OTP and user behavior-based certification and authorization method in mobile cloud computing environment
A computing environment, authentication and authorization technology, applied in the field of cloud computing security, can solve problems such as immaturity, high cost of identification equipment, poor stability, etc., and achieve the effect of preventing illegal users from operating, ensuring credibility, and ensuring security
Inactive Publication Date: 2015-11-25
JIANGSU BOZHI SOFTWARE TECH CO LTD
View PDF10 Cites 20 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
However, the technology is not yet mature enough, and there are problems such as high cost of identification equipment and poor stability.
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment Construction
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
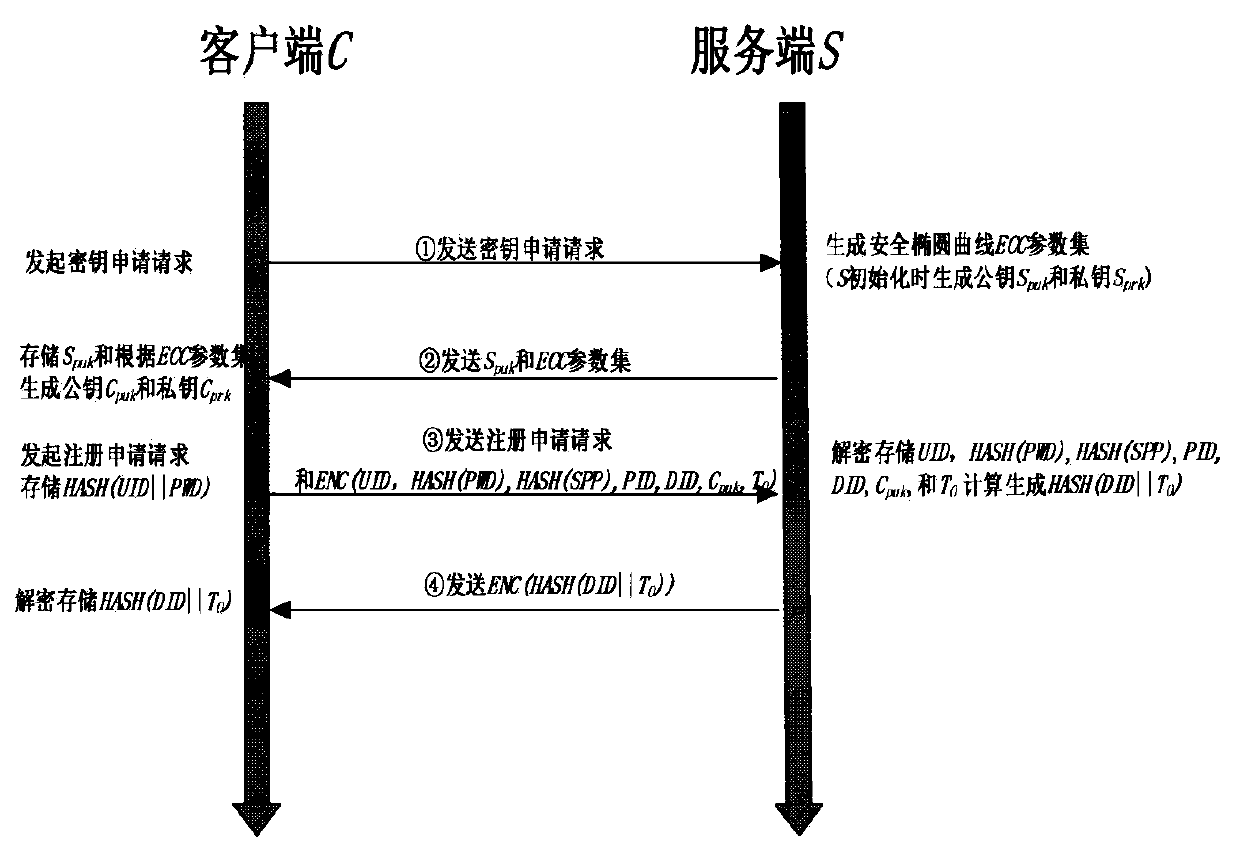
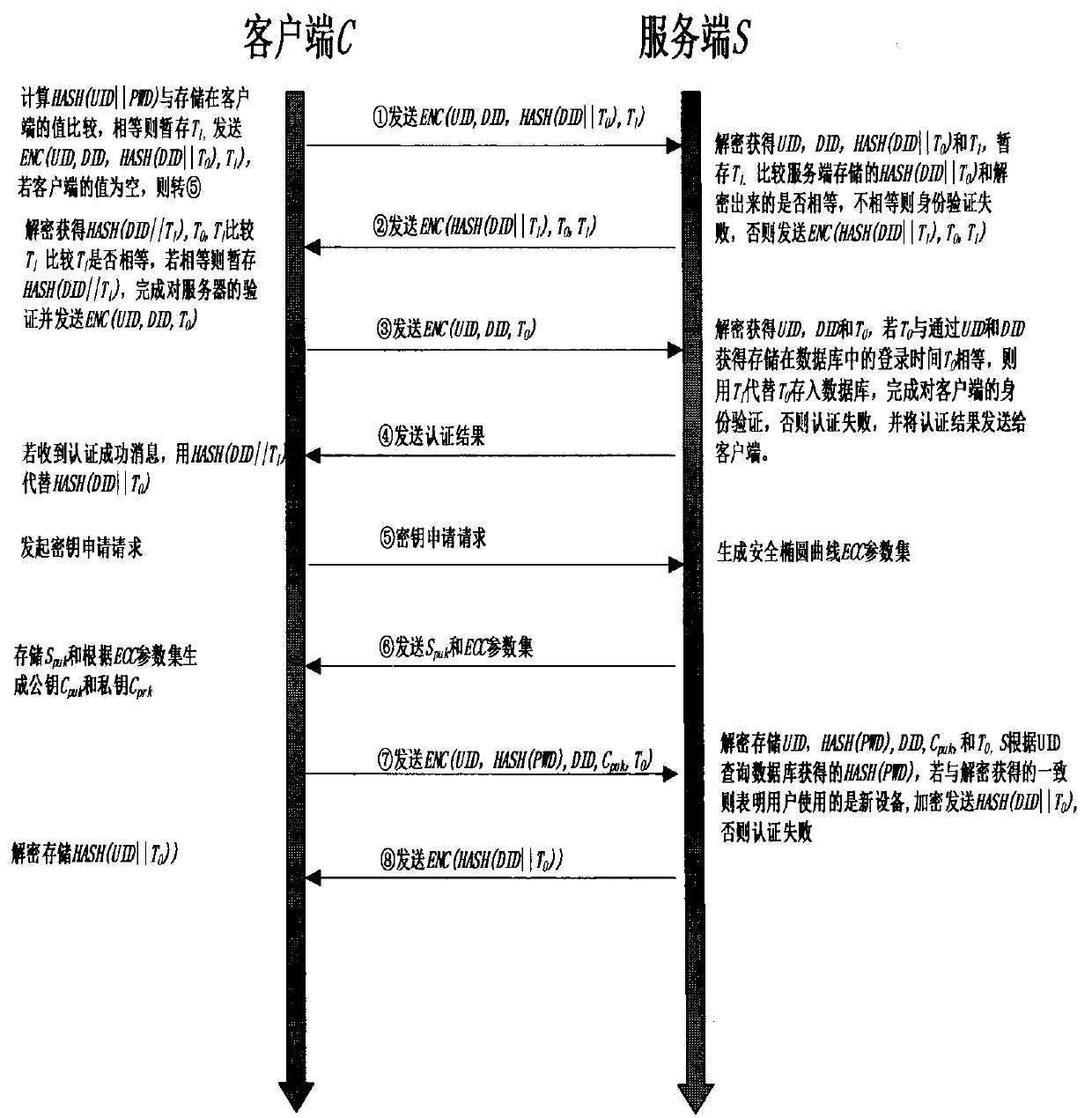
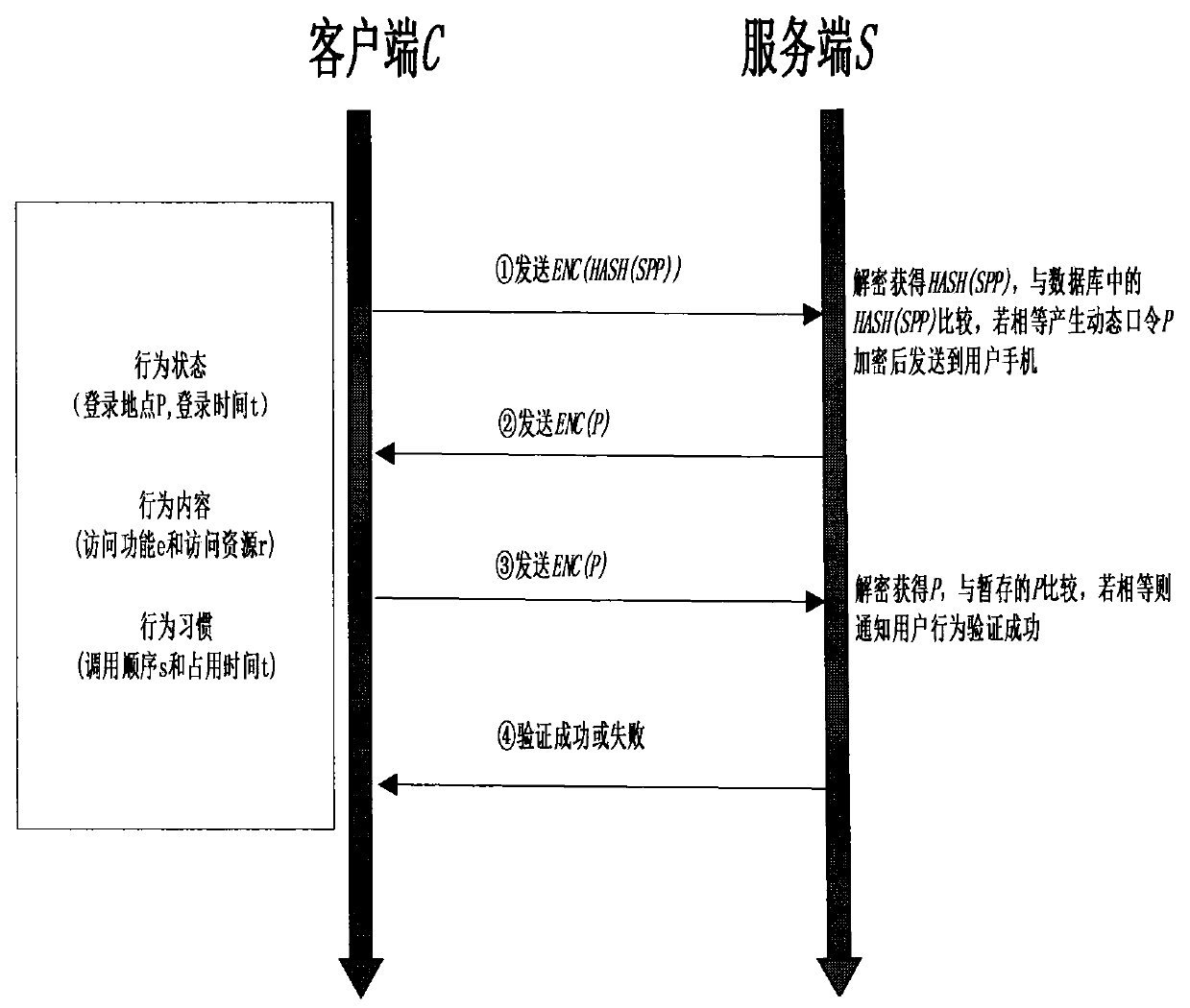
