Patents
Literature
312results about "Signature reading/verifying" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
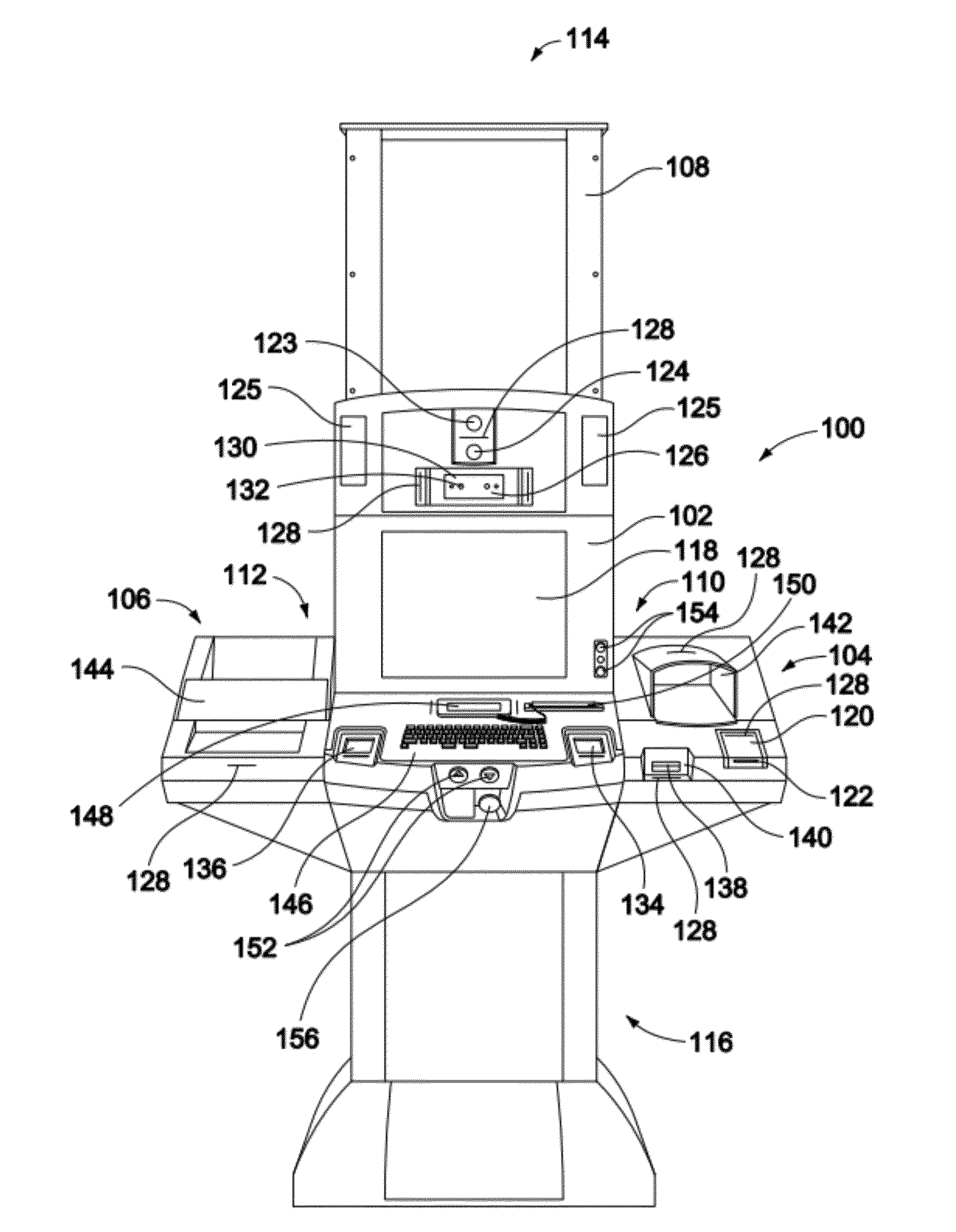
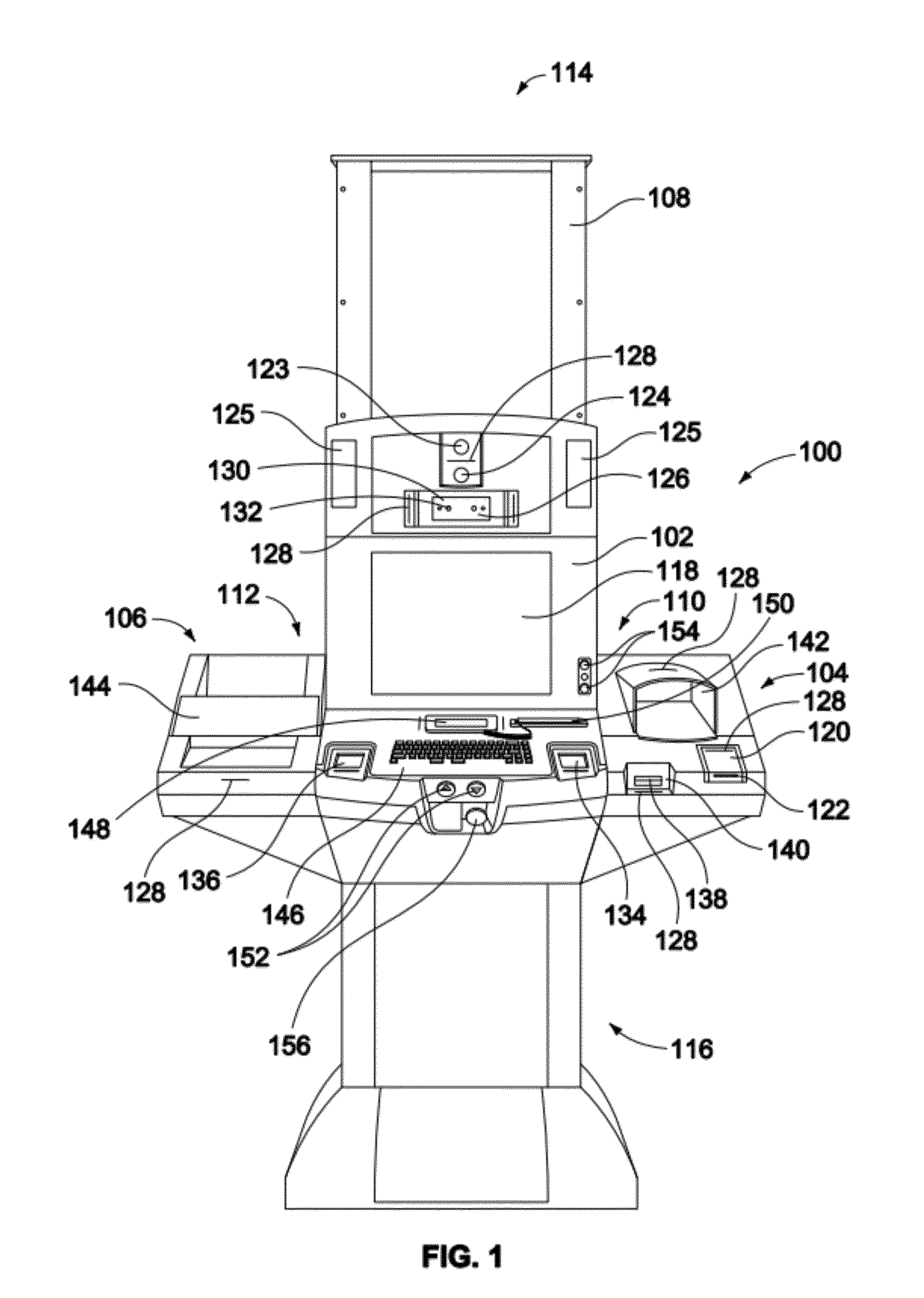
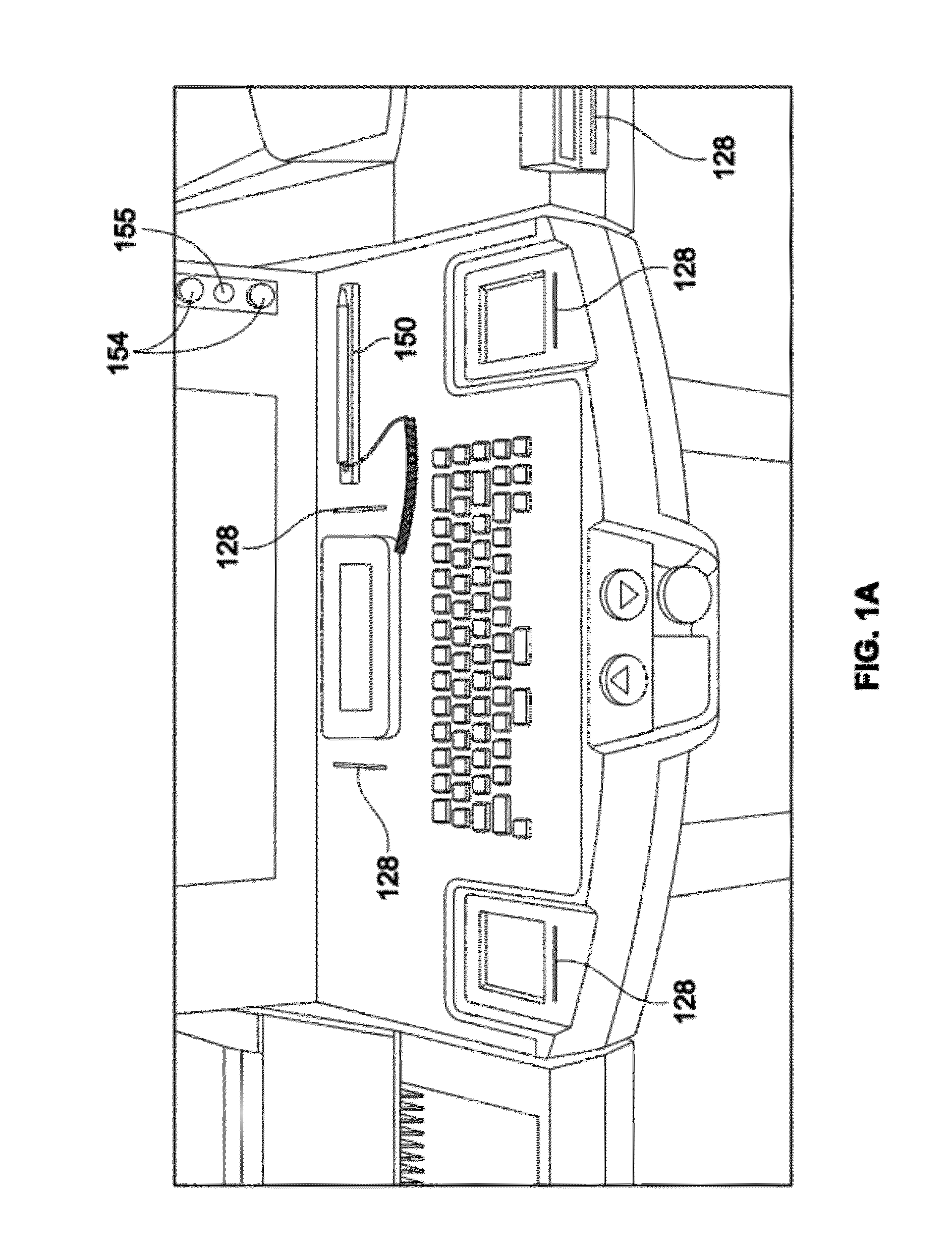
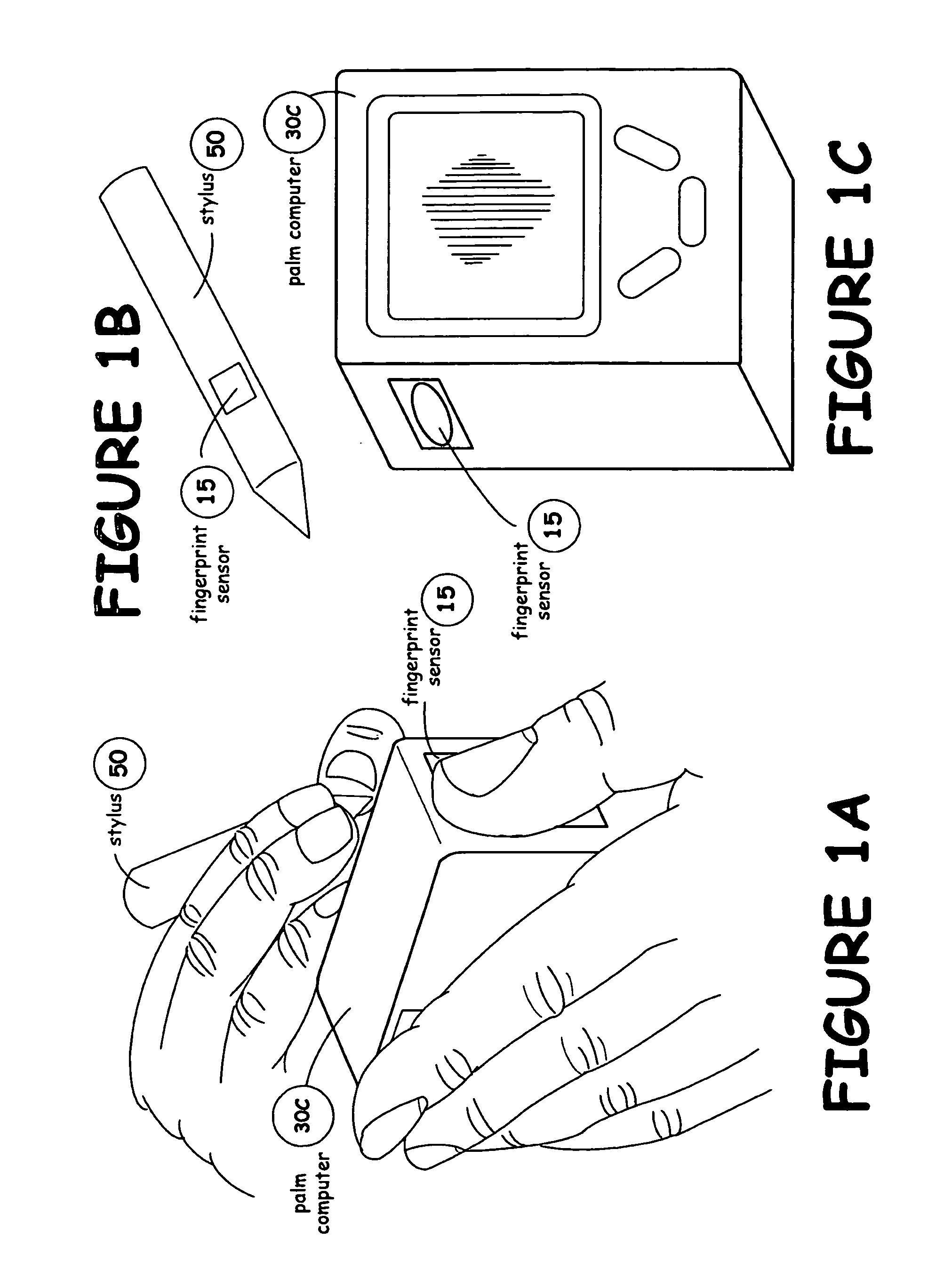
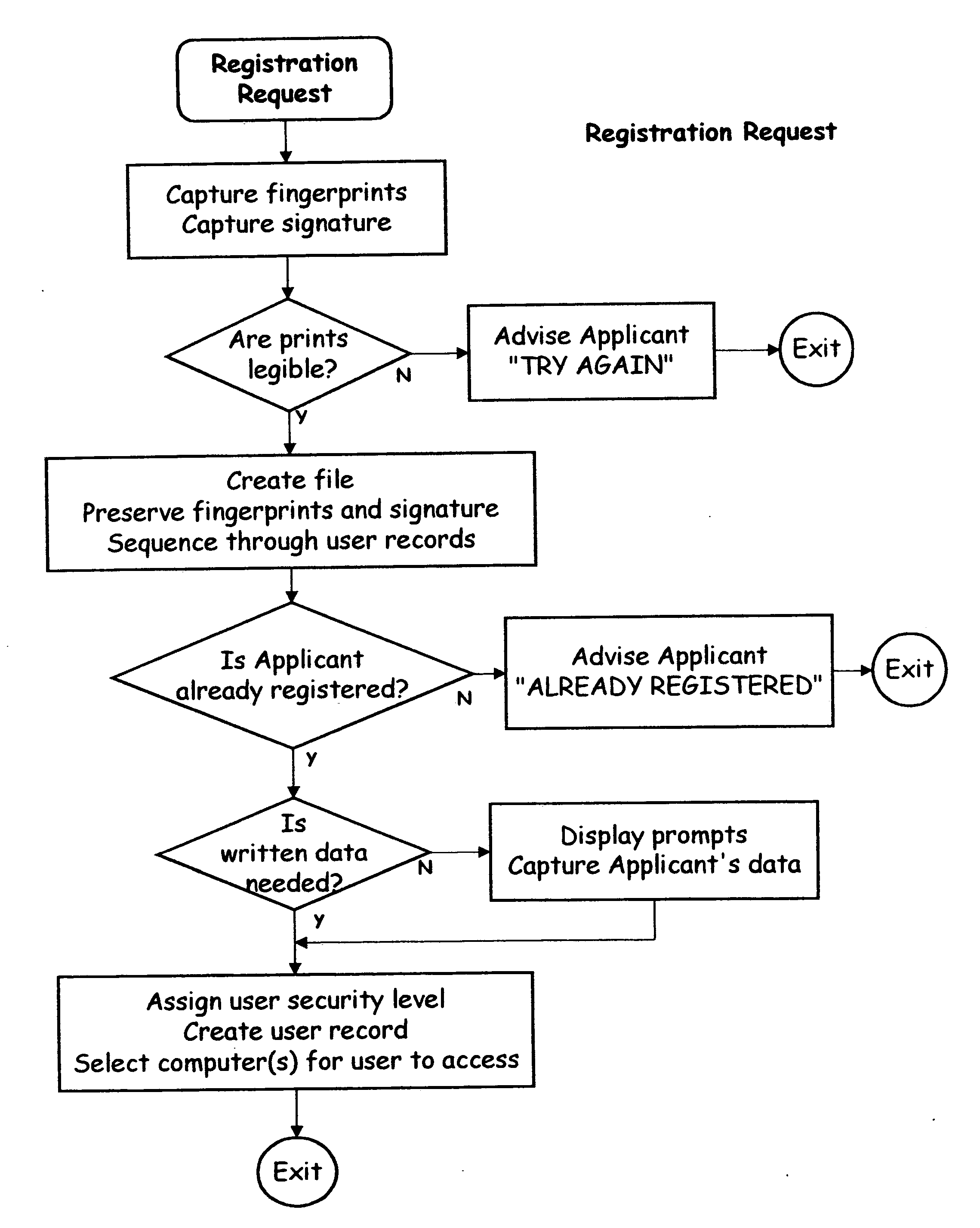
Multi-biometric enrollment kiosk including biometric enrollment and verification, face recognition and fingerprint matching systems
ActiveUS20120293642A1Easy to transportEasy to installDigital data processing detailsAnalogue secracy/subscription systemsComputer scienceEmbedded system
A biometric and identity enrollment kiosk for collecting personal data includes a slidable main module and at least one modifiable section removably coupled to the main module. The main module includes a processor and one or more biometric sensing devices coupled to the processor. The one or more biometric sensing devices include a right fingerprint sensor coupled to the processor and a left fingerprint sensor coupled to the processor. The right fingerprint sensor is positioned proximate a right end of the main module and the left fingerprint sensor is positioned proximate a left end of the main module. The right fingerprint sensor is positioned a predetermined distance apart from the left fingerprint sensor. The at least one modifiable section includes at least one first input device coupled to the processor.
Owner:NEXTGENID
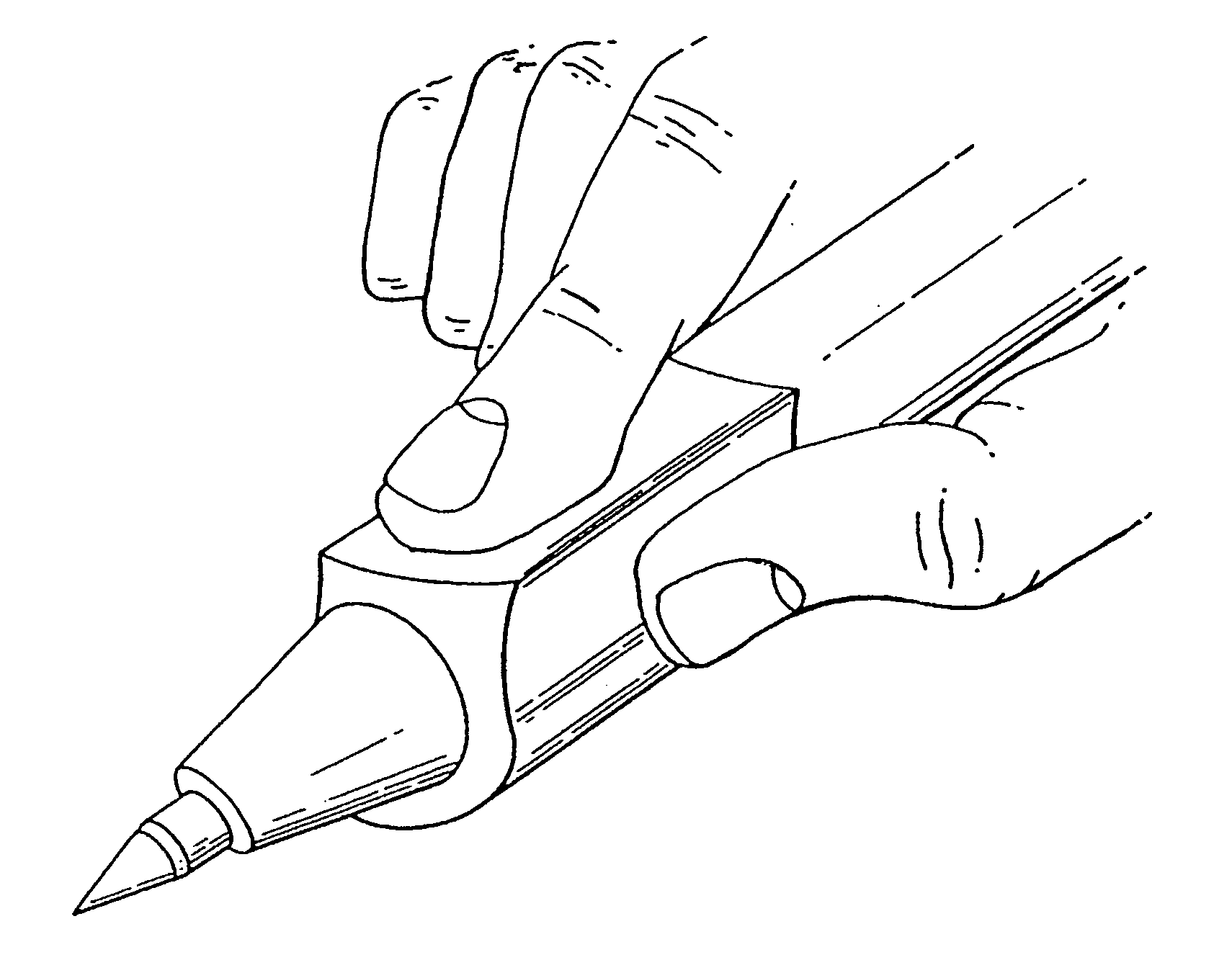
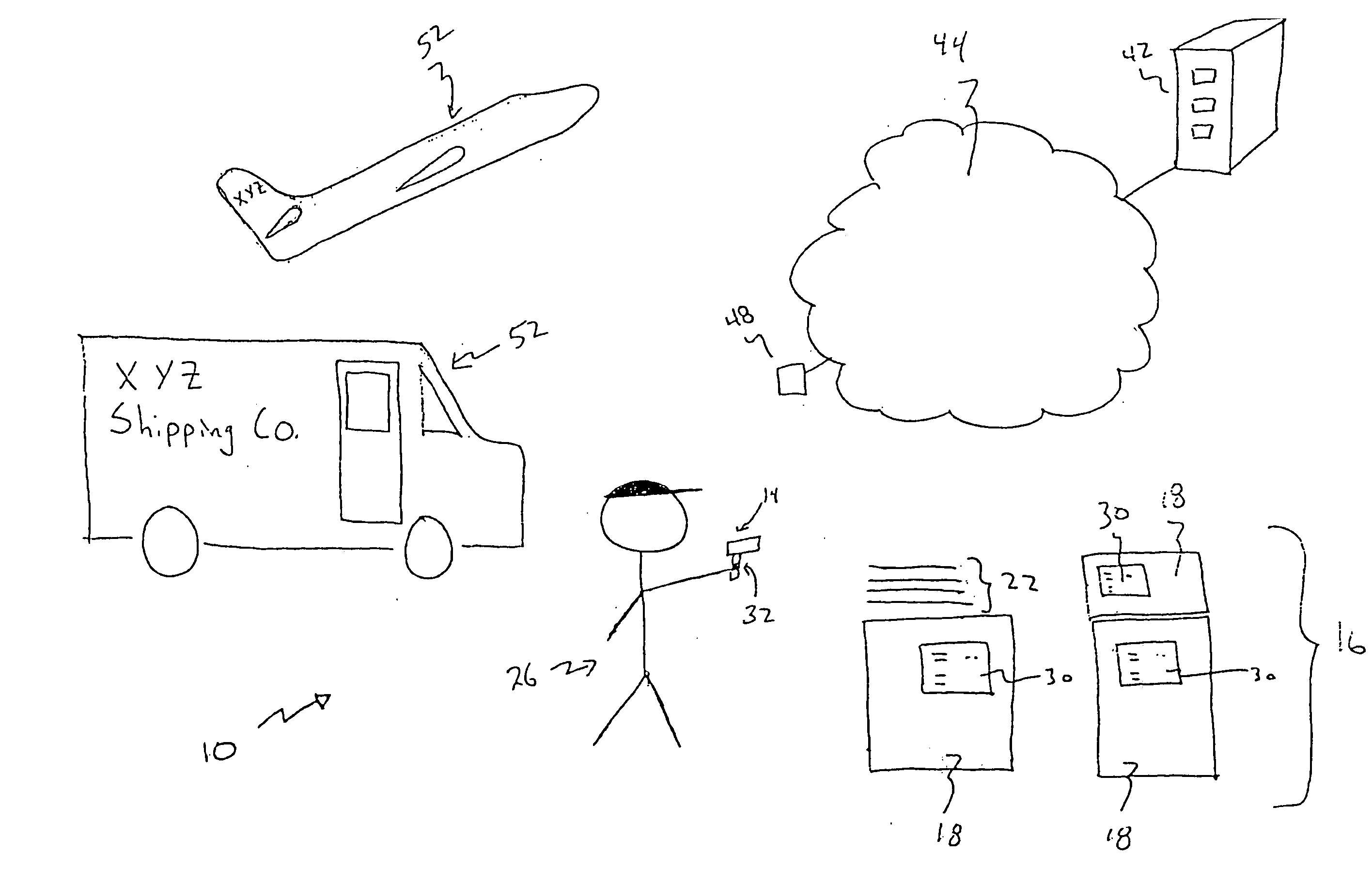
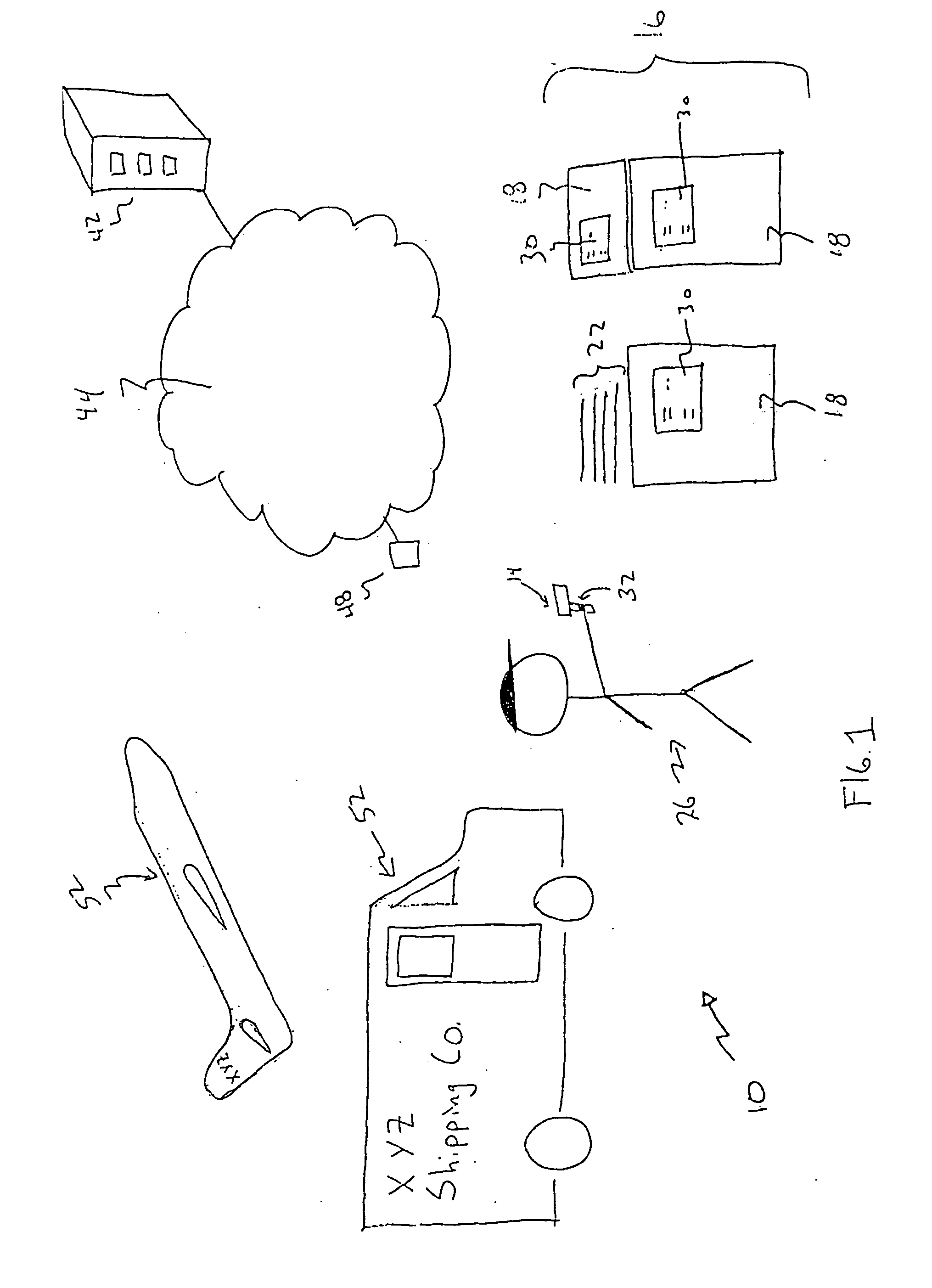
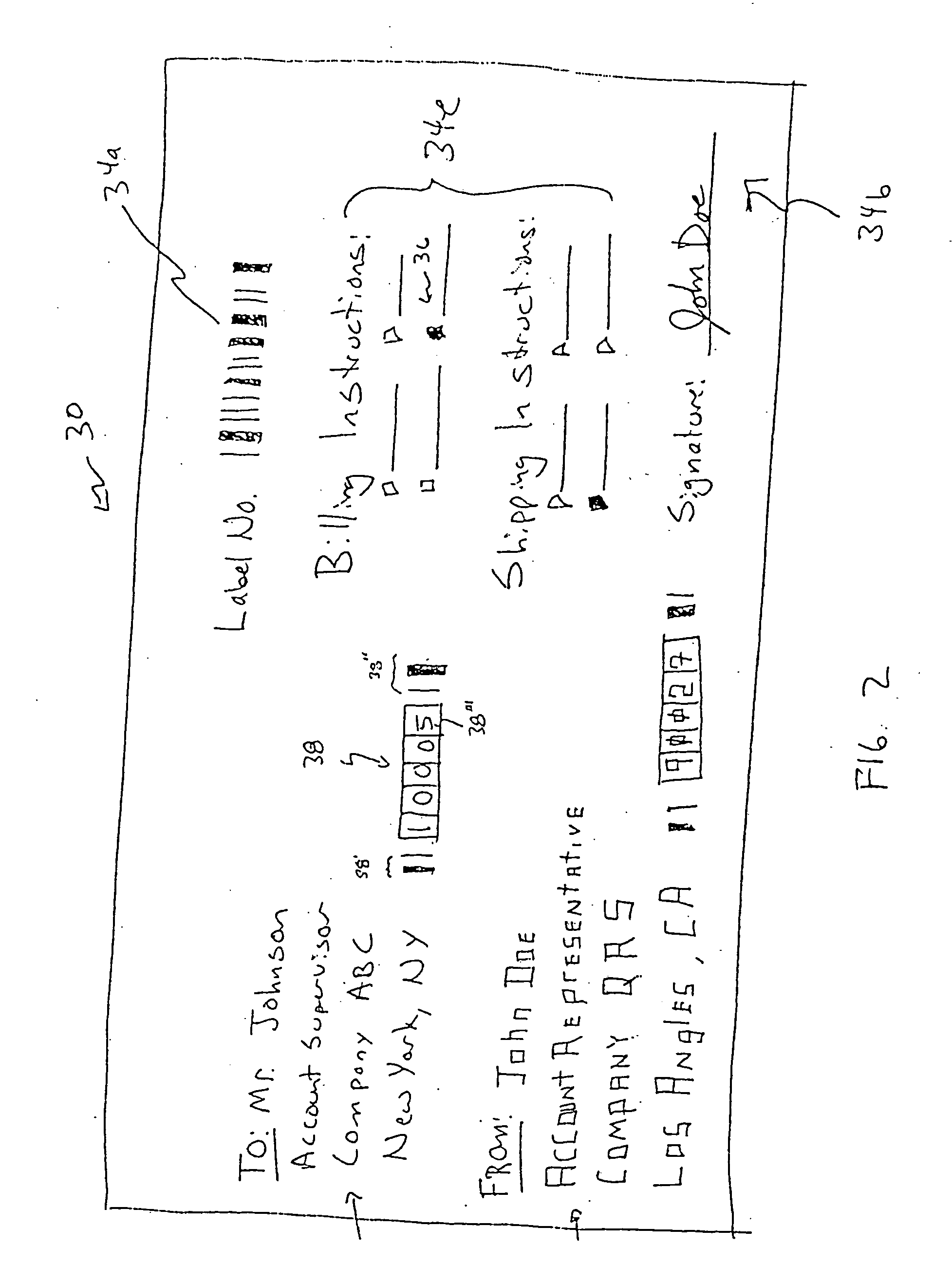
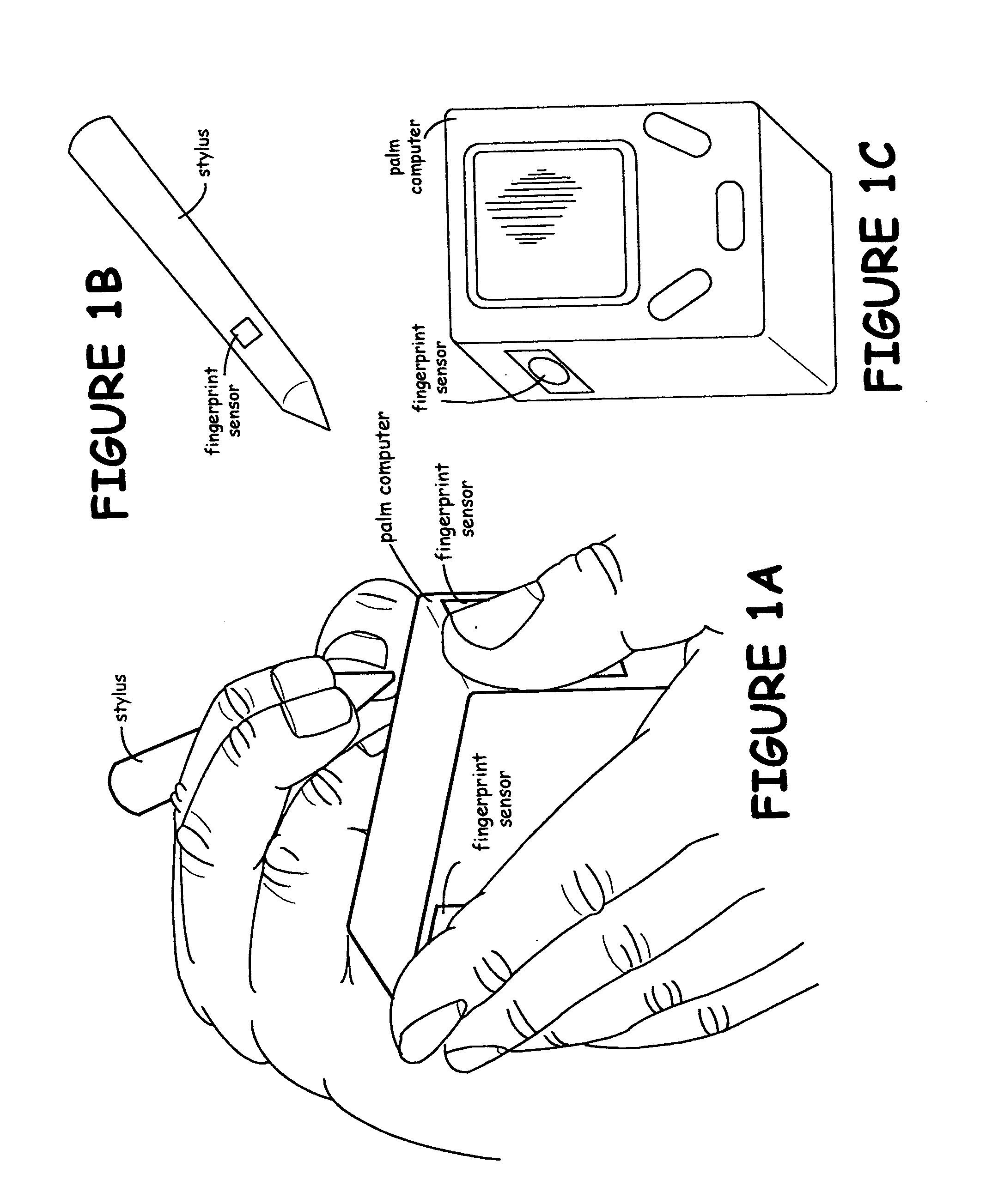
Method for identity verification
InactiveUS20050180618A1Processing speedMinimize privacy concernDigital data processing detailsChecking apparatusInternet privacyIndex finger
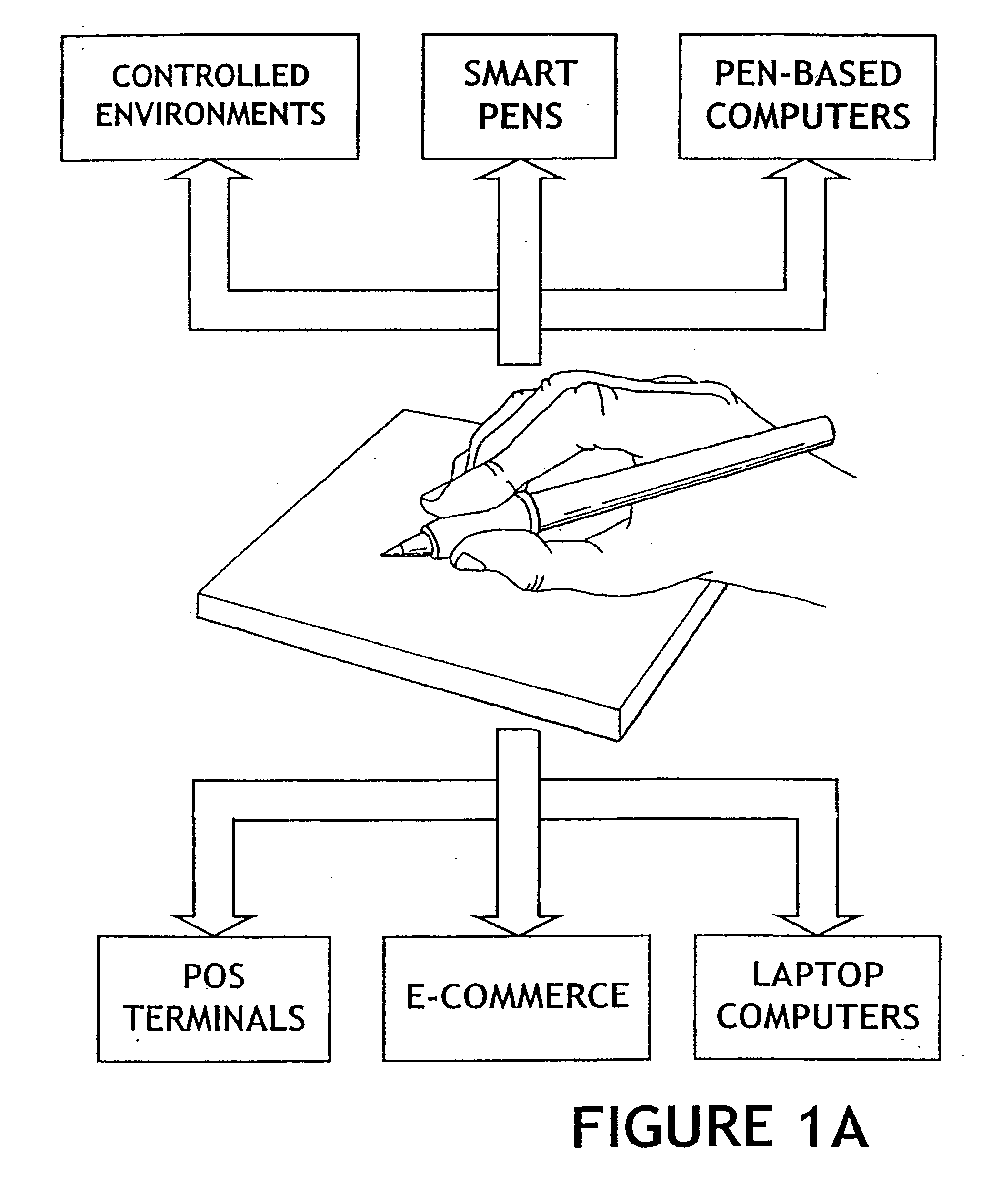
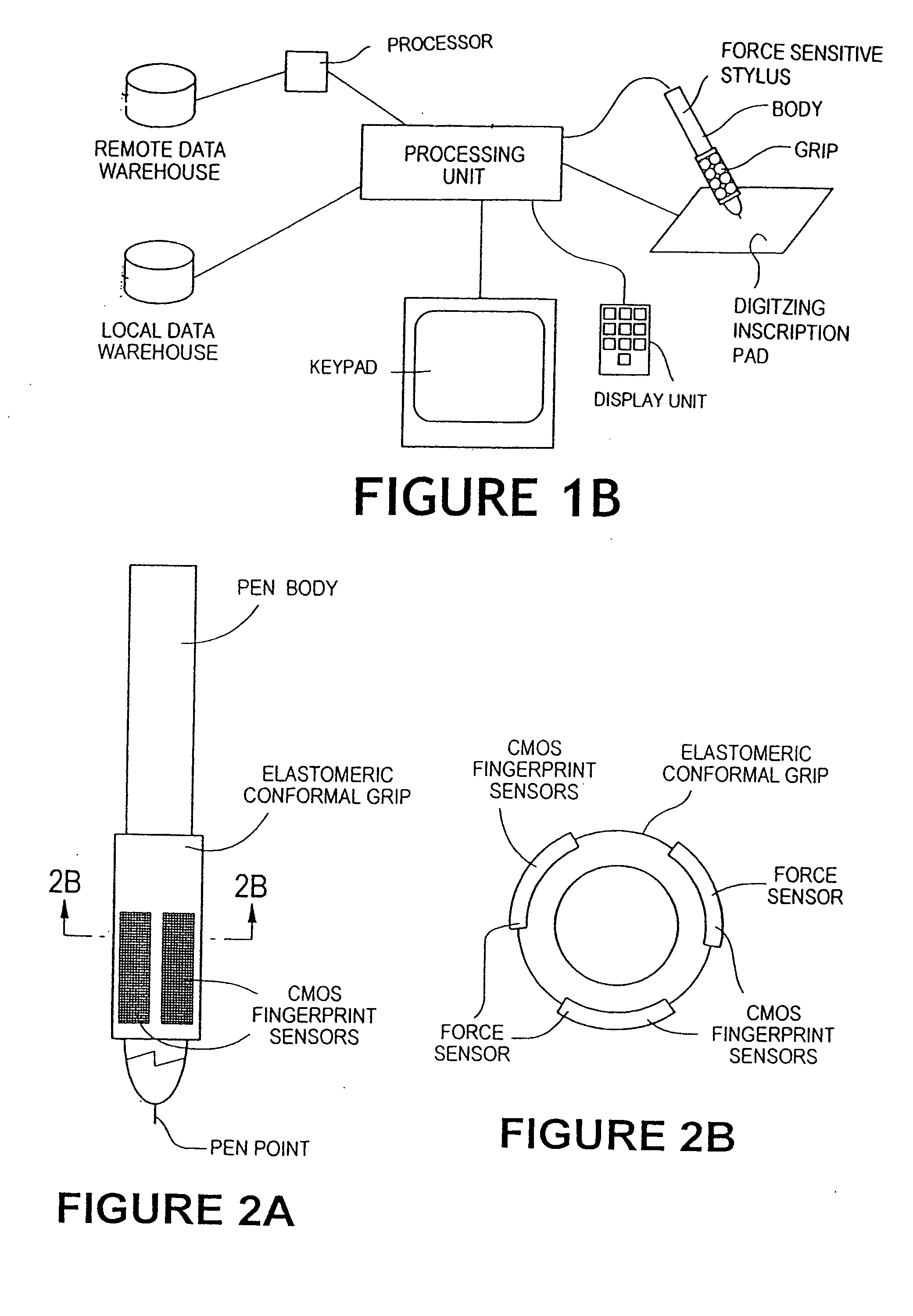
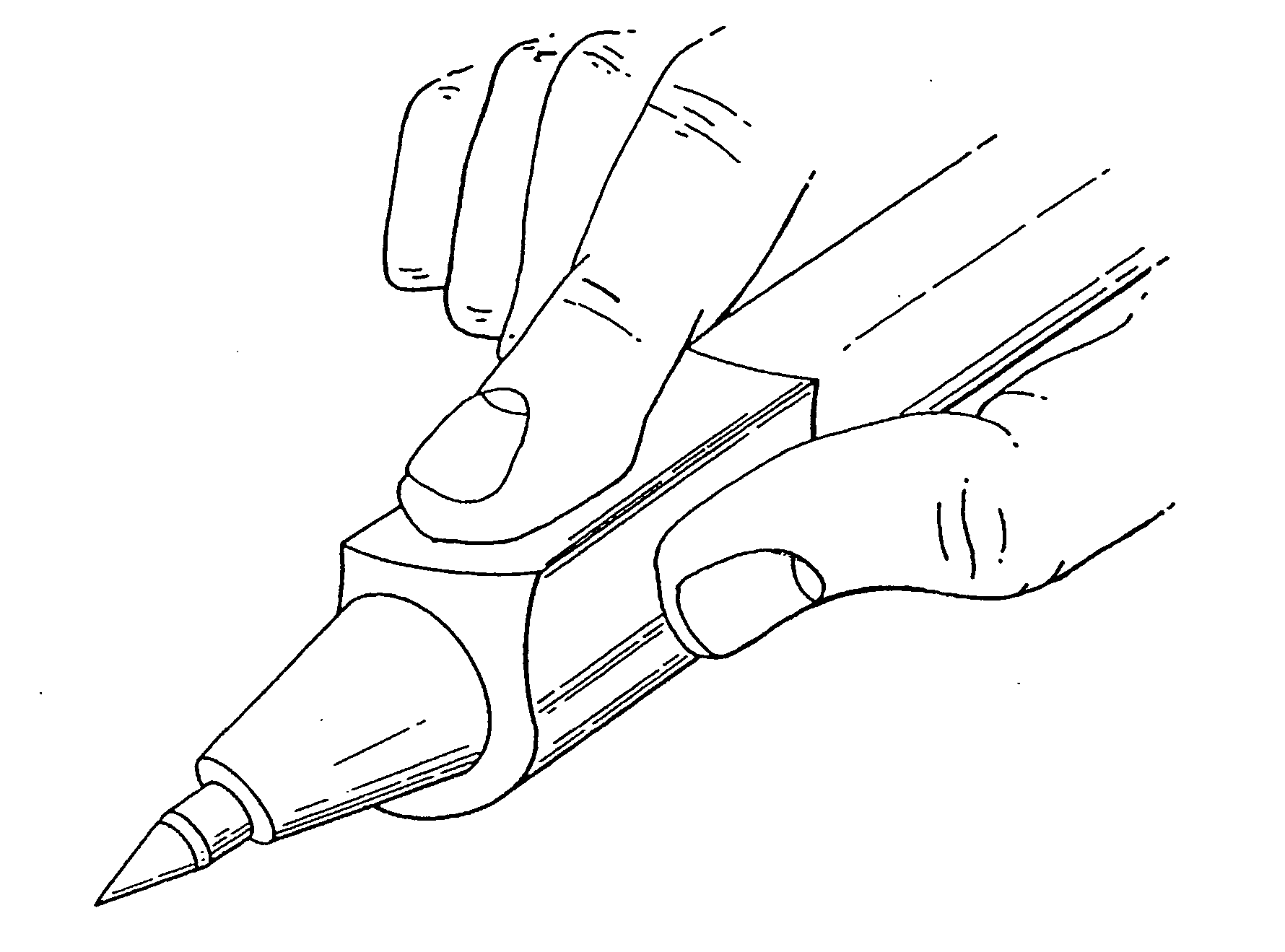
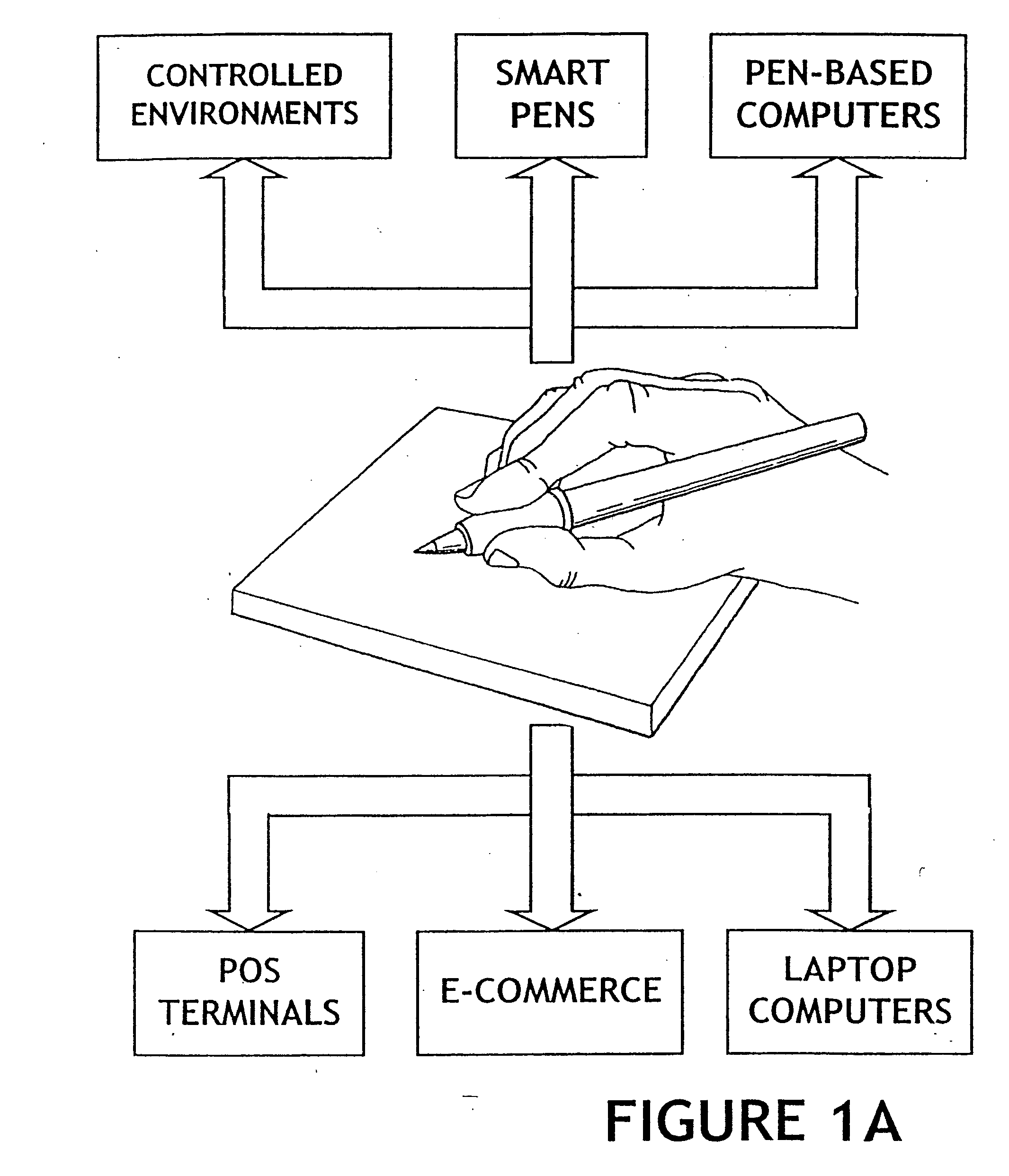
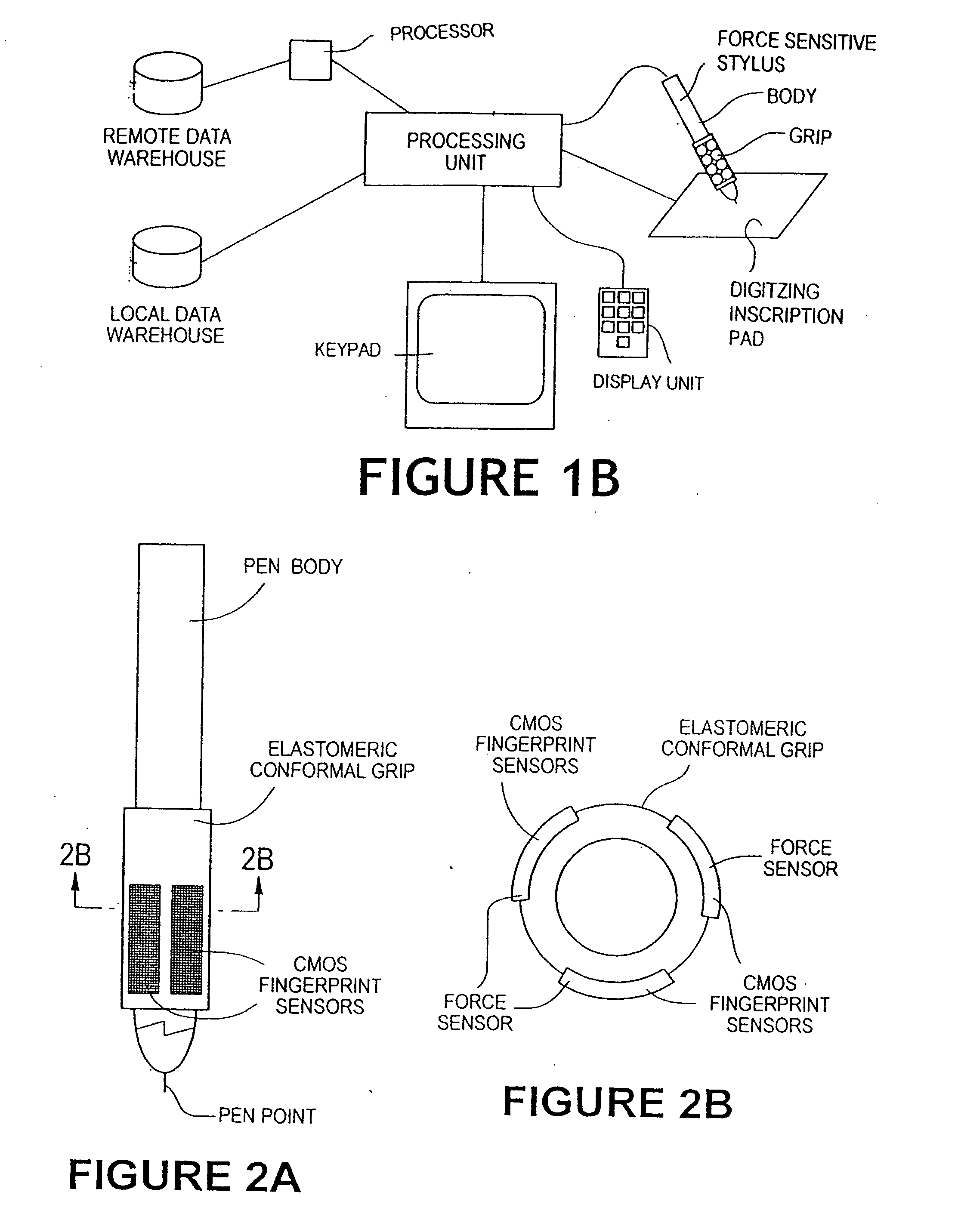
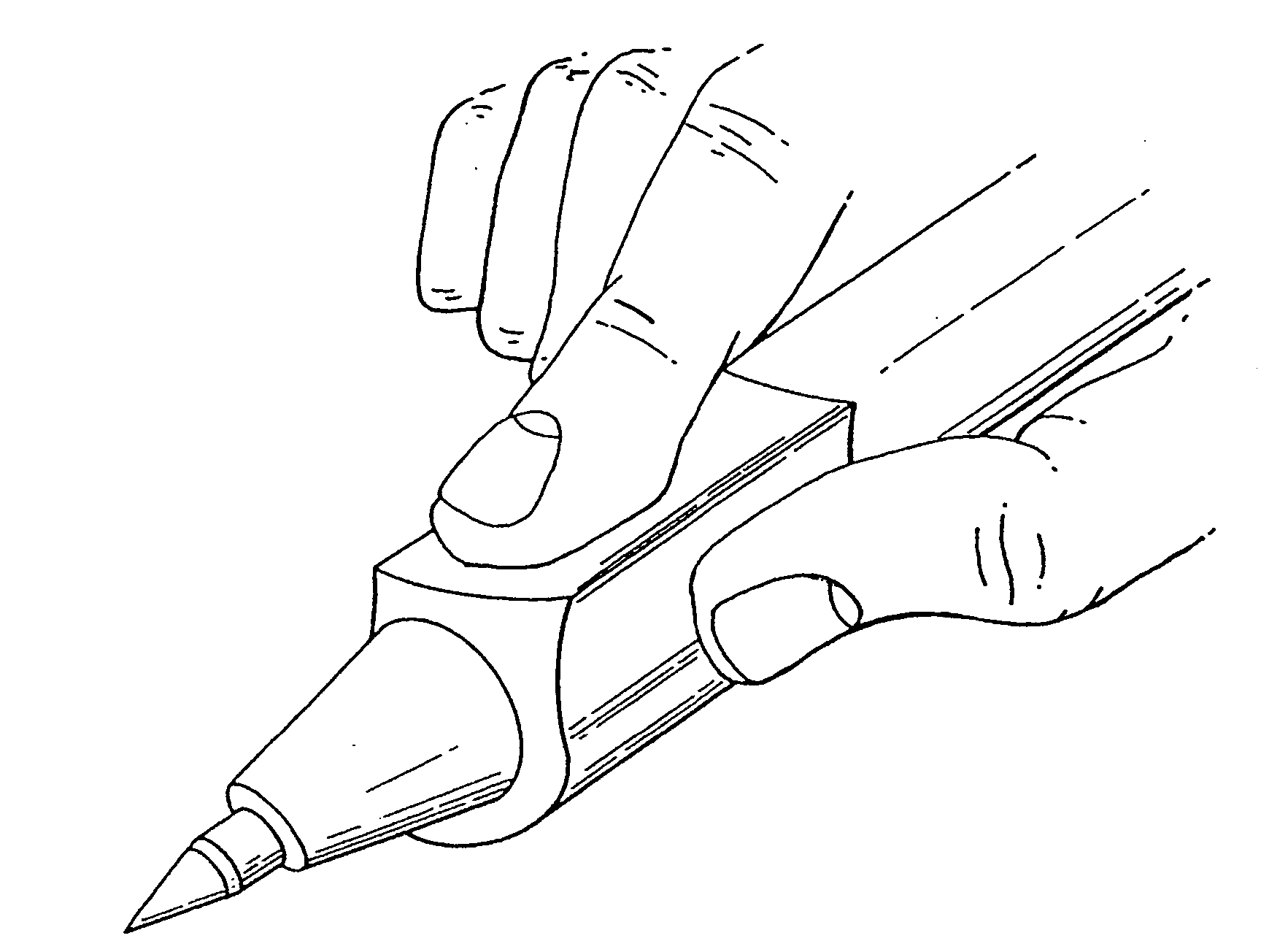
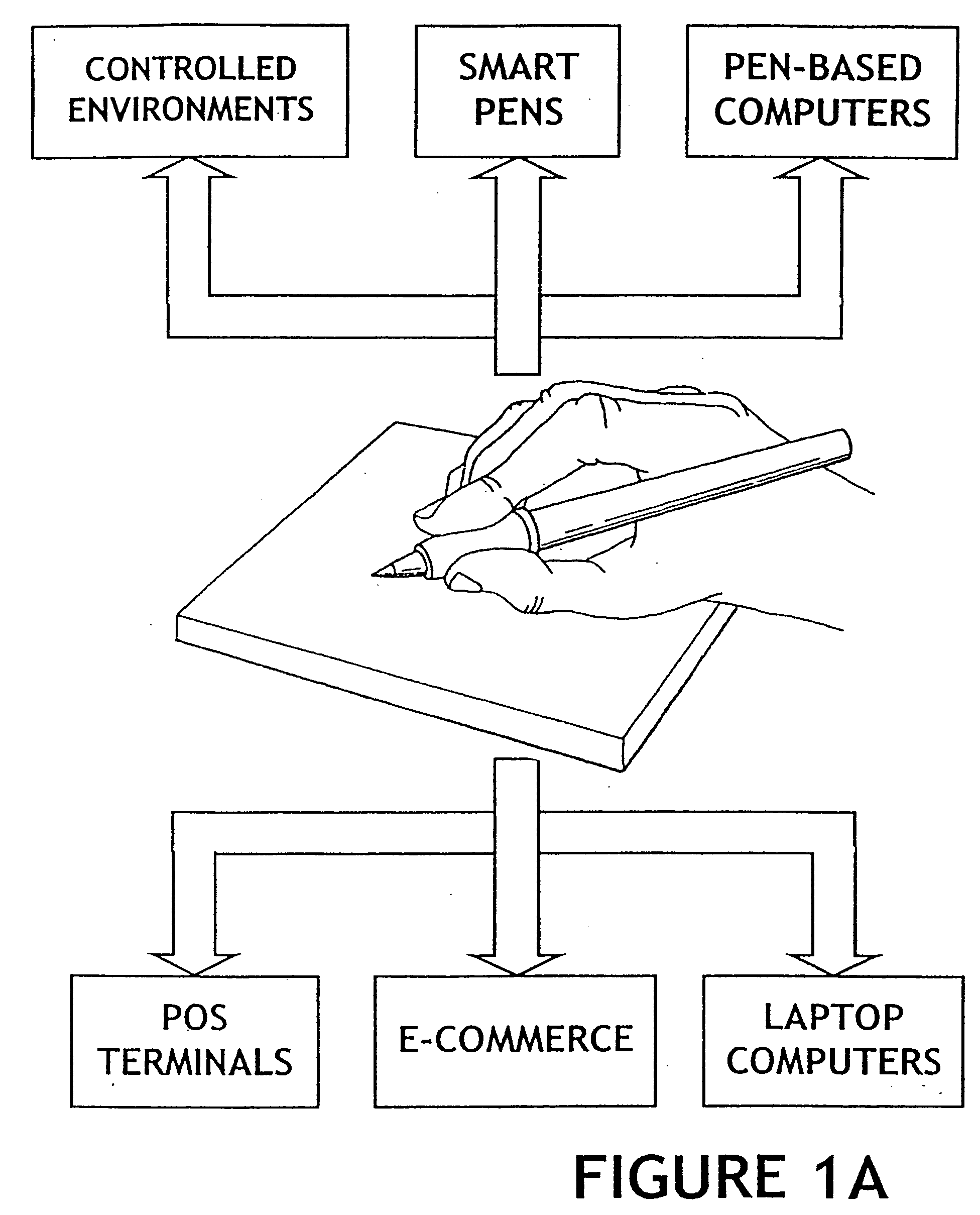
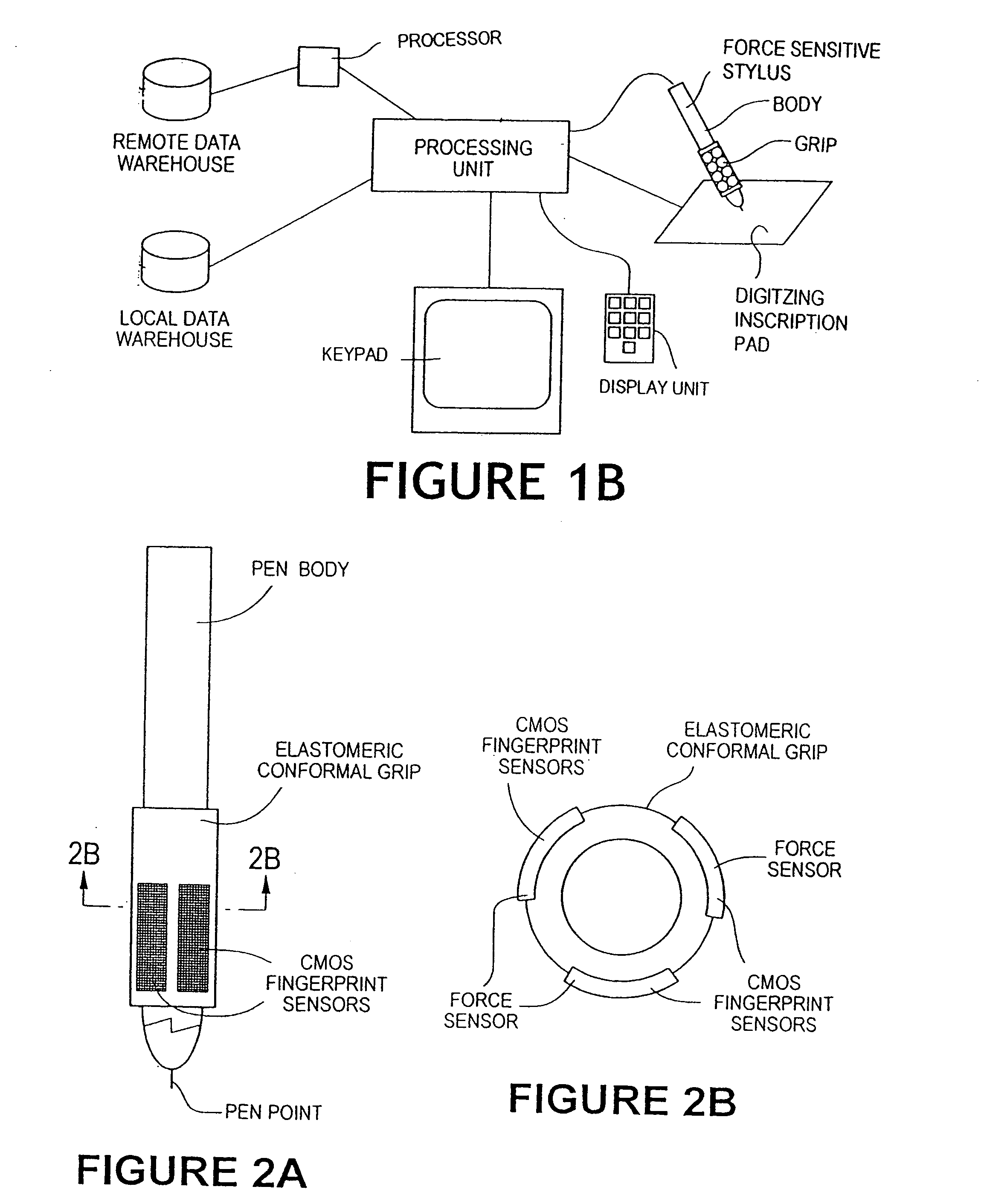
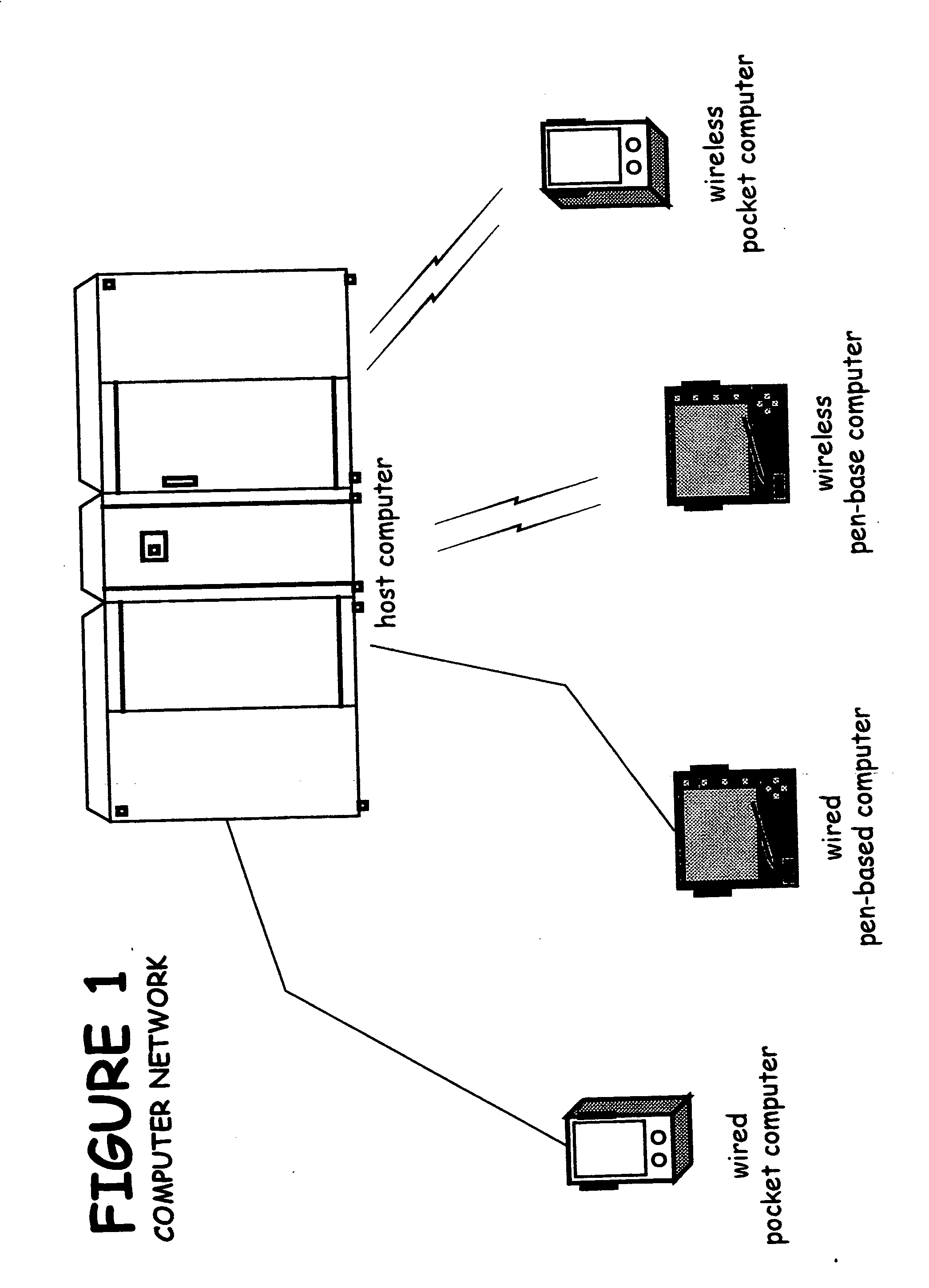
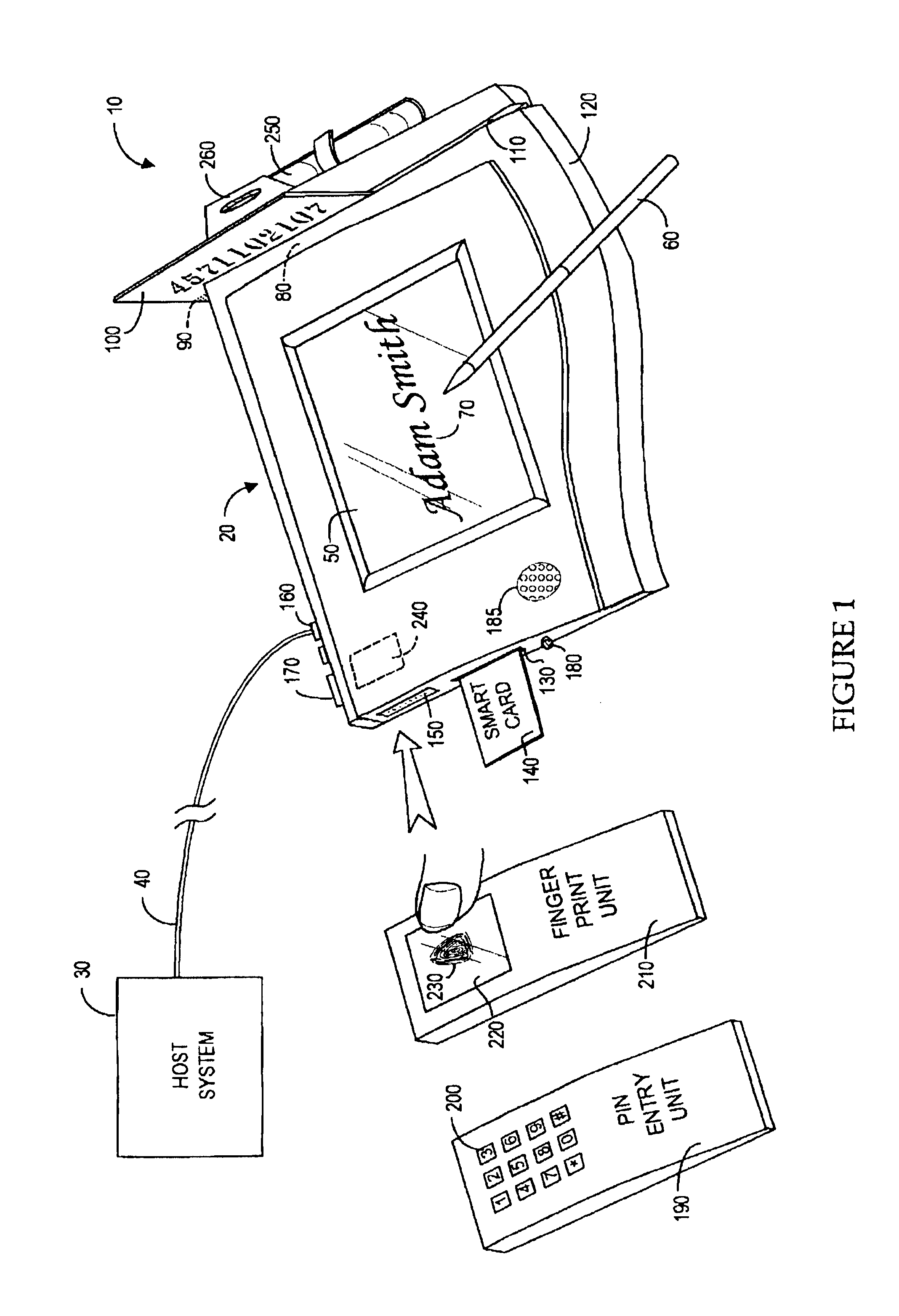
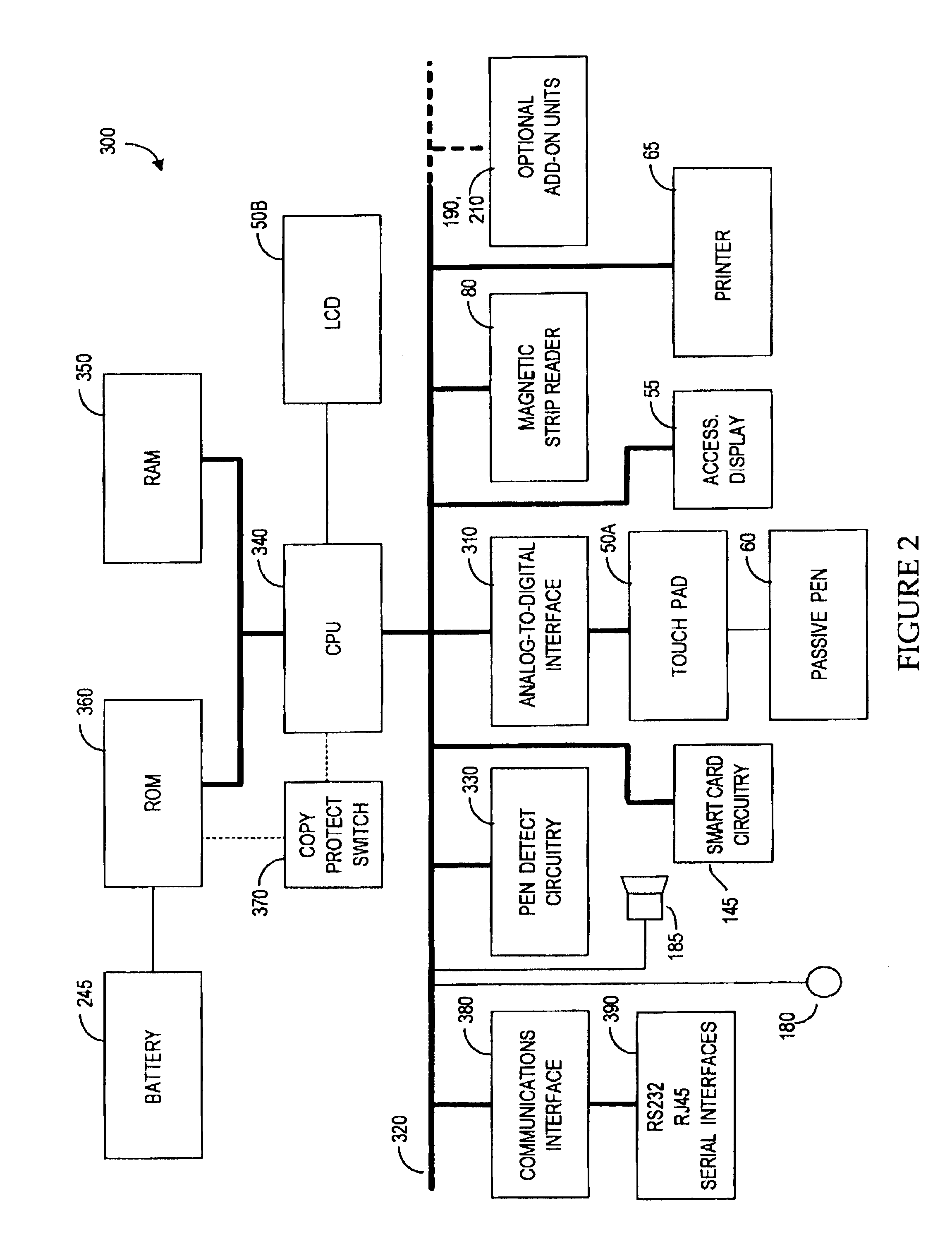
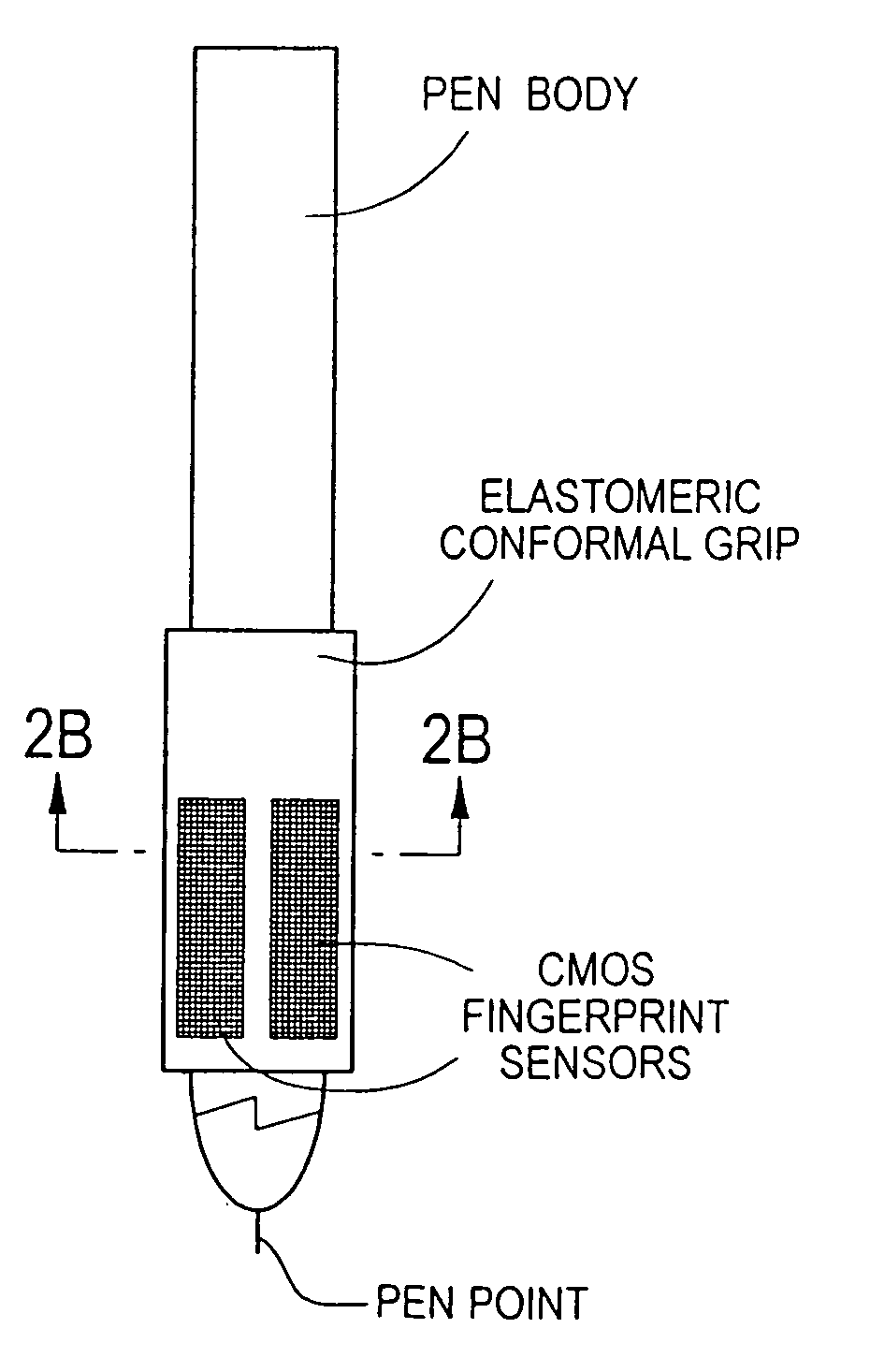
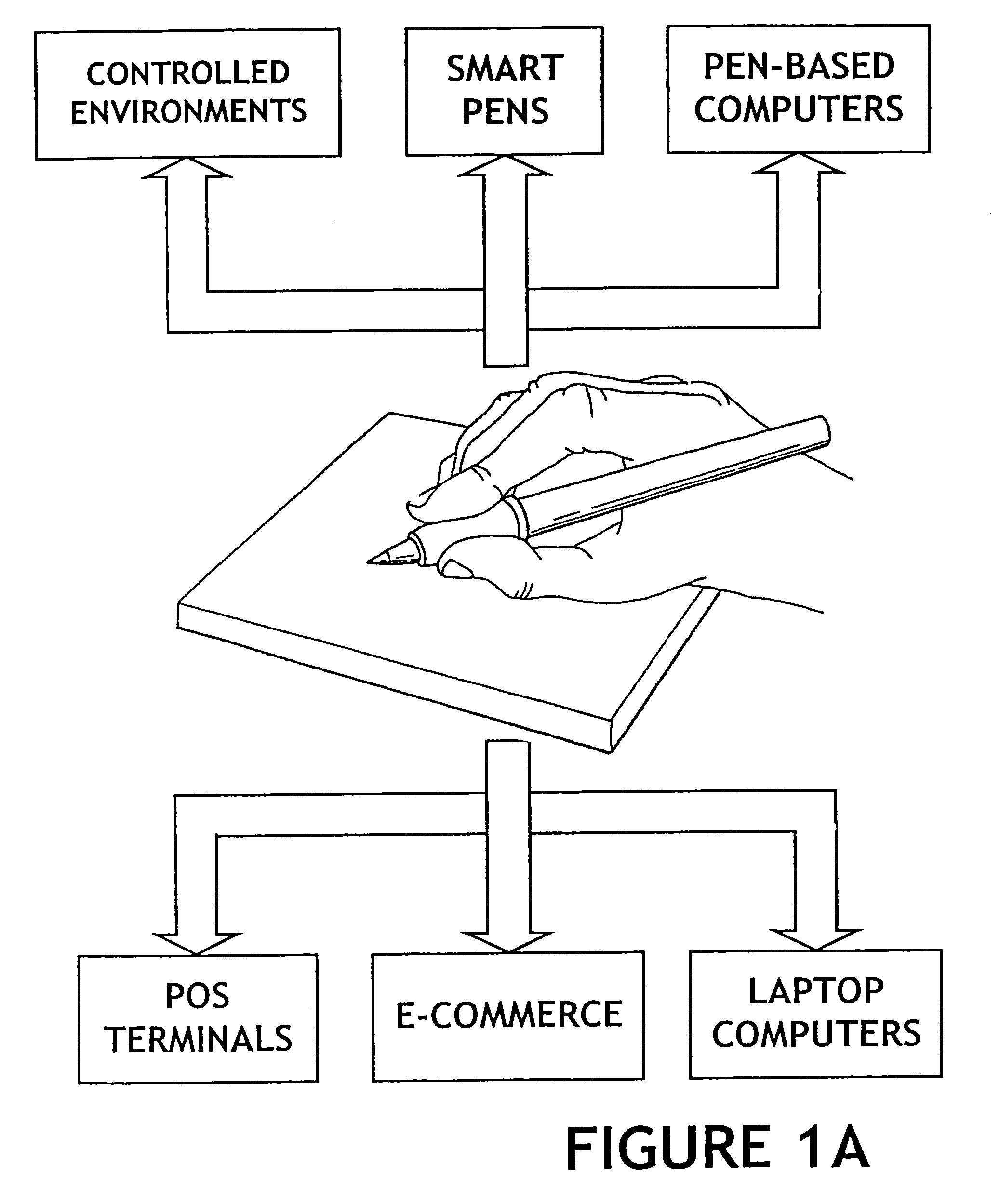
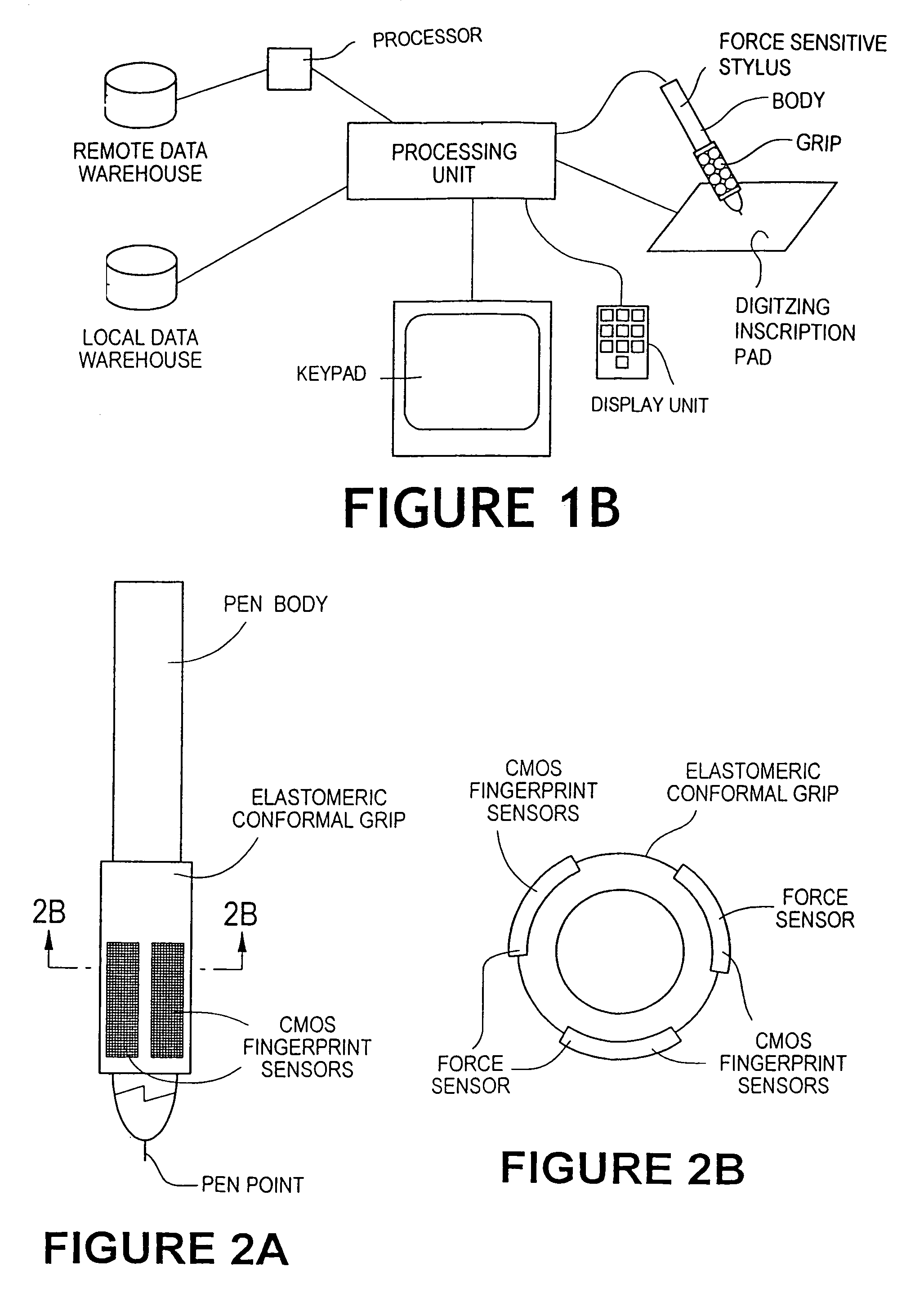
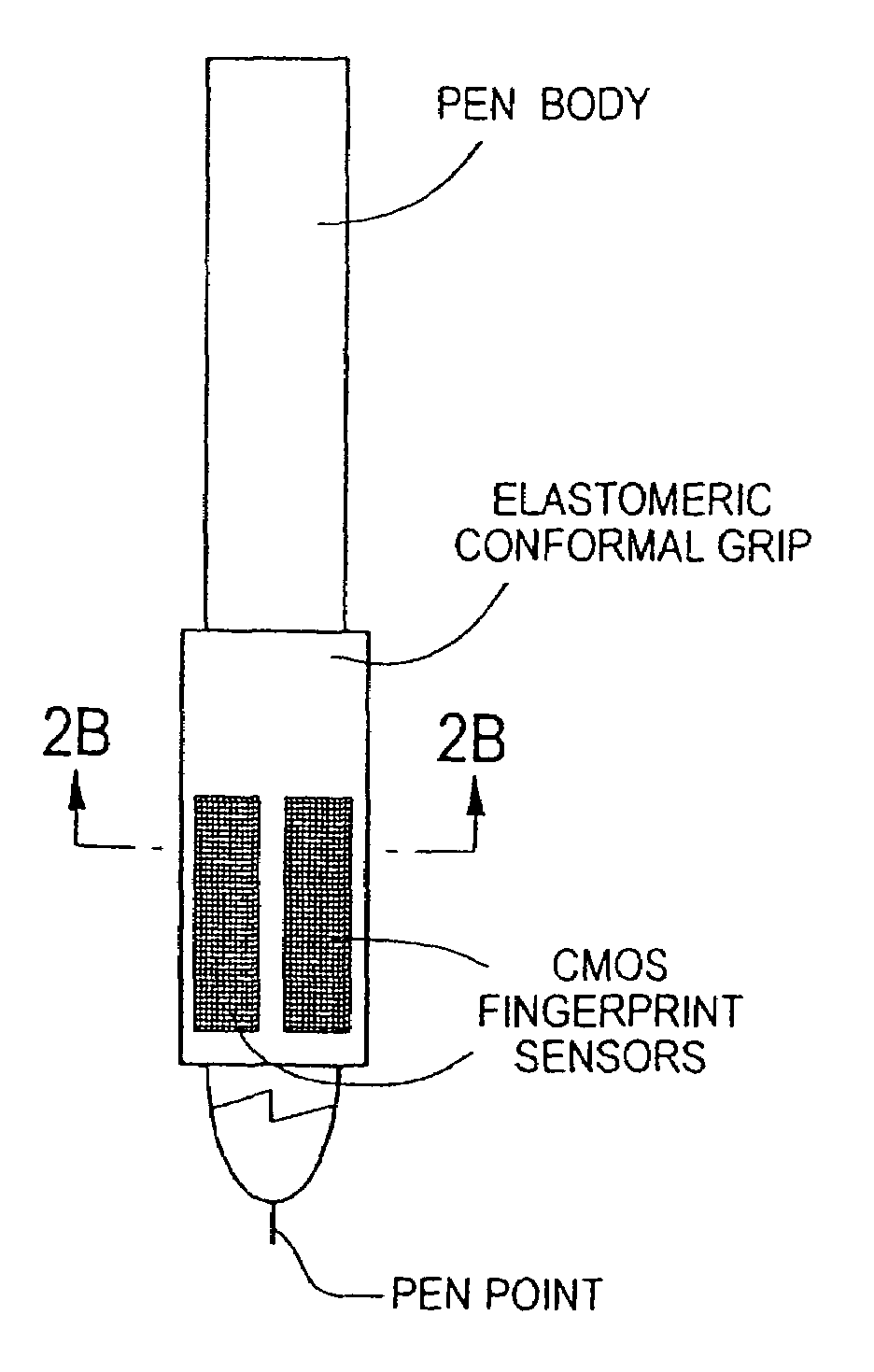
