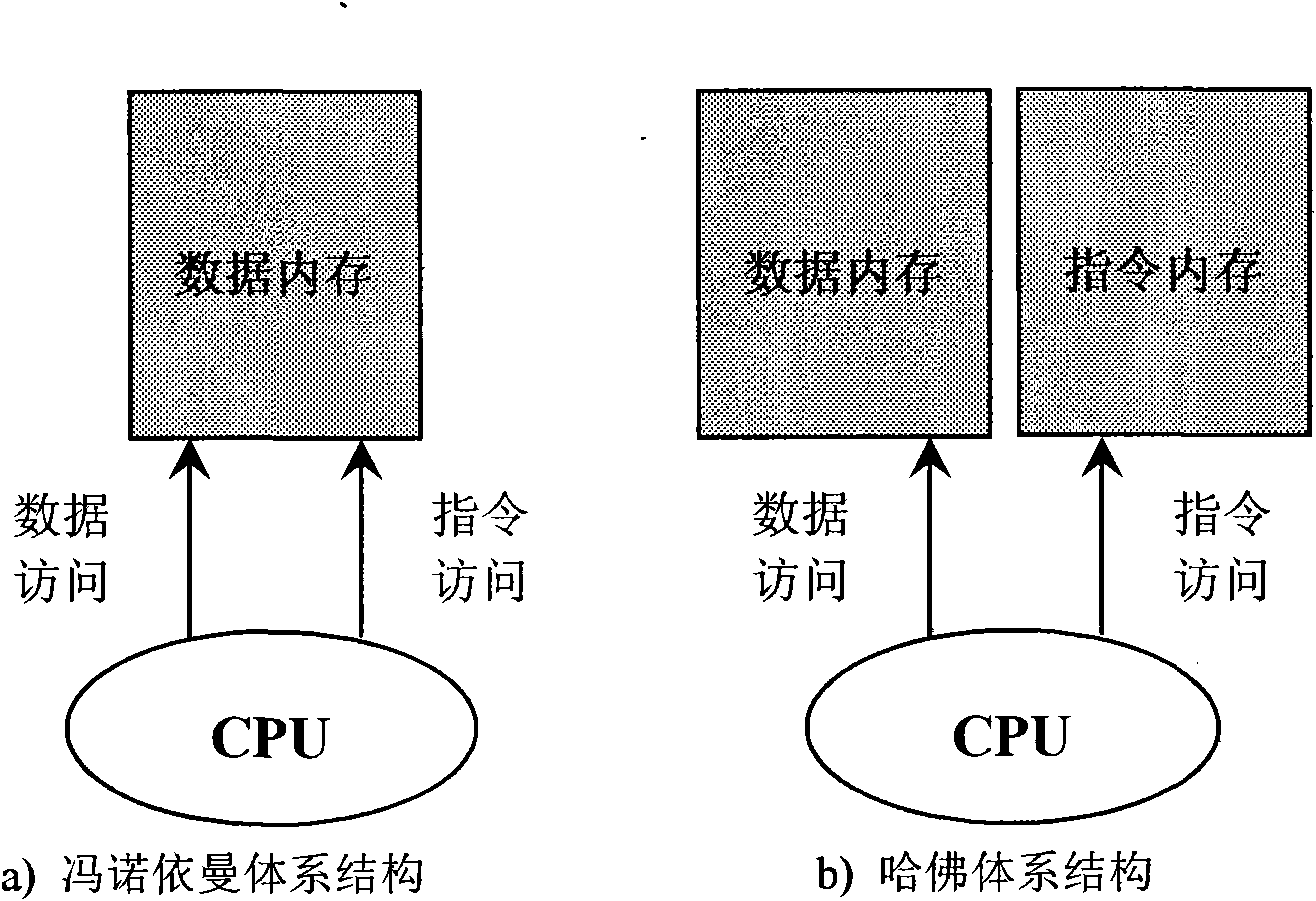
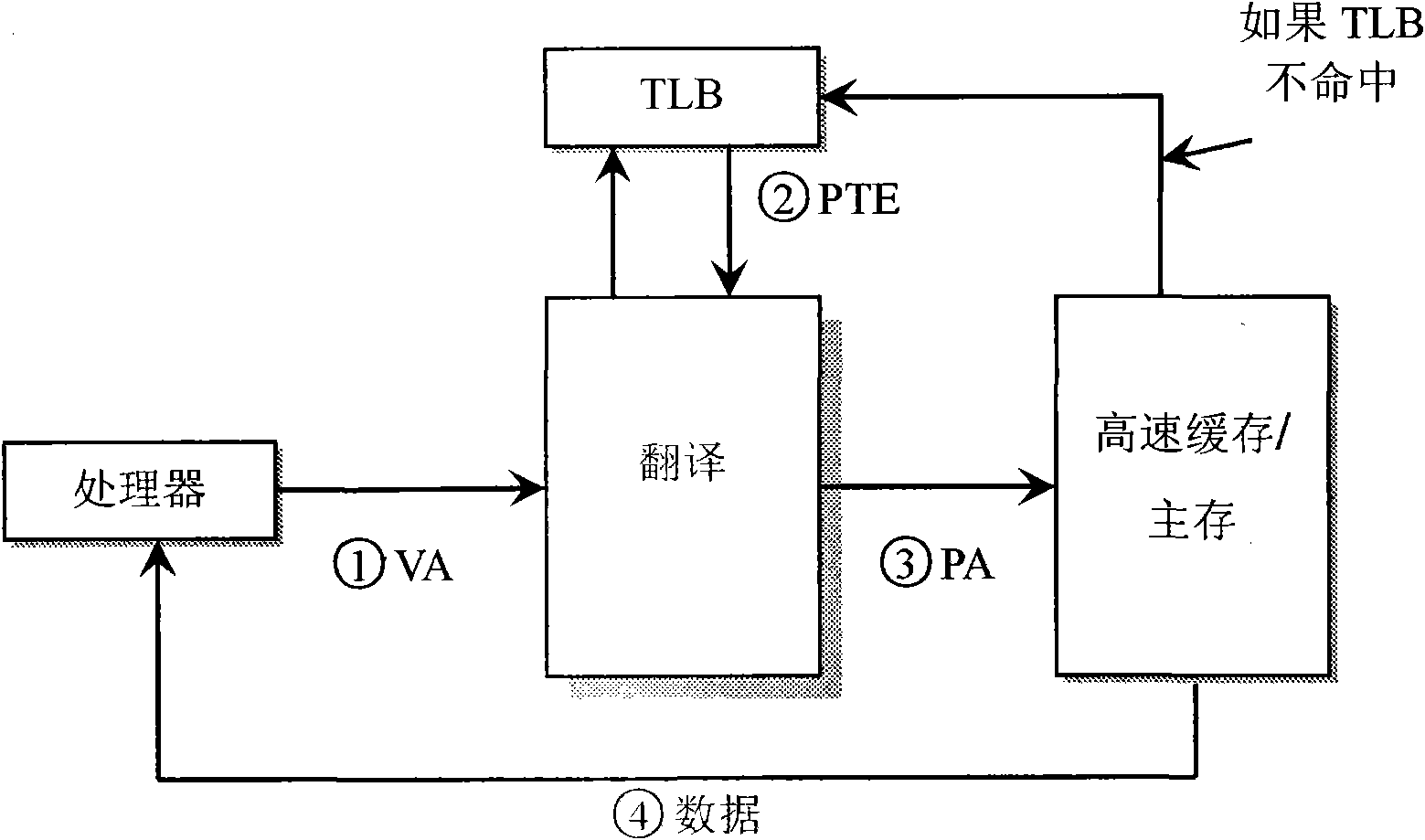
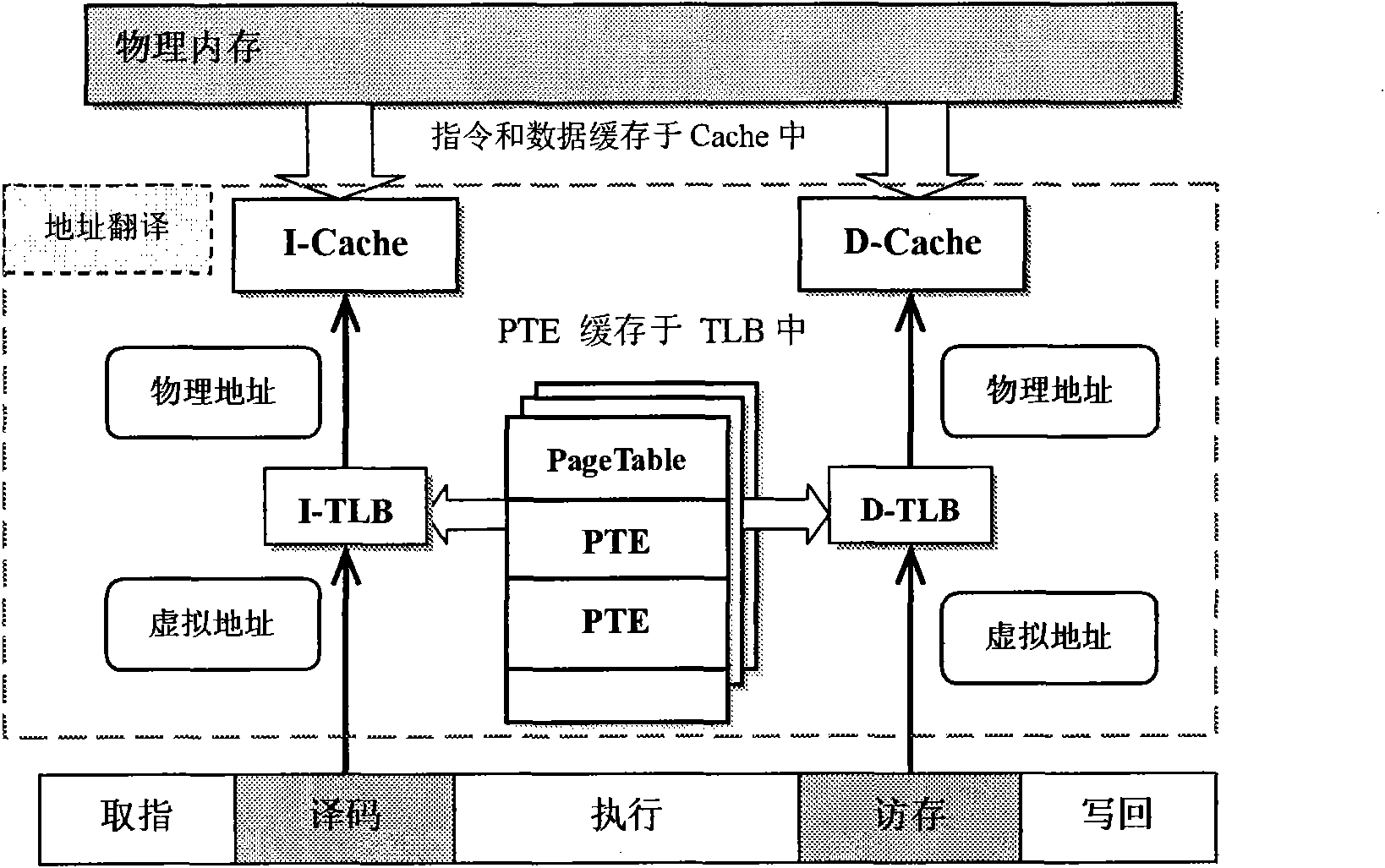
Kernel code protection method based on Harvard architecture
A kernel and code technology, applied in the field of protecting kernel code, to achieve the effect of convenient deployment, guaranteed safety, and small performance loss
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] The method of the present invention does not require too much hardware, although it is a virtualization technology, it does not need the support of CPU hardware virtualization technology, so the experimental platform of the present invention can be a computer with common configuration. As shown in the table below.
[0034] Table 1 The hardware and software configuration of the experiment
[0035]
[0036] The realization of the method of the present invention needs to recompile the kernel. Since Fedora Core 4 itself has no source code package, so in order to set up the protection mechanism of the present invention, the kernel source code package of the current operating system must be installed at first. Then modify the current kernel source code and recompile to get the required kernel.
[0037] There are four steps to build an experimental test environment based on the software and hardware environment: install the kernel source code package, modify the kernel sour...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com