Method for detecting false station in GSM and LTE network
A detection method and pseudo base station technology, which is applied in the field of detection of pseudo base stations in GSM and LTE networks, can solve problems such as the inability to eliminate pseudo base stations, and achieve the effects of excellent cost performance, easy portability, and enhanced communication security performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
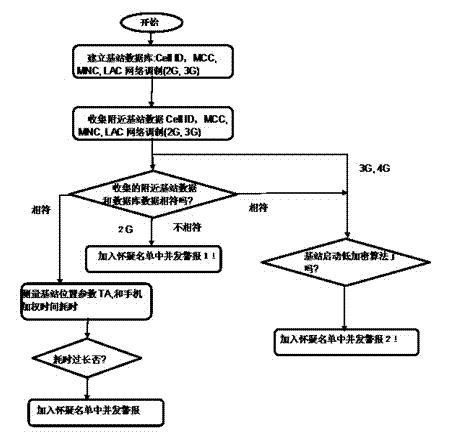
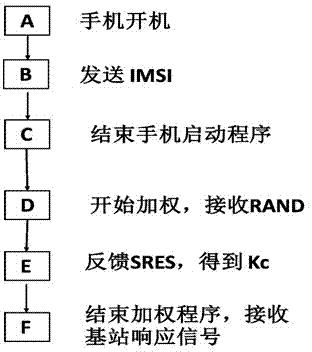
[0021] In the 2G network, as long as a fake base station sends a similar broadcast, it can deceive the terminal to re-enter the network of the new base station. The terminal will not verify the identity of the base station but directly send the IMSI code. The terminal can be connected to its own network, and services such as calls and text messages can be completed through its own network. The process is roughly like this. First, the base station sends spectrum signals that can accept users through the BCH channel (also known as beacon channel). After the mobile phone receives this signal, it reads an IMSI code (approximately equal to the user ID) assigned by the operator from the SIM card. After receiving the IMSI code, the base station verifies whether the terminal (mobile phone) is a legal terminal, and then decides whether to allow it to access the network. If the base station agrees to allow the terminal to access the network, the base station will issue a RAND code to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com