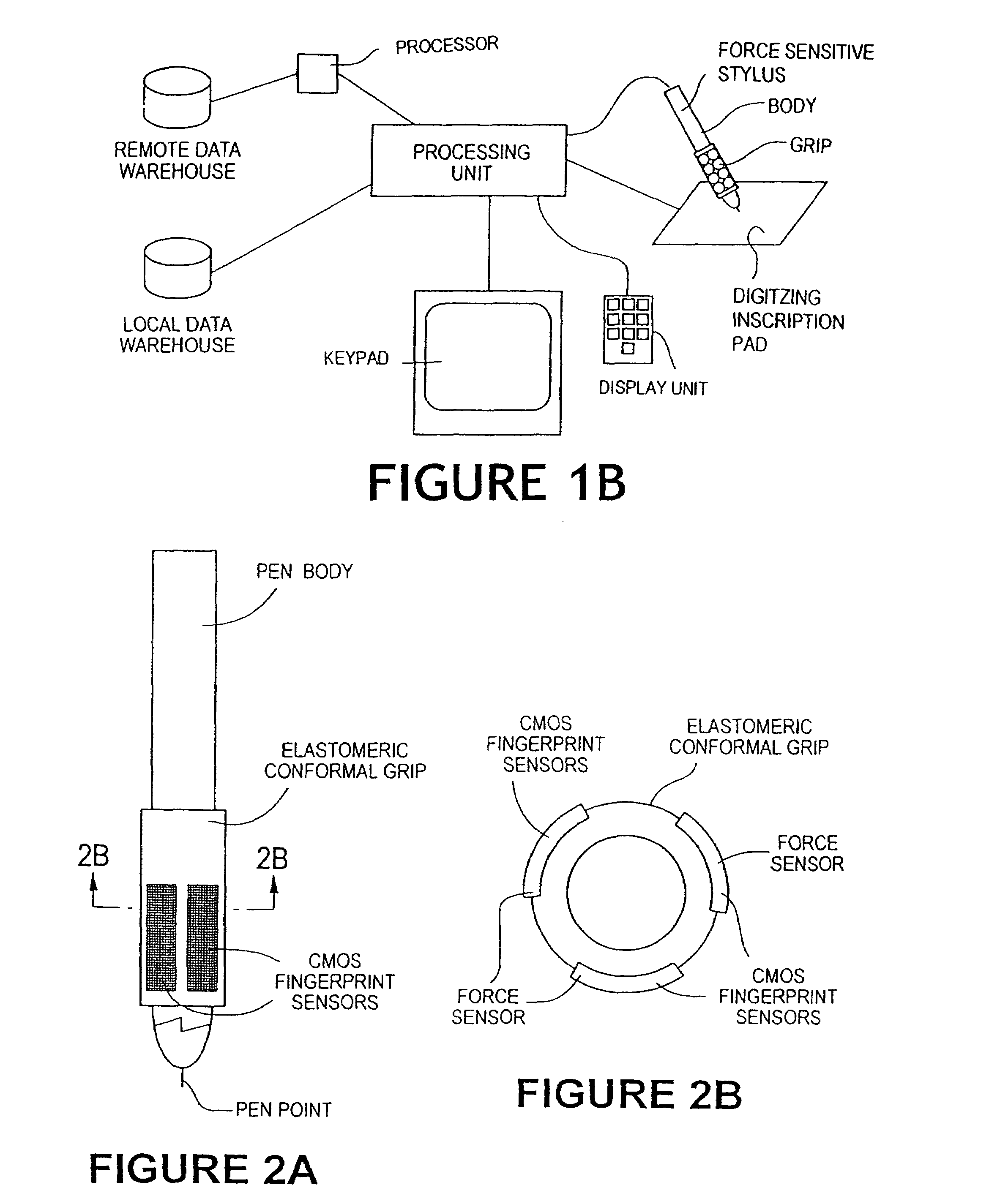
The method for identity verification employs biometric technology. Positioned at the center of the system is a stylus with any of a number of biometric properties or their combination or with one or more metric sensors, while the customer uses the stylus to sign his / her name, or even for writing anything. The identity verification system is used at point-of-sale terminals, in various closed environments, to access a computer network, in applications involving pen-based computers and smart-pens, and for e-commerce. When fingerprint sensors are used, the sensors are positioned in the stylus grip, one sensor for the index finger, and a second sensor for the thumb. In one variation, one-to-one biometric matching is used. Each participant carries on his / her person a device that includes an encrypted biometric for reference purposes to gain access Into the system. Processing is simplified since the system need only make a “MATCH” or “NO MATCH” decision. In a second variation that is particularly useful in closed environments, one-to-many biometric matching is used. During each event access request, the community of reference prints is searched for a match with the applicant. Each member of the community need carry nothing on his / her person to participate in the system. In either variation, the stylus is either attached to each site or is portable, one such stylus being carried by each participant.
Owner:UNITED STATES CP LLC
Data security system
InactiveUS7047419B2Easy accessNeed can be addressedDigital data processing detailsInternal/peripheral component protectionComputer usageData access
A data security system comprises a host processor, and a plurality of remote computers. Each remote computer provides biometric authentication of a user prior to responding to the user request for data access. The remote computers are handheld when in operational mode. A sensor in the handheld computer captures a biometric image while the remote computer is being used. The biometric sensor is positioned in such a way that the sensor enables the capture of the biometric image continually during computer usage with each request for access to secure data. The biometric authentication occurs in a seamless manner and is incidental to the data request enabling user identity authentication with each request to access secure data.
Owner:UNITED STATES CP LLC
