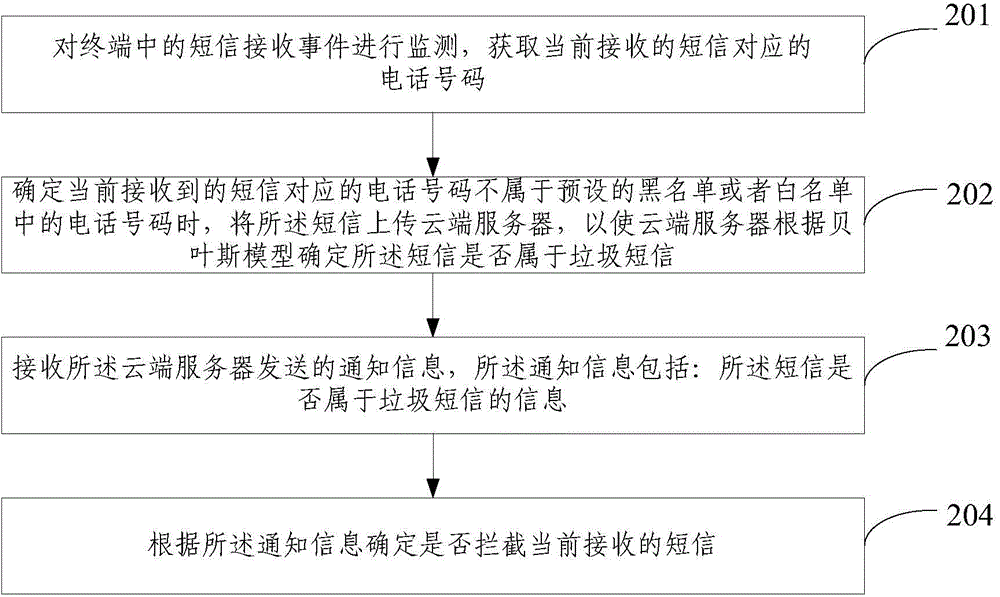
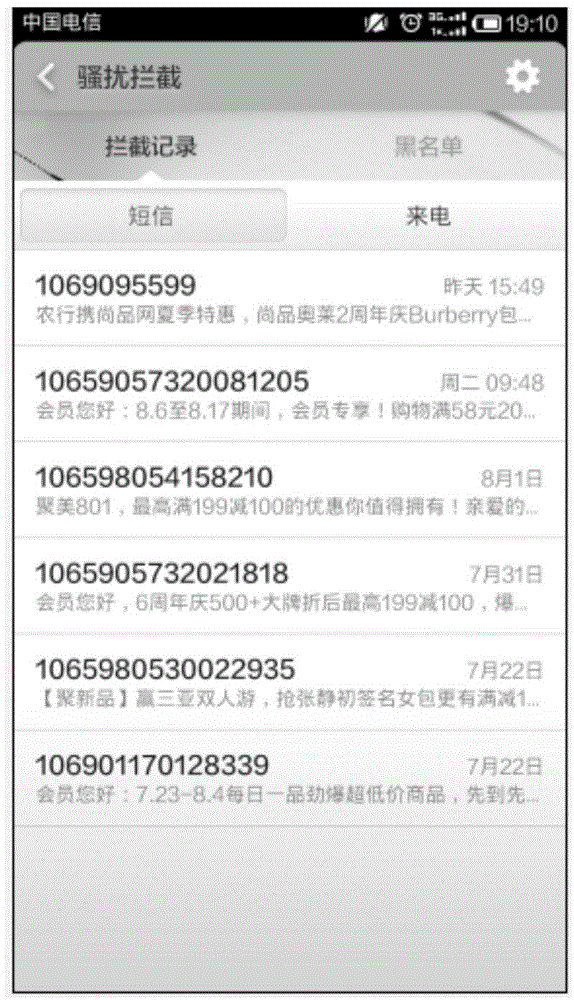
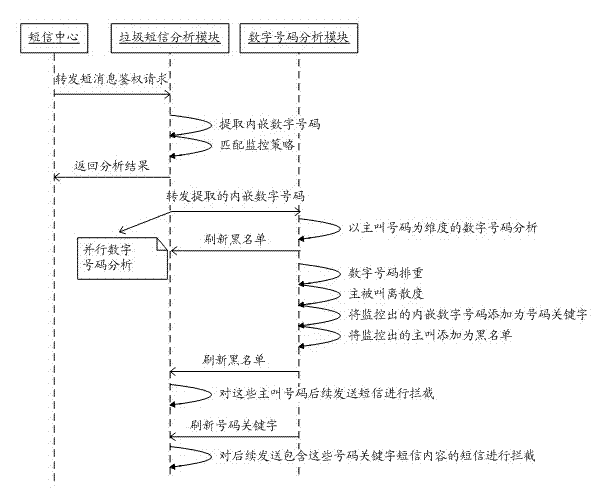
Short message intercepting method and device and cloud server
InactiveCN104168548AImprove recognition rateImprove interception efficiencyMessaging/mailboxes/announcementsSecurity arrangementComputer networkCloud server
The invention provides a short message intercepting method and device and a cloud server. The short message intercepting method comprises the steps that short messages uploaded by the short message intercepting device are received; word segmentation processing is conducted on text content of the short messages, and key words of the text content are obtained; first probability weighted values of all the key words belonging to junk short messages and second probability weighted values of all the key words belonging to normal short messages are obtained; a first joint probability of all the first probability weighted values of the key words and a second joint probability of all the second probability weighted values of the key words are obtained; whether the short messages are junk short messages or not is determined according to the first joint probability and the second joint probability; informing information is sent to the short message intercepting device, wherein the informing information comprises the information for judging whether the short messages belong to information of junk short messages or not so that the short message intercepting device can determine whether to intercept the short messages currently received or not according to the informing information. The short message intercepting method can solve the problems that in the prior art, the junk short message recognition rate and intercepting efficiency are low, and cost is high.
Owner:BEIJING QIHOO TECH CO LTD +1
Interception method of low-altitude low-velocity small targets
ActiveCN101982720ALow costShort reaction timeDefence devicesWeapon control systemsCommand and controlSmall target
The invention discloses an interception method of low-altitude low-velocity small targets. The method is realized by adopting detection equipment, command and control equipment, aiming control equipment, launch control equipment, a launching unit and a interception device, and comprises the following steps: the detection equipment in a networking mode or the aiming control equipment in a man-portable mode searches and tracks the targets and then sends target information to the launch control equipment; and meanwhile the launch control equipment performs trajectory calculation and then controls the launching unit to launch the interception device for intercepting the targets. By utilizing the method of launching the interception device from the ground for capturing the aerial targets, the problem that the existing method for capturing the ground targets is unavailable for capturing the aerial targets is solved; and the interception method has the advantages of low cost, short reaction time, decelerated surplus load falling and applicability to urban environment.
Owner:BEIJING MECHANICAL EQUIP INST
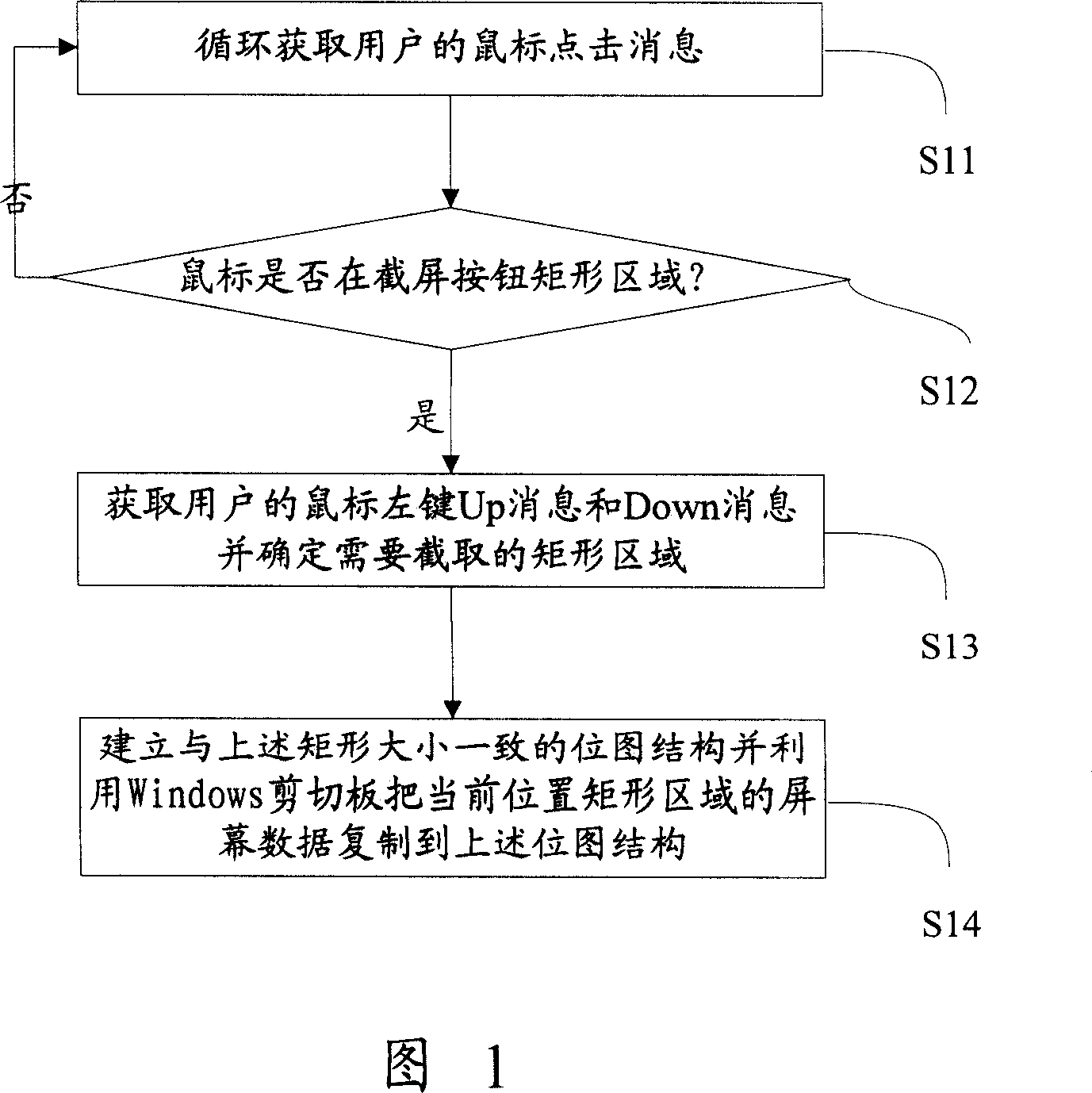
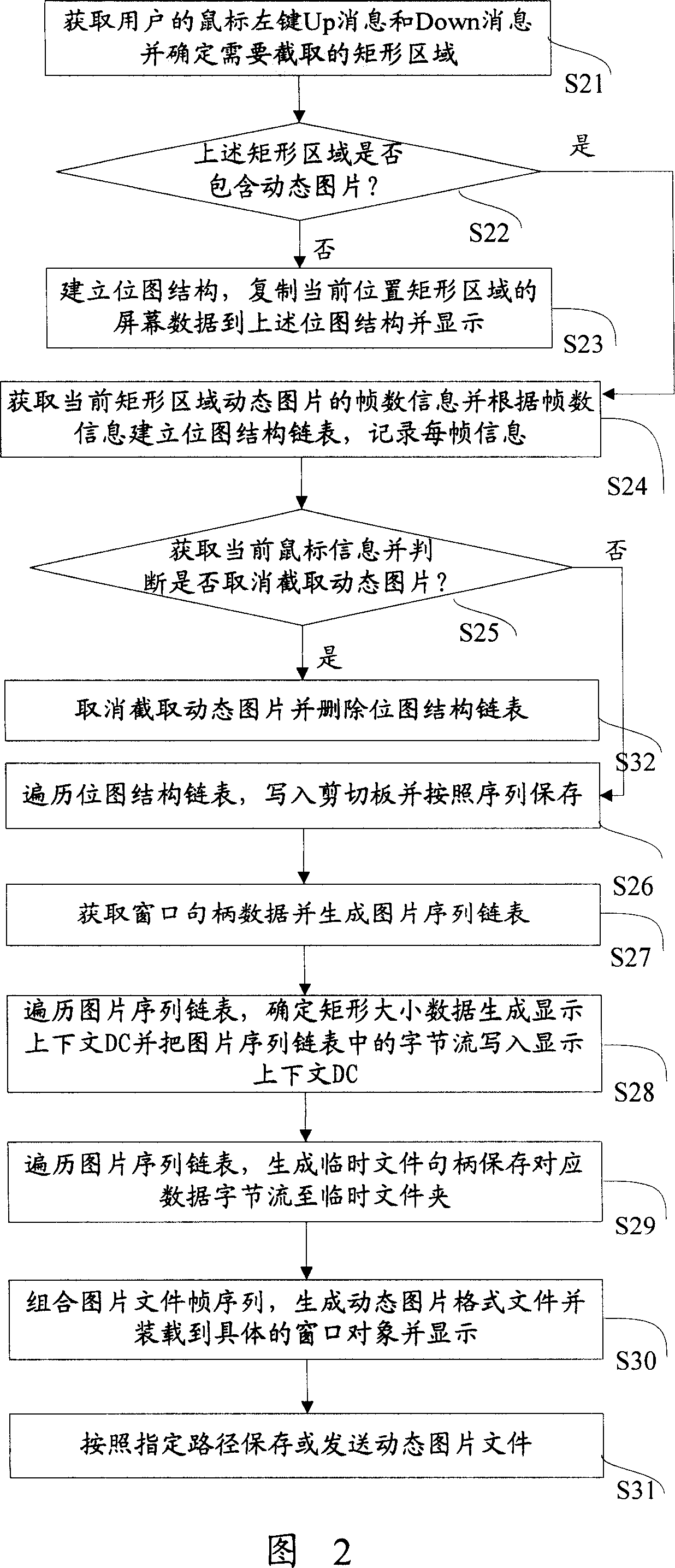
An intercept method of dynamic picture
ActiveCN1963748ARich communication experienceImprove experienceSpecific program execution arrangementsComputer graphics (images)Algorithm
This invention discloses one dynamic picture catch method, which comprises the following steps: using Windows hook mechanism to get user mouse cursor information to determine rectangle area for recording, displaying and sending current rectangle dynamic picture information. By applying this invention, user can not only process regular message interaction but also can catch web page or other dynamic picture to singly send or merge text and dynamic pictures.
