Multiparty joint key production and digital sign method and system
A technology of digital signature and joint signature, which is applied in the field of information security and can solve problems such as hidden private key security leakage.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
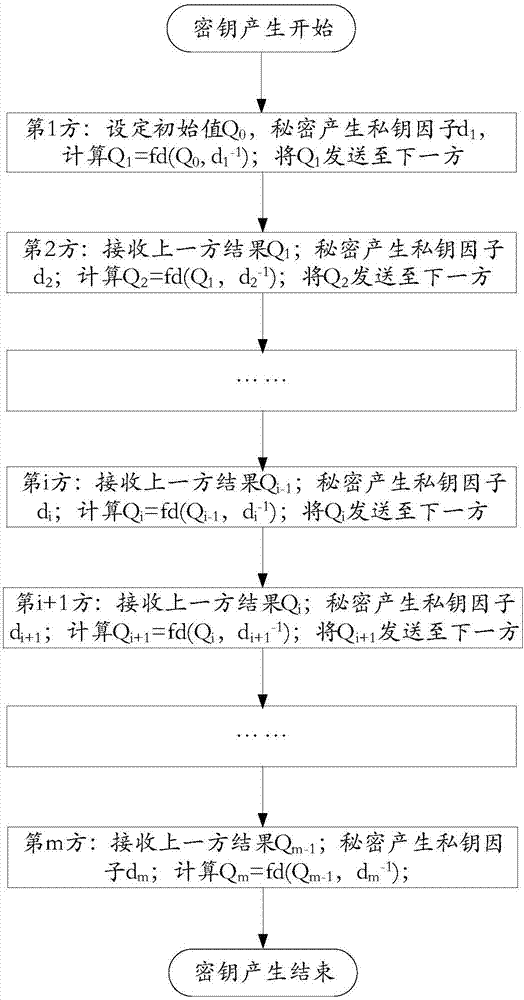
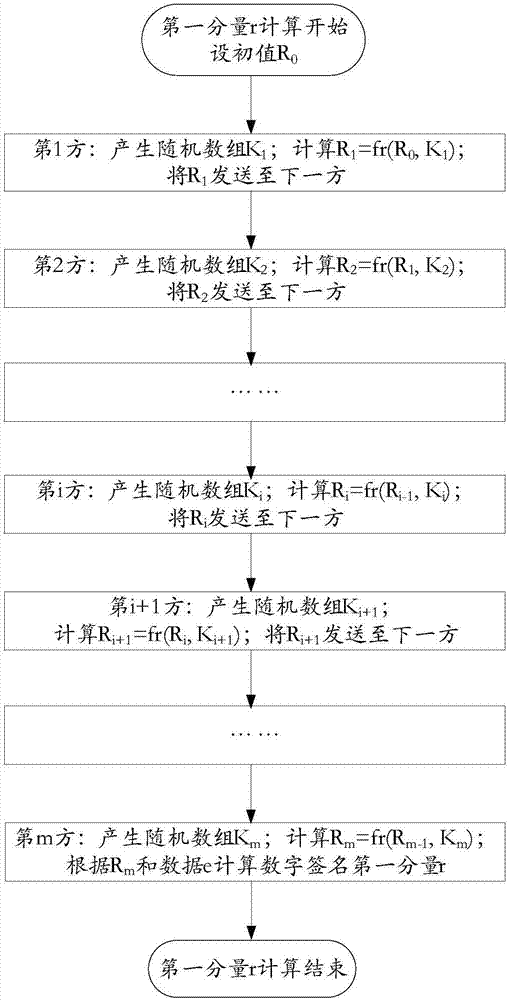
[0171] This embodiment relates to the three-party key generation process and the realization of digital signatures. A typical application is that a partner company has three main leaders, namely the first party: chief financial officer, the second party: general manager and the third party : Chairman. Important documents of the company require three parties to jointly digitally sign the document. Each of the three parties has a private key factor of the company's signature private key. Only the joint signature of the three parties can complete the digital signature of the company's important documents. And agree that the order of signature is the chief financial officer, the general manager, and the chairman, that is, the order is the first party, the second party, and the third party. The signing devices of the three parties can be their personal computers, mobile phones or special signing devices, such as USB-KEY.