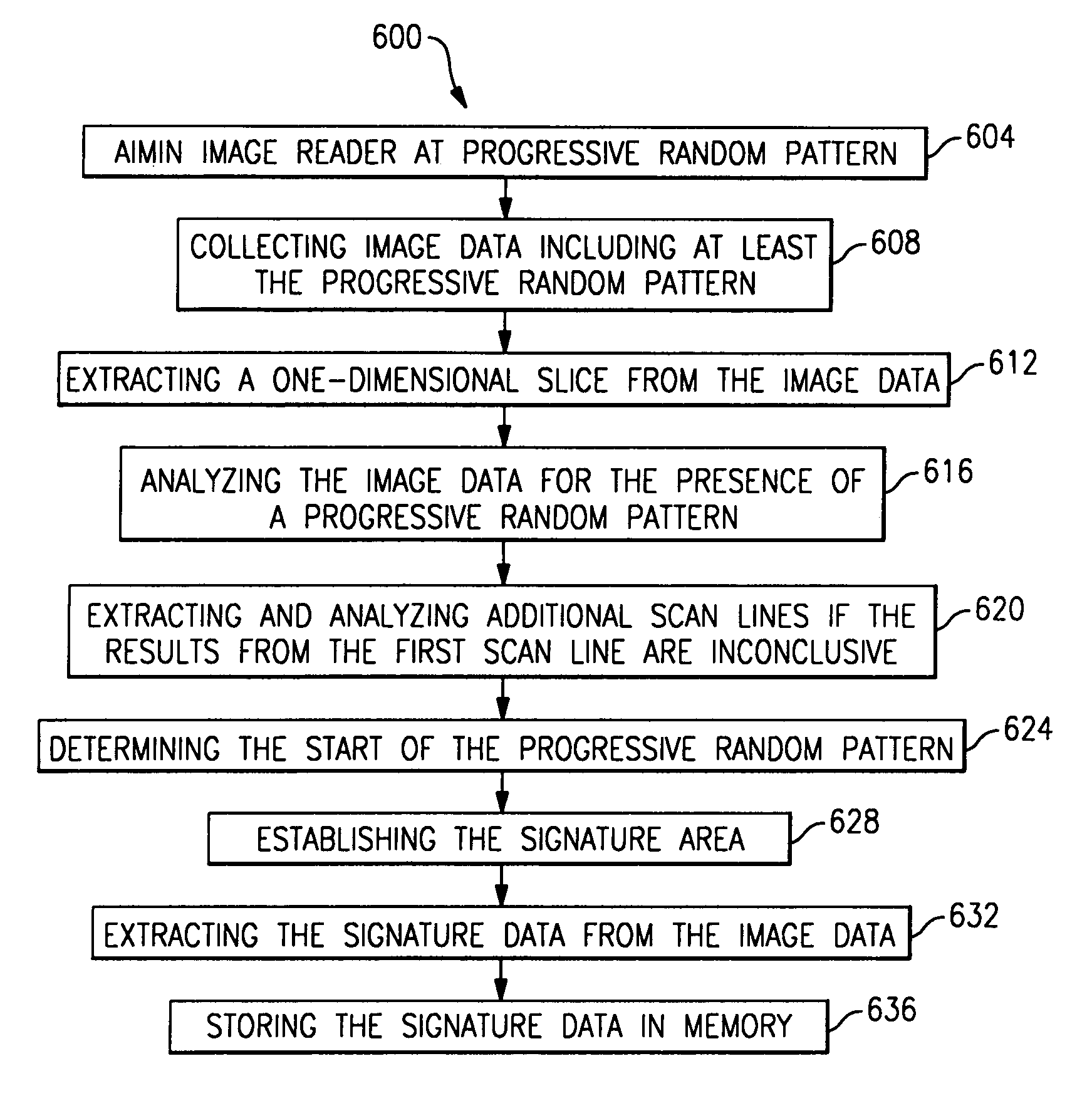
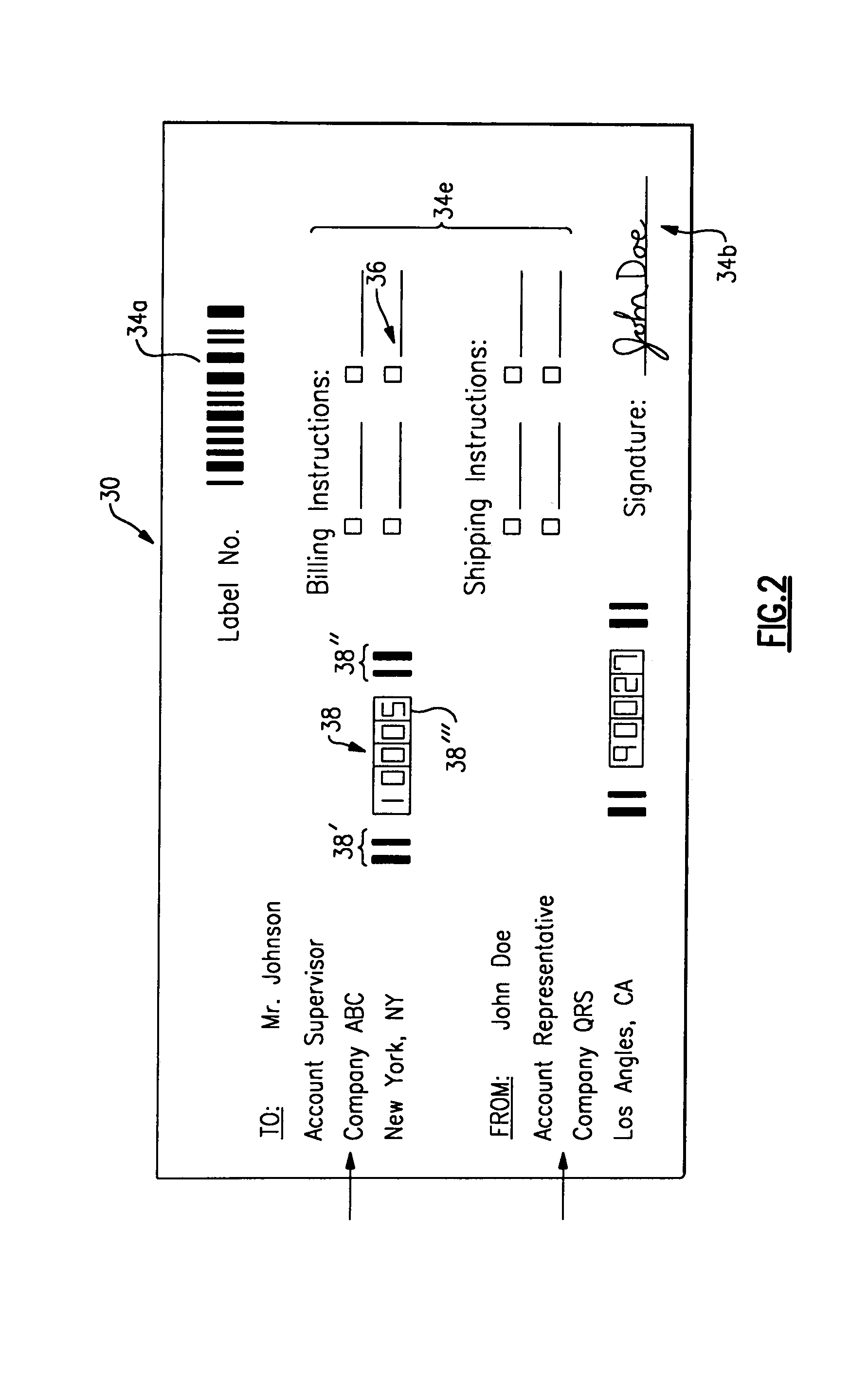
System and method to automatically discriminate between a signature and a barcode
The invention features a system and method for automatically discriminating between different types of data, such as a barcode and a signature, with an image reader. In brief overview of one embodiment, the automatic discrimination feature of the present image reader allows a human operator to aim a hand-held image reader at a target containing a dataform, a signature, or another data type and actuate the trigger on the image reader. An autodriscrimination module in the image reader in one embodiment analyzes image data representative of the target and determines whether the target contains a dataform, a signature, or another type of data. If the target contains a dataform, the image reader decodes the dataform and outputs decoded dataform data, such as the alphanumeric sequence encoded by a barcode. If the target contains a signature, the image reader captures or stores a representation of the signature.
Owner:HAND HELD PRODS
Electronic transaction verification system
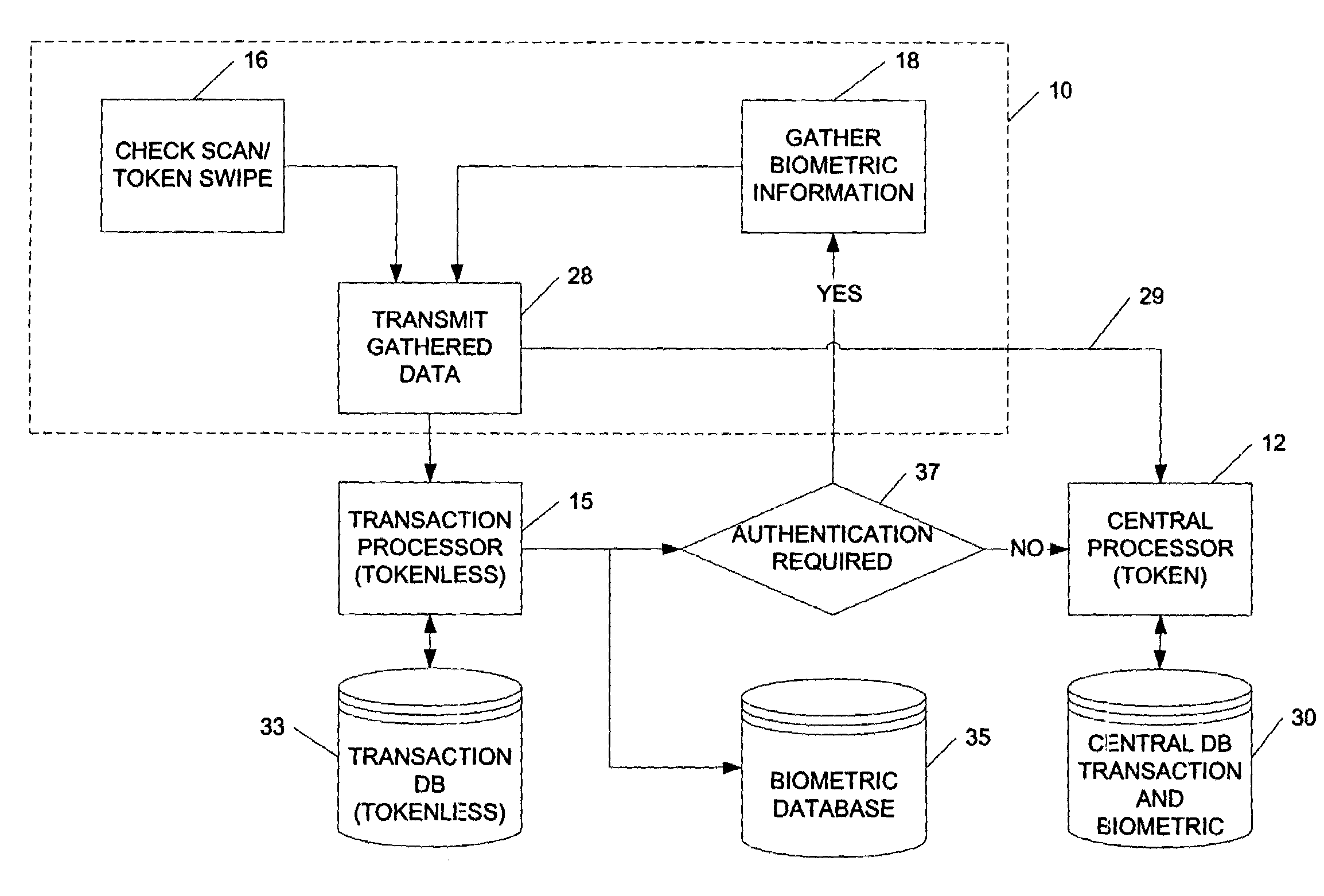
InactiveUS7349557B2Inhibitory activityIndustrial applicabilityElectric signal transmission systemsDigital data processing detailsPaymentBiometric data
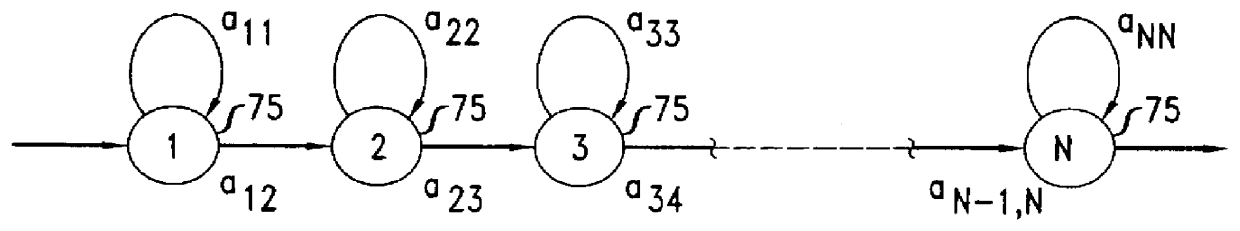
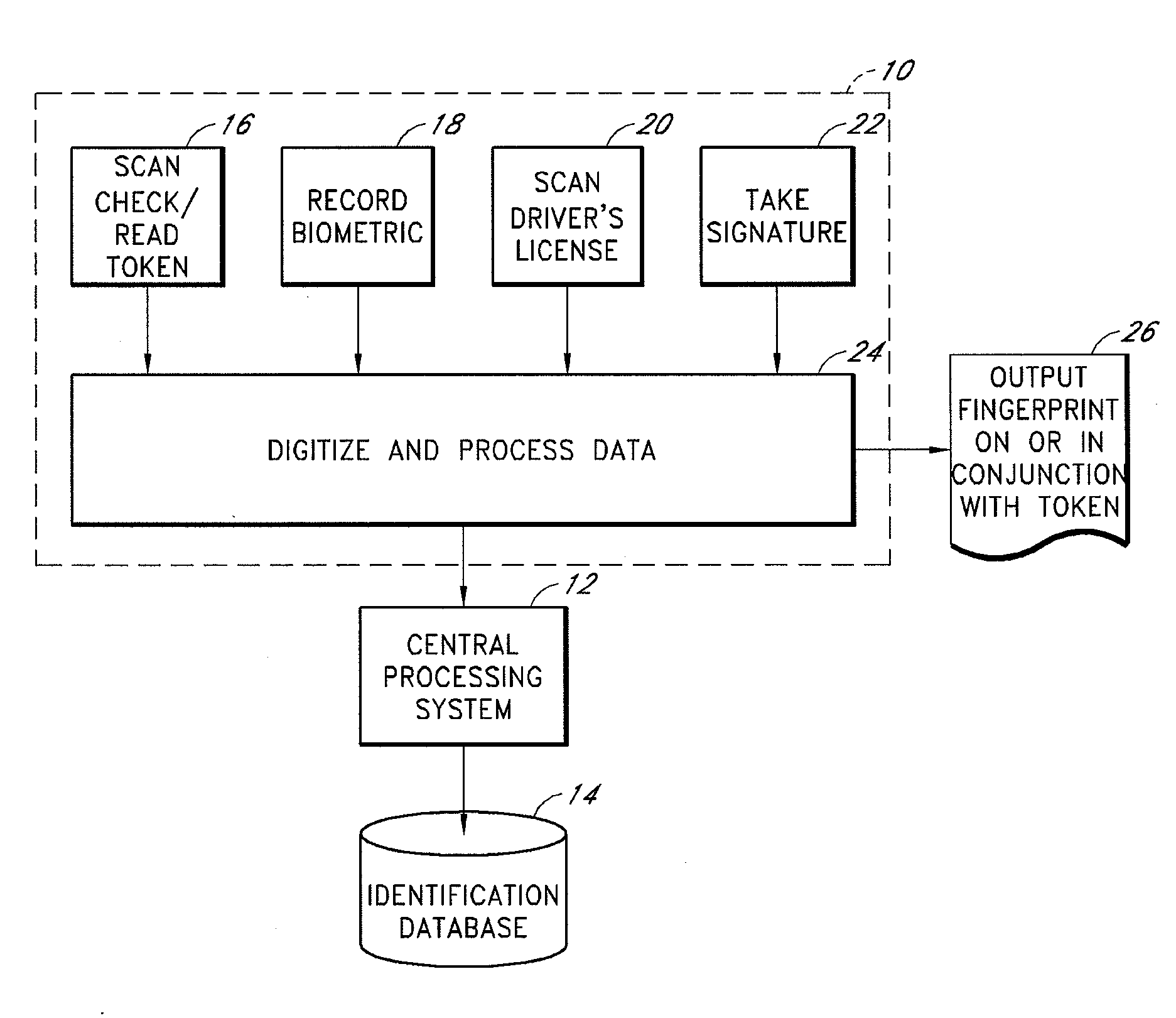
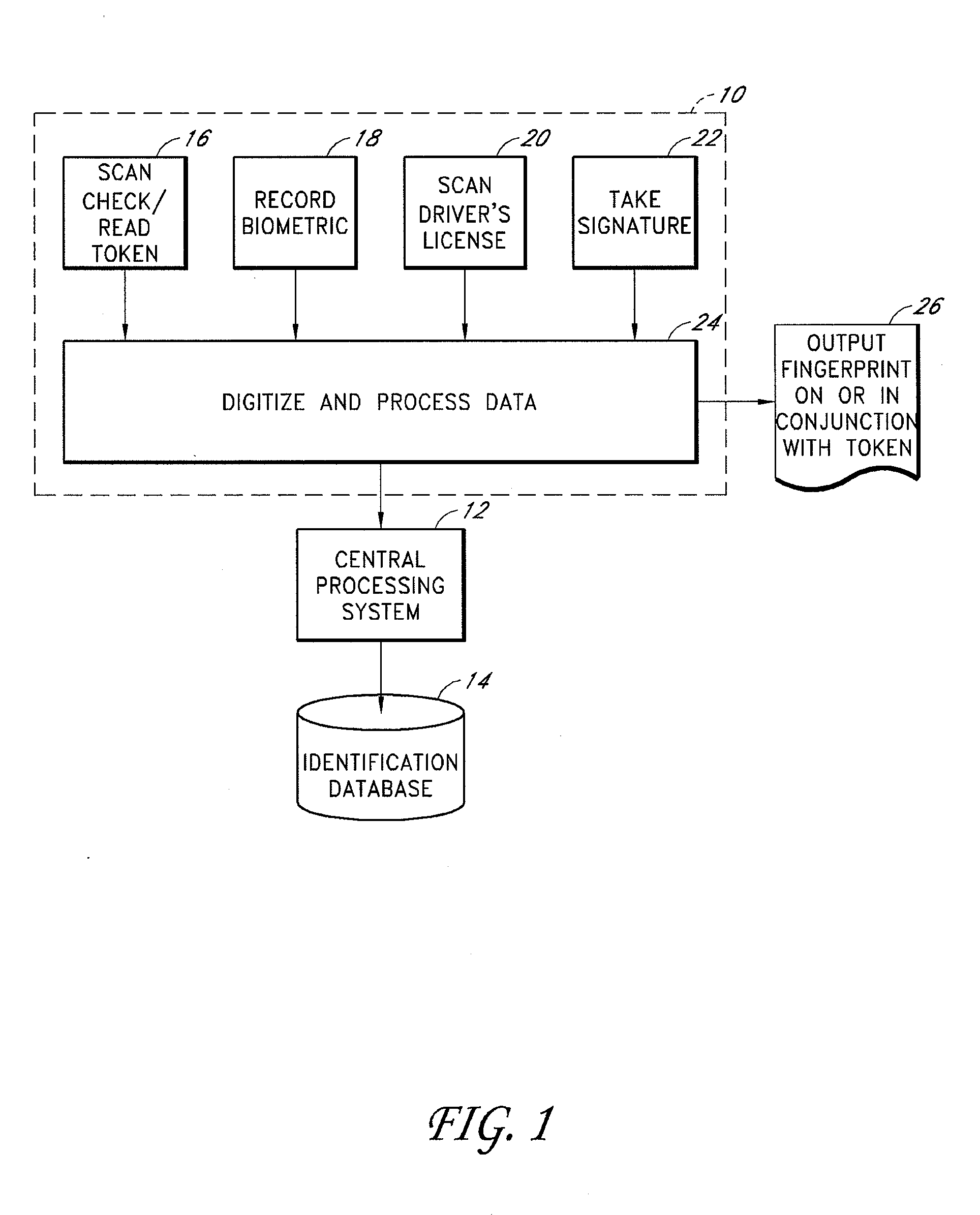
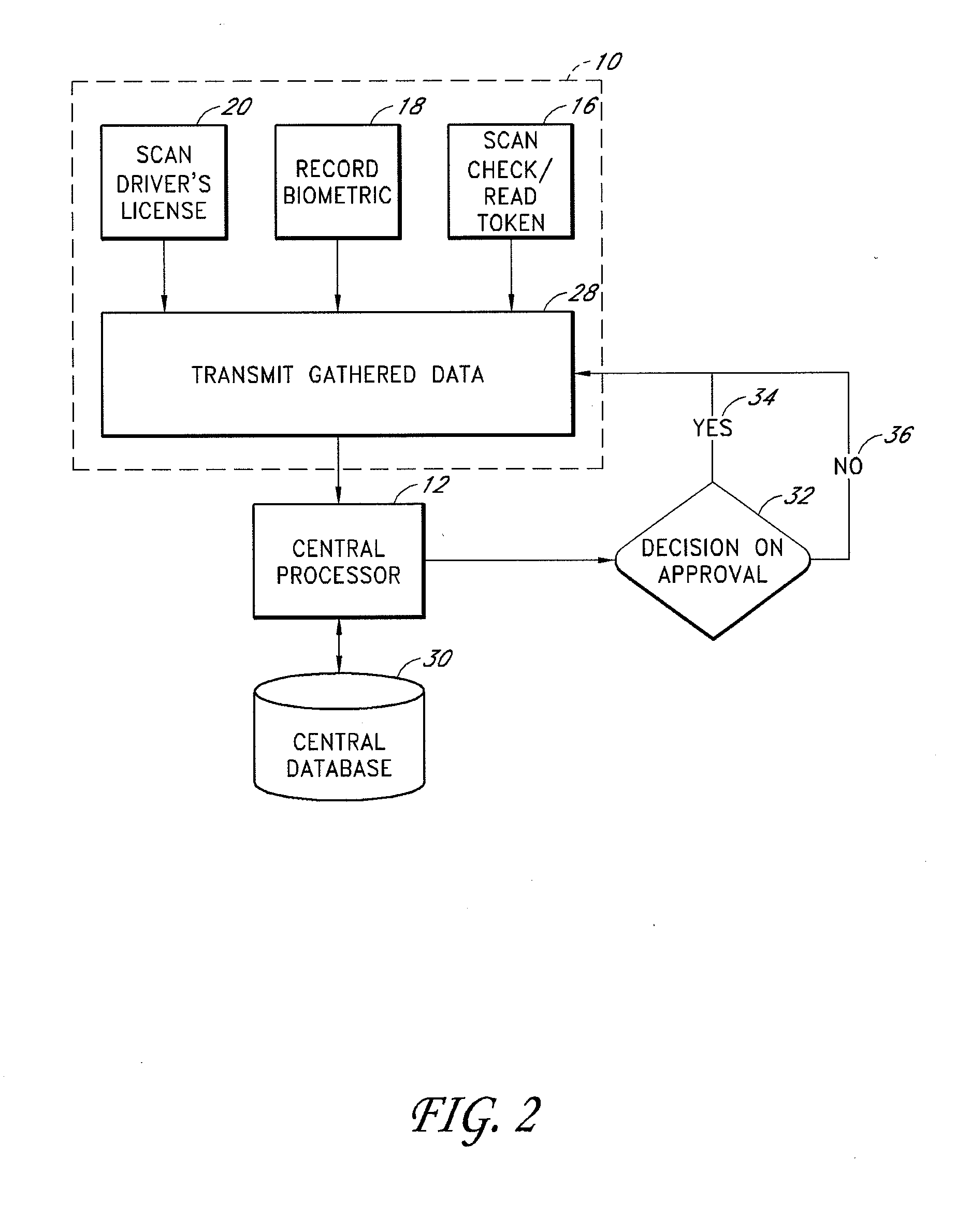
An electronic transaction verification system for use at a location where a transaction token is presented for payment. The electronic transaction verification system digitizes various indicia of the token, and transmits the transaction information data to a central processing system. The central processing system compares the transaction data with an existing database of information to determine if the customer at the point of the transaction is authorized to use the account. The electronic verification system includes a biometric data device for recording and / or transmitting biometric data taken at the transaction location. The electronic transaction verification system can be used in conjunction with a tokenless transaction processing system to determine if the token presented for payment is associated with an account established for an authorized user that has registered with the tokenless transaction processing system.