Owner:TENCENT TECH (SHENZHEN) CO LTD
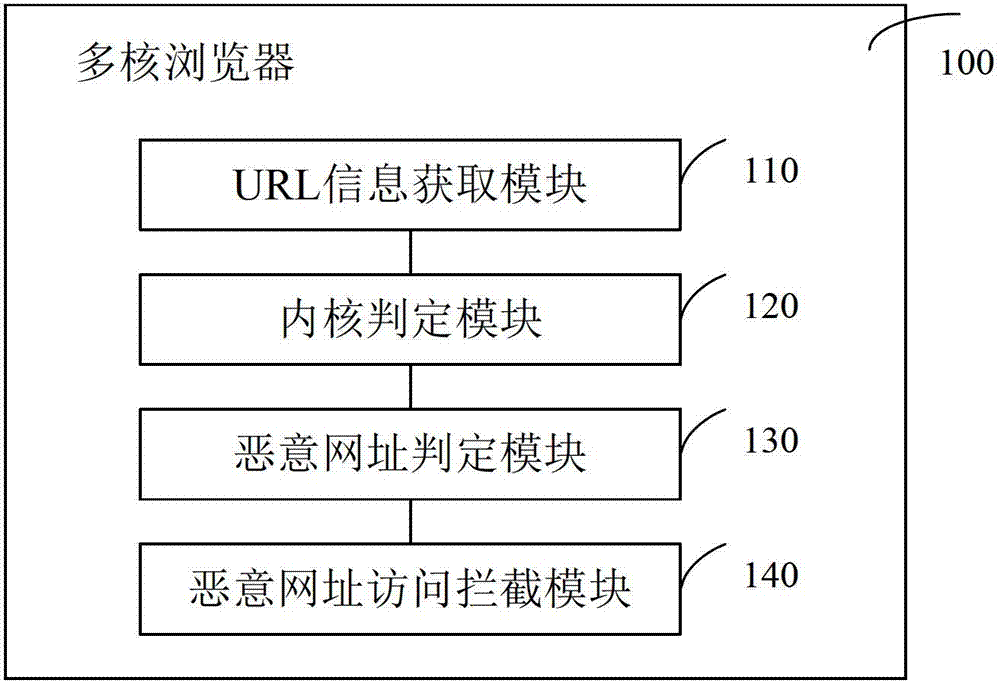
Malicious website intercepting method and device in multi-core browser
ActiveCN102932356AEffective interceptionSolve the problem of blockingTransmissionThird partyUniform resource locator
The invention discloses a malicious website intercepting method and a device in a multi-core browser. The device comprises a uniform resource locator (URL) information obtaining module, a core judging module, a malicious website judging module and a malicious website access intercepting module, wherein the core judging module is suitable for judging a core which renders a loading webpage according to URL information, and after judgment is completed, the core sends the judgment to the malicious website intercepting module whether the judgment is a request of a malicious website. The malicious website access intercepting module is also suitable for downloading an updated blacklist or an updated white list through a website safety judging server and for updating a local blacklist or a local white list through the updated blacklist and the updated white list. The malicious website intercepting method and the device in the multi-core browser can solve the problem that the malicious website can not be intercepted in a browser when a third party device is not arranged on a terminal or the third party device is not started on the terminal, and achieve a beneficial effect of timely and effective intercepting on the malicious website.
Owner:BEIJING QIHOO TECH CO LTD
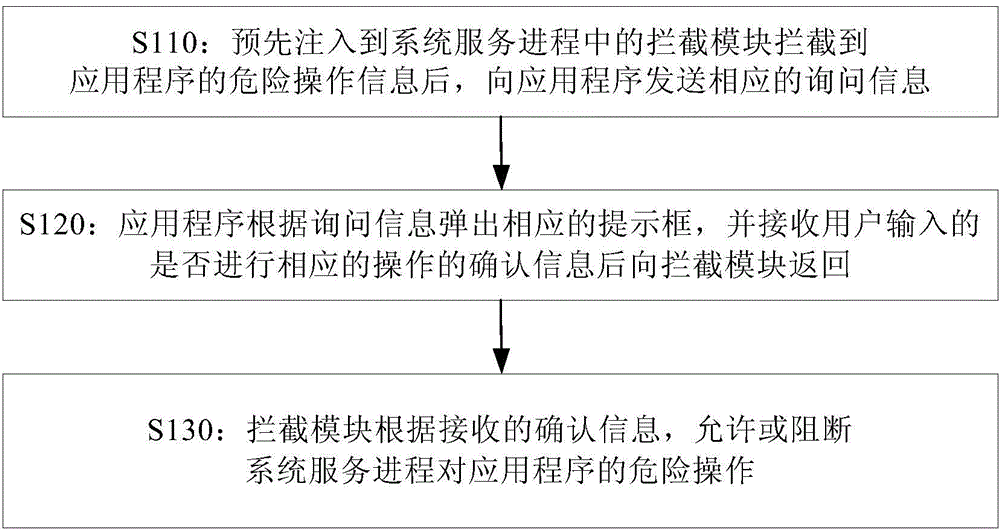
Application behavior intercepting method and application behavior intercepting device
ActiveCN104376263AEffective interceptionImprove experiencePlatform integrity maintainanceTemporary StoppingData information
An embodiment of the invention provides an application behavior intercepting method and an application behavior intercepting device. The method comprises the following steps of transmitting corresponding inquiry information to an application after dangerous operation information of the application is intercepted by an intercepting module which is injected into a system service process in advance; popping a corresponding prompt box by using the application according to the inquiry information; receiving confirmation information of a corresponding operation inputted by a user; returning the confirmation information to the intercepting module; and allowing or stopping a dangerous operation of the system service process on the application by using the intercepting module according to the received confirmation information. By the method and the device, behaviors of the application can be intercepted effectively; after the behaviors of the application are intercepted, the corresponding operation is stopped temporarily, the temporary stopping operation is notified to the user, the corresponding operation only can be carried out after the confirmation information of the user is obtained, so that the leakage possibility of data information and individual privacy information which are stored in the application is reduced, the safety of personal data is improved, and the user experience is also improved.
Owner:BEIJING QIHOO TECH CO LTD
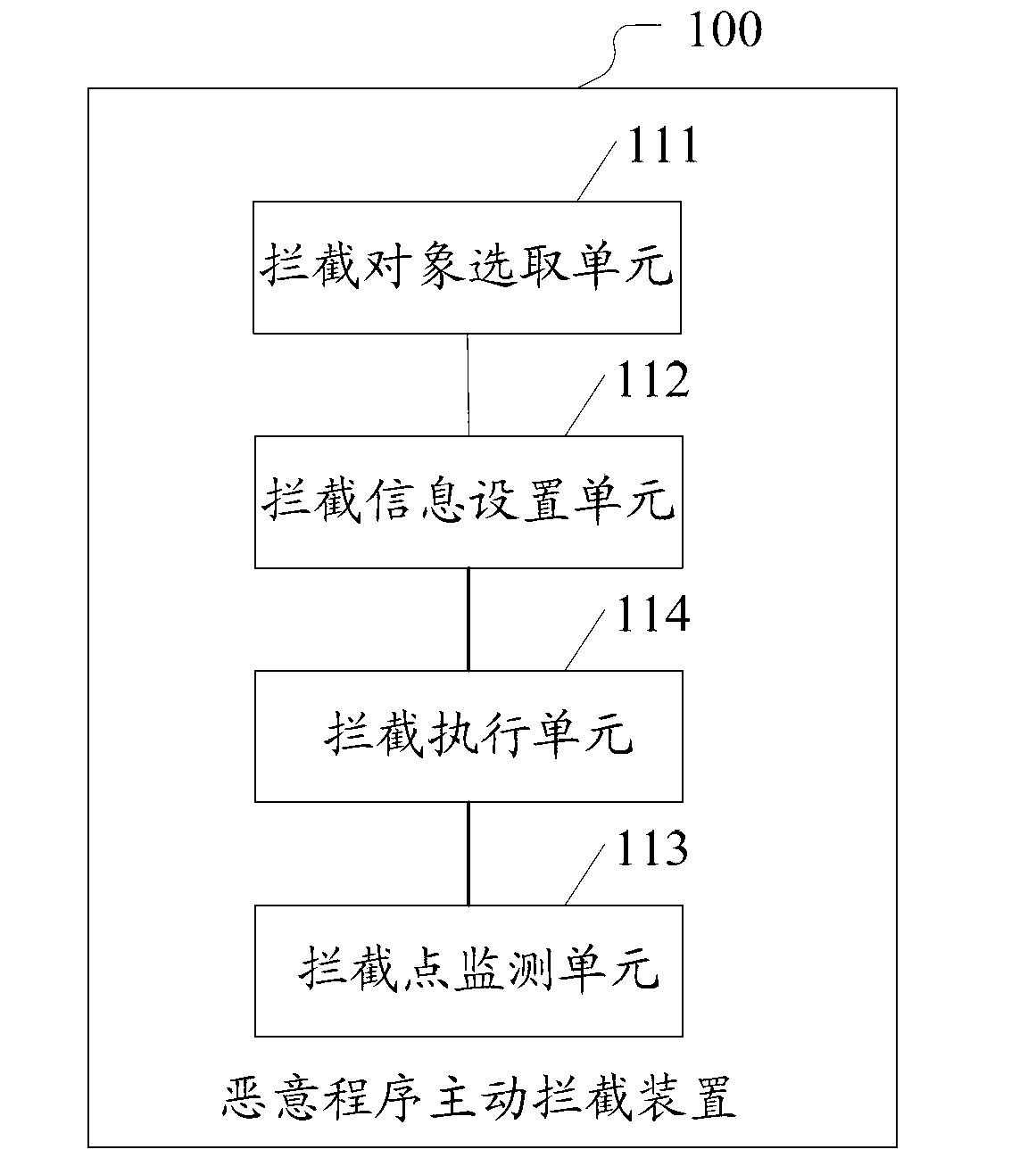
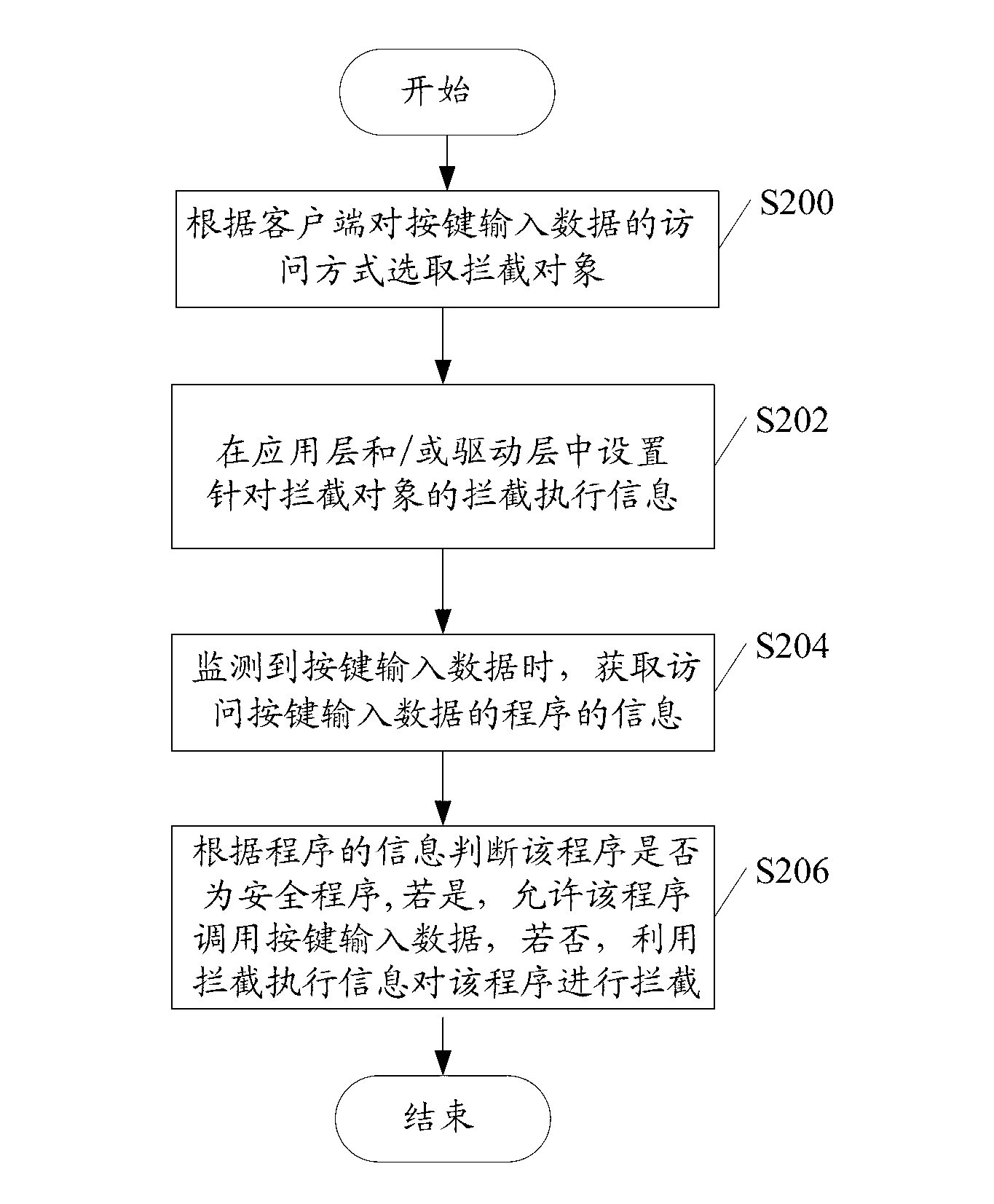
Initiative intercept method and initiative intercept device for malicious program and client end equipment
ActiveCN103020526AImprove accuracyAvoid the problem of low killing accuracyPlatform integrity maintainanceExecution unitData needs
The invention discloses an initiative intercept method and an initiative intercept device for a malicious program and client end equipment. The initiative intercept device for the malicious program comprises an intercept object selection unit, an intercept information setting unit, an intercept point monitoring unit and an intercept execution unit, wherein the intercept object selection unit is suitable for selecting an intercept object needs to be intercepted according to an access mode of a client end to key input data; the intercept information setting unit is suitable for arranging intercept execution information aiming at the intercept object in an application layer and / or a drive layer; the intercept point monitoring unit is suitable for acquiring information of a key input data accessing program when the key input data is monitored; the intercept execution unit is suitable for judging whether the program is safe according to the information of the program, if so, the program is allowed to call the key input data, if not, the program is intercepted, wherein the intercept point monitoring unit is suitable for judging whether the monitored key input data is data needs to be protected before the information of the key input data assessing program is acquired, if so, the information of the key data assessing program is acquired, and if not, the operation is finished.
