Patents
Literature
213 results about "Swarm computing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
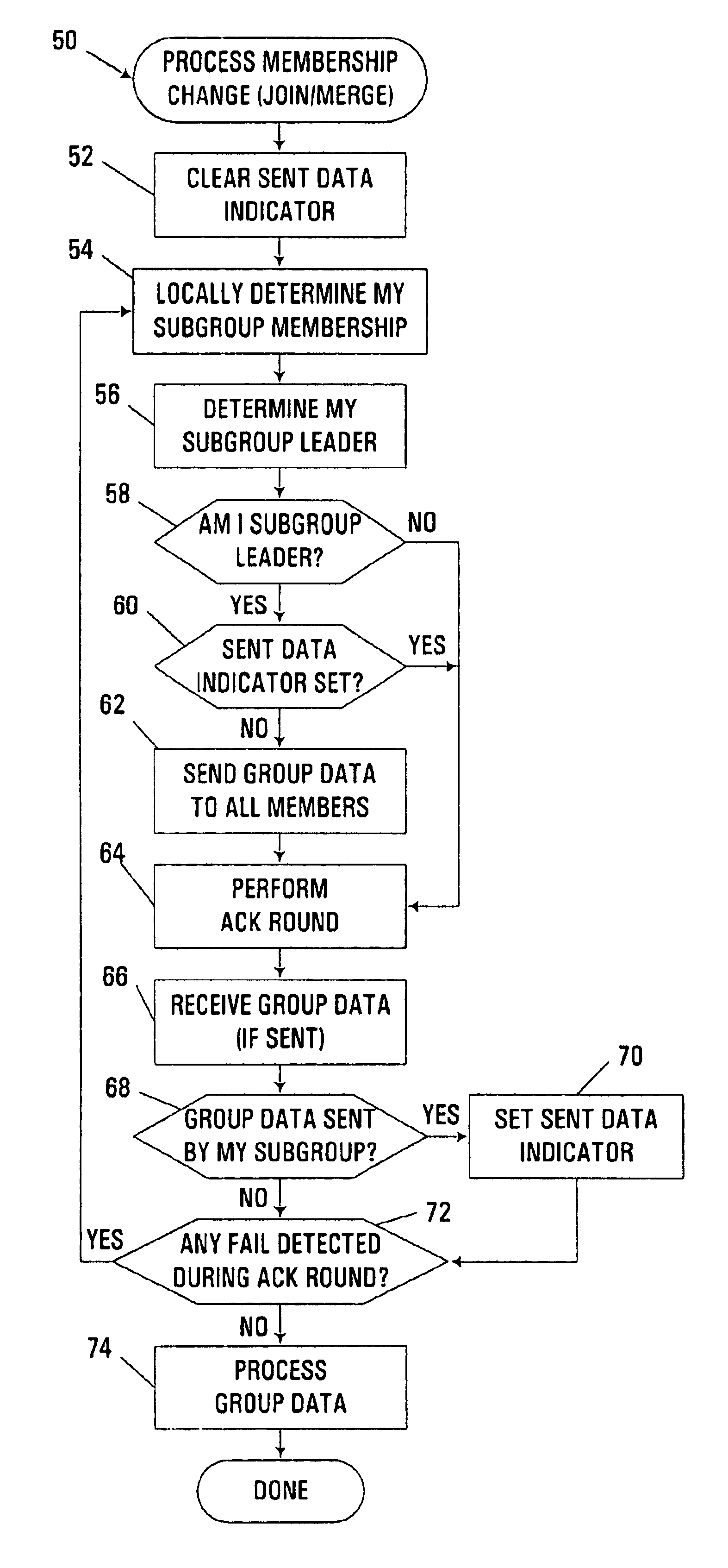
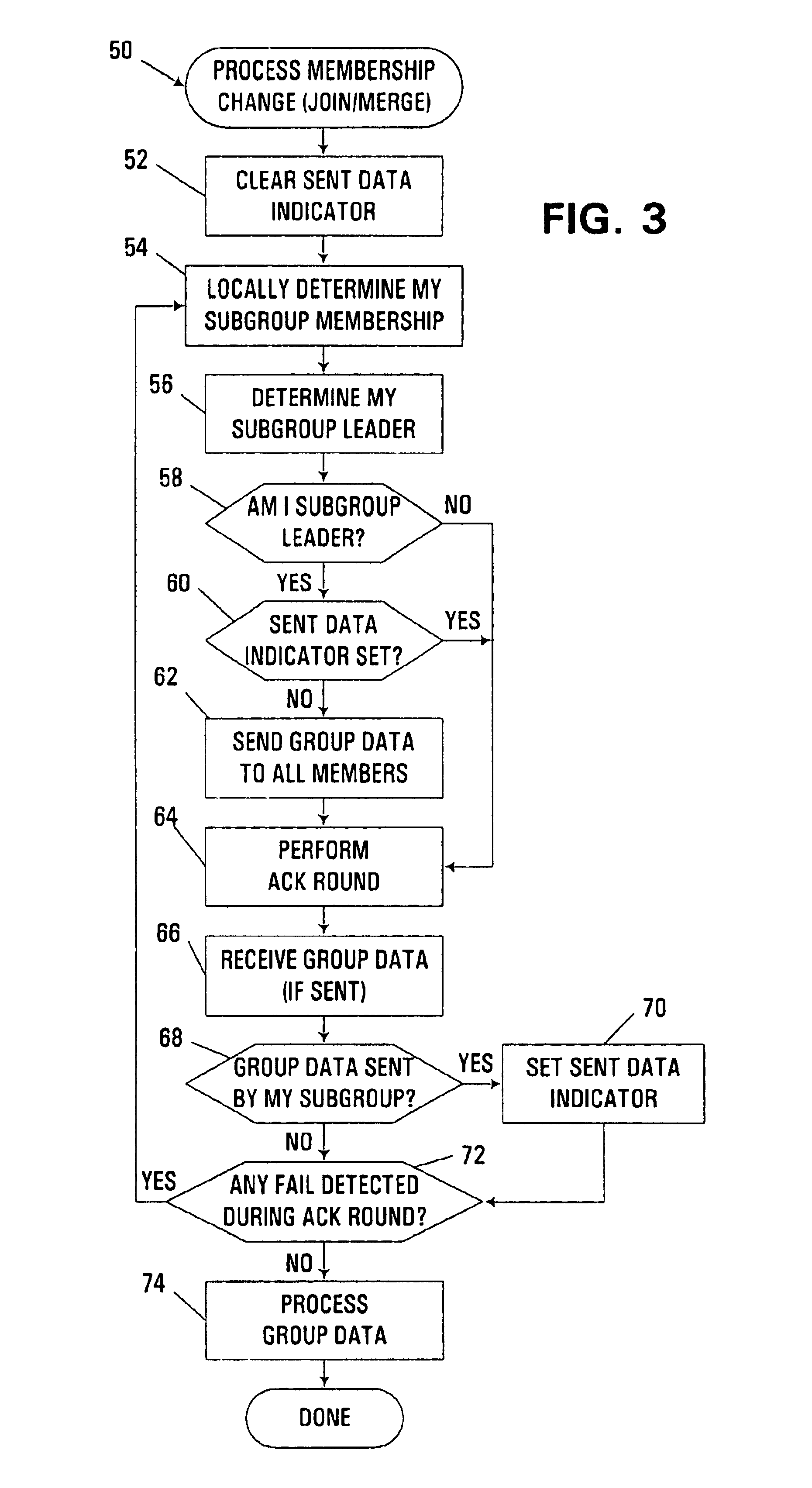
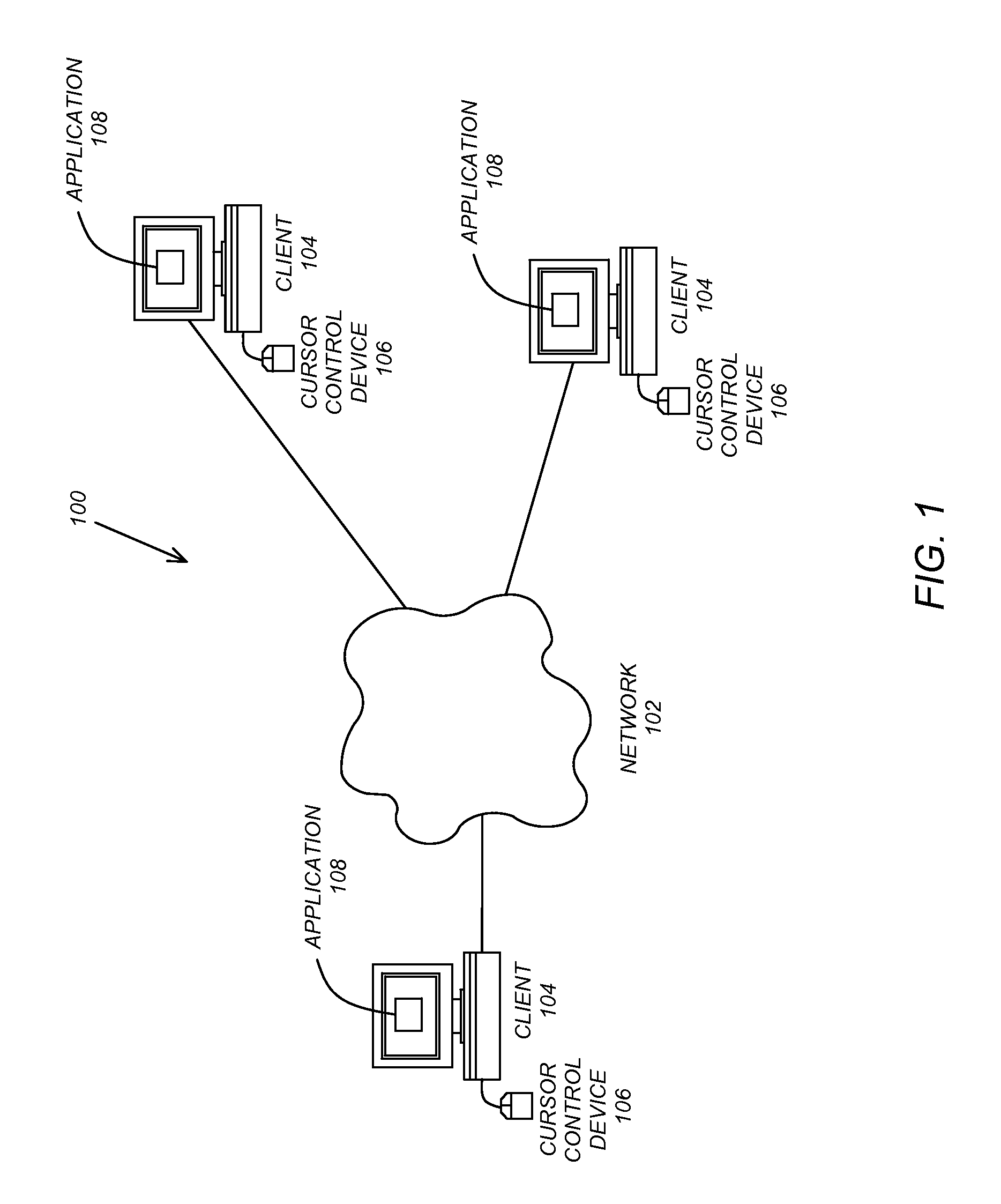
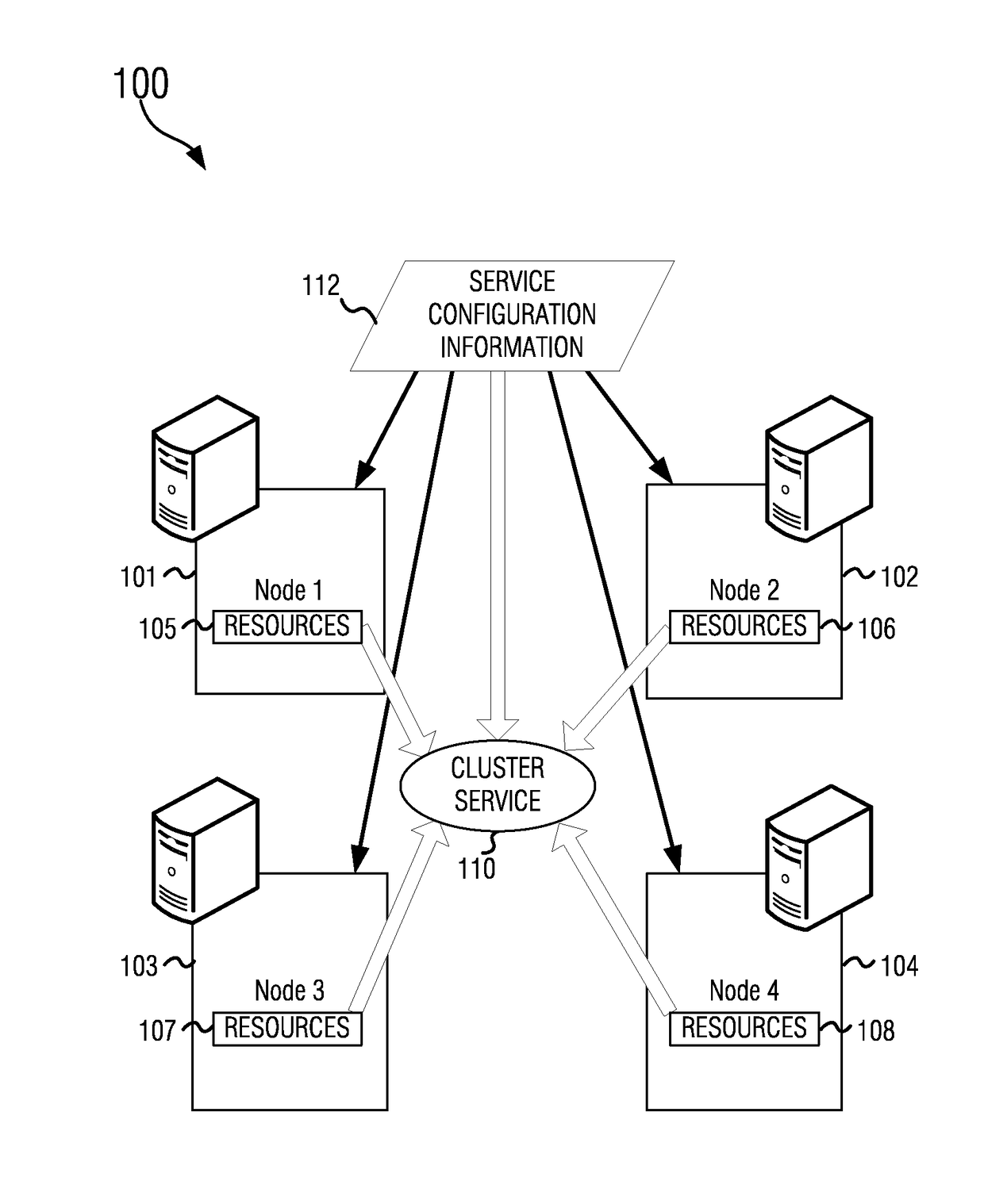
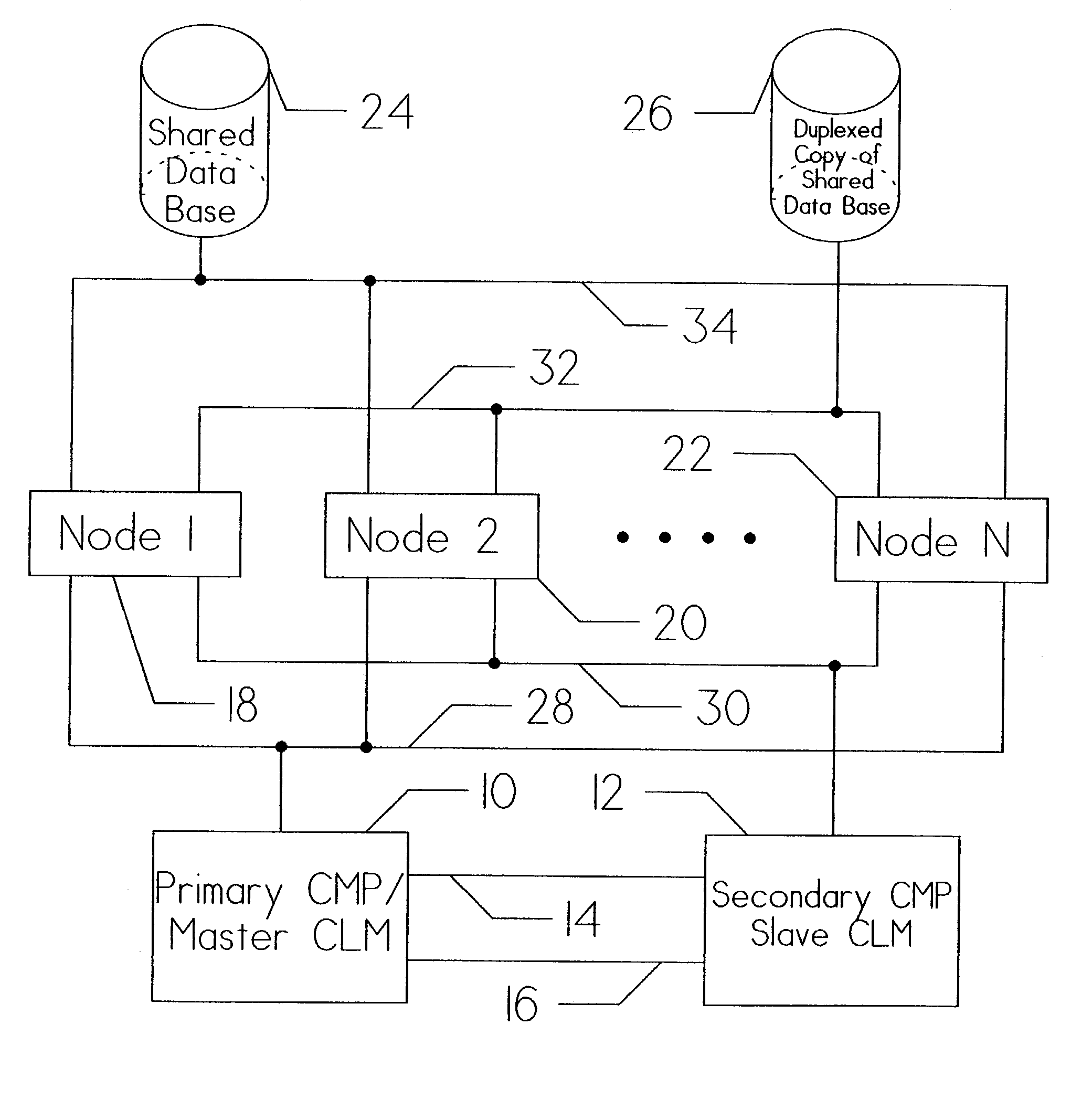
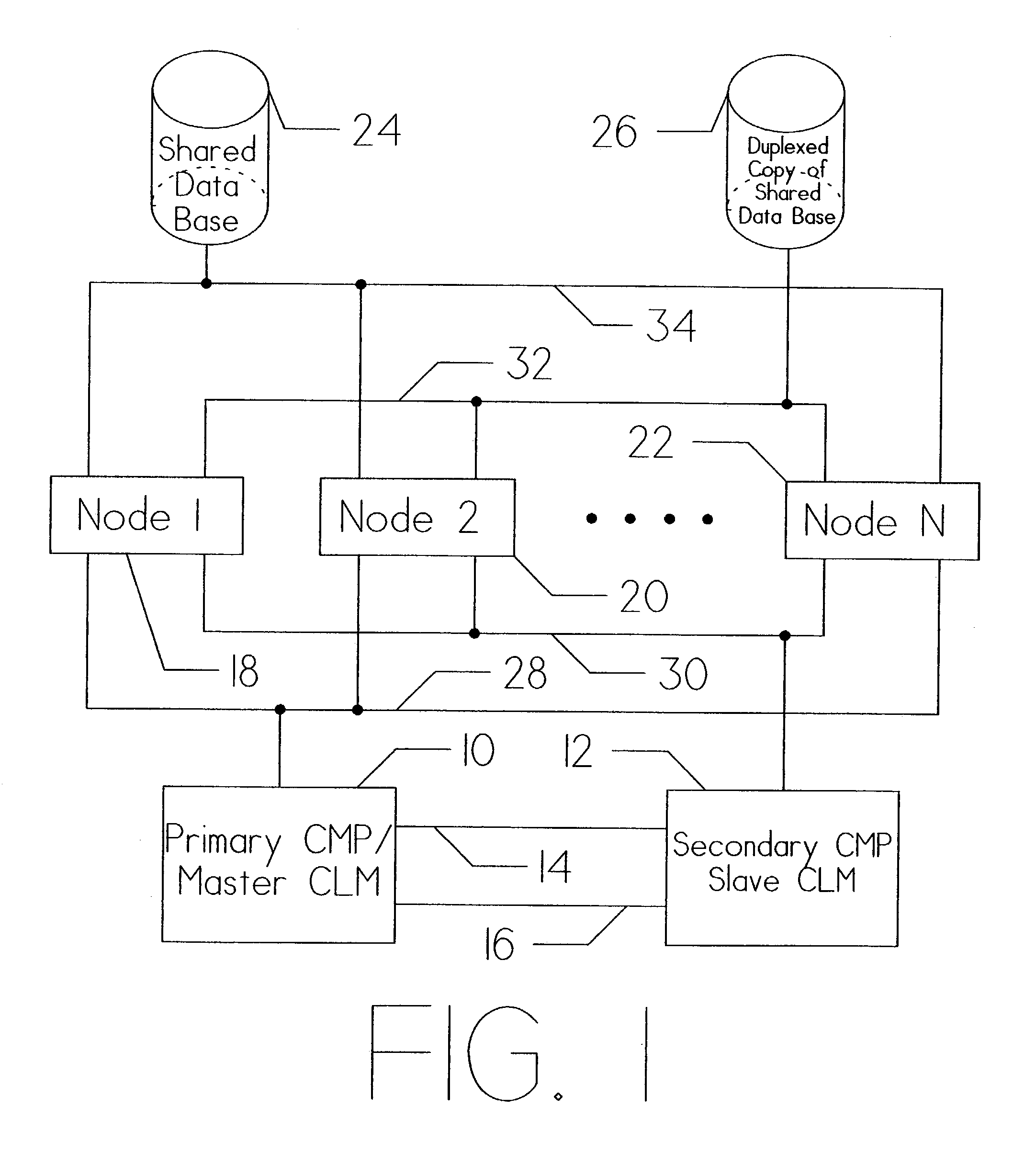
Group data sharing during membership change in clustered computer system
InactiveUS6839752B1Error preventionFrequency-division multiplex detailsComputerized systemData sharing
An apparatus, program product and method utilize subgroup-specific leader members to exchange group data between group members during the handling of a request to organize members into a group in a clustered computer system, e.g., when handling a membership change operation such as a merge or join. Such subgroup leaders may be determined locally within individual subgroup members, and moreover, the subgroup members may locally track the transmission status of group data for the various subgroups. Each subgroup includes one or more members that are known to store group data that is coherent among all subgroup members.
Owner:IBM CORP
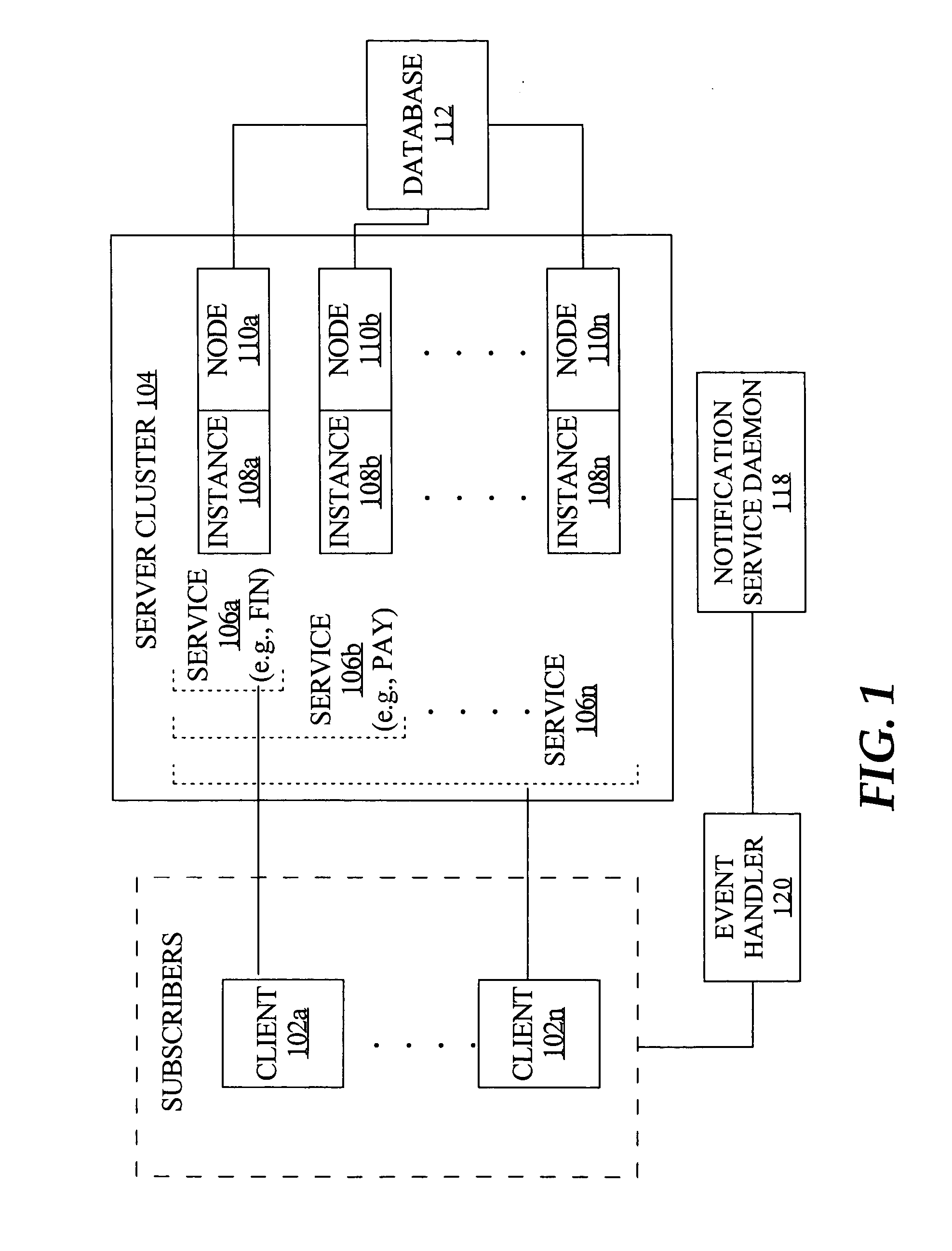
Fast application notification in a clustered computing system
ActiveUS20050038772A1Resource allocationDigital data processing detailsComputer networkService experience
With fast notification of changes to a clustered computing system, through which a number of events are published for system state changes, applications can quickly recover and sessions can quickly be rebalanced. When a resource associated with a service experiences a change in status, such as a termination or a start / restart, a notification event is immediately published. Notification events contain information to enable subscribers to identify, based on matching a session signature, the particular sessions that are affected by the change in status, and to respond accordingly. This allows sessions to be quickly aborted and ongoing processing to be quickly terminated when a resource fails, and allows fast rebalancing of work when a resource is restarted.