Owner:BIOMETRIC PAYMENT SOLUTIONS
Method for identity verification
InactiveUS20050169504A1Processing speedMinimize privacy concernDigital data processing detailsChecking apparatusInternet privacyIndex finger
The method for identity verification employs biometric technology. Positioned at the center of the system is a stylus with any of a number of biometric properties or their combination or with one or more metric sensors, while the customer uses the stylus to sign his / her name, or even for writing anything. The identity verification system is used at point-of-sale terminals, in various closed environments, to access a computer network, in applications involving pen-based computers and smart-pens, and for e-commerce. When fingerprint sensors are used, the sensors are positioned in the stylus grip, one sensor for the index finger, and a second sensor for the thumb. In one variation, one-to-one biometric matching is used. Each participant carries on his / her person a device that includes an encrypted biometric for reference purposes to gain access Into the system. Processing is simplified since the system need only make a “MATCH” or “NO MATCH” decision. In a second variation that is particularly useful in closed environments, one-to-many biometric matching is used. During each event access request, the community of reference prints is searched for a match with the applicant. Each member of the community need carry nothing on his / her person to participate in the system. In either variation, the stylus is either attached to each site or is portable, one such stylus being carried by each participant.
Owner:PEN ONE INC
Method for identity verification
InactiveUS20060215886A1Processing speedMinimize privacy concernComputer security arrangementsPrint image acquisitionIndex fingerInternet privacy
The method for identity verification employs biometric technology. Positioned at the center of the system is a stylus with any of a number of biometric properties or their combination or with one or more metric sensors, while the customer uses the stylus to sign his / her name, or even for writing anything. The identity verification system is used at point-of-sale terminals, in various closed environments, to access a computer network, in applications involving pen-based computers and smart-pens, and for e-commerce. When fingerprint sensors are used, the sensors are positioned in the stylus grip, one sensor for the index finger, and a second sensor for the thumb. In one variation, one-to-one biometric matching is used. Each participant carries on his / her person a device that includes an encrypted biometric for reference purposes to gain access Into the system. Processing is simplified since the system need only make a “MATCH” or “NO MATCH” decision. In a second variation that is particularly useful in closed environments, one-to-many biometric matching is used. During each event access request, the community of reference prints is searched for a match with the applicant. Each member of the community need carry nothing on his / her person to participate in the system. In either variation, the stylus is either attached to each site or is portable, one such stylus being carried by each participant.
Owner:UNITED STATES CP LLC
Information management system with authenticity check
InactiveUS20080075333A1Improve securityCredit registering devices actuationCredit schemesDigital recordingDigital records
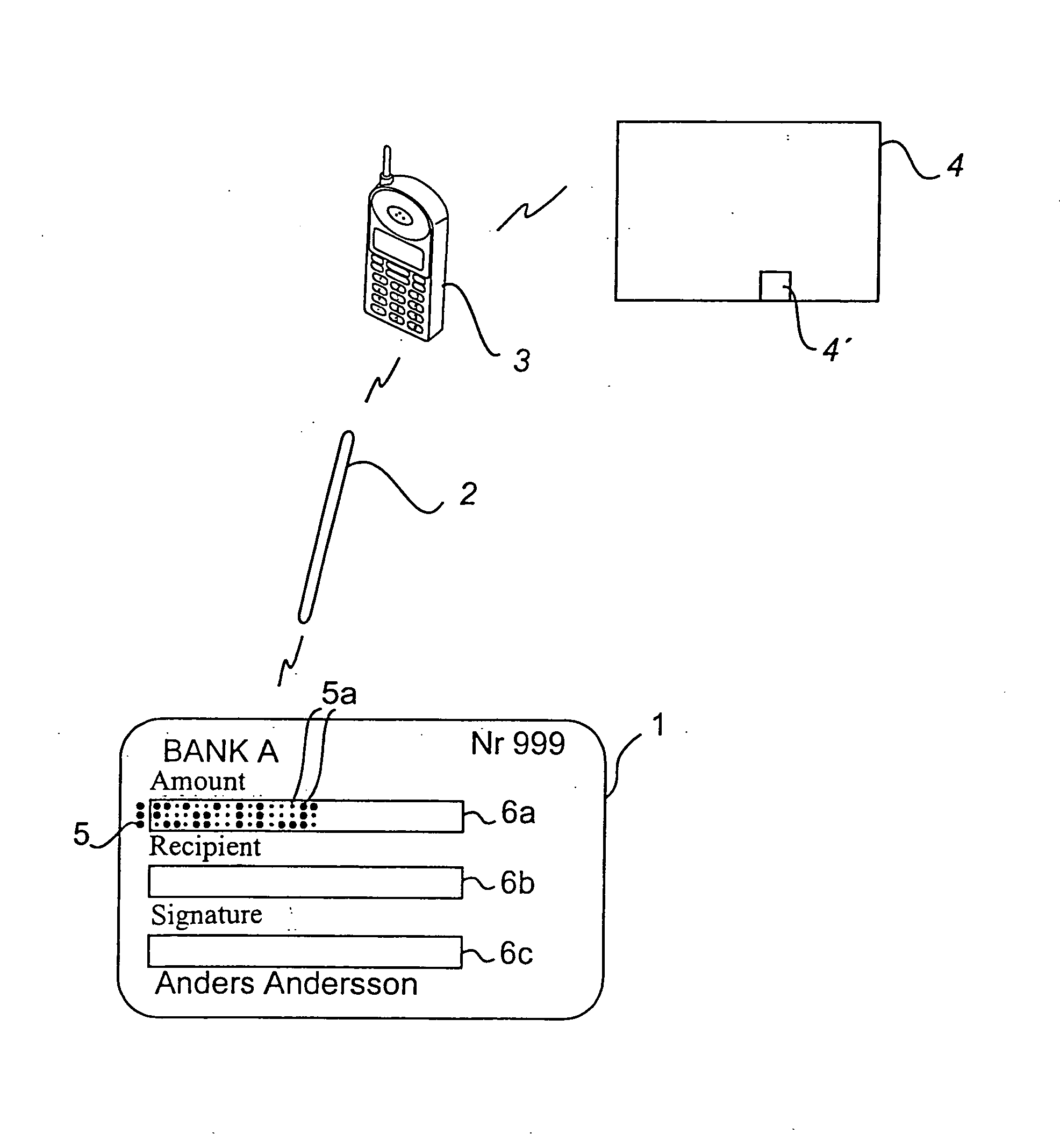
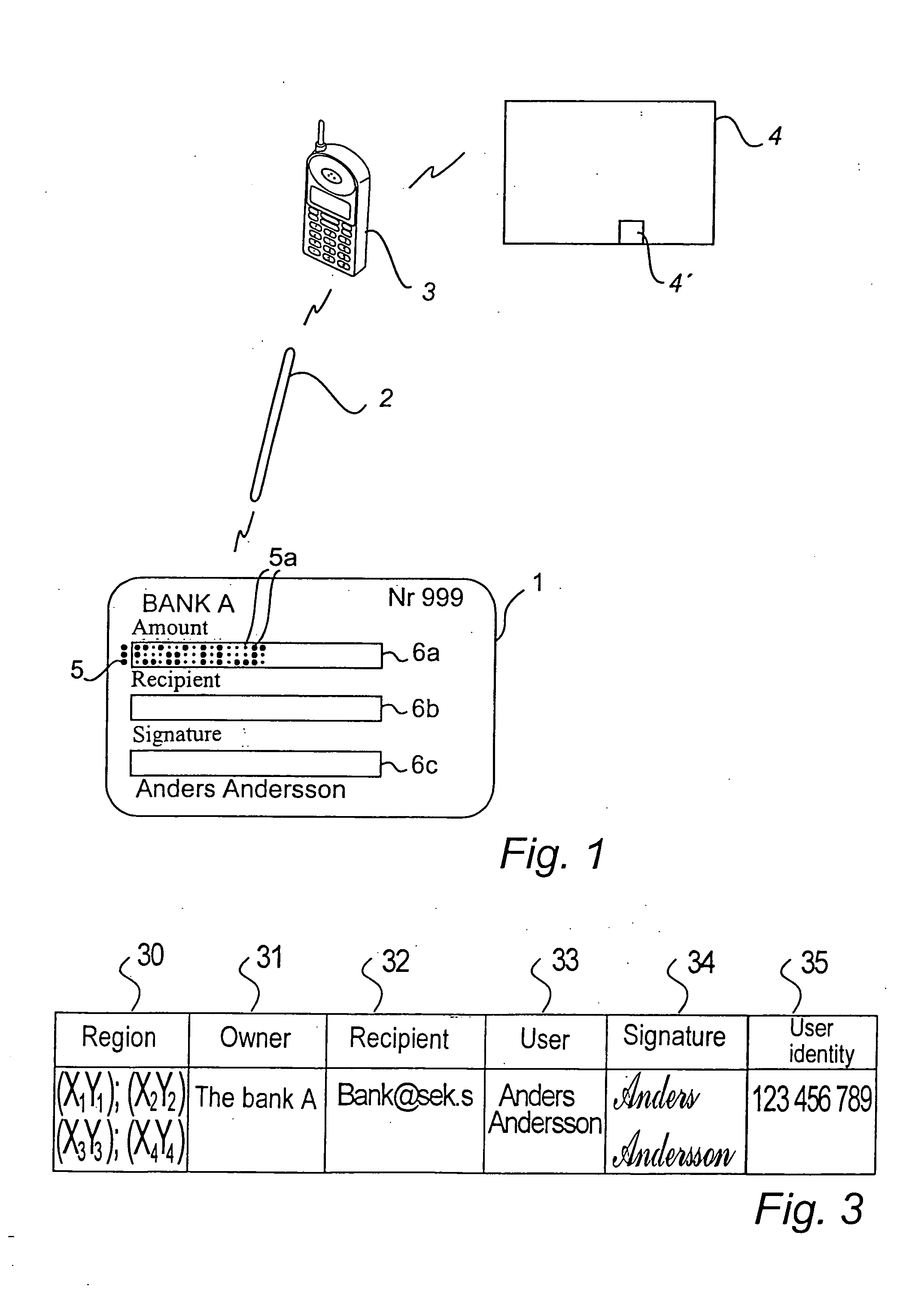
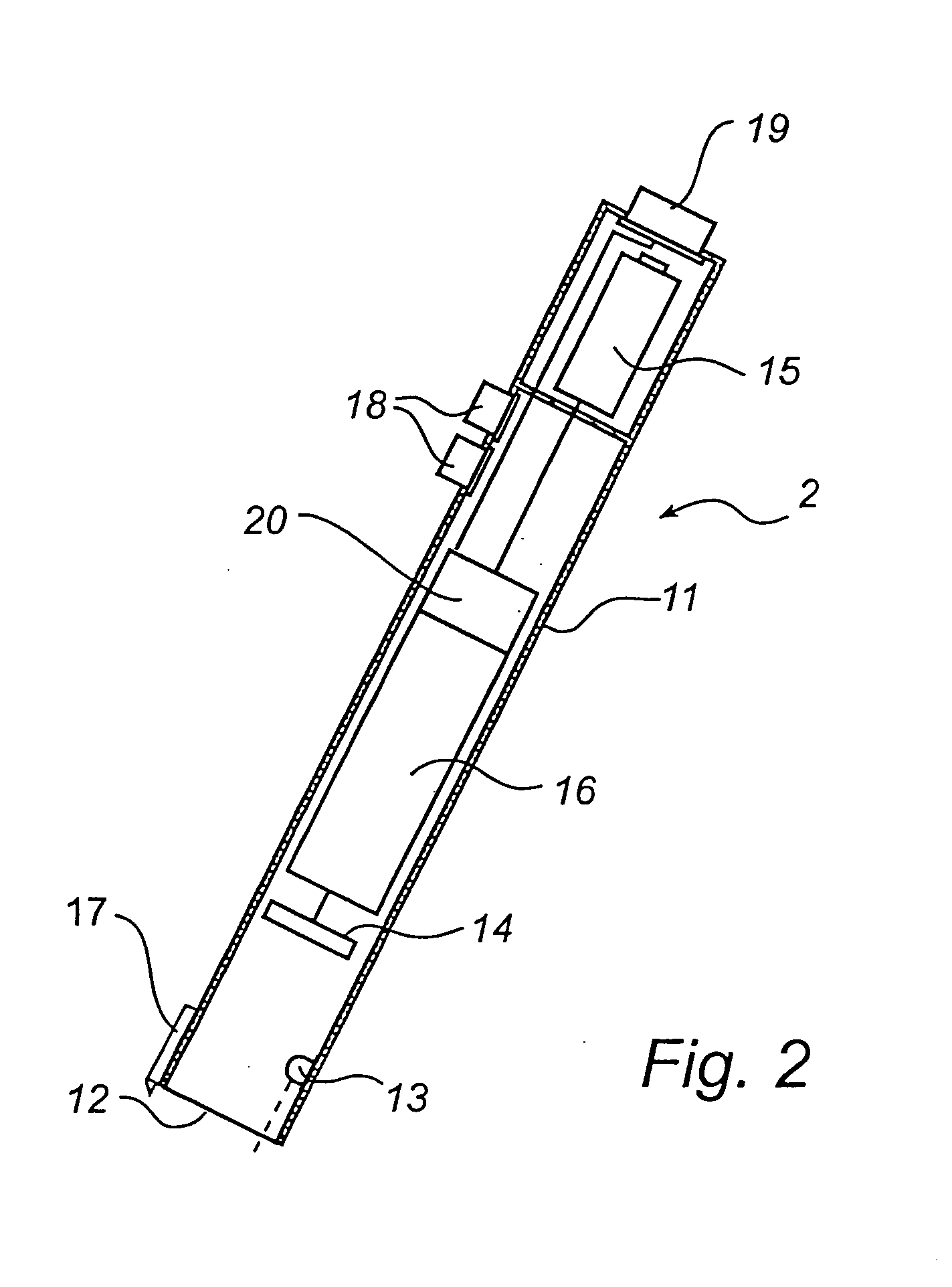
A payment product has a writing area (6c) which is intended for a user's signature. In the writing area there is a first position-coding pattern (5) which makes possible digital recording of the signature. The first position-coding pattern is a subset of a larger second position-coding pattern.The payment product is used in a payment system which is based on electronic payment information, which has been recorded by means of the position-coding pattern, being sent to a server unit, which utilizes the position-coding pattern to check that the payment information is valid.
Owner:ANOTO IP LIC
System and method to automatically discriminate between a signature and a dataform
There is described a system and method for automatically discriminating between different types of data with an image reader. In brief overview of one embodiment, the automatic discrimination feature of the present image reader allows a human operator to aim a hand-held image reader at a target that can contain a dataform and / or a signature and actuate the image reader. An autodiscrimination module in the image reader in one embodiment analyzes image data representative of the target and determines a type of data represented in the image data.
Owner:HAND HELD PRODS
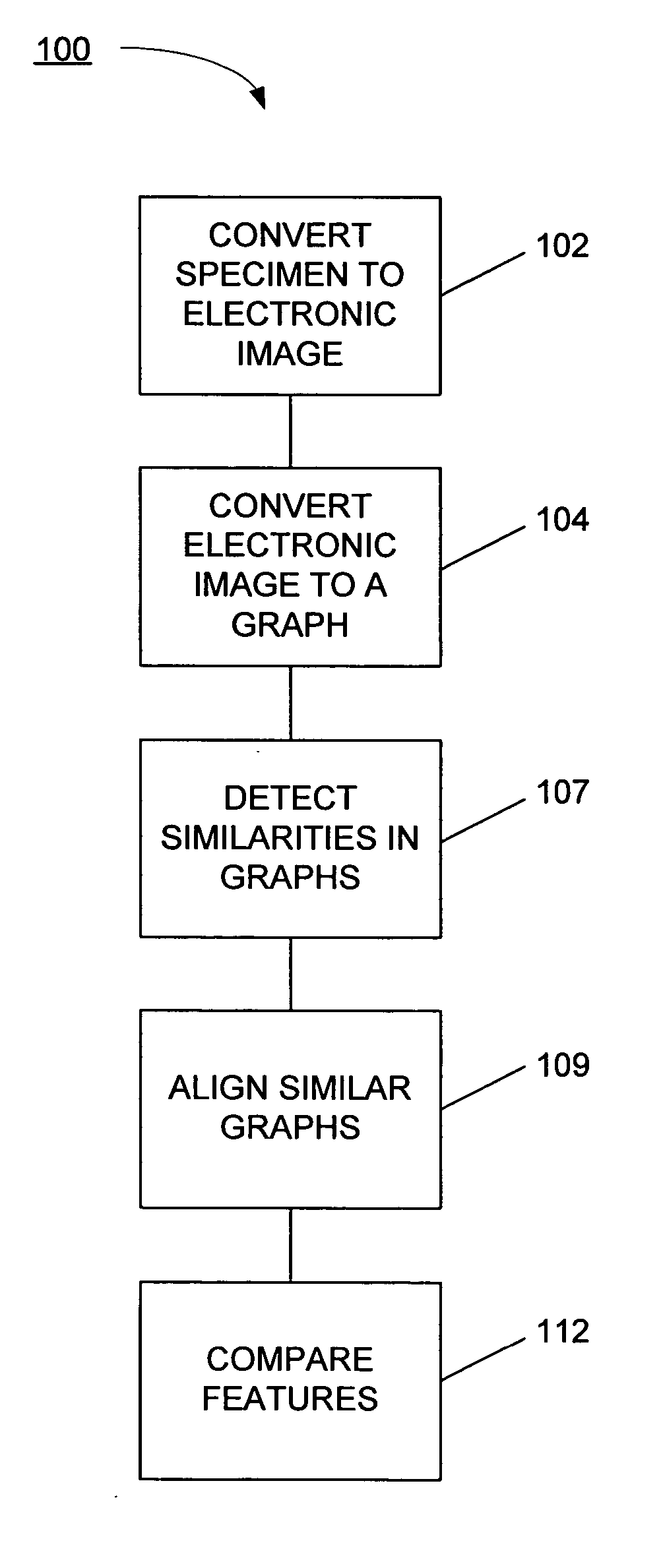
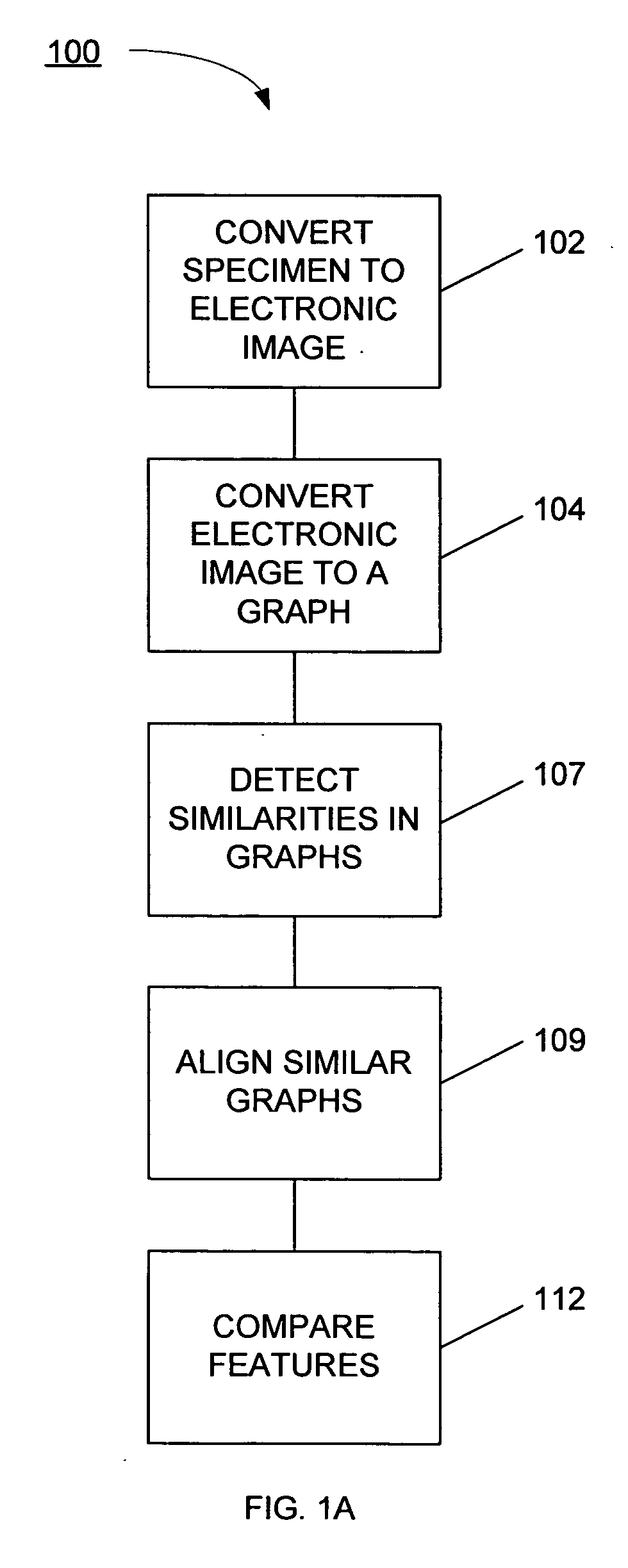
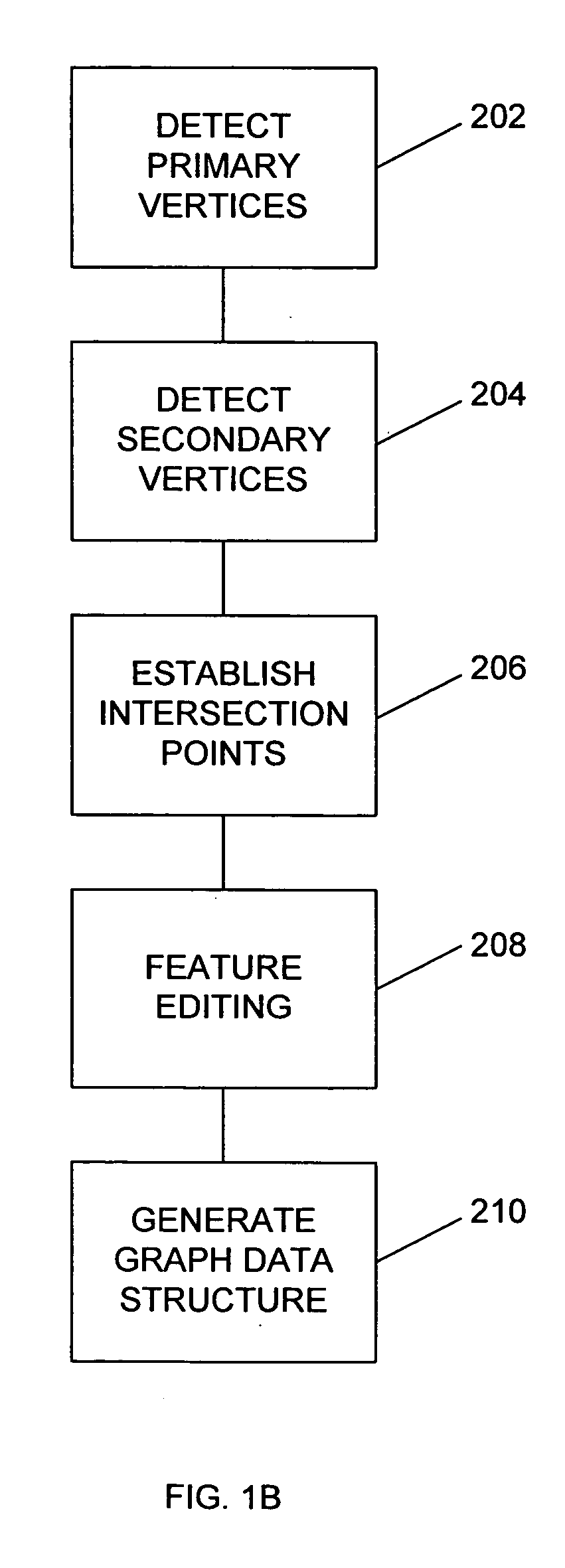
Systems and methods for biometric identification using handwriting recognition
A biometric handwriting identification system converts characters and a writing sample into mathematical graphs. The graphs comprise enough information to capture the features of handwriting that are unique to each individual. Optical character recognition (OCR) techniques can then be used to identify these features in the handwriting sample so that drafts from two different samples can be aligned to compare to determine if the features in the writing sample correlate with each other.
Owner:GANNON TECH GROUP
Data security system
InactiveUS20060005042A1Easy accessNeed can be addressedDigital data processing detailsChecking apparatusData accessComputer usage
A data security system comprises a host processor, and a plurality of remote computers. Each remote computer provides biometric authentication of a user prior to responding to the user request for data access. The remote computers are handheld when in operational mode. A sensor in the handheld computer captures a biometric image while the remote computer is being used. The biometric sensor is positioned in such a way that the sensor enables the capture of the biometric image continually during computer usage with each request for access to secure data. The biometric authentication occurs in a seamless manner and is incidental to the data request enabling user identity authentication with each request to access secure data.
Owner:UNITED STATES CP LLC
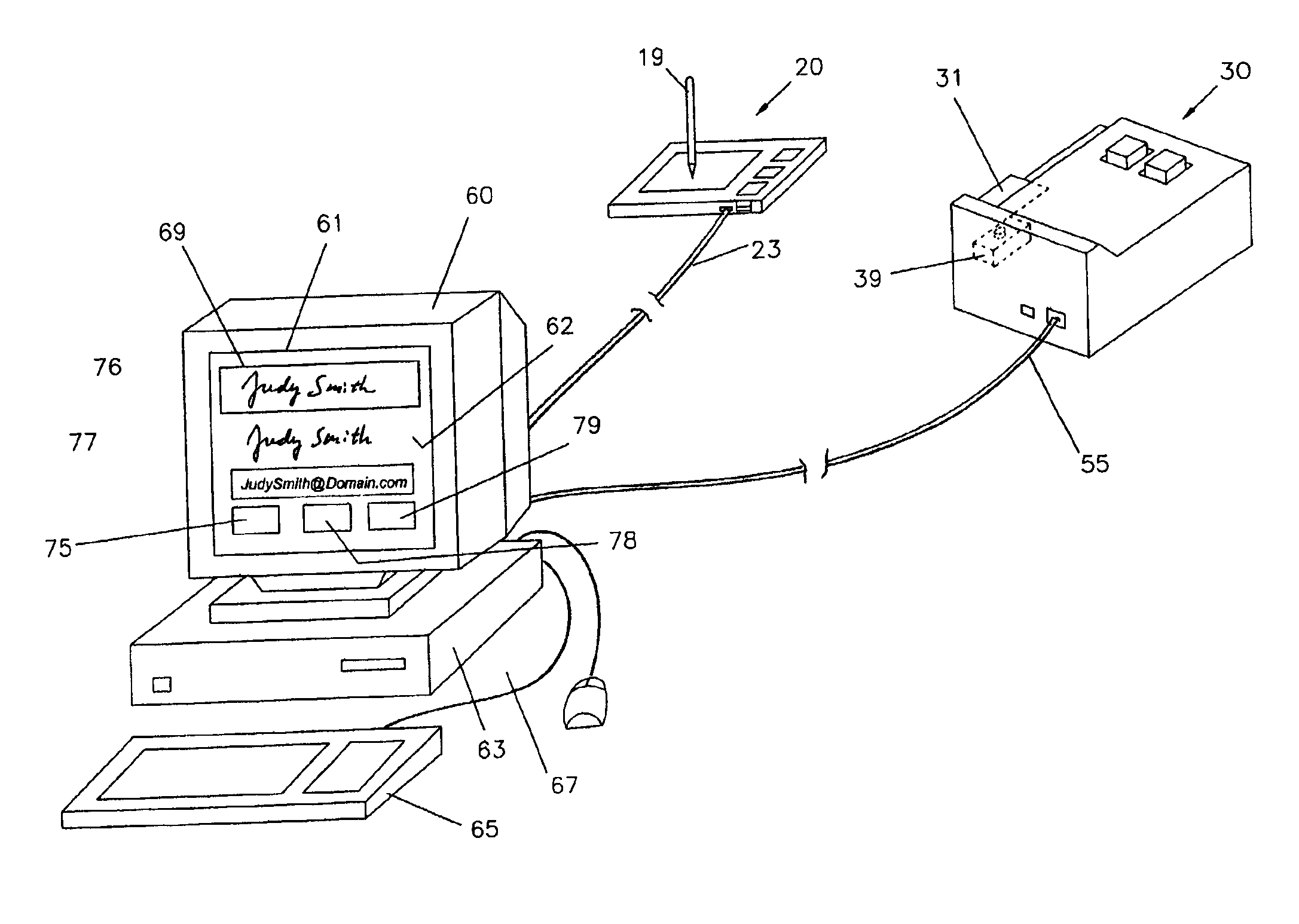
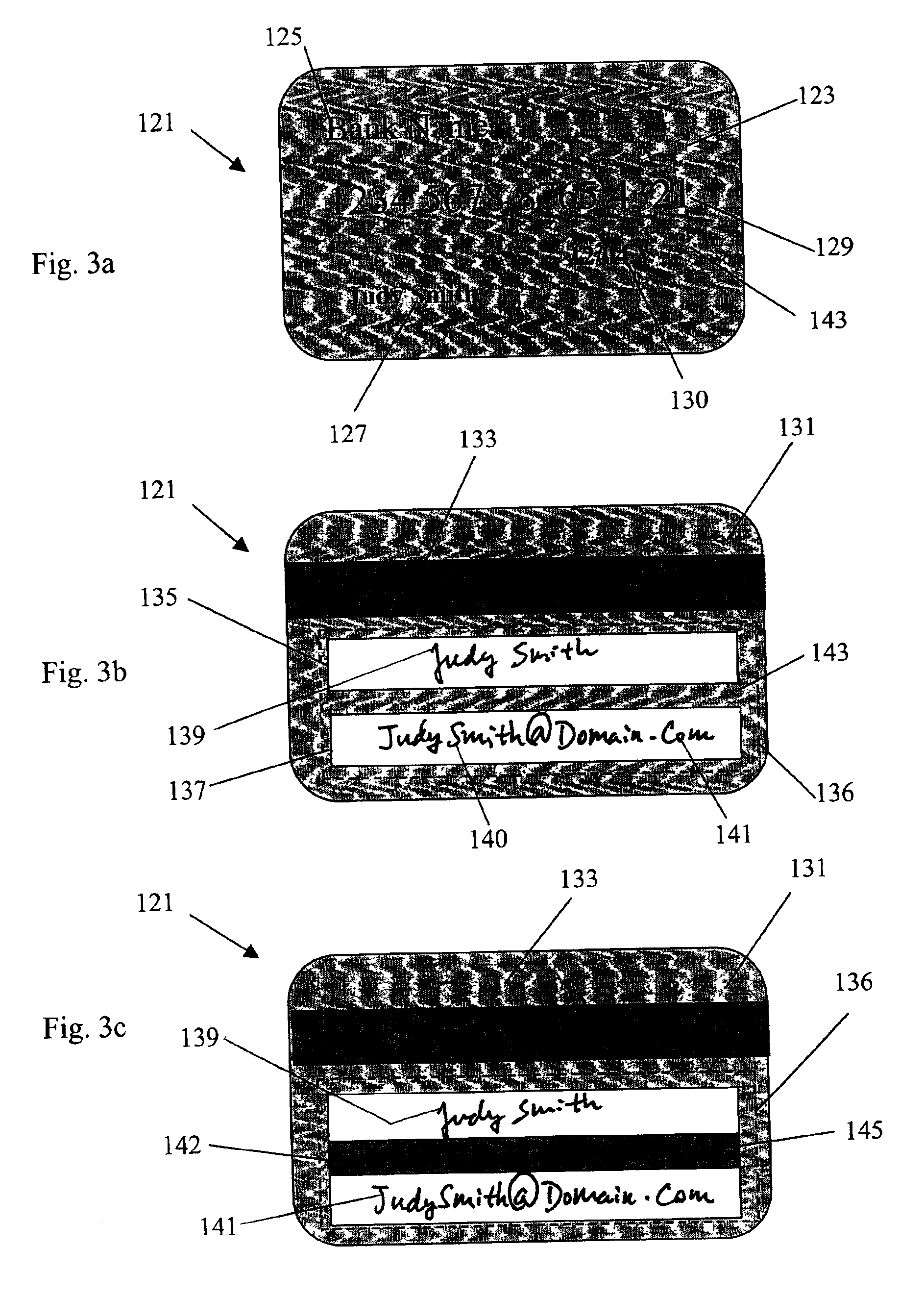
System of central signature verifications and electronic receipt transmissions
InactiveUS6873715B2Eliminate needElectric signal transmission systemsMultiple keys/algorithms usageCredit cardEmail address
A credit-card reader having a built-in digital camera for capturing a template signature and an email address on a credit card. The email address is identified by an optical character recognition program and input to an email system. A test signature is entered on a touch-pad input device and both the test and the template signatures are normalized and displayed for verification. Action buttons are provided on the display screen for enforcing the signature verification actions. The system enables the transmission of an electronic receipt selectively controlled by the customer and eliminates the needs of physically handling a credit card for signature verification and manual input or pre-registration of an email address for an electronic receipt. The computer-assisted features enables a central system of signature verification for purchase transactions at self-service check-out counters.