Owner:BEIJING QIHOO TECH CO LTD
Short message intercepting method and system
InactiveCN102480702AEffective interceptionReduce misjudgmentMessaging/mailboxes/announcementsPattern recognitionText message
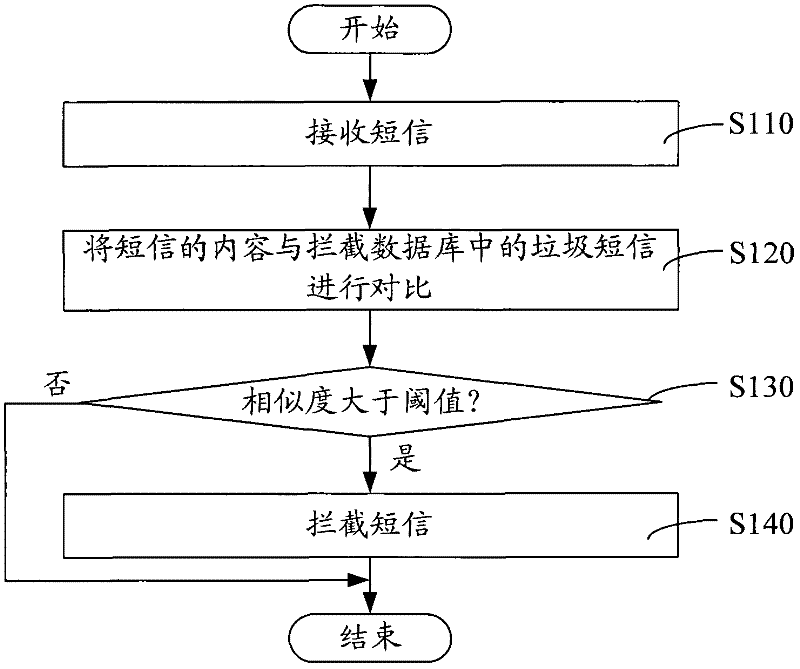
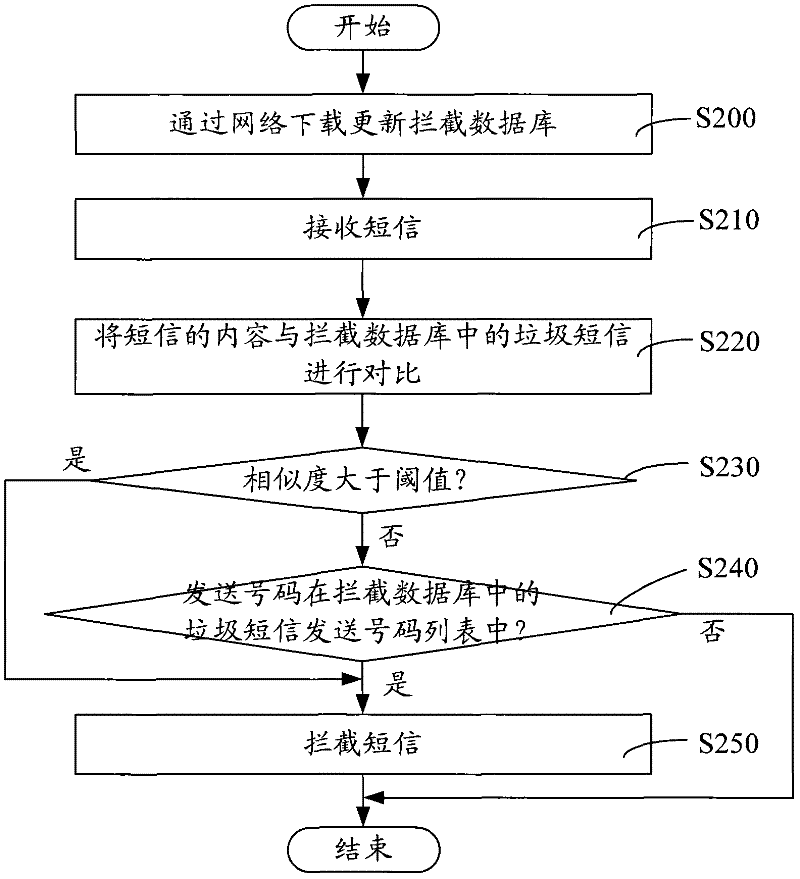
The invention relates to a short message intercepting method, comprising the steps of: receiving a short message; comparing the content of the short message with the content of a spam message in an interception database; judging whether the similarity of the content of the short message and the content of the spam message is more than a threshold value; if the similarity is more than the threshold value, the short message is intercepted. In the short message intercepting method, the content of the short message and the spam message in the database are compared to determine whether to perform interception according to the similarity of the content of the short message and the content of the spam message, and the spam message can be still recognized according to the change condition of a number of a sender; and the misjudgment possibility is reduced and the spam message can be effectively intercepted. Besides, the invention also provides a short message intercepting system.
Owner:TENCENT TECH (SHENZHEN) CO LTD
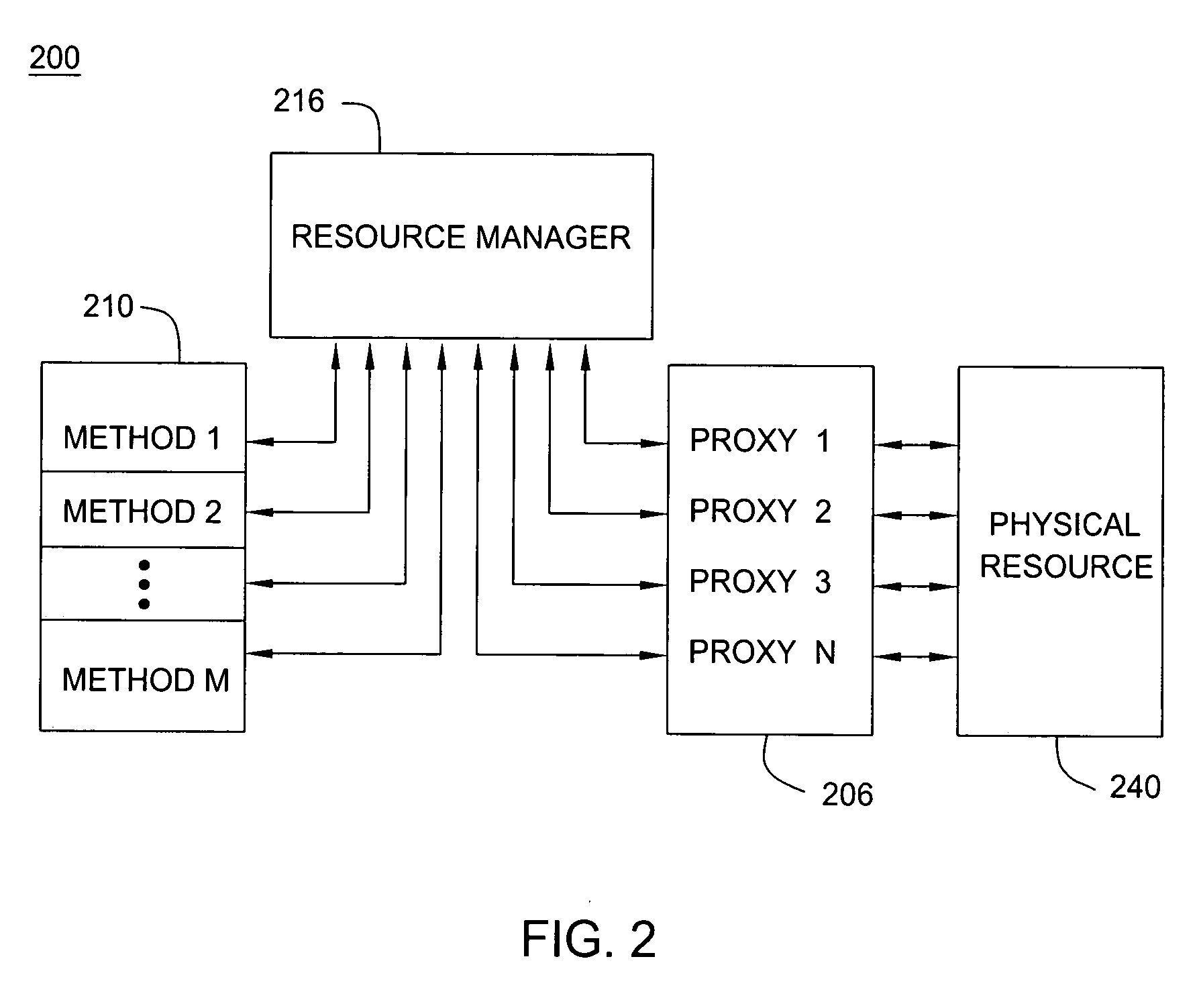
Resource access control
ActiveUS20060174333A1Digital data processing detailsUser identity/authority verificationControl systemResource management
A method and apparatus for enabling multiple application programs to control a system's physical resources by way of multiple resource proxies, while still enabling exclusive control of the physical resource by one application program. Control tokens are used to limit control to one proxy. The proxy having the control token is tracked in an access control list. Java API methods that can alter the state of a physical resource are marked with an access control attribute during grinding. A resource management module intercepts API methods attempting to obtain control of the physical resource. If a proxy controlled by the application program invoking the intercepted method has control the method is allowed to use the proxy to control the physical resource.
Owner:COMCAST CABLE COMM MANAGEMENT LLC
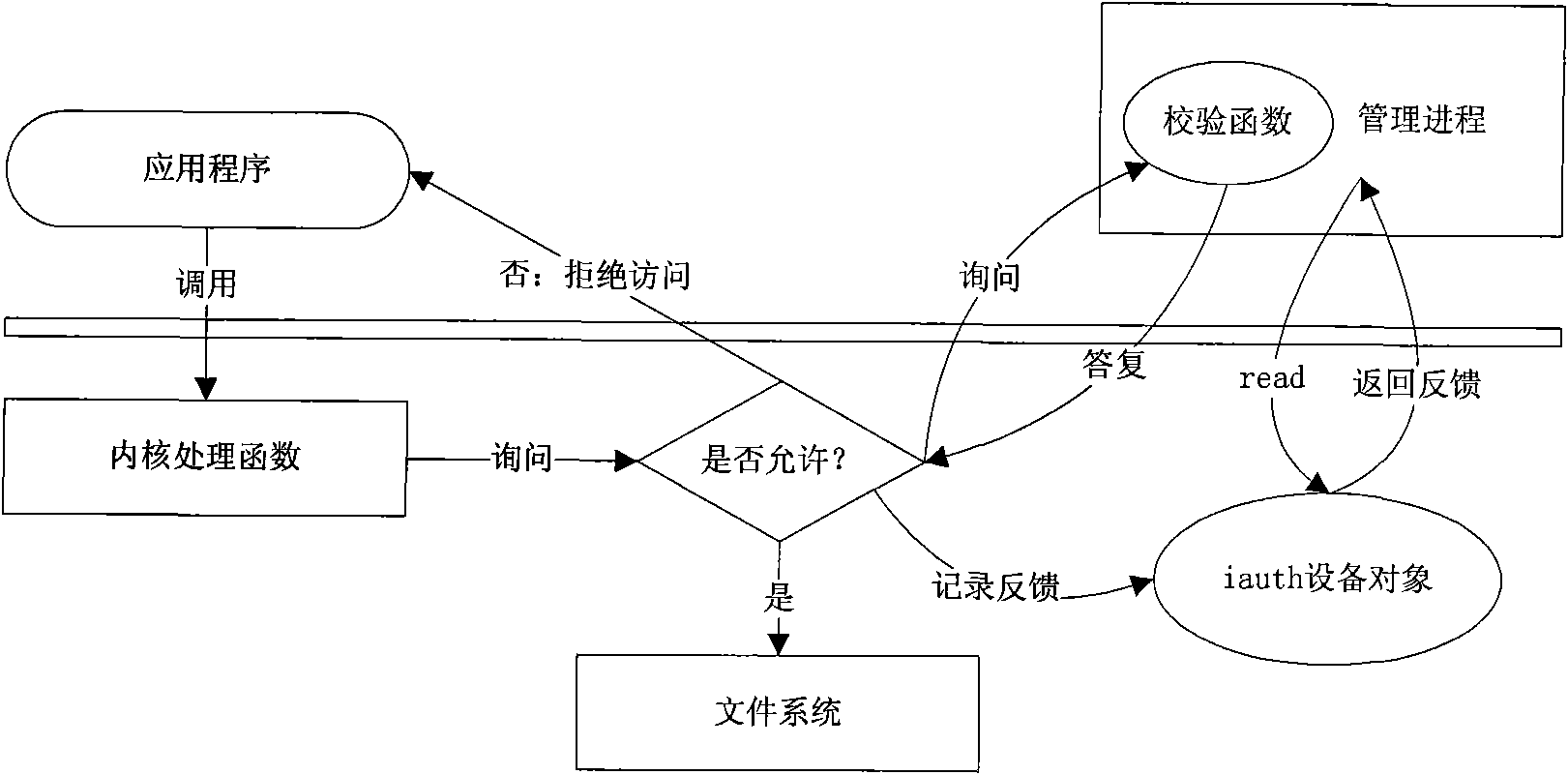
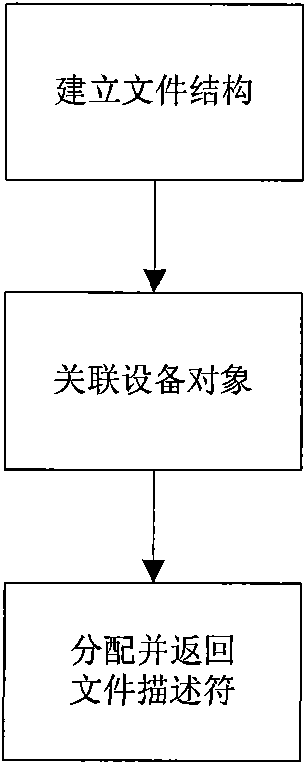
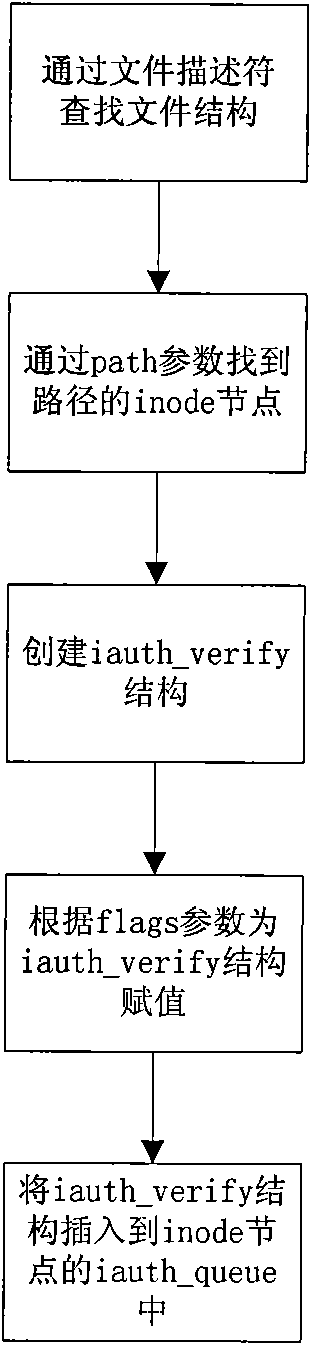
File system operation intercepting method based on event monitoring mechanism
ActiveCN101556608AAdd monitoring at willAdd any interceptioPlatform integrity maintainanceSpecial data processing applicationsSystems managementFile system
The invention relates to a file system operation intercepting method based on an event monitoring mechanism. The method comprises the following steps: a supervisor program which is trusted by a user calls function iauth_init to start the intercept service, and the function returns a file descriptor; the supervisor program calls function iauth_add_watch to monitor the key part of a system, and when the function is called, the supervisor program is required to specify a call back function so as to judge whether an access is illegal; when other application programs try to read and write monitored files, the call back function provided by the supervisor program can be called and decides the validity of the reading and writing so as to judge whether to let the reading and writing to pass or reject the reading and writing, and the action can lead the file operation of the application program which is tried to be read and written to be successful or failed. The invention has the advantages that the method provides user-friendly system call to lead a system manager to arbitrarily add monitoring, intercepting and preventing functions to the file system operation of the computer. The function can provide convenience for the application software on the system security aspect.
Owner:INSIGMA TECHNOLOGY CO LTD
Firing table fitting-based low-altitude low-speed small object intercepting method
InactiveCN102087082AIncrease the chance of a single hitEasy to operateDefence devicesWeapon control systemsLow speedData information
The invention discloses a firing table fitting-based low-altitude low-speed small object intercepting method. Used components comprise an object probing system, a command and control system, a launch control system, an interception executive system, a communication bus a, a communication bus b and a communication bus c. A set of firing table data information under a standard working condition and fitting parameters under different working conditions are stored in the systems in advance; and according to object flight data and environment data parameters, the launch control system predicts, measures an aiming point in advance, calculates and control the time sequence of every step in a combat process, and outputs firing data to the interception executive system to realize object interception. The method can effectively simplify the intercepting and operating process of a low-altitude low-speed small object, realizes combat process ground control on a non-control missile, improves the single shot hit probability of an interception system, and lowers interception cost.
