Data leakage detecting method, system, device and storage medium
A data leakage and detection method technology, applied in the field of data security, can solve the problems of data leakage detection system such as missed judgment, difficult deployment, poor stability, etc., achieve convenient deployment and maintenance, prevent data encryption attacks, and improve speed and efficiency Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0050]It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
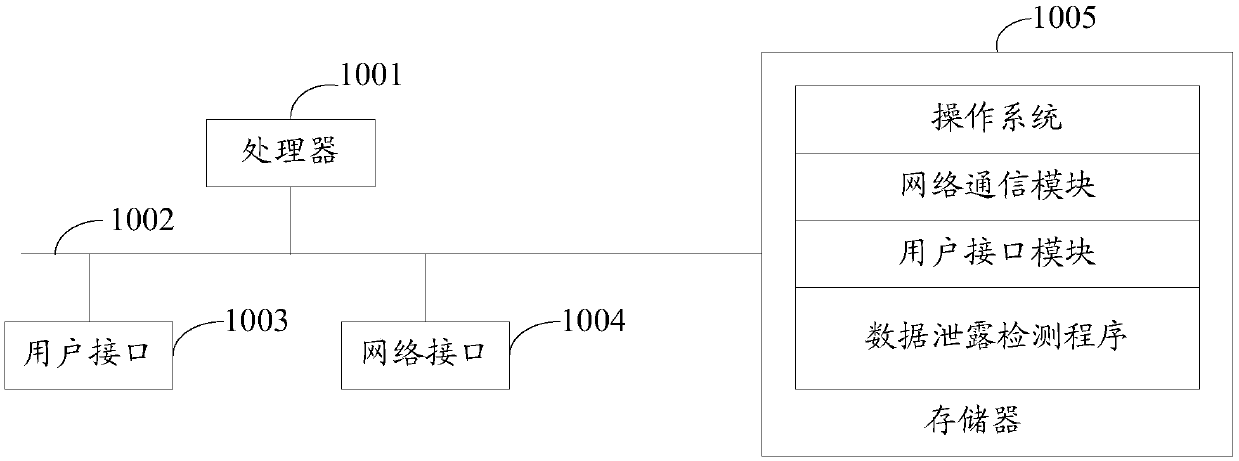
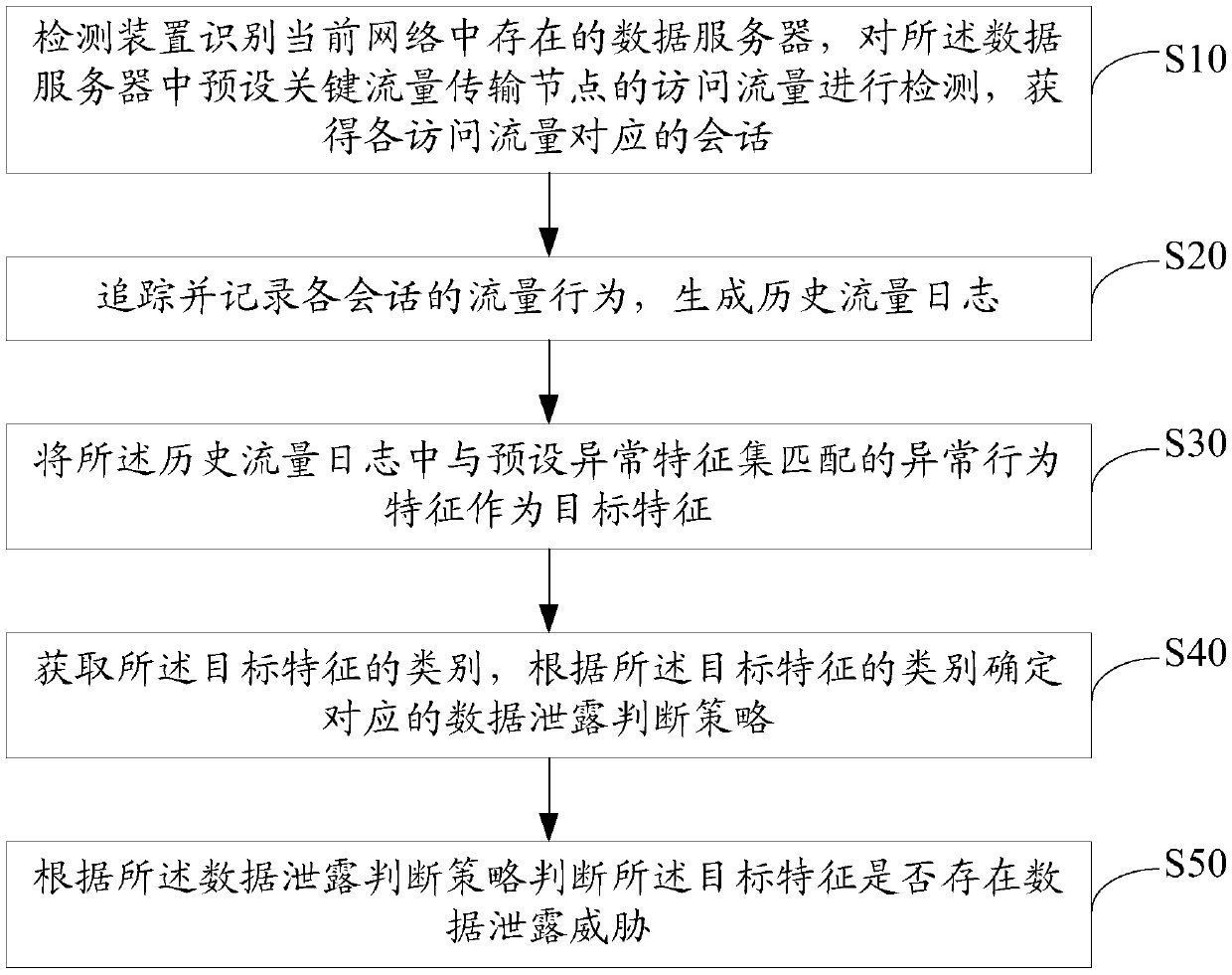
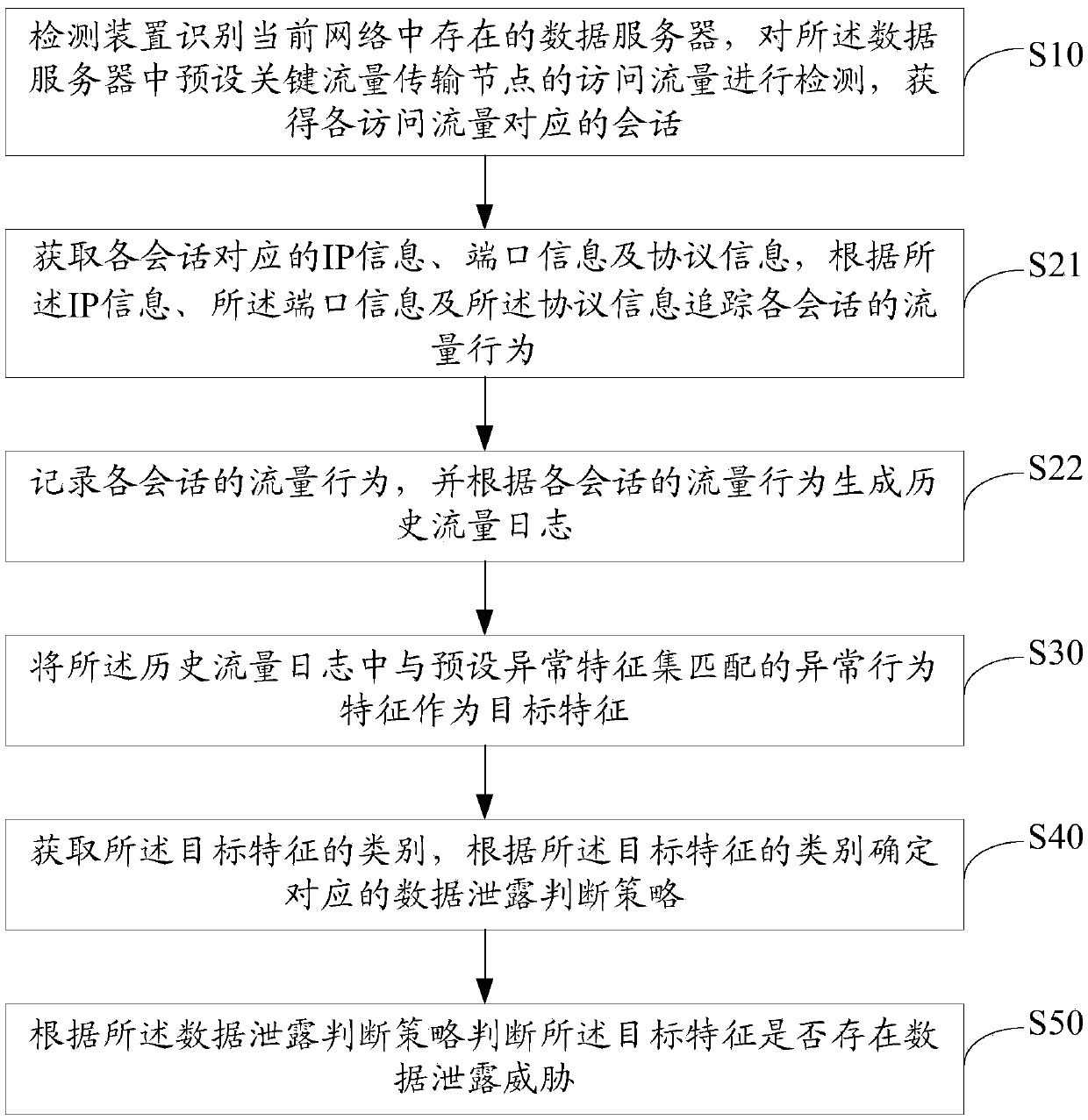
[0051] The solution of the embodiment of the present invention is mainly: identify the data server existing in the current network through the detection device, detect the access traffic of the preset key traffic transmission node in the data server, and obtain the session corresponding to each access traffic; track and Recording the traffic behavior of each session, generating a historical traffic log; using the abnormal behavior characteristics in the historical traffic log that match the preset abnormal feature set as the target feature; obtaining the category of the target feature, and determining according to the category of the target feature Corresponding data leakage judgment strategy; according to the data leakage judgment strategy, it is judged whether there is a data leakage threat in the target feature, and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com