Owner:KUO YOU TI +1
Modular signature and data-capture system and point of transaction payment and reward system
InactiveUSRE41716E1Increase flexibilityMinimizes paper-workComplete banking machinesFinanceReward systemCompatible accessories
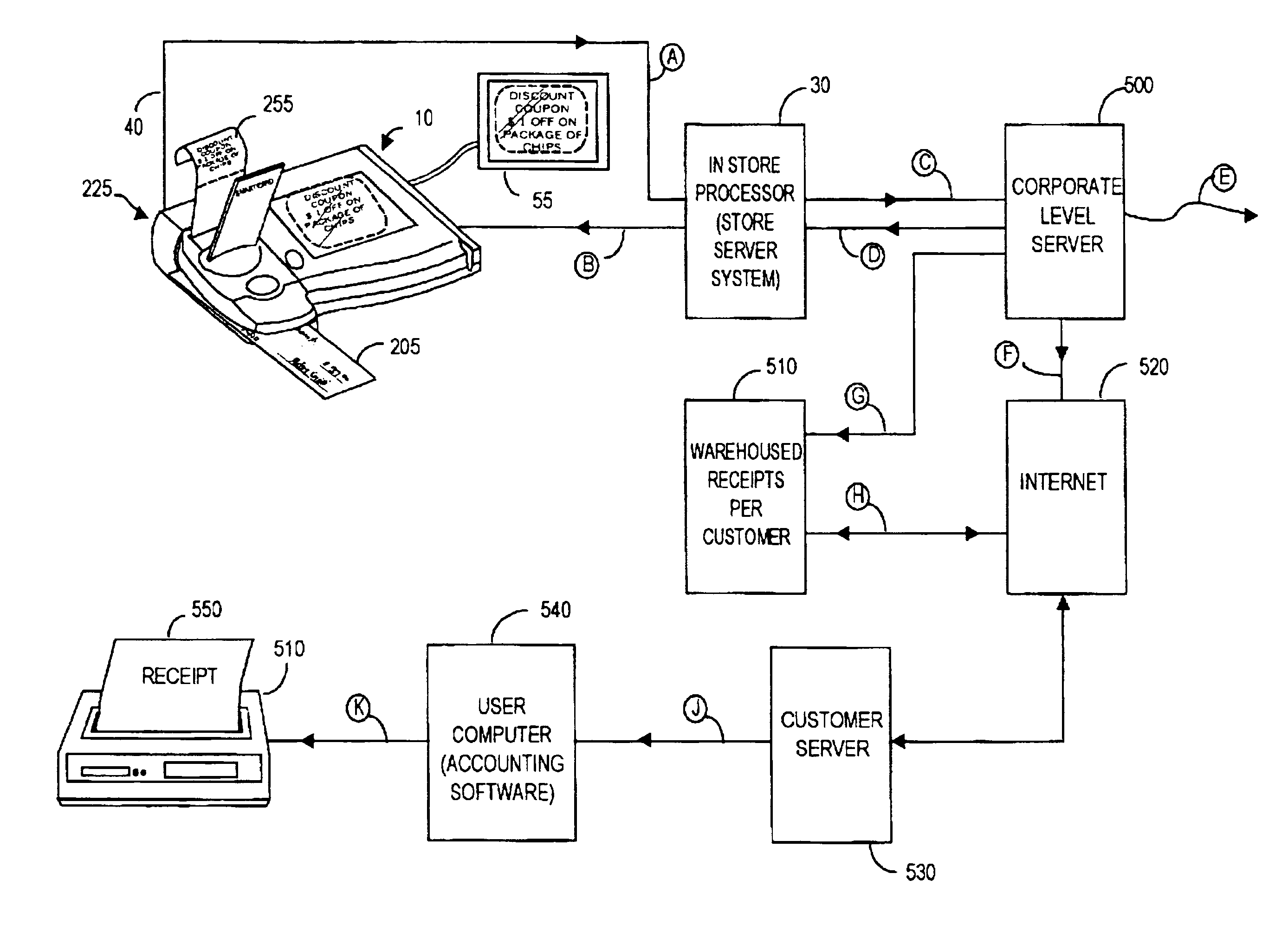
A modular signature and data capture device employs a standardized ISA bus, standardized communication ports, and standardized ×86 CPU architecture to promote flexibility in using past, present, and future software and accessories. A VGA-caliber backlit LCD is superimposingly combined with a pressure touch pad that is useable with a passive stylus. The LCD displays pen drawn signatures and graphics in real-time, and can display images and data stored in the device, or downloaded from a host system, including advertisements. The LCD can also display menus, device instructions, virtual pressure-sensitive data keys, and control keys. The device includes a built-in a three-stripe magnetic card reader unit. The device accepts PCMCIA-compatible accessories including solid state memory units and smartcards, and is compatible with plug-in accessories including an external PIN keypad entry unit, a fingerprint unit, an omnibus unit including a printer and check processor in addition to a fingerprint unit. Security is provided by DES-encrypting PIN data and / or using Master / Session and / or DUKPT key management, or by using fingerprint token data as a PIN. The invention may be used to conduct paperless transactions in which the merchant is paid in realtime. Further, merchant purchase profiles may be generated on a per-user basis to promote more effective advertising.
Owner:SYMBOL TECH LLC
Systems and methods for handwriting analysis in documents
InactiveUS20040218801A1Character recognitionSignature reading/verifyingNatural language processingHandwriting
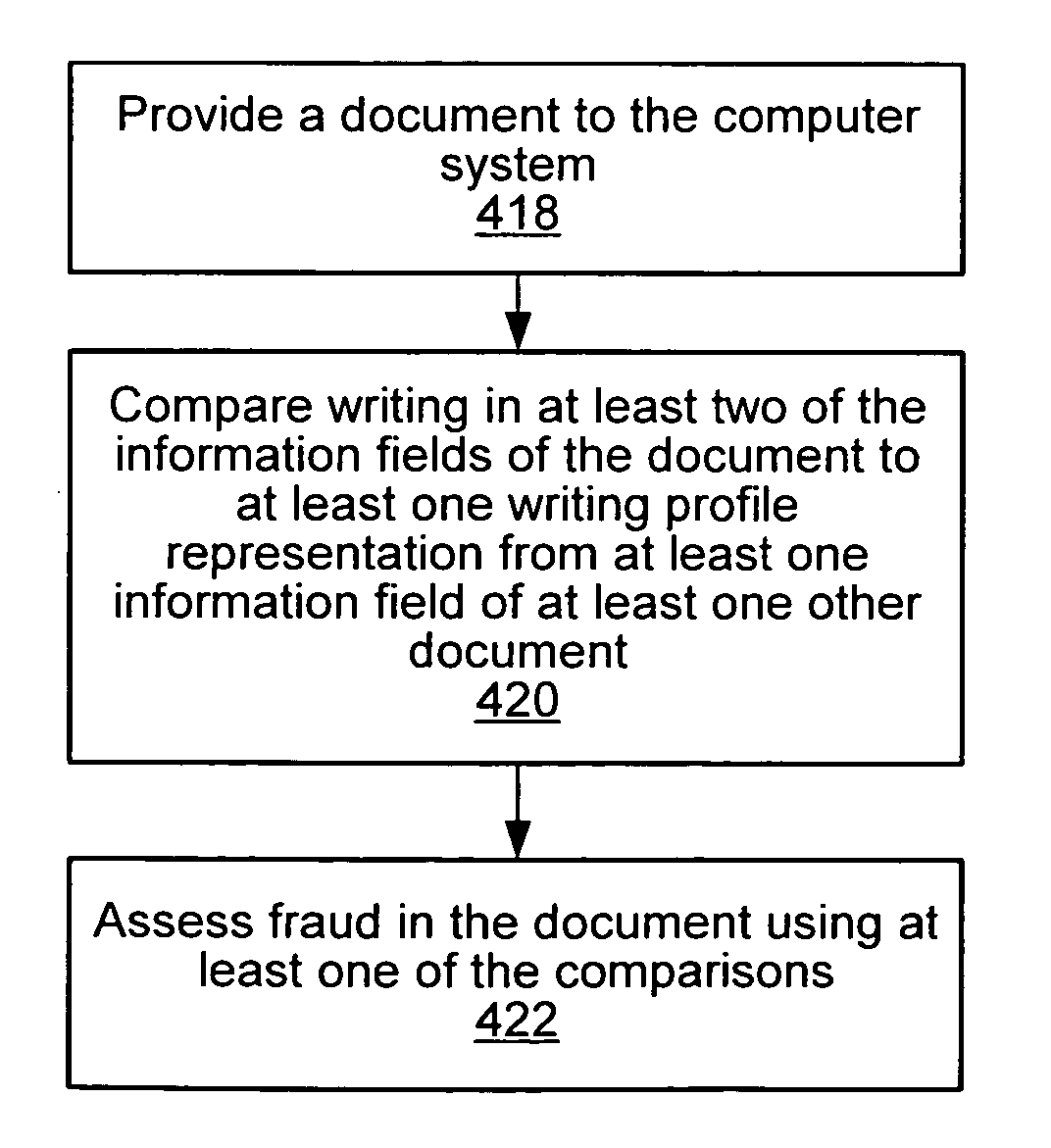
Methods and systems are provided for analyzing and assessing documents using a handwriting profile for documents, such as a payment instrument. A method may include providing one or more documents to a computer system. In one embodiment, handwriting profile representations may be determined for information fields of the document. The determination may use handwriting from at least one of the information fields of the documents. In some embodiments, handwriting profile representations may be updated from one or more additional documents. In certain embodiments, a document may be provided to a computer system for assessment. Assessment may include comparing handwriting in the information fields of the document to handwriting profile representations from information fields of at least one other document. In an embodiment, the method may include assessing fraud in the document using at least one of the comparisons.
Owner:COMP SCI A OF NV
Signature verification method using hidden markov models
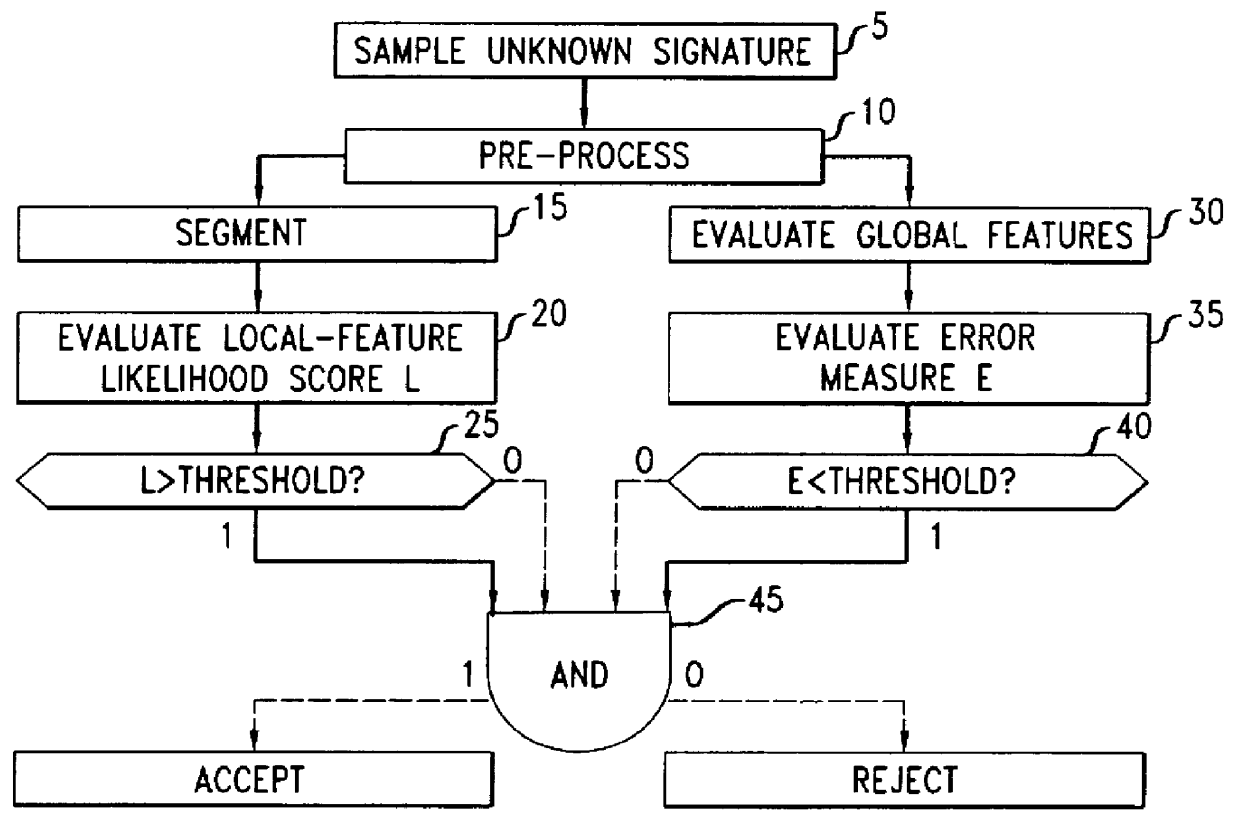
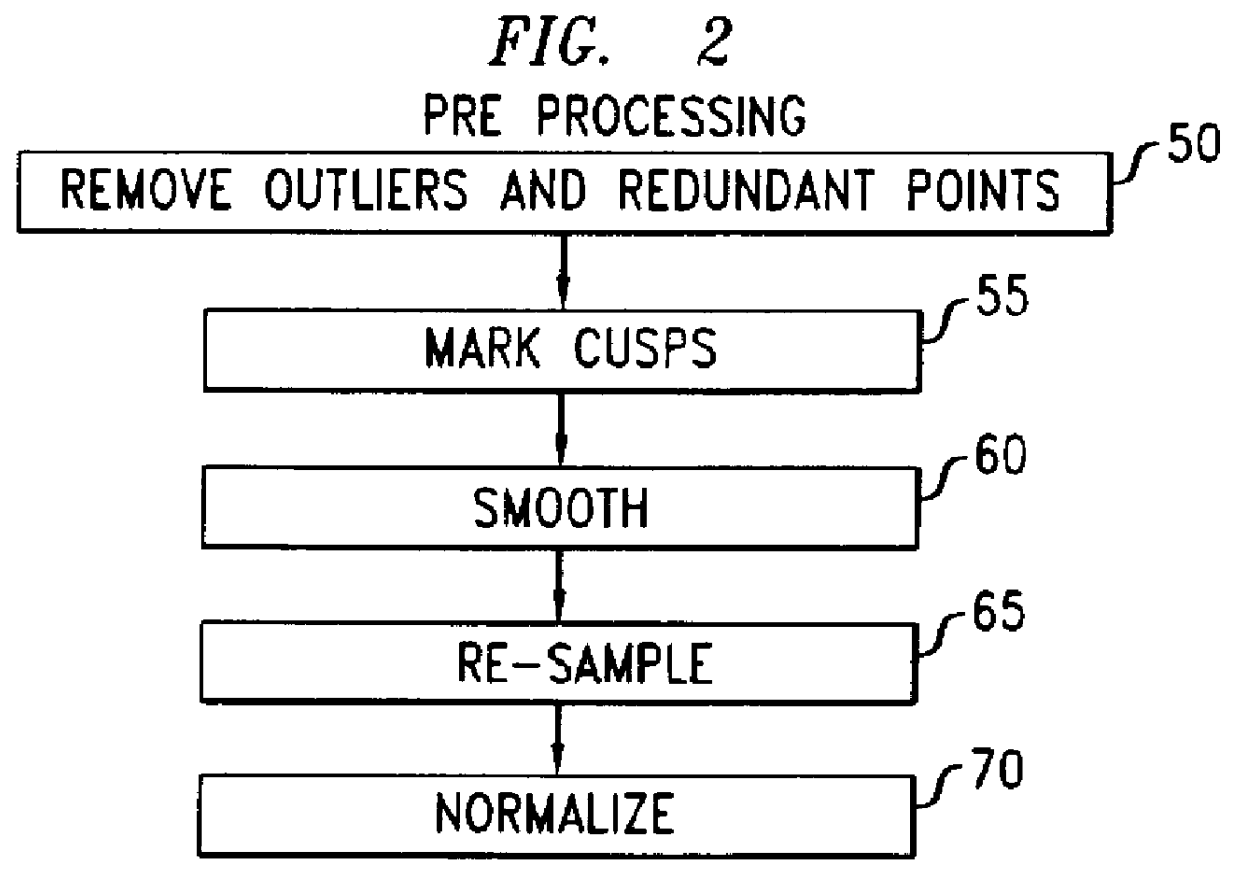
A signature verification method involves segmenting a smoothed and normalized signature and, for each segment, evaluating at least one local feature, thereby to obtain a feature-value vector. The method further includes computing the likelihood that the segments having the observed sequence of feature values were generated by a particular hidden Markov model, such model comprising a sequence of states having duration probabilities and feature-value histograms. In one aspect, the invention involves explicit state-duration modeling to account for duration in the respective states underlying the unknown signature. In another aspect, the invention involves computing a measure of signature complexity, and setting the number of states of the hidden Markov model according to such complexity measure.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO +1
Electronic Transaction Verification System
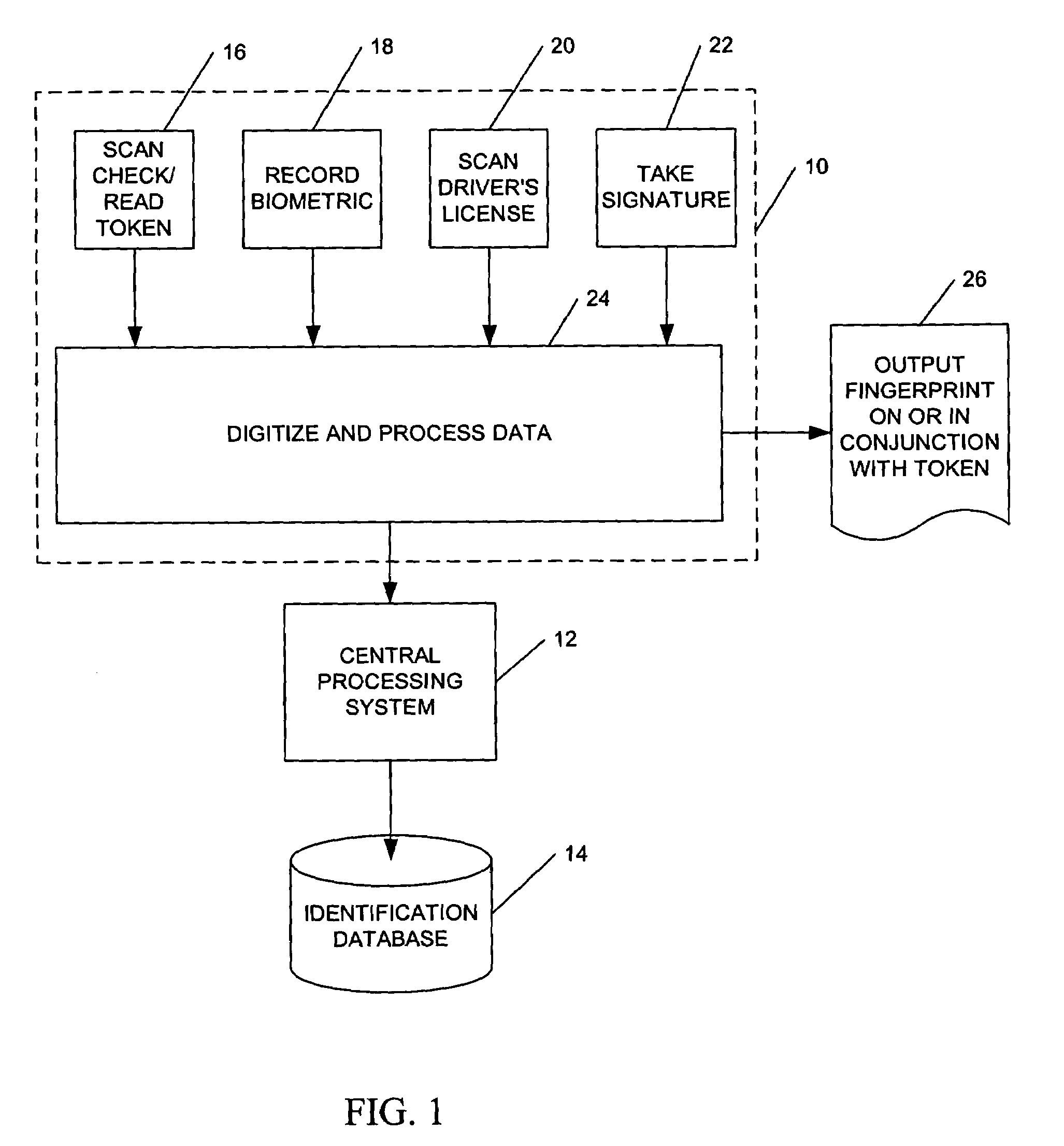
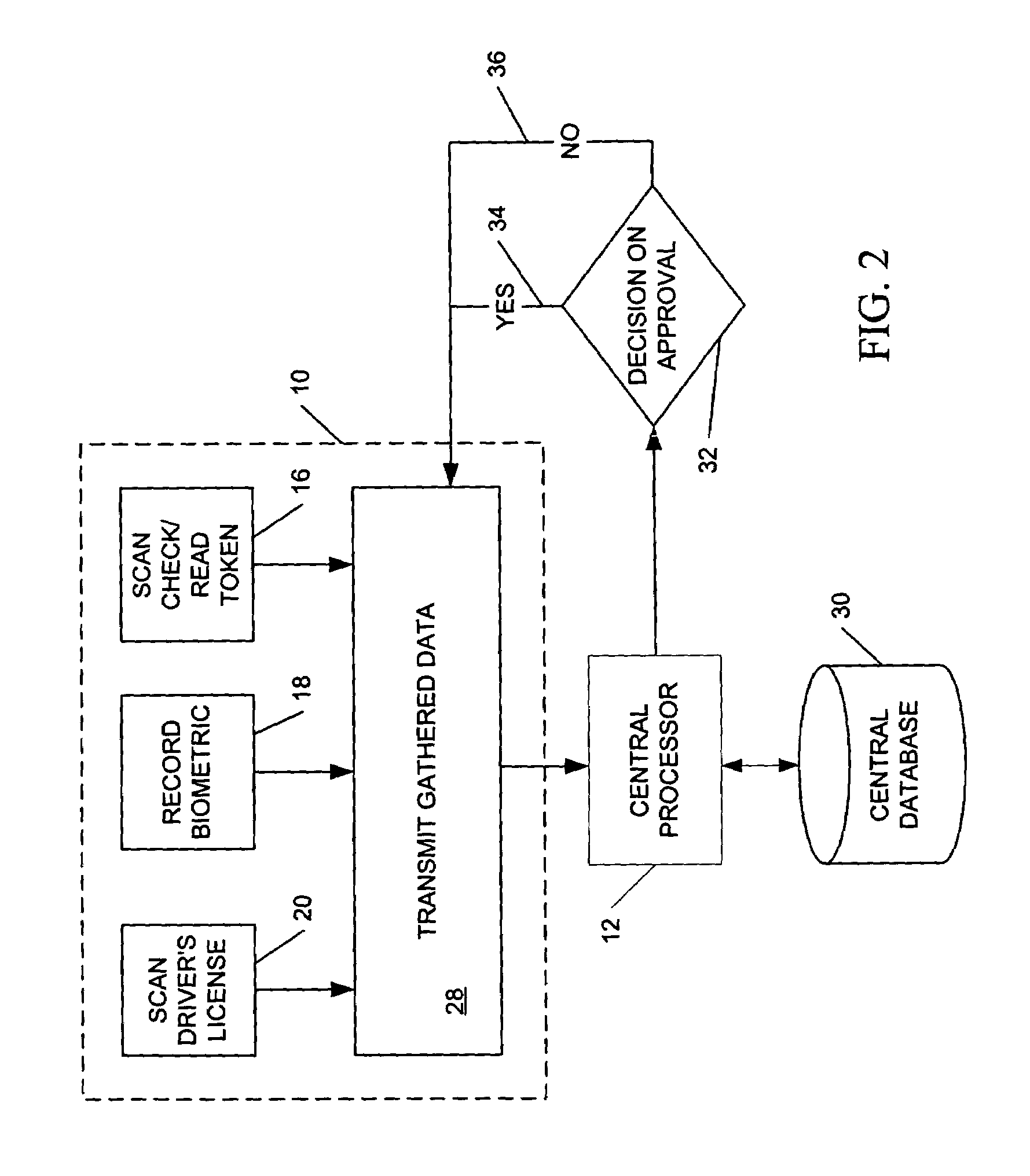
InactiveUS20080156866A1Industrial applicabilityGreat riskComplete banking machinesFinanceBiometric dataCheque
An electronic transaction verification system for use with transaction tokens such as checks, credit cards, debit cards, and smart cards that gathers and transmits information about the transaction token and biometric data. The system preferably has the ability to read or scan transaction and account information printed or encoded on the transaction token, digitally encode biometric data, scan drivers' licenses or other identification cards, and take a signature of a customer, all at a transaction location for purposes of account verification. The electronic transaction verification system preferably digitizes various indicia of the token, such as the magnetic ink (MICR) line on a presented check or the magnetic strip on a credit card or debit card, and transmits the transaction information data to a central processing system, at which the central processing system compares the inputted data with an existing database of information to determine if the customer at the point of the transaction is in fact authorized to use the account, and if the account is in satisfactory condition for approval of the transaction. The electronic verification system includes a biometric data device for recording and / or transmitting biometric data taken at the transaction location. The electronic transaction verification system can be used in conjunction with a tokenless transaction processing system to determine if the token presented for payment is associated with an account established for an authorized user that has registered with the tokenless transaction processing system.
Owner:BIOMETRIC PAYMENT SOLUTIONS
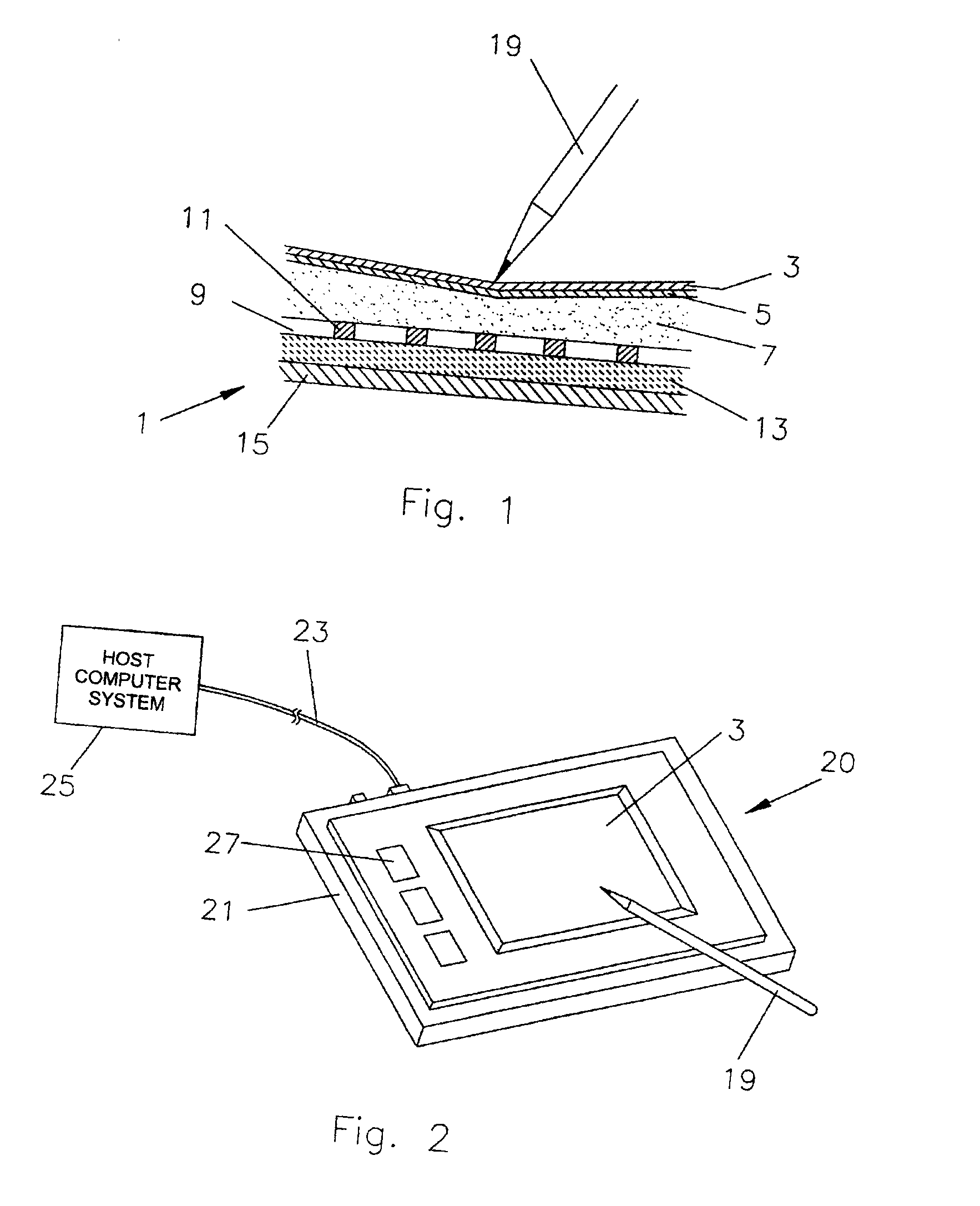
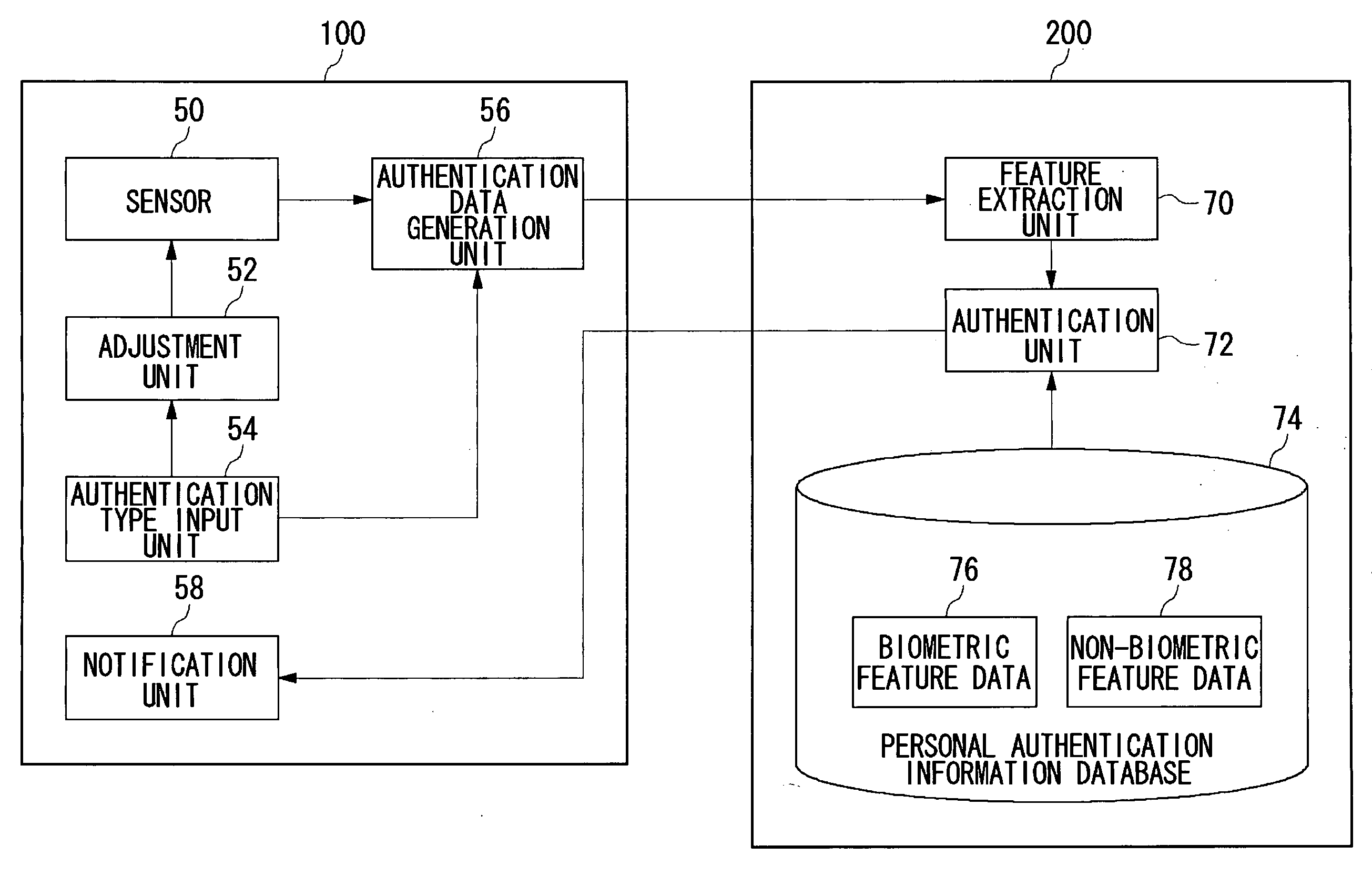
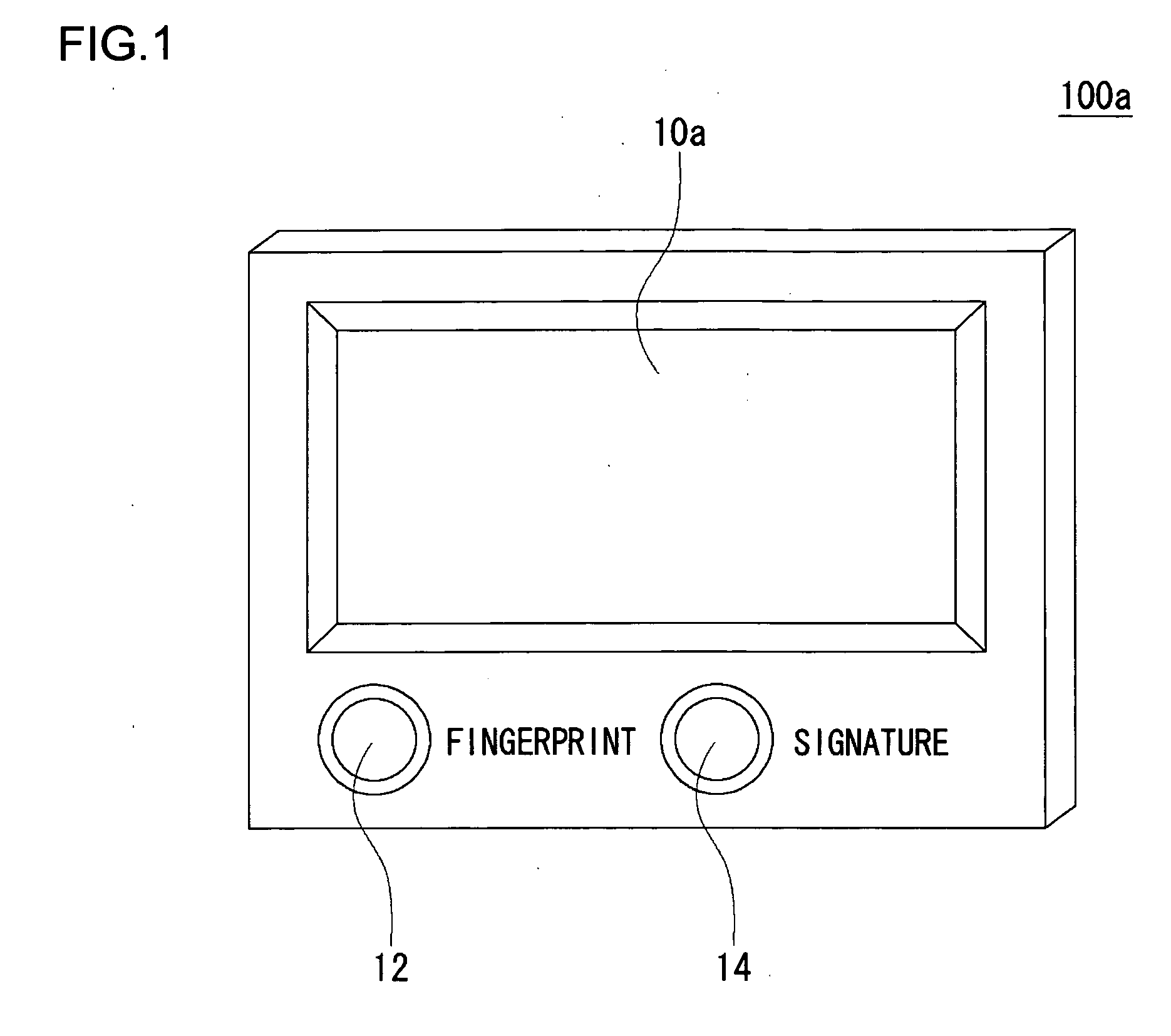
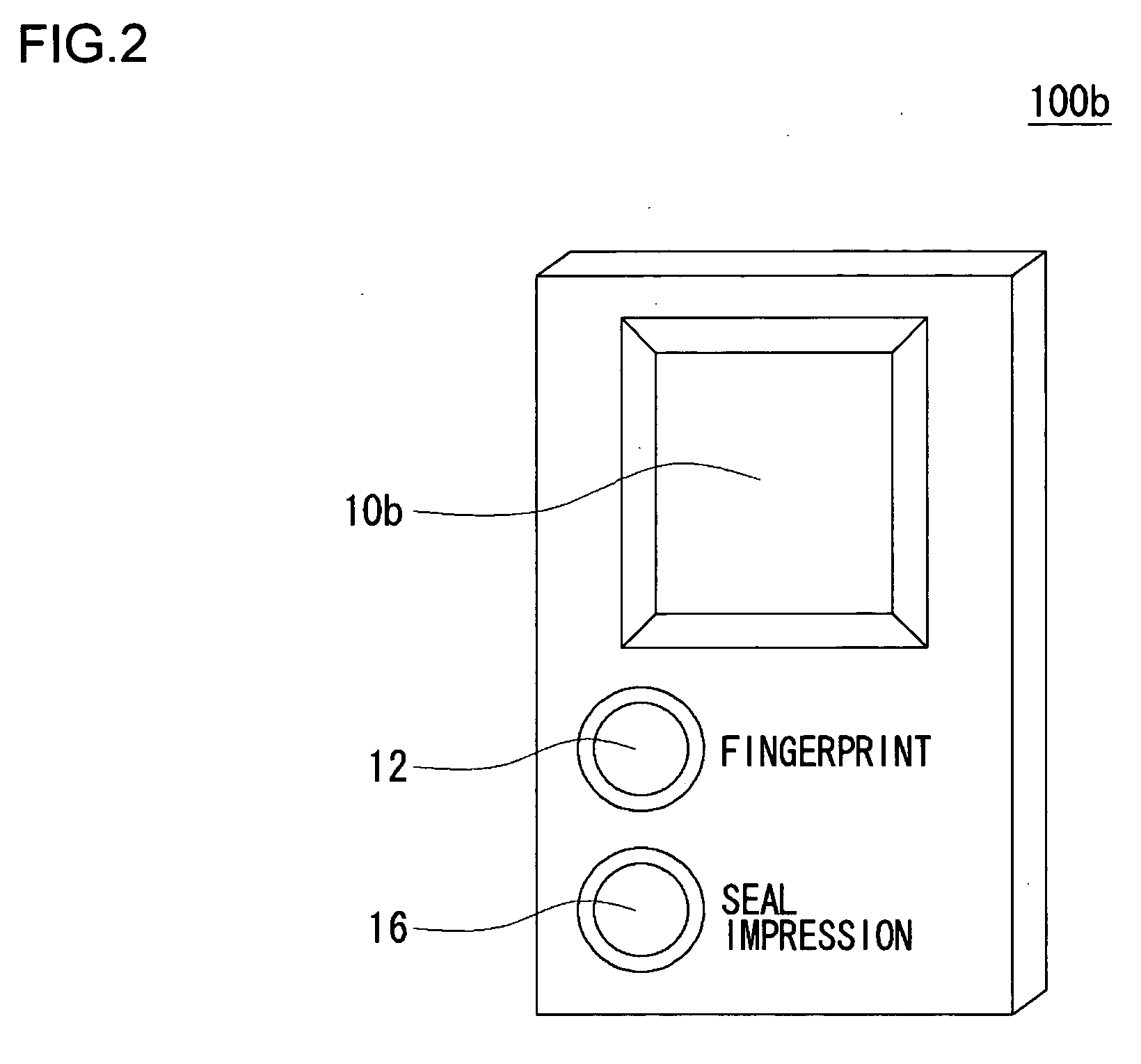
Authentication apparatus and authentication method
InactiveUS20050063567A1Combination structure is simpleReduce manufacturing costImage analysisUser identity/authority verificationUser inputFingerprint
In an authentication input apparatus, an input unit is a surface for inputting data of an input device such as a pressure sensitive sensor. The input device may also be an optical sensor such as a CCD. The input unit receives from a user input of a fingerprint, a signature or the like. In inputting the signature, the input unit functions as a tablet for inputting signatures utilizing a stylus equipment or the like. In inputting the fingerprint or the signature the user specifies the type of authentication information to be inputted by pressing a fingerprint selection button or a signature selection button. Fingerprint data are obtained by the input device when the user puts the finger on the input unit after pressing the fingerprint selection button. Signature data are obtained by the input device when the user signs on the input unit 10 after pressing the signature selection button.