Owner:BEIJING MECHANICAL EQUIP INST
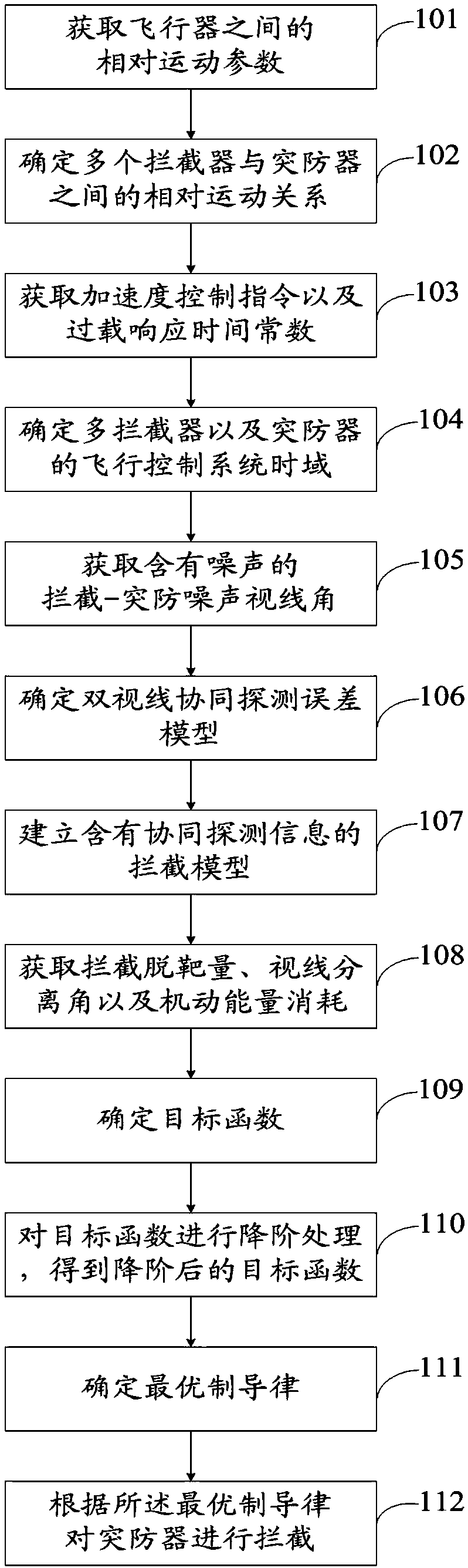
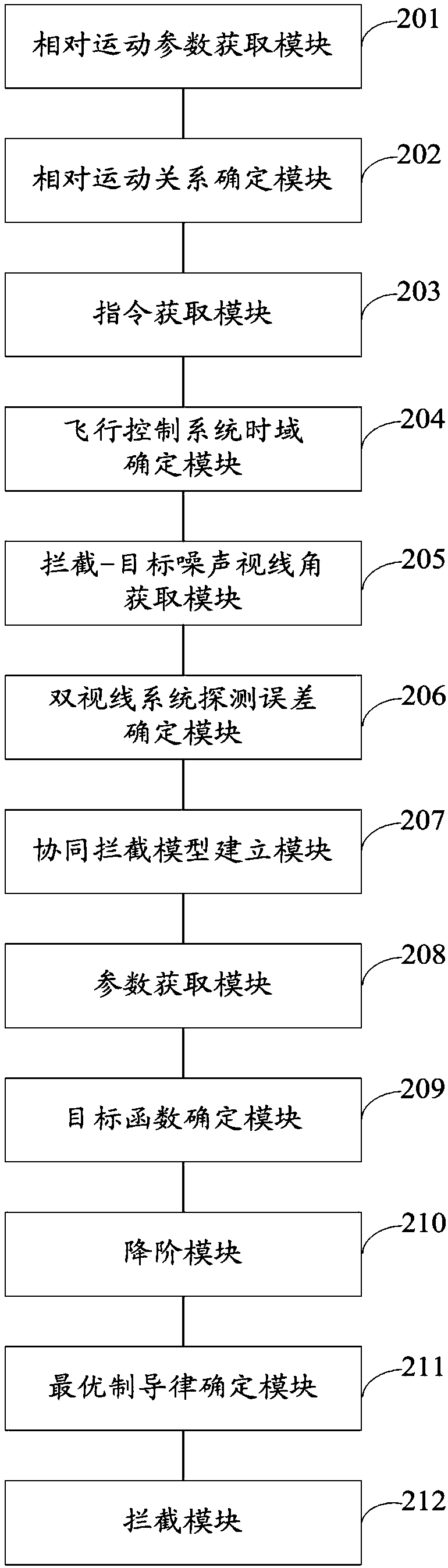
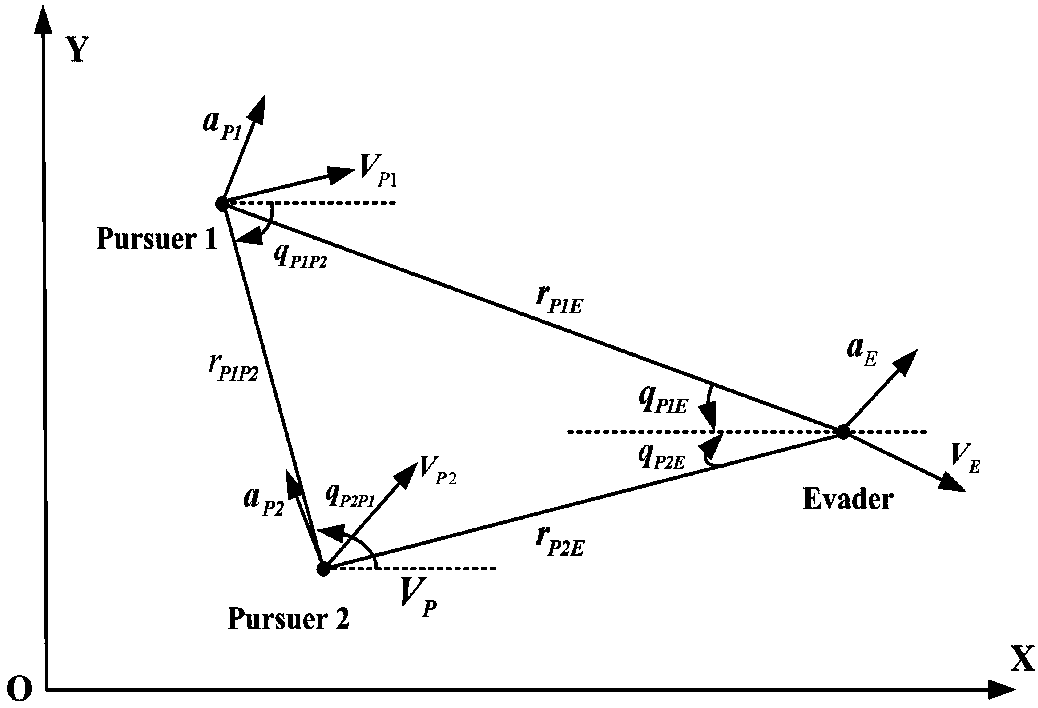
Multiple interceptor collaborative detection and guidance integrated type intercepting method and system
ActiveCN108362174AReduce collaborative detection errorImprove detection accuracyDefence devicesComplex mathematical operationsOrder reductionOptimal control
The invention discloses a multiple interceptor collaborative detection and guidance integrated type intercepting method and system. On the basis of an aircraft relative motion relation and a double-sight collaborative detection error model, an interception model containing collaborative detection information is established; by taking intercepting miss distance, maneuvering energy consumption minimizing and effective modulation of an sight separation angle as control and optimization targets, a system performance constraint function is determined, and through system order reduction, and on thebasis of optimal control theory, an optimal guidance law is determined; and collaborative interception is carried out on a penetration device according to the optimal guidance law, and the optimal guidance law can ensure that multiple aircrafts has the collaborative detection effect in the collaborative guidance process. By adopting the intercepting method and system, the collaborative detection and guidance precision is improved, and meanwhile, the integrated design of multiple interceptors on the two links of cooperative detection and guidance is realized.
Owner:ROCKET FORCE UNIV OF ENG
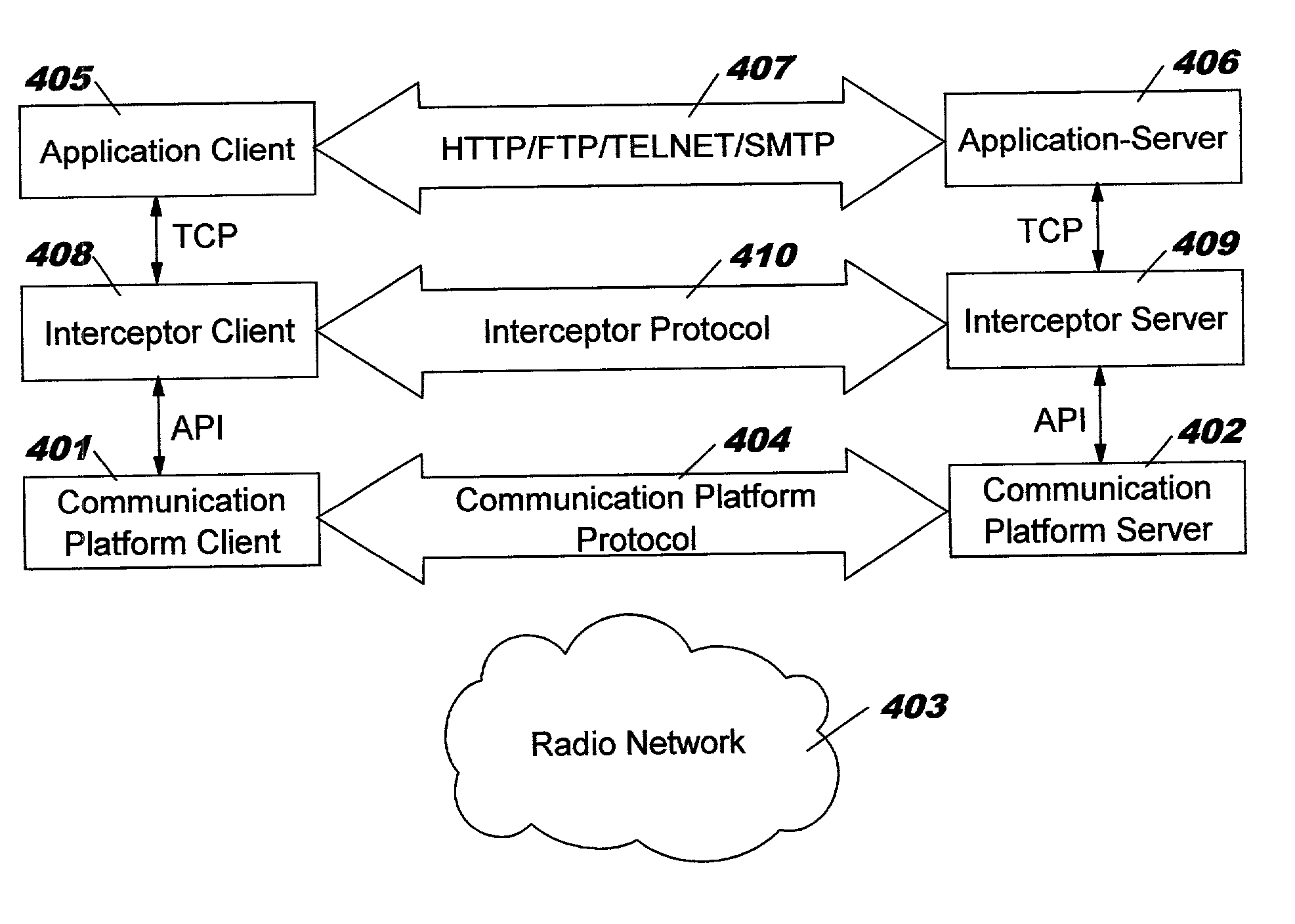
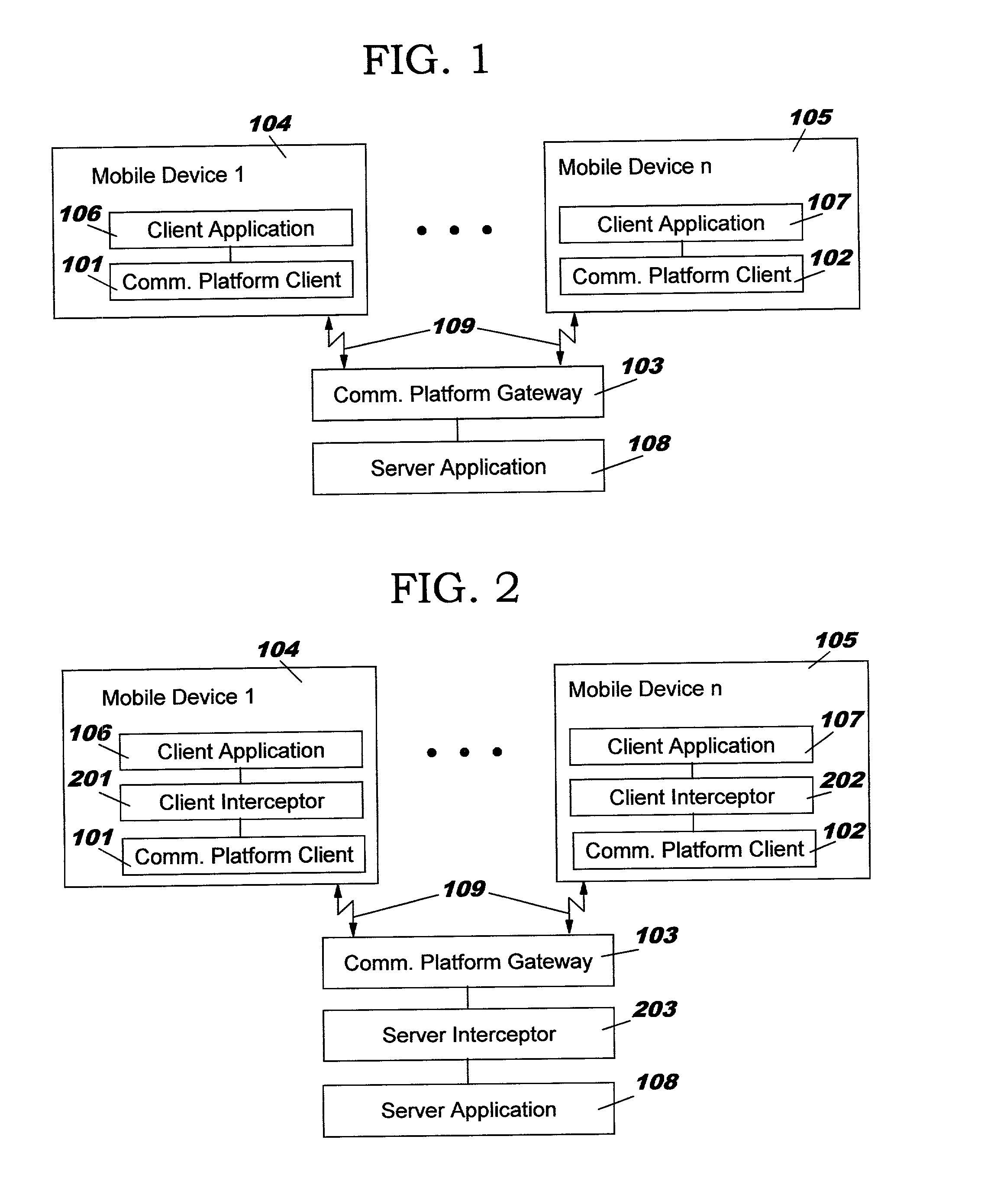
Interception method and system for compensating disadvantageous characteristics of a communication protocol
InactiveUS7139822B2Effective wayMultiple digital computer combinationsTransmissionApplication softwareClient-side
Means and method of data communication compensating disadvantageous characteristics of a first protocol for data communication between a client-application and a server-application. Communication requests of the client application and the server application adhering to a second protocol are intercepted by an client interceptor and a server interceptor. Besides mapping the second protocol onto the first protocol and back again the interceptors compensate disadvantageous characteristics inherent to the first protocol or arising from the combination of protocols transparently.