The present invention discloses an OTP and user behavior-based certification and authorization method in a mobile cloud computing environment. The method is characterized in that various intelligent mobile terminals available for users are enabled to be accessed to the cloud service via a wireless network in the mobile cloud computing environment and the bidirectional identity authentication between a client and a server is realized through improving the one-time password (OTP) technology. In this way, the safety and the reliability of the identity authentication process are improved. Meanwhile, according to the specific behavior habits of a user accessed to the cloud service, the features of historical behavior data of the user are analyzed and extracted based on the data mining technology. In this way, a knowledge database of the normal behavior patterns of the user is formed. When the user behaves abnormally or suspiciously, the identity of the user is authenticated again. Only when the user passes the identity authentication process, the corresponding service is authorized for the user. Therefore, the illegal operation of others is avoided, and the information security of the user is fully ensured.
Description
technical field The invention belongs to the field of cloud computing security, in particular to an authentication and authorization method based on OTP and user characteristics in a mobile cloud computing environment. Background technique Since Google proposed the concept of mobile cloud computing in 2006, various services and platforms related to cloud computing have appeared in people's field of vision, and cloud services have become more and more popular due to their convenience, scalability, and savings. , users can store and calculate information in the cloud, which reduces many constraints caused by limited storage and computing resources. With the widespread use of various smart terminals such as smartphones and tablet computers in people's daily life, various mobile cloud computing services based on smart terminals have also emerged correspondingly, enabling users to use various cloud services through wireless networks. However, the following cloud security issue...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More IPC IPC(8): H04L9/32H04L29/06H04L29/08
Inventor 傅涛傅德胜经正俊孙文静
Owner JIANGSU BOZHI SOFTWARE TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com