Owner:SANYO ELECTRIC CO LTD
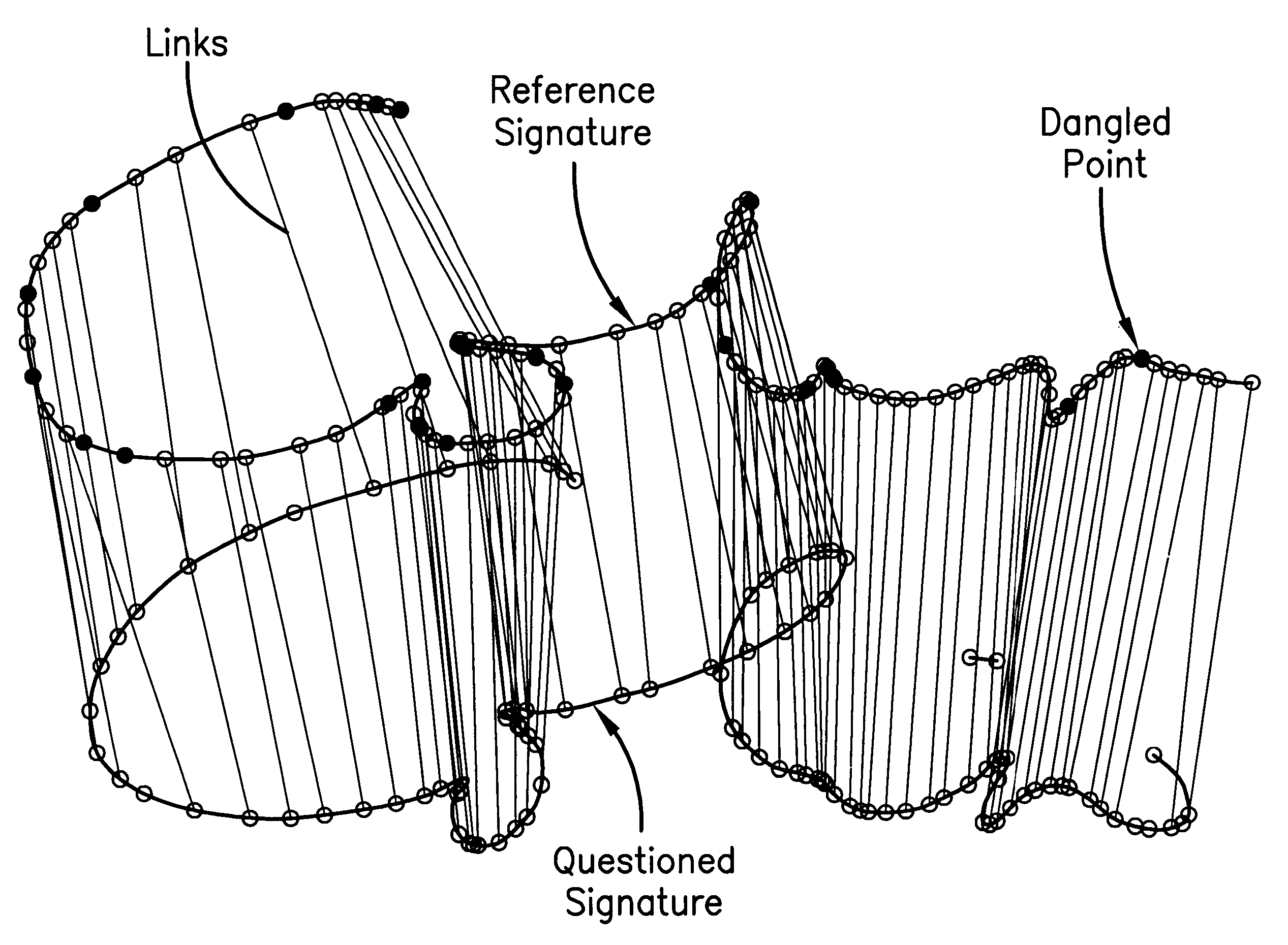
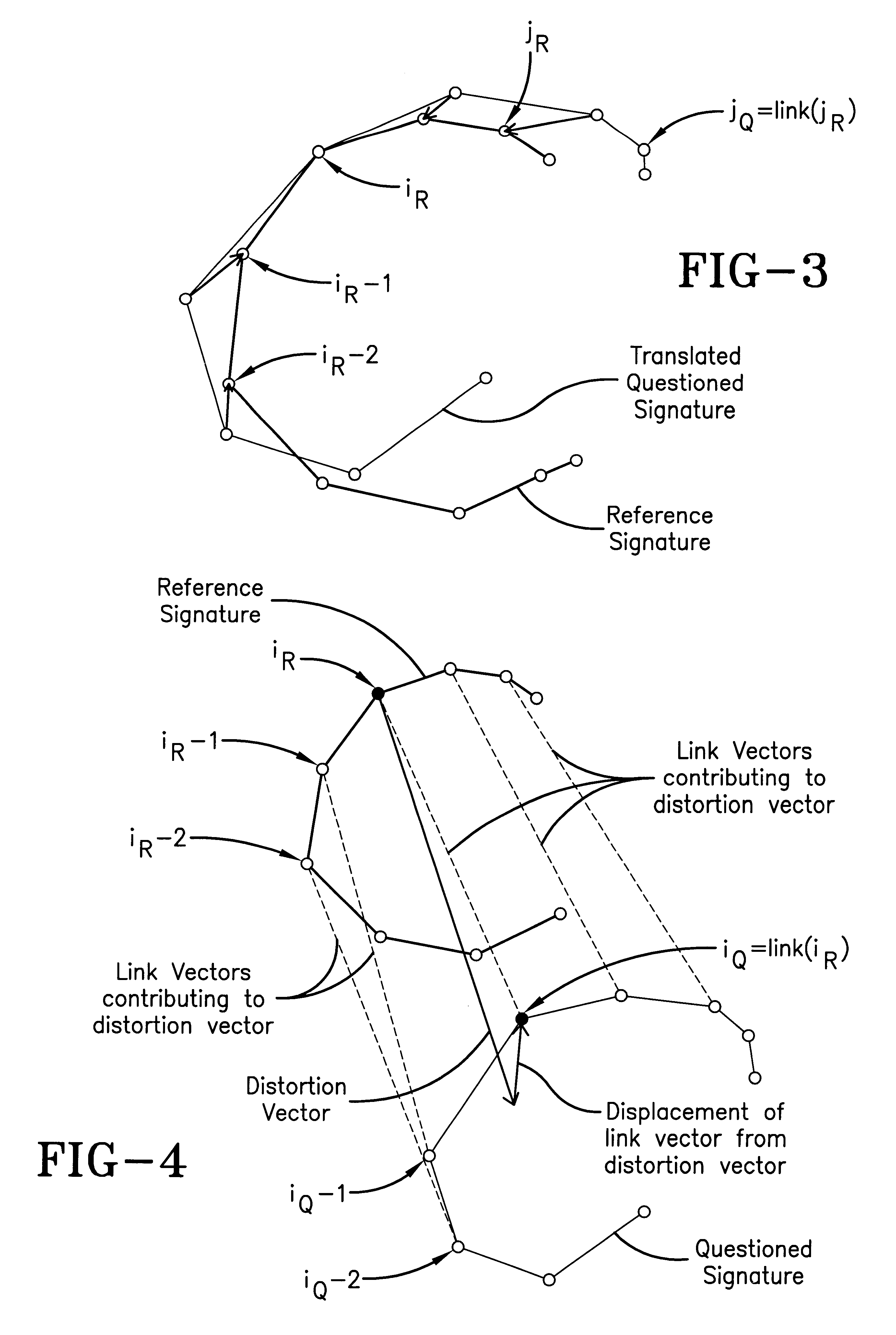
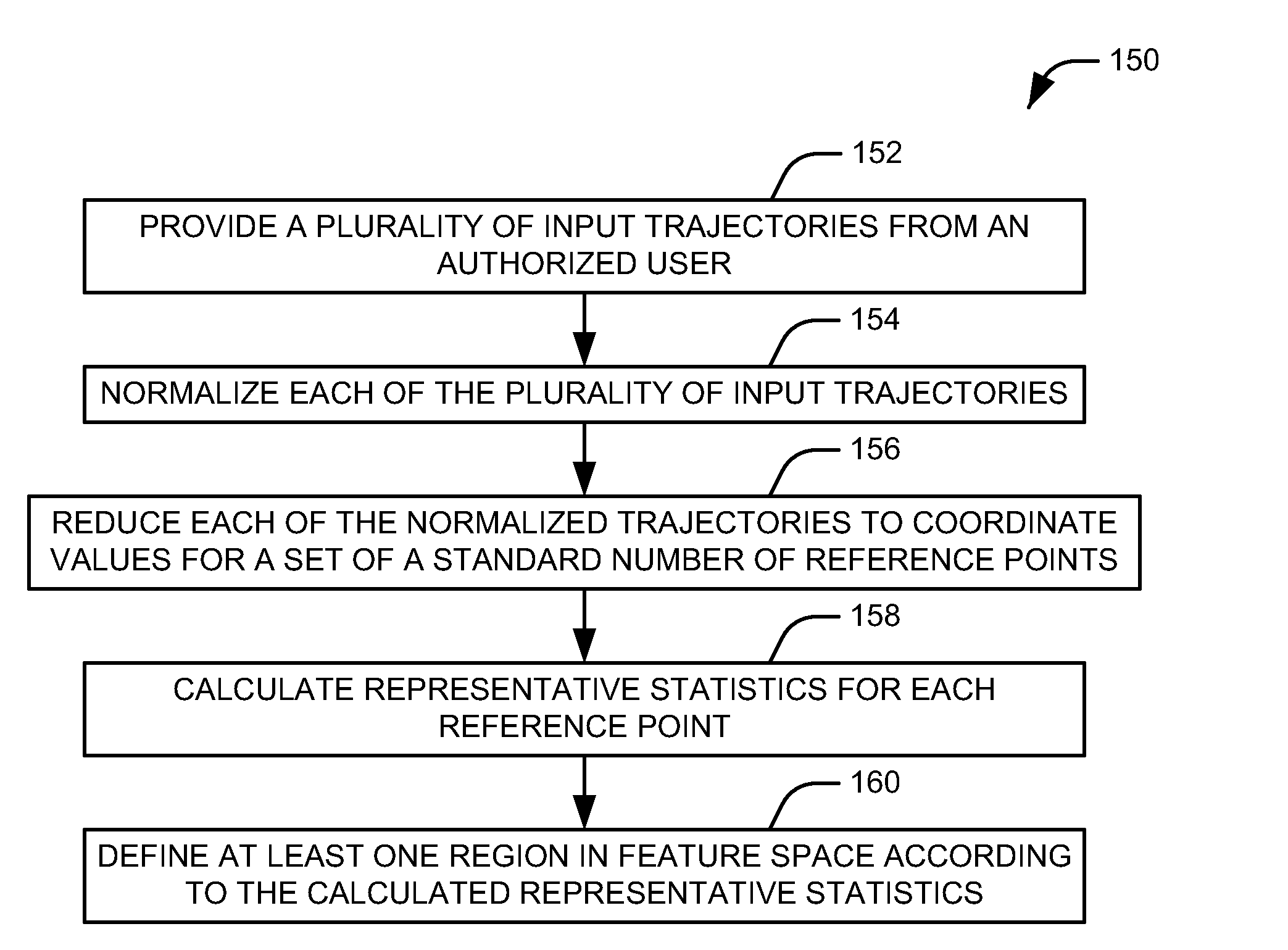
Signature matching
InactiveUS6487310B1Individual entry/exit registersSignature reading/verifyingSpatial correlationAlgorithm
The invention is of an "elastic matching" method for comparing one signature against another, comprising the operations of creating a mapping between corresponding points in two signatures to be compared measured at different times after the commencement of writing the signatures which maximizes the correlation between the local spatial neighborhood of the measured points and simultaneously minimizes the curvature of the elastic spatial distortion from the mapping, providing quantitative measures of both the degree of the spatial correlations and the degree of the non-uniform spatial distortions in the mapping, thereby providing measures of the similarity between the signatures.
Owner:PENOP
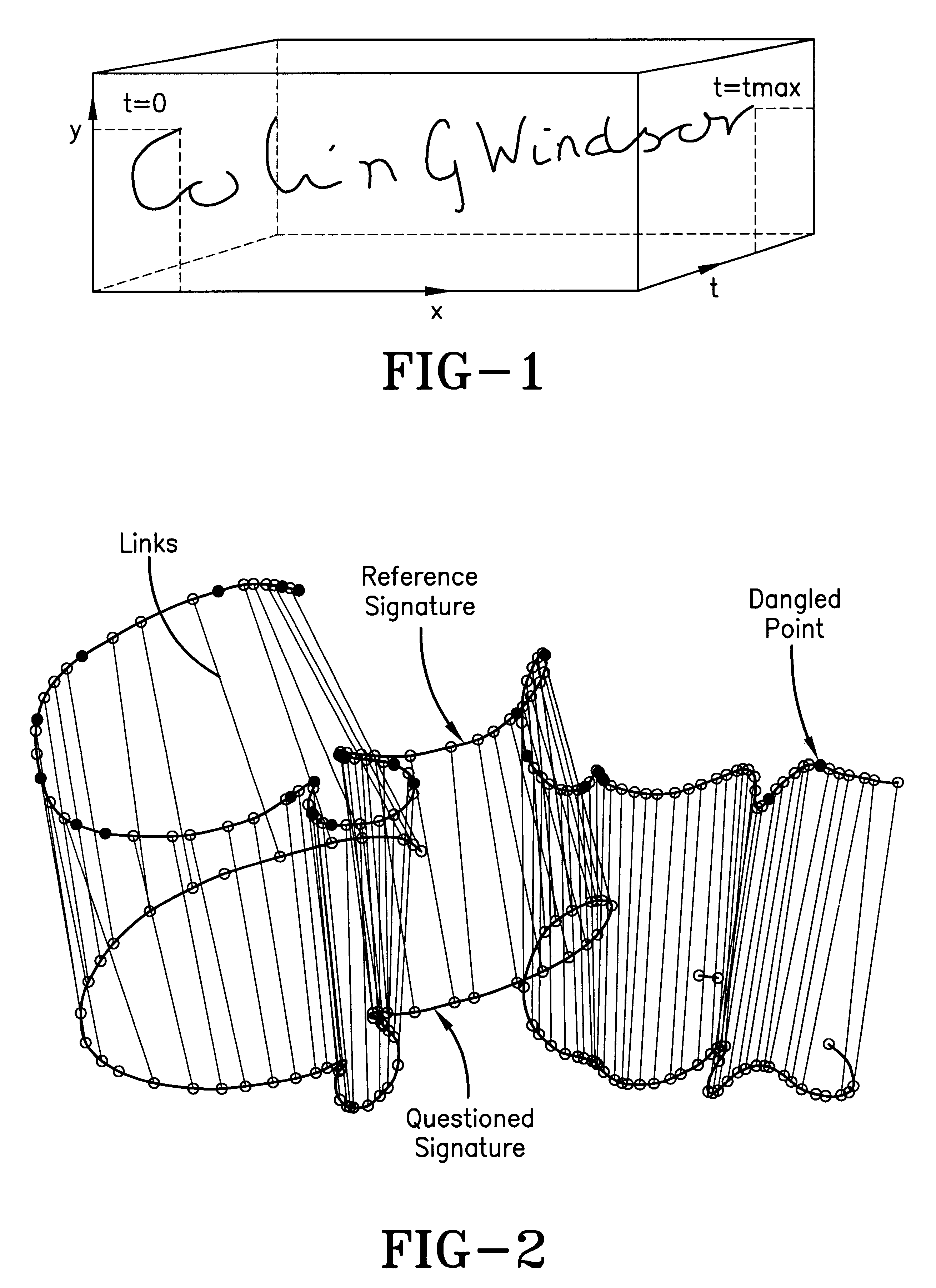
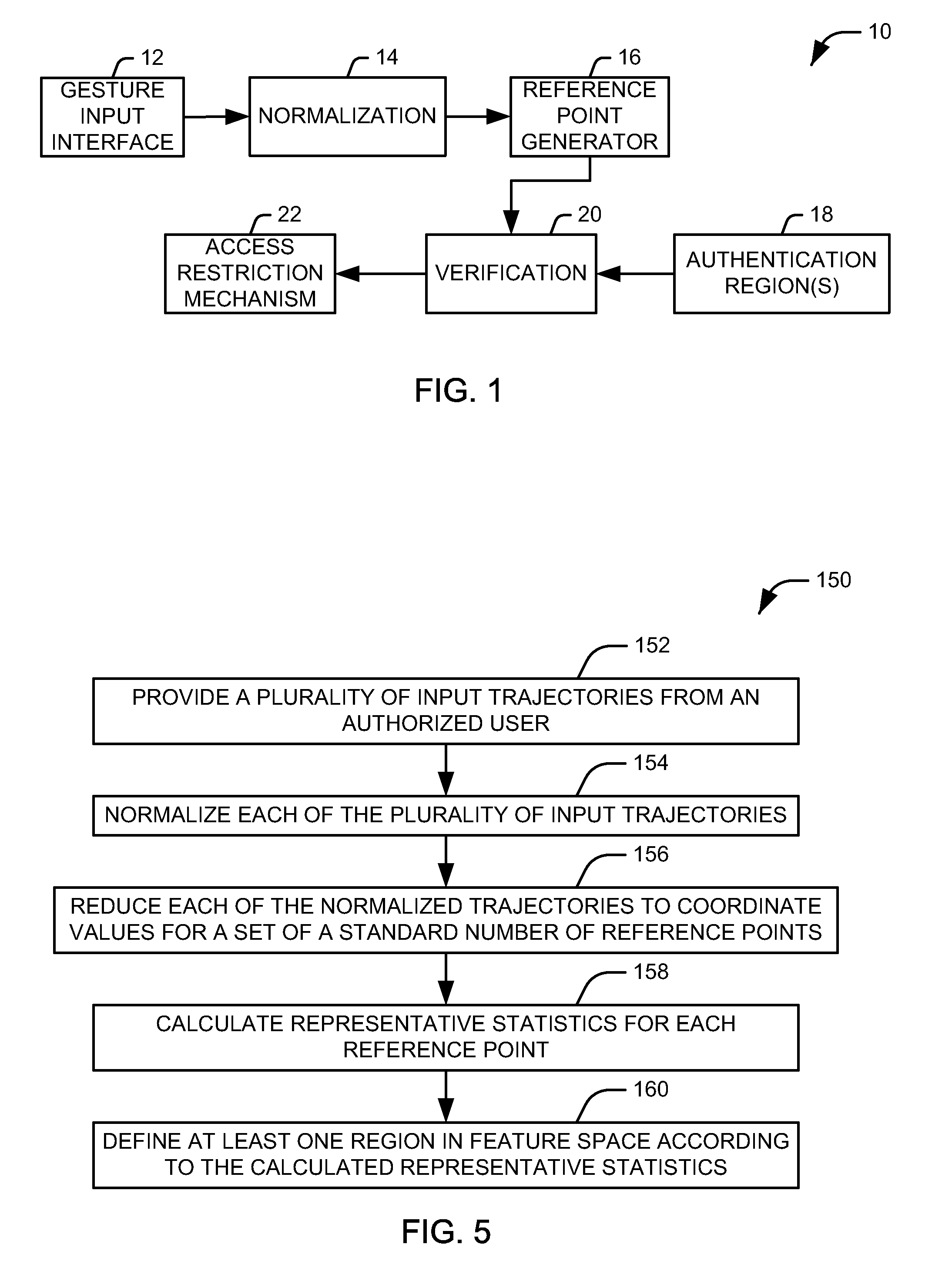
Security System Utilizing Gesture Recognition
ActiveUS20100052851A1Electric signal transmission systemsDigital data processing detailsComputer scienceSecurity system
Systems and methods are provided for restricting access to an item of interest. A normalization component resamples an input trajectory to produce a resampled trajectory having a standard size. A reference point generator reduces the resampled trajectory to respective values for a set of reference points, each having at least two associated coordinates. The system further includes at least one authentication region. Each of the at least one authentication region represents at least one of the set of reference points. A verification component is configured to determine if the values for the set of reference points from a given input falls within the at least one authentication region. An access restriction mechanism restricts access to the item of interest unless a threshold number of values for the set of reference points from the input falls within their associated authentication regions.
Owner:NORTHROP GRUMMAN SYST CORP
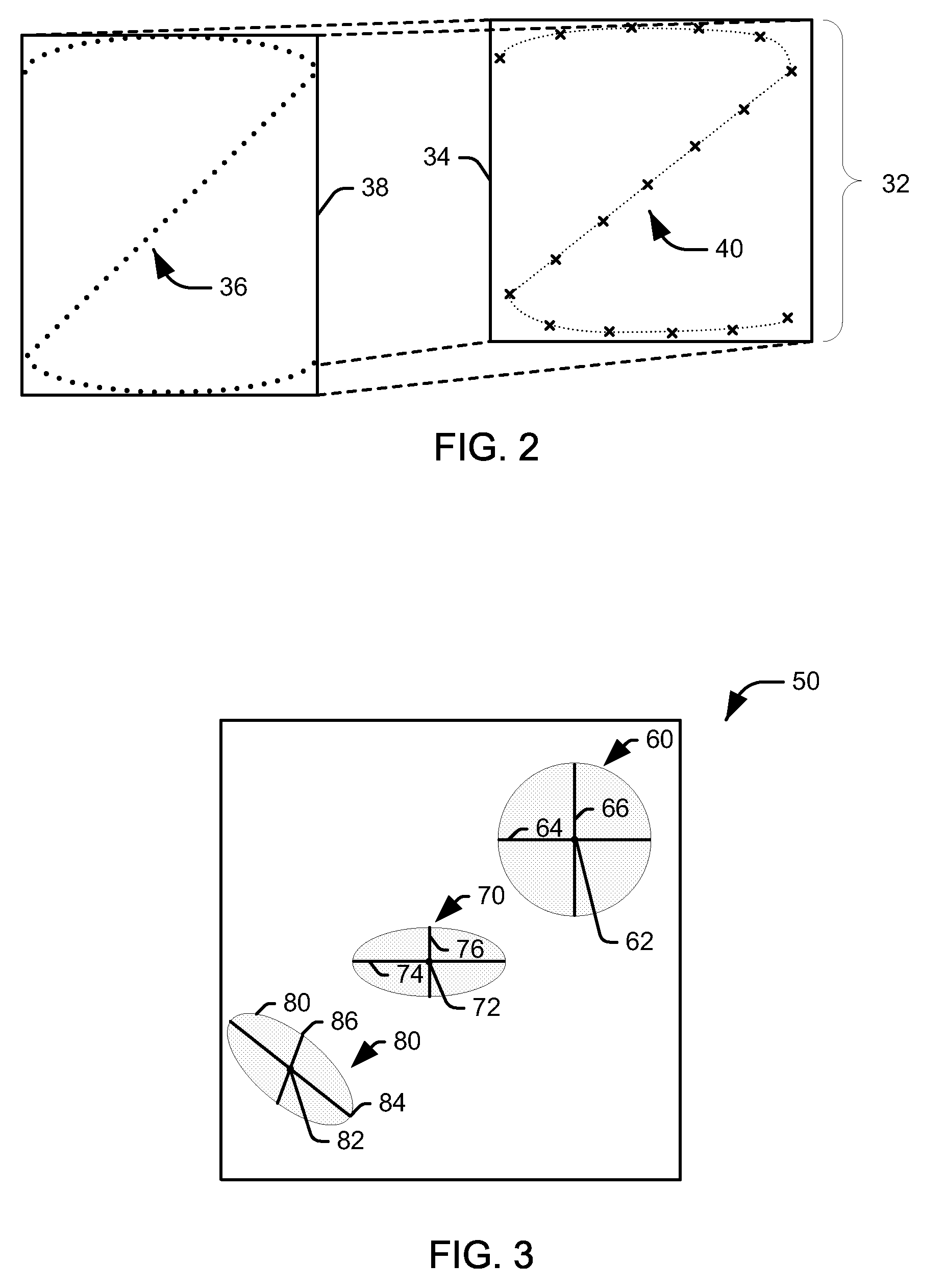
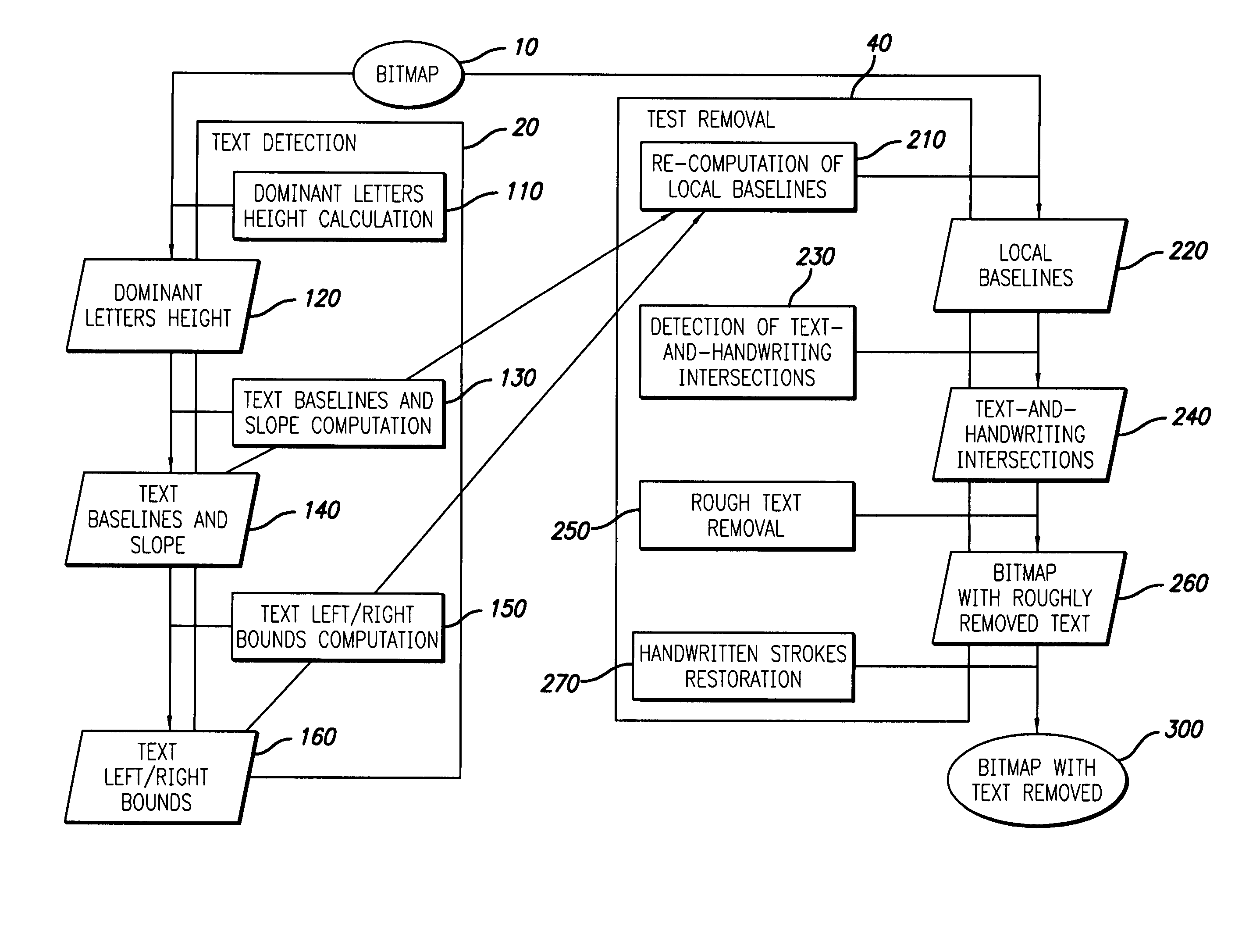
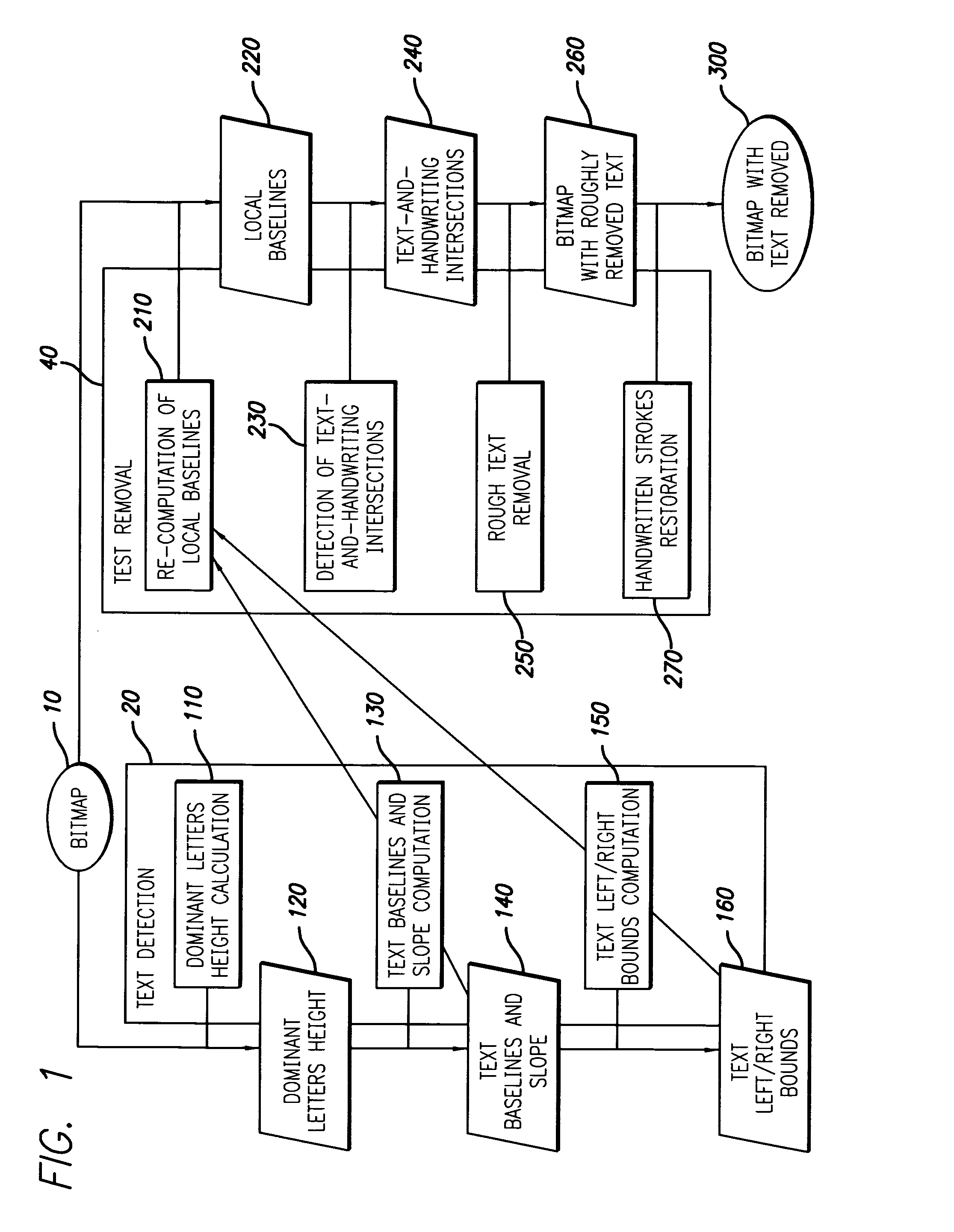
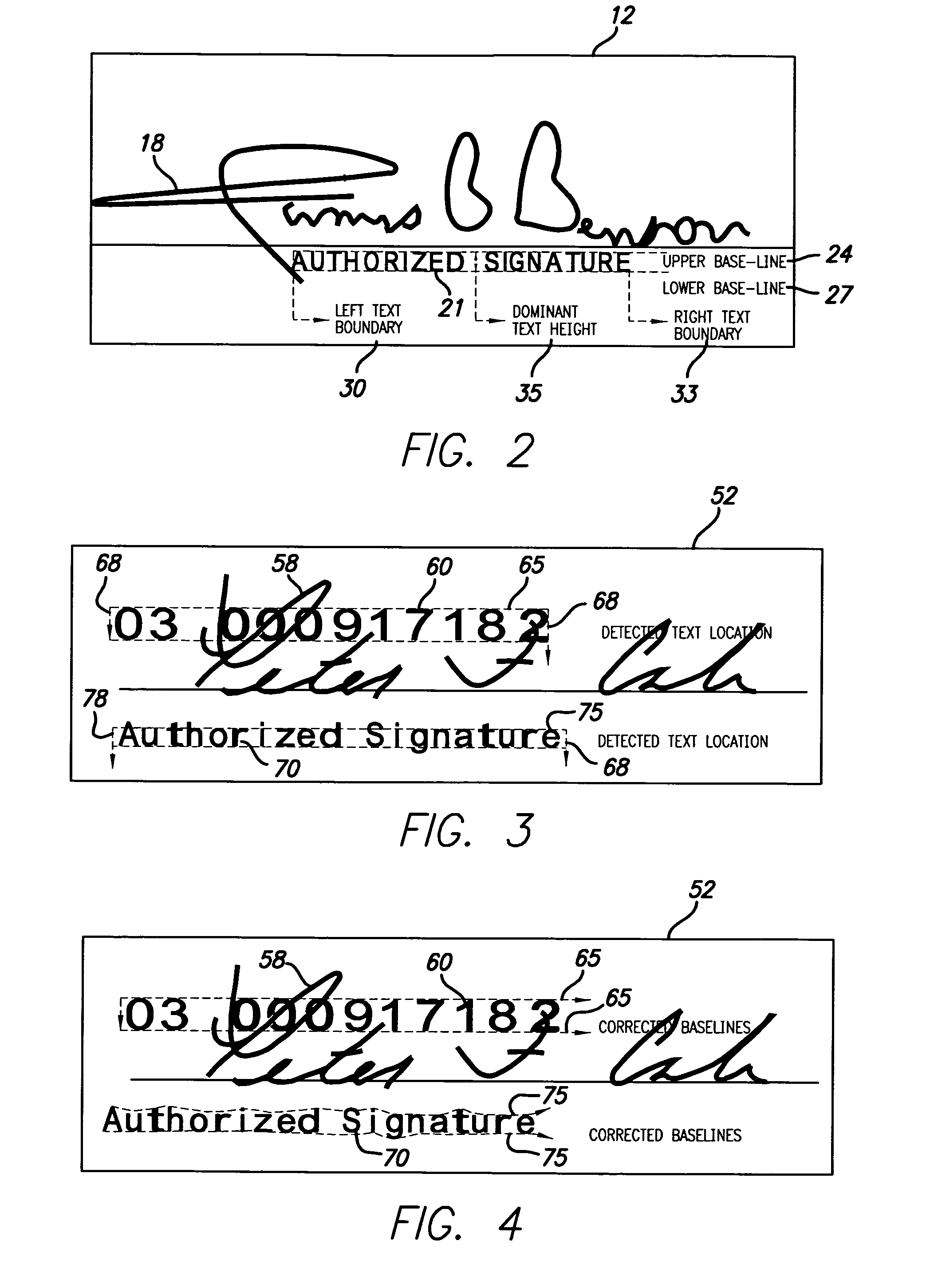
Method for automatic removal of text from a signature area
ActiveUS7657091B2Efficient separationComplete banking machinesFinanceDocument preparationDocumentation
The present invention provides a method for processing a document involving the automatic removal of text from a predetermined area of a document, the method comprising inputting a bitmap containing the predetermined area of the document from which the text will be removed wherein the predetermined area contains handwritten strokes, detecting the text, removing the text and any handwritten strokes that intersect with the text and outputting the bitmap with the text removed therefrom.