Owner:KYNDRYL INC
Convenient method and system for electronic text-processing and searching
InactiveCN101201841AEasy to skipMeeting urgent needsSpecial data processing applicationsText processingKeyword search
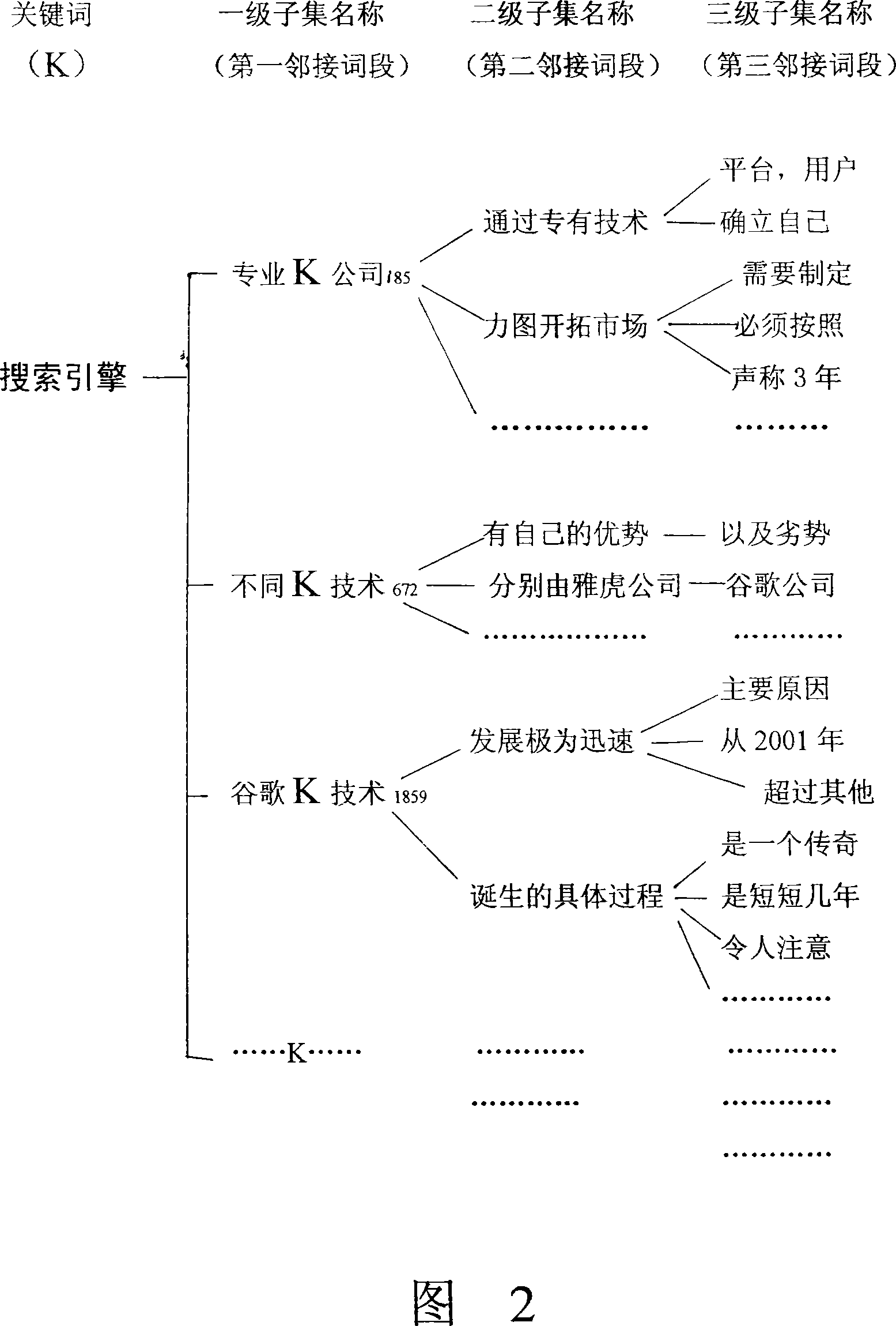
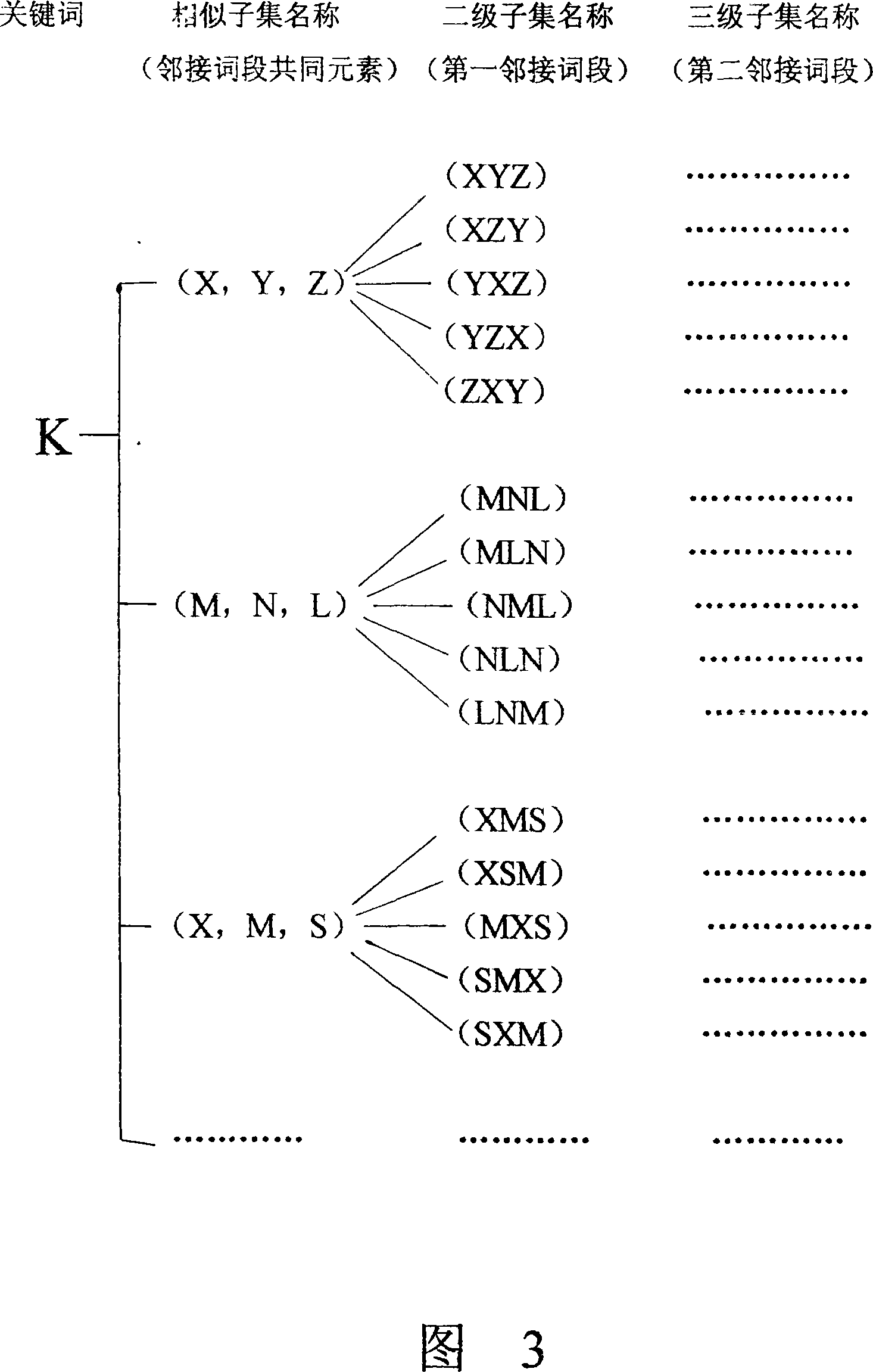
The invention relates to a method and a system for treating a plurality of electronic texts containing same keywords and is implemented by a computer. The invention includes the following steps: obtaining a plurality of electronic texts containing same keywords, stipulating the word quantity contained in an adjacent word segment and the intercepting method of the adjacent word segment, according to whether the adjacent word segment of the keyword in each text content of part of or whole text is same with other texts or not, classifying the text and other texts into the same or different subclasses or classes which are subject to same or different processing. The massive searching results obtained by keyword search can form multilevel subset systems, catalogs or example sequences, core contents of which are not repeated or lost; therefore, the invention can help users to narrow searching range rapidly and strictly, and to obtain the expected searching results completely and accurately.
Owner:刘二中
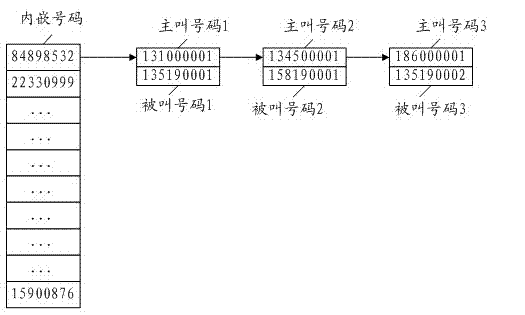
Spam message intercepting method
InactiveCN102761872ASupport identificationSupport extractionSecurity arrangementDigital numberBlack list
The invention discloses a spam message intercepting method which comprises the steps of: extracting a calling number of a short message forwarded by a short message center and an embedded digital number in a content of the short message, matching the extracted embedded digital number with a number keyword stored in a spam message monitoring platform, matching the extracted calling number with a blacklist stored in the spam message monitoring platform, if one matching fails, judging that the short message forwarded from the short message center is the spam message, and intercepting the spam message. According to the invention, the recognition and the extraction of a generalized digital number are supported, a masking spam message can be effectively recognized, the total flow and the calling and called dispersion combined, the accuracy rate is high, misjudgment can be effectively prevented, user complaint can be effectively reduced, the whole intercepting process does not need to be participated manually, the blacklist and the number keyword are automatically updated, and manual cost is saved.
Owner:成都四方信息技术有限公司
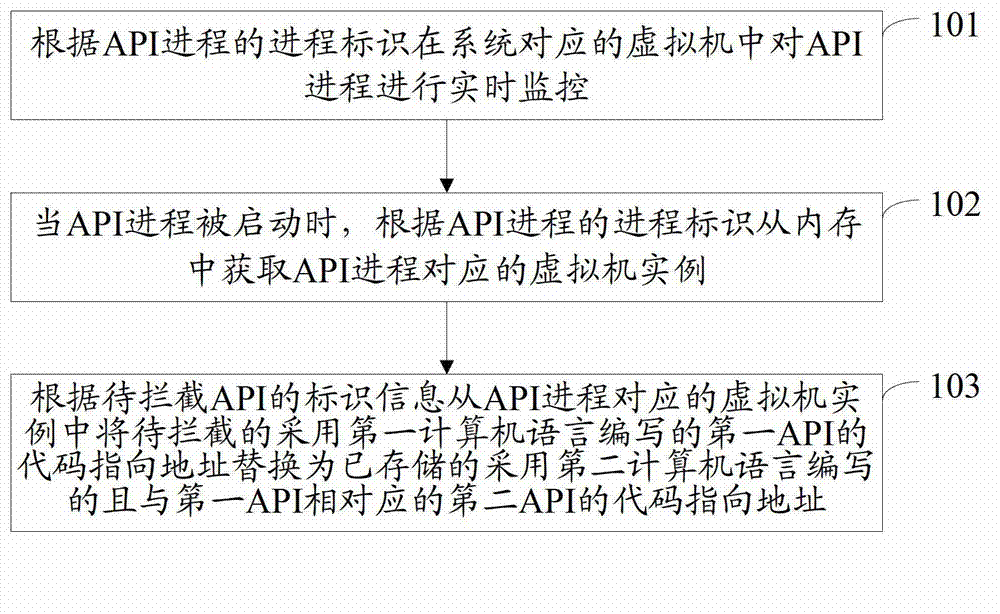
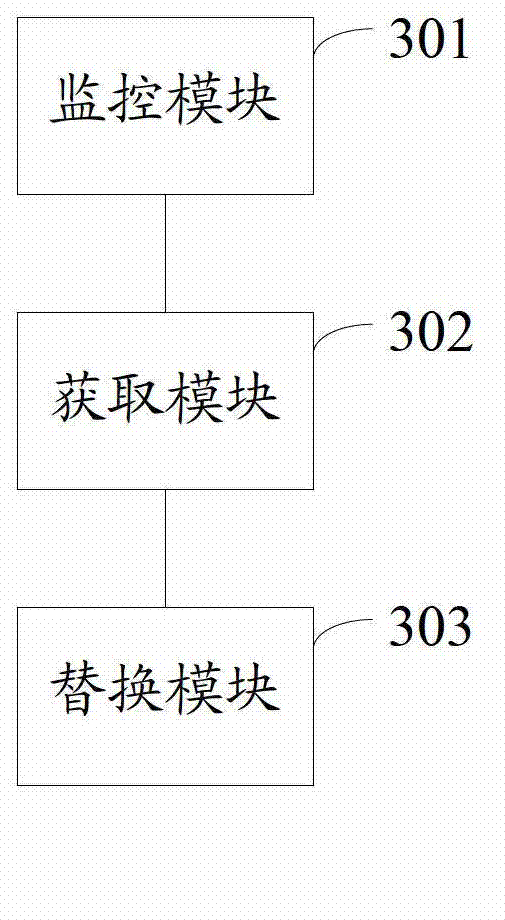
Application program interface (API) intercepting method and device and mobile terminal
ActiveCN102855138AImplement interceptionError identificationSpecific program execution arrangementsApplication programming interfaceHuman language
The invention discloses an application program interface (API) intercepting method, an API intercepting device and a mobile terminal and belongs to the field of mobile terminals. The method comprises the following steps of: monitoring an API progress in a virtual machine corresponding to the system in real time according to a progress identifier of the API progress; acquiring a virtual machine instance which corresponds to the API progress from a memory according to the progress identifier of the API progress when the API progress is started; replacing a code directing address of the intercepted first API written by the first computer language into a code directing address of the stored second API which is written by the second computer language and corresponds to the first API from the virtual machine instance which corresponds to the API progress according to the identification information of the intercepted API, wherein the second language is different from the first code; and controlling the API progress through a second function. The device comprises a monitoring module, an acquisition module and a replacement module. The application function can be expanded or modified.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
Advertisement intercepting method and advertisement intercepting device
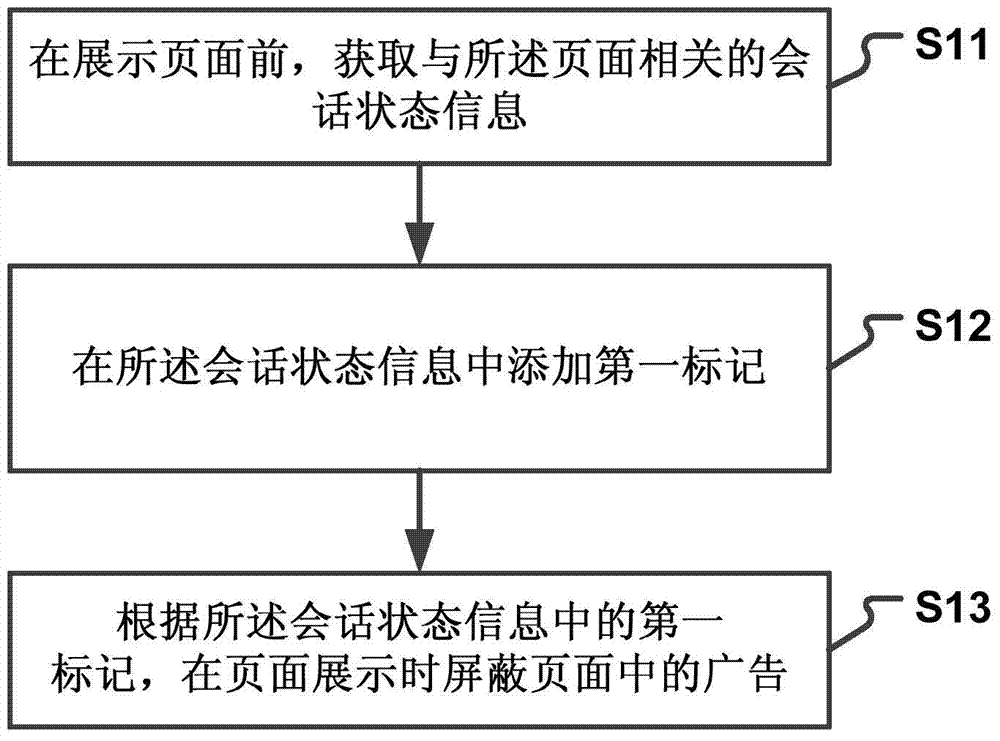
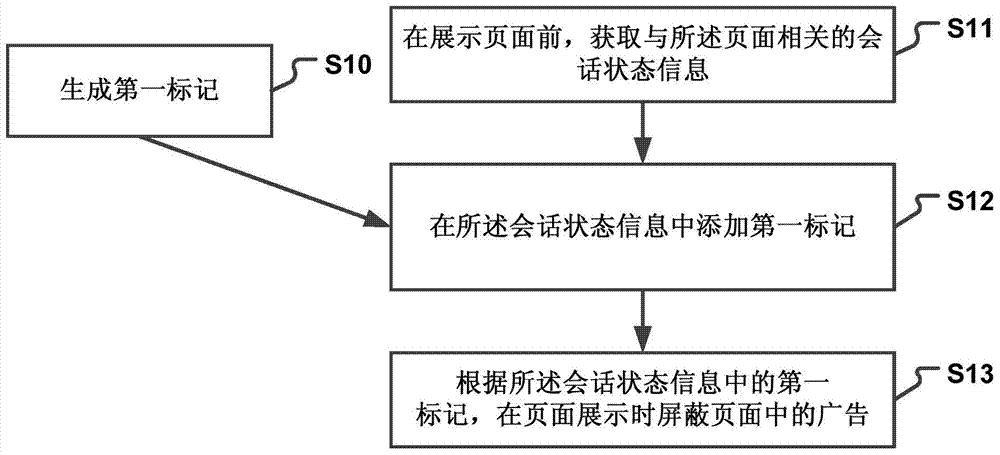
ActiveCN103927356AImprove experienceAchieve immune functionSoftware engineeringSpecial data processing applicationsSession stateWorld Wide Web
The invention discloses an advertisement intercepting method and an advertisement intercepting device. The advertisement intercepting method includes: before displaying a page, acquiring dialogue state information relates to the page; adding a first sign in the dialogue state information, wherein the first sign is used for identifying advertisements in the page to be accessed; shielding advertisements in the page when the page is displayed according to the first sign in the dialogue state information. The invention further discloses the advertisement intercepting device which comprises an acquiring module, a signing module and a displaying module. The advertisement intercepting method and the advertisement intercepting device are used for realizing immunity for 'popup advertisements'.
