Trusted safe mobile storage device
A technology of mobile storage device and mobile storage device, applied in the field of information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
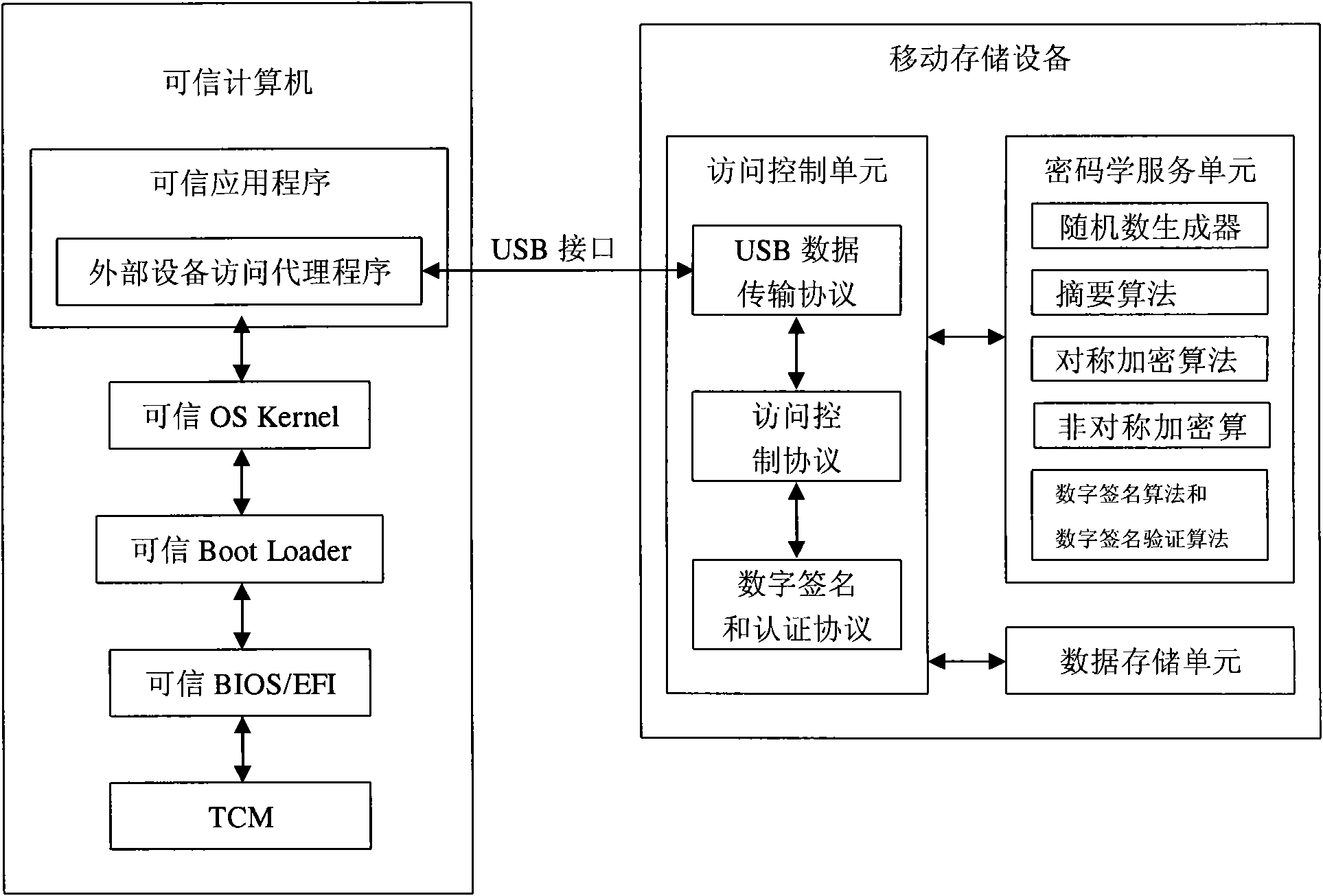
[0024] see figure 1 , the present invention includes a mobile storage device and a trusted computing device such as a trusted PC, a trusted server, or a trusted mobile phone connected to the removable storage device. The mobile storage device and the trusted computing device are bound by digital signature and signature authentication. Only the letter computing device can read or write data from the data storage unit of the mobile storage device. One trusted computing device can be bound to one or more mobile storage devices at the same time, and one mobile storage device can be bound to one or more trusted computing devices at the same time. Trusted computing equipment includes interconnected trusted applications, trusted OSKernel, trusted Boot Loader, trusted BIOS / EFI and trusted cryptographic module TCM. The trusted cryptographic module TCM serves as the trusted root of the trusted computing device, and builds a trusted computing environment based on the trusted root. The ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com