Credible virtual machine platform
A technology of virtual machine and privileged virtual machine, applied in the field of virtual machine platform, can solve problems such as lack of communication between virtual domains and insufficient security mechanism of virtual machine platform, so as to improve stability and anti-attack, prevent malicious code transmission, prevent The effect of information leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
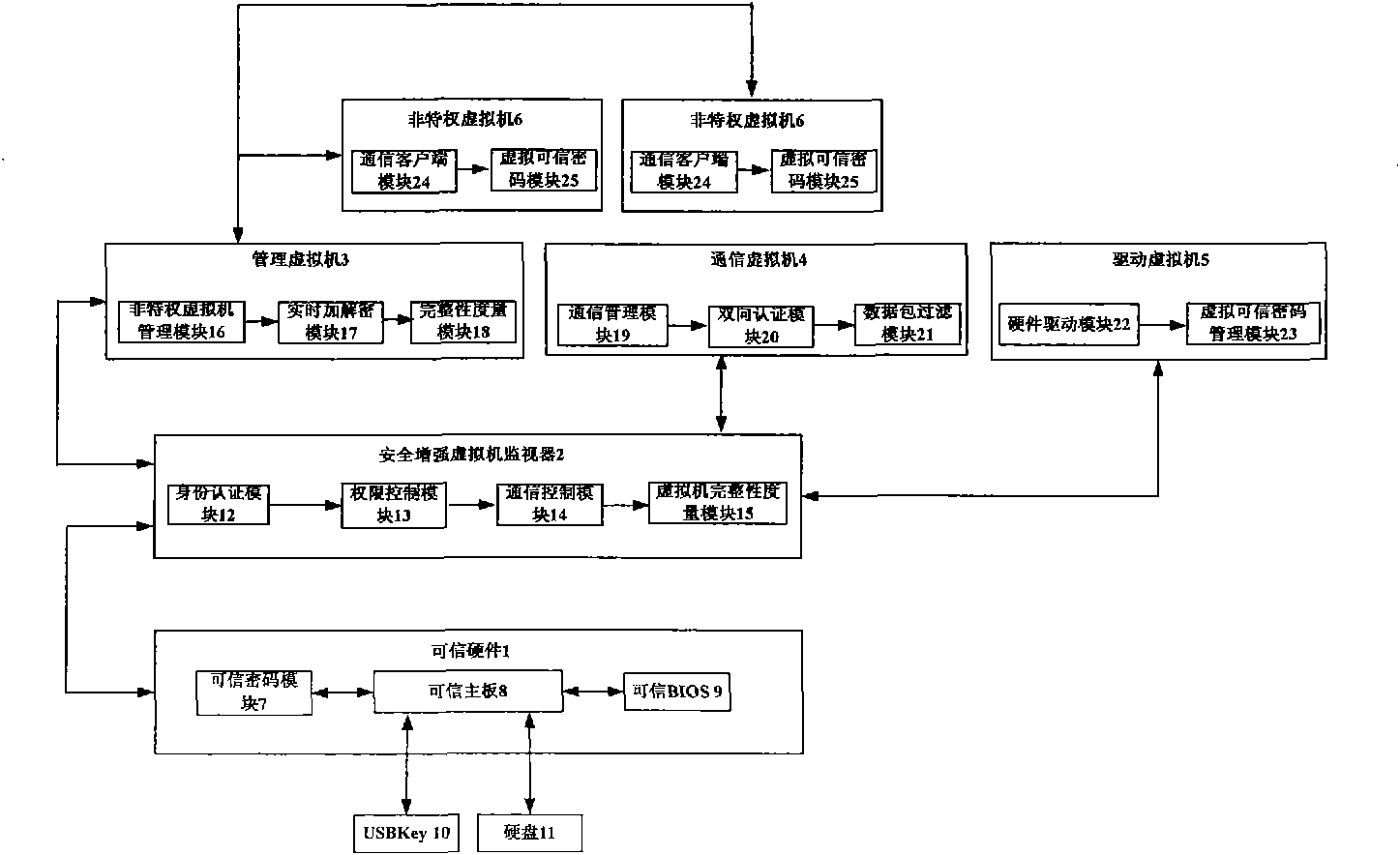
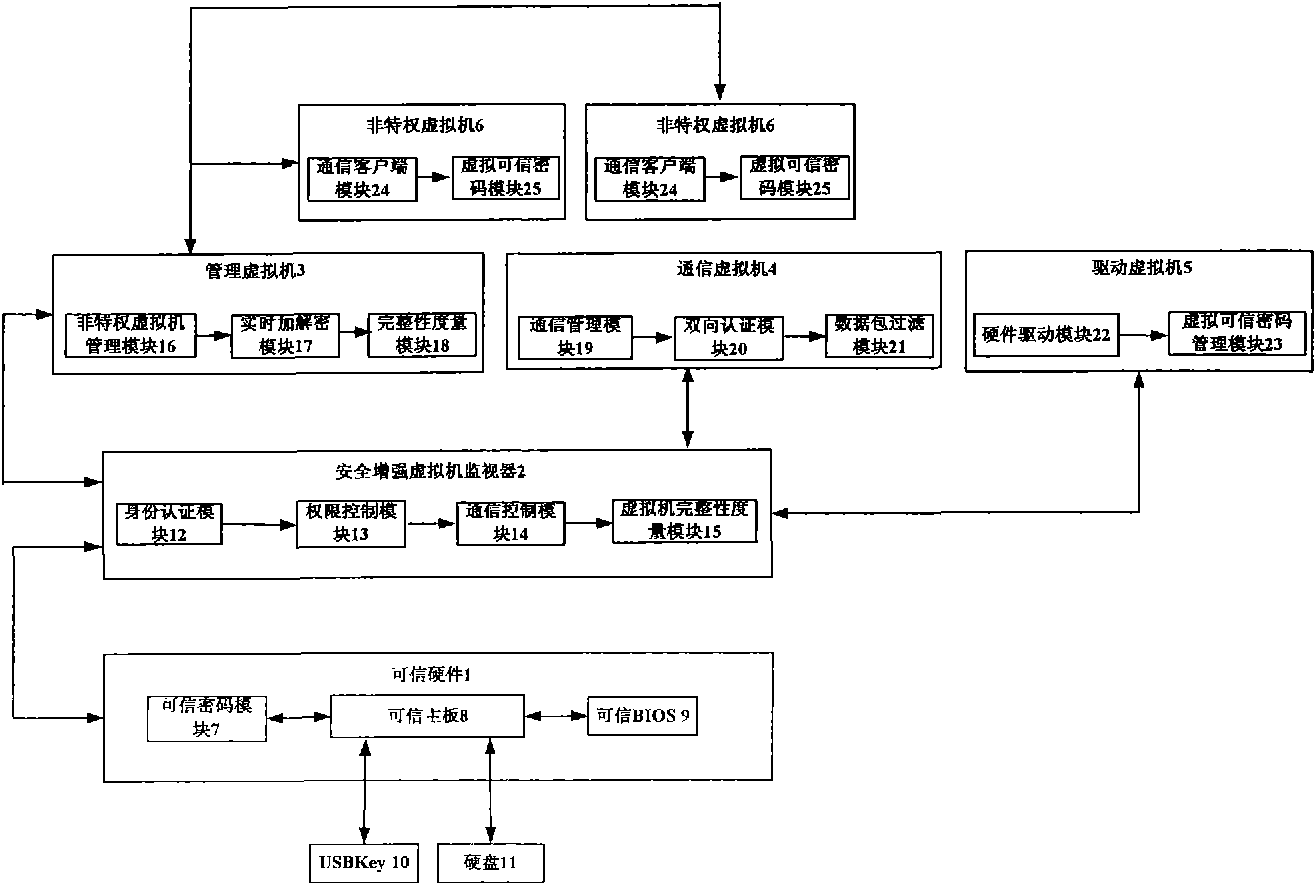
[0013] A trusted virtual machine platform, including: hard disk 11, USBKey10 and non-privileged virtual machine 6, also includes: trusted hardware 1, security enhanced virtual machine monitor 2, management virtual machine 3, communication virtual machine 4 and driver virtual machine 5; Wherein, trusted hardware 1 includes: trusted motherboard 8, trusted password module 7 and trusted BIOS 9; security enhanced virtual machine monitor 2 includes: identity authentication module 12, authority control module 13, communication control module 14 and Virtual domain integrity measurement module 15; management virtual machine 3 includes: non-privileged virtual machine management module 16, real-time encryption and decryption module 17 and integrity measurement module 18; drive virtual machine 5 includes: hardware driver module 22 and virtual trusted password management Module 23; the communication virtual machine 4 includes: a communication management module 19, a two-way authentication m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com