Method for verifying authorization on basis of biological recognition
A verification method and biometric technology, applied in the field of biometrics, can solve problems such as poor accuracy of verification results, complexity of identity confirmation work, and the inability of biometric terminals to retrieve and output characteristic data, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
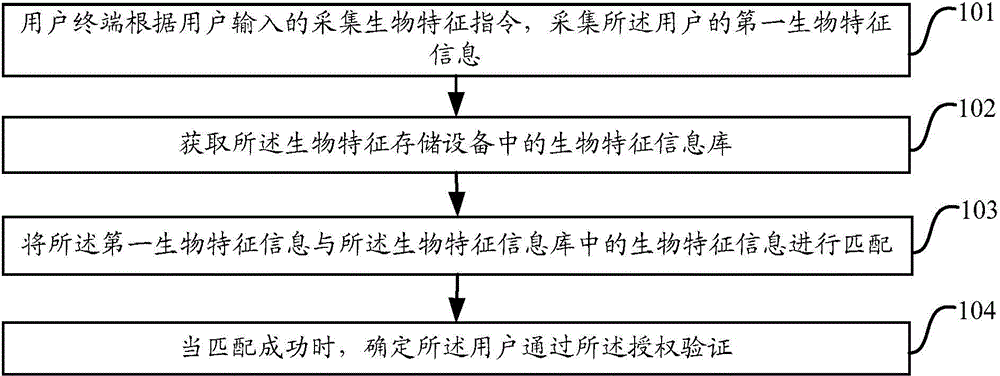
[0023] figure 1 It is a flowchart of a biometric information authorization verification method provided in Embodiment 1 of the present invention.
[0024] Such as figure 1 As shown, the biometric information authorization verification method includes the following steps:
[0025] Step 101, the user terminal collects first biometric information of the user according to an instruction input by the user for collecting biometric characteristics.
[0026] Specifically, the user terminal may be a biological collection device such as a mobile phone, a computer, and a tablet computer with a camera function; the first biological feature information is the biological feature information of the user to be authenticated for identity authorization.
[0027] When using a biometric storage device for identity authorization verification, the user enters an instruction to collect biometric information on the user terminal as needed to enable the biometric information collection function, for...
Embodiment 2
[0048] In this embodiment, the biometric information stored in the biometric storage device can be specifically the facial information of the user; the biometric storage device can be specifically an ID card with a wireless near-field communication NFC function; the user terminal can be specifically a camera function and a wireless Connected phone. Taking mobile phone card authorization or mobile phone function authorization as an example, the identity authorization verification process is described in detail. The specific identity authorization verification process is as follows:
[0049] The mobile phone collects the user's facial feature information according to the command of collecting facial feature information input by the user; when the mobile phone receives the command of collecting facial feature information, the mobile phone sends a wireless connection request to the ID card; after the ID card receives the wireless connection request message sent by the mobile phone...
Embodiment 3
[0051] This embodiment provides a mobile phone and a bank card for identity authorization through wireless communication. In this embodiment, online transfer is taken as an example. The specific process is as follows:
[0052] The user conducts online transfer through the mobile phone, and the user enters the online transfer application software of the mobile phone through the user name and password set; then enters the name of the owner of the transfer account, the transfer account, the transfer amount and other relevant transaction information; the transfer application software prompts the user to perform identity authorization verification; According to the prompt information, send a wireless connection request message to the bank card; when the bank card receives the wireless connection request message sent by the mobile phone, it matches the identity of the mobile phone and the bank card, and sends a wireless connection response message to the mobile phone; the mobile phone...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com