Owner:BEIJING KINGSOFT NETWORK TECH
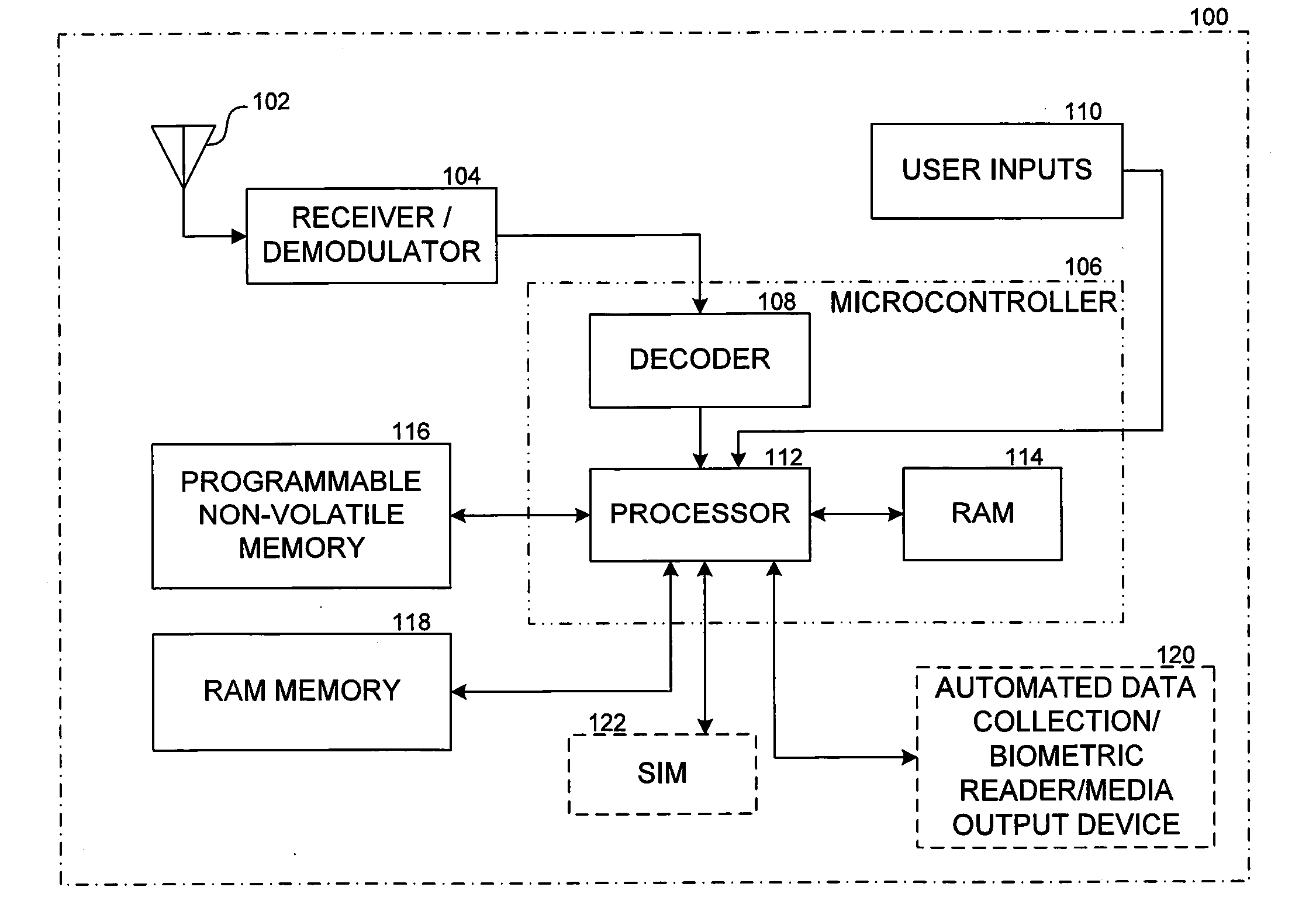
Call intercept methods, such as for customer self-support on a mobile device
ActiveUS20110117894A1Special service for subscribersCommmunication supplementary servicesMobile deviceCustomer support
A method for intercepting calls from a remote or mobile device for customer self-support detects when users or subscribers dial one or more predetermined numbers. If the number corresponds to one of the predetermined numbers (such as a customer support number), the phone may intercept the call and display a list of potential solutions to the subscriber's problems. Various other features and embodiments art disclosed.
Owner:NUANCE COMM INC
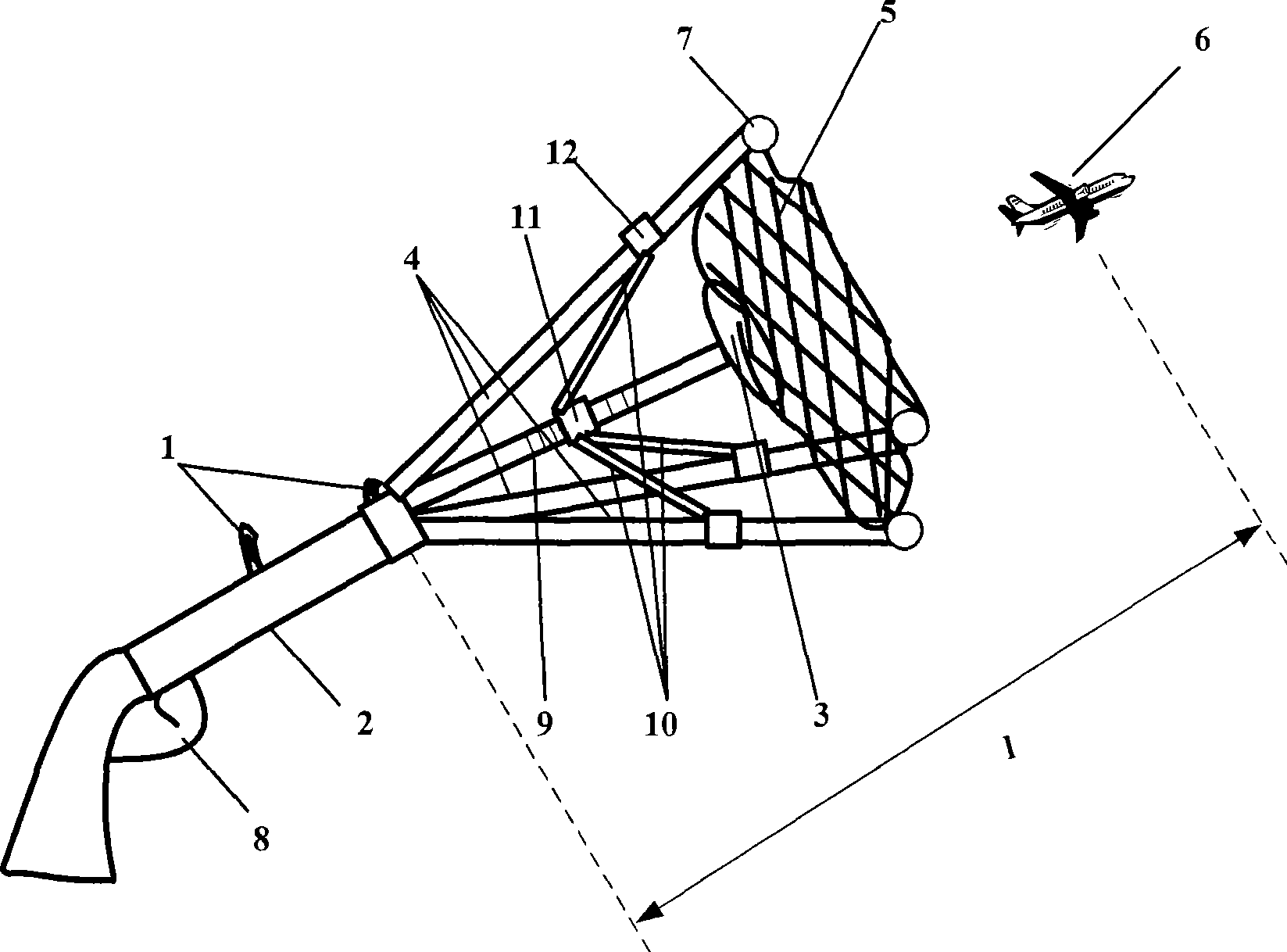
Aeromodelling interception method and device
The invention provides a method and a device for intercepting a navigation model. The navigation model interception device comprises a launching device, an interception net and a launching missile, wherein steel corners of the interception net is connected with the launching missile, the interception net can be launched along with the launching missile and expanded, so that the targeted navigation model can be captured by the interception net. The method and the device fill up the blank of the navigation model interception method and device in the prior art, and the device is simple and easy to operate.