[0172] Such as Figure 5 As shown, the following examples...
example 2
[0192] This embodiment relates to the non-central four-party key generation process and the realization of digital signatures. Another feature of the present invention is reciprocity, that is, the m joint signers are equal to each other, and there may be no upper-lower relationship. This example uses an example composed of four joint signers to illustrate their peer-to-peer key generation process and the realization of digital signatures.
[0193] refer to Figure 6 , Figure 6 It is a schematic diagram of the four-party non-center joint key generation and digital signature process with m=4. For the sake of showing that their status is equal, it is assumed that the four joint parties are respectively A, B, C, and D. This example is only to illustrate the peer-to-peer relationship between the parties, so the process of generating and transferring the public key factors of all parties is ignored.
[0194] 1. No central four-party key generation process
[0195] Assume in adv...
Embodiment 3
[0214] This embodiment relates to the central four-party key generation process and the realization of digital signatures.
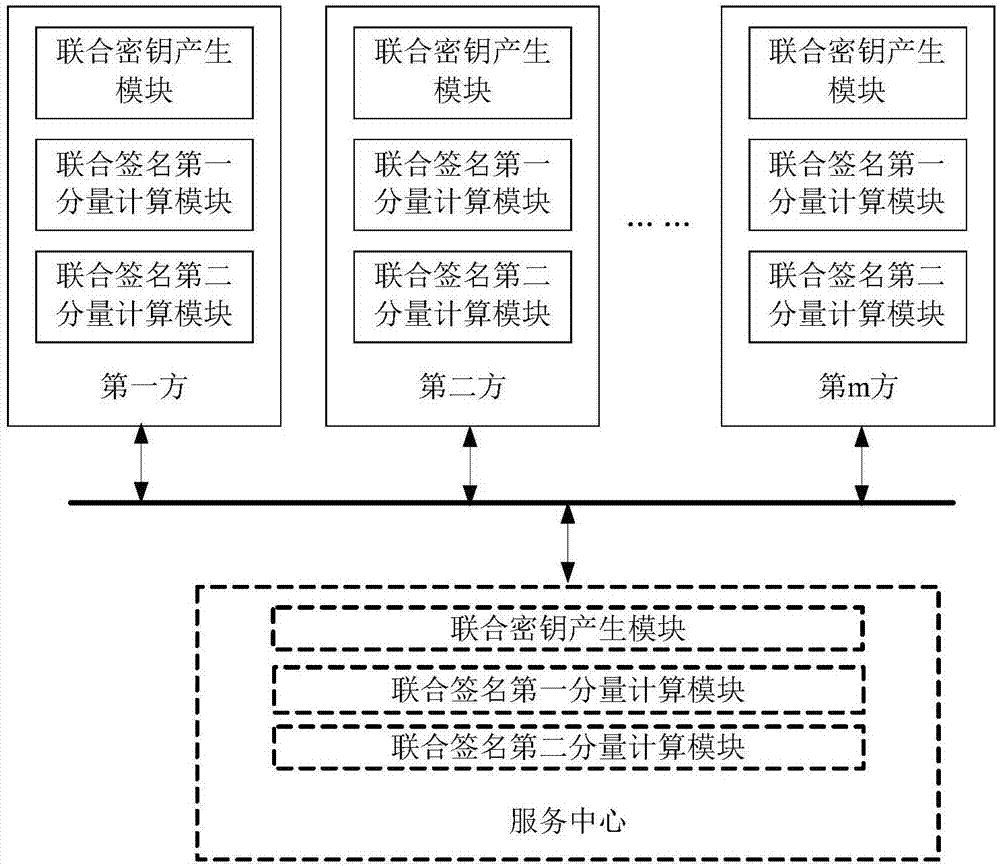
[0215] The multi-party joint key generation and digital signature method can also be a system with a center, which is characterized in that the center is responsible for all contact and communication with the joint, so that all parties do not need to send messages or results to each other. Under the coordination of the center, all parties use their own private key factors to complete joint key generation and digital signature. In the case of a center, the parties to the joint signature and the center can also have a mutually exclusive encryption key pair, which can encrypt the information between the parties and the center, and can also sign the information to ensure Confidentiality and authenticity of information between parties and the Center.
[0216] A typical application is that a joint-stock company A has four shareholders. The important documents...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com