Owner:MITEK SYST
Creation of electronically processable signature files
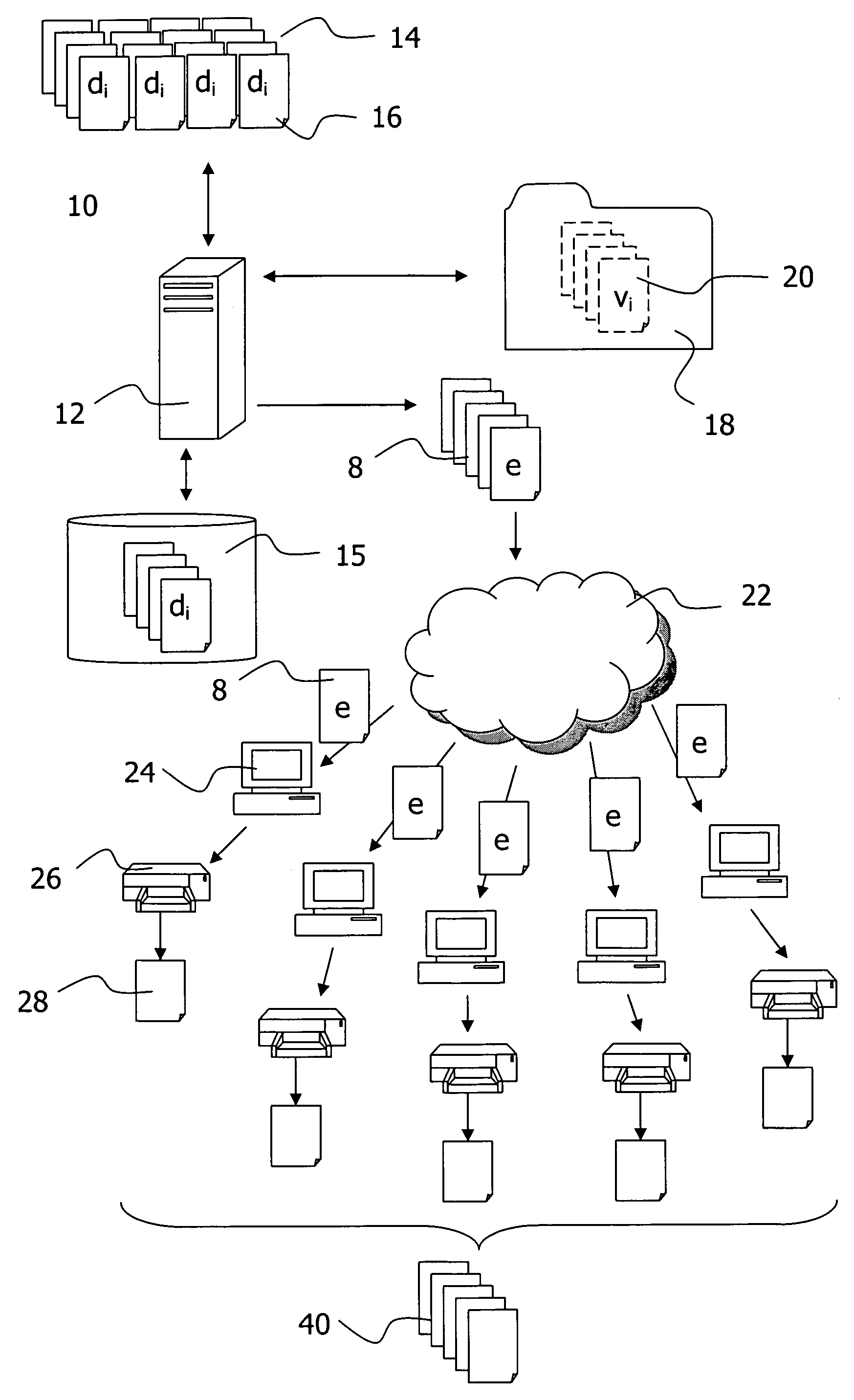
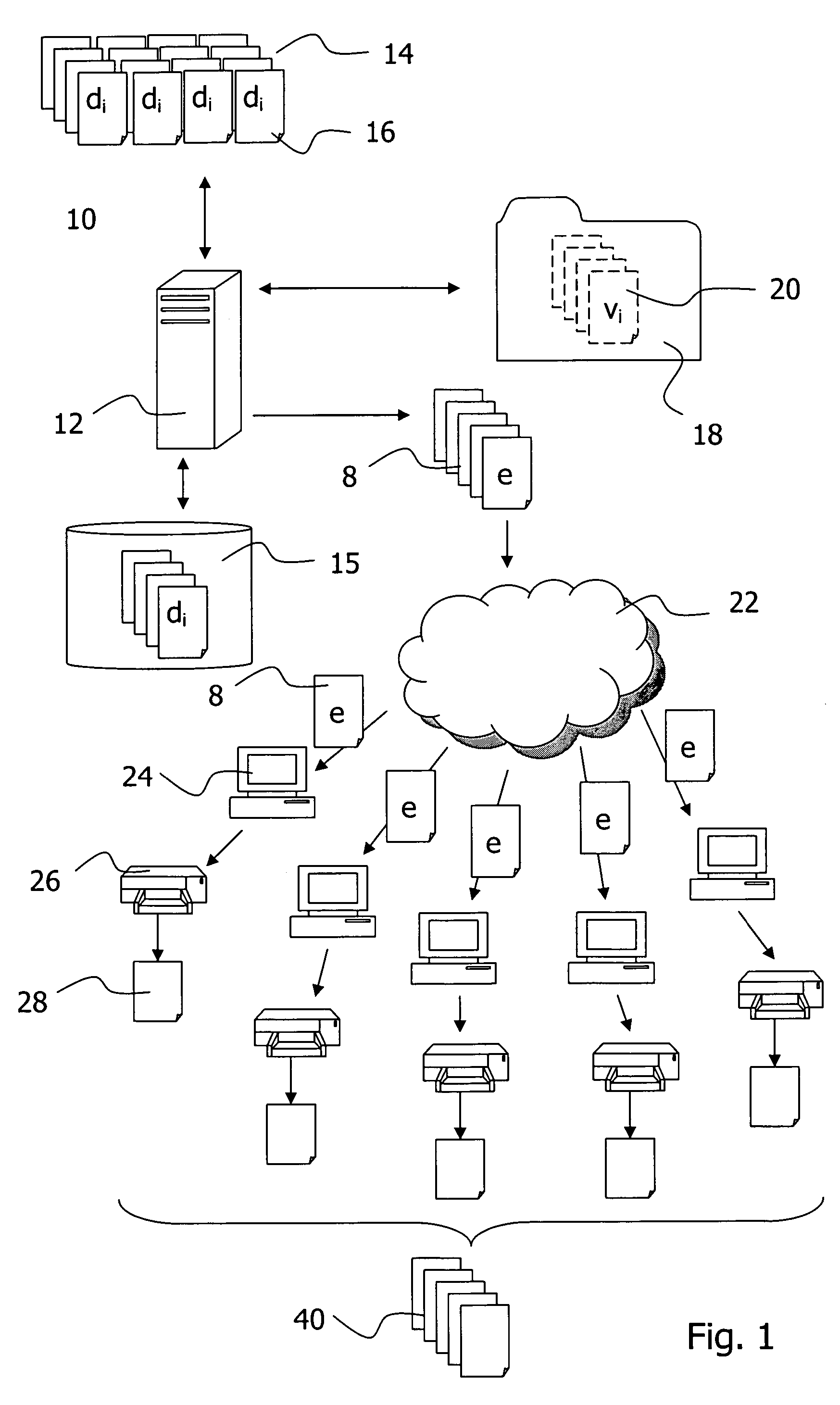
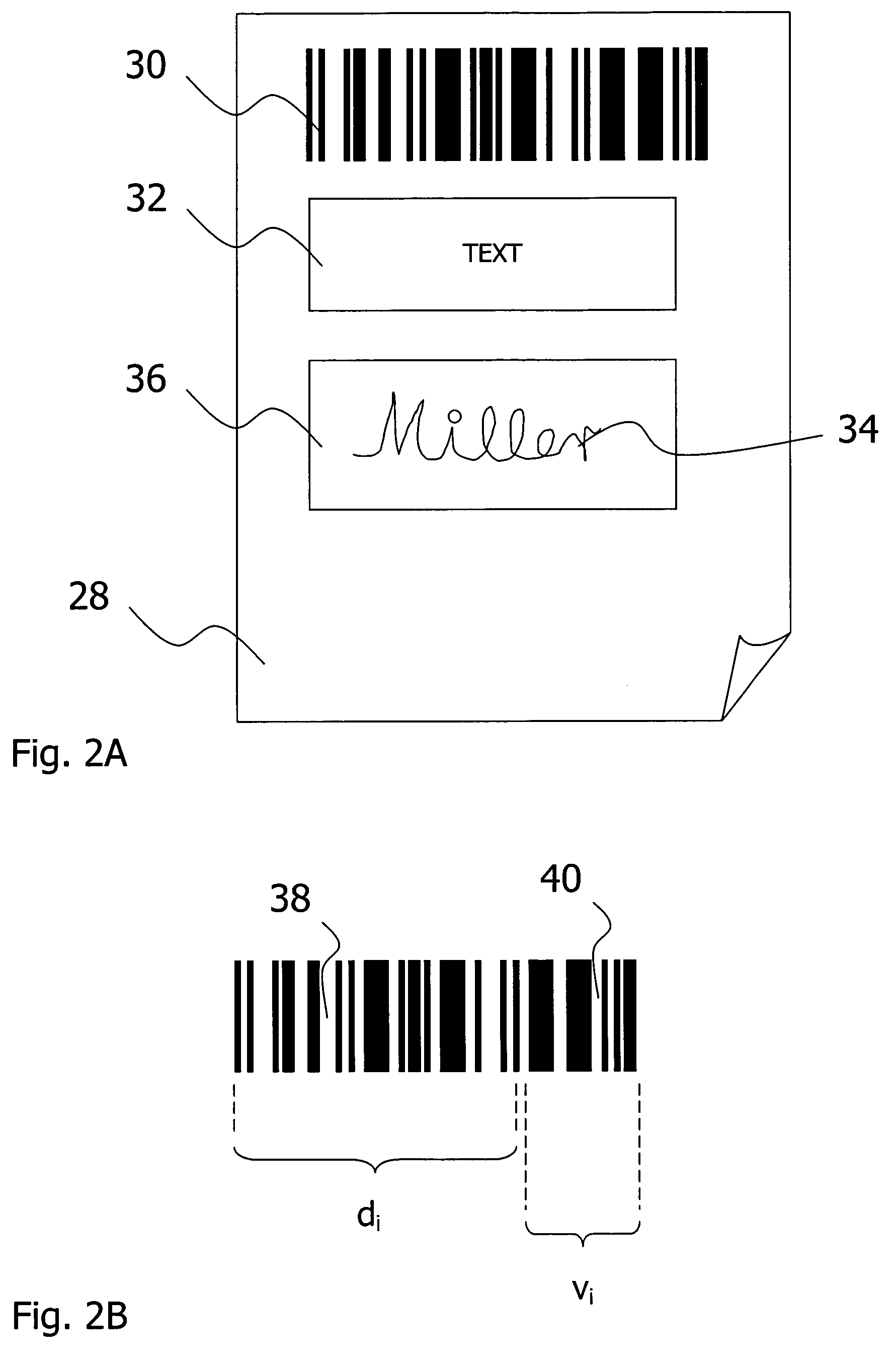
InactiveUS7685516B2Easy to operateTo offer comfortNatural language data processingSpecial data processing applicationsBatch processingSignature file
The invention relates to aspects in connection with the automatic generation and processing of signature files. The signature files are generated in paper form on the basis of documents (28) that comprise a personal signature (34) and also control information items (30) assigned to the signature (34) and / or the documents (28). The documents in paper form (28) are scanned in within the scope of a batch processing operation in order to generate signature files that contain the personal signatures (34) in an electronically processable form and also representations of the respectively assigned control information items (30). The control information items (30) contained in a signature file are identified and interpreted document-wise. Then the signature files are automatically processed as a function of the content of the assigned control information items (30).
Owner:UBS BUSINESS SOLUTIONS AG
Method for identity verification
InactiveUS7082213B2Processing speedMinimize privacy concernDigital data processing detailsChecking apparatusIndex fingerInternet privacy
The method for identity verification employs biometric technology. Positioned at the center of the system is a stylus with any of a number of biometric properties or their combination or with one or more metric sensors, while the customer uses the stylus to sign his / her name, or even for writing anything. The identity verification system is used at point-of-sale terminals, in various closed environments, to access a computer network, in applications involving pen-based computers and smart-pens, and for e-commerce. When fingerprint sensors are used, the sensors are positioned in the stylus grip, one sensor for the index finger, and a second sensor for the thumb. In one variation, one-to-one biometric matching is used. Each participant carries on his / her person a device that includes an encrypted biometric for reference purposes to gain access into the system. Processing is simplified since the system need only make a “MATCH” or “NO MATCH” decision. In a second variation that is particularly useful in closed environments, one-to-many biometric matching is used. During each event access request, the community of reference prints is searched for a match with the applicant. Each member of the community need carry nothing on his / her person to participate in the system. In either variation, the stylus is either attached to each site or is portable, one such stylus being carried by each participant.
Owner:UNITED STATES CP LLC
System and method for information management using handwritten identifiers
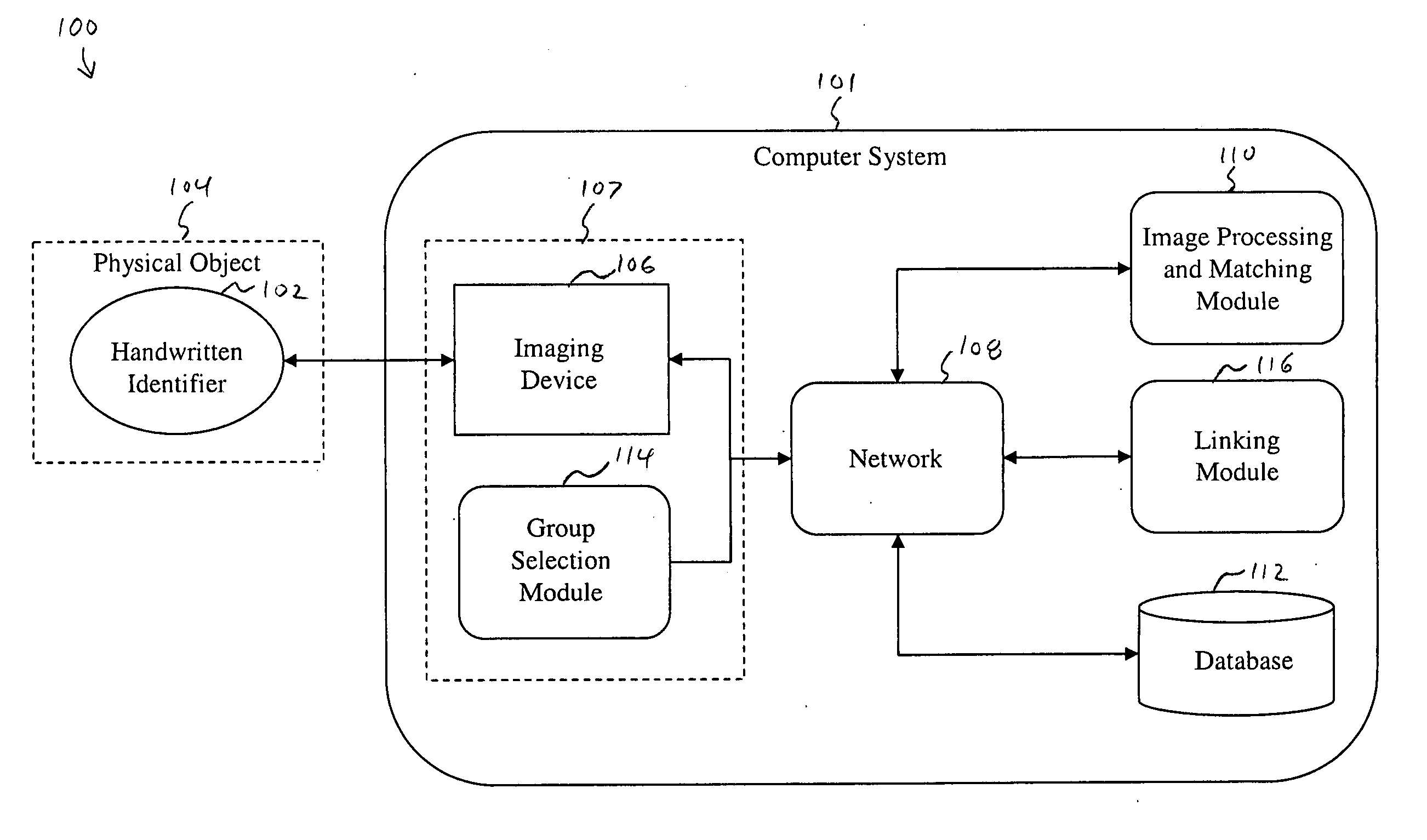
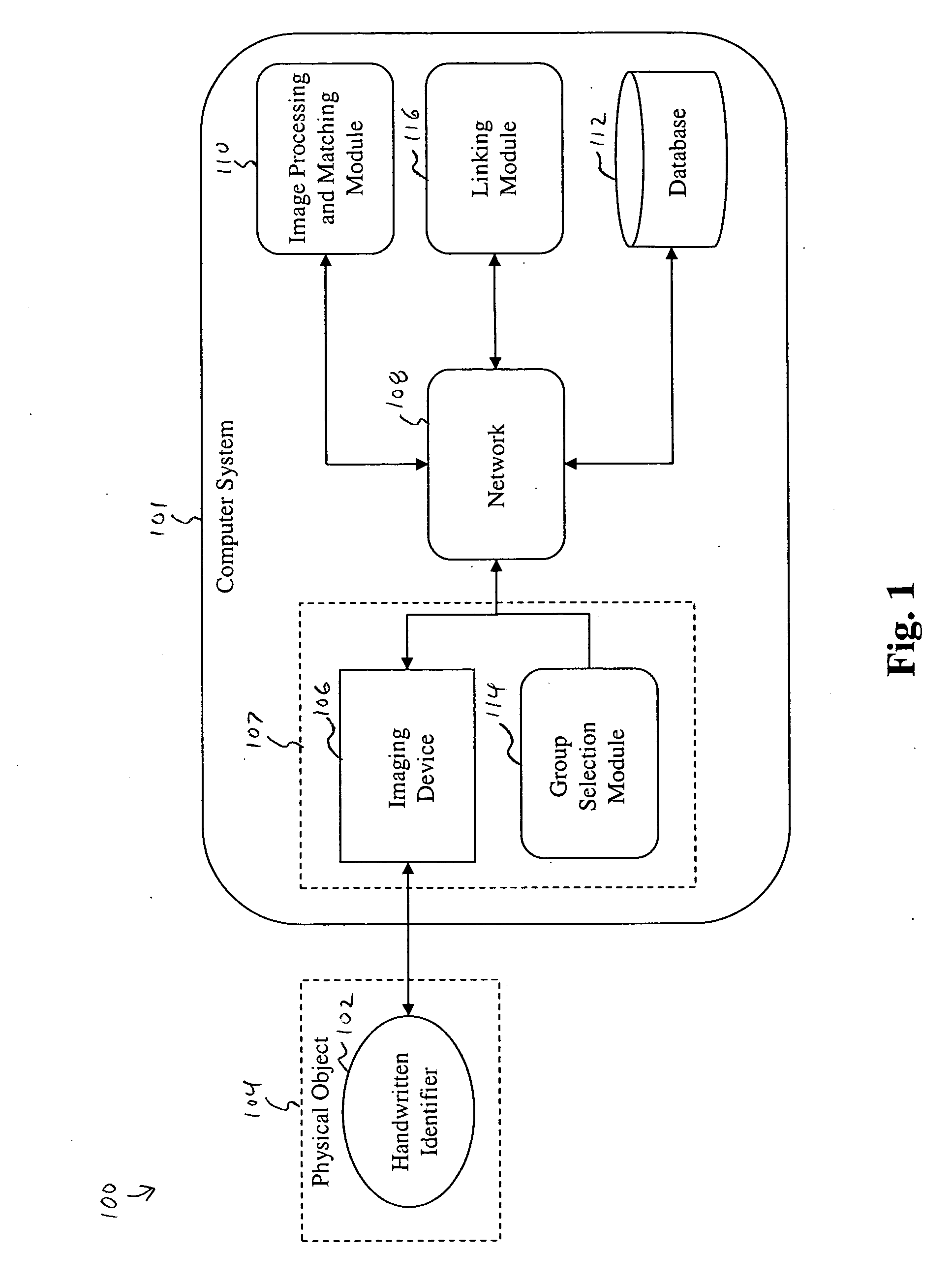
The method discloses: scanning an original copy of a handwritten identifier; comparing the identifier to a set of prerecorded identifiers; adding the identifier to the set of prerecorded identifiers, if the identifier shares less than a predetermined similarity with any identifier within the set of prerecorded identifiers; linking the identifier to a set of information; scanning the original copy a second time; matching the second scan of the original copy with the first scan of the original copy; and retrieving the set of information in response to the matching. The system discloses: a computer system; a handwritten identifier; an imaging device for scanning an original copy of a handwritten identifier; an image processing and matching module for comparing the identifier to a set of prerecorded identifiers; a linking module for linking the identifier to a set of information.
Owner:HEWLETT PACKARD DEV CO LP
Signature input apparatus and a signature verification system
InactiveUS6118889AImprove securityEasy to changeImage analysisTransmission systemsHandwritingVerification system
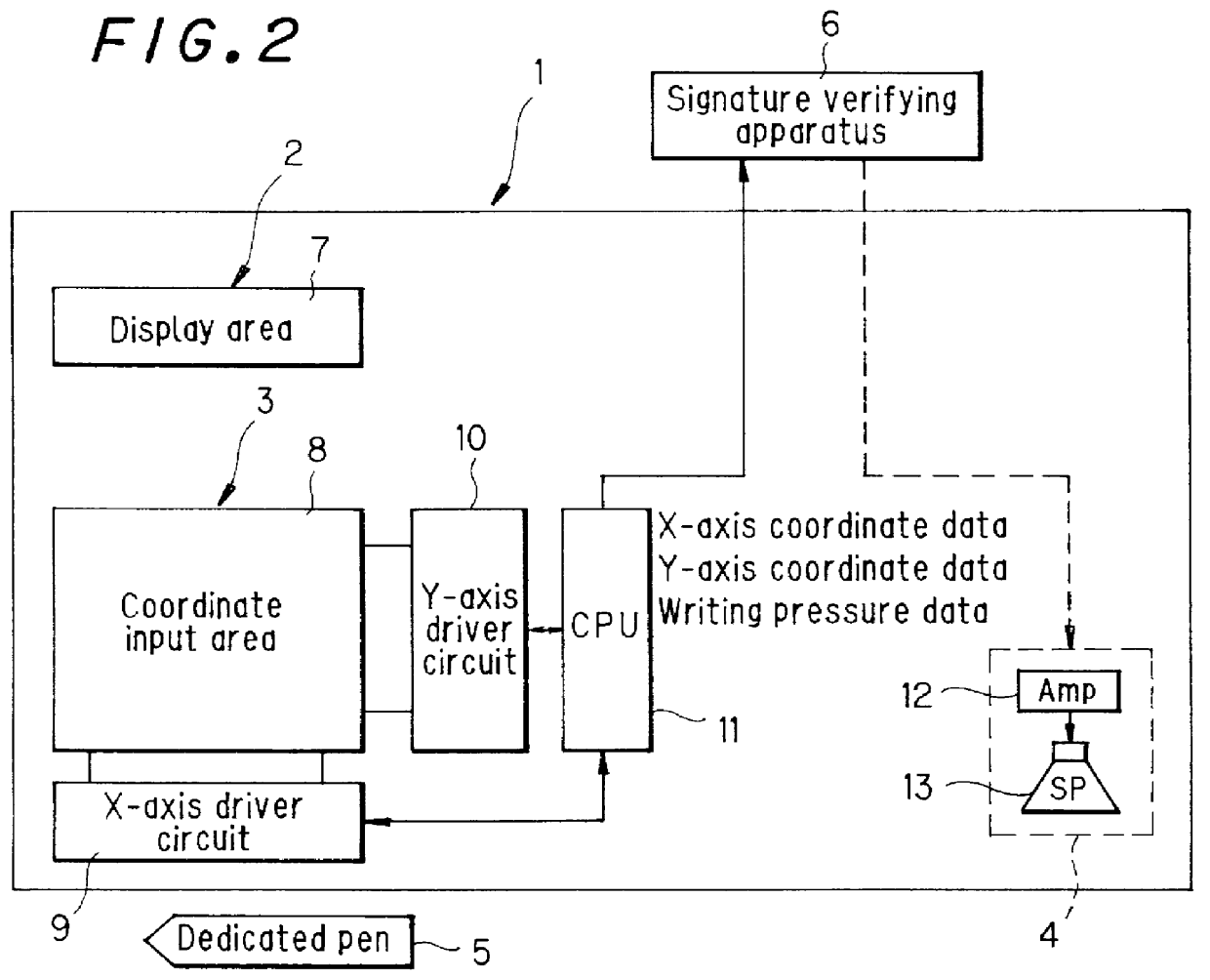
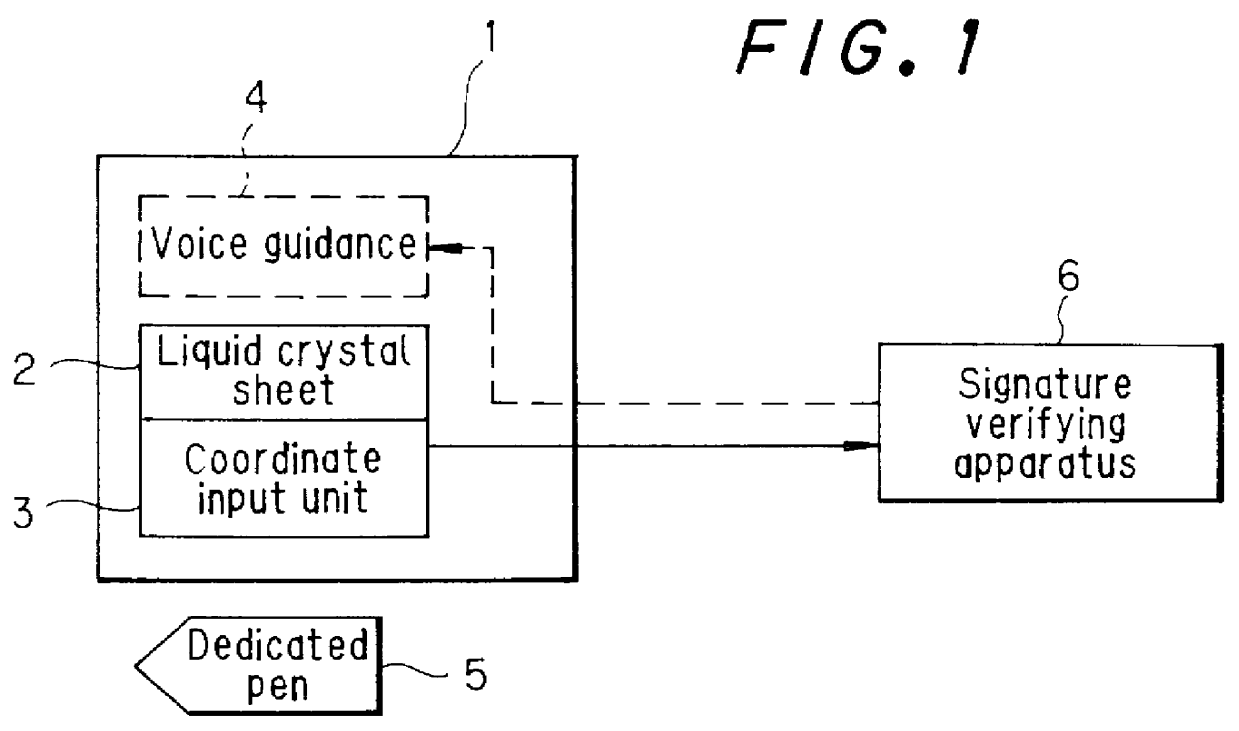
PCT No. PCT / JP97 / 02403 Sec. 371 Date Mar. 23, 1998 Sec. 102(e) Date Mar. 23, 1998 PCT Filed Jul. 10, 1997 PCT Pub. No. WO98 / 05001 PCT Pub. Date Feb. 5, 1998The object is to improve the accuracy of signature input and signature verification and improve security by causing the handwriting of a signature to disappear by itself. The signature verification system includes a signature input apparatus 1 and a signature verifying apparatus 6. Signature input apparatus 1 has an externally charged type liquid crystal sheet 2 which has an underside being adhesive and is placed on a coordinate input unit 3. When a dedicated pen 5 having the function of applying static charge onto this liquid crystal sheet 2 is used to write a signature, the handwriting of the signature is liquid crystal representation on the display area of liquid crystal sheet 2 and this handwriting of the signature will disappear by itself after a predetermined period of time. Further, signature verifying apparatus 6 reads the handwriting coordinate information of a signature output from coordinate input unit 3 for detecting the handwriting coordinate information of a signature and verifies this handwriting coordinate information with the handwriting coordinate information of signatures which have been registered beforehand.
Owner:PILOT PEN CO LTD
Method for applying a signature simplicity analysis for improving the accuracy of signature validation
Owner:MITEK SYST
Methods of processing a check in an automatic signature verification system
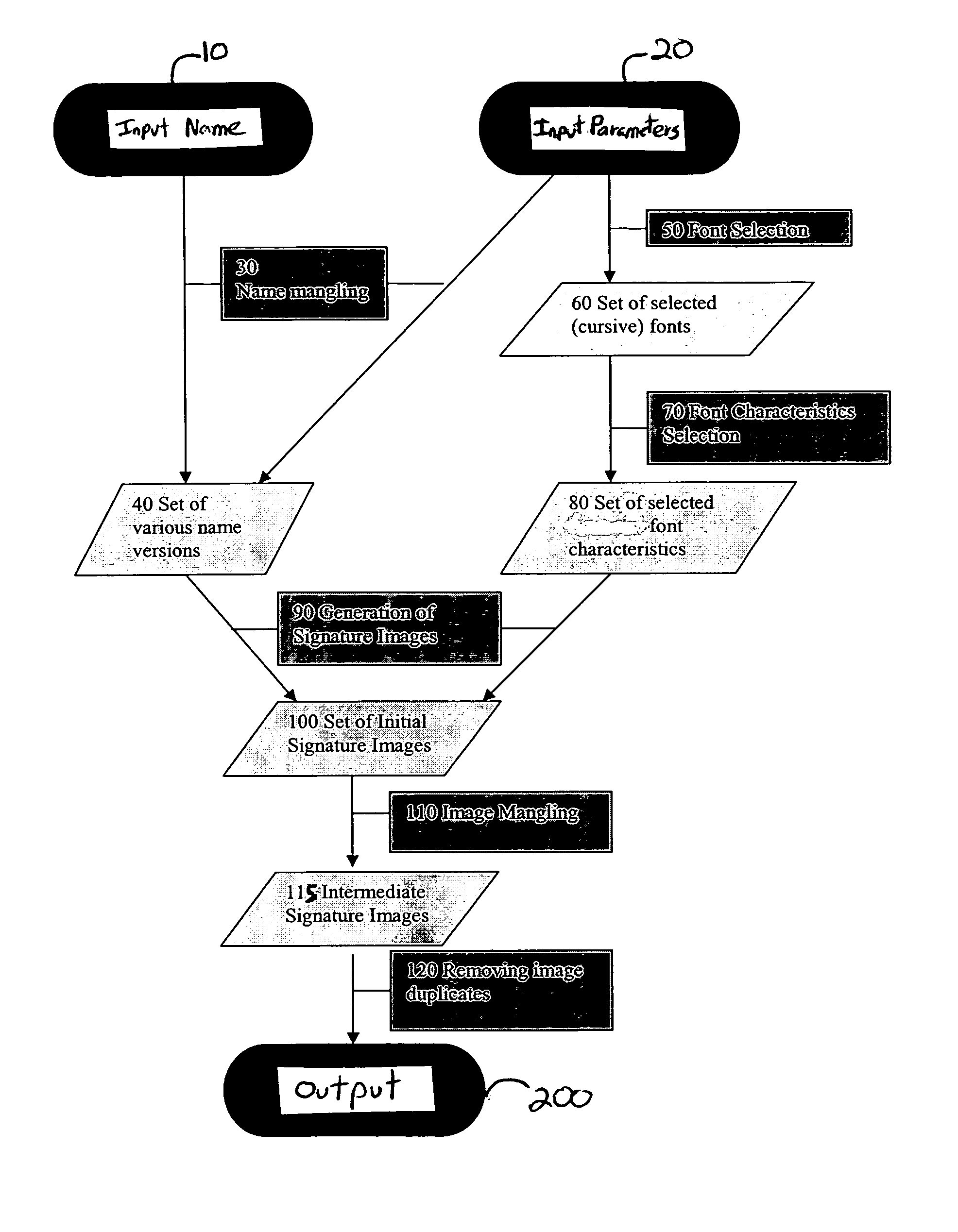
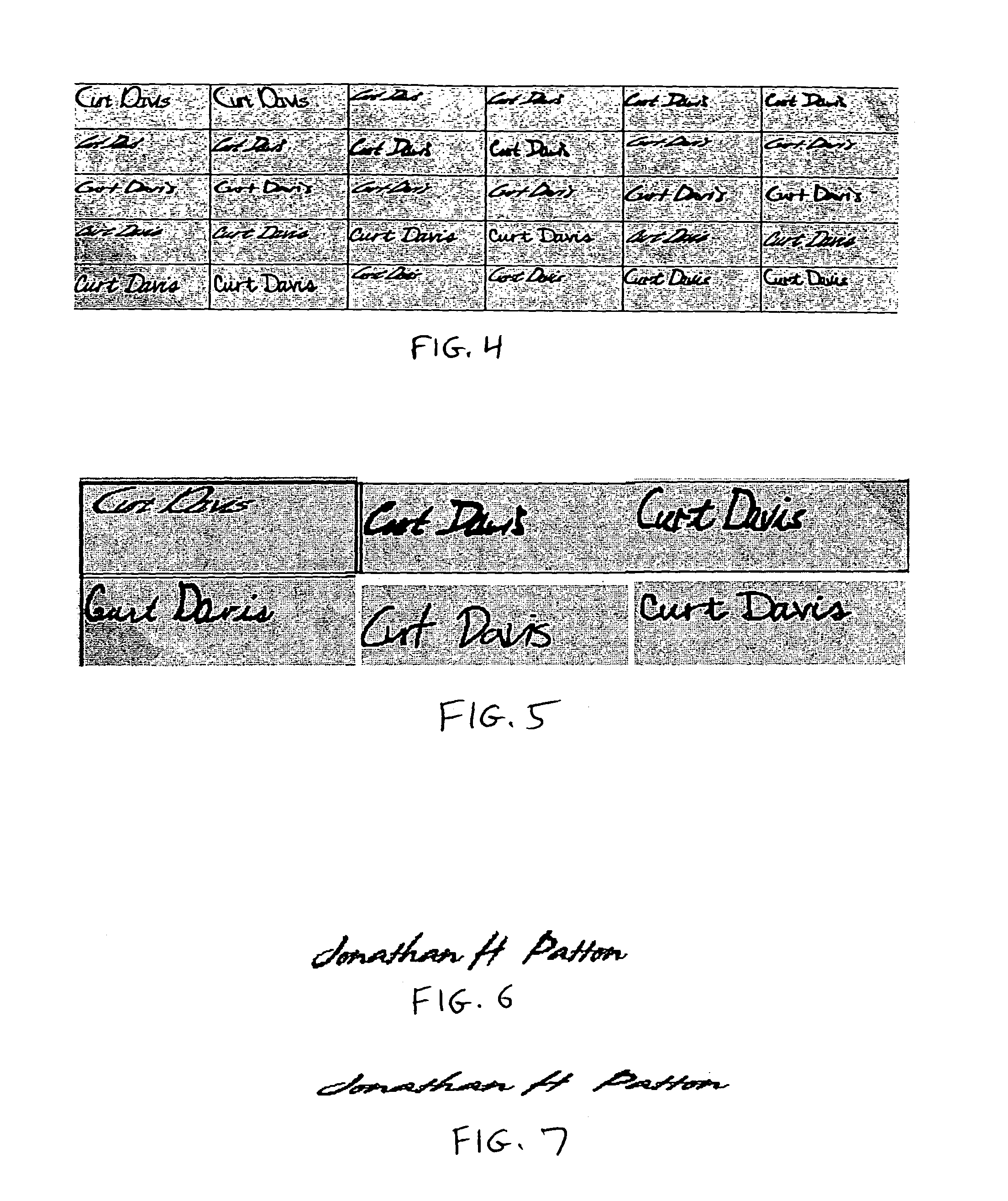
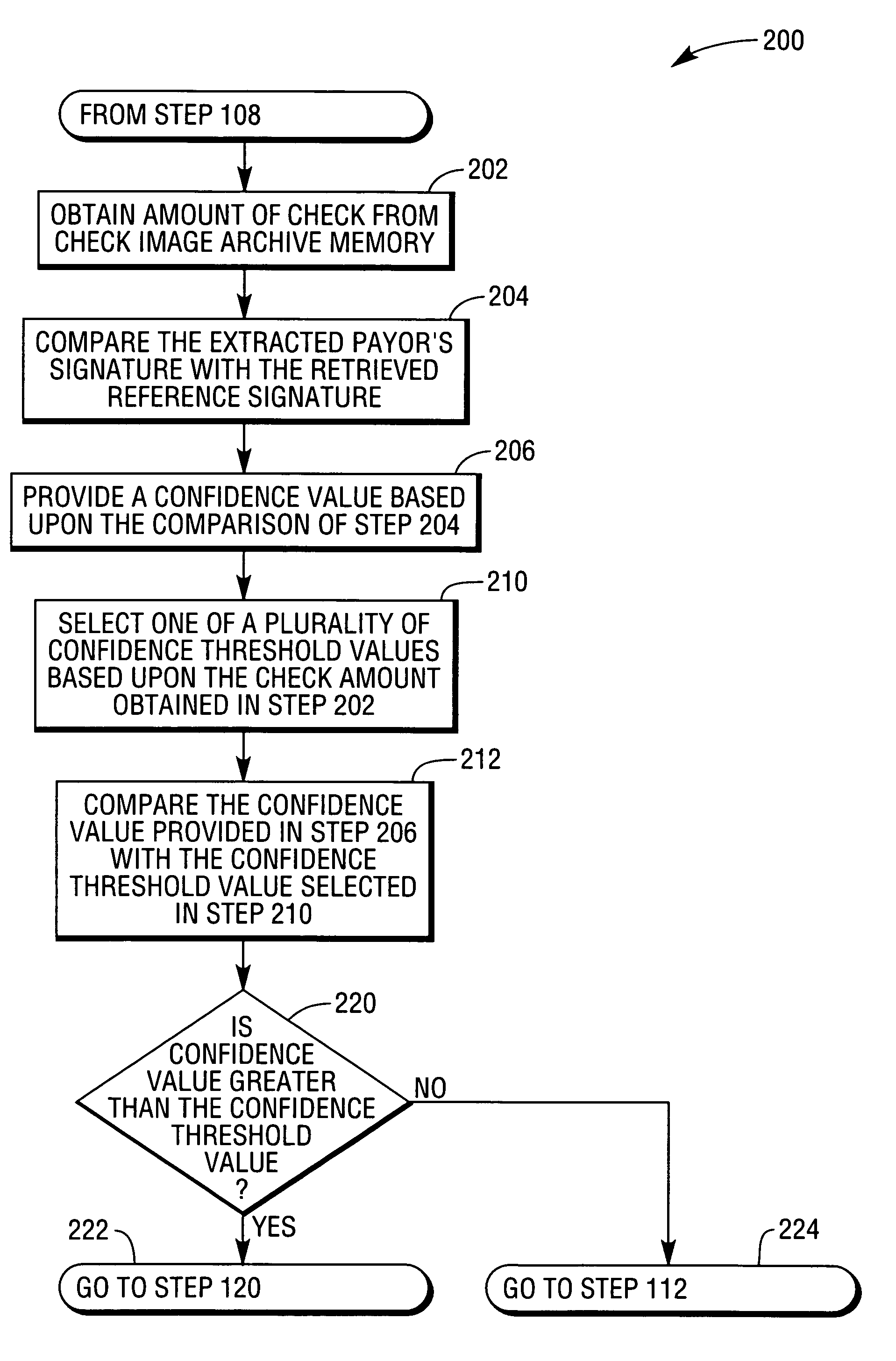
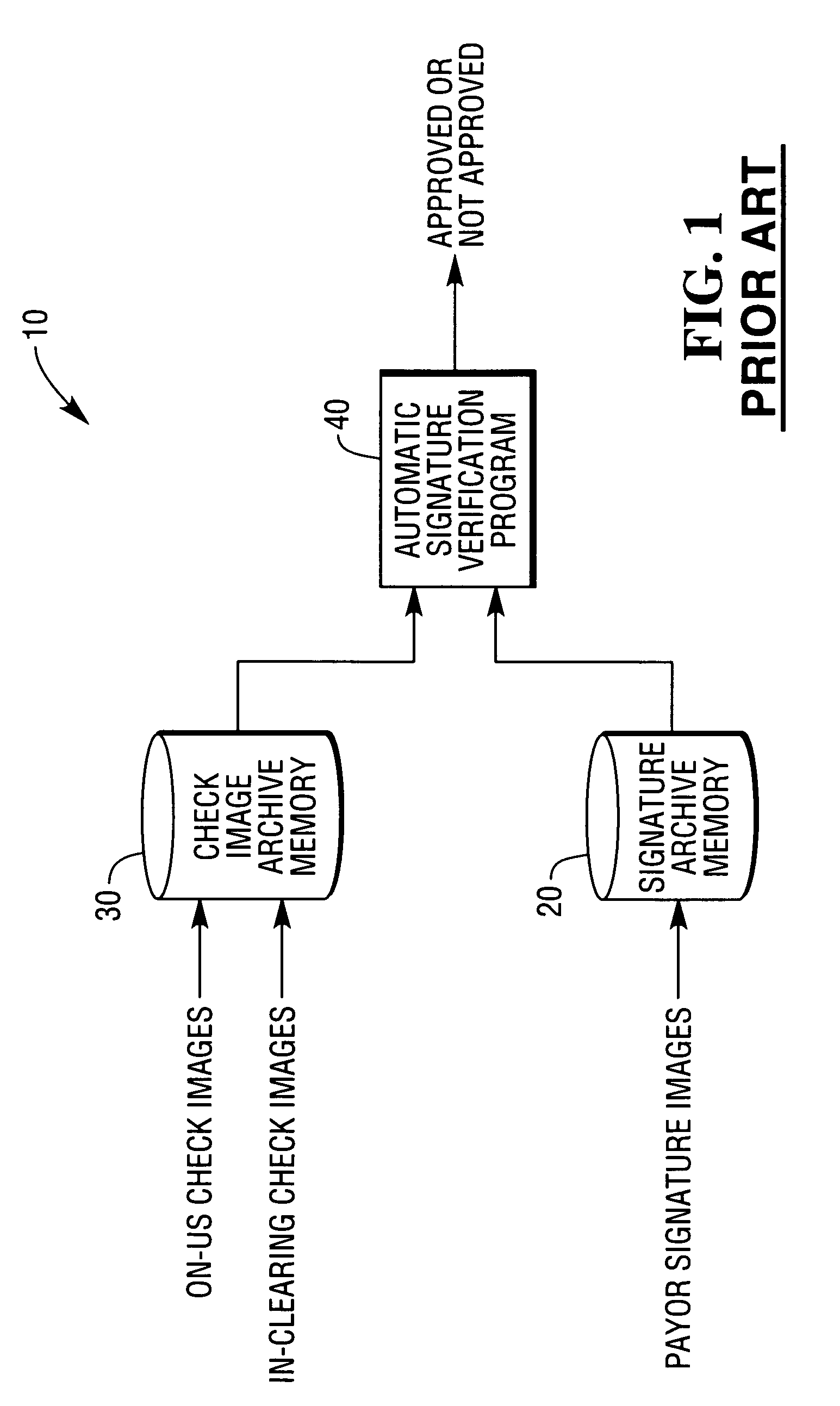
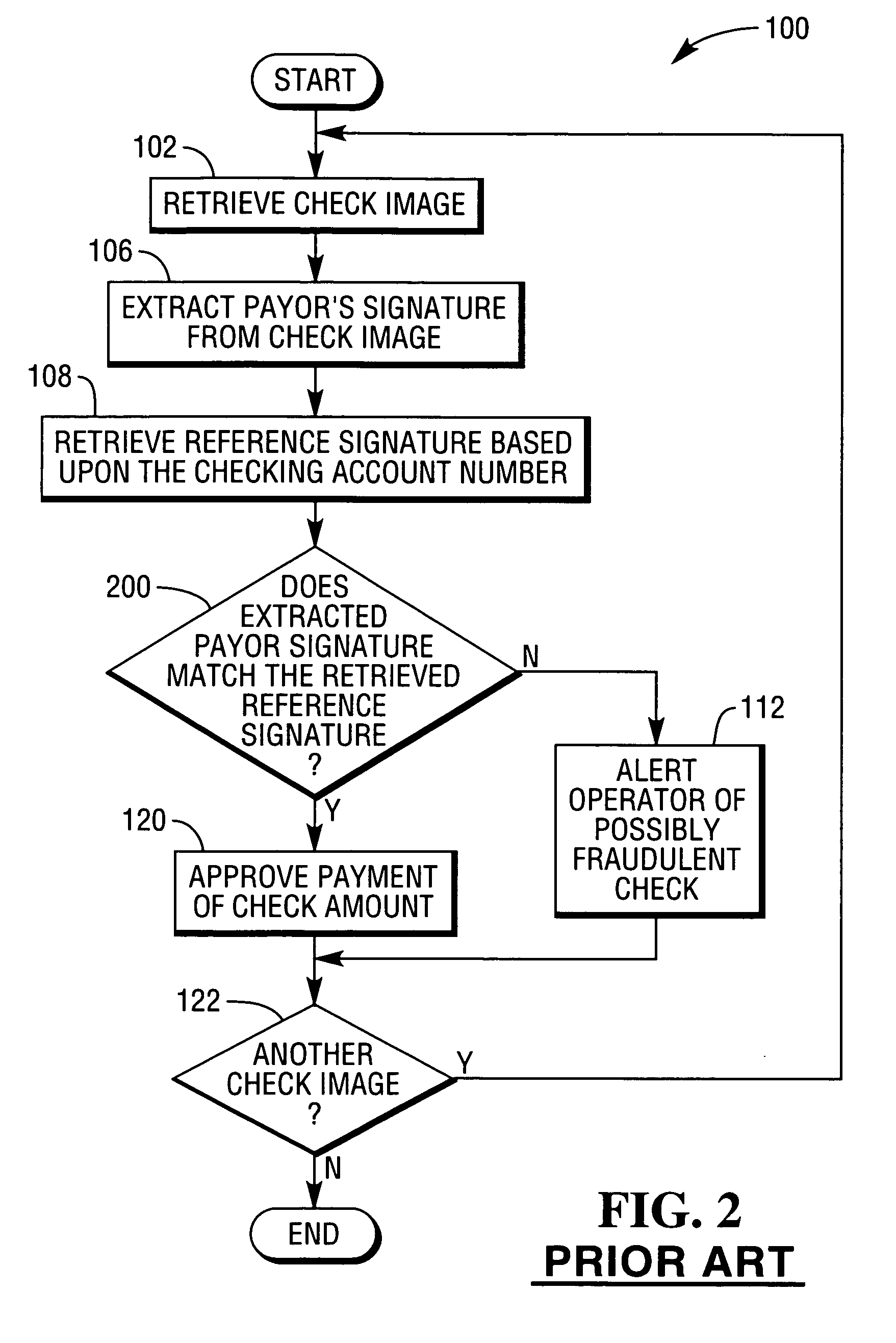
A method is provided of a bank processing a check in an automatic signature verification system. The method comprises receiving a check image having a payor's signature, extracting the payor's signature from the check image, comparing the extracted payor's signature with a reference signature, providing a confidence value based upon the comparison of the extracted payor's signature with the reference signature, selecting one of a plurality of confidence threshold values based upon amount of the check, and comparing the confidence value with the selected confidence threshold value to determine if payment of the check amount is approved.