Owner:INST OF MECHANICS - CHINESE ACAD OF SCI
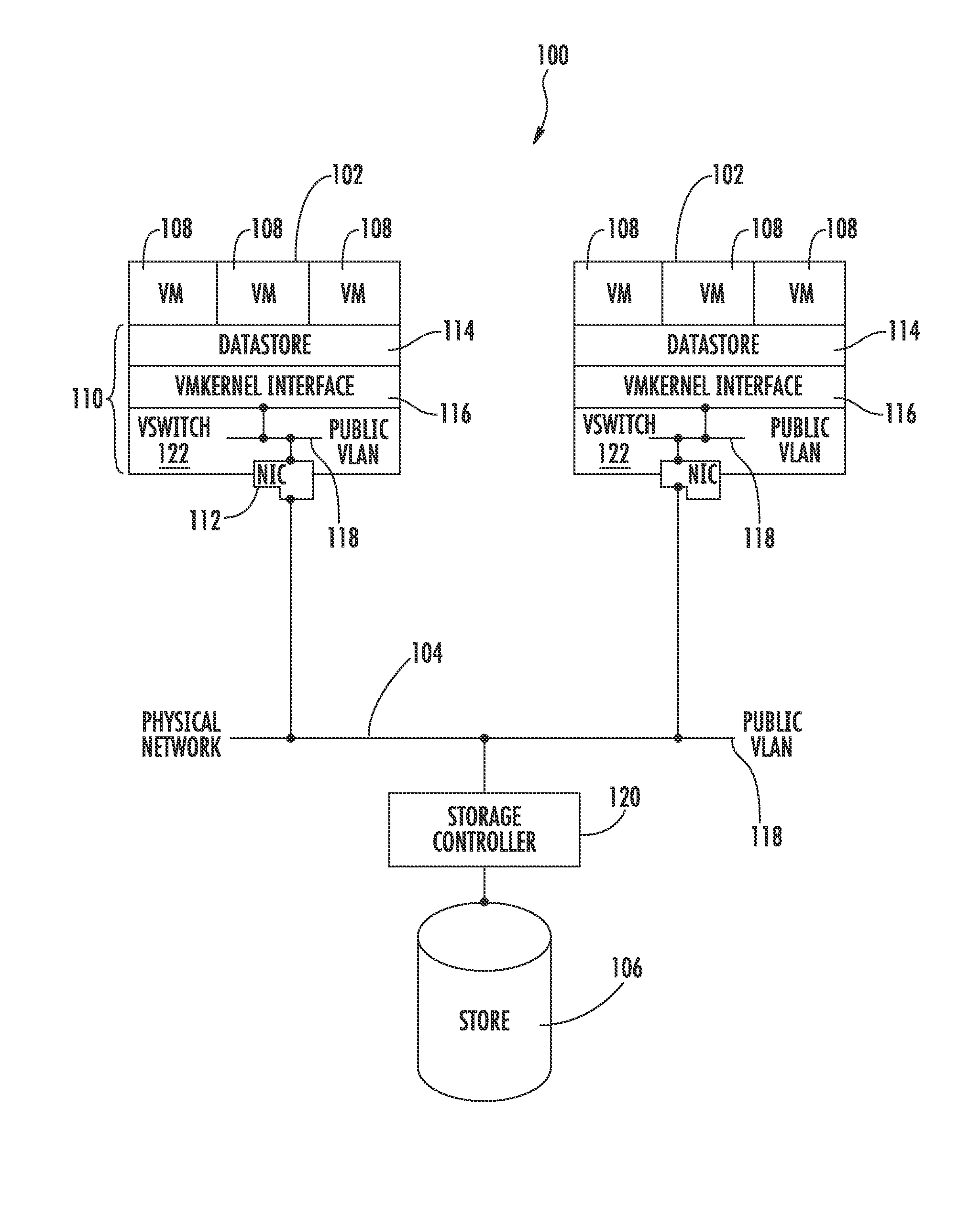
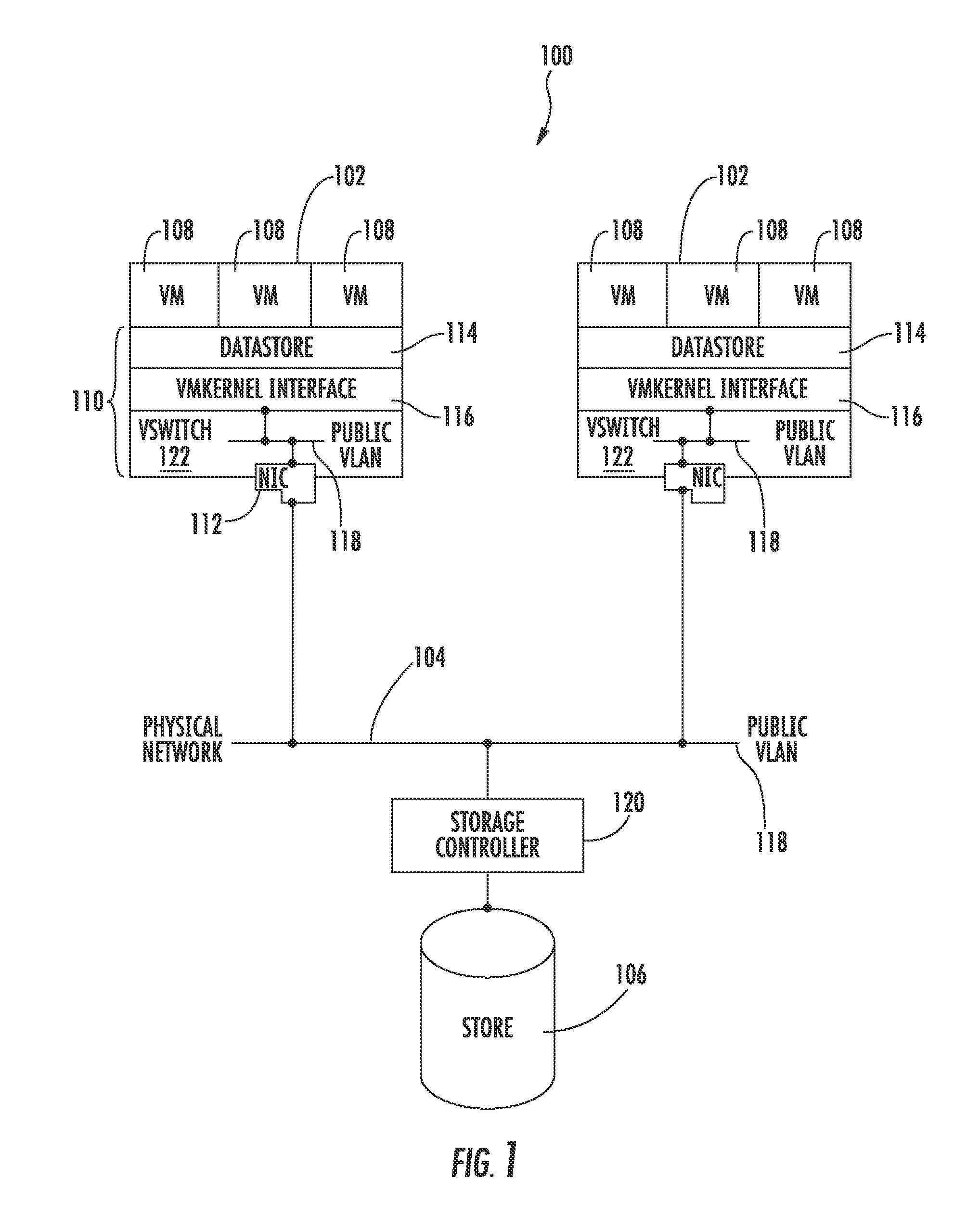
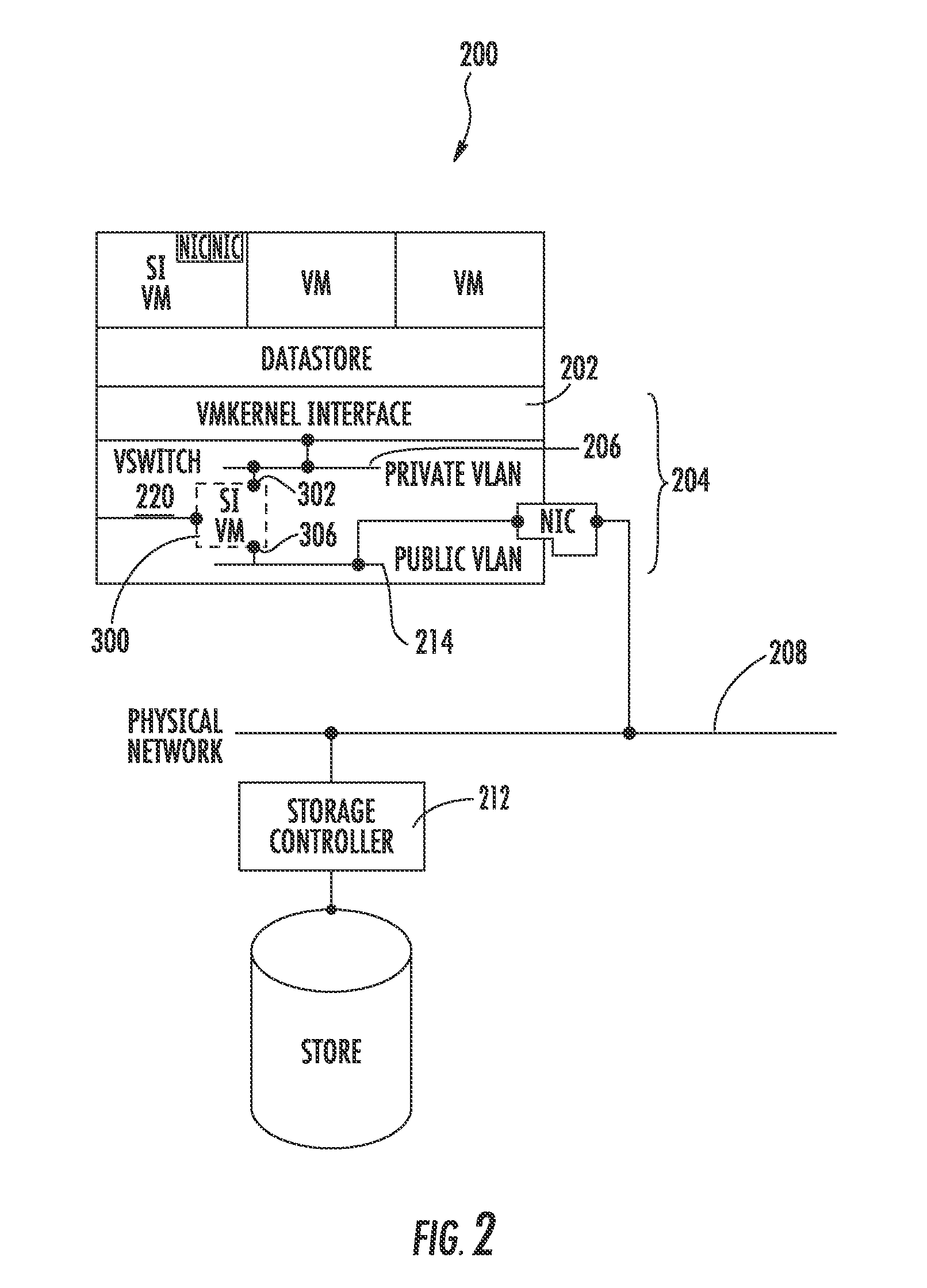
Hypervisor Storage Intercept Method
InactiveUS20140282542A1Digital computer detailsData switching networksControl storeVirtual appliance
Two levels of address masquerading are employed to make a virtual appliance a transparent gateway between a hypervisor and a storage controller. This approach allows a virtual appliance to be inserted or removed from the IP storage path of a hypervisor without disrupting communications. One embodiment of the invention enables a virtual appliance to intercept, manipulate, reprioritize, or otherwise affect IP (Internet Protocol) storage protocols sent or received between a hypervisor and storage controller(s).
Owner:INFINIO SYST
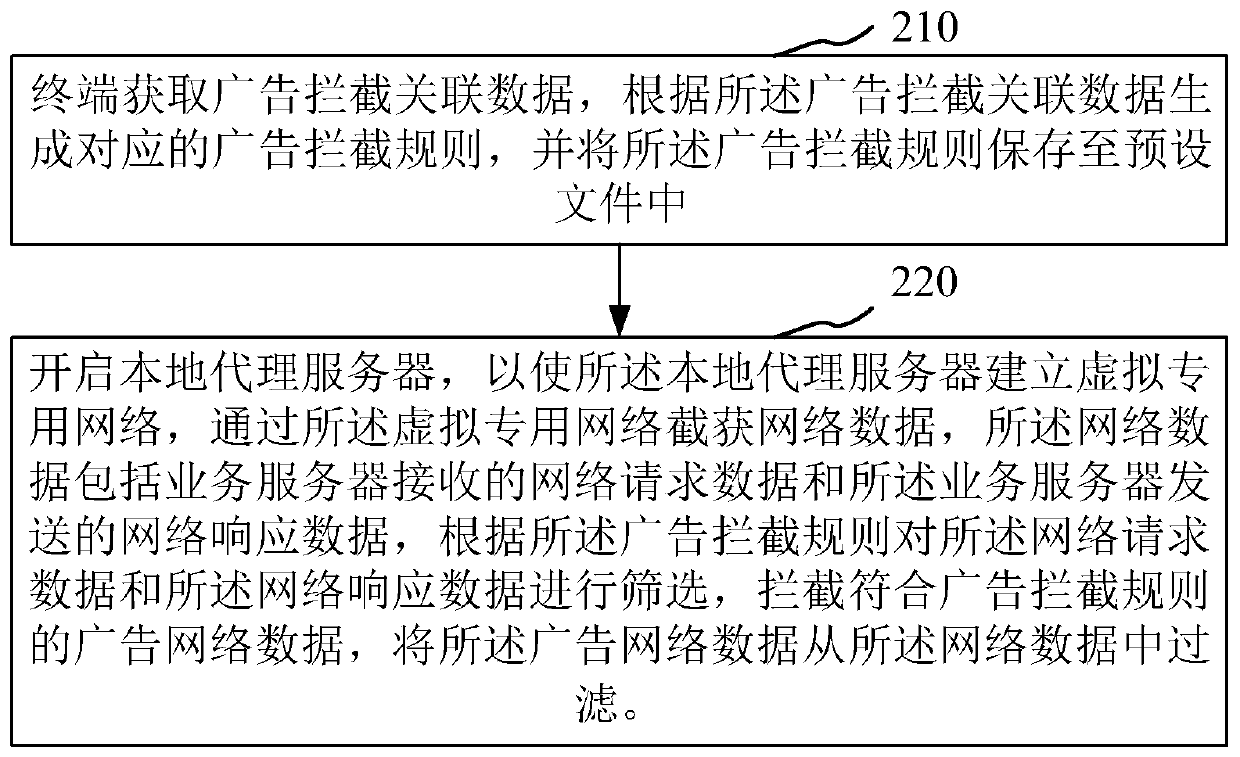
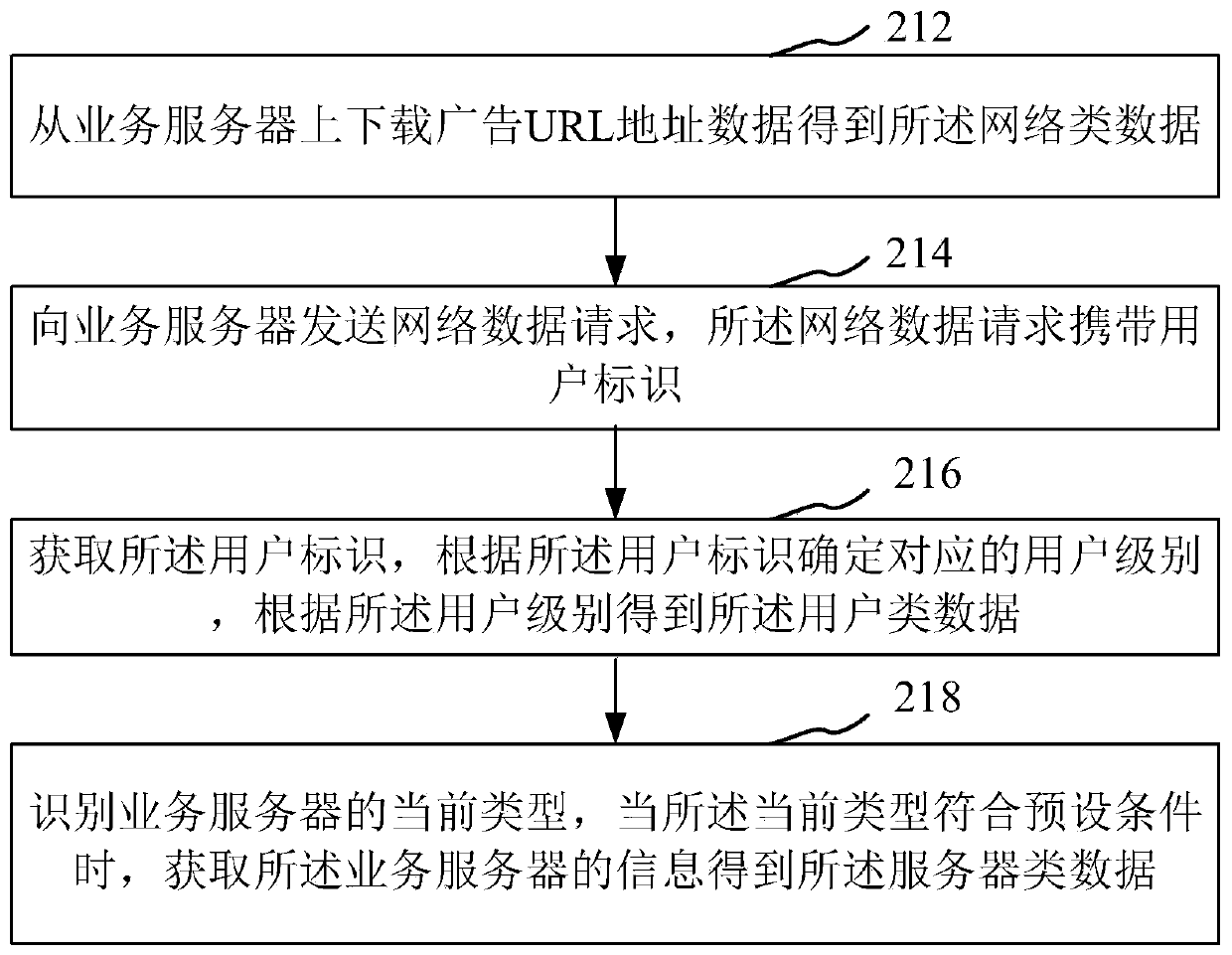
Advertisement interception method and device and storage medium
ActiveCN109842617ASave traffic resourcesRun fastTransmissionSpecial data processing applicationsTraffic capacityPrivate network
The invention relates to the field of monitoring, and provides an advertisement intercepting method and device and a storage medium. The method comprises the following steps: acquiring advertisement interception associated data, generating a corresponding advertisement interception rule according to the advertisement interception associated data, and storing the advertisement interception rule into a preset file; starting a local proxy server, establishing a virtual private network through the local proxy server, intercepting network data through the virtual private network, and the network data comprise network request data received by a service server and network response data sent by the service server; and the local server screens the network request data and the network response dataaccording to the advertisement interception rule, intercepts the advertisement network data conforming to the advertisement interception rule, and filters the advertisement network data from the network data. And the intercepted network data is modified and reset according to the advertisement interception rule, so that the effect of saving flow resources can be achieved, and the operation speedis increased.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
Rapid metallographic determination method for grain size of GCr15 steel bearing assembly
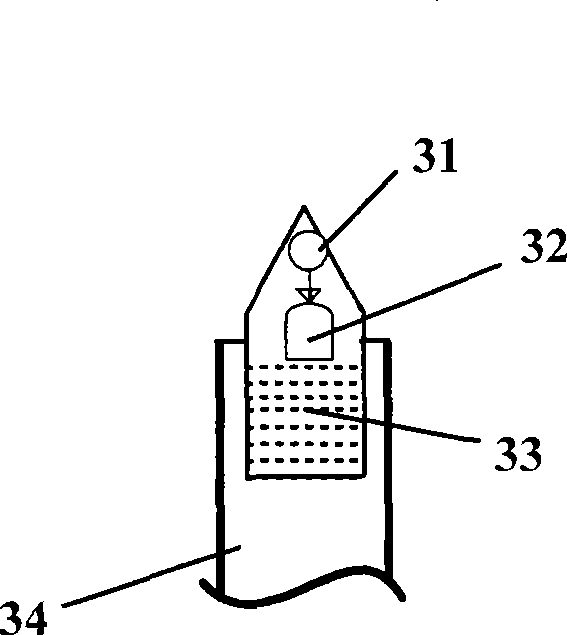
InactiveCN103344532AEasy to operateAccelerated corrosionPreparing sample for investigationParticle size analysisMetallurgyImaging analysis
The invention belongs to the technical field of bearing detection. The invention relates to a rapid metallographic determination method for of grain size of a GCr15 steel bearing assembly. The rapid metallographic determination method comprises the following steps of 1), preparing an etching solution; 2), etching a sample of the bearing assembly; 3), determining the grain size: shooting a metallograph of a grain boundary profile by using an optical microscope, then determining the grain size of the metallograph by using image analysis software and in reference to steel size determination standards of an average grain size of the steel by an intercept method. The clear grain boundary profile can be obtained by using a rapid and easily operational chemical etching method; and efficient and accurate determination for the GCr15 steel bearing assembly can be realized by combining the metallographic determination method for the grain size.