Owner:ORACLE INT CORP
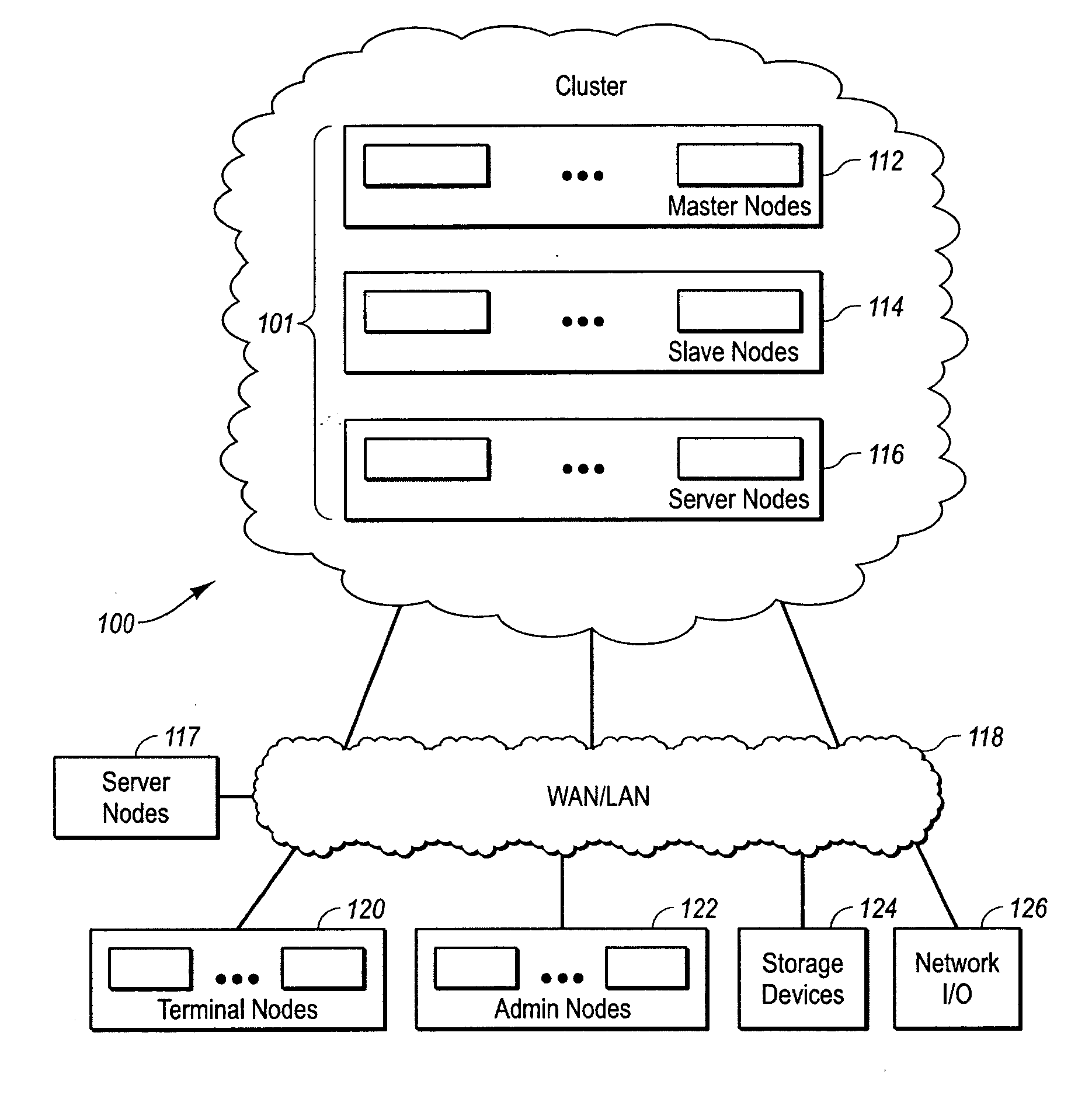
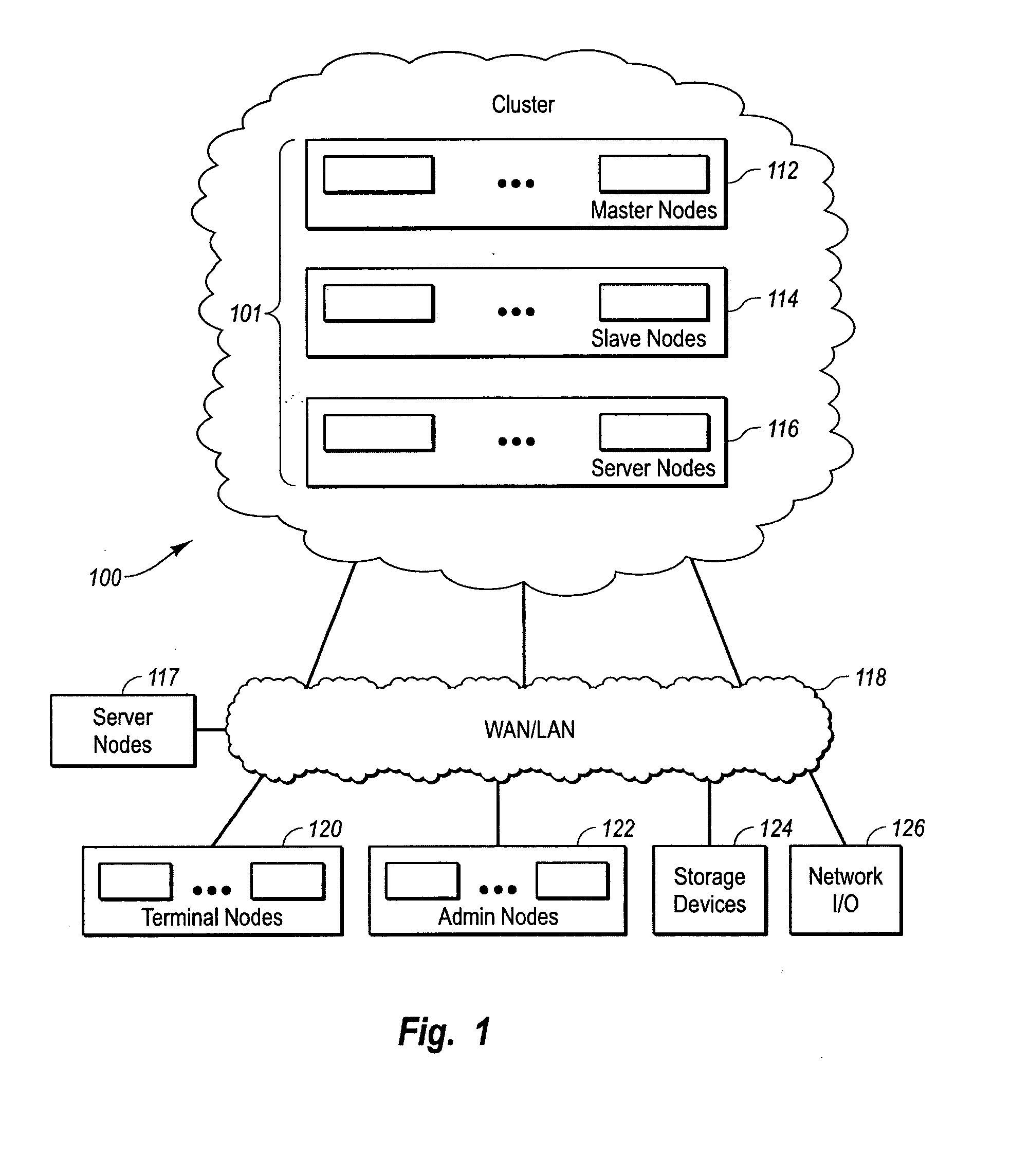
Clustered computer system with centralized administration
InactiveUS20060053216A1Digital computer detailsComputer security arrangementsOperational systemComputer cluster
Systems and methods for a computer cluster and for conducting user sessions in a managed enterprise computer network. A cluster includes multiple inter-connected nodes with specific roles. Master nodes administer and monitor slave nodes and the slave nodes are used to conduct user sessions with users through terminal nodes that provide an interface to the cluster. The cluster also may include server nodes that provide network services. Master nodes also control admittance to the cluster of external nodes and sub-clusters. Admin nodes form a control plane used to control and administer the cluster through the master nodes. The cluster provides a virtual environment for the user session that is built from at least an operating system image, an application image and other data needed for the user session.
Owner:METAMACHINIX
Navigation system with single pass clustering based template generation mechanism and method of operation thereof
ActiveUS20120232788A1Instruments for road network navigationNavigational calculation instrumentsAlgorithmEngineering
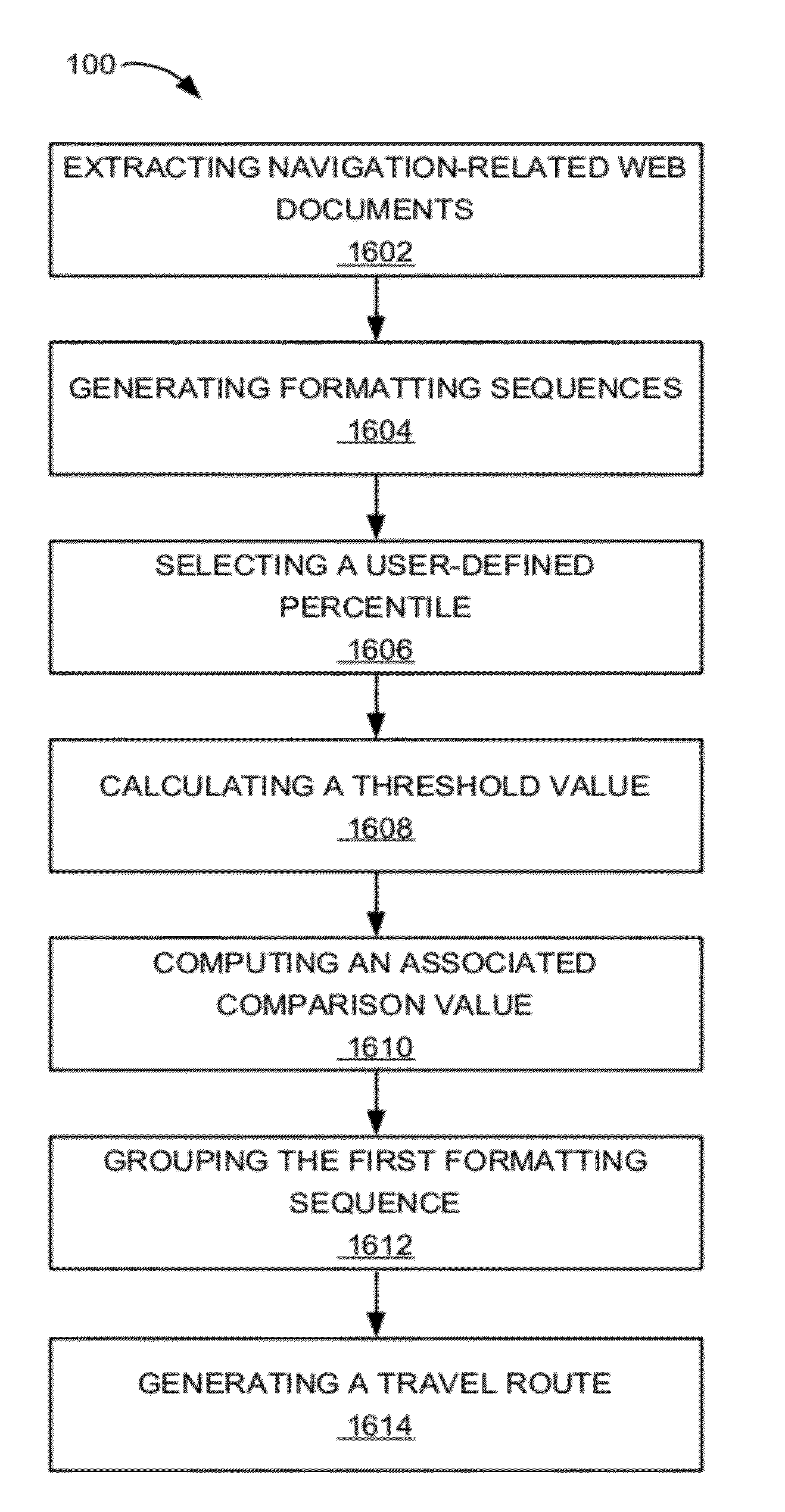
A method of operation of a navigation system includes: extracting navigation-related web documents having a point of interest; generating formatting sequences of the navigation-related web documents; selecting a user-defined percentile representing reciprocal fraction of an expected number of clusters; calculating a threshold value for a first cluster with the threshold value to be equal to the user-defined percentile of a first normalized distribution of sample comparison values between the first cluster and formatting sequence samples from the formatting sequences, the first cluster is from the clusters; computing an associated comparison value between a first formatting sequence from the formatting sequences and the first cluster; grouping the first formatting sequence with the first cluster when the associated comparison value exceeds the threshold value for the first cluster; and generating a travel route for the point of interest related to the first cluster for displaying on a device.
Owner:TELENAV INC
System and method for initializing and maintaining a series of virtual local area networks contained in a clustered computer system
InactiveUS20090106405A1Multiple digital computer combinationsProgram controlVirtual LANNetwork connection
A system and method for sharing network resources; the system comprising: (1) at least one network switch; (2) a plurality of computing devices, where the computing device comprises (i) at least one network connection; (ii) a plurality of processing nodes; and (iii) at least one storage device containing software for (a) initializing and maintaining a plurality of top-layer virtual local area networks (VLANs), (b) initializing and maintaining a plurality of client VLANs; and (c) using an empty VLAN as a virtual wire between the client VLAN and a shared network resource.
Owner:VIRTUDATACENT HLDG
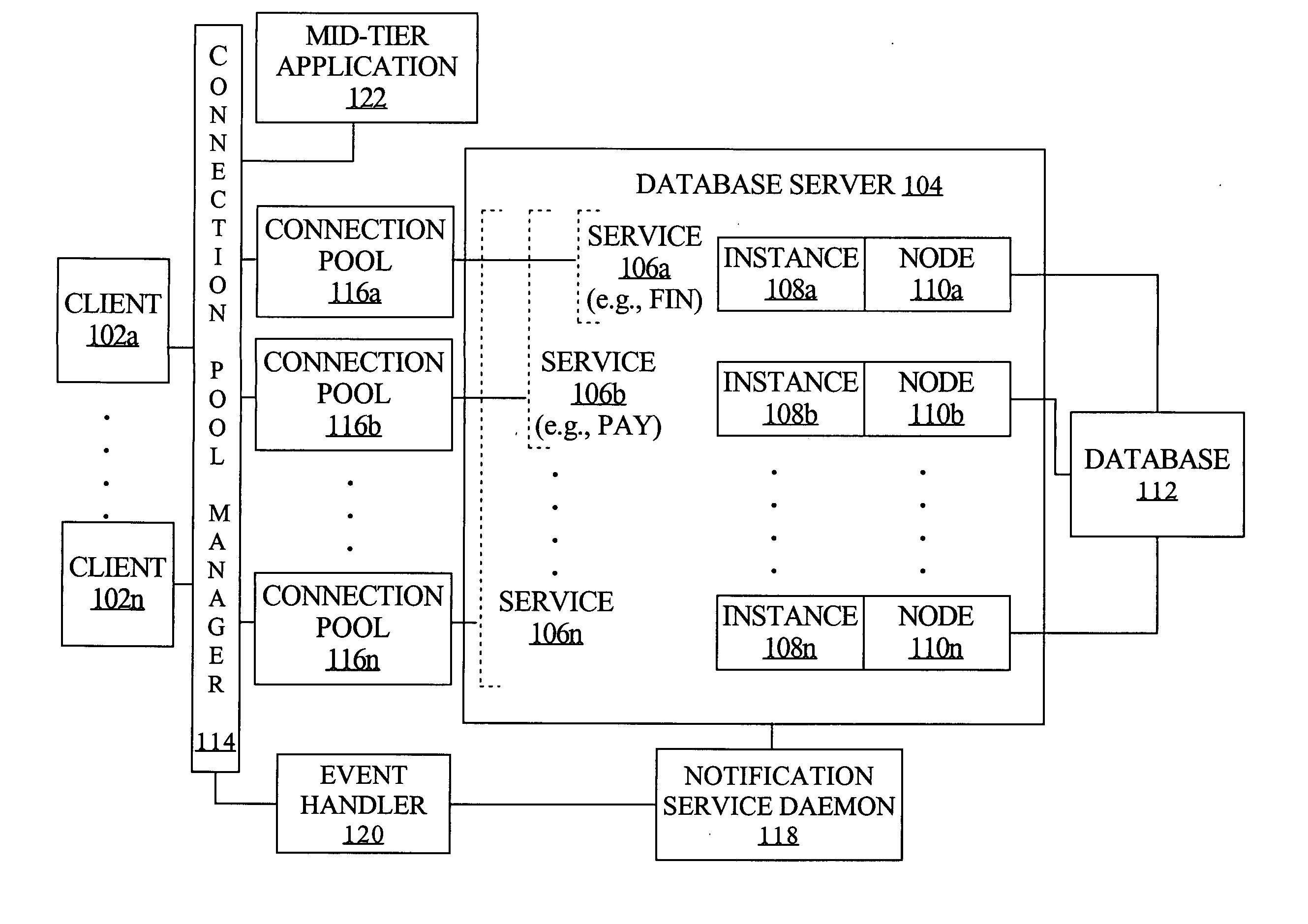
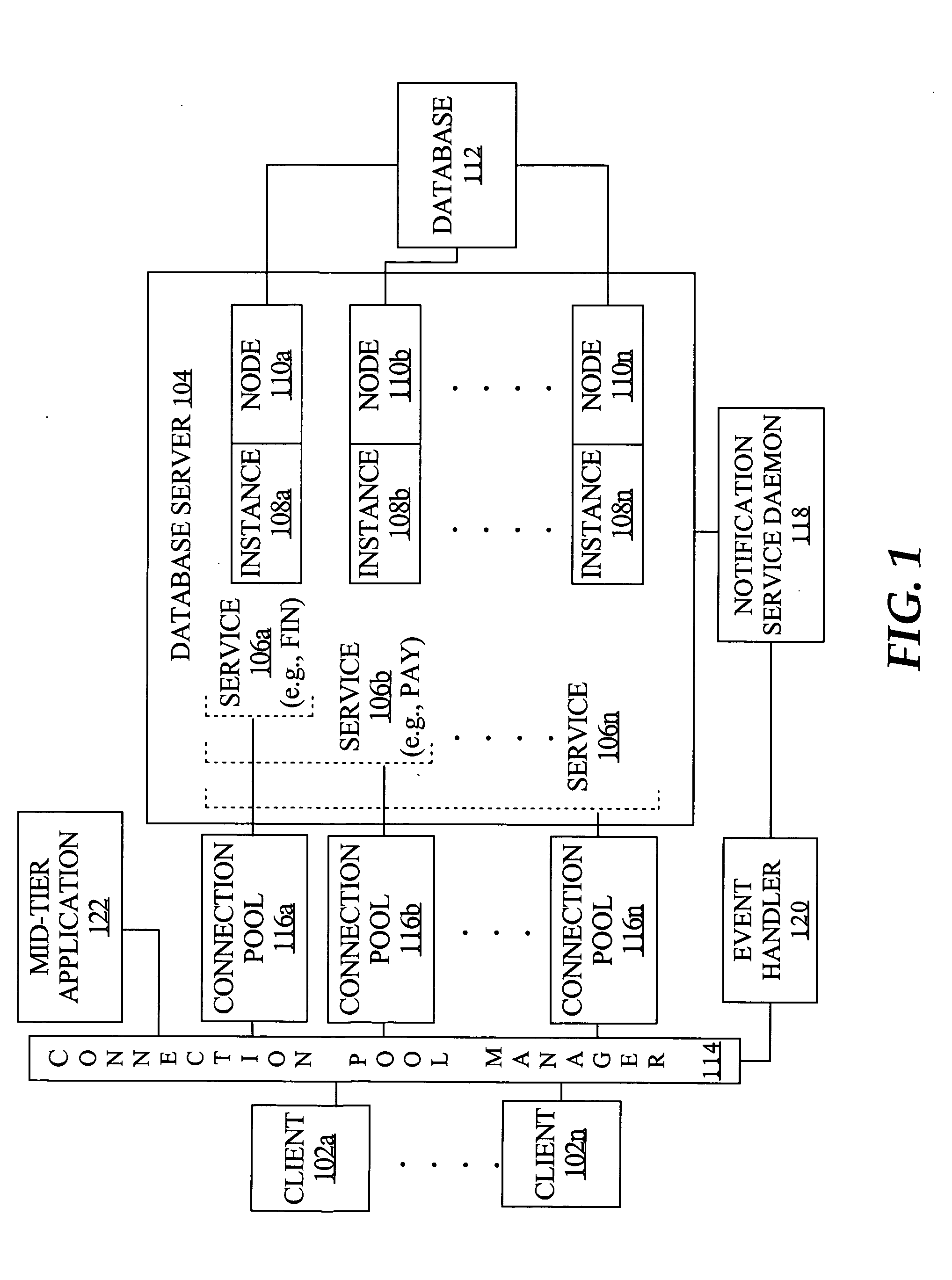
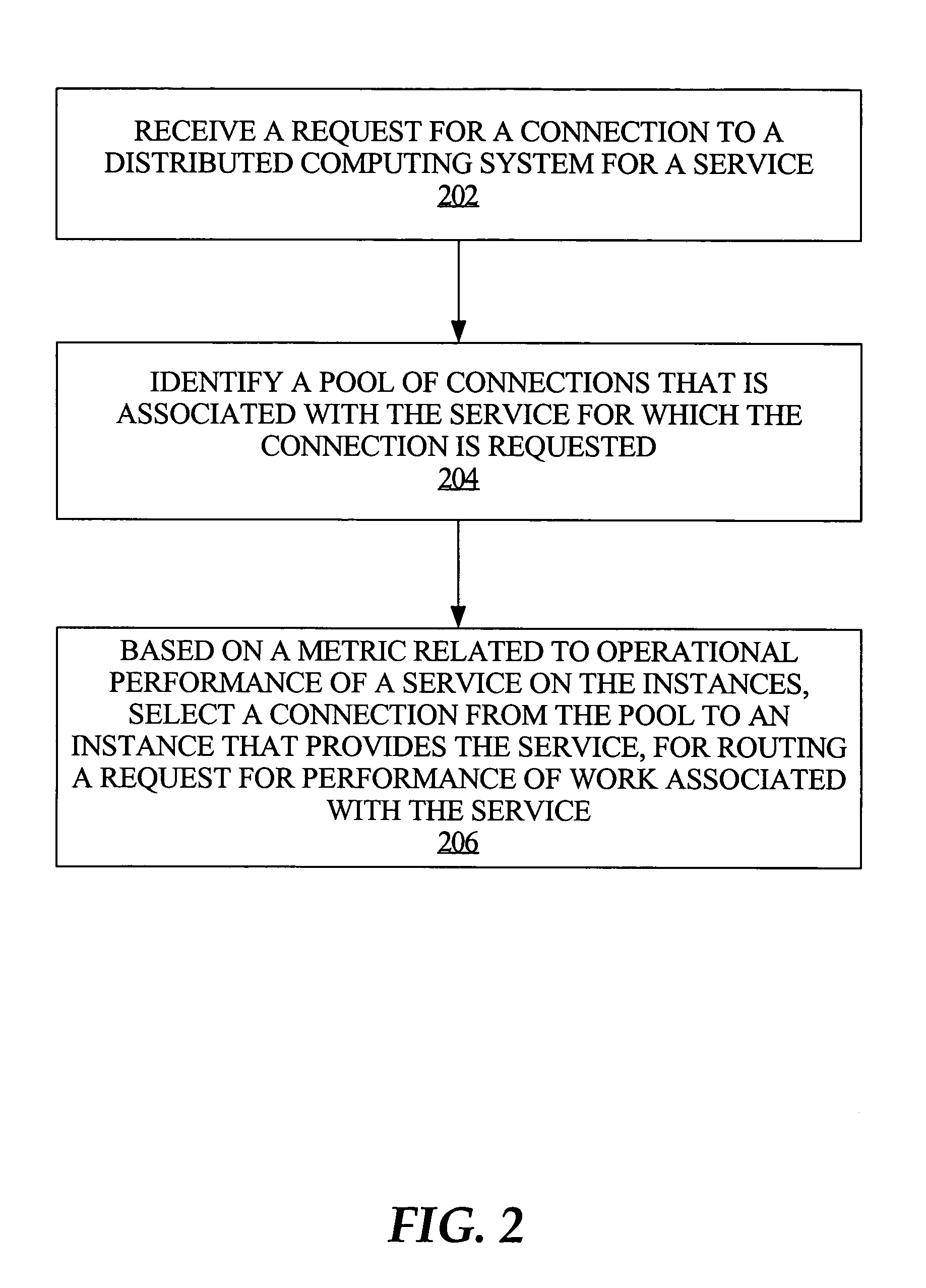
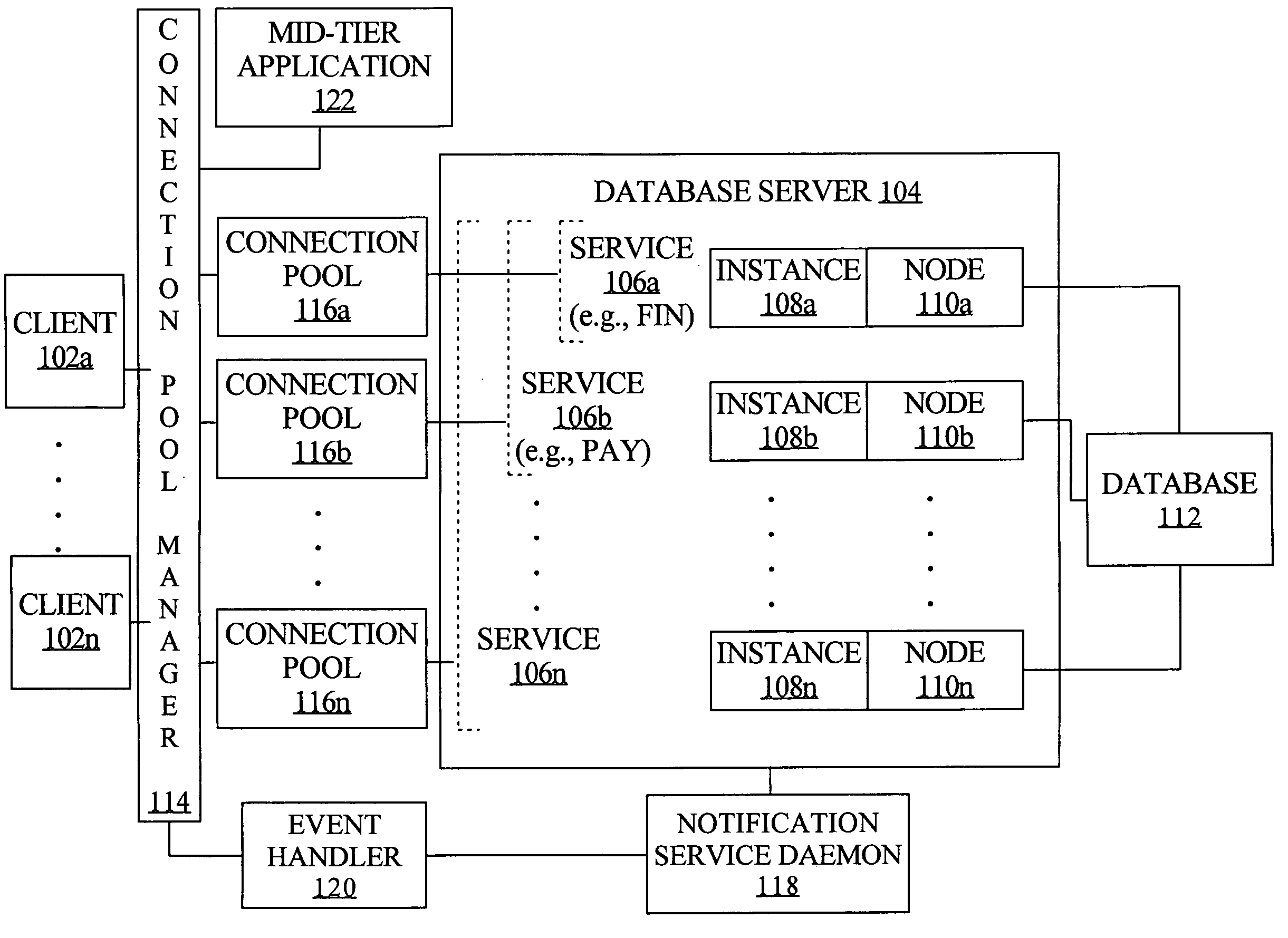
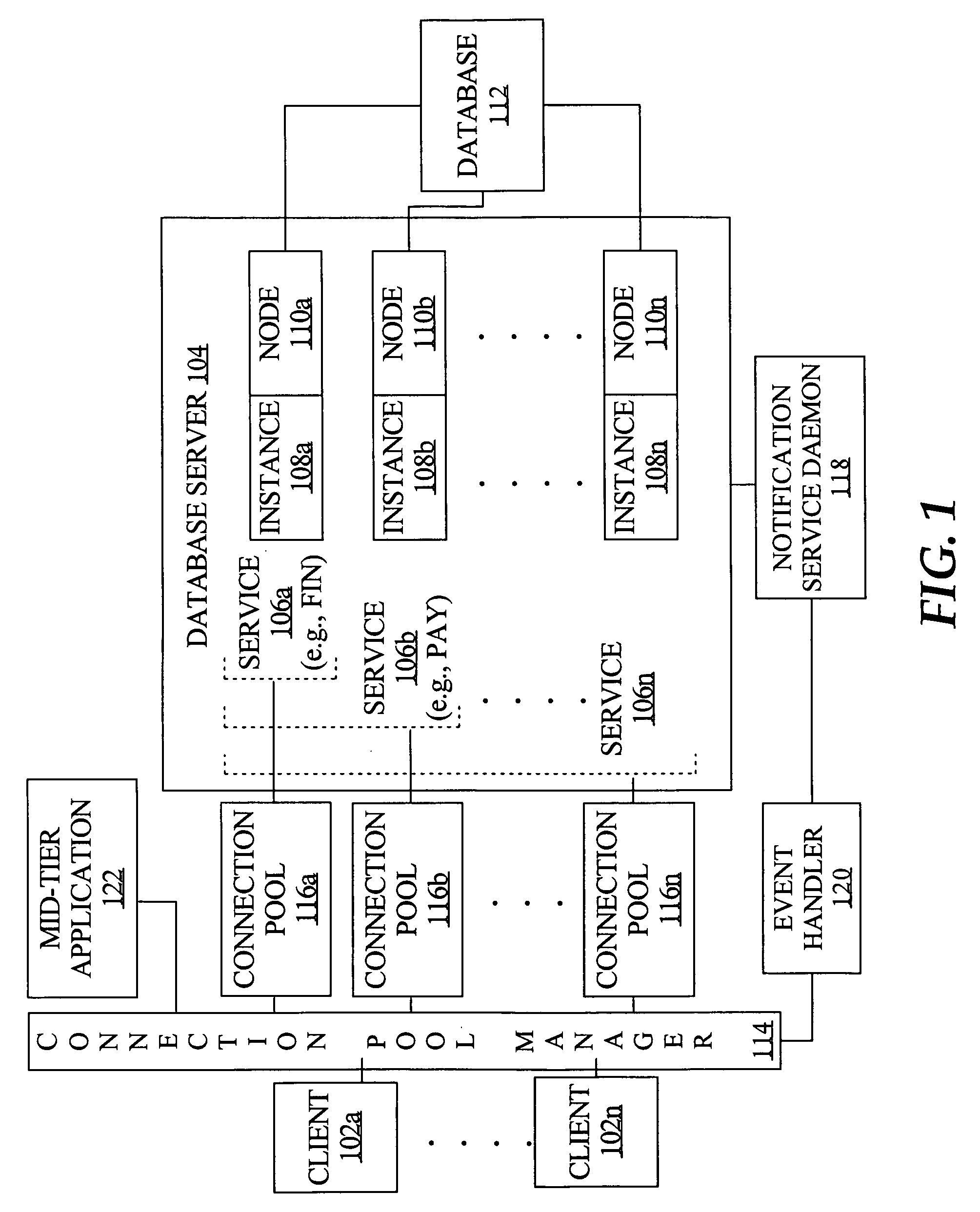
Connection pool use of runtime load balancing service performance advisories
Runtime connection load balancing of work across connections to a clustered computing system involves the routing of requests for a service, based on the current operational performance of each of the instances that offer the service. A connection is selected from an identified connection pool, to connect to an instance that provides the service for routing a work request. The operational performance of the instances may be represented by performance information that characterizes the response time and / or the throughput of the service that is provided by a particular instance on a respective node of the system, and is relative to other instances that offer the same service.
