Patents
Literature
132 results about "Signature recognition" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Signature recognition is a behavioural biometric. It can be operated in two different ways...
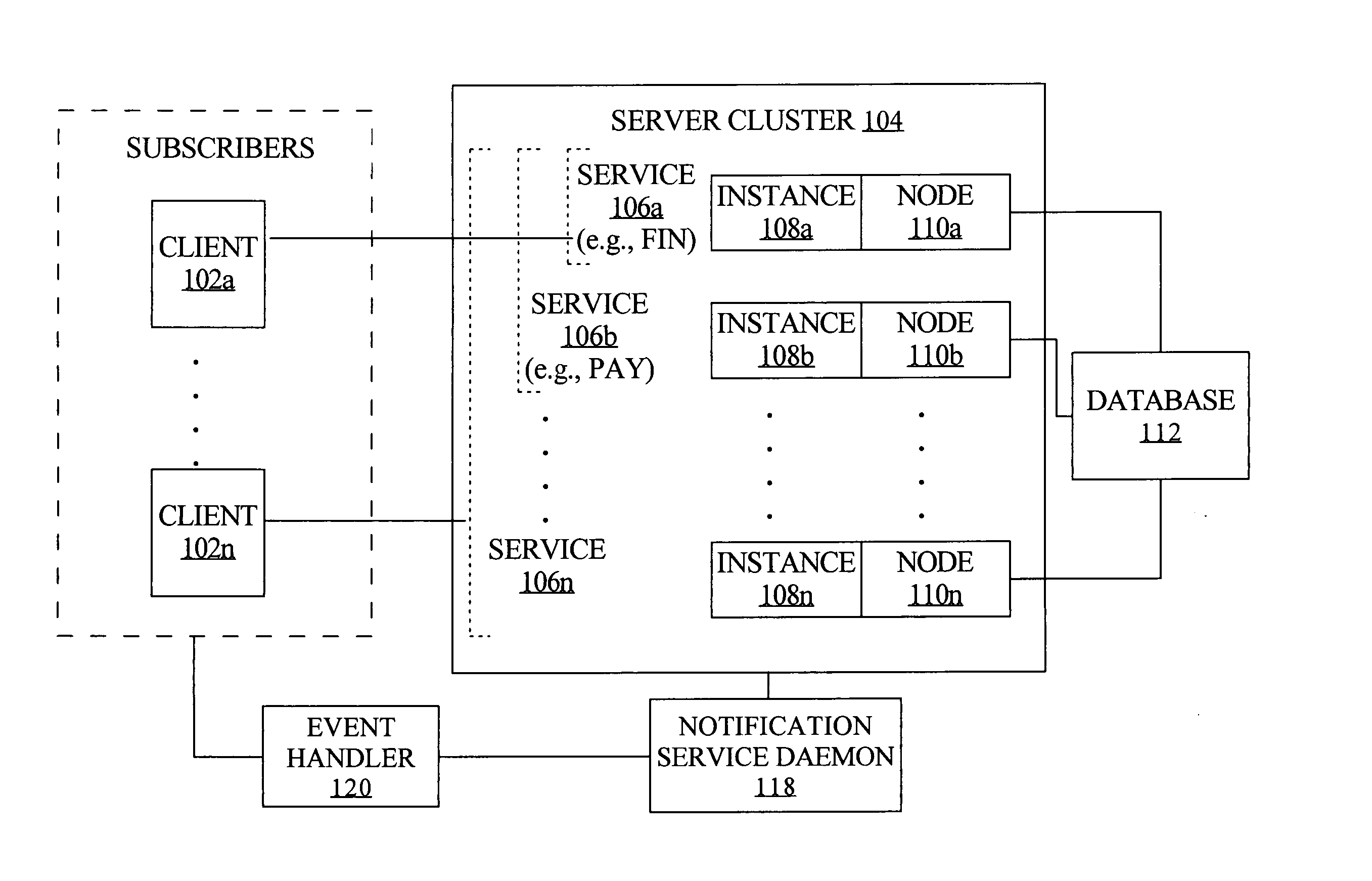
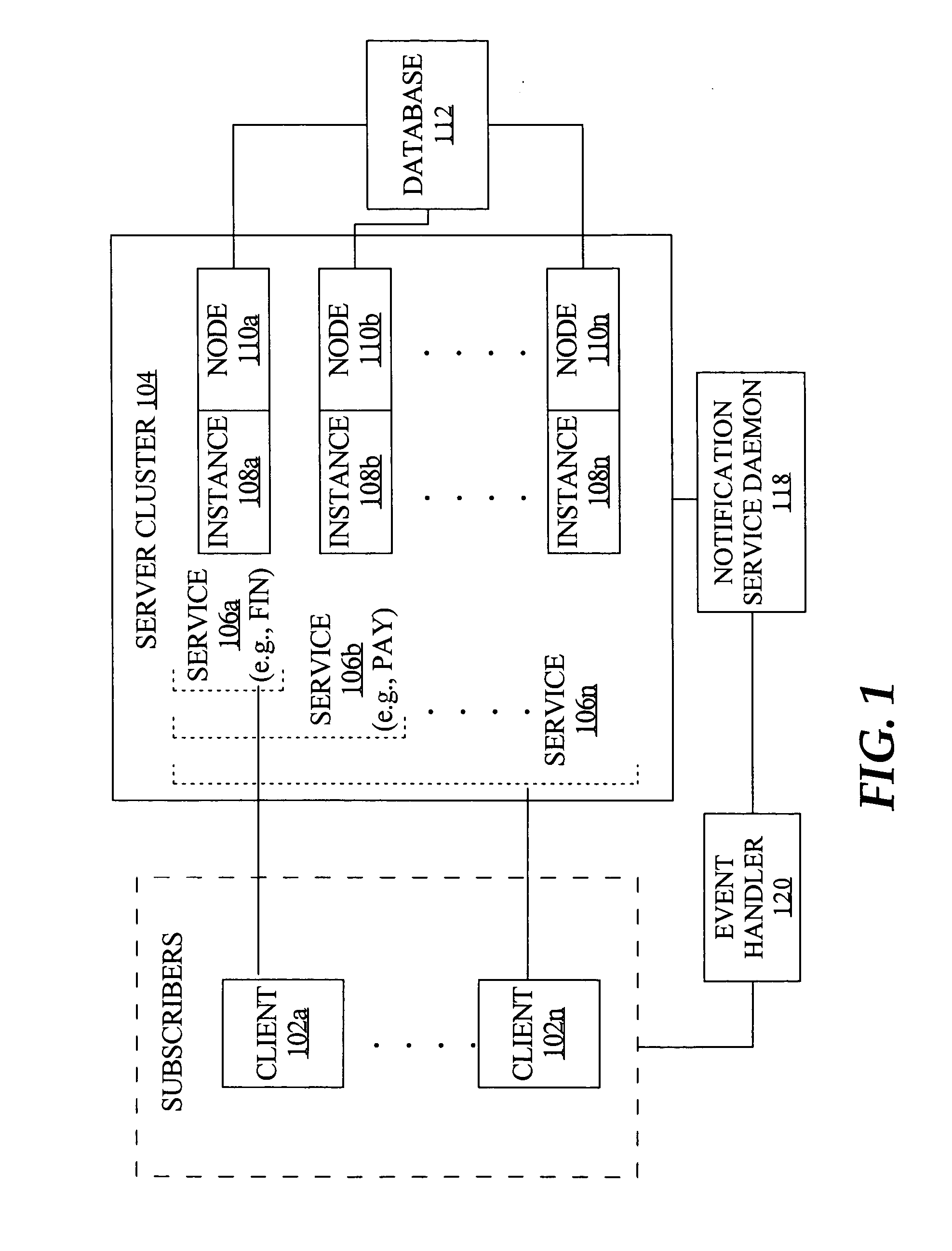
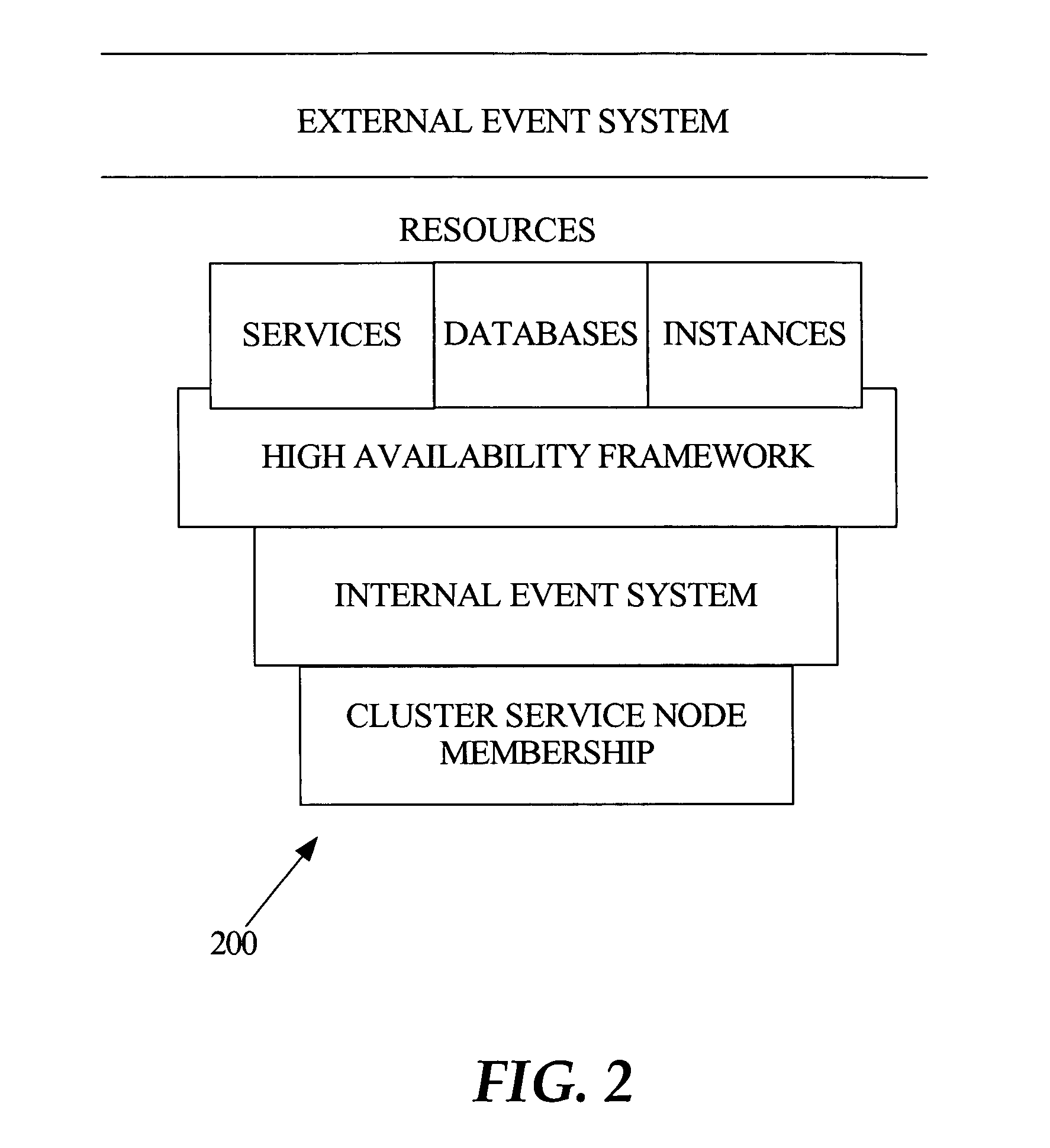
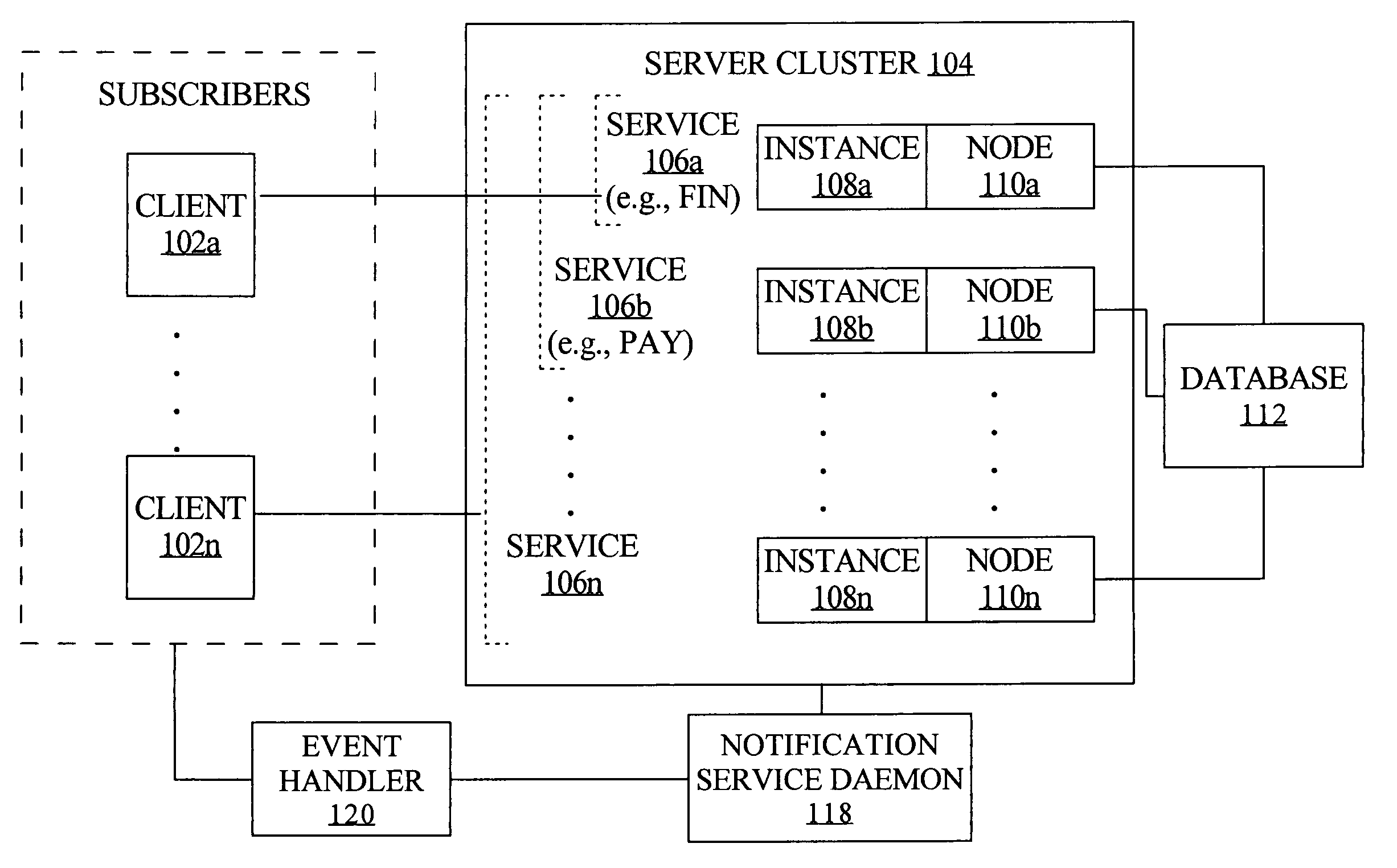
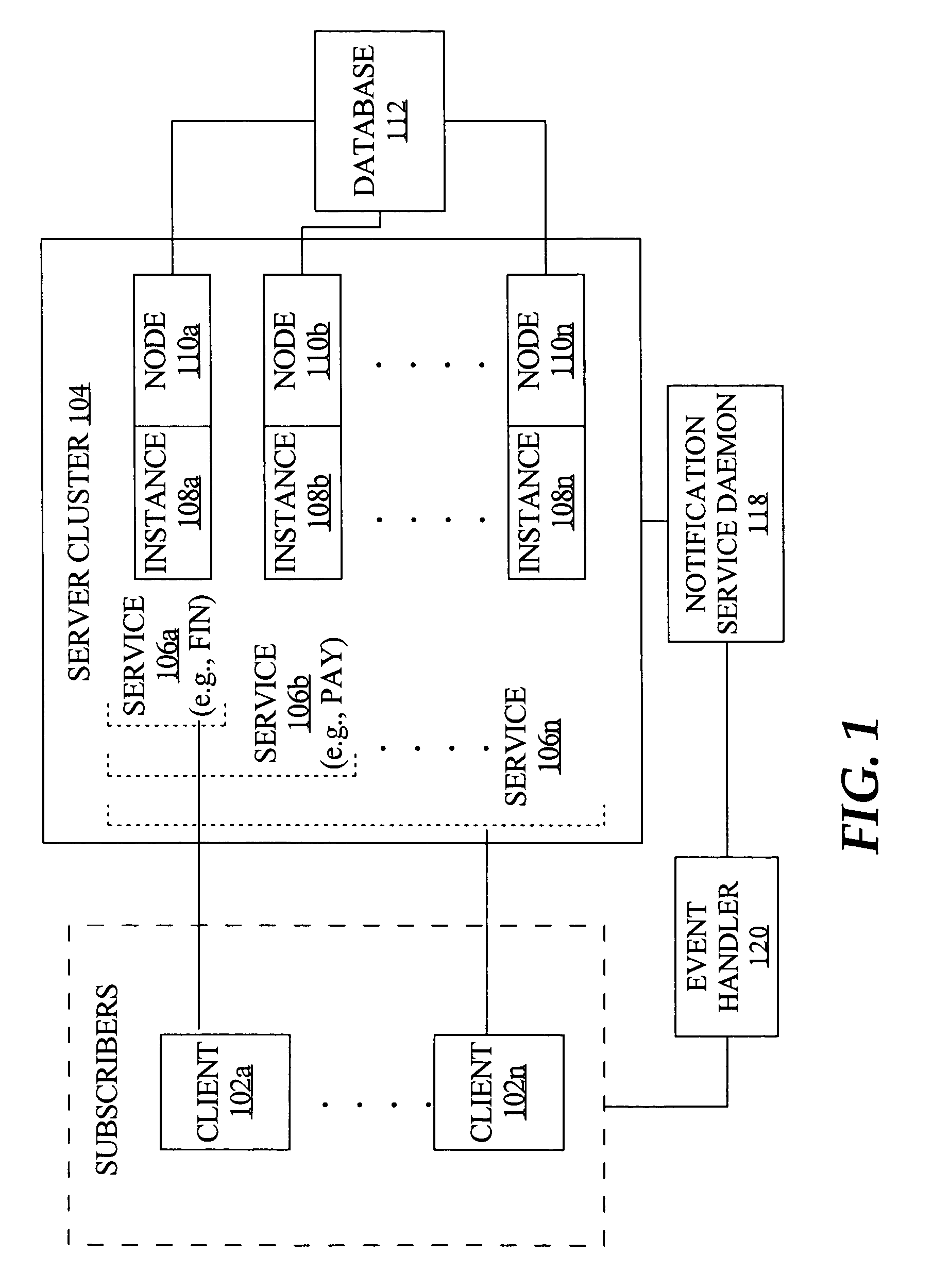
Fast application notification in a clustered computing system
ActiveUS20050038772A1Resource allocationDigital data processing detailsComputer networkService experience
With fast notification of changes to a clustered computing system, through which a number of events are published for system state changes, applications can quickly recover and sessions can quickly be rebalanced. When a resource associated with a service experiences a change in status, such as a termination or a start / restart, a notification event is immediately published. Notification events contain information to enable subscribers to identify, based on matching a session signature, the particular sessions that are affected by the change in status, and to respond accordingly. This allows sessions to be quickly aborted and ongoing processing to be quickly terminated when a resource fails, and allows fast rebalancing of work when a resource is restarted.
Owner:ORACLE INT CORP
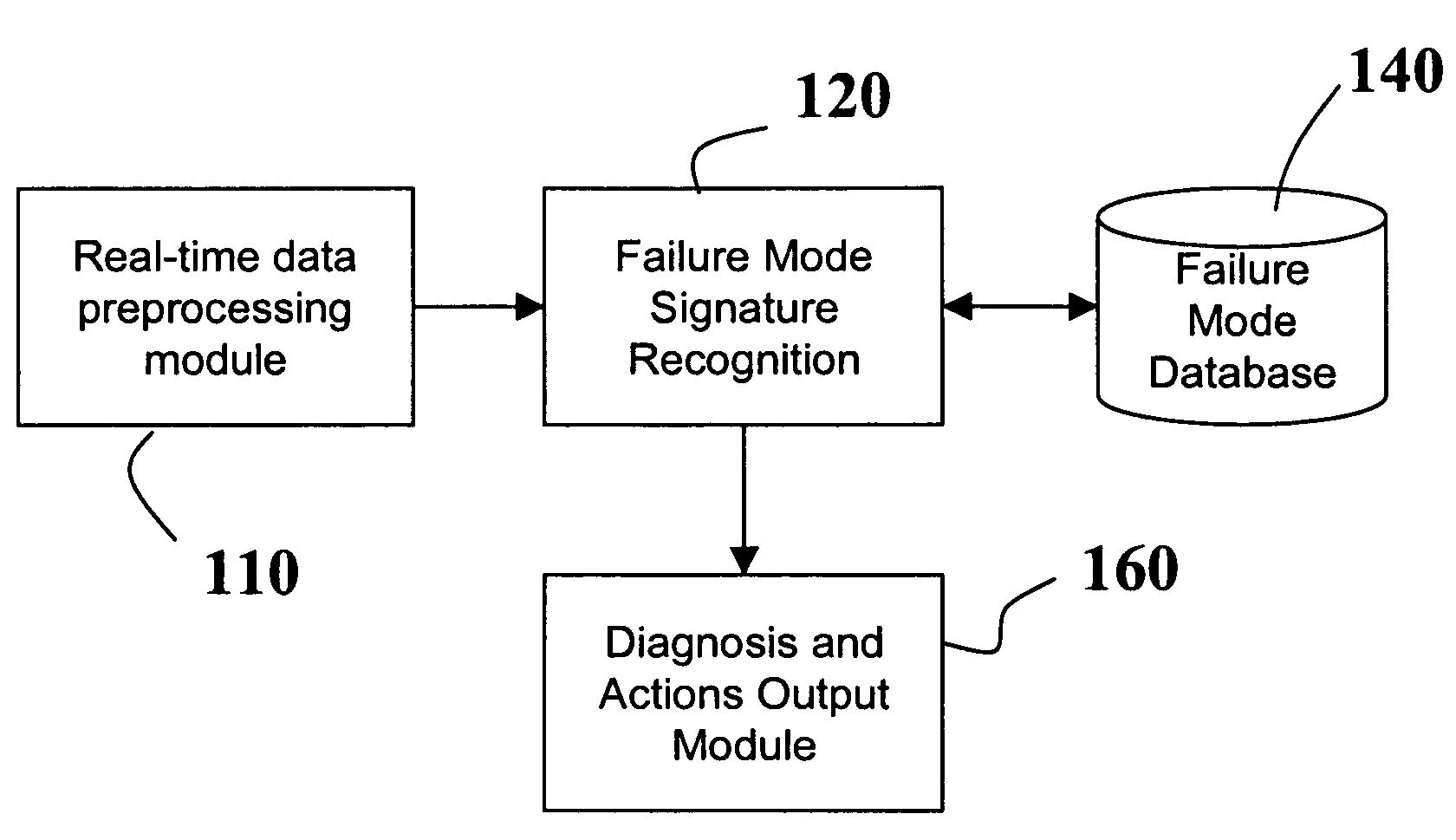
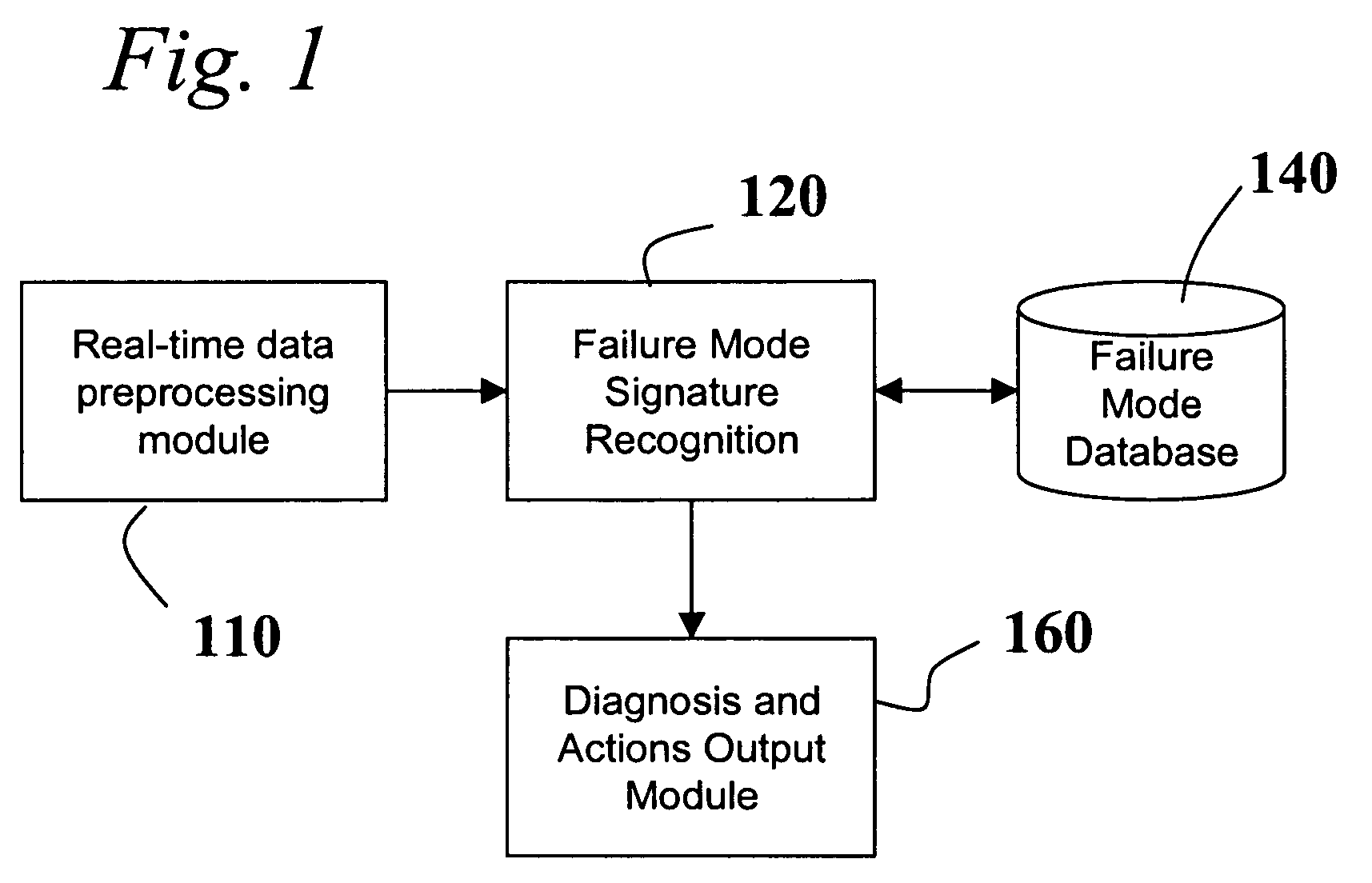
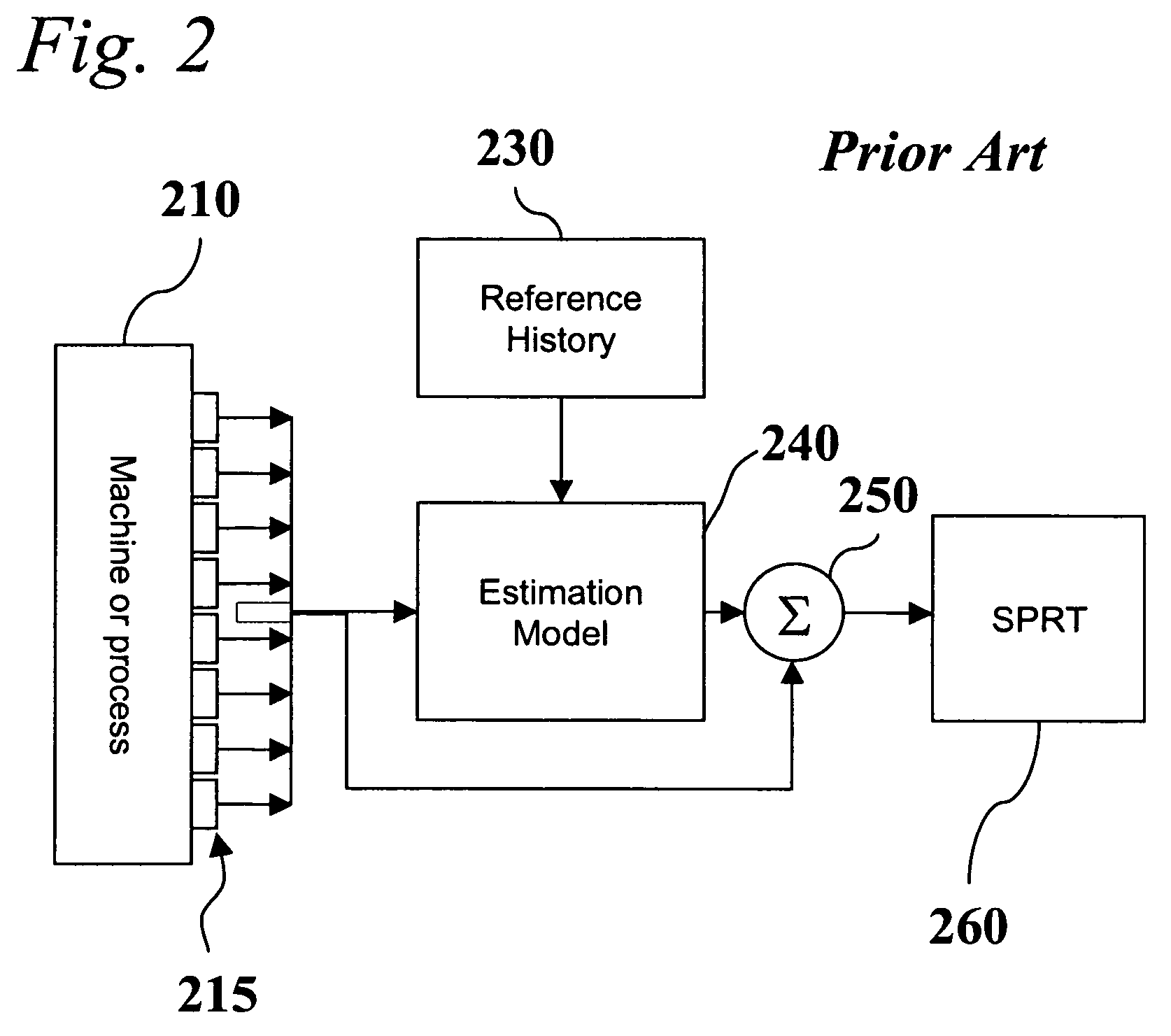
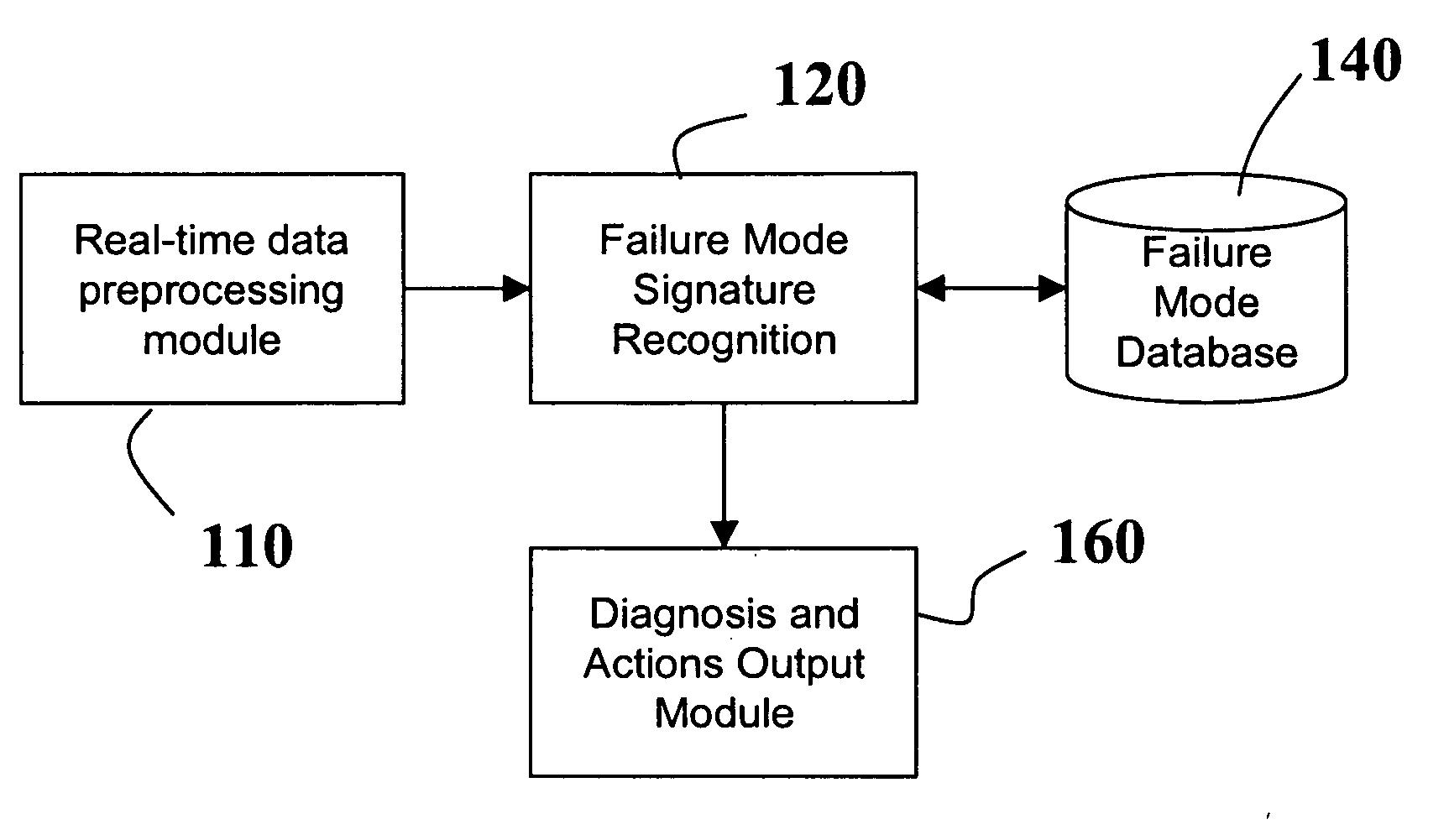
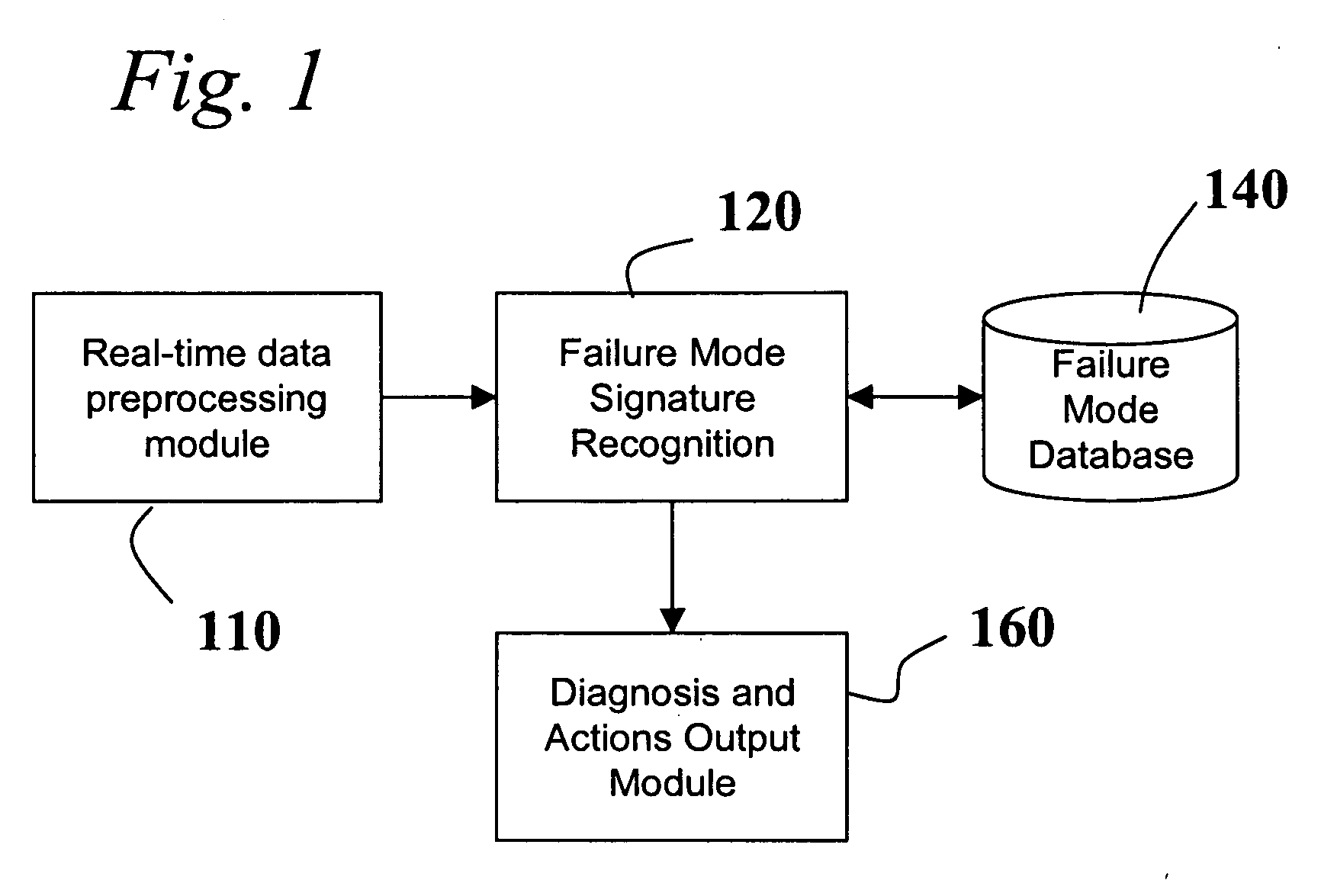
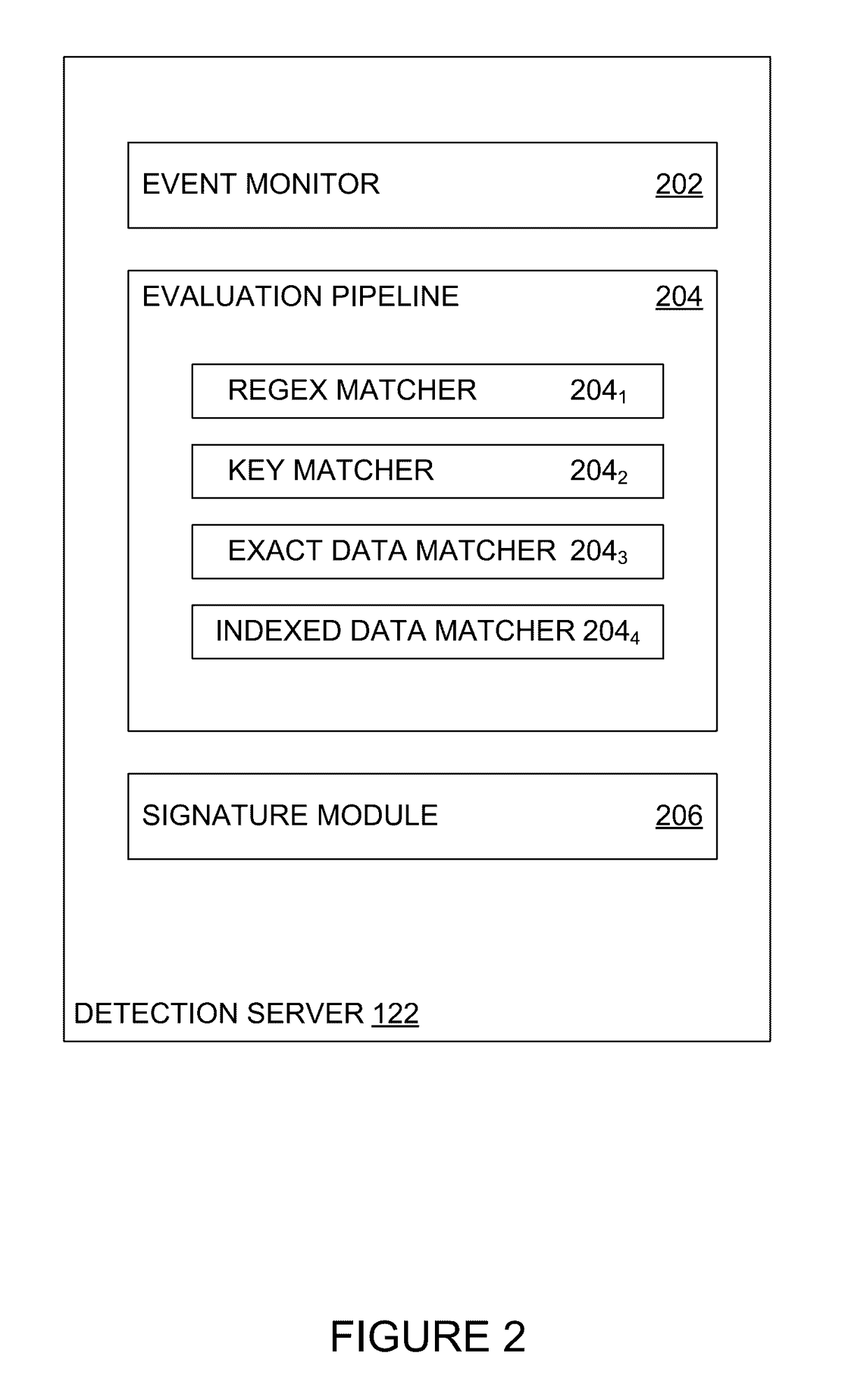
Diagnostic systems and methods for predictive condition monitoring
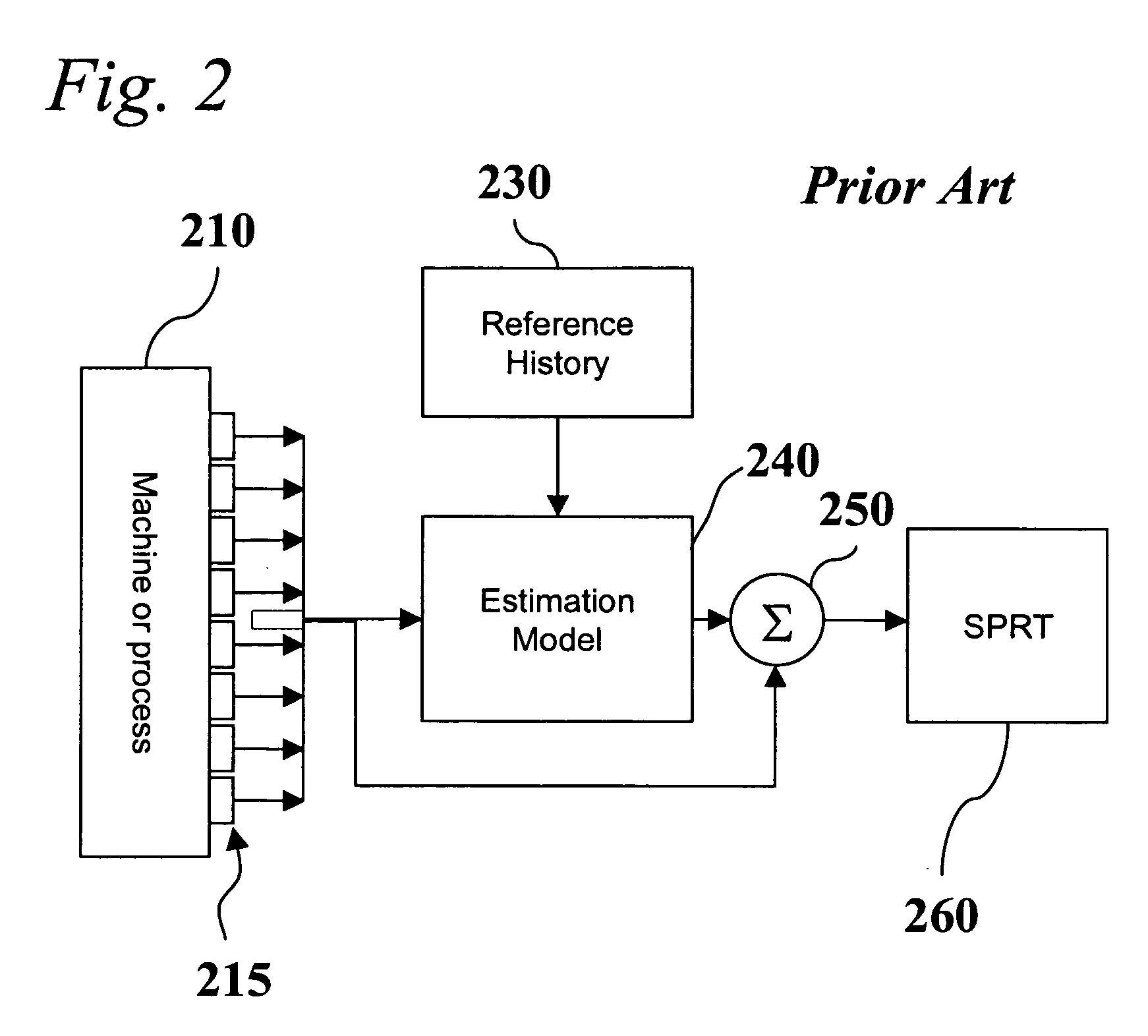
A system for empirically diagnosing a condition of a monitored system. Estimates of monitored parameters from a model of the system provide residual values that can be analyzed for failure mode signature recognition. Residual values can also be tested for alert (non-zero) conditions, and patterns of alerts thus generated are analyzed for failure mode signature patterns. The system employs a similarity operator for signature recognition and also for parameter estimation. Failure modes are empirically determined, and precursor data is automatically analyzed to determine differentiable signatures for failure modes.
Owner:SMARTSIGNAL CORP
Diagnostic systems and methods for predictive condition monitoring
InactiveUS20060036403A1Picture changing apparatusElectric testing/monitoringResidual valueComputer science
A system for empirically diagnosing a condition of a monitored system. Estimates of monitored parameters from a model of the system provide residual values that can be analyzed for failure mode signature recognition. Residual values can also be tested for alert (non-zero) conditions, and patterns of alerts thus generated are analyzed for failure mode signature patterns. The system employs a similarity operator for signature recognition and also for parameter estimation. Failure modes are empirically determined, and precursor data is automatically analyzed to determine differentiable signatures for failure modes.
Owner:SMARTSIGNAL CORP
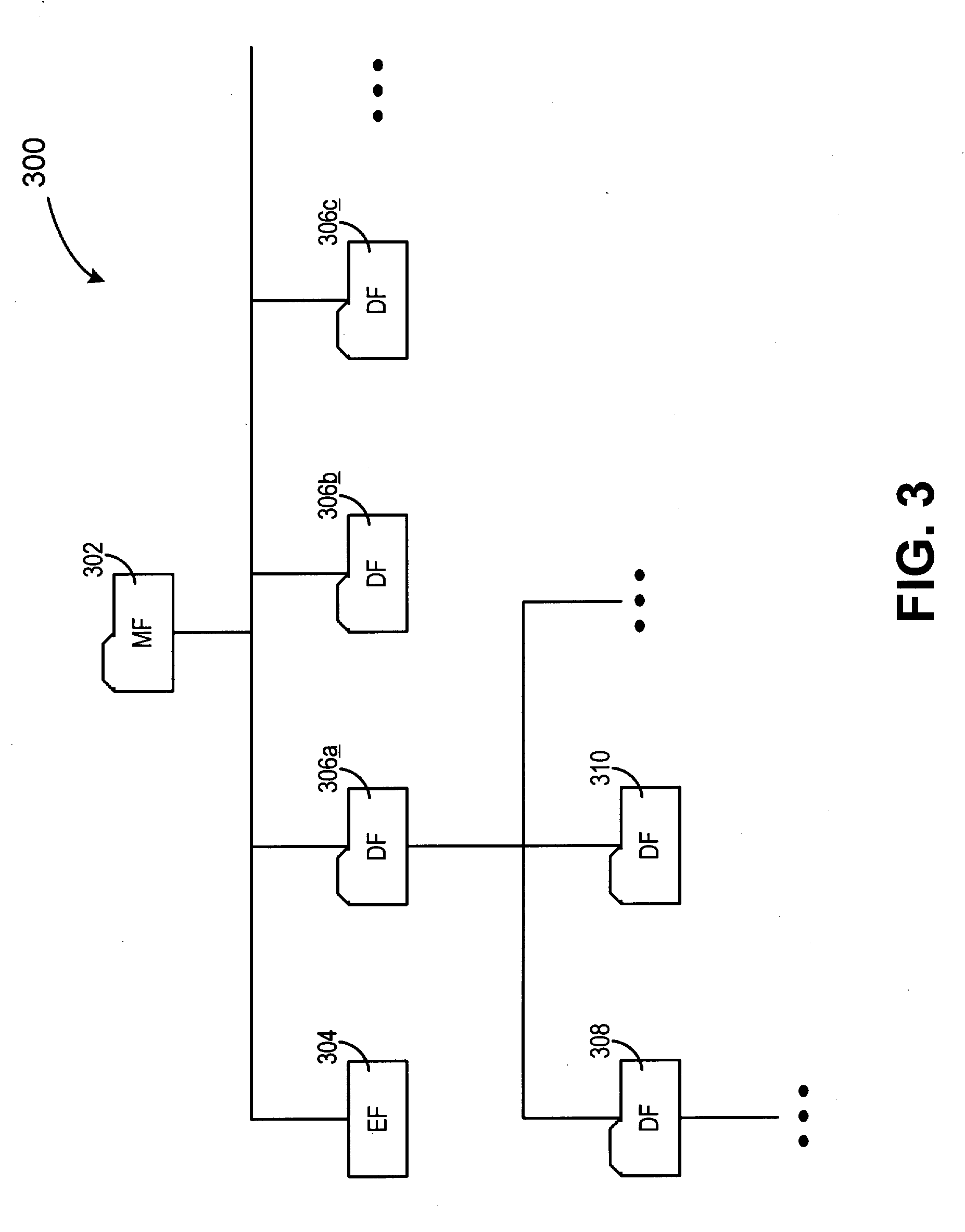
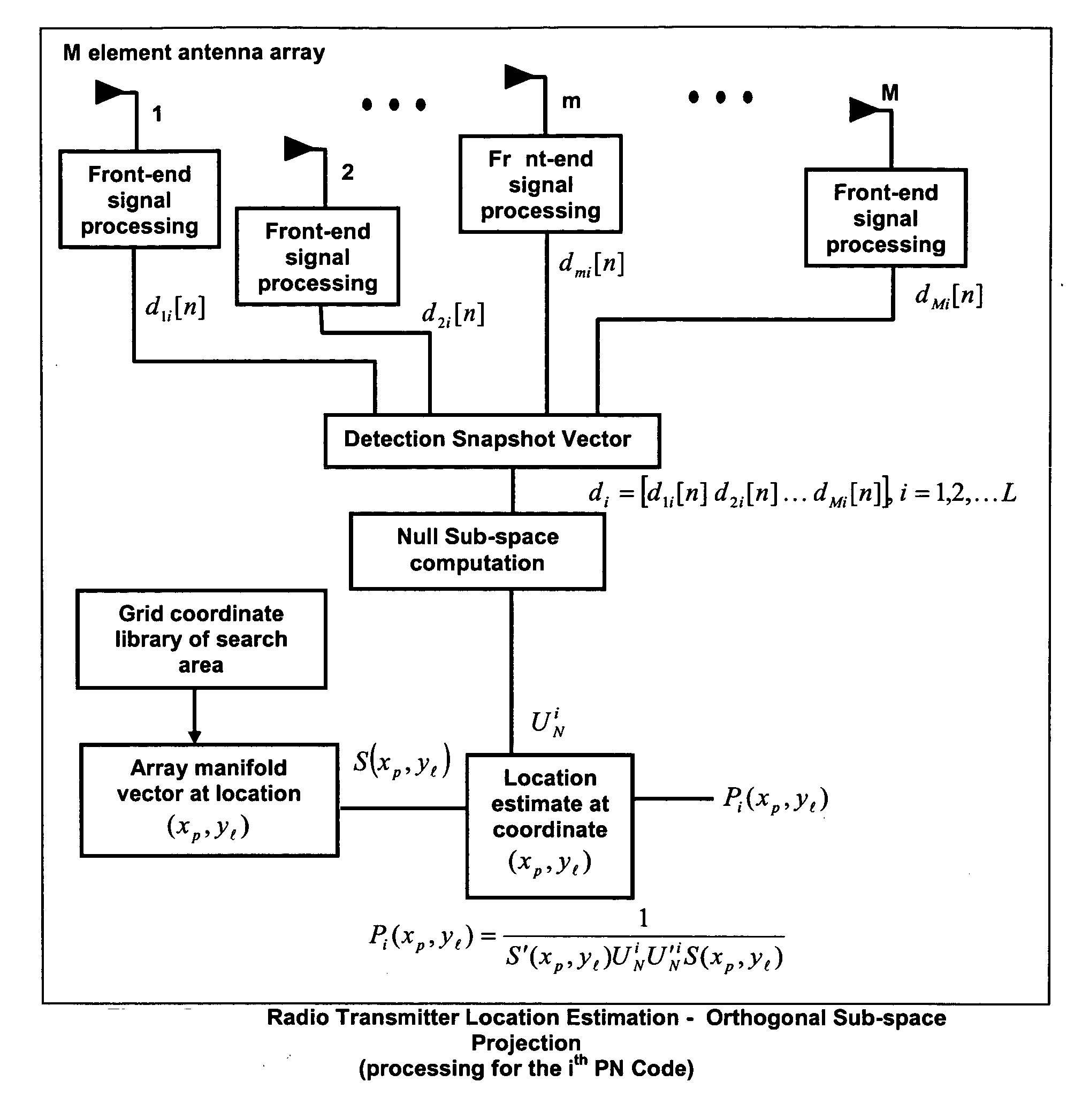
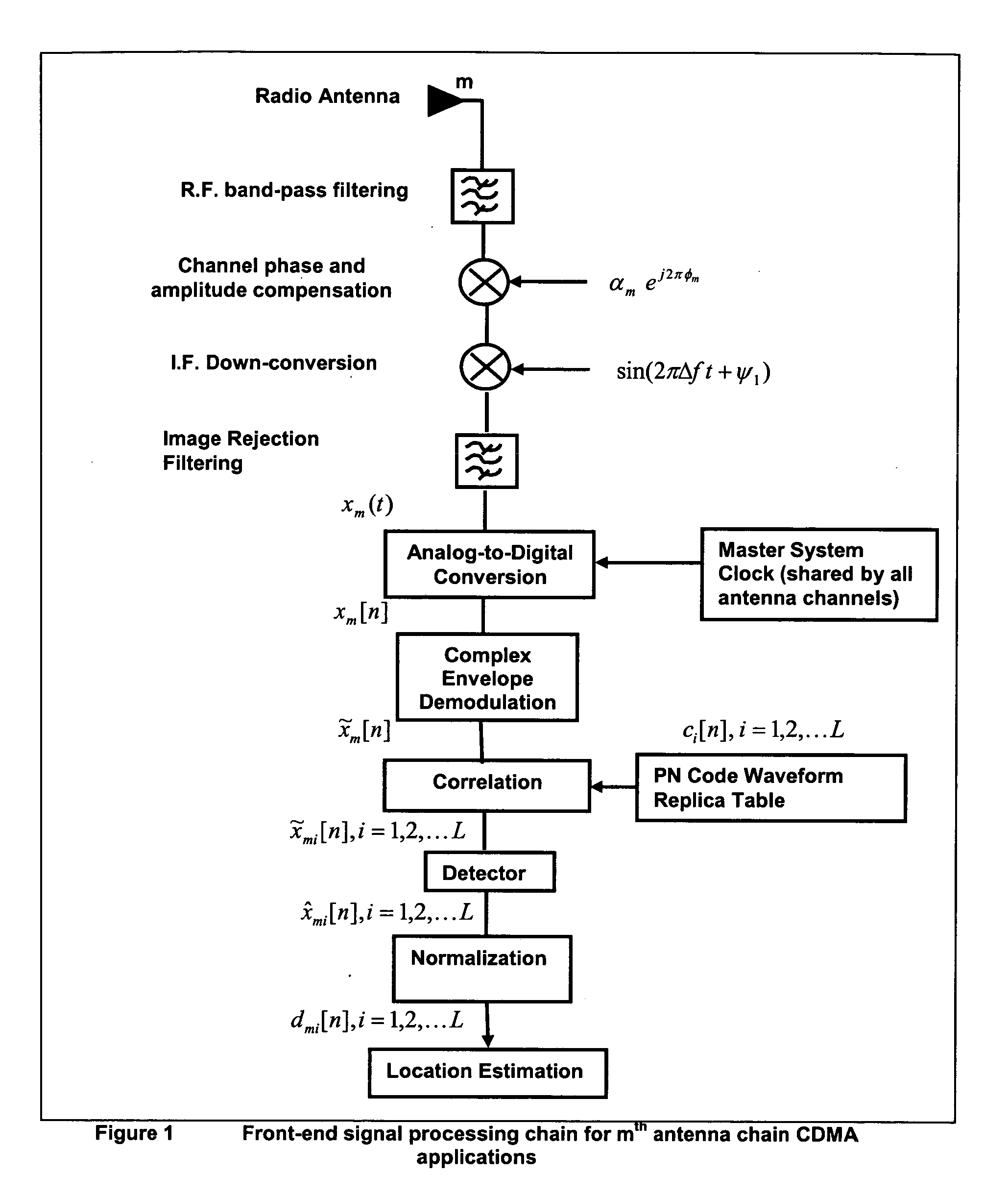
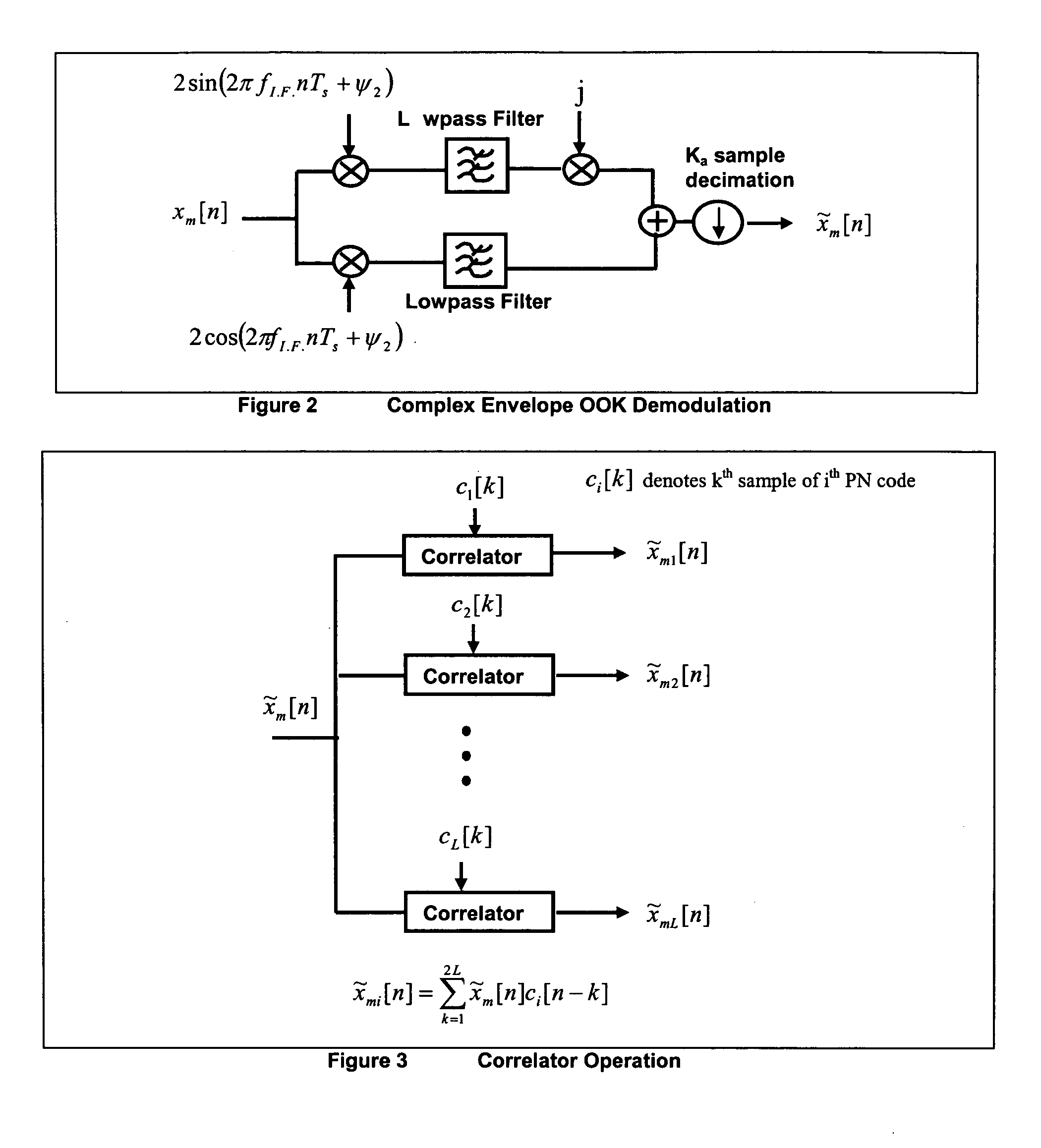
Random antenna array interferometer for radio location
InactiveUS6985107B2Effective of noise powerReduce coherenceDirection finders using radio wavesImage resolutionCarrier signal
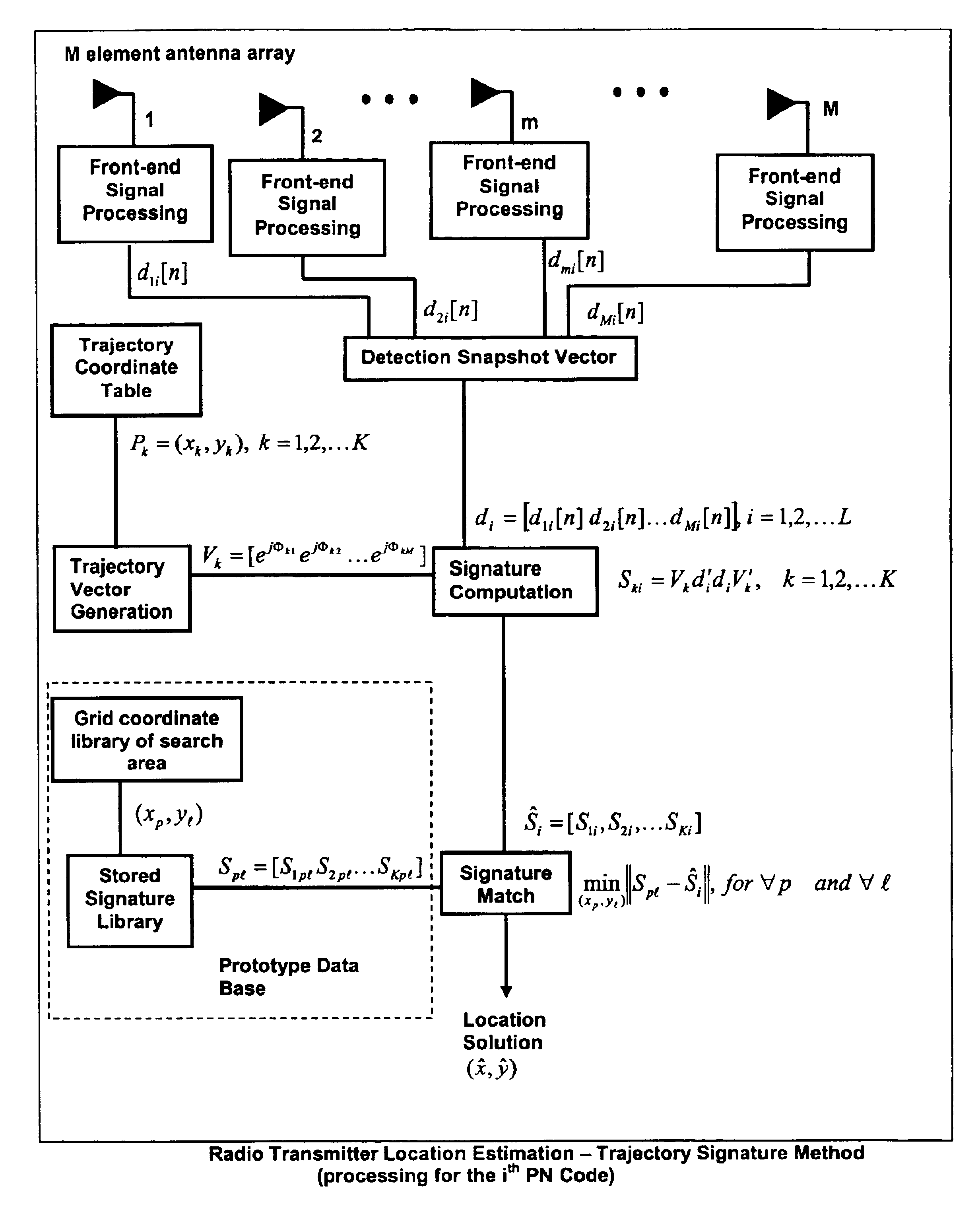
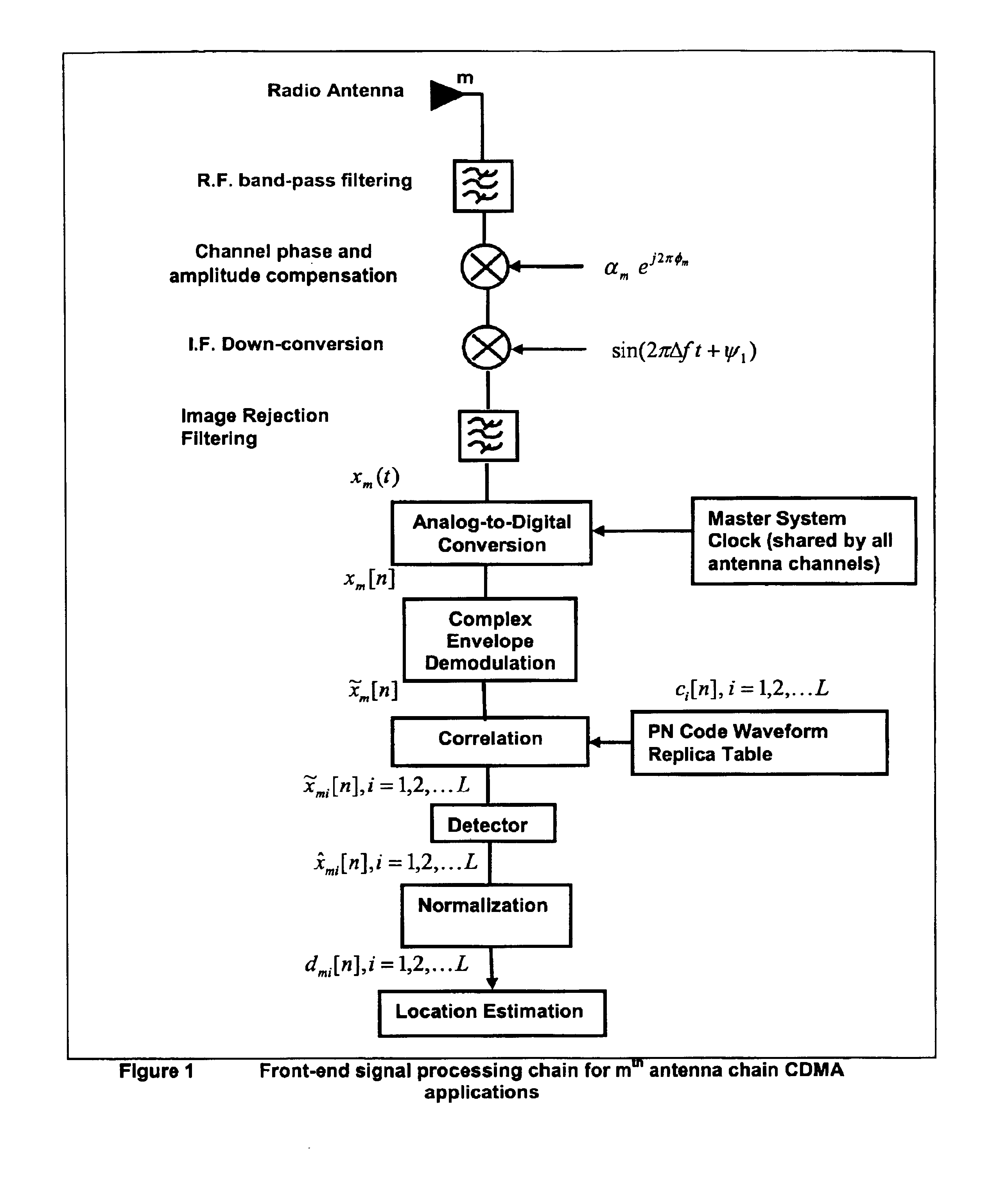
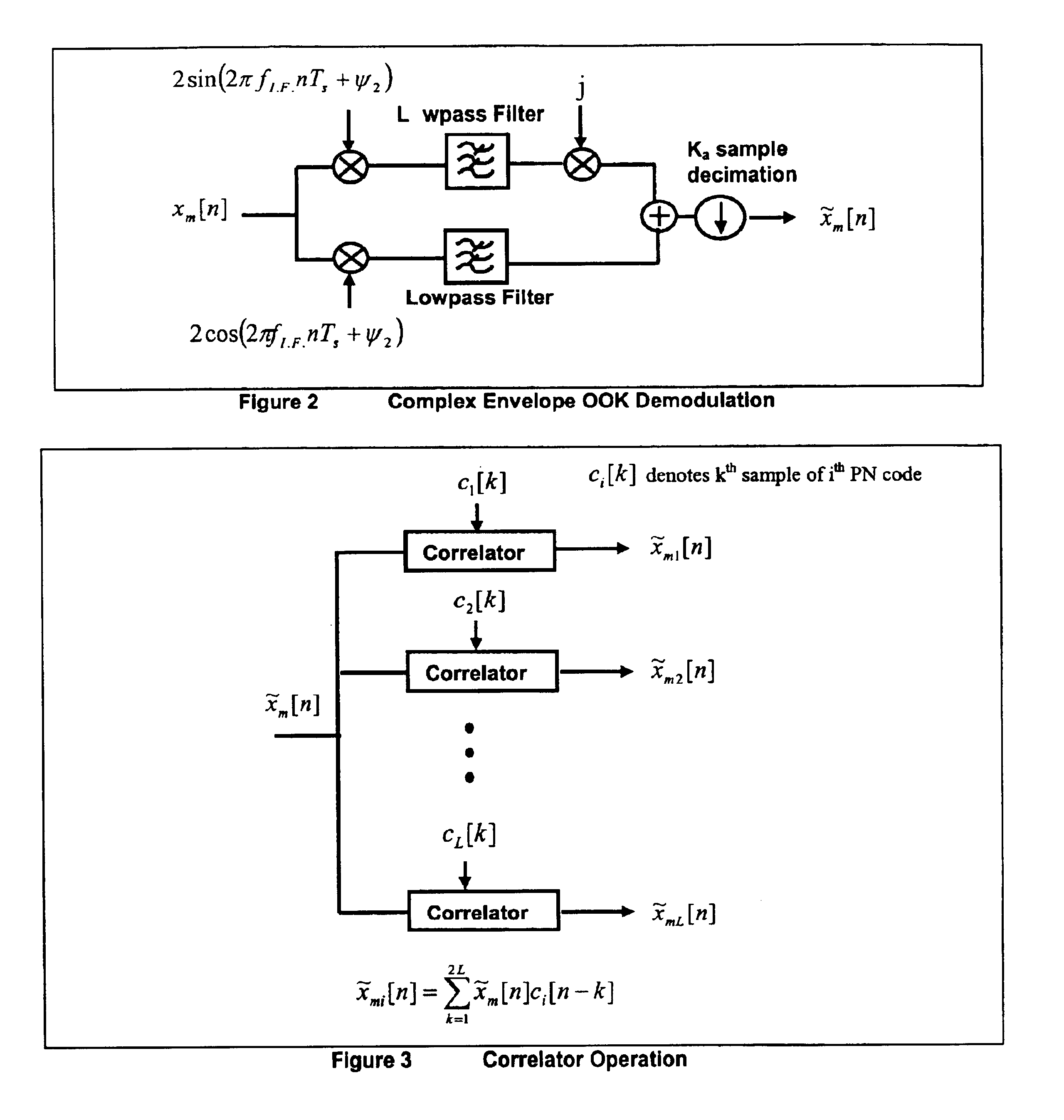
This invention relates to a method and system for the radio location of CDMA and non-CDMA enabled transmitters within a reception zone. The invention exploits the superposition of antenna patterns that create complex and asymmetrical interference structures at very small scales. By randomly distributing a random antenna array of M elements across a two or three-dimensional surface, fine scale interference structures on the scale of ¼ the carrier wavelength are generated. Once the minimum number of antennas are placed, additional antennas will not improve the resolution. Such interference structures when sampled at ⅛ the carrier wavelength or greater yields unique spatial patterns with respect to a given antenna array geometry and transmitter location. The invention incorporates signature recognition (matching) and orthogonal sub-space projection estimators to derive location estimates of a radio transmitter.
Owner:LOTEK WIRELESS
Unsupervised indoor localization and heading directions estimation
InactiveUS20150281910A1Improve the accuracy of the indoor localization of that userParticular environment based servicesPosition fixationStudy PositionSignature recognition
Owner:DUKE UNIV
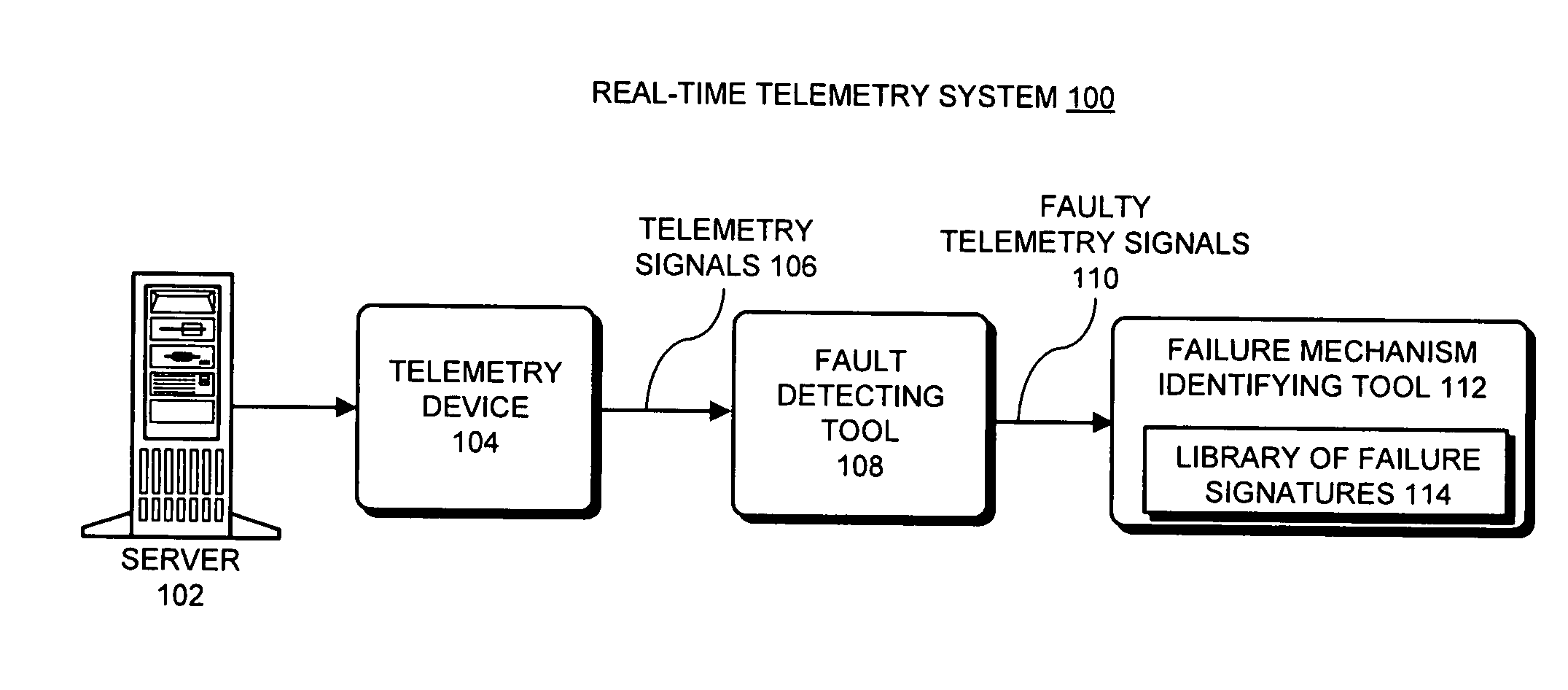
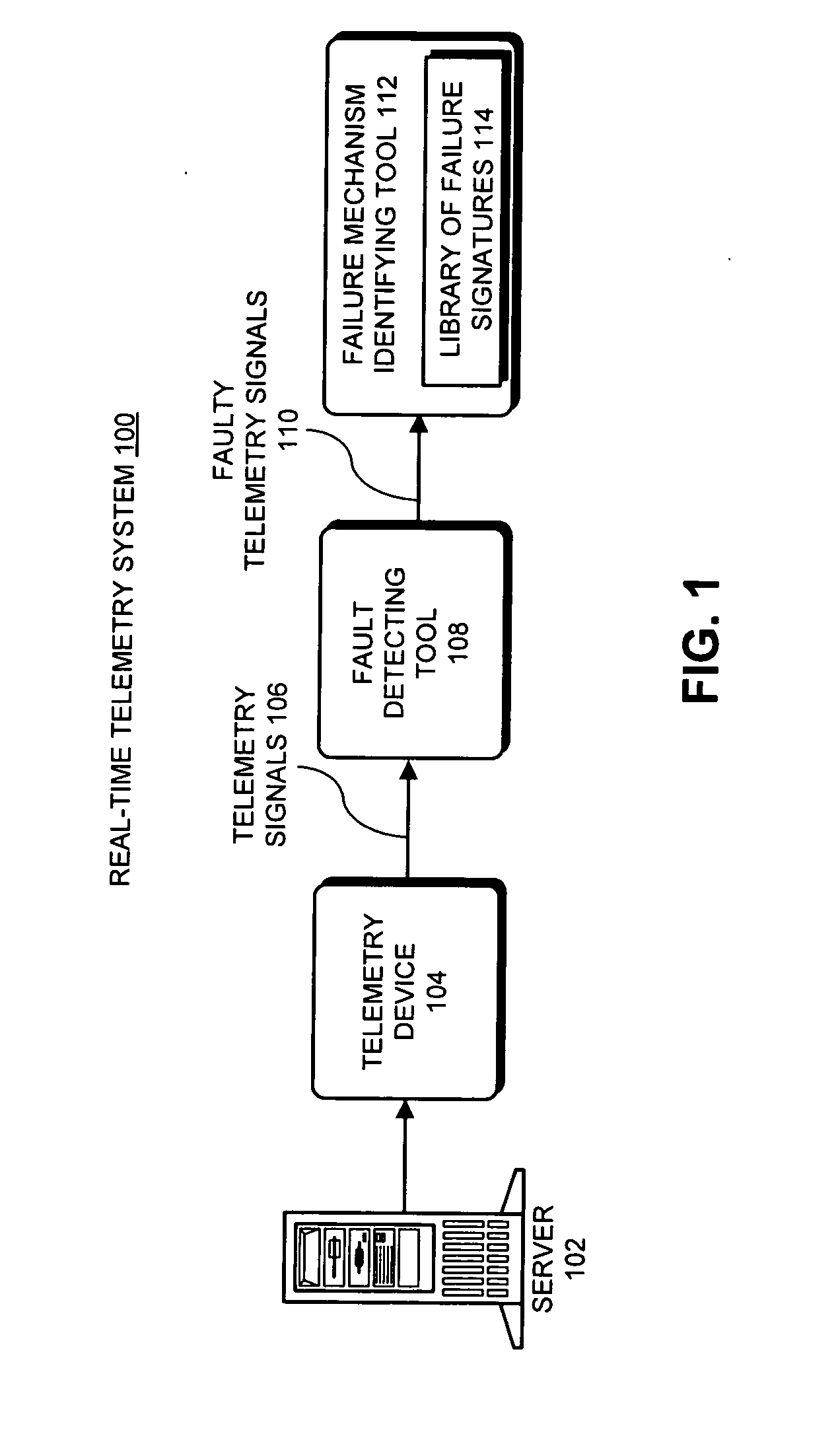
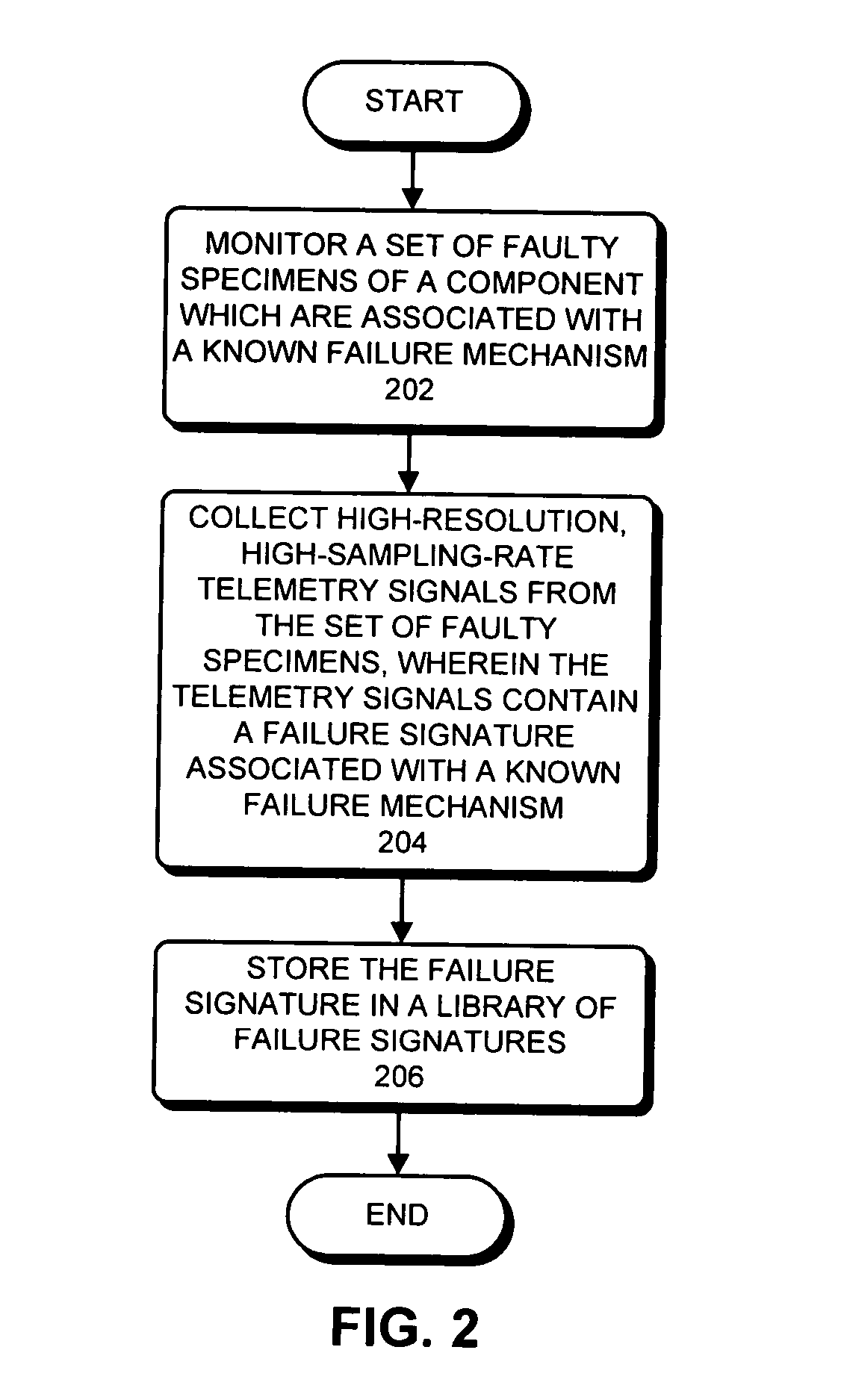
Method and apparatus for identifying a failure mechanism for a component in a computer system
ActiveUS20070294591A1Reduce resolutionNuclear monitoringDigital computer detailsPattern matchingFailure mechanism
One embodiment of the present invention provides a system that identifies a failure mechanism for a component. The system first constructs a library of failure signatures from a set of components, wherein each failure signature in the library characterizes a known failure mechanism associated with a component in the set of components. Next, the system receives a telemetry signal which is measured from a component under surveillance. The system then determines if there is an anomaly in the telemetry signal. If so, the system performs pattern-matching operations between the telemetry signal and failure signatures in the library. Next, if a match is found, the system identifies the failure mechanism for the component under surveillance based on the matching failure signature.
Owner:ORACLE INT CORP
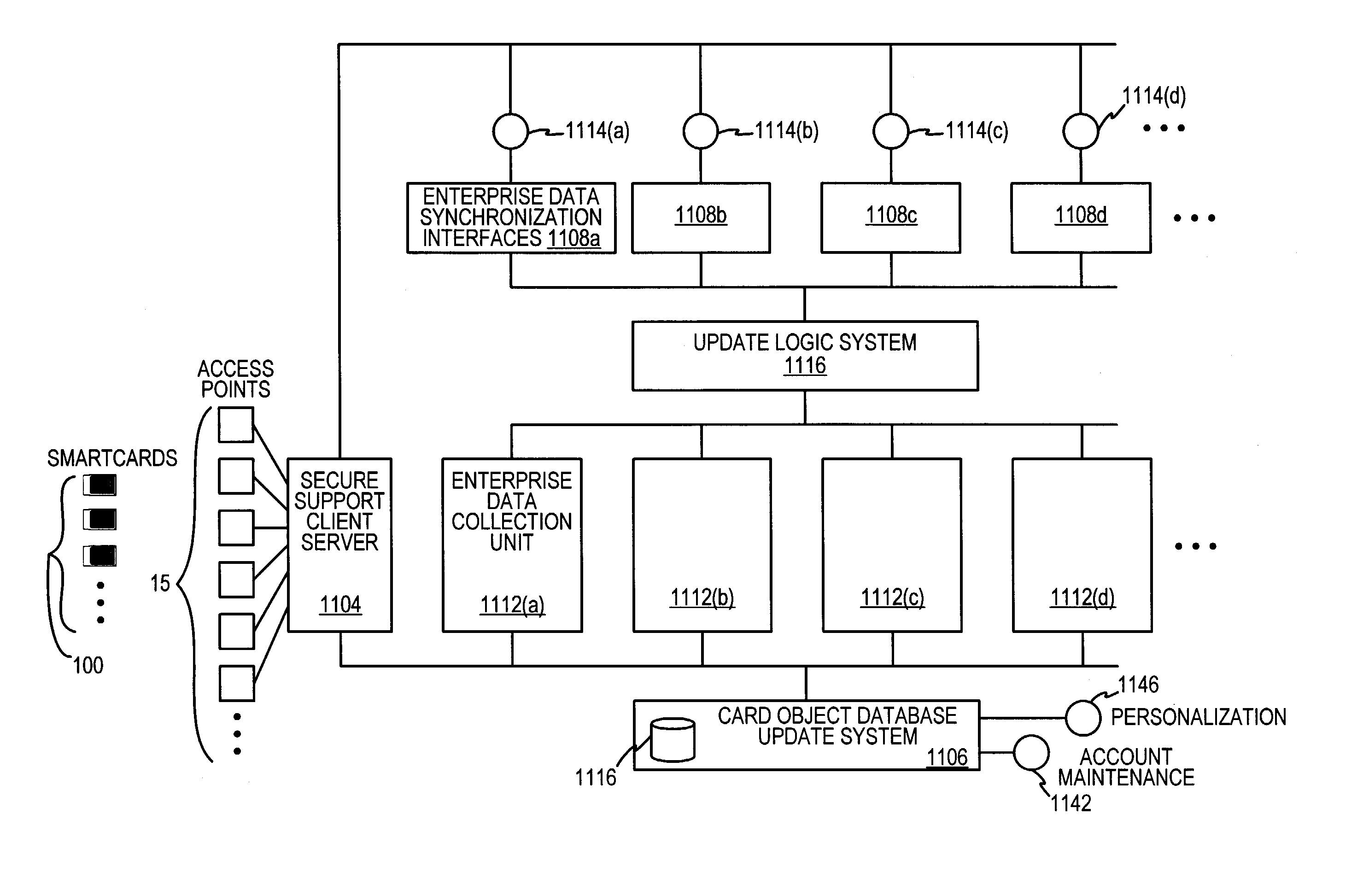
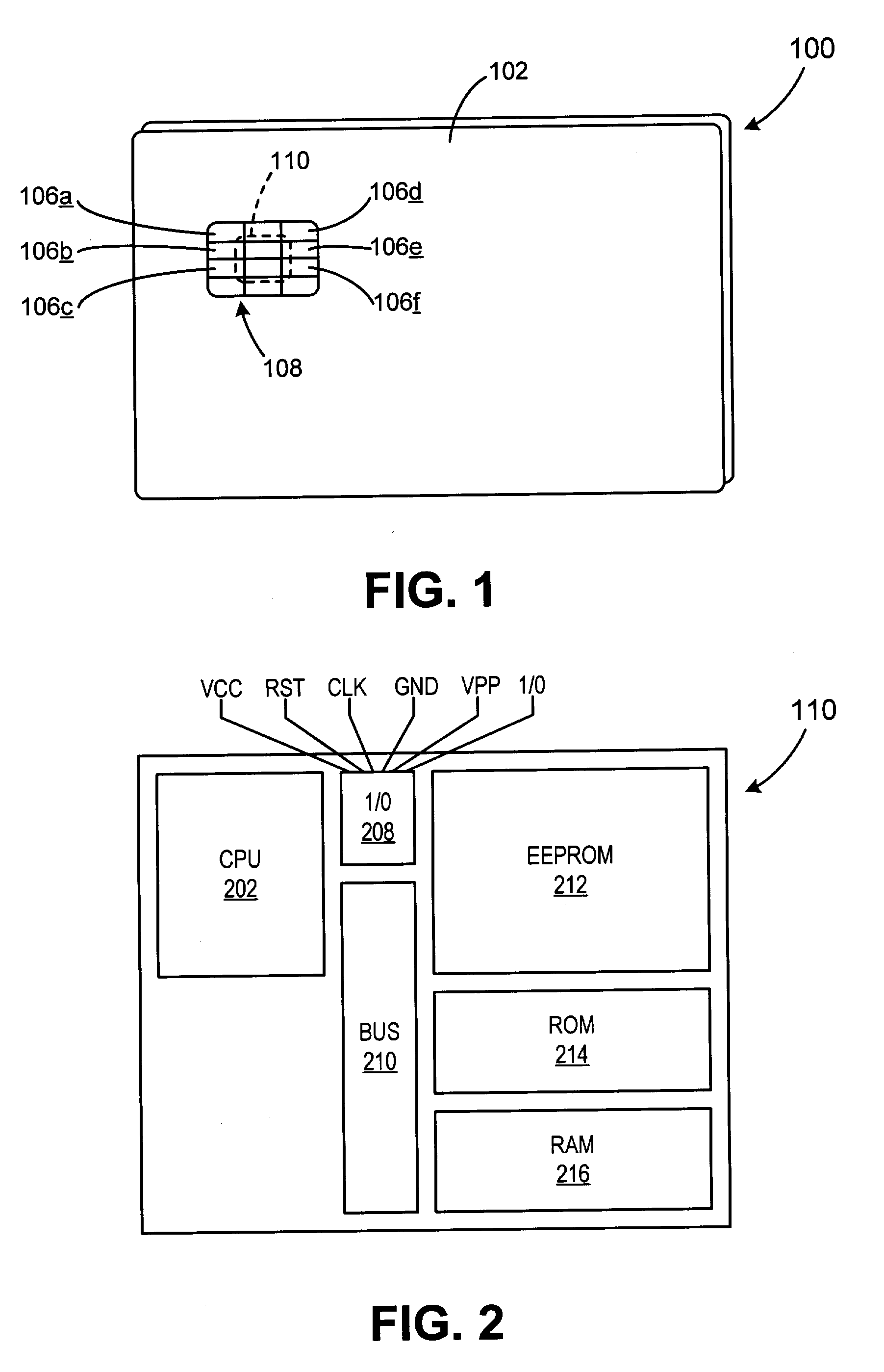
Method and system for signature recognition biometrics on a smartcard
InactiveUS20060000897A1Security is importantAcutation objectsPayment architectureSmart cardAuthorization
The present invention discloses a system and methods for biometric security using signature recognition biometrics in a smartcard-reader system. The biometric security system also includes a signature scan sensor that detects biometric samples and a device for verifying biometric samples. In one embodiment, the biometric security system includes a smartcard configured with a signature scan sensor. In another embodiment, the system includes a reader configured with a signature scan sensor. In yet another embodiment, the present invention discloses methods for proffering and processing signature samples to facilitate authorization of transactions.
Owner:LIBERTY PEAK VENTURES LLC +1
Random antenna array interferometer for radio location
InactiveUS20050007278A1Effective of noise powerReduce coherenceDirection finders using radio wavesImage resolutionCarrier signal
This invention relates to a method and system for the radio location of CDMA and non-CDMA enabled transmitters within a reception zone. The invention exploits the superposition of antenna patterns that create complex and asymmetrical interference structures at very small scales. By randomly distributing a random antenna array of M elements across a two or three-dimensional surface, fine scale interference structures on the scale of ¼ the carrier wavelength are generated. Once the minimum number of antennas are placed, additional antennas will not improve the resolution. Such interference structures when sampled at ⅛ the carrier wavelength or greater yields unique spatial patterns with respect to a given antenna array geometry and transmitter location. The invention incorporates signature recognition (matching) and orthogonal sub-space projection estimators to derive location estimates of a radio transmitter.
Owner:LOTEK WIRELESS
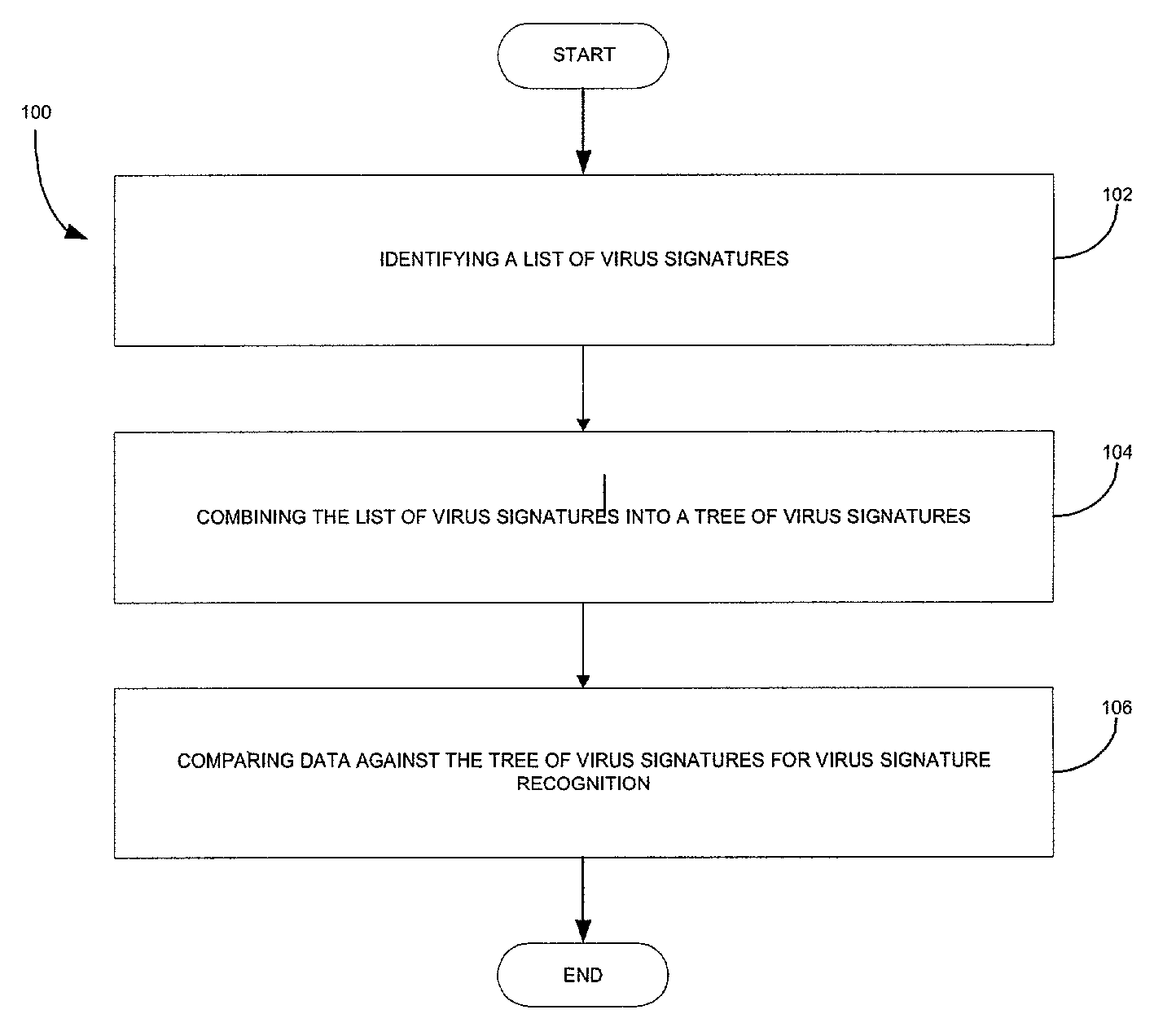
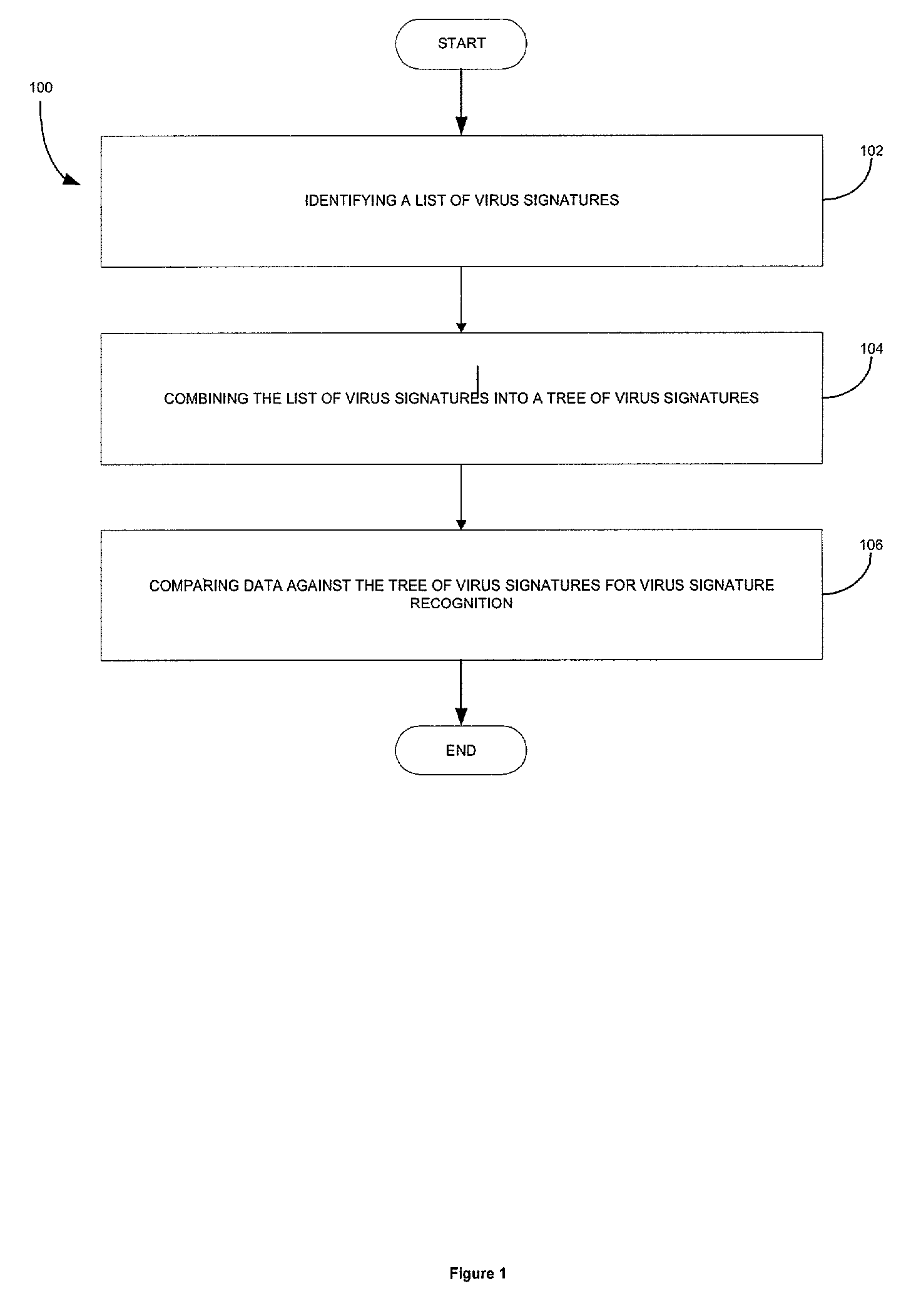
Tree pattern system and method for multiple virus signature recognition
ActiveUS6980992B1Improve efficiencyData processing applicationsComputer security arrangementsTree patternVirus
A system, method and computer program product are provided for recognizing virus signatures. Initially, a list of virus signatures is provided. Next, the list of virus signatures is combined into a tree of virus signatures. Data is subsequently compared against the tree of virus signatures for virus signature recognition.
Owner:MCAFEE LLC
System for and method of web signature recognition system based on object map
InactiveUS7715600B2Simple methodDigital data processing detailsUser identity/authority verificationGraphicsObject based
The present invention includes a system and a method of validating an identity of a user using a pointing device by comparing a sampled mouse signature with an authenticated mouse signature. The method includes presenting a virtual pad including a background graphic image, a plurality of objects positioned on the background graphic image to a user. The user moves the pointing device to manipulate a cursor on the background graphic image. The method includes a step of sampling a plurality of events corresponding to positions of the cursor to provide a sampled mouse signature including a set of position vectors. The present invention includes comparing the sampled mouse signature to a stored mouse signature representing the identity of a user, and validating the identity of a user in response to the comparing step.
Owner:ARTIFICIAL INTELLIGENCE RES GRP LTD
Method and device for recognizing handwritten signature and starting system by handwritten signature
InactiveCN101526992AImprove recognition efficiencyImprove matching accuracyCharacter and pattern recognitionPattern recognitionSignature recognition
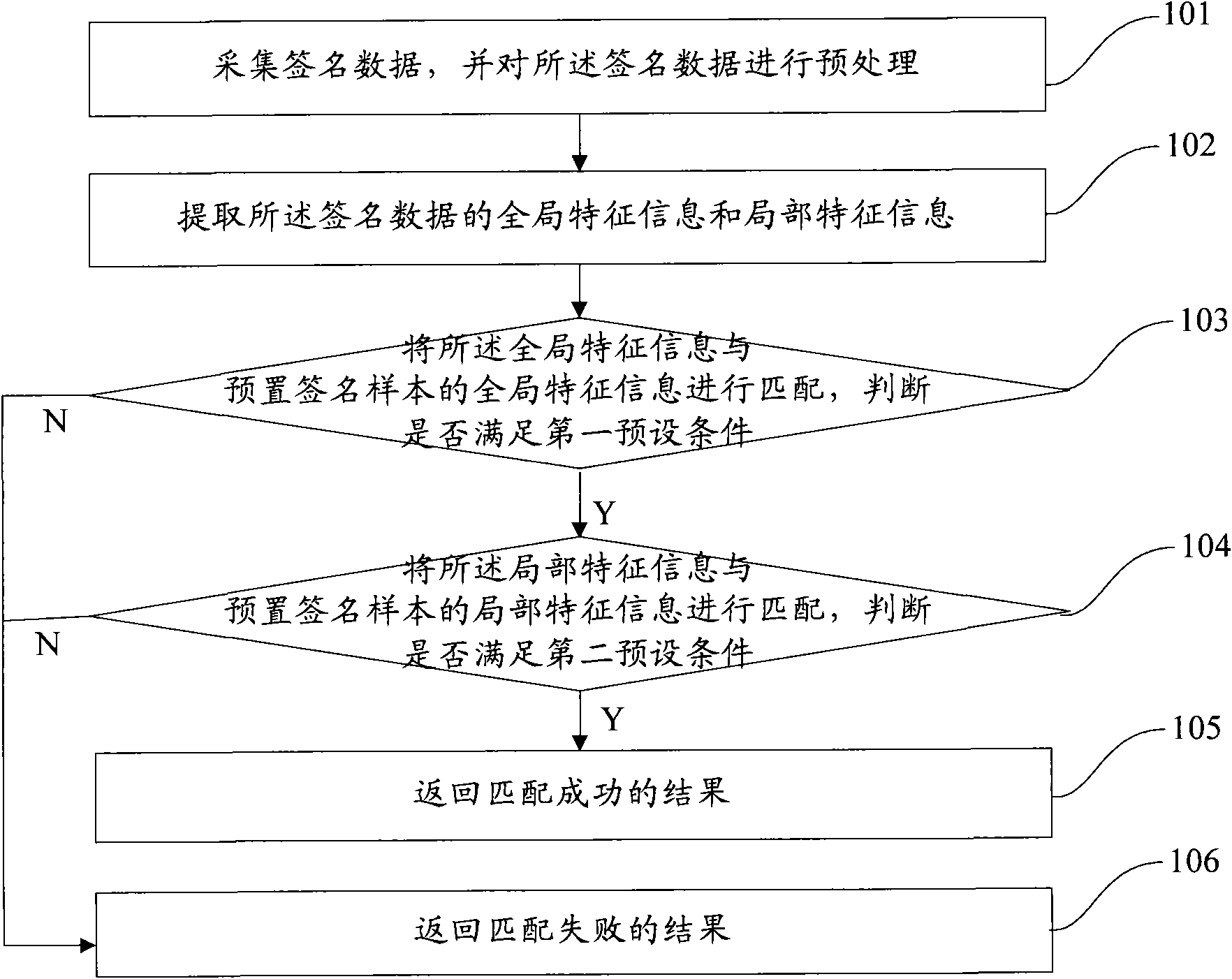
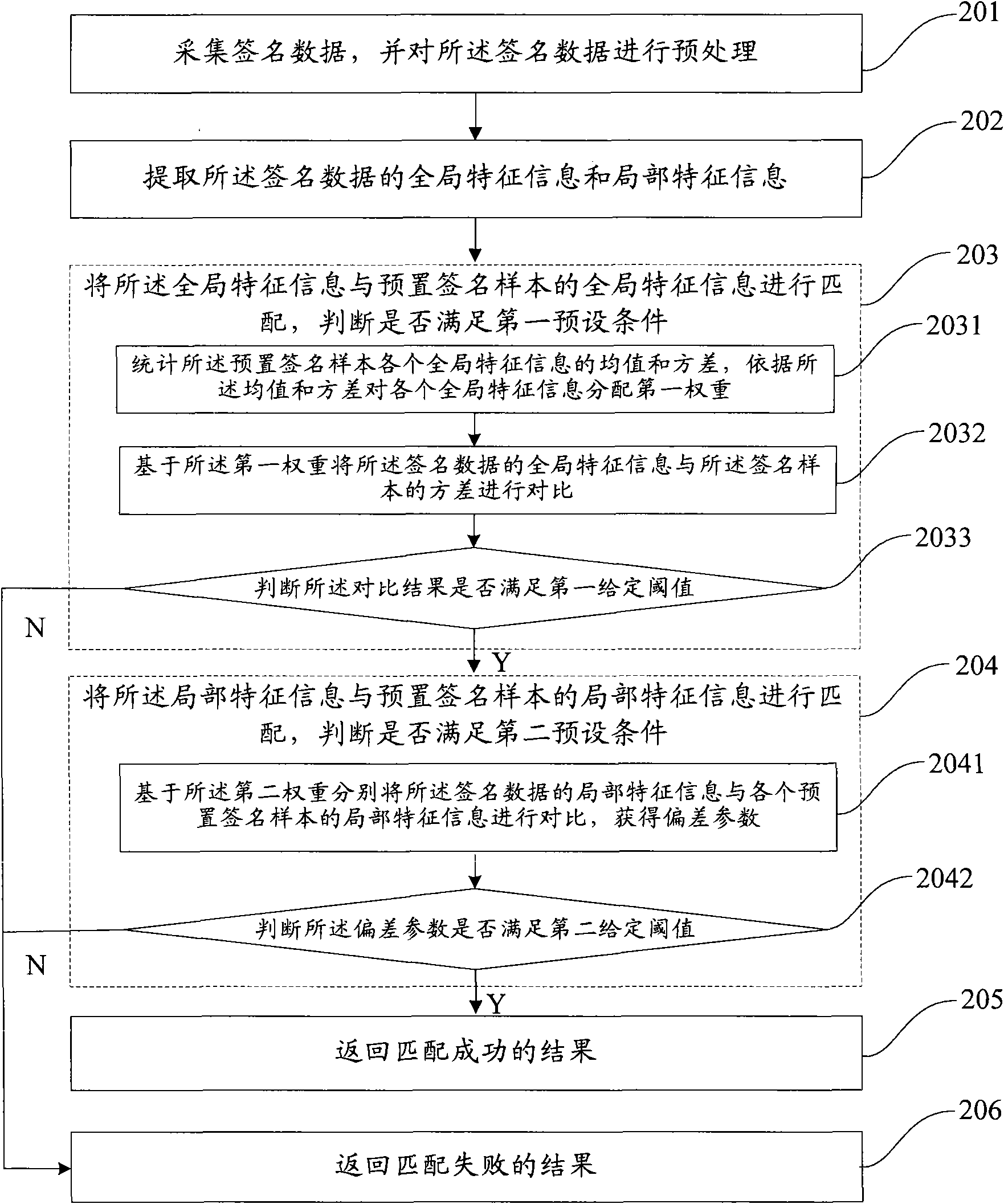
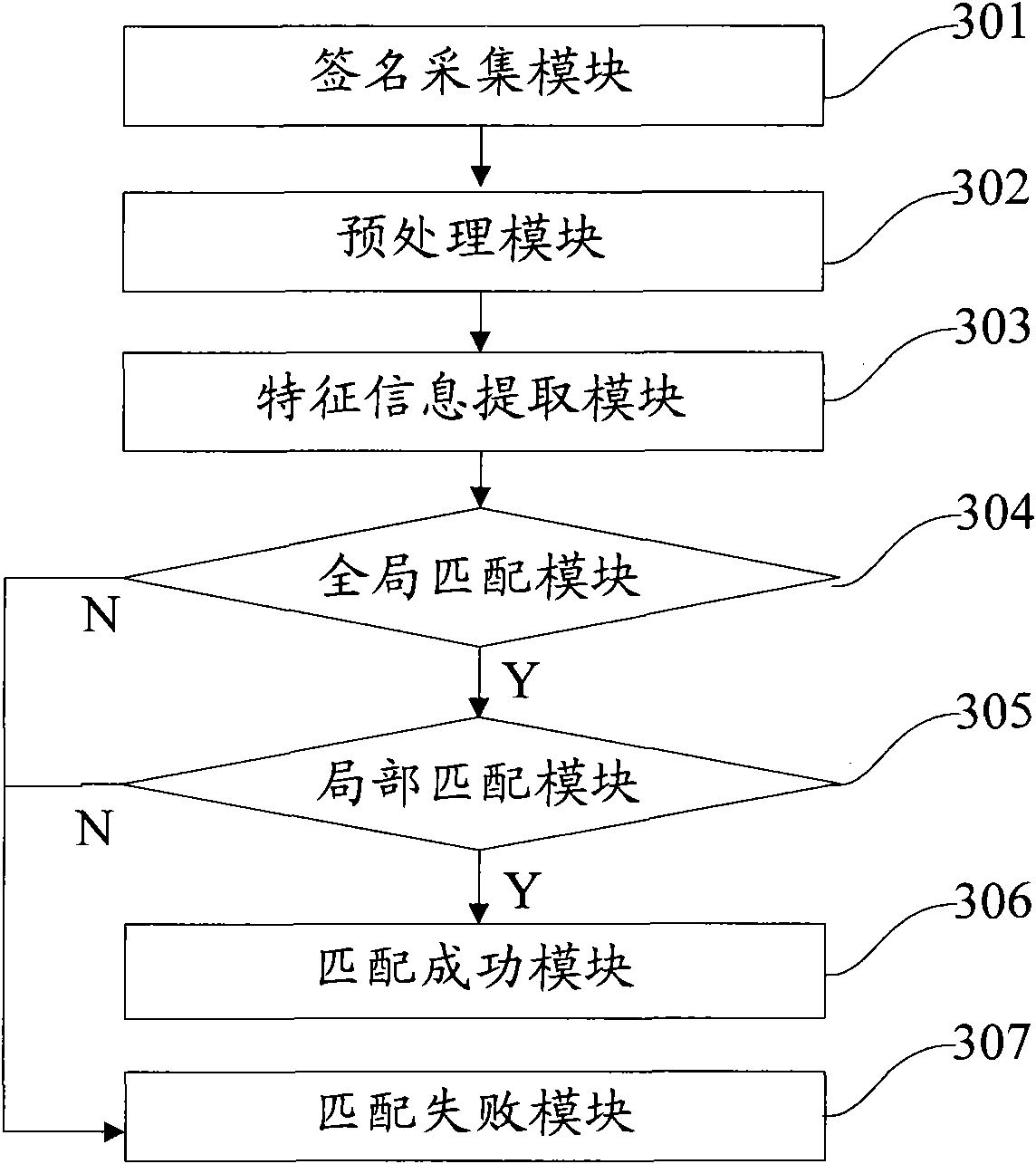
The invention discloses a method for recognizing a handwritten signature, which comprises the following steps: acquiring signature data and preprocessing the same; extracting global characteristic information and local characteristic information of the signature data; matching the global characteristic information with the global characteristic information of a preset signature sample and judging whether a first preset condition is satisfied; and if the first preset condition is satisfied, matching the local characteristic information with the local characteristic information of the preset signature sample; if the first preset condition is not satisfied, returning to the result of the failed matching directly; and if the matching result of the local characteristic information satisfies a second preset condition, returning to the result of the successful matching. The method can improve the efficiency and the accuracy of handwritten signature recognition so that a user can obtain a better using experience.
Owner:HANVON CORP
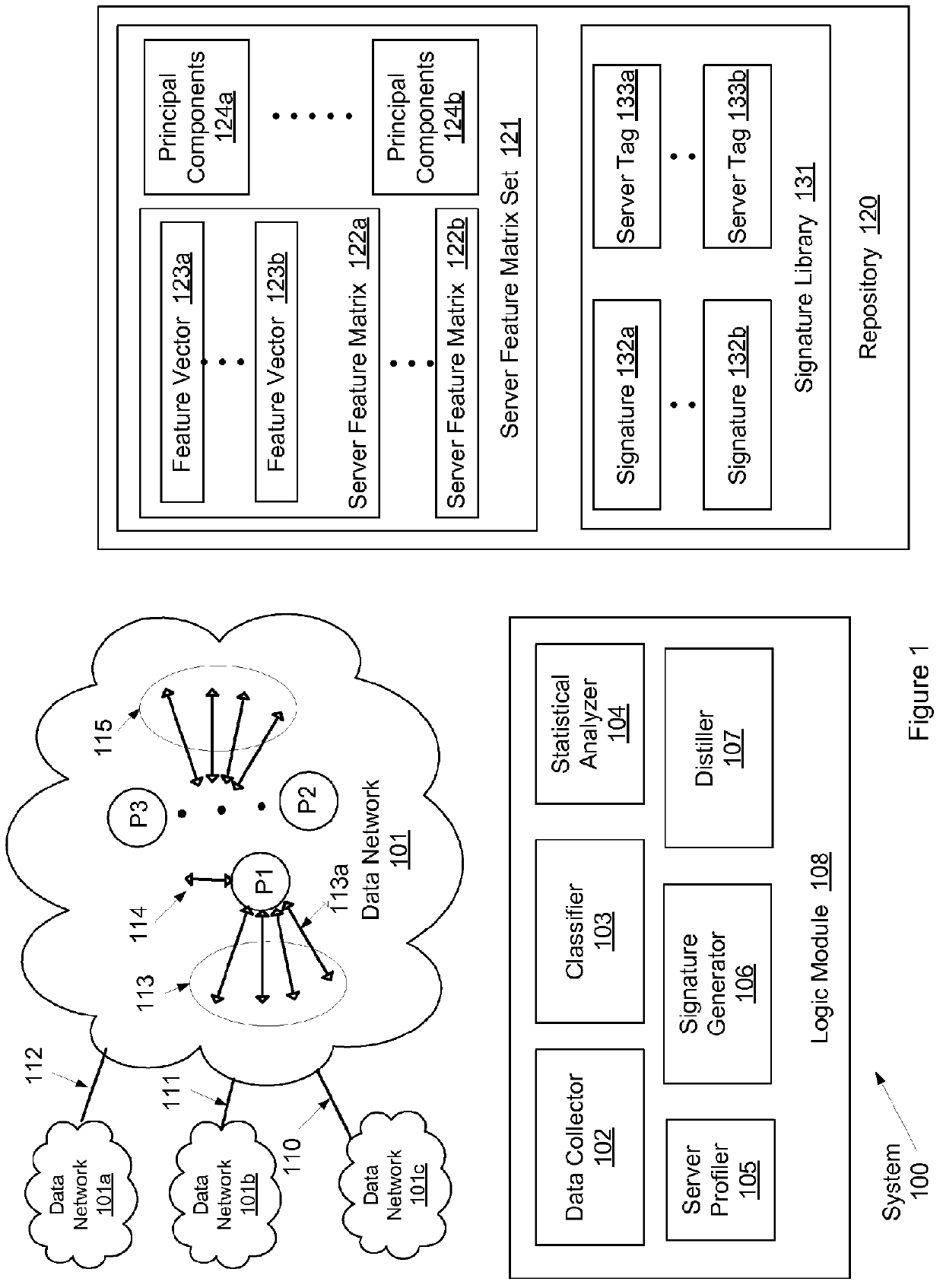
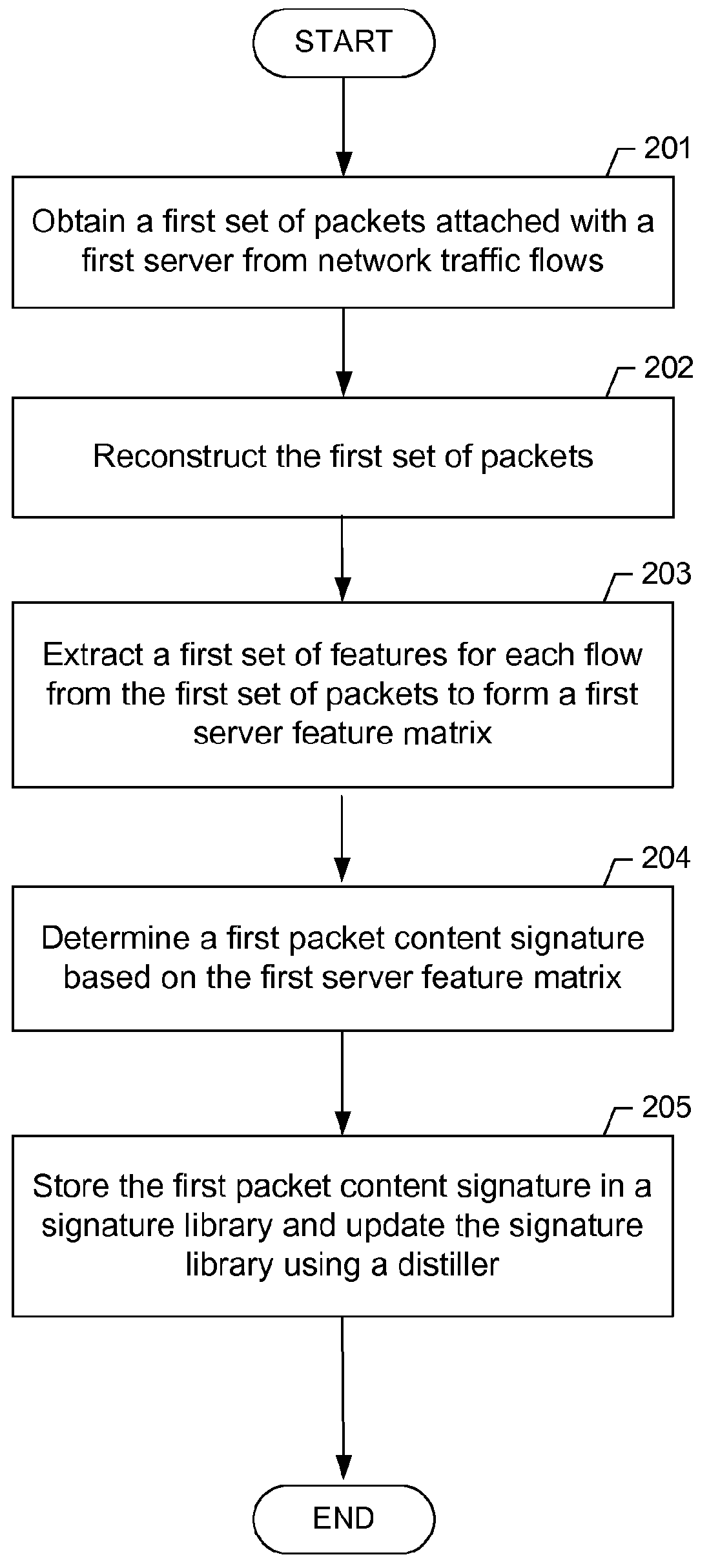