Owner:WUHAN UNIV OF TECH
Method and system for automatically guiding an unmanned vechile
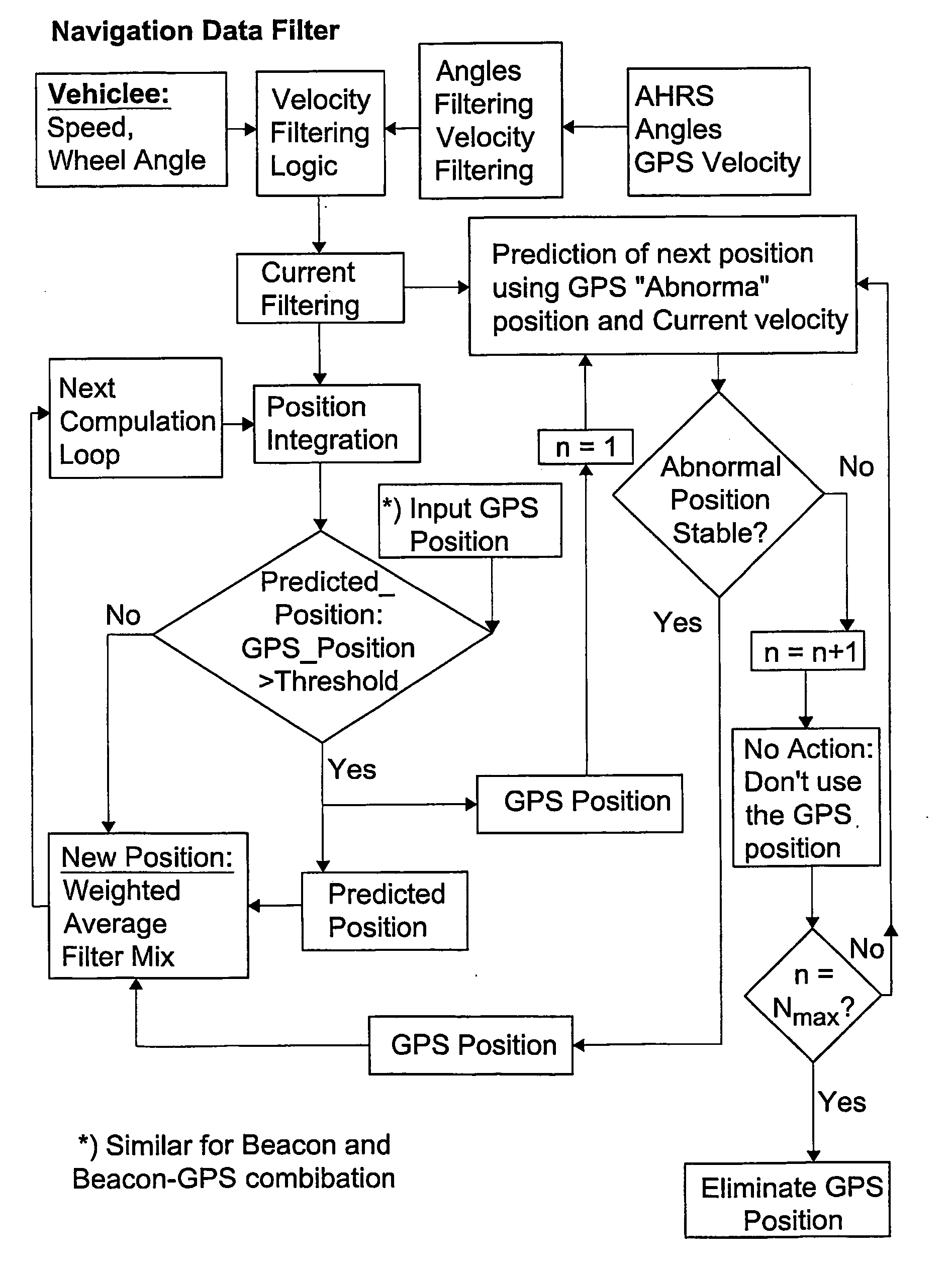
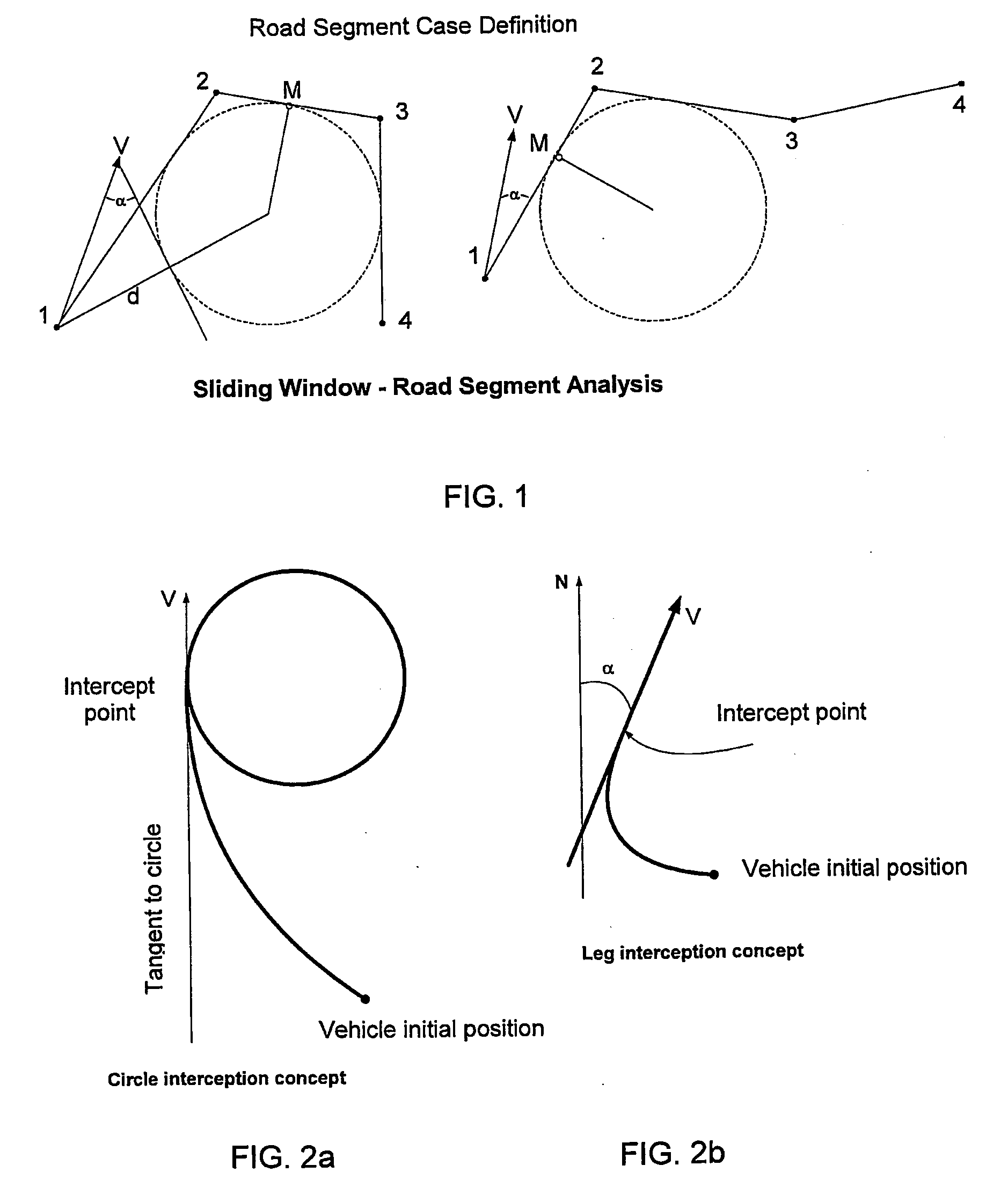
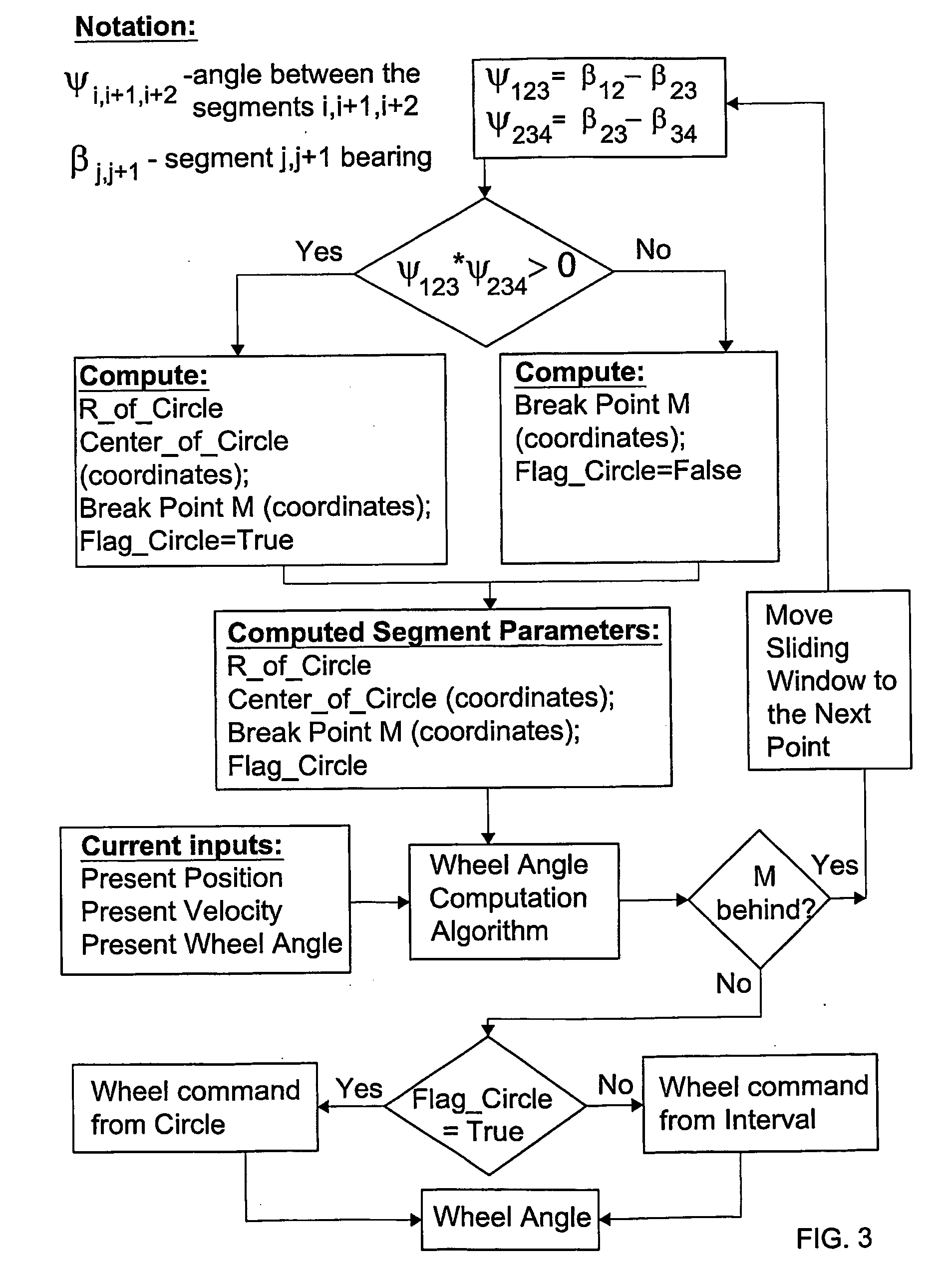
InactiveUS20100198442A1Navigation by speed/acceleration measurementsSatellite radio beaconingEngineeringLinearity
An unmanned vehicle is guided by selecting locations along a predetermined mute defining adjacent first, second and third linear portions. If an imaginary circle can be constructed that is mutually tangential to all three linear portions or to projections thereof, the vehicle is guided according to the circle intercept method until it reaches an imaginary point of contact (M) between the circle and the second linear portion or passes its traverse. If an imaginary circle cannot be constructed that is mutually tangential to all three linear portions or to projections thereof, an imaginary circle is constructed that is mutually tangential to the first and second linear portions; and the vehicle is guided along according to the leg intercept method until it reaches an imaginary point of contact (M) between the circle and the first linear portion or passes its traverse. The process is repeated iteratively in respect of successive locations.
Owner:ISRAEL AEROSPACE IND
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com