Owner:ORACLE INT CORP
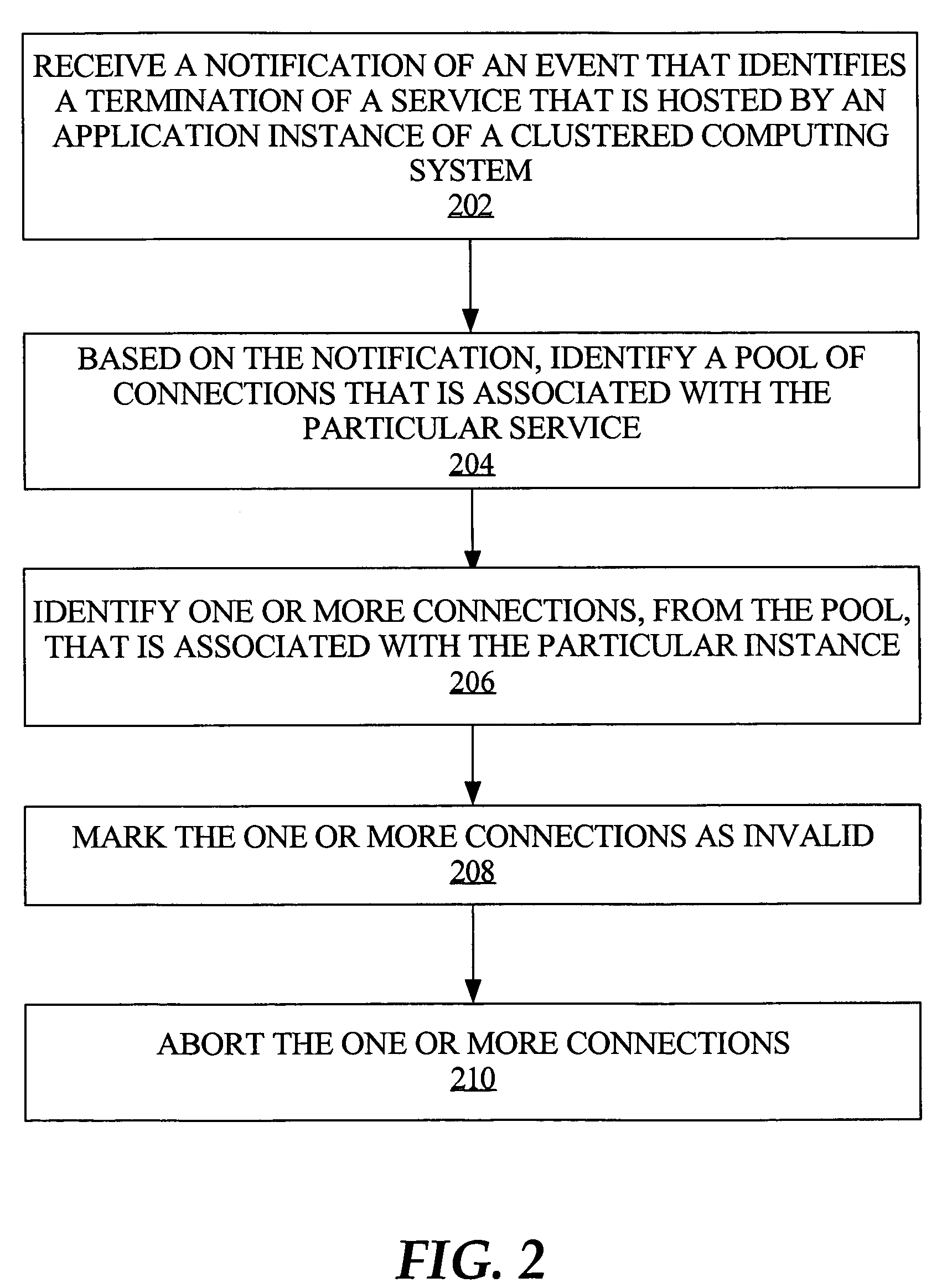
Fast reorganization of connections in response to an event in a clustered computing system
ActiveUS20050038801A1Easy to handleRapid positioningError detection/correctionDigital data processing detailsParallel computingConnection pool
Techniques for fast recovery and / or balancing of connections to a clustered computing system provide management of such connections by determining a number of connections to load balance across nodes and by triggering creation of such connections. In one aspect, a notification of an event regarding the clustered computing system is received by a connection pool manager, a pool of connections to the system is identified based on the notification, and one or more connections from the pool are processed in response to the event. According to an embodiment, the notification comprises the identities of the service, database, server instance and machine that correspond to the event.
Owner:ORACLE INT CORP
Method and apparatus for managing operations of clustered computer systems
InactiveUS6862613B1Great and reliable protectionImprove integrityDigital computer detailsRedundant hardware error correctionAlgorithmDistributed computing
Improved techniques for managing operations of clustered computing system are disclosed. The improved techniques provide protection against potential problems encountered in operation of clustered computing. More particularly, the improved techniques can be implemented as an integral solution that provide protection against undesired partitions in space and partitions in time. The improved techniques do not require any human intervention.
Owner:ORACLE INT CORP
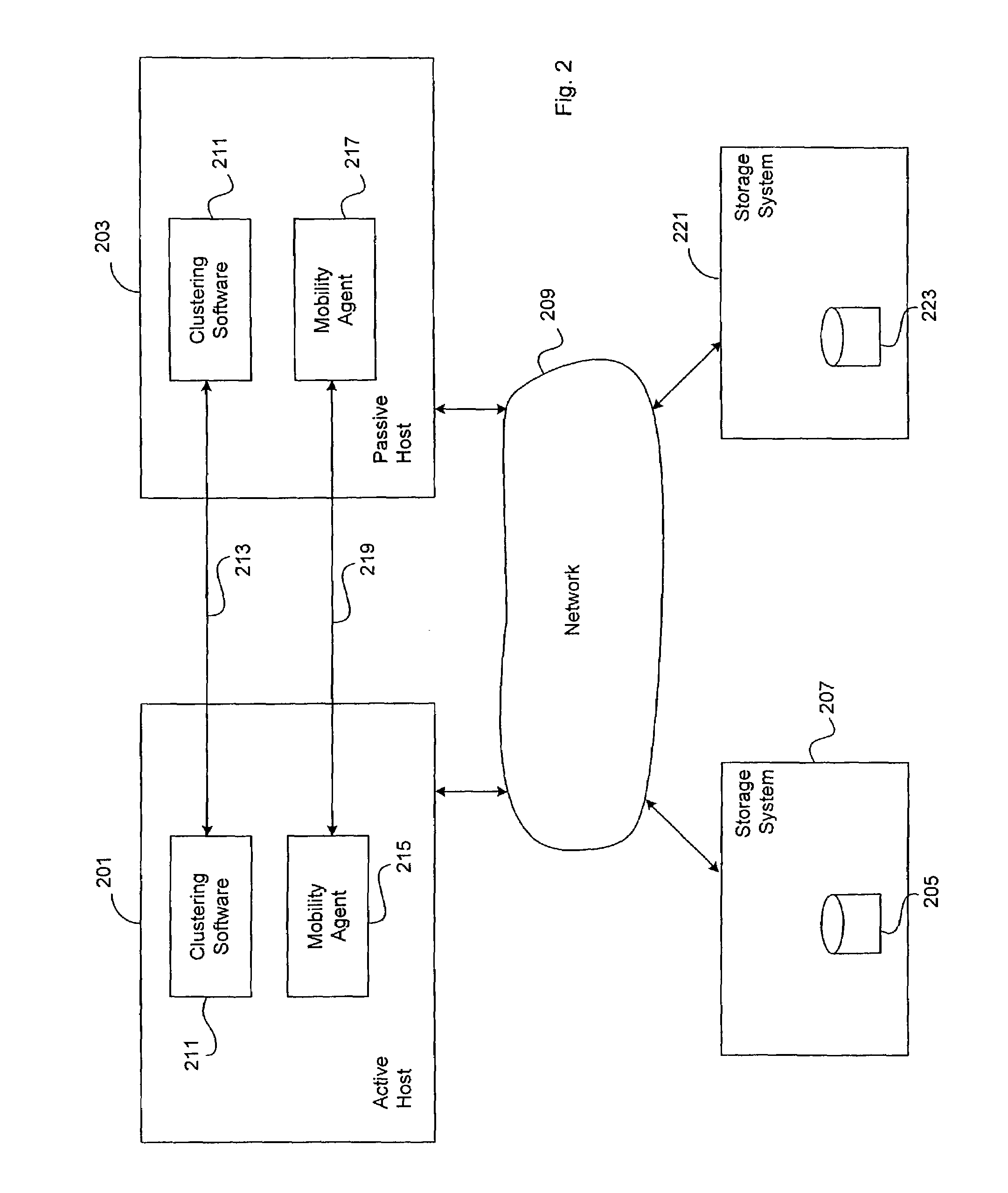
Method and apparatus for managing migration of data in a clustered computer system environment
ActiveUS7080221B1Data processing applicationsError detection/correctionData migrationDistributed computing
Methods and apparatus for performing a data migration in a clustered computer system. In one aspect, the availability of the data being migrated is maintained during the migration. In another aspect, a data set is migrated by a transfer utility in one of the hosts in the cluster, and in response to a failure of the host, the migration is resumed without restarting from the beginning point of the data set. In a further embodiment, the hosts in the cluster have agents associated therewith to manage the data migration, and prior to taking at least one action associated with the data migration, the agents coordinate to ensure that the hosts in the cluster are prepared to have the at least one action taken.
Owner:EMC IP HLDG CO LLC
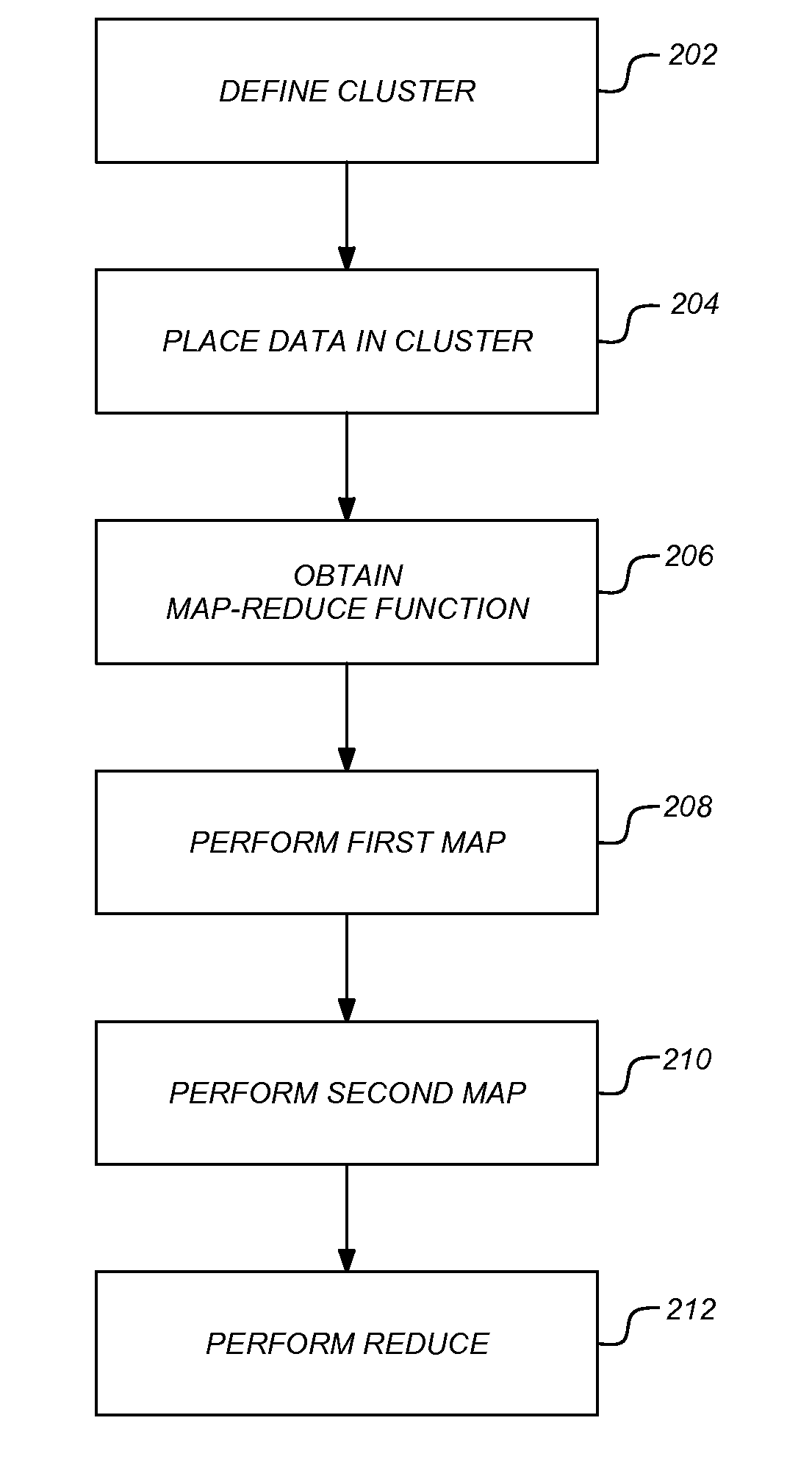
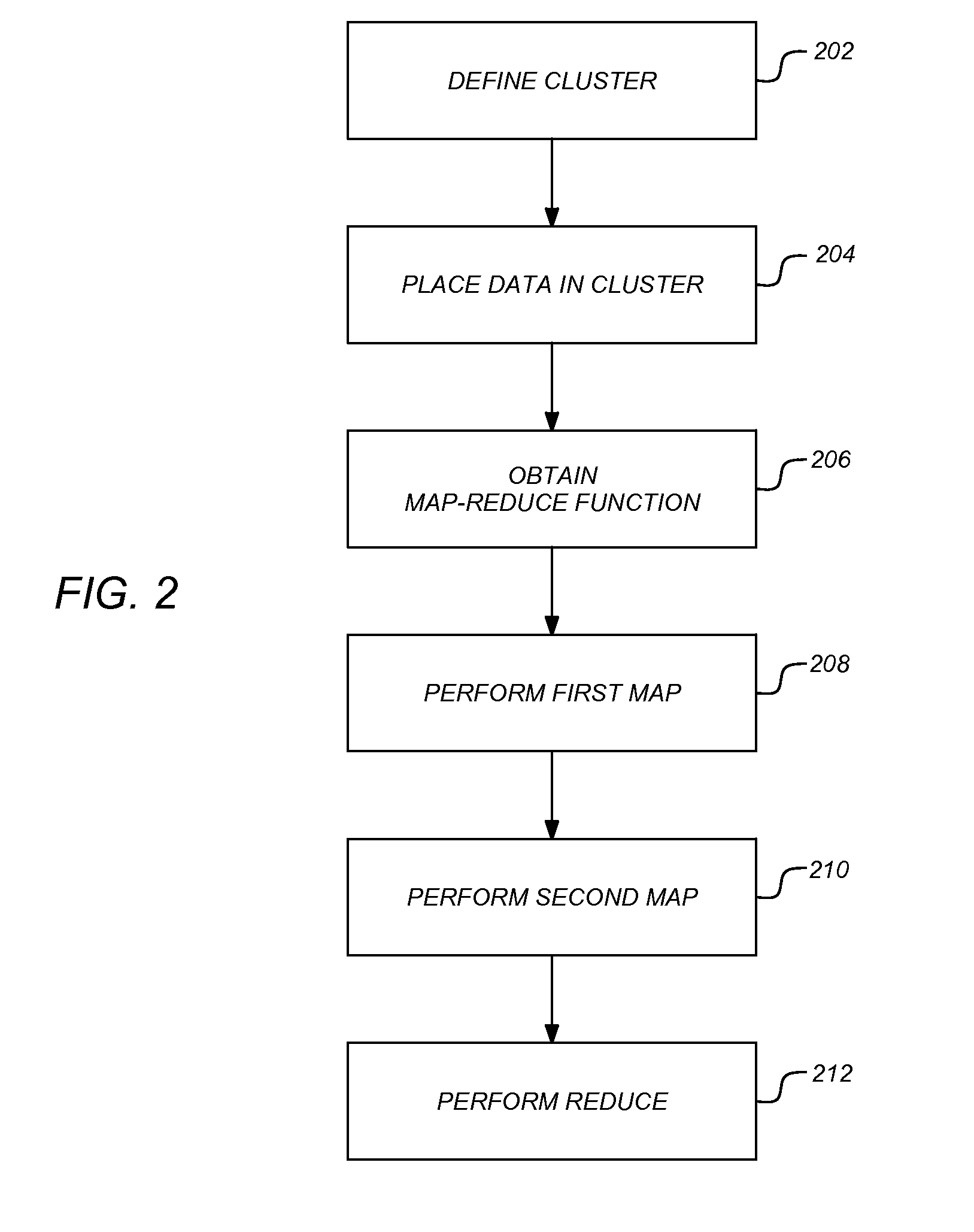
Double map reduce distributed computing framework
ActiveUS20110066649A1Create quicklyEfficient sortingDigital data processing detailsMultiple digital computer combinationsMap reduceTheoretical computer science
A method, apparatus, system, article of manufacture, and data structure provide the ability to perform a sorted map-reduce job on a cluster. A cluster of two or more computers is defined by installing a map-reduce framework onto each computer and formatting the cluster by identifying the cluster computers, establishing communication between them, and enabling the cluster to function as a unit. Data is placed into the cluster where it is distributed so that each computer contains a portion of the data. A first map function is performed where each computer sorts their respective data and creates an abstraction that is a representation of the data. The abstractions are exchanged and merged to create complete abstraction. A second map function searches the complete abstraction to redistribute and exchange the data across the computers in the cluster. A reduce function is performed in parallel to produce a result.
Owner:MYSPACE LLC
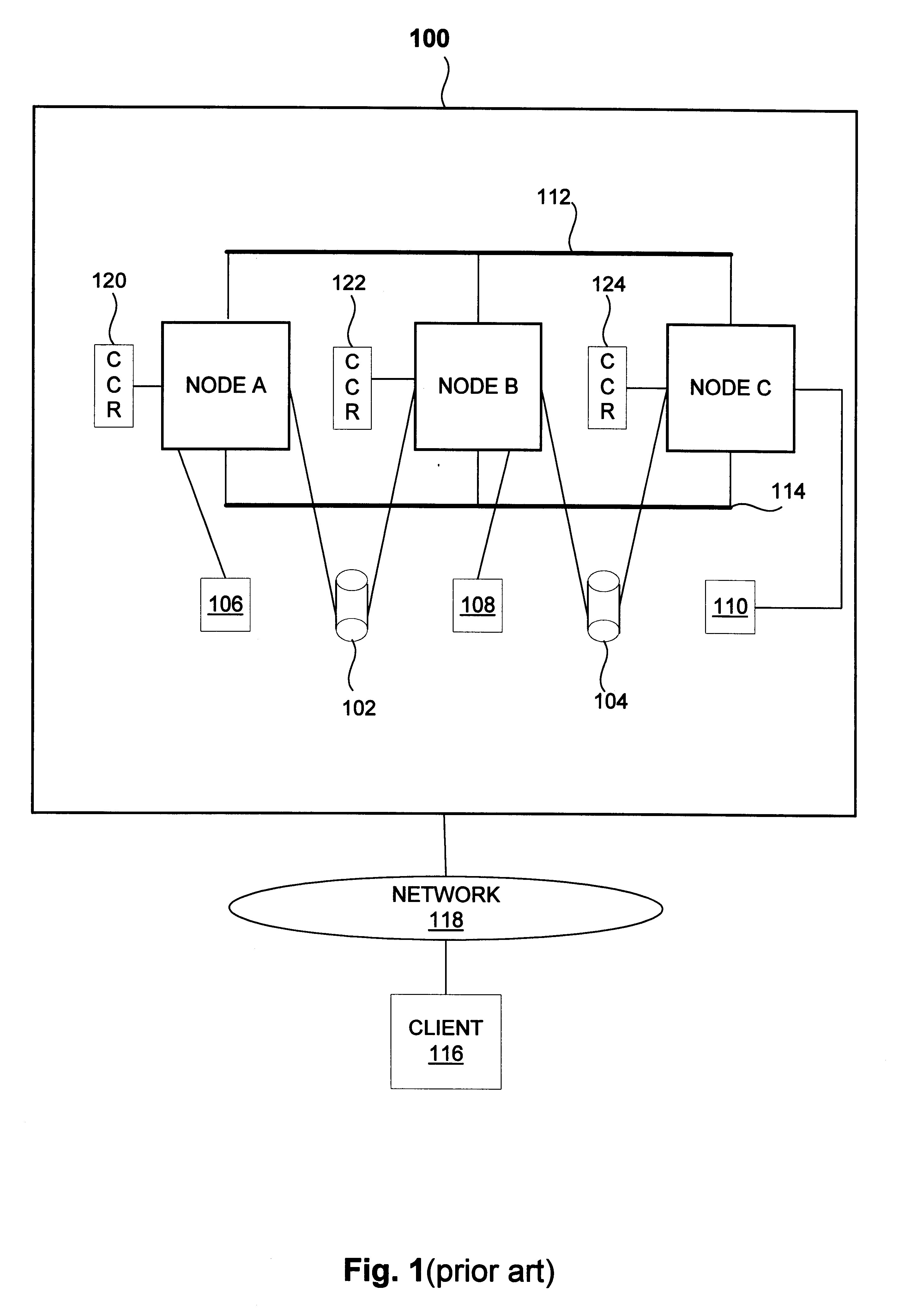
Suicide among well-mannered cluster nodes experiencing heartbeat failure
Methods for re-configuring a cluster computer system of multiple or more nodes when the cluster experiences communications failure. First and second nodes of the cluster have respective channel controllers. A SCSI channel and the controllers communicatively connect the multiple nodes. When a node becomes aware of a possible communications failure, the node attempts to determine the authenticity the failure and responds according to the determined authenticity. According to one method, a first node detects heartbeat node-to-node communications failure on the channel and then tests a physical drive on the channel. If the testing is successful, the node kills the other node. If the testing is unsuccessful, the first node commits suicide. In one embodiment, the coupling includes multiple channels communicatively coupling the first and second nodes and the first node selecting one of the channels for node-to-node communications. In this environment, choosing a physical drive involves testing node-to-node communications on another of the channels if no physical drive is online on the channel (and terminating the re-configuring method). If a drive is available, the first node uses the first physical drive online on the channel for testing. In another method, the second node initially detects communications failure and communicates that by attempting to negotiate wih the first node for a new configuration of the computer system. The first node tests a physical drive in response and negotiates with the second node if the testing was successful. If the testing was unsuccessful, the first node commits suicide.
Owner:XYRATEX TECH LTD
Method and apparatus for migrating data in a clustered computer system environment
ActiveUS7805583B1Memory systemsInput/output processes for data processingData setDistributed computing
Methods and apparatus for performing a data migration in a clustered computer system. In one aspect, the availability of the data being migrated is maintained during the migration. In another aspect, a data set is migrated by a transfer utility in one of the hosts in the cluster, and in response to a failure of the host, the migration is resumed without restarting from the beginning point of the data set. In a further embodiment, the hosts in the cluster have agents associated therewith to manage the data migration, and prior to taking at least one action associated with the data migration, the agents coordinate to ensure that the hosts in the cluster are prepared to have the at least one action taken.
Owner:EMC IP HLDG CO LLC
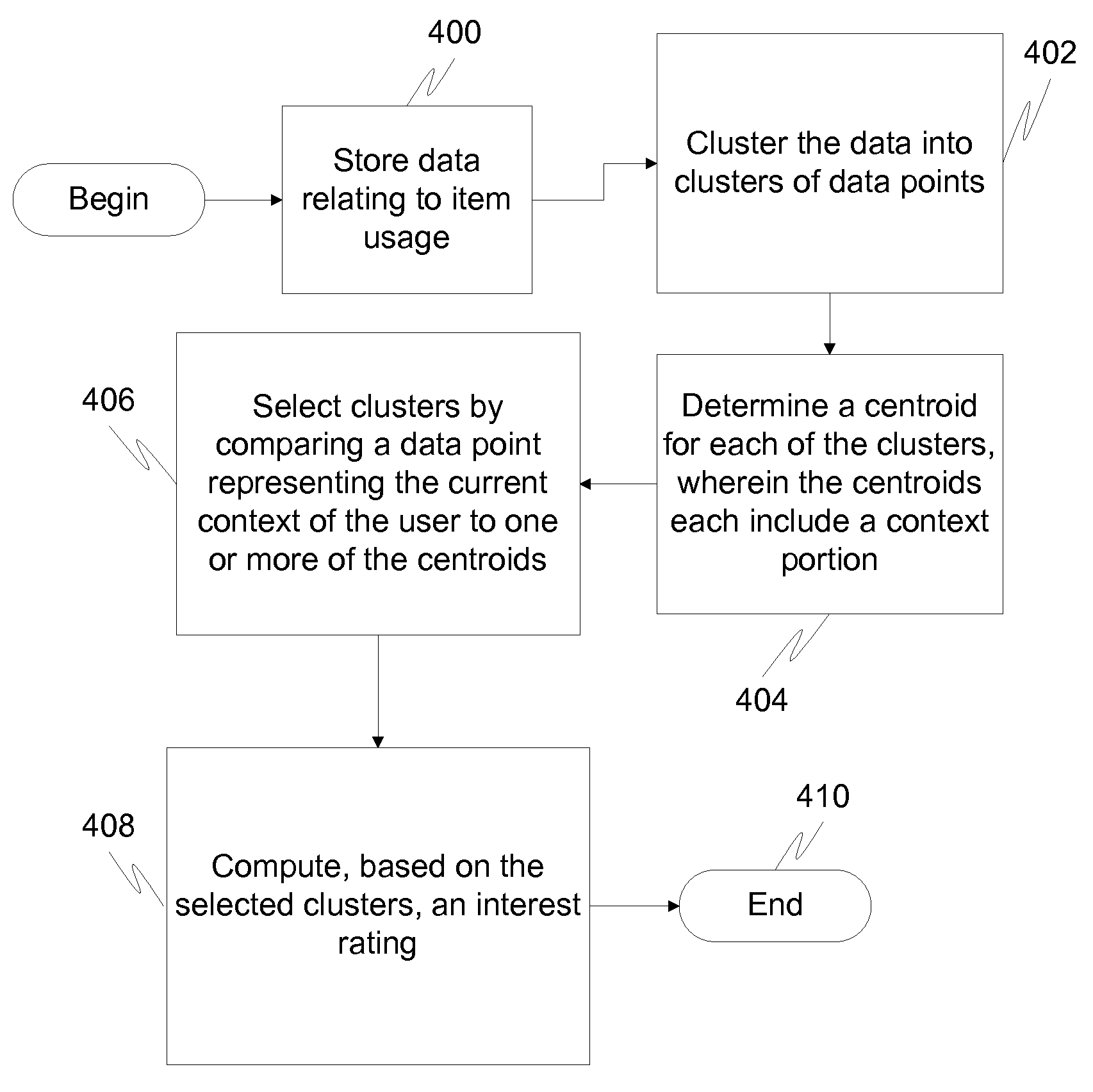
Clustering-based interest computation
InactiveUS20090307176A1Digital data information retrievalDigital data processing detailsData miningCluster based
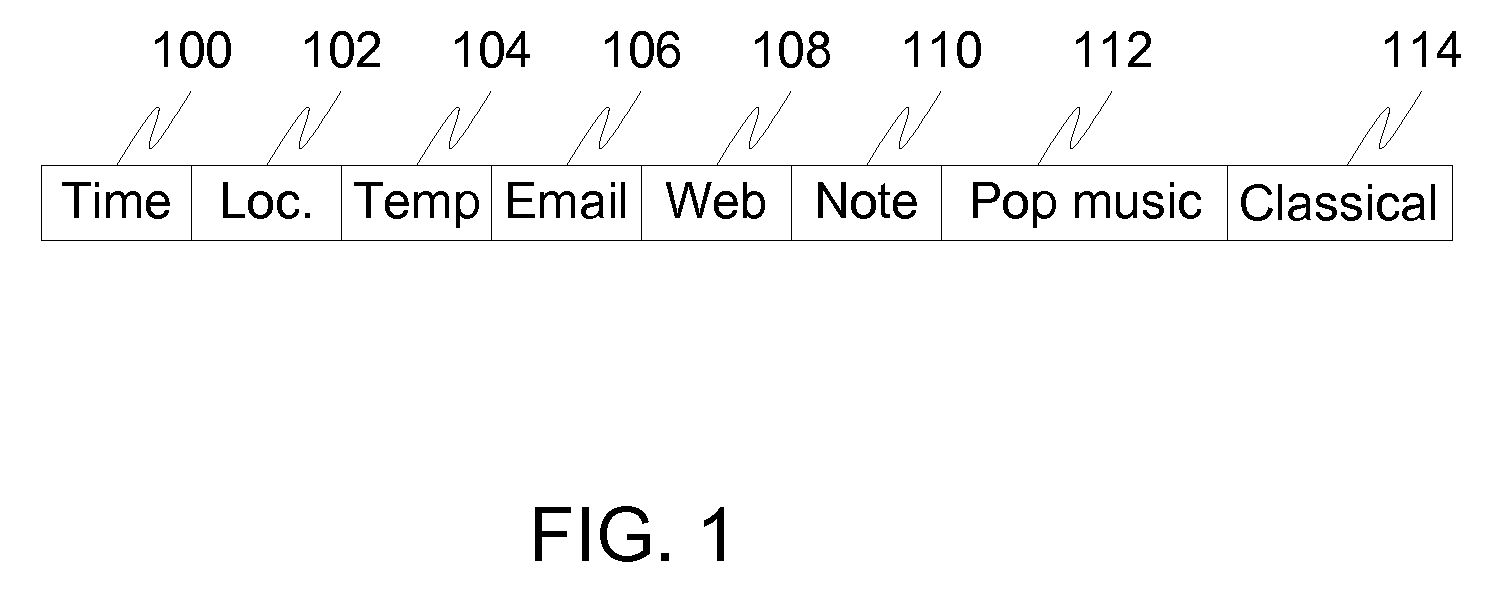
Data relating to usage patterns of the user are stored. The data includes a context portion having information as to the context in which items were used and an interest rating portion indicative of an interest of the user in one or more objects of interest. The data is clustered into clusters of data points. For each of the clusters, a centroid is determined. The centroid includes a context portion and an interest rating portion. A current context of the user is received. Clusters are selected by comparing a data point representing the current context with the context portion of one or more centroids. Based on the selected clusters, an interest rating is computed. The computed interest rating indicates an interest of the user in one of the one or more objects of interest, given the current context.
Owner:SAMSUNG ELECTRONICS CO LTD
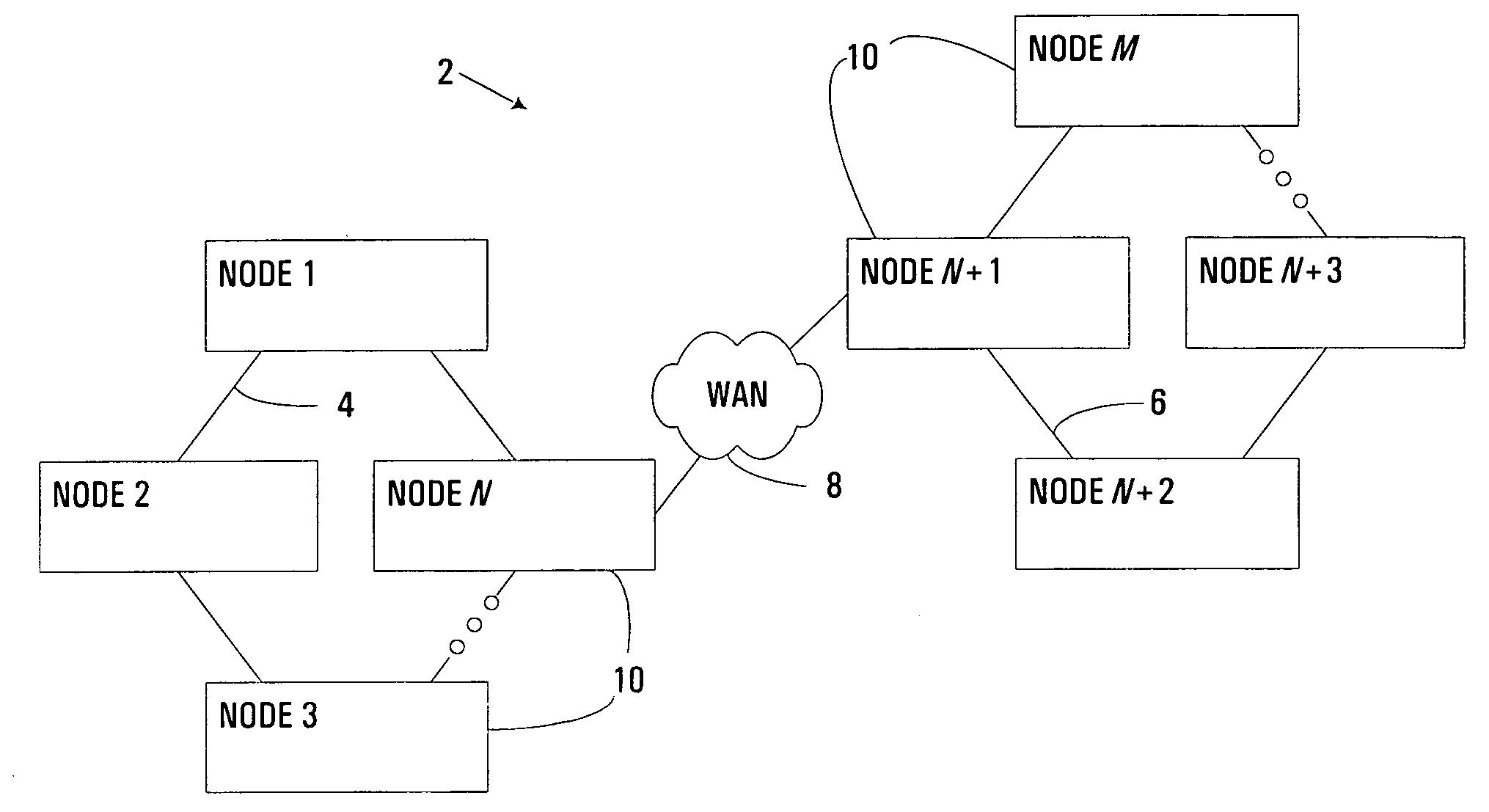
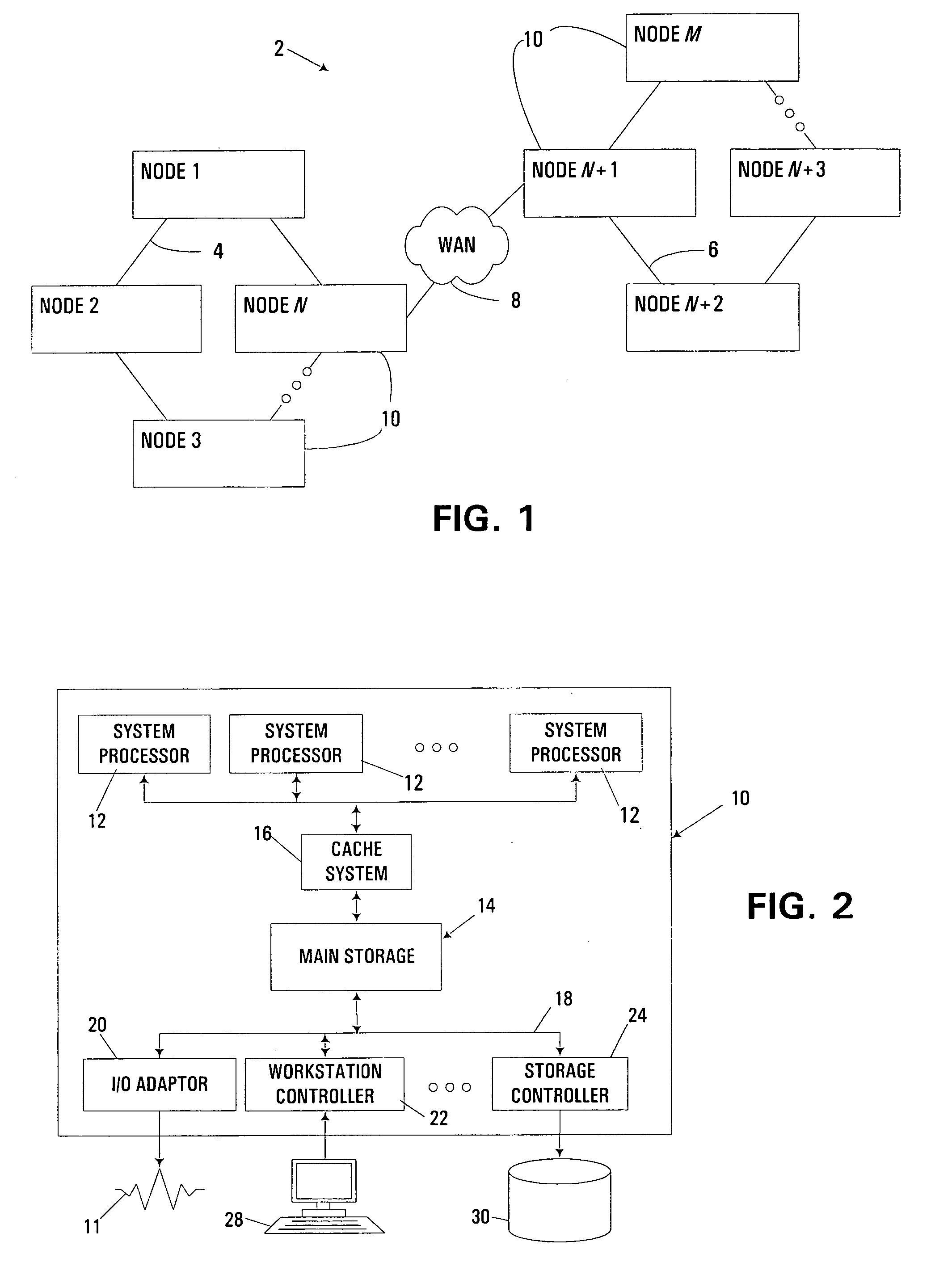
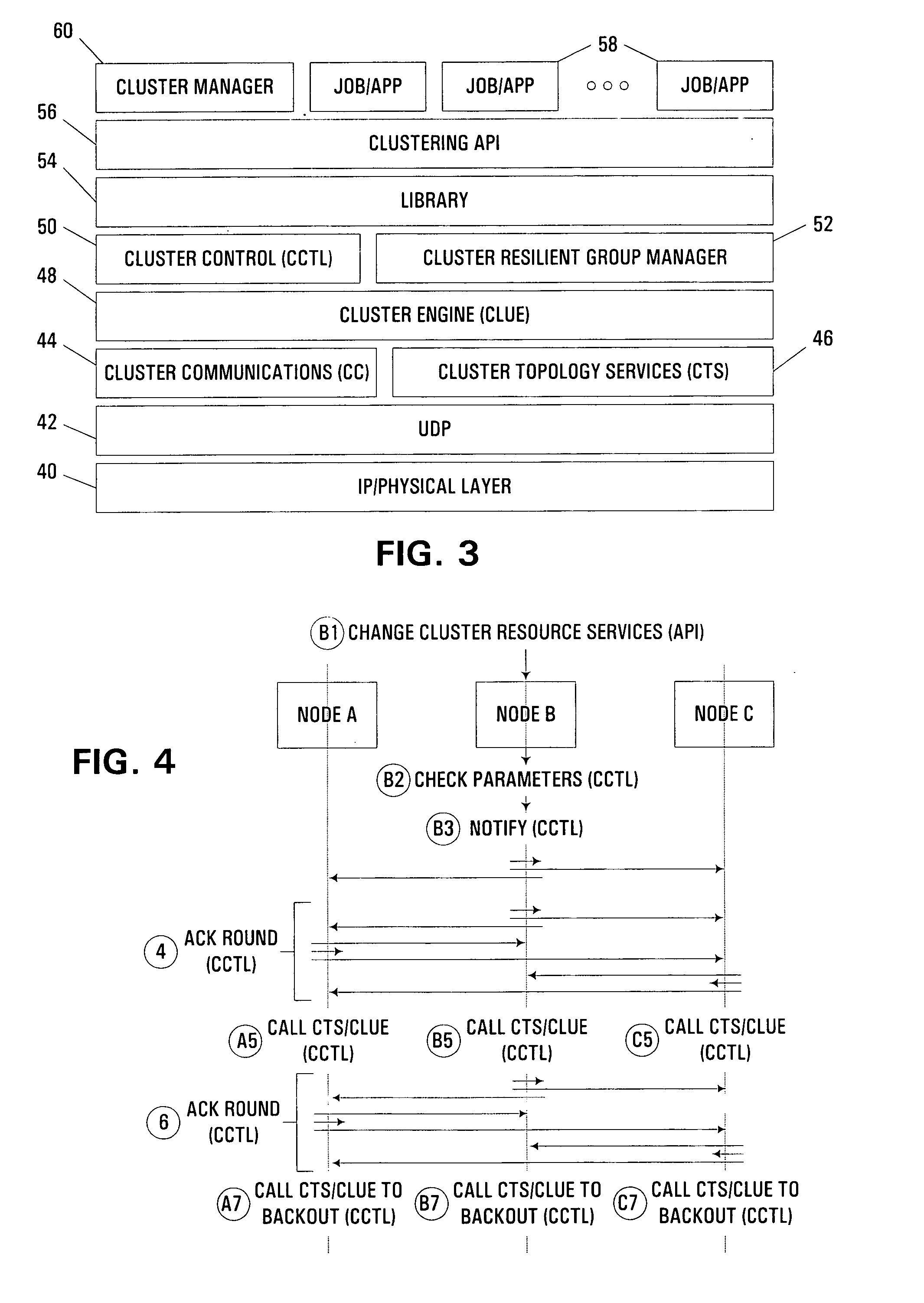
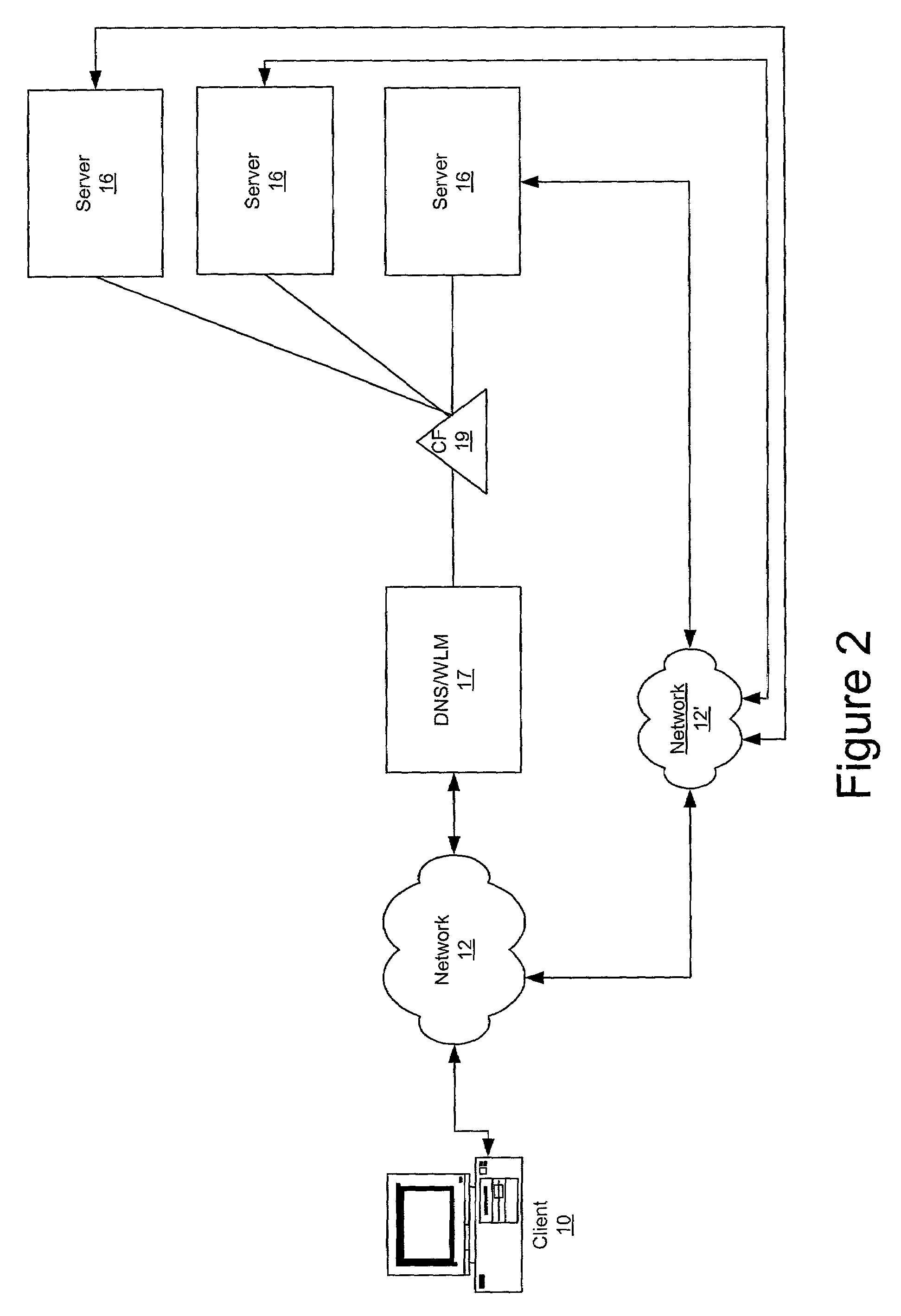
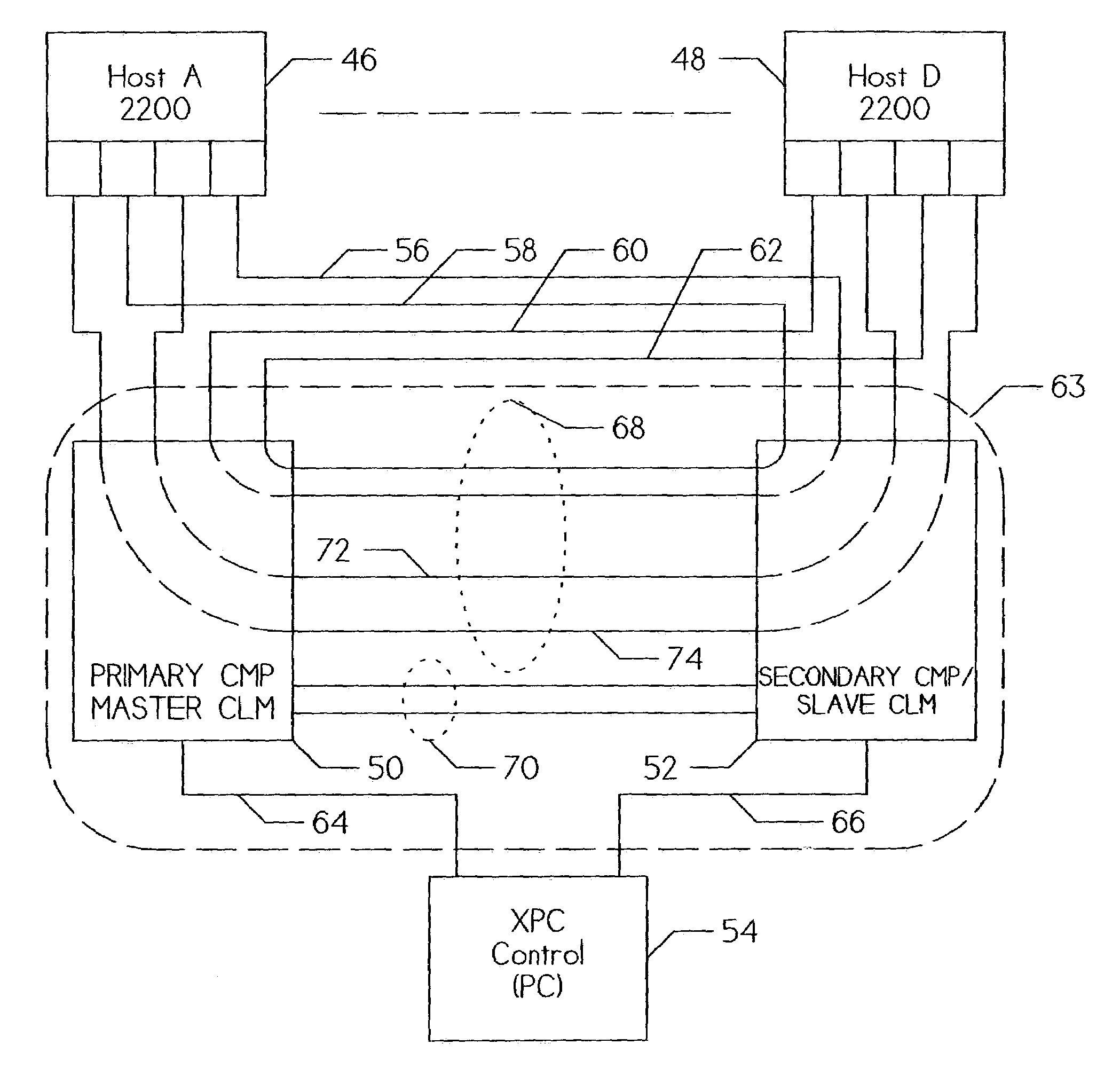
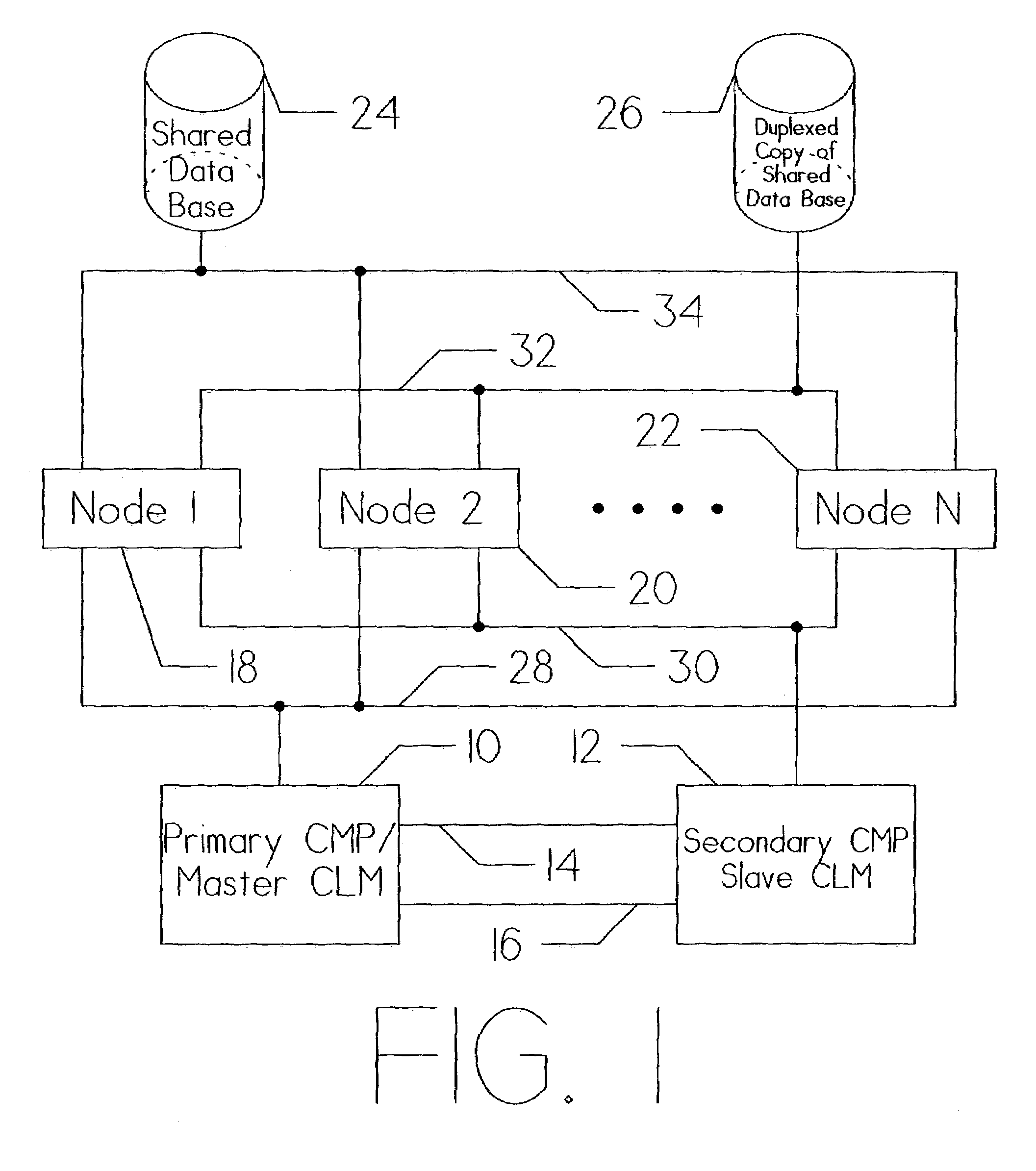
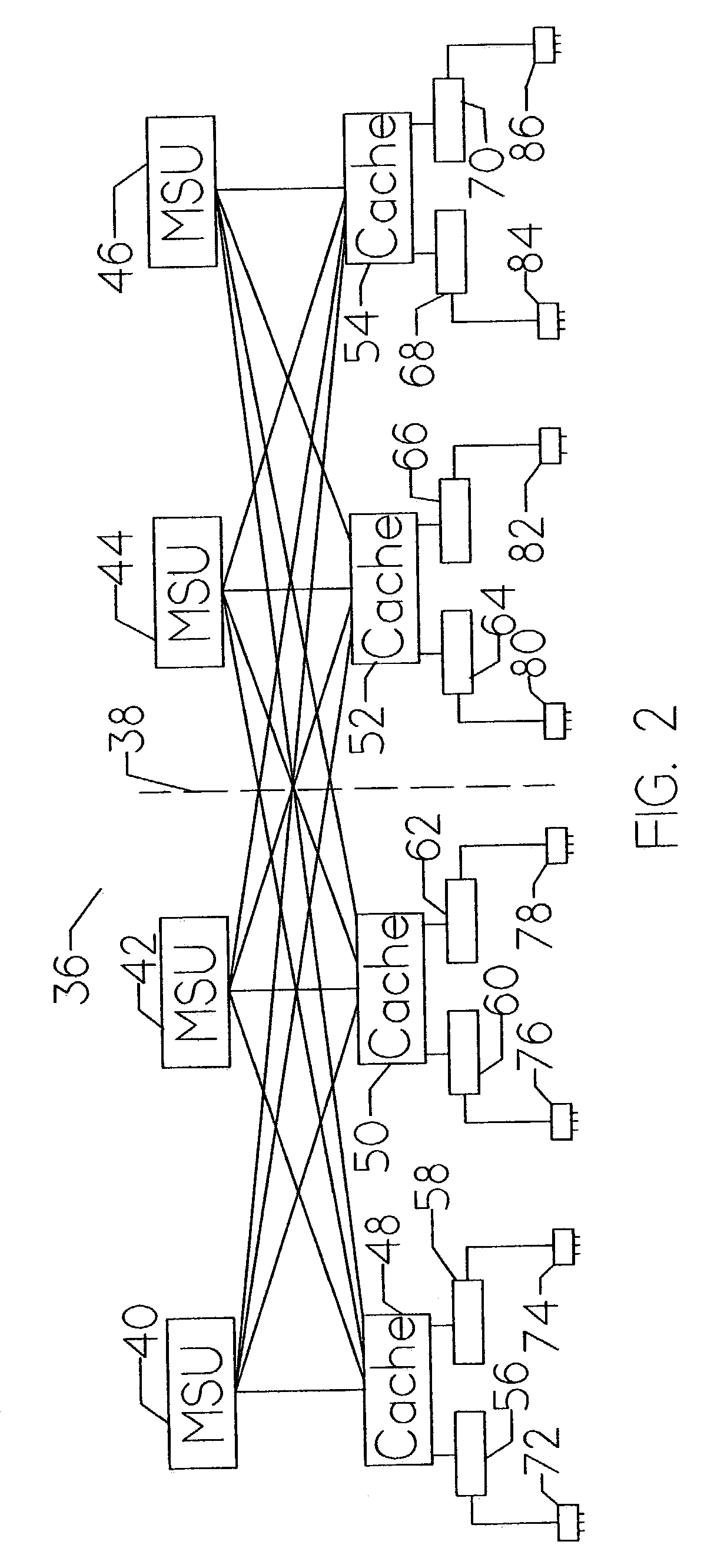
Clustered computing model and display
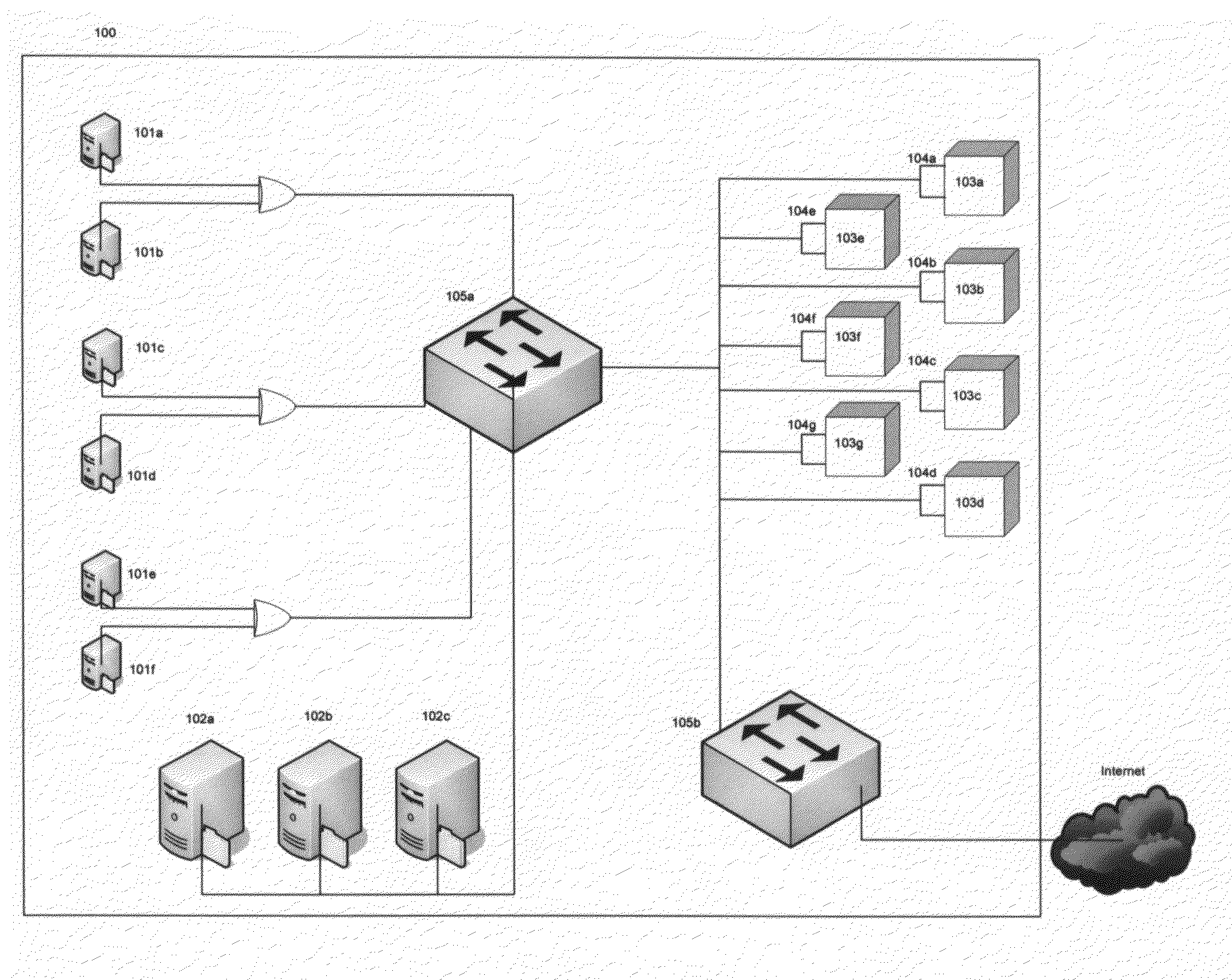
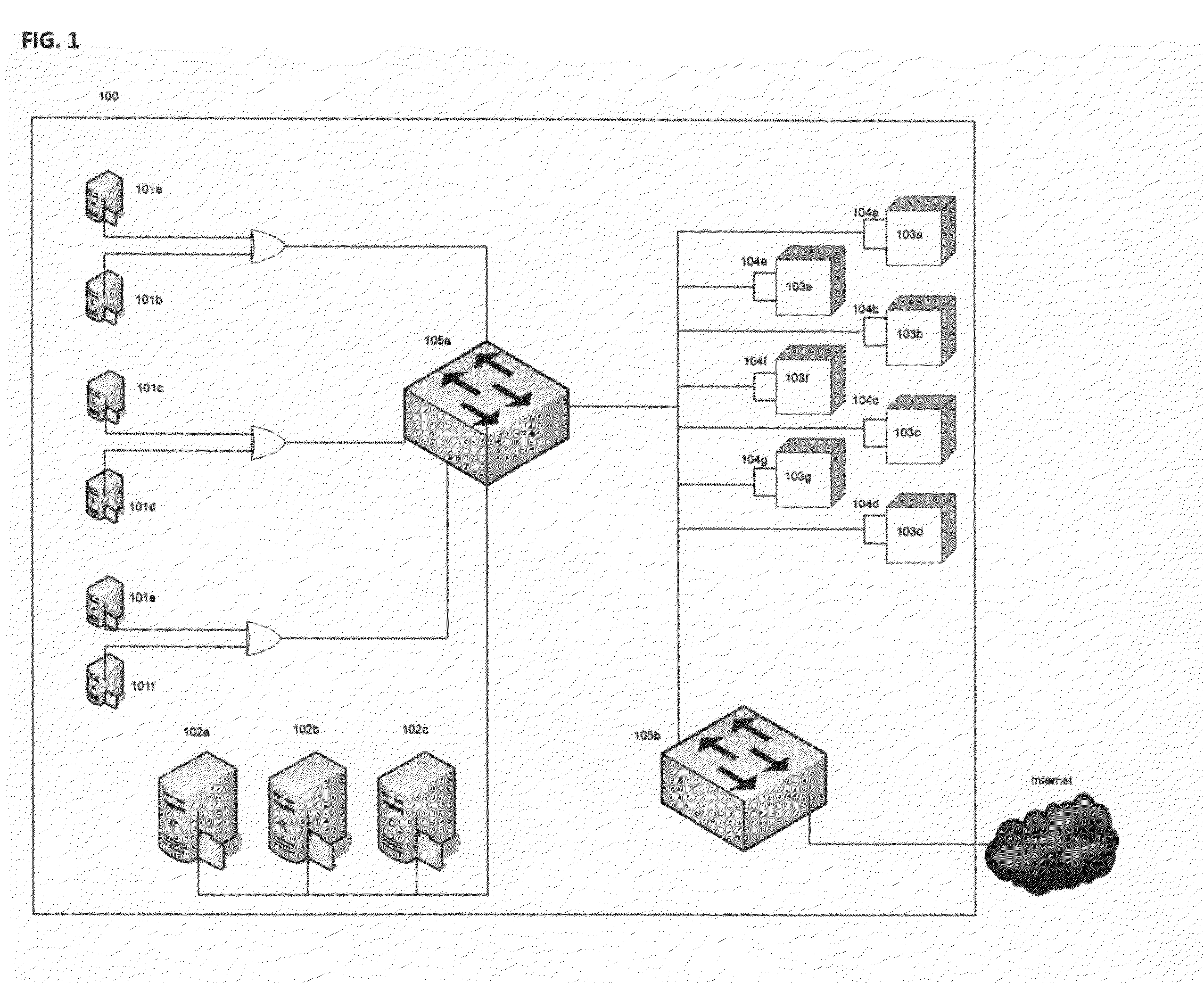
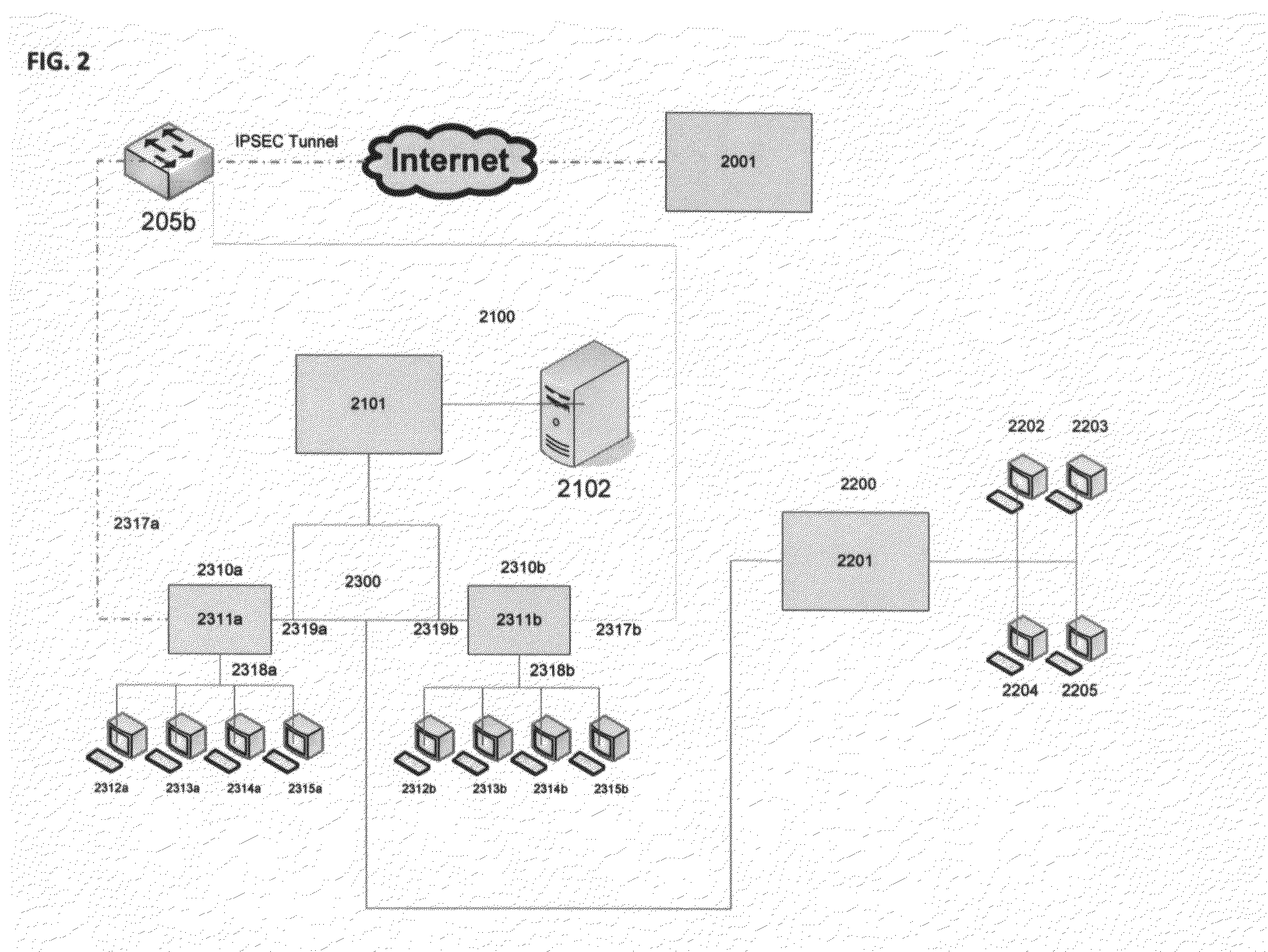
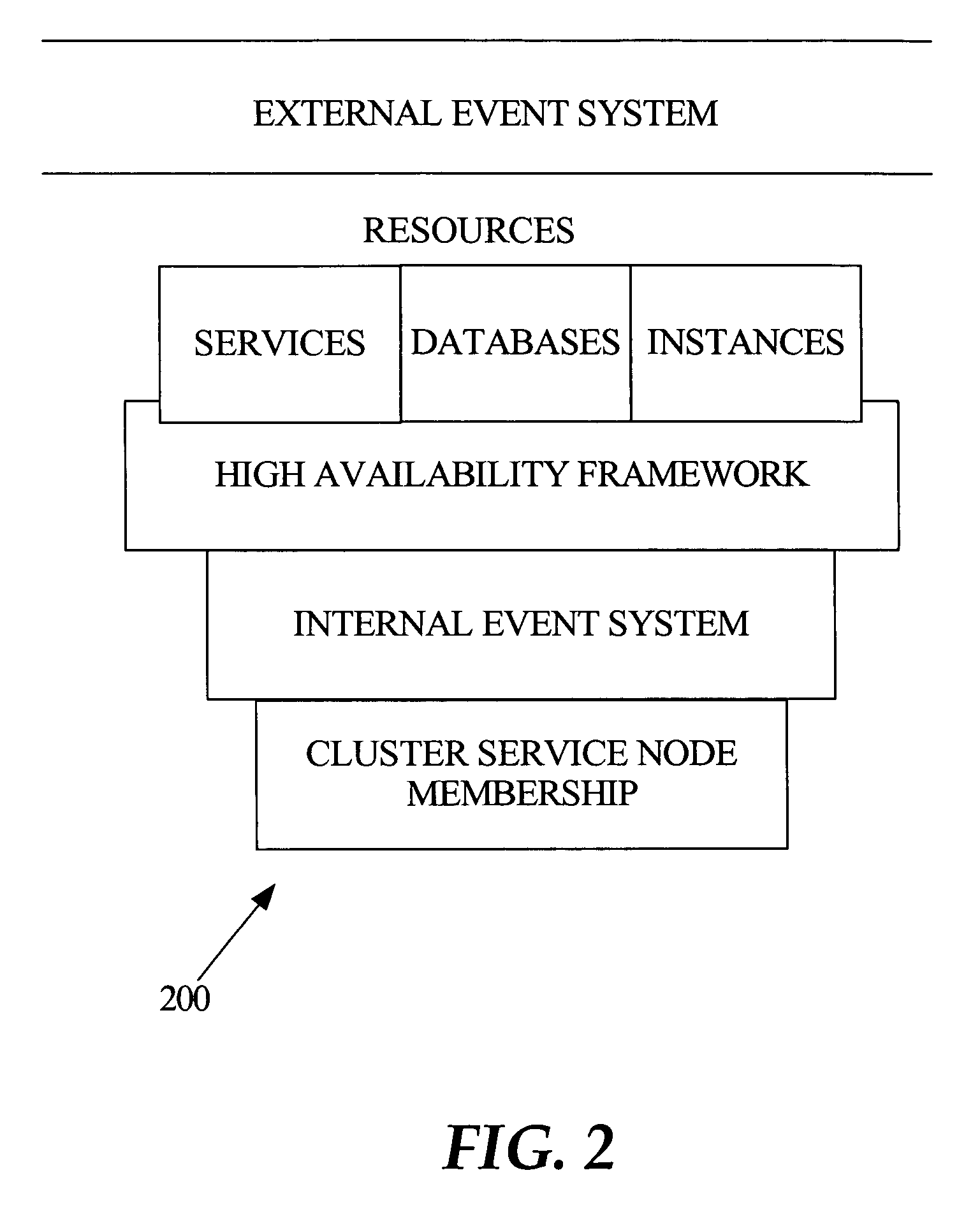
InactiveUS7555549B1Improve performanceSure easyDigital computer detailsHybrid transportDistributed computingSwarm computing
Owner:INTEL CORP
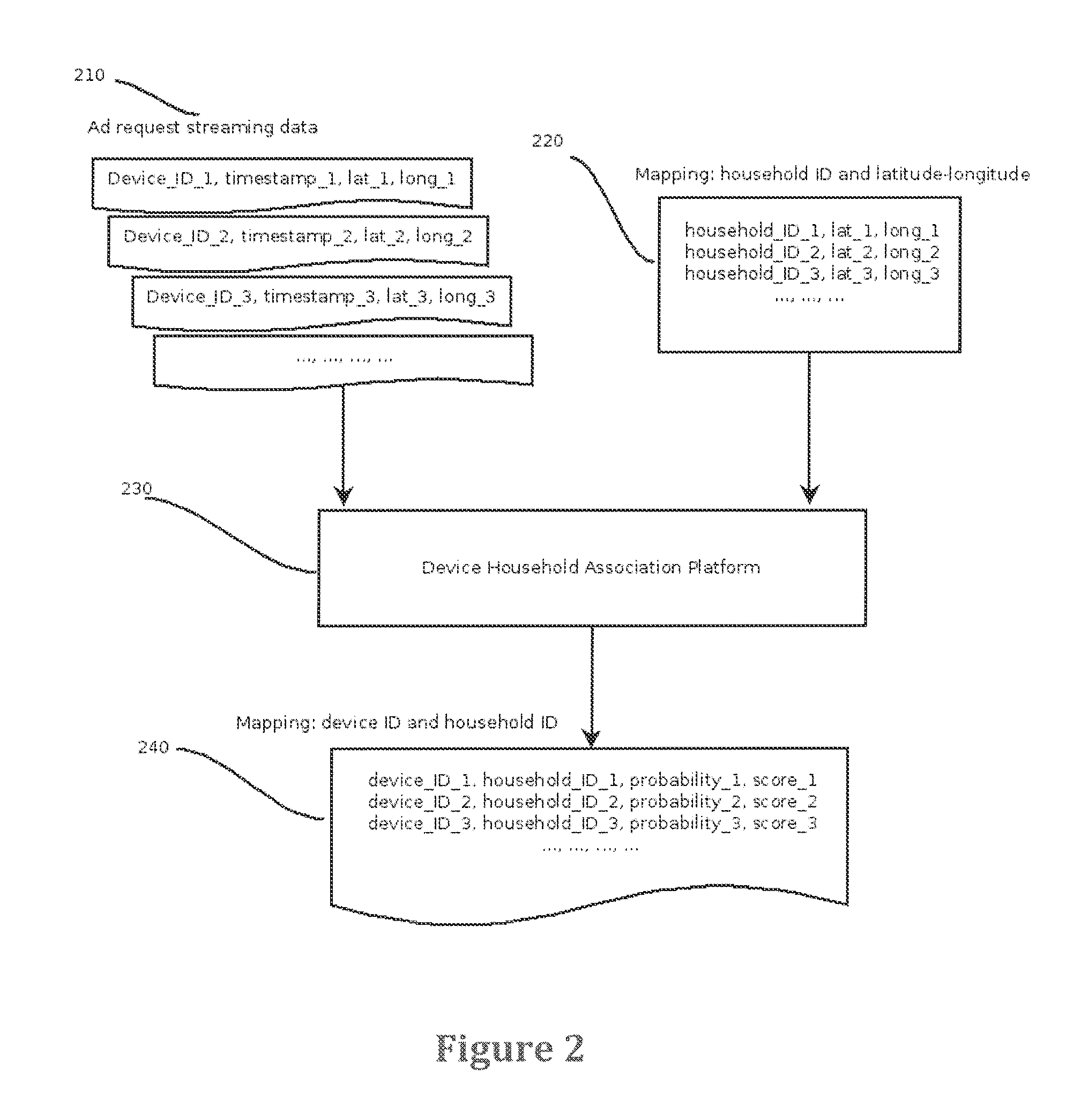
Systems and methods for statistically associating mobile devices to households
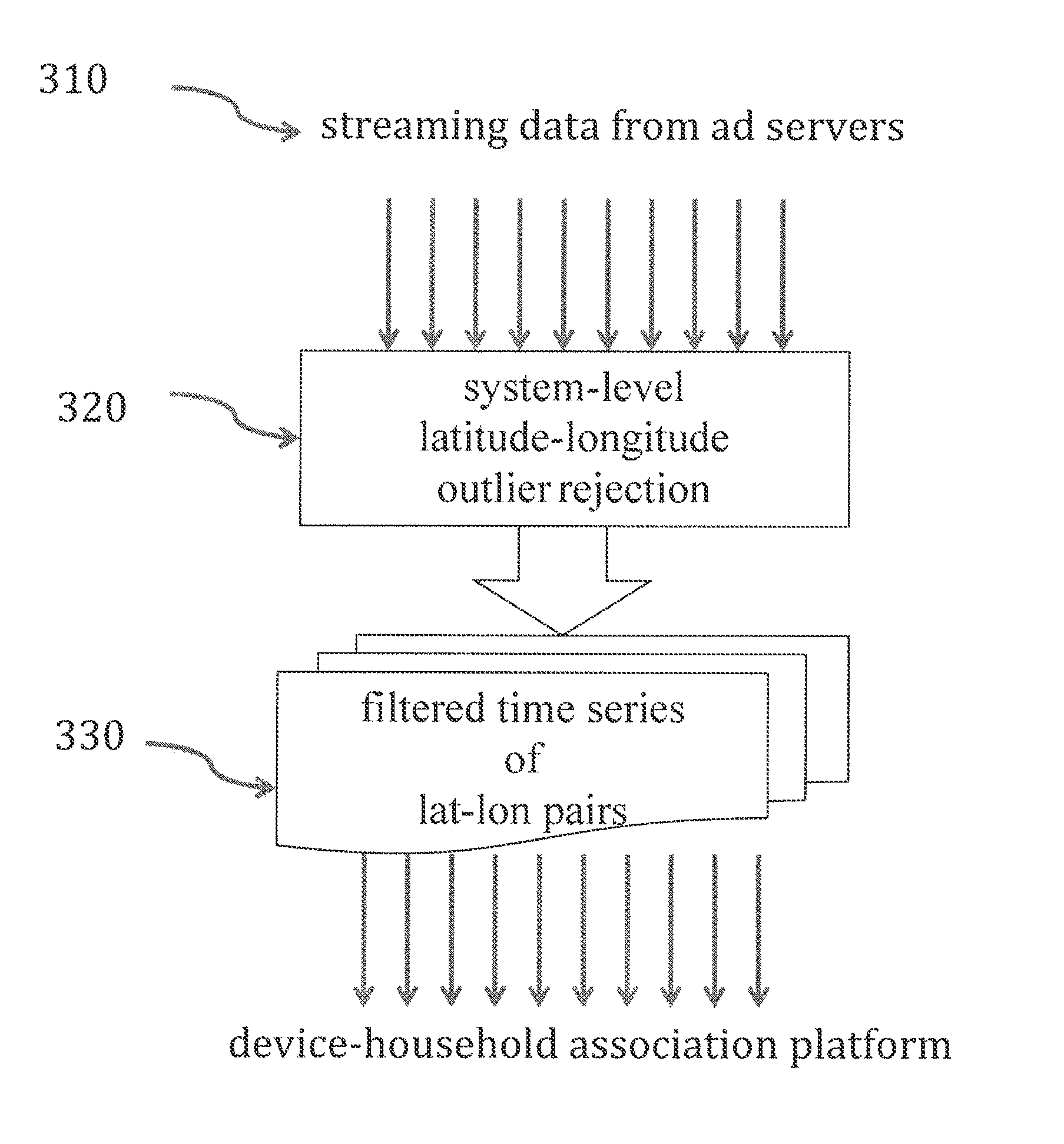
Embodiments of the invention relate to methods and systems for associating a mobile device to a household. In various embodiments, a plurality of latitude-longitude pairs is received for a mobile device during a time period. The latitude-longitude pairs are organized into a plurality of clusters corresponding to geographic regions visited by the mobile device during the time period. For each cluster, a score is calculated that represents a likelihood that a user of the mobile device resides in a household within the cluster. The cluster with the highest score is identified as being the location of the user's household. The computation is preferably conducted recursively over time periods. The mobile device is then associated with the user's household.
Owner:CADENT LLC
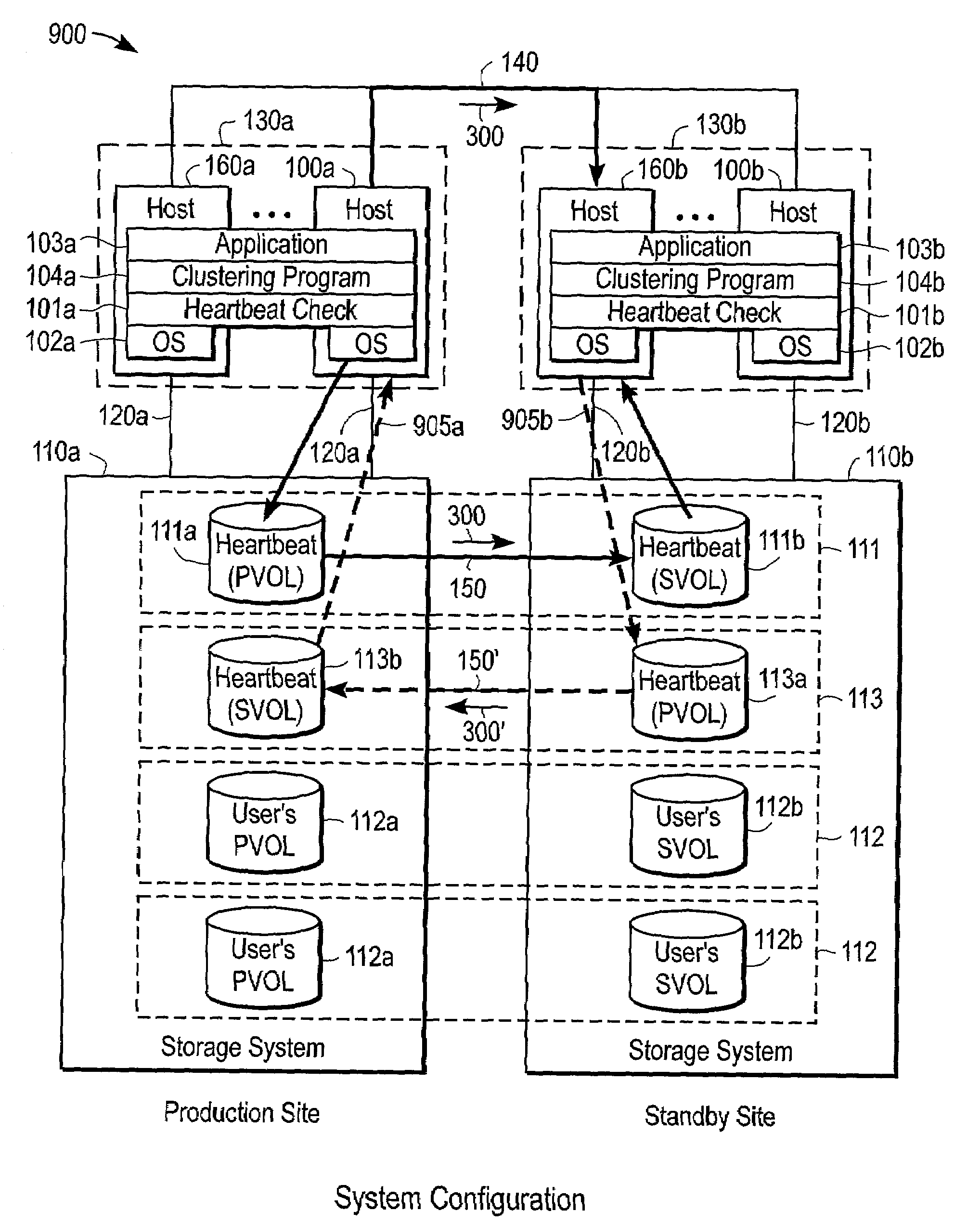
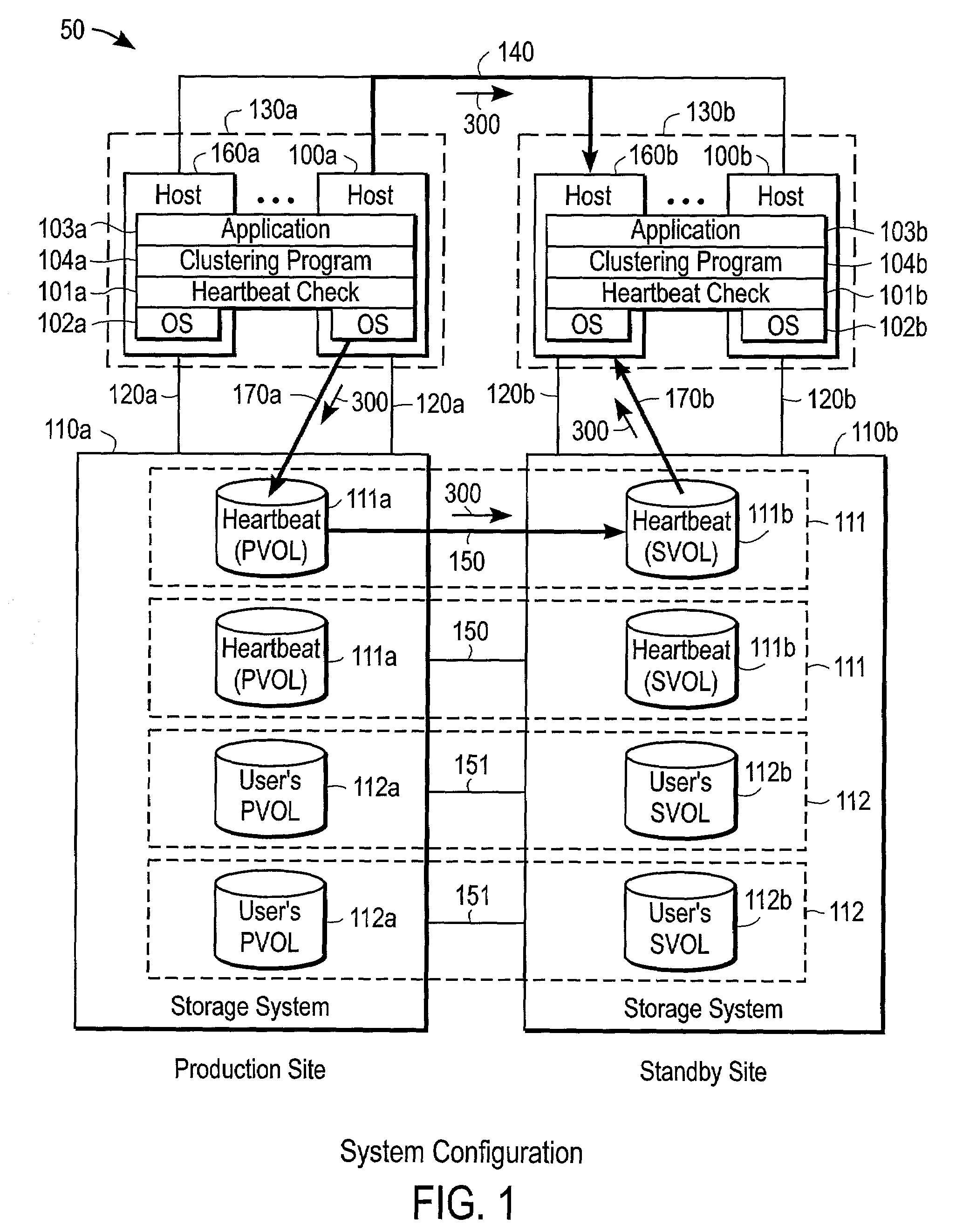
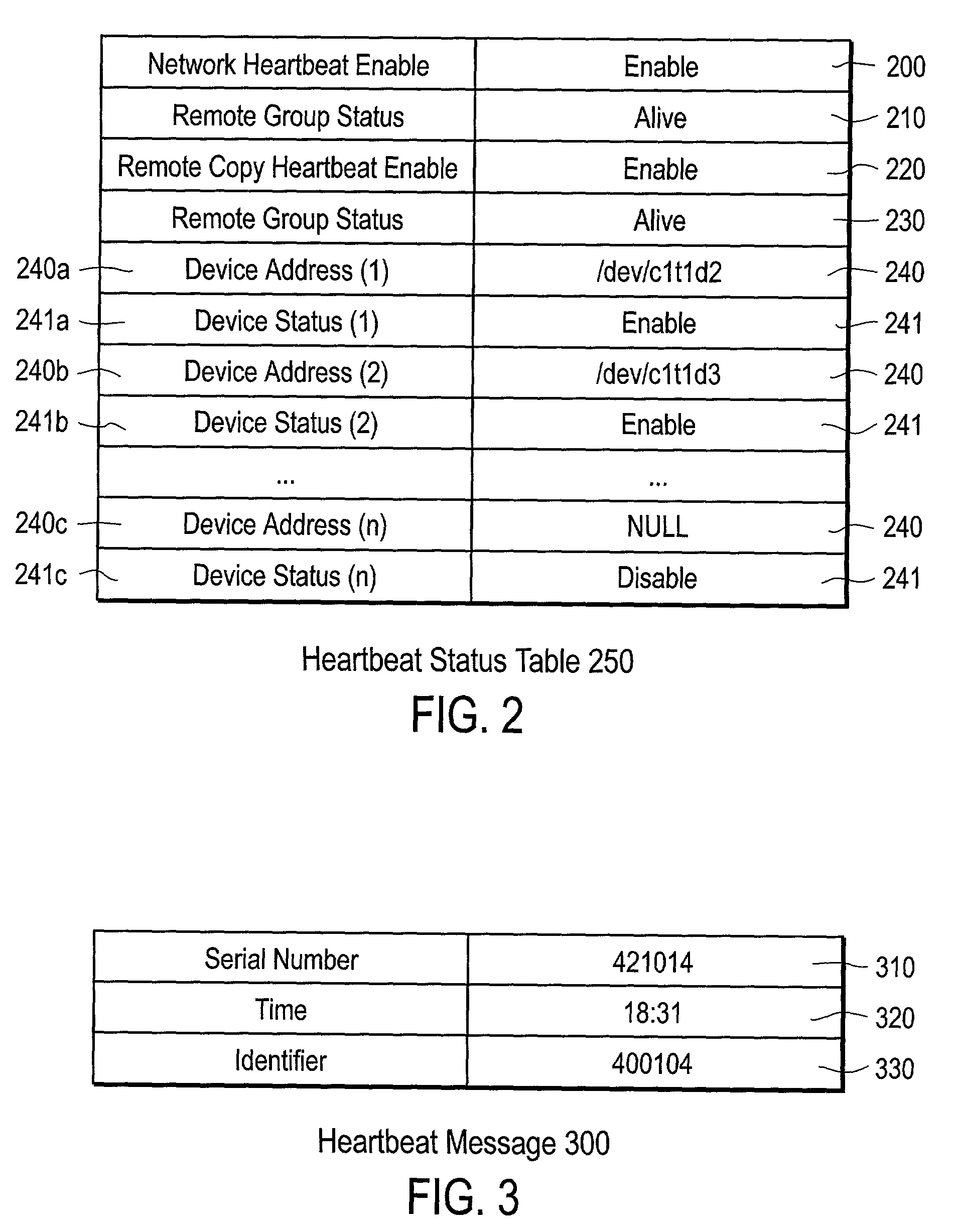
Failure notification method and system using remote mirroring for clustering systems
InactiveUS7275100B2Improve reliabilityEasy fault detectionDigital computer detailsHardware monitoringPort mirroringCluster systems
A cluster computing system, comprises: a production host group; a standby host group coupled to the production host group by a network; and a remote mirror coupled between the production host group and the standby host group, the remote mirror including a production site heartbeat storage volume (heartbeat PVOL) and a standby site heartbeat storage volume (heartbeat SVOL) coupled by a remote link to the heartbeat PVOL, with the production host group configured to selectively send a heartbeat signal to the standby host group by use of at least one of the network and the remote link. A method of checking for failure in a cluster computing system, comprises: generating a heartbeat signal from a production host group; selectively sending the heartbeat signal to the standby host group from the production host group by use of at least one of a network and a remote link; and enabling the standby host group to manage operations of the cluster computing system if an invalid heartbeat signal is received by the standby host group from the production host group.
Owner:HITACHI LTD
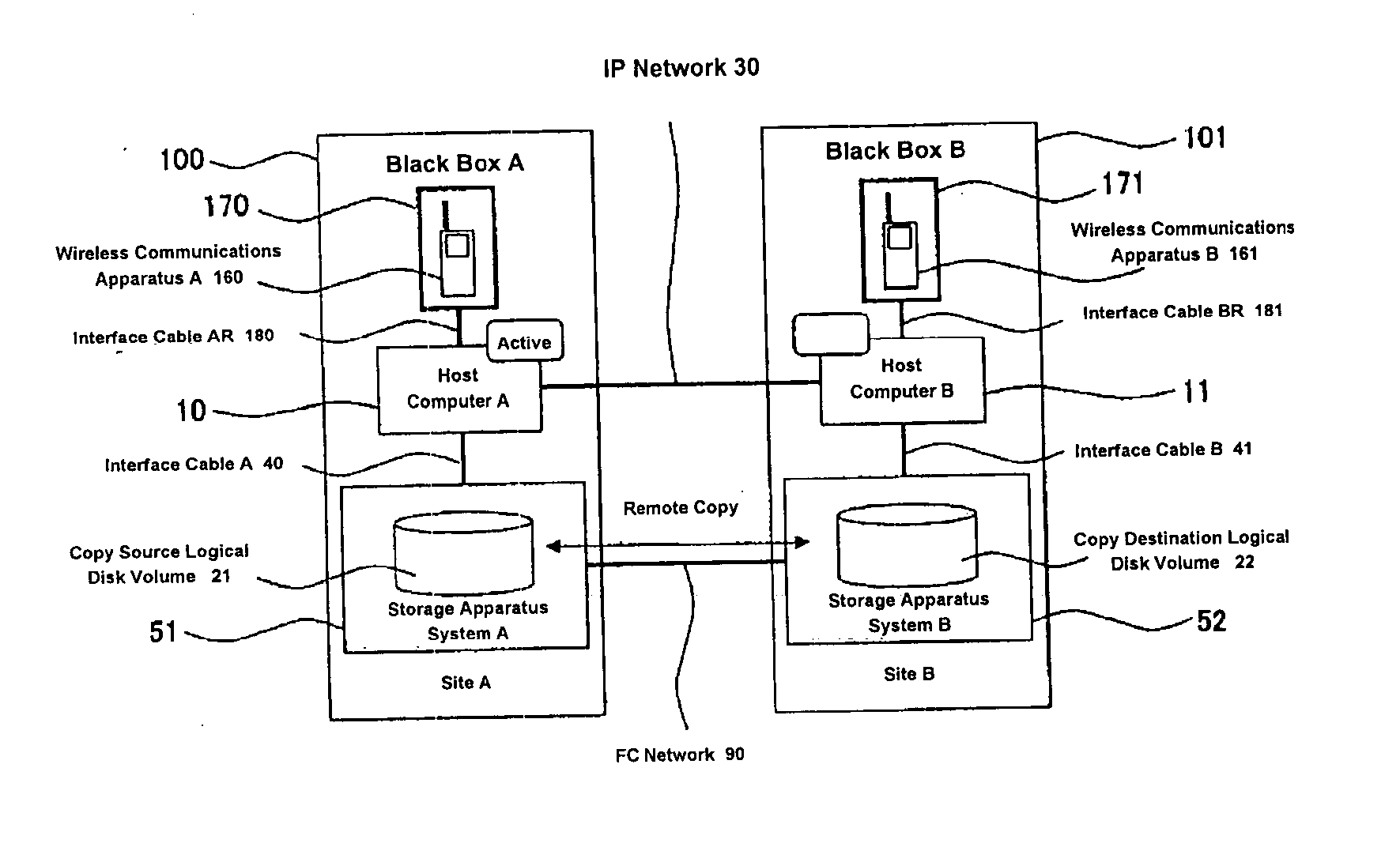
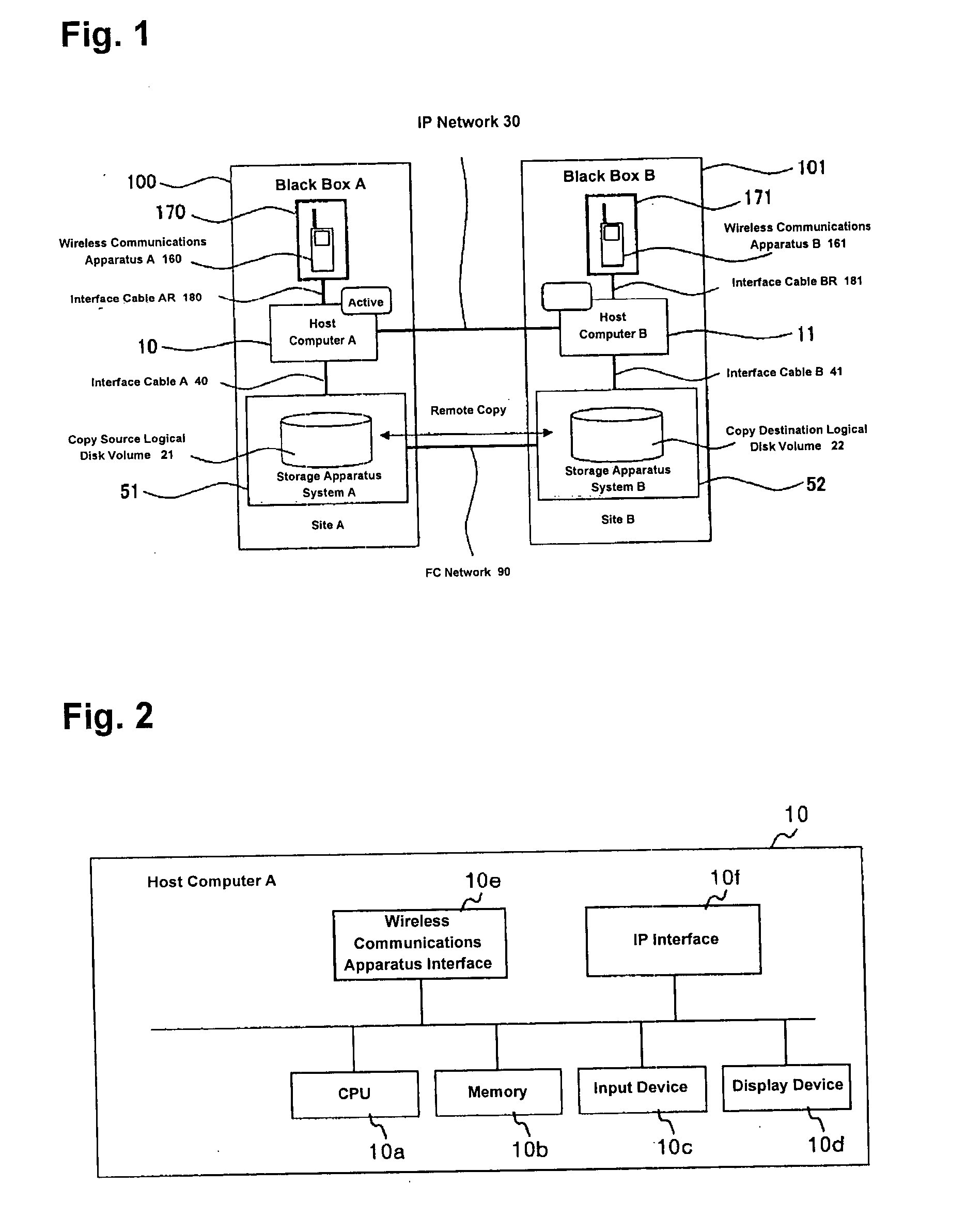
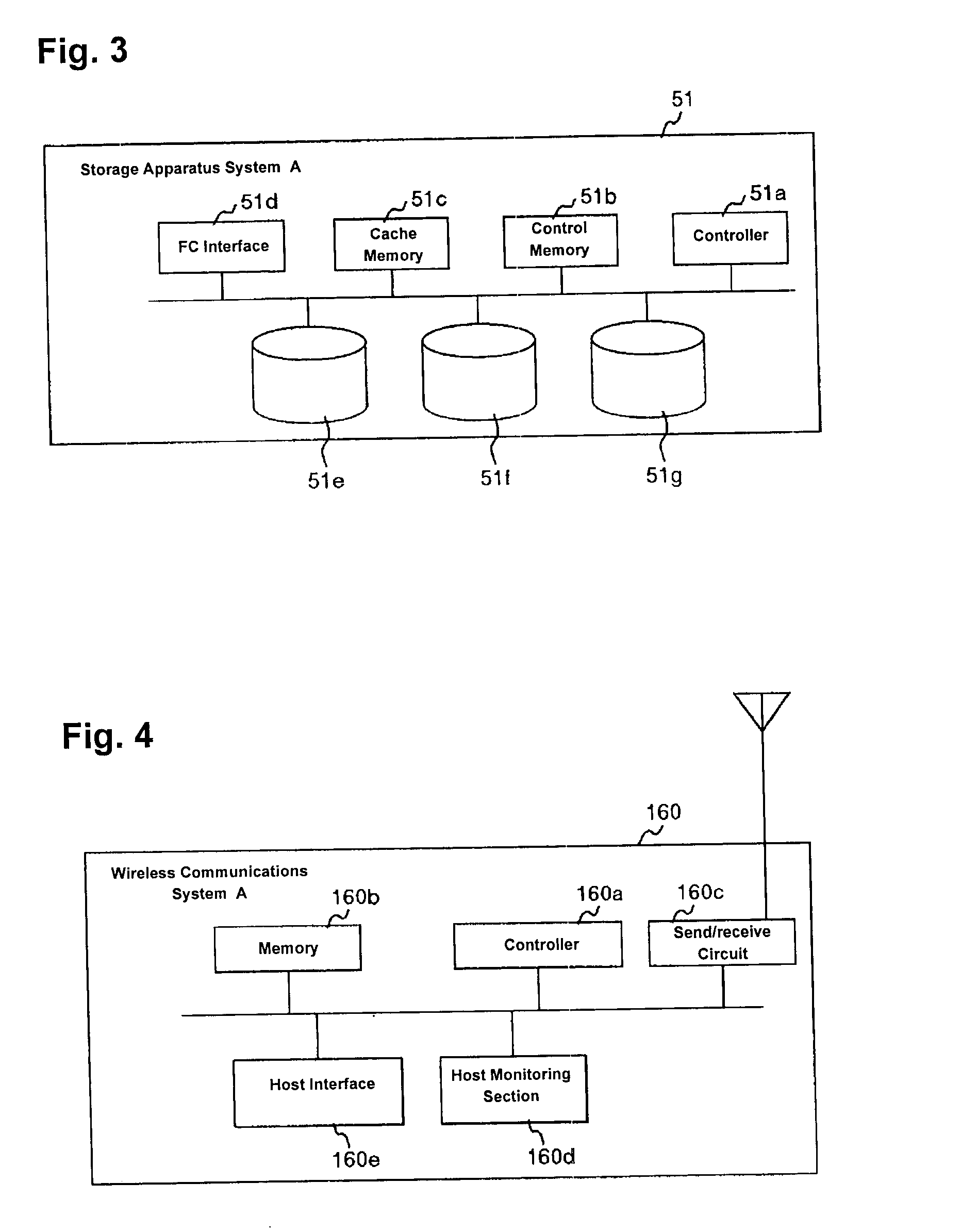
Cluster computing system and its failover method
InactiveUS20050005001A1Eliminate shortcomingsImprove system reliabilityDigital computer detailsTransmissionFailoverActive systems
A cluster computing system includes an active system and a standby system connected via wire networks. The active system and the standby system each has a wireless communications apparatus, such that when all of the wire networks connecting the active system with the standby system are disconnected, the wireless communications apparatus of the active system reports the standby system of the failure of the active system using its wireless communications capability with the wireless communications apparatus of the standby system. The report includes the verification ID of the active system, and the standby system begins operation upon receiving a packet containing the verification ID.
Owner:HITACHI LTD
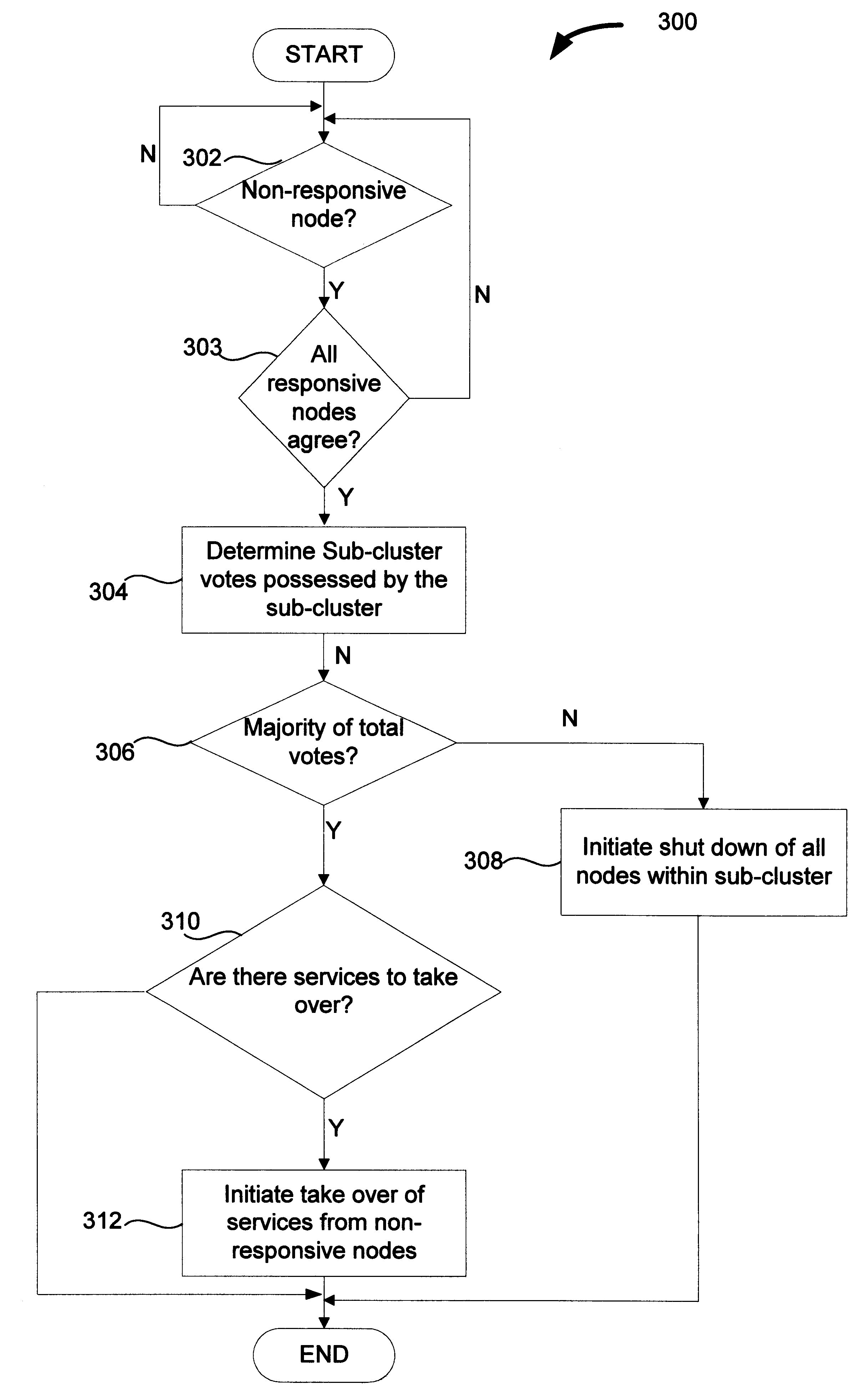
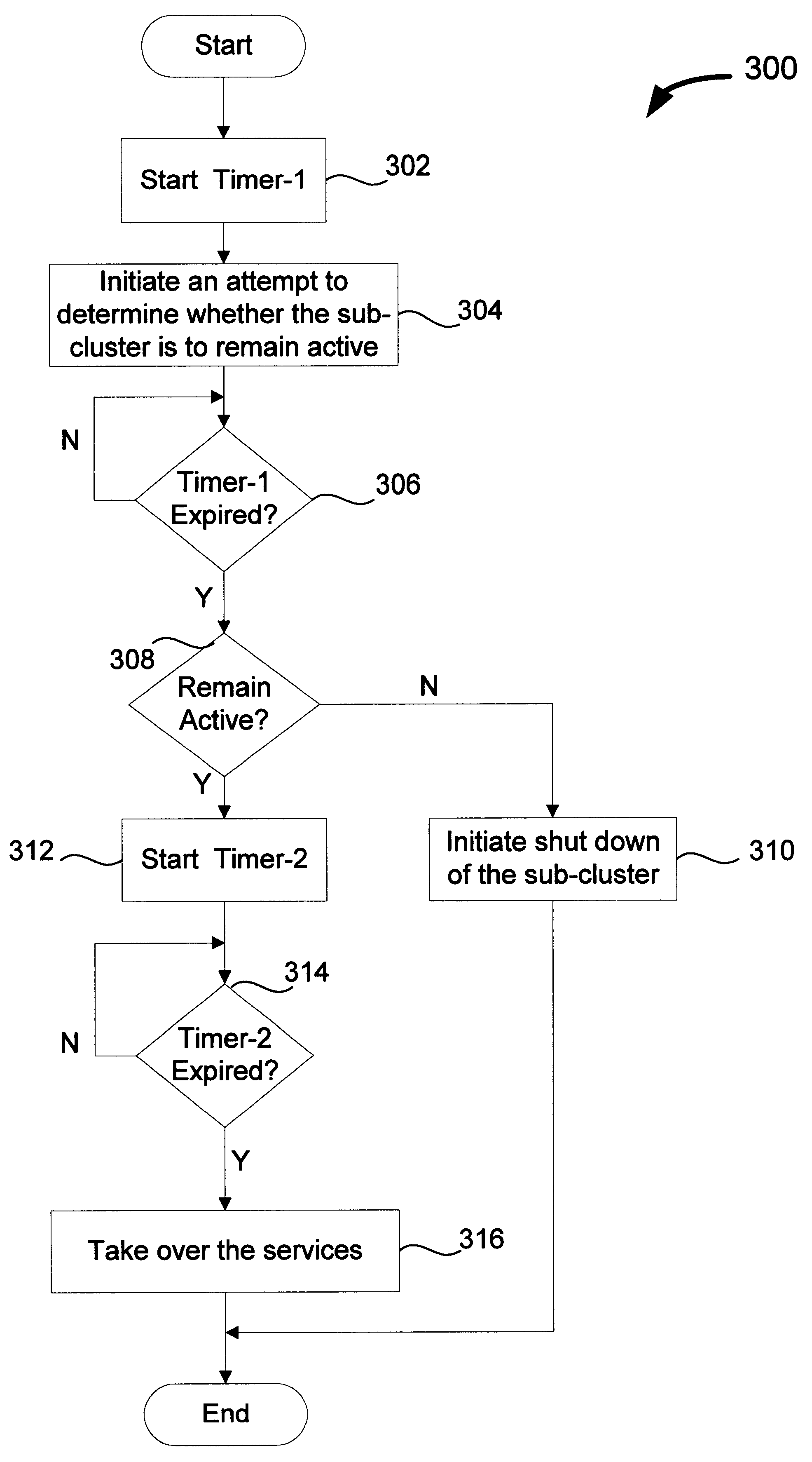
Controlled take over of services by remaining nodes of clustered computing system
InactiveUS6789213B2Take over serviceSafely provide serviceError detection/correctionDigital computer detailsComputing systemsDistributed computing
Improved techniques for controlled take over of services for clustered computing systems are disclosed. The improved techniques can be implemented to allow one sub-cluster of the clustered computing system to safely take over services of one or more other sub-clusters in the clustered computing system. Accordingly, if the clustered computing system is fragmented into two or more disjointed sub-clusters, one sub-cluster can safely take over services of the one or more other sub-clusters after the one or more other sub-clusters have been shutdown. As a result, the clustered computing system can continue to safely provide services even when the clustered computing system has been fragmented into two or more disjointed sub-clusters due to an operational failure.
Owner:ORACLE INT CORP
Anisotropic three-dimensional prestack time migration method
InactiveCN102141633AImprove imaging effectAccurate homing and margin protectionSeismic signal processingMineral SourcesData acquisition
The invention provides an anisotropic three-dimensional prestack time migration method which is applied to processing reflection seismic data in seismic exploration and relates to a prestack time migration method aiming at three-dimensional seismic data acquisition. The method takes into account the effect of the velocity anisotropy of an earth medium on the travel time and the amplitude value propagated by a seismic wave and can independently determine the migration velocity and the anisotropic parameters during the migration process, therefore, a migration image which is accurately homed and is preserved in amplitude is obtained. The method determines the three-dimensional time-varying migration aperture in an anisotropic medium according to an underground structure time-varying inclination angle and can simultaneously press the migration noise during the migration process. With the adoption of the method, the efficient and parallel calculation is realized through reasonable distribution of the seismic data among compute nodes of a cluster computer. The method has the key point that the travel time, the amplitude value and the imaging weight coefficients of the seismic wave and an incident angle in the anisotropic medium are solved with the application of a one-way wave operator with deep migration and the steady phase point principle; and has the important application value for oil-gas and mineral resource exploration.
Owner:INST OF GEOLOGY & GEOPHYSICS CHINESE ACAD OF SCI
Dynamic modification of fragmentation size cluster communication parameter in clustered computer system
InactiveUS6934768B1Little and no effect on system availabilitySpecial service provision for substationError detection/correctionSize changeDistributed computing
An apparatus, program product and method support the dynamic modification of cluster communication parameters such as a fragmentation size parameter through controllably deferring the processing of a requested fragmentation size change in a source node until after receipt an acknowledgment message for at least one unacknowledged message sent by the source node to a plurality of target nodes. By controllably deferring such processing until it is confirmed that any such previously-unacknowledged messages sent by a source node have been received by any target nodes, synchronization between the source node and the target nodes may be obtained, and a fragmentation size change may occur in a coordinated fashion such that future messages from the source node to the target node will be processed by both the source and the target nodes using the modified fragmentation size parameter.
Owner:IBM CORP
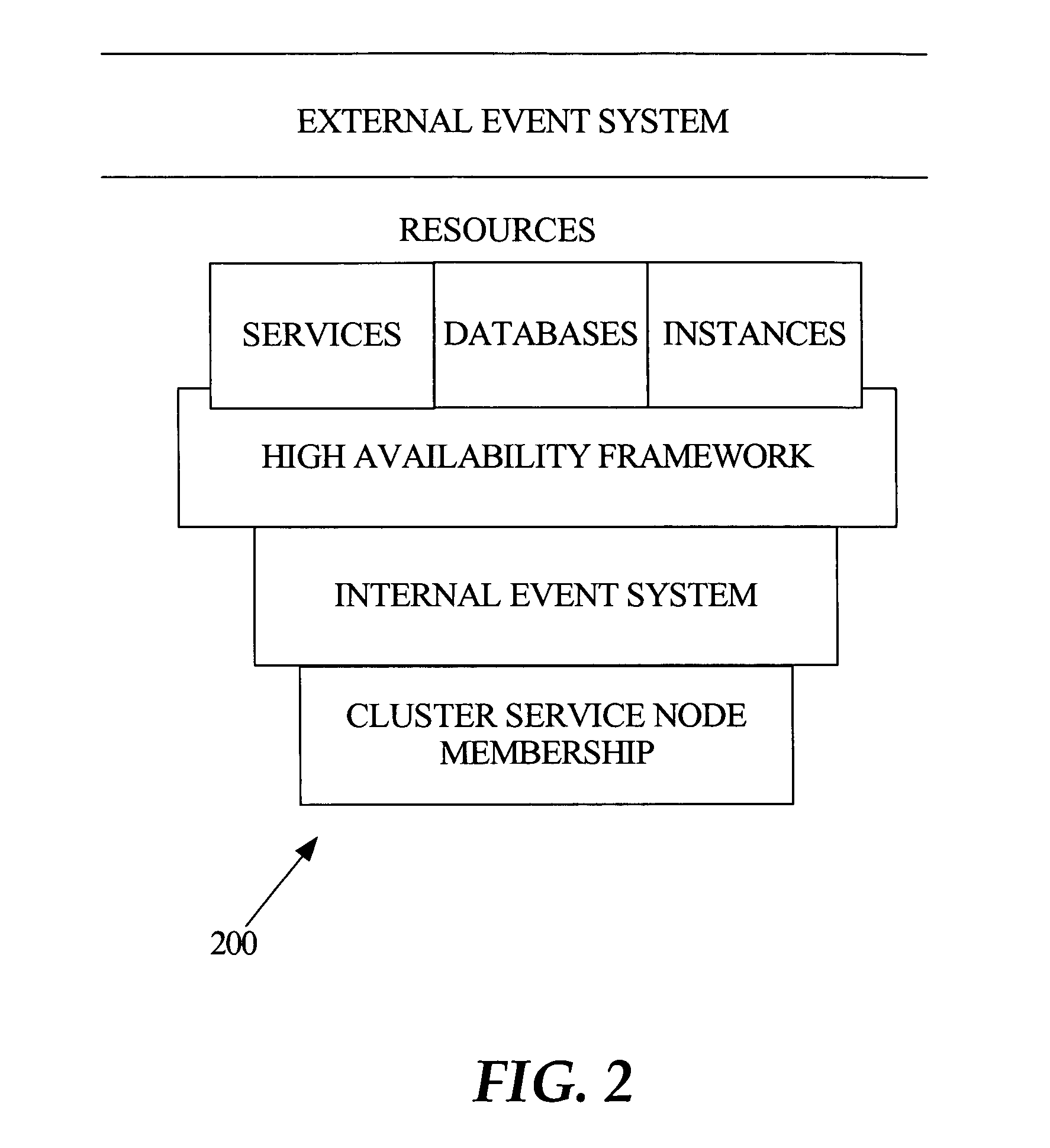
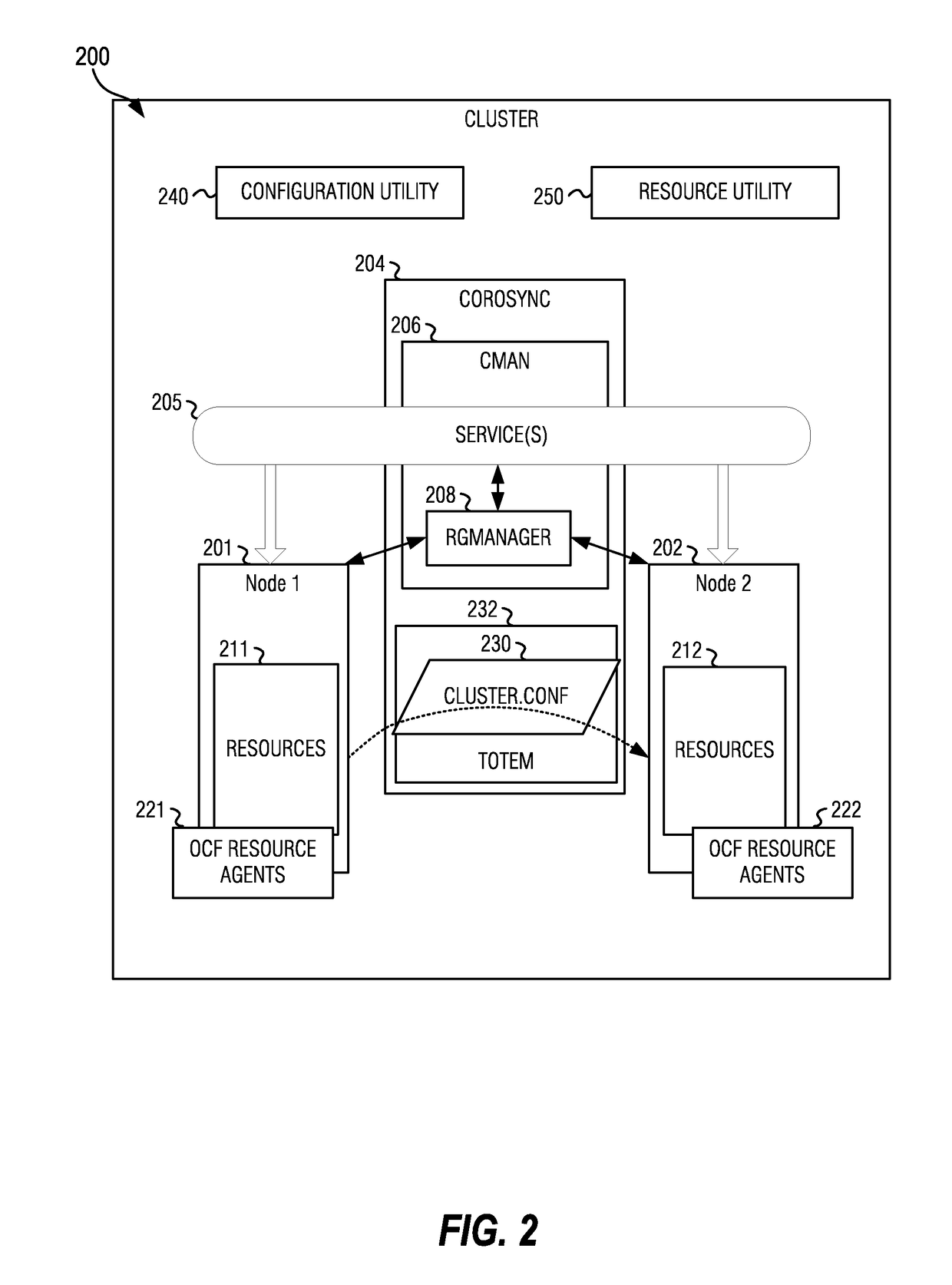
High availability management techniques for cluster resources
The present disclosure describes methods and system configurations for failover of cluster computing system resources, for a cluster computing system including a plurality of cluster nodes. In some examples, operations are performed to monitor an abstracted resource and reconfigure the abstracted resource, to enable fail-over processing for component members of the abstracted resource. In further examples, a hierarchy of resource dependencies is defined to enable enhanced fail-over processing for the failure of abstracted resources that cause the failure of services within the cluster computing system that are dependent upon the abstracted resources.
Owner:SANMINA-SCI CORPORATION
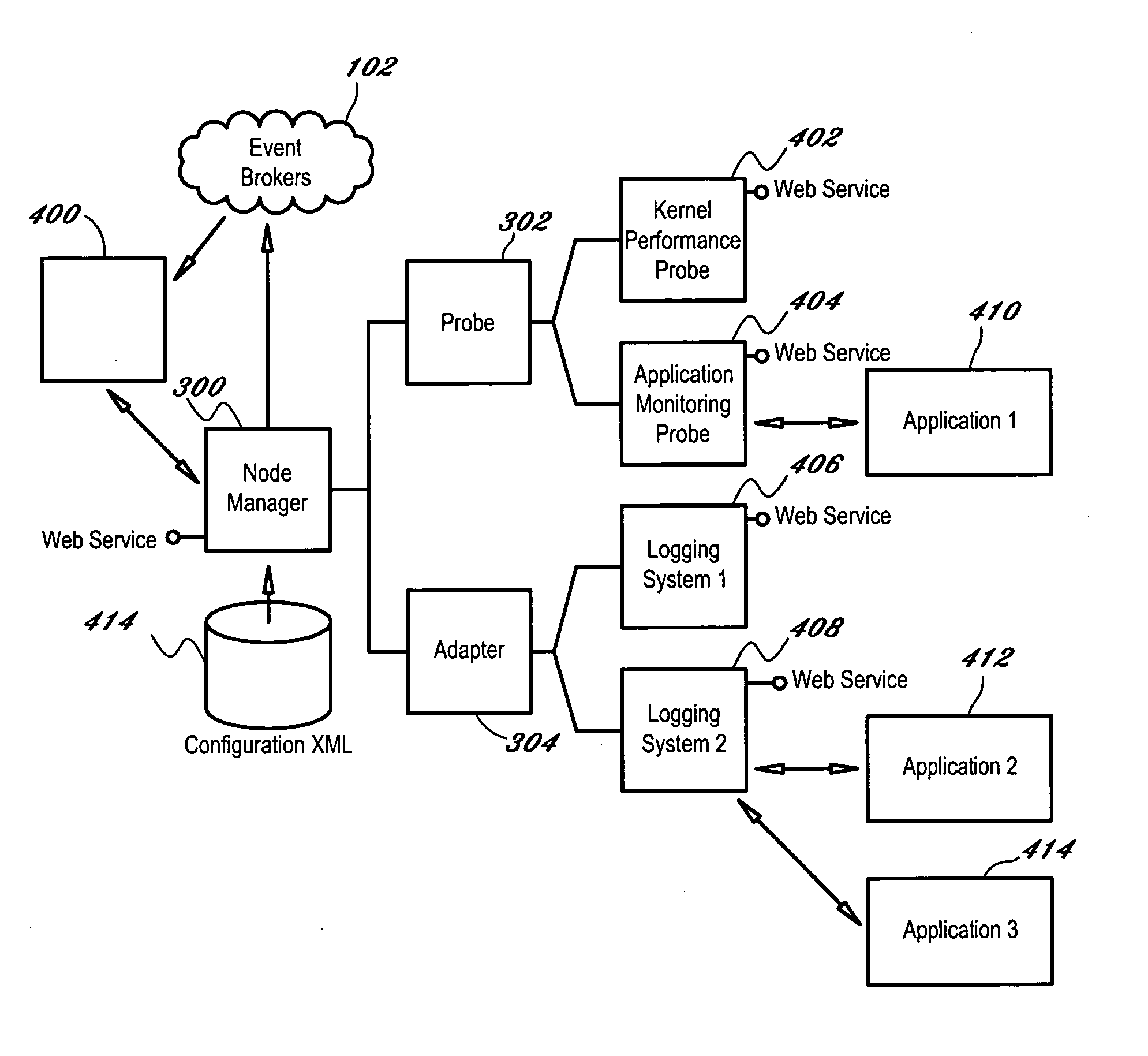
Cluster monitoring system with content-based event routing
InactiveUS20060179059A1Reduce and eliminate numberError detection/correctionProgram controlMonitoring systemClient-side
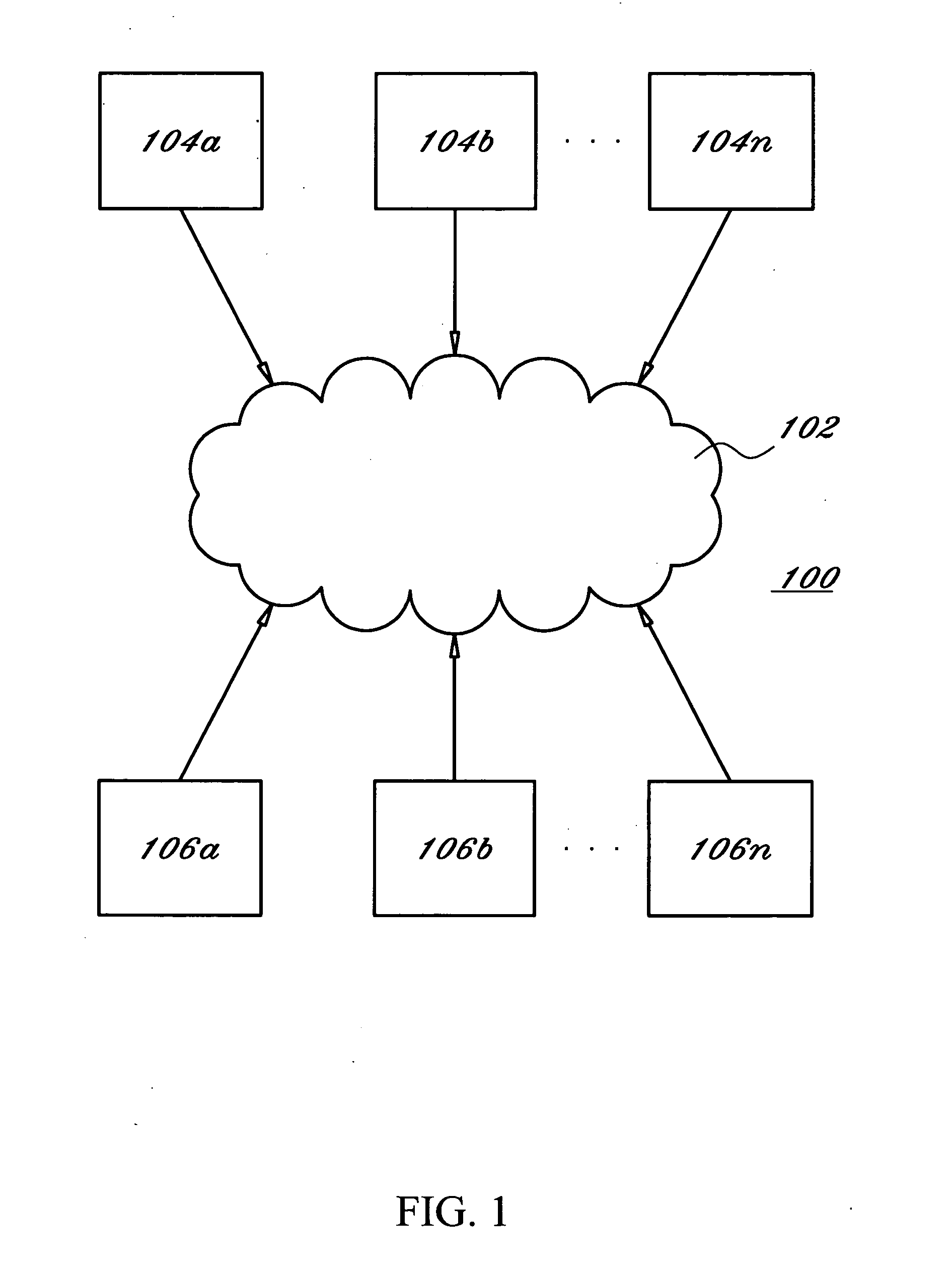
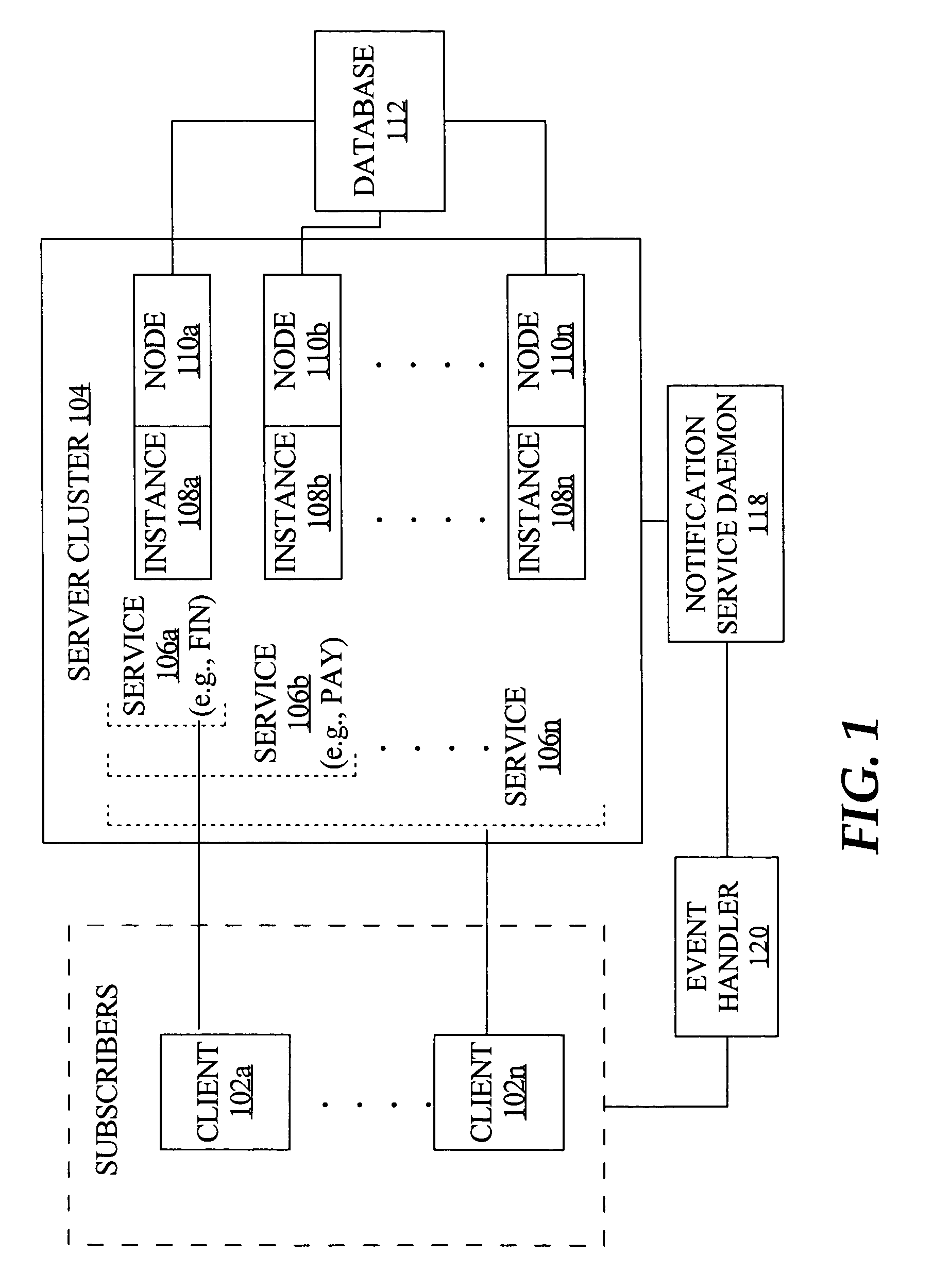
A node manager (300) resides on a node (104) in a cluster computing system (100) and transfers information and events being communicated across the node (104) to a broker (102) coupled to the node manager (300). The broker (102) transmits information to client devices (106) who subscribe to particular events. The node manager (300) includes an adapter (304) that interprets events occurring on the system and publishes messages to the broker, and a system probe (302) that publishes information to the broker (102) in accordance with a configurable schedule. An autonomic agent (400) measures the rate of information loss between the node (104) and client (106) and regulates the rate of information by adjusting one or more information flow control points within the system once an overload state is detected.
Owner:IBM CORP
Fast application notification in a clustered computing system
ActiveUS7747717B2Resource allocationMultiple digital computer combinationsComputer networkService experience
With fast notification of changes to a clustered computing system, through which a number of events are published for system state changes, applications can quickly recover and sessions can quickly be rebalanced. When a resource associated with a service experiences a change in status, such as a termination or a start / restart, a notification event is immediately published. Notification events contain information to enable subscribers to identify, based on matching a session signature, the particular sessions that are affected by the change in status, and to respond accordingly. This allows sessions to be quickly aborted and ongoing processing to be quickly terminated when a resource fails, and allows fast rebalancing of work when a resource is restarted.
Owner:ORACLE INT CORP
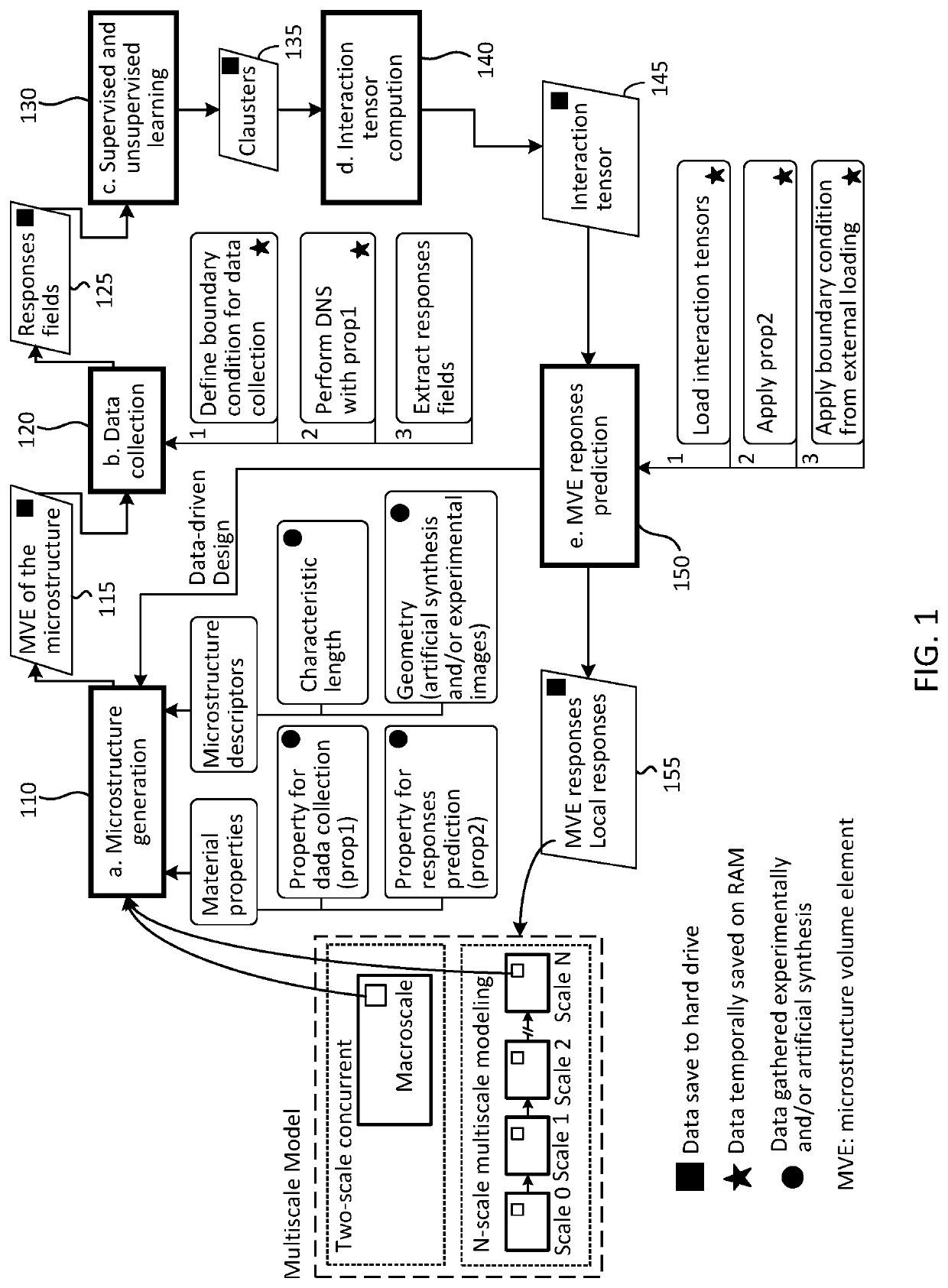
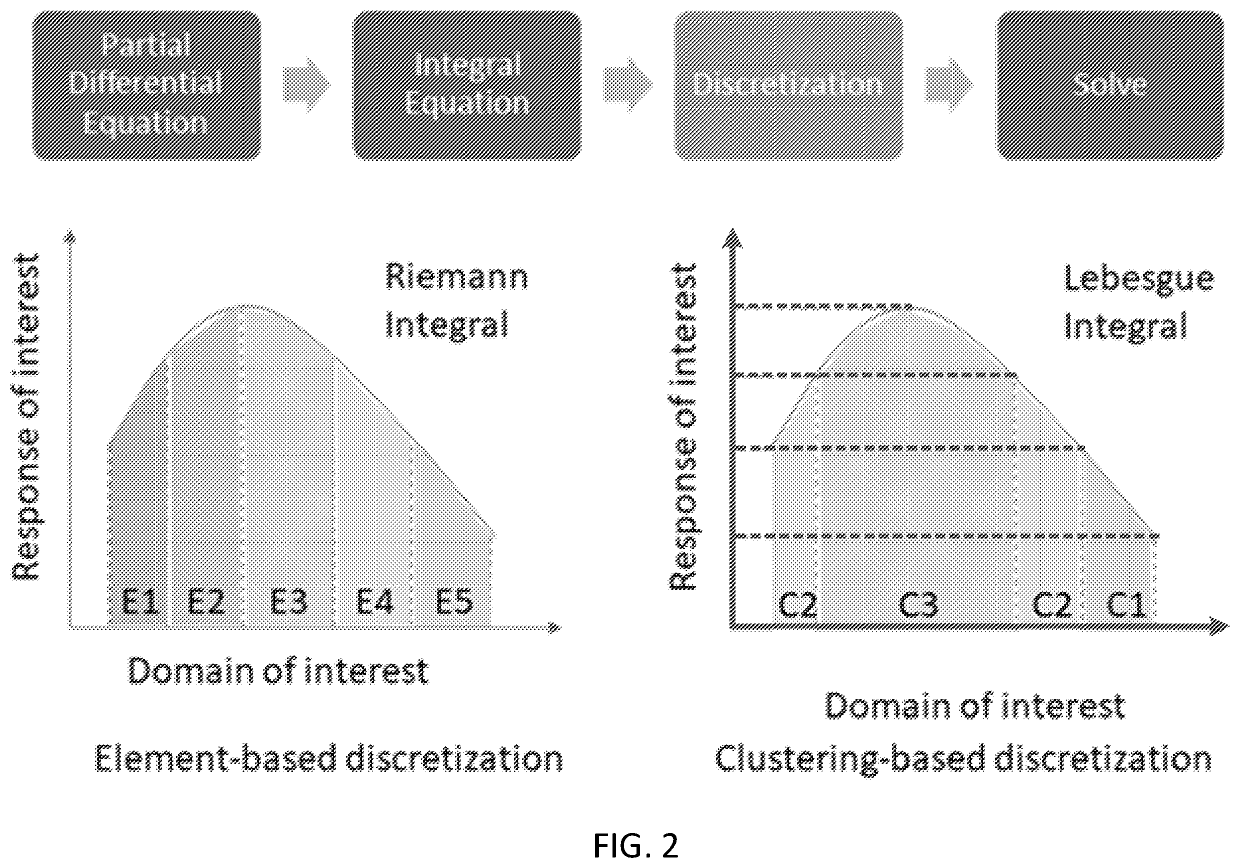
Data-driven representation and clustering discretization method and system for design optimization and/or performance prediction of material systems and applications of same
PendingUS20210357555A1Reduce in quantityReduced representationAdditive manufacturing apparatusDesign optimisation/simulationTheoretical computer sciencePartial differential equation
A method and system for design optimization and / or performance prediction of a material system includes generating a representation of the material system at a number of scales, the representation at a scale comprising microstructure volume elements (MVE) of building blocks of the material system at said scale; providing inputs to the MVEs; collecting data of response fields of the MVE computed from a material model of the material system over a predefined set of material properties and boundary conditions; applying machine learning to the collected data to generate clusters; computing an interaction tensor of interactions of each cluster with each of the other clusters; and solving an governing partial differential equation using the generated clusters and the computed interactions to result in a response prediction usable in an iterative scheme in a multiscale model for the material system. The performance of each scale can be predicted for design optimization.
Owner:NORTHWESTERN UNIV
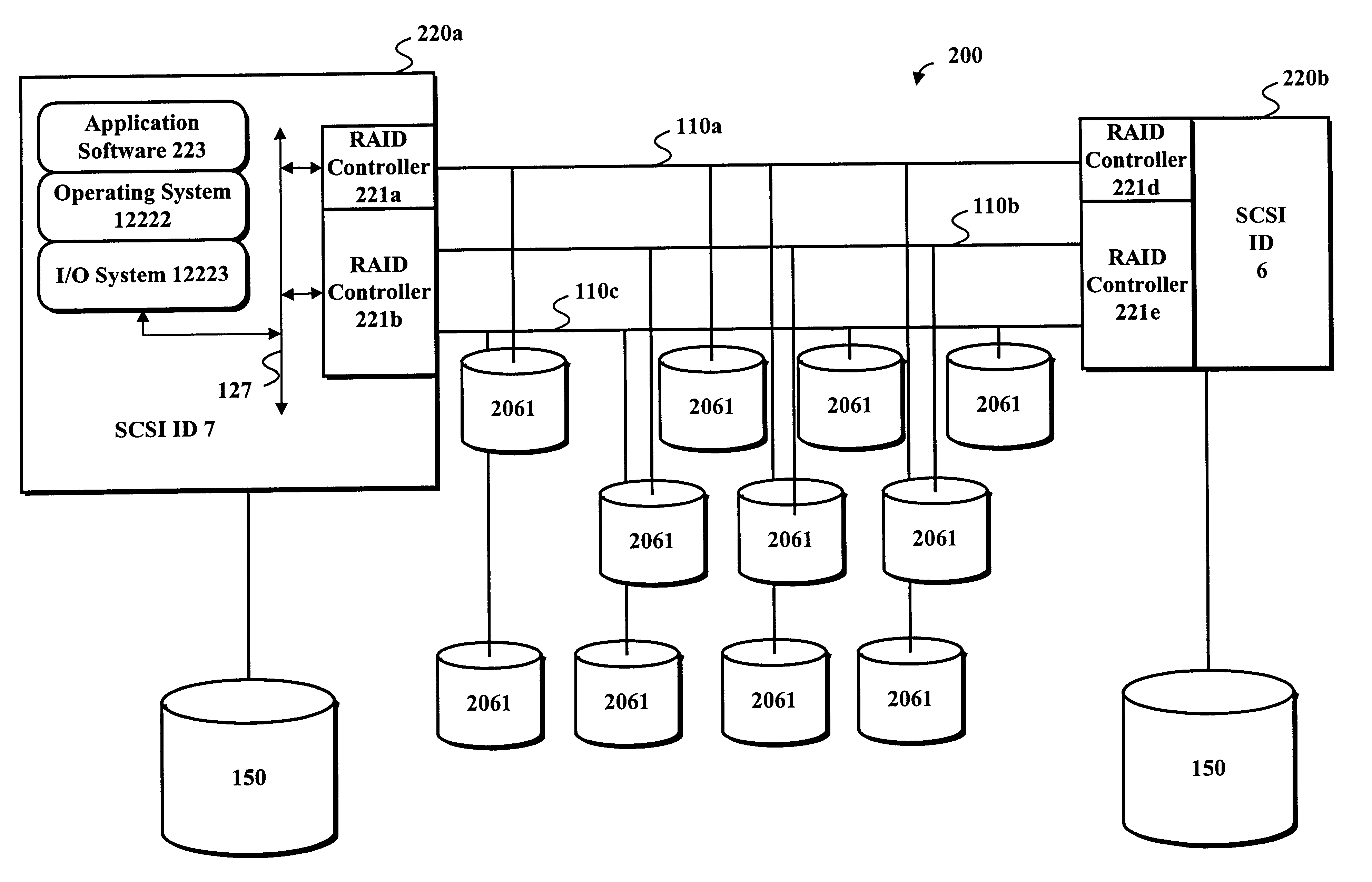
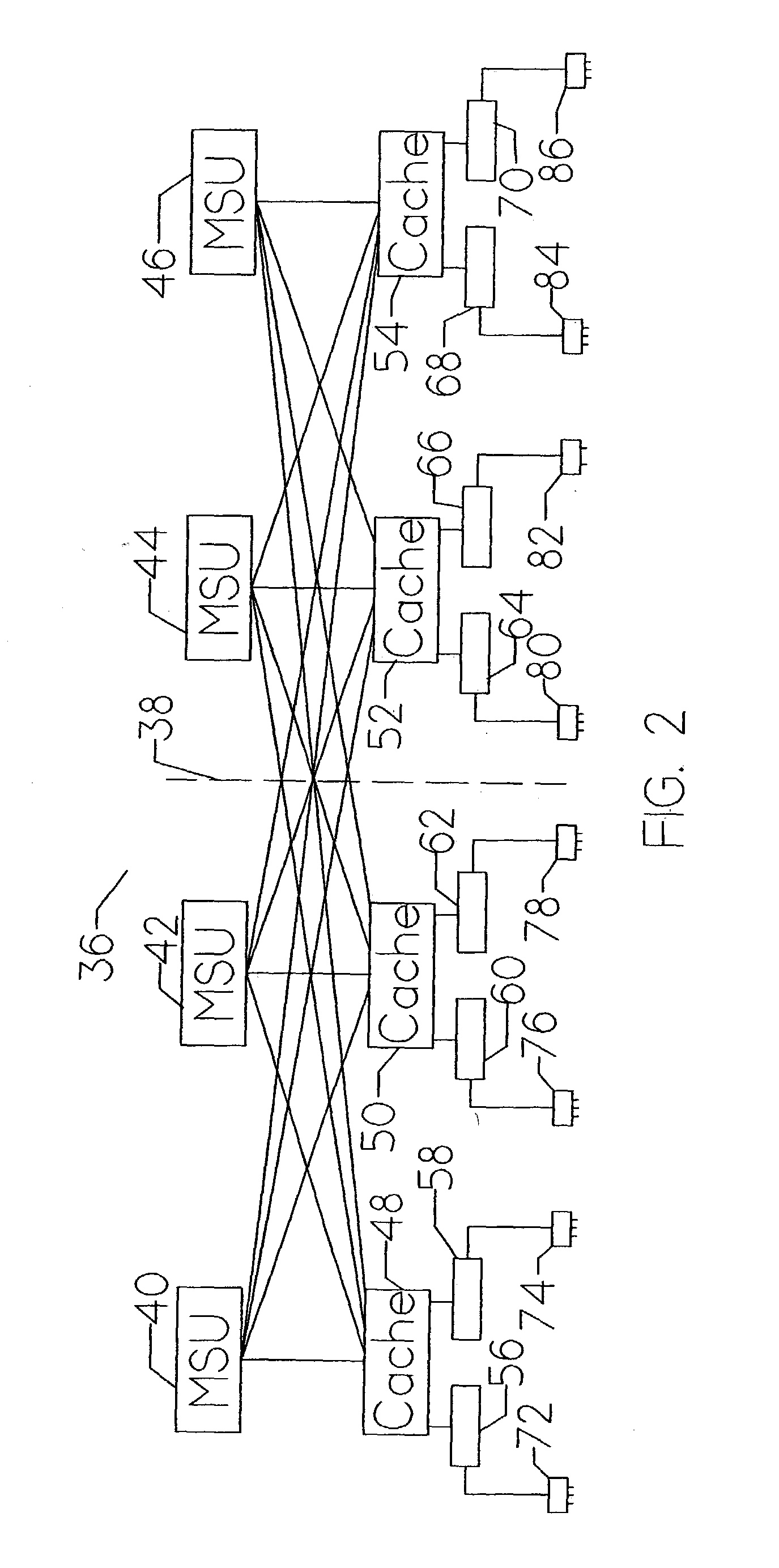
Clustered computer system utilizing separate servers for redundancy in which the host computers are unaware of the usage of separate servers
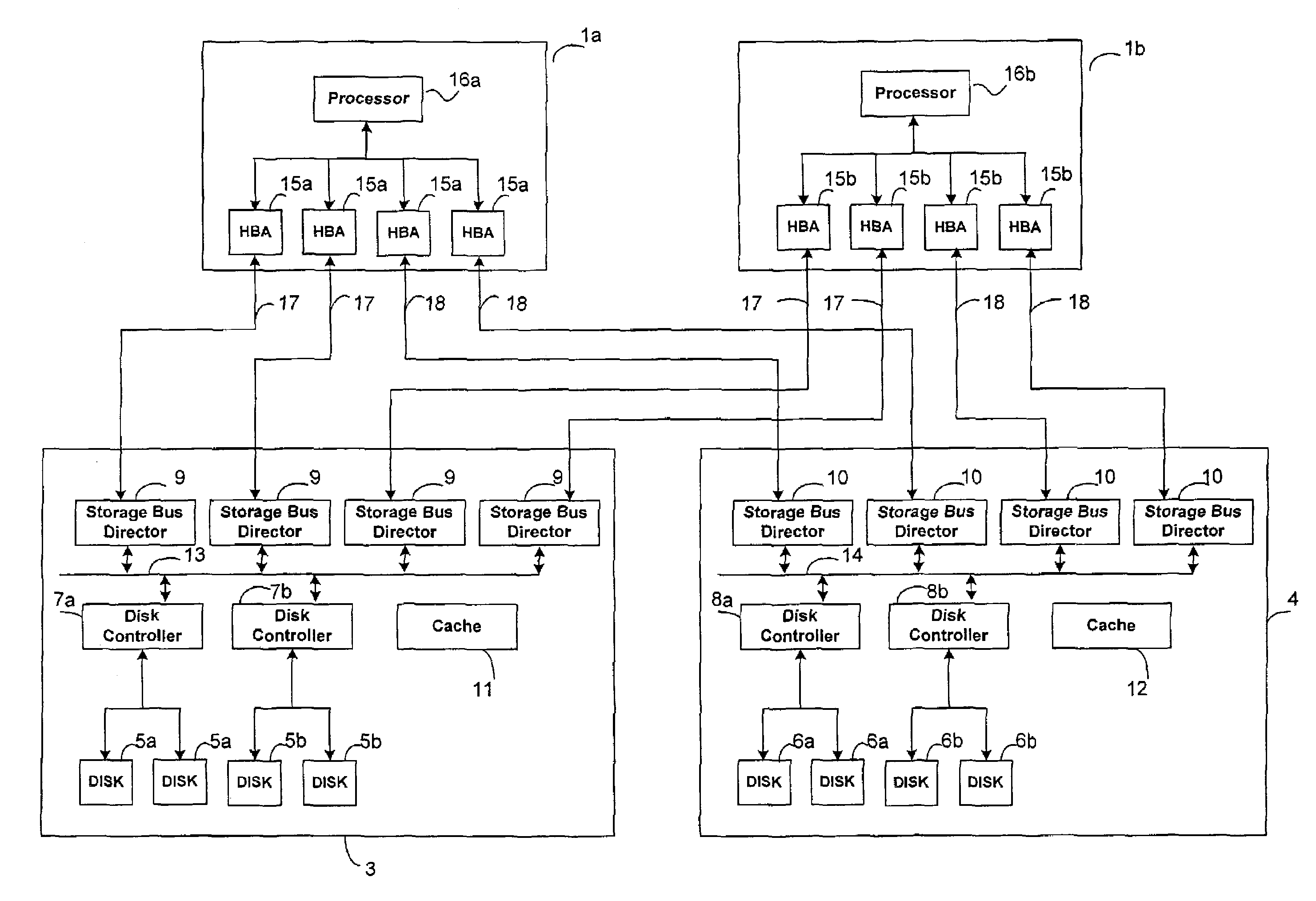
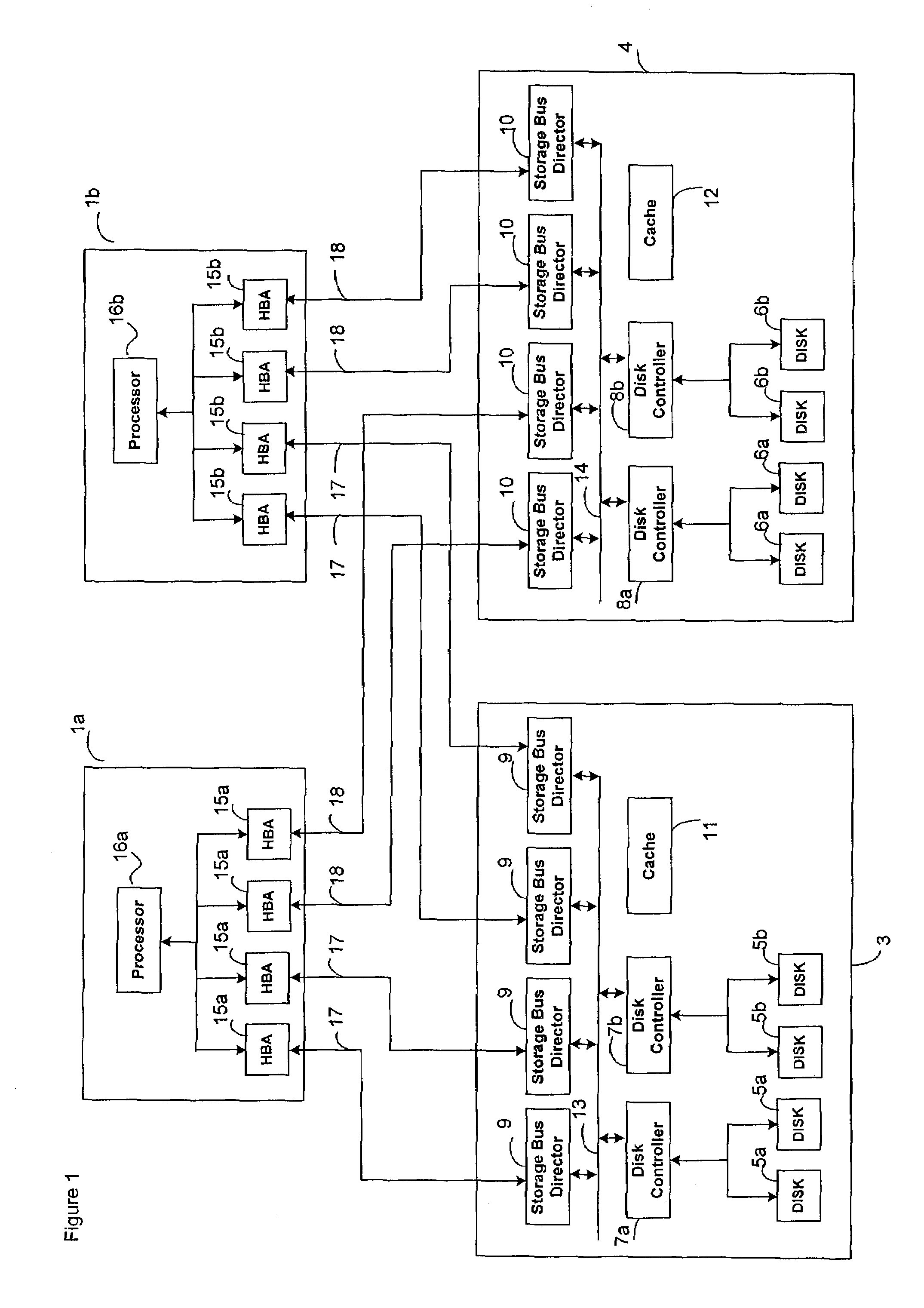
ActiveUS7155638B1Improve performanceLow costError detection/correctionProgram controlMass storageOperational system
An apparatus for and method of enhancing reliability within a cluster lock processing system having a relatively large number of commodity cluster instruction processors which are managed by a cluster lock manager. Because the commodity processors have virtually no system viability features such as memory protection, failure recovery, etc., the cluster / lock processors assume the responsibility for providing these functions. The low cost of the commodity cluster instruction processors makes the system almost linearly scalable. The cluster / locking, caching, and mass storage accessing functions are fully integrated into a single hardware platform which performs the role of the master. Upon failure of this hardware platform, a second redundant hardware platform converts from slave to master role. The logic for the failure detection and role swapping is placed within software, which can run as an application under a commonly available operating system. Furthermore, the recovery is completely accomplished without assistance of the Host computer(s) or ultimate user(s) coupled via the Host computer(s).
Owner:UNISYS CORP
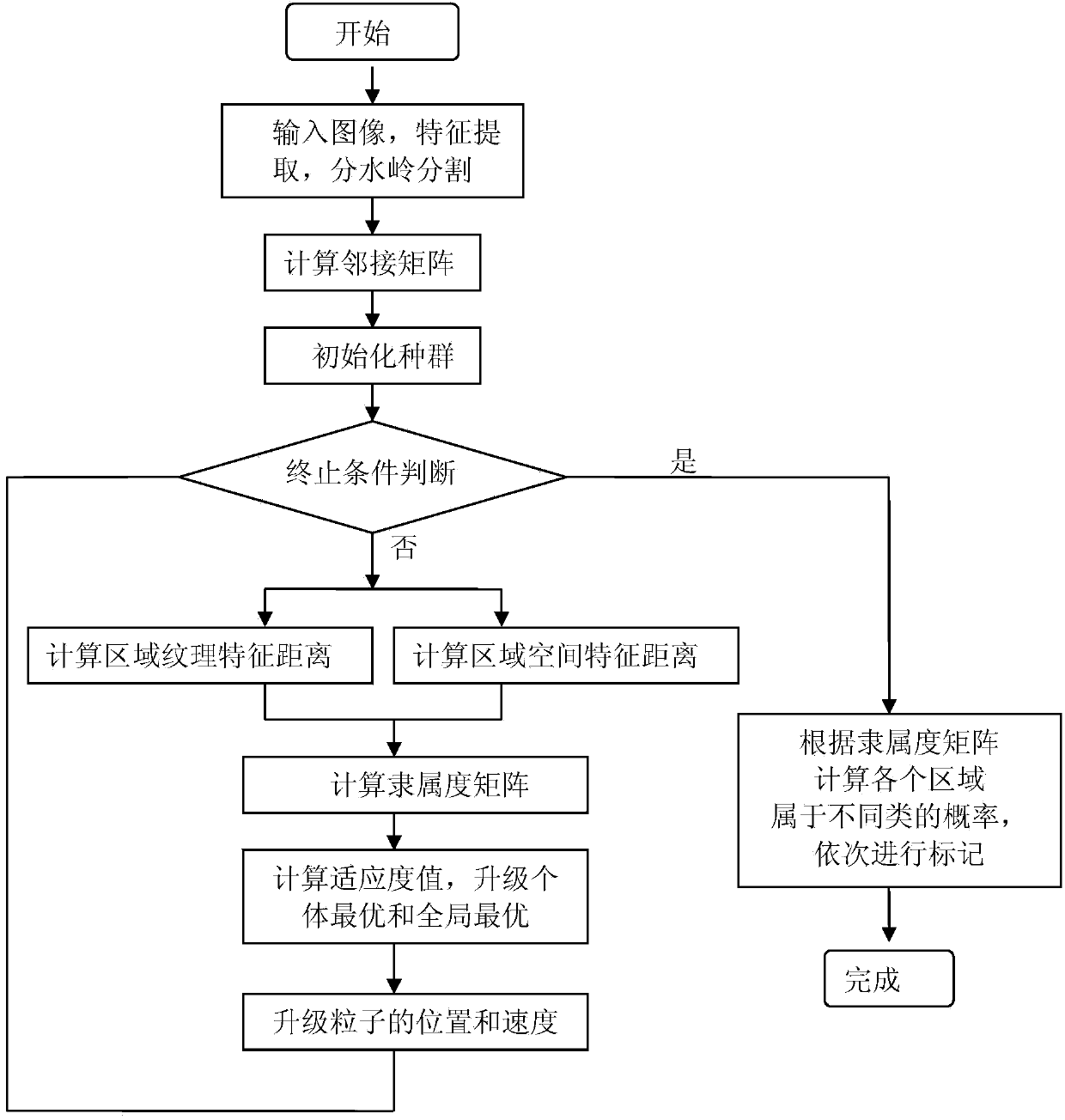
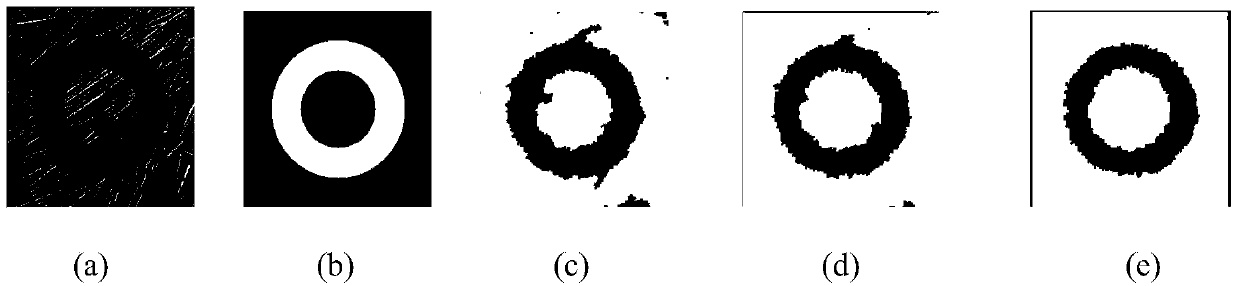
Clustered image splitting method based on particle swarm optimization and spatial distance measurement
ActiveCN103593855AIntegrity guaranteedImprove regional consistencyImage analysisBiological modelsClustered dataImage extraction
The invention discloses a clustered image splitting method based on particle swarm optimization and spatial distance measurement. The clustered image splitting method mainly solves the problem that the existing clustered image splitting technology has local misdivision phenomena and multiple area miscellaneous points. The clustered image splitting method includes the steps: (1) inputting an original image, extracting pixel characteristics and conducting watershed splitting, (2) calculating an adjacent matrix according to a split area and generating clustered data, (3) using the clustered data to initialize a cluster at random, (4) calculating membership matrixes and adaptability values of the cluster, upgrading individuals and overall to be optimum, and evolving the cluster, (5) upgrading iterations, outputting the best membership matrix if the preset maximum iterations are achieved, and continuously executing the step (4) if the preset iterations are not achieved, and (6) according to the best membership matrix, marking according to the maximum probability principle to obtain the splitting result. Compared with the prior art, the clustered image splitting method has the advantages of being good in area coincidence, high in splitting accuracy and capable of being used for object identification on an SAR image.
Owner:XIDIAN UNIV
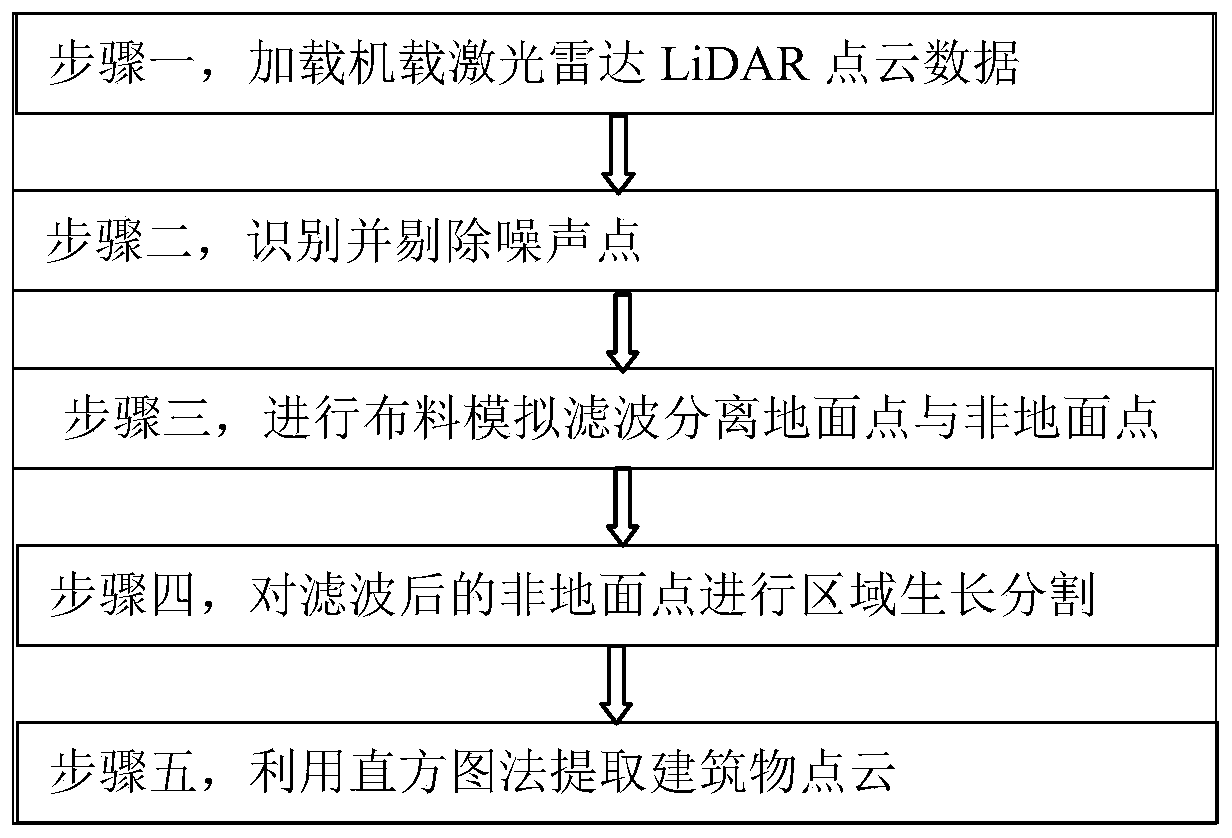
Segmentation-based airborne LiDAR point cloud building extraction method
PendingCN110992341AAccurate extractionEffective WaysImage enhancementImage analysisLidar point cloudEngineering
The invention discloses a segmentation-based airborne LiDAR point cloud building extraction method. The method comprises the steps of: (1) loading airborne laser LiDAR point cloud data; (2) identifying noise points in the airborne laser LiDAR point cloud, and removing the noise points; (3) carrying out material distribution simulation filtering to separate ground points from non-ground points; (4)carrying out region growth segmentation on filtered non-ground point cloud; and (5) calculating the direction cosine of the local normal vector and normal vector of each cluster which is obtained after the segmentation, generating a histogram, separating building point cloud from non-building point cloud through the generated histogram, thereby realizing the accurate extraction of the building point cloud. The invention provides the simple and efficient histogram method for distinguishing buildings from non-buildings. According to the difference of the normal vector characteristics of a building roof and a vegetation surface, a PCL-based region growing algorithm is utilized to perform three-dimensional point cloud segmentation on the non-ground points; and the histogram method is used incombination to distinguish the buildings from the non-buildings, so that the building point cloud data are accurately extracted.
Owner:SHENYANG JIANZHU UNIVERSITY
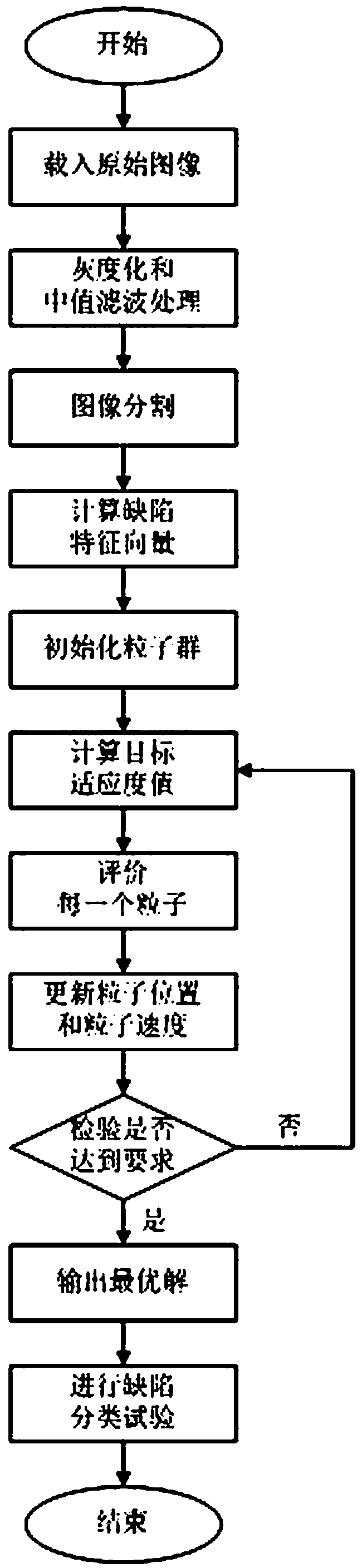
Defect classification method based on improved particle swarm wavelet neural network
ActiveCN109934810AGuaranteed generalization abilityBalanced Search CapabilitiesImage enhancementImage analysisFeature vectorMachine vision
The invention belongs to the technical field of machine vision detection, and particularly relates to a defect classification method based on an improved particle swarm wavelet neural network. The problems that a traditional BP neural network algorithm is prone to convergence and prematurity, and cause a local minimum value and the like are solved. The method comprises the following steps: loadingan original image, carrying out graying and median filtering processing, segmenting the image, calculating a defect feature vector, initializing a particle swarm, calculating a target fitness value,evaluating each particle, updating the position and speed of each particle, checking whether the requirement is met, outputting an optimal solution, and finally carrying out defect classification on the image. According to the method, a variation factor is added, so that the generalization capability of the algorithm is ensured. A nonlinear weight factor is set, and a target of flexible adjustmentof global search and local search is realized. A global extreme value of Gaussian weighting is introduced, convergence of the global extreme value to the optimal solution direction is facilitated, defects can be classified quickly and accurately, the classification result is more accurate, and the efficiency is higher.
Owner:TAIYUAN UNIV OF TECH
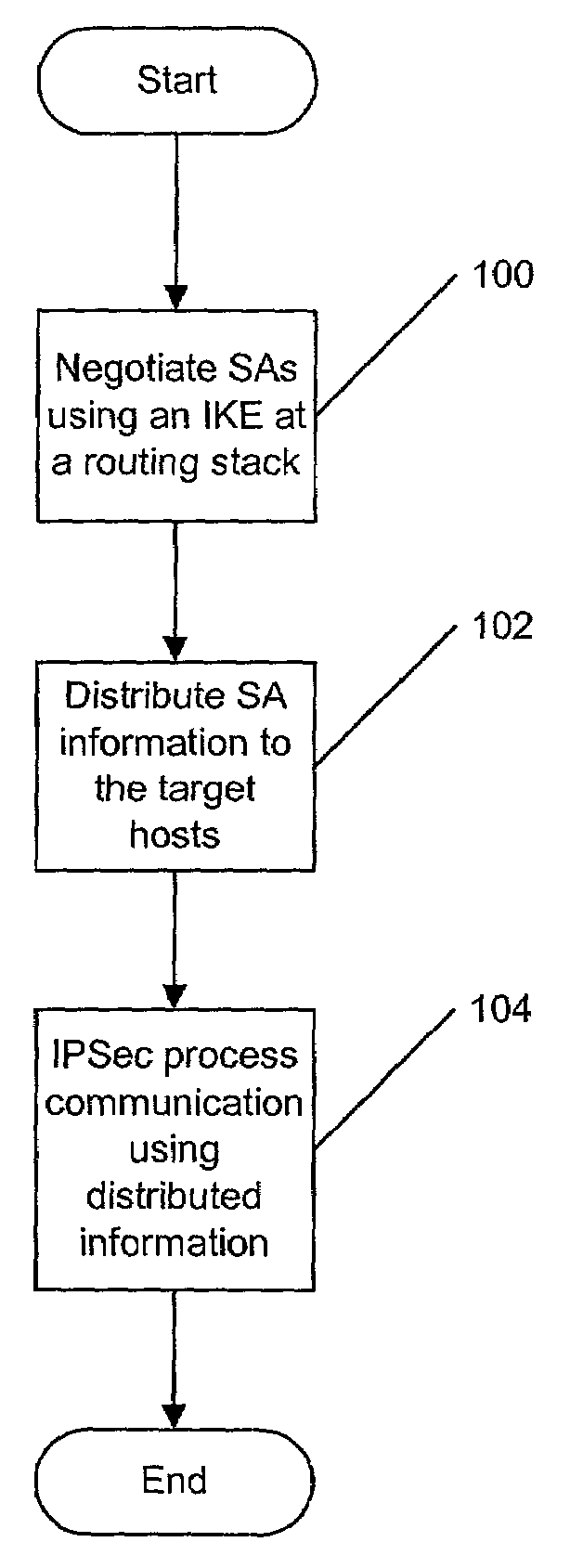
Methods, systems and computer program products for security processing outbound communications in a cluster computing environment
ActiveUS7107350B2Multiple digital computer combinationsProgram controlOutbound communicationSecurity association
Methods, systems and computer program products provide Internet Protocol Security (IPSec) to a plurality of target hosts in a cluster of data processing systems which communicate with a network through a routing communication protocol stack utilizing a dynamically routable Virtual Internet Protocol Address (DVIPA) for communications from the plurality of target hosts by negotiating security associations (SAs) associated with the DVIPA utilizing an Internet Key Exchange (IKE) component associated with the routing communication protocol stack and distributing information about the negotiated SAs to the target hosts so as to allow the target hosts to perform IPSec processing of communications to the network utilizing the negotiated SAs. Communications to the network are IPSec processed utilizing the distributed information at communication protocol stacks at respective ones of the plurality of target hosts.
Owner:IBM CORP
Method for allowing a clustered computer systems manager to use disparate hardware on each of the separate servers utilized for redundancy
ActiveUS7178057B1Improve performanceLow costProgram controlRedundant hardware error correctionSystems managementLock manager
An apparatus for and method of providing failure recovery from redundancy, notwithstanding that the failed subsystem and its replacement have differing capacities. This is especially useful when implementing a cluster lock processing system having a relatively large number of commodity instruction processors which are managed by a highly scalable, cluster lock manager. Reliability is built into the managing communication processor by dividing the system into master and slave subsystems. The master has primary responsibility for system management and coordination, whereas the slave has primary responsibility to backup the master and be prepared to assume management responsibility. Upon the need to transfer responsibility from the master to the slave, whether it be manual (e.g., maintenance) or automatic (e.g., failure), the only concern is that the slave has sufficient capacity to accept the current level of processing, even though it does not have the same level of capacity as the master.
Owner:GOOGLE LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com