Trusted payment computer system
A computer system and computer technology, applied in the field of information security, can solve the problems of inconvenience for users, error-prone, reduced ease of use of electronic payment services, etc., and achieve the effects of enhancing ease of use, preventing attacks and ensuring security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
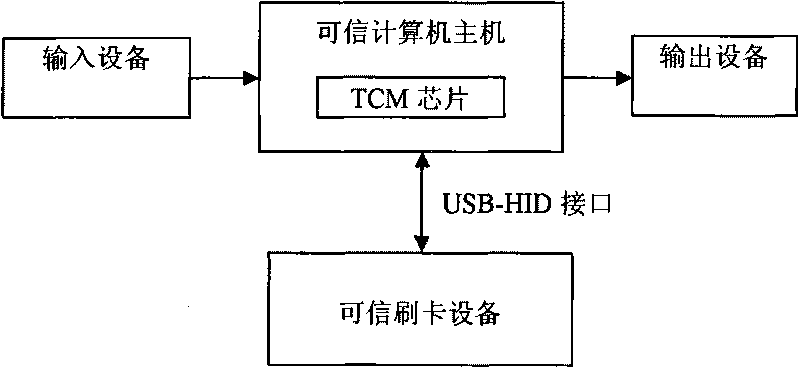
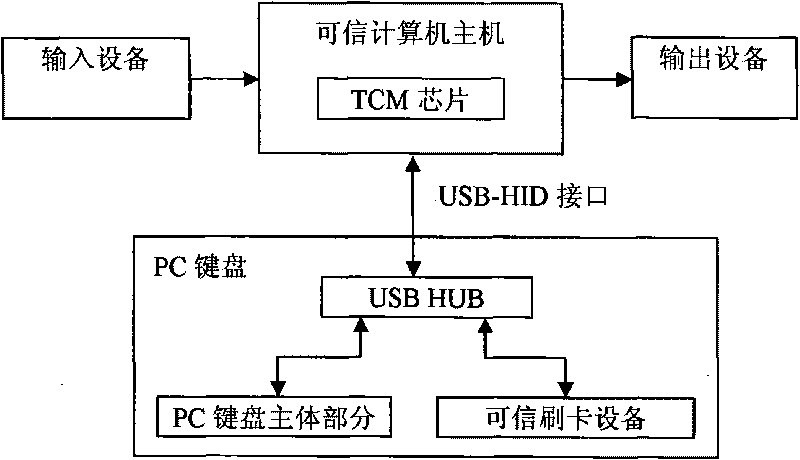
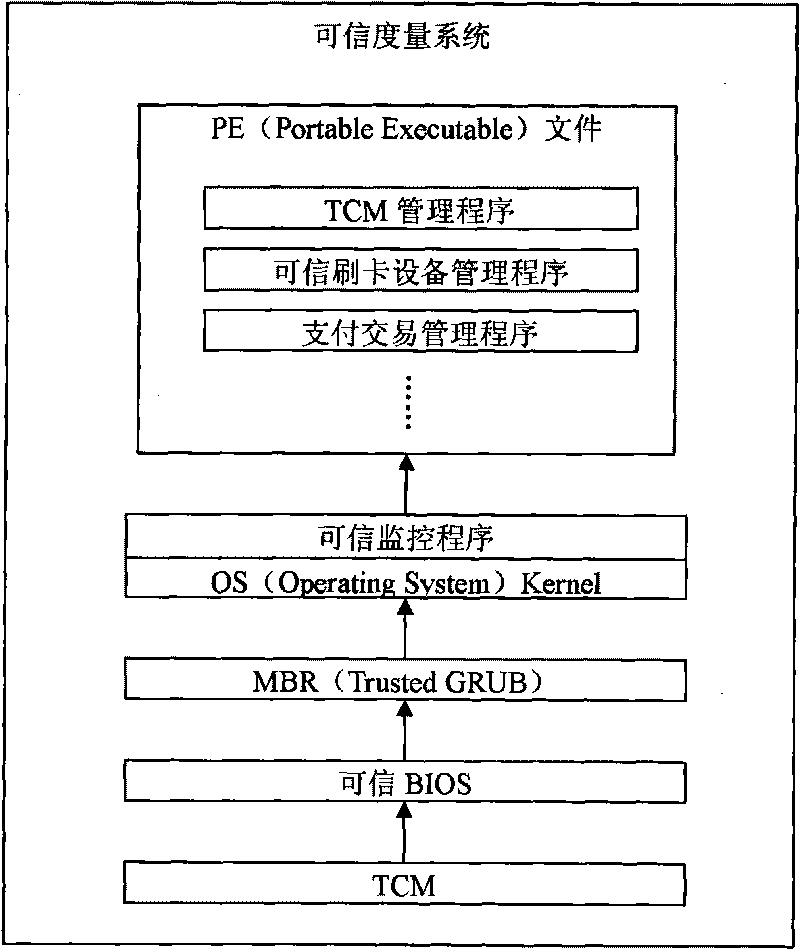
[0031] see Figure 1 to Figure 4 , the invention includes sequentially connected input device, trusted computer host, output device and trusted card swiping device interconnected with trusted computer host through USB-HID interface. The input device is the keyboard and mouse, and the output device is the monitor. The trusted card-swiping device is connected to the trusted computer host through the USB-HID protocol as a separate USB device, or is integrated with the PC keyboard and connected to the USB-HUB in parallel, and then connected to the trusted computer host through the USB-HID protocol. The TCM chip is embedded in the trusted computer host as the trusted measurement root, trusted reporting root and trusted storage root, and the trusted measurement system inside the trusted computer host measures TCM step by step——trusted BIOS——MBR——OS Kernel And trusted monitoring program - PE file integrity. The software system installed on the trusted computer host includes a TCM m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com