Owner:NCR CORP
Method for identity verification
InactiveUS7609862B2Processing speedMinimize privacy concernHardware monitoringComputer security arrangementsInternet privacyIndex finger
The method for identity verification employs biometric technology. Positioned at the center of the system is a stylus with any of a number of biometric properties or their combination or with one or more metric sensors, while the customer uses the stylus to sign his / her name, or even for writing anything. The identity verification system is used at point-of-sale terminals, in various closed environments, to access a computer network, in applications involving pen-based computers and smart-pens, and for e-commerce. When fingerprint sensors are used, the sensors are positioned in the stylus grip, one sensor for the index finger, and a second sensor for the thumb. In one variation, one-to-one biometric matching is used. Each participant carries on his / her person a device that includes an encrypted biometric for reference purposes to gain access Into the system. Processing is simplified since the system need only make a “MATCH” or “NO MATCH” decision. In a second variation that is particularly useful in closed environments, one-to-many biometric matching is used. During each event access request, the community of reference prints is searched for a match with the applicant. Each member of the community need carry nothing on his / her person to participate in the system. In either variation, the stylus is either attached to each site or is portable, one such stylus being carried by each participant.
Owner:UNITED STATES CP LLC
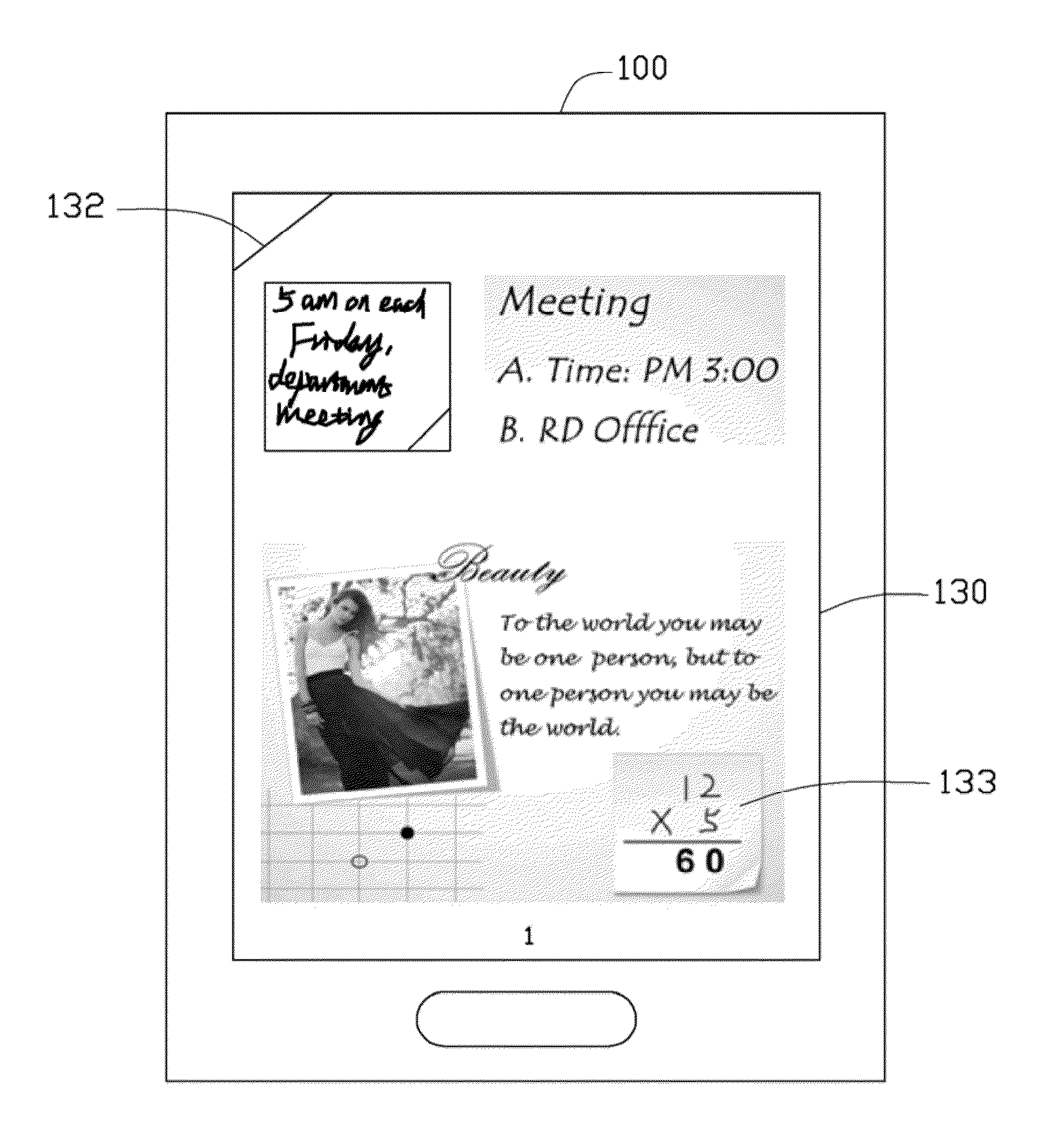
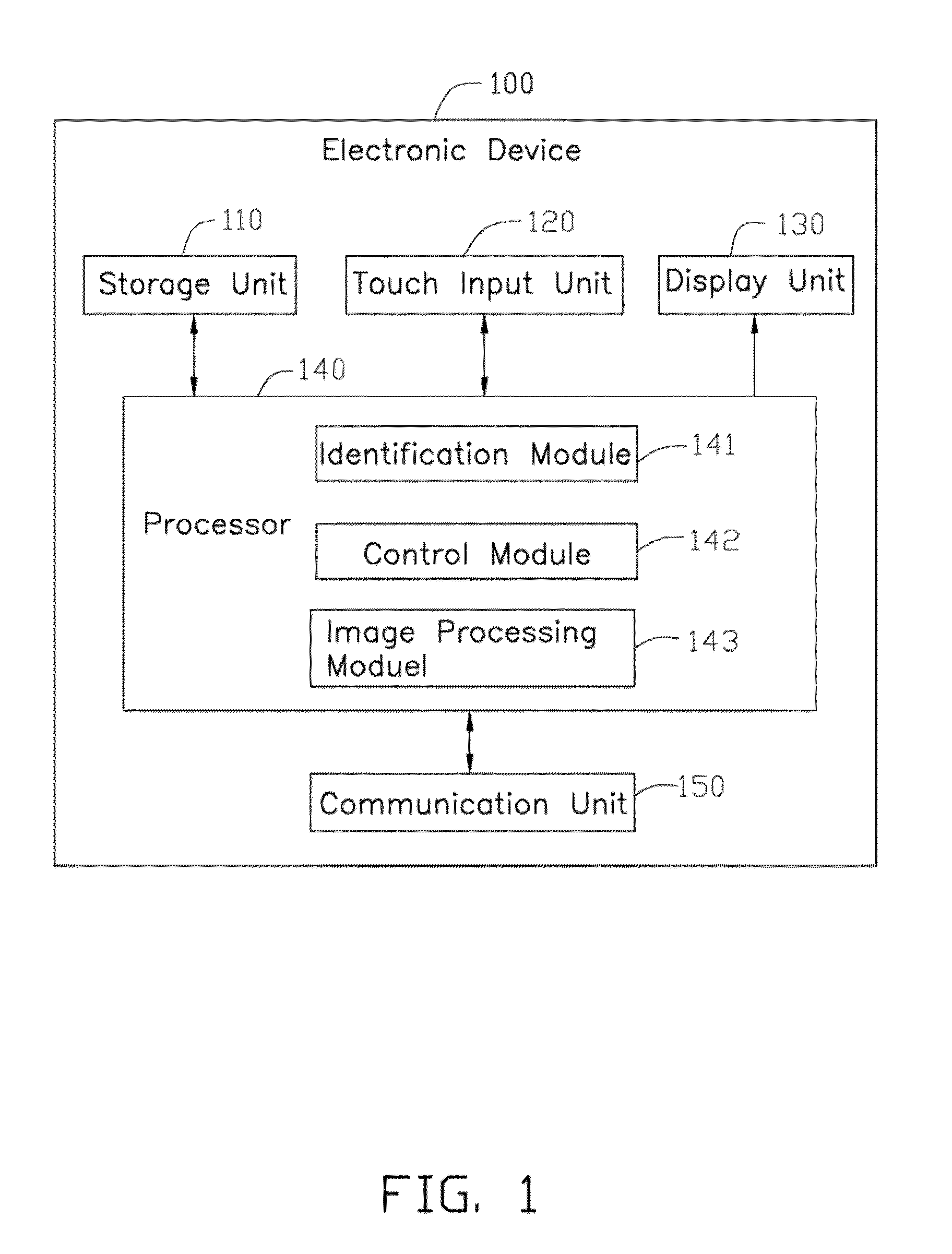
Electronic device and calculation control method thereof
InactiveUS20140007002A1Special data processing applicationsInput/output processes for data processingTouch SensesHuman–computer interaction
A calculation control method is used for an electronic device. The electronic device includes a storage unit storing a number of arithmetic equation models. The method includes the following steps. Sense handwritten touch input on a touch sensing unit by a user. Generate signals associated with the user's handwritten touch input. Display the handwritten content according to the generated signals. Recognize the handwritten content of the user, and convert the recognized handwritten content into an arithmetic operation if the recognized handwritten content matches one of the arithmetic equation models stored in the storage unit. Calculate a result of the arithmetic operation, if the recognized handwritten content matches one of the arithmetic equation models. And display the calculated result to the user.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
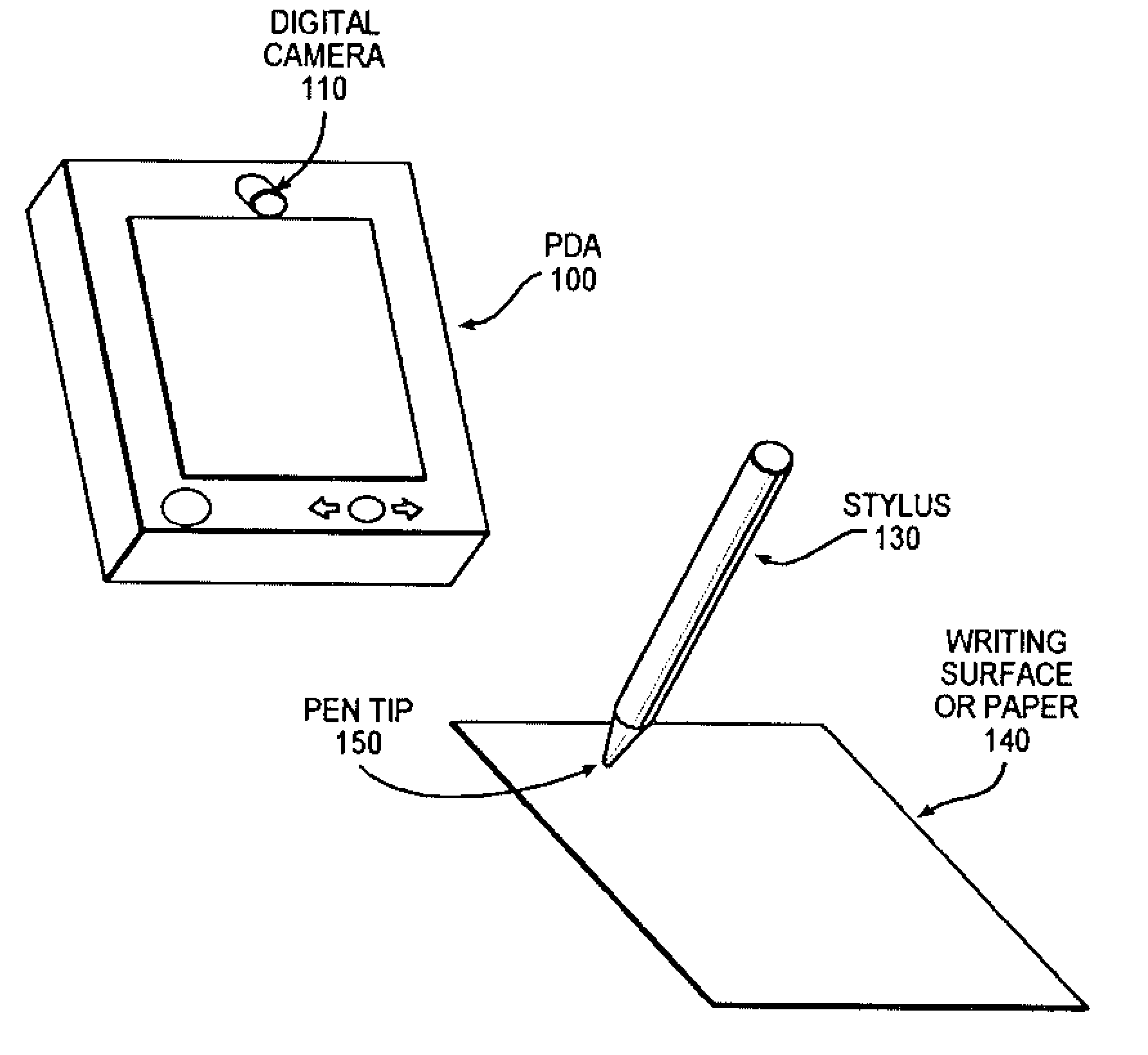
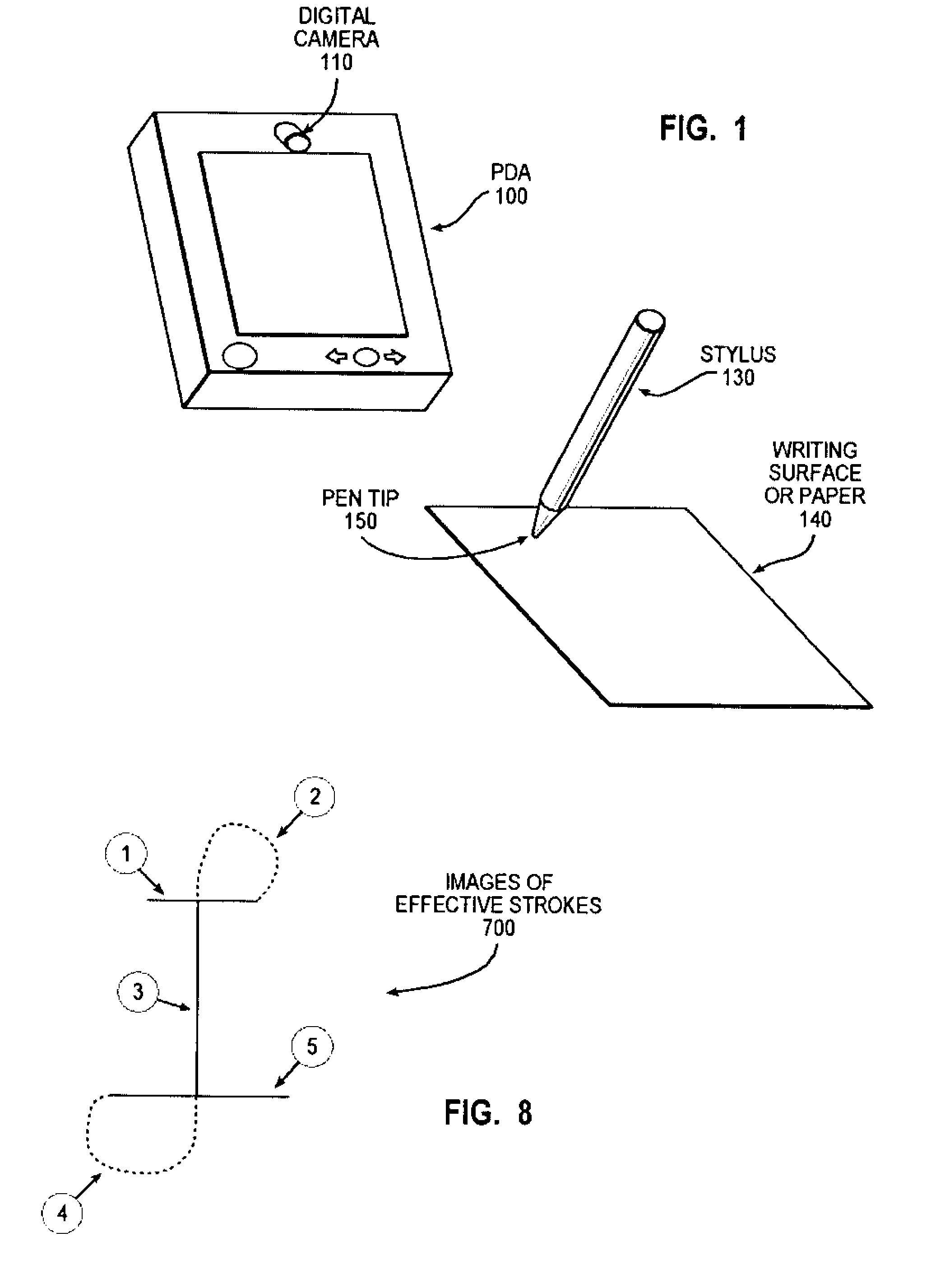
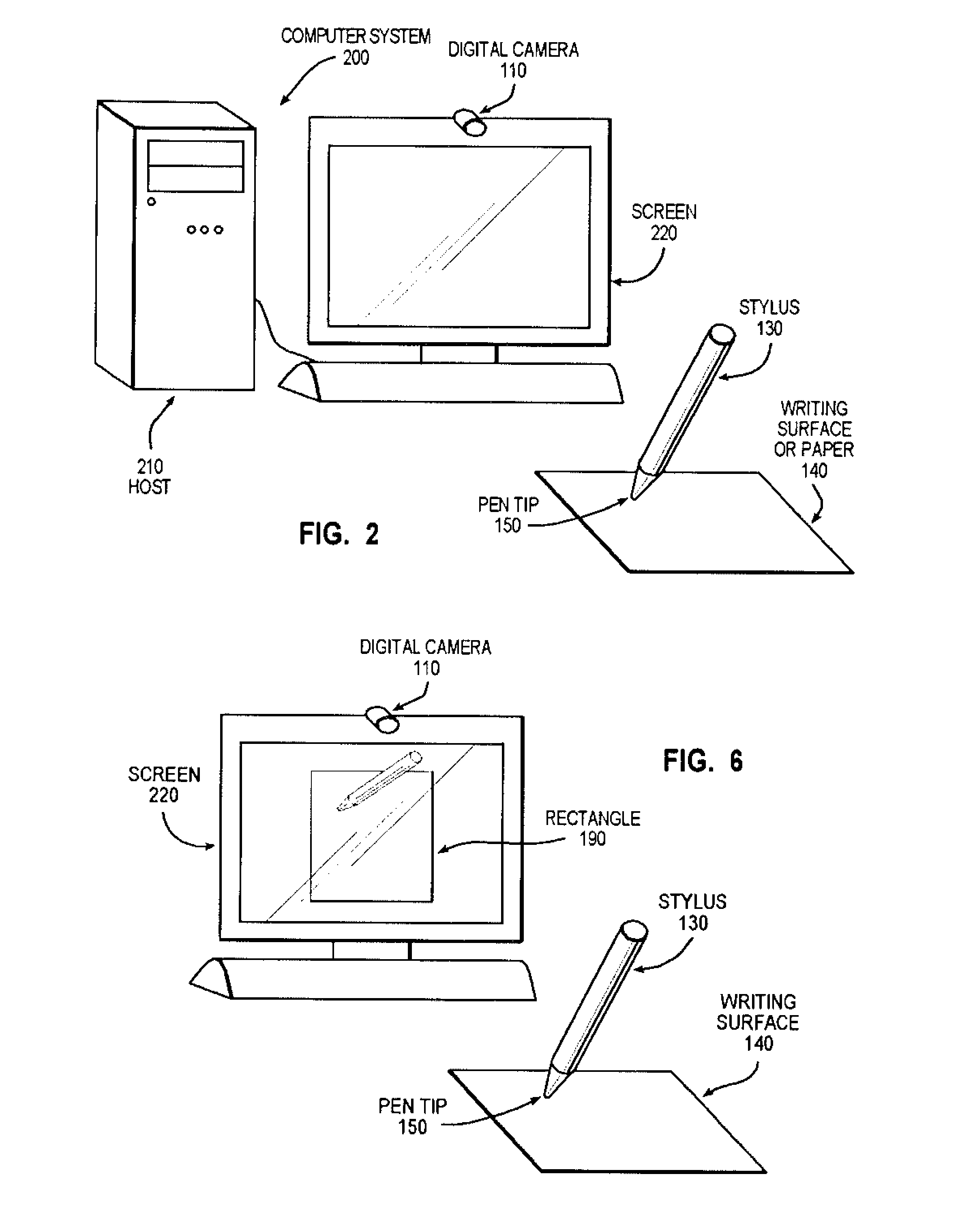
Video-based biometric signature data collecting method and apparatus
InactiveUS20100283766A1Low costSimple and low-costTransmission systemsGraph readingHandwritingDigital data
Disclosed are a method, an apparatus, and a computer recording medium for video-based handwriting input for biometric Signature Data Collecting. The invention is implemented by finding out all of the relative positions among all light points of light sources when all light sources mounted on a stylus are turned ON; capturing an image including effective strokes and digital data of pen pressure with a digital camera, when a user writes on a writing surface with a stylus having a light source (e.g. LED) indicating x-y coordinates of strokes, said images are time-stamped; wherein the stylus comprising a micro-switch, when the stylus touches the writing surface, the micro-switch is turned on to let the light source indicating x-y coordinates of strokes ON and generate a “light point”; and extracting effective stroke images and digital data of pen pressure by comparing the captured images with the light point on the stylus. Moreover, the invention discloses a low-cost, wireless method and apparatus for handwriting input which enables a user to write on a paper without a touch sensor provided for a computer system equipped with an embedded digital camera.
Owner:IBM CORP
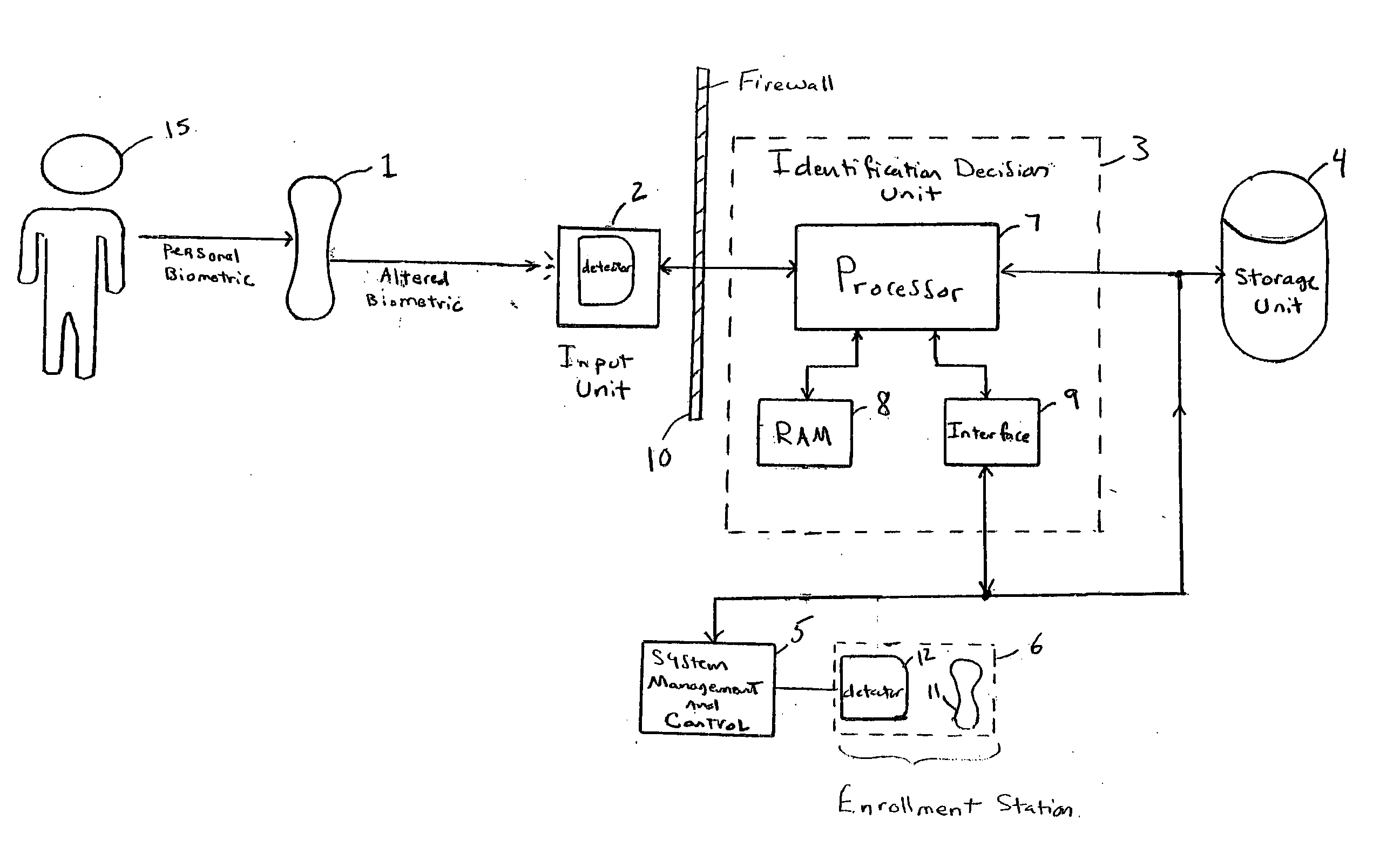
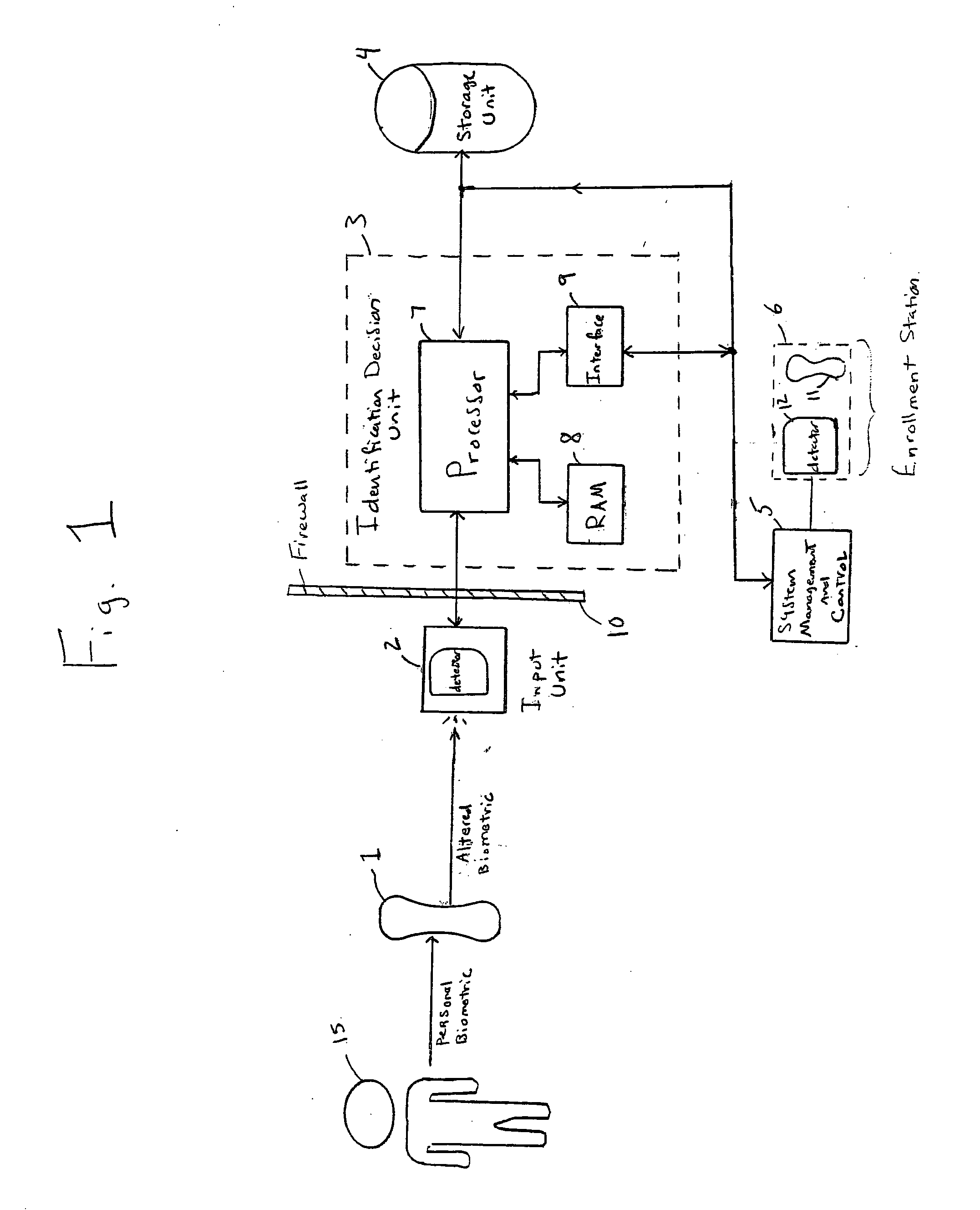
Recoverable biometric identity system and method
InactiveUS20060133651A1Great level of securityIncrease elasticitySpeech analysisAcquiring/recognising eyesHandwritingPalm print
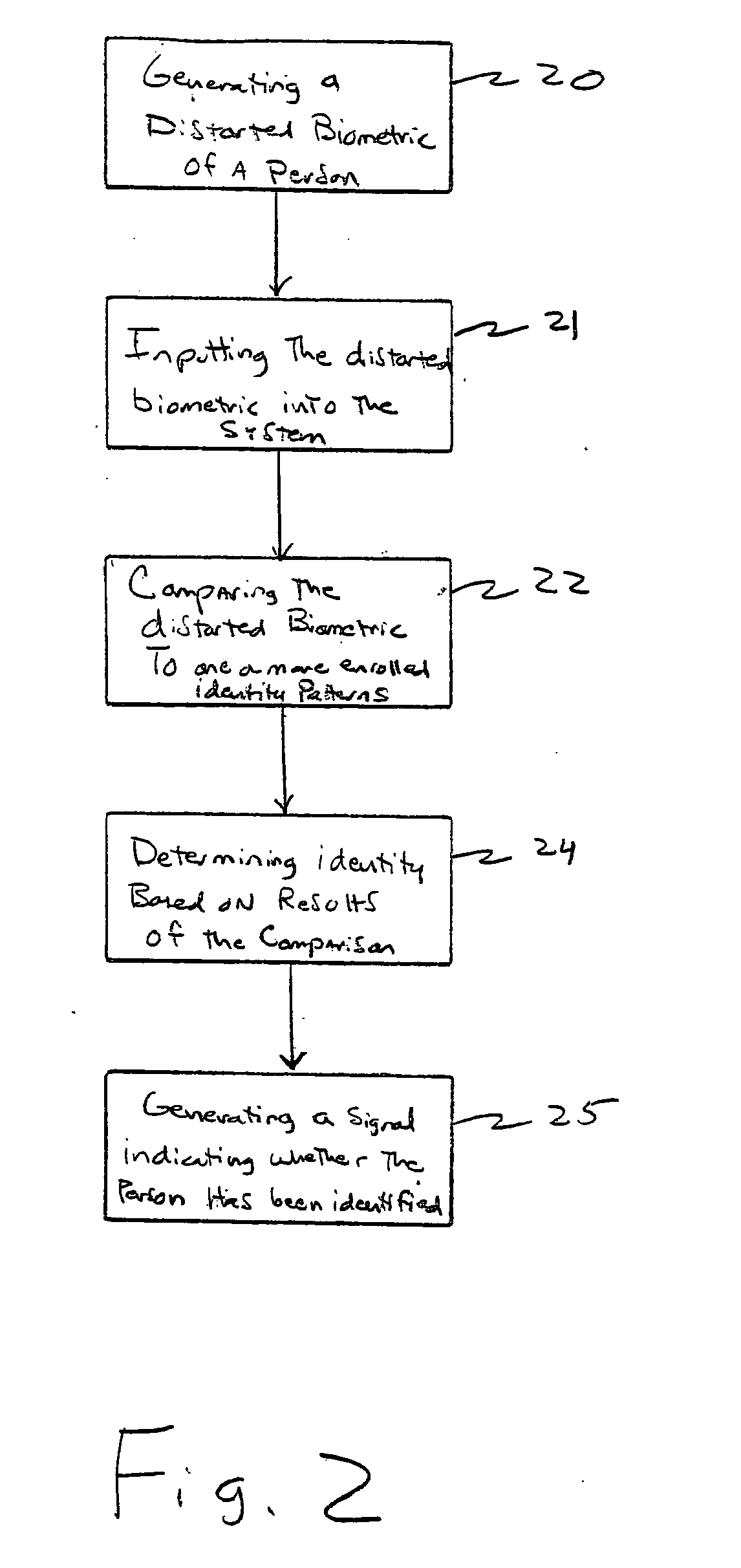
A method for identifying persons based on biometric data achieves enhanced security and increased accuracy compared with other systems by distorting one or more biometrics prior to detection and recognition. The method includes detecting a distorted biometric for input into an identification system, comparing the distorted biometric to one or more distortion patterns, and determining an identity of the person based on results of the comparison. The biometric may be an eye pattern, a fingerprint or palm print, a voice print, a handwriting sample, a DNA sample, a facial image, or any other type of characteristic or behavioral attribute of a person. The biometric may be distorted in any one of a variety of ways for comparison to previously enrolled biometrics which have been distorted using the same or similar element. A system and program embodied within a computer-readable medium performs the steps of the method.
Owner:POLCHA ANDREW J +1
Popular searches
Color television details Closed circuit television systems Digital data authentication Matching and classification Payment architecture Coded identity card or credit card actuation Acquiring/reconising fingerprints/palmprints Verifying markings correctness Coin/currency accepting devices ATM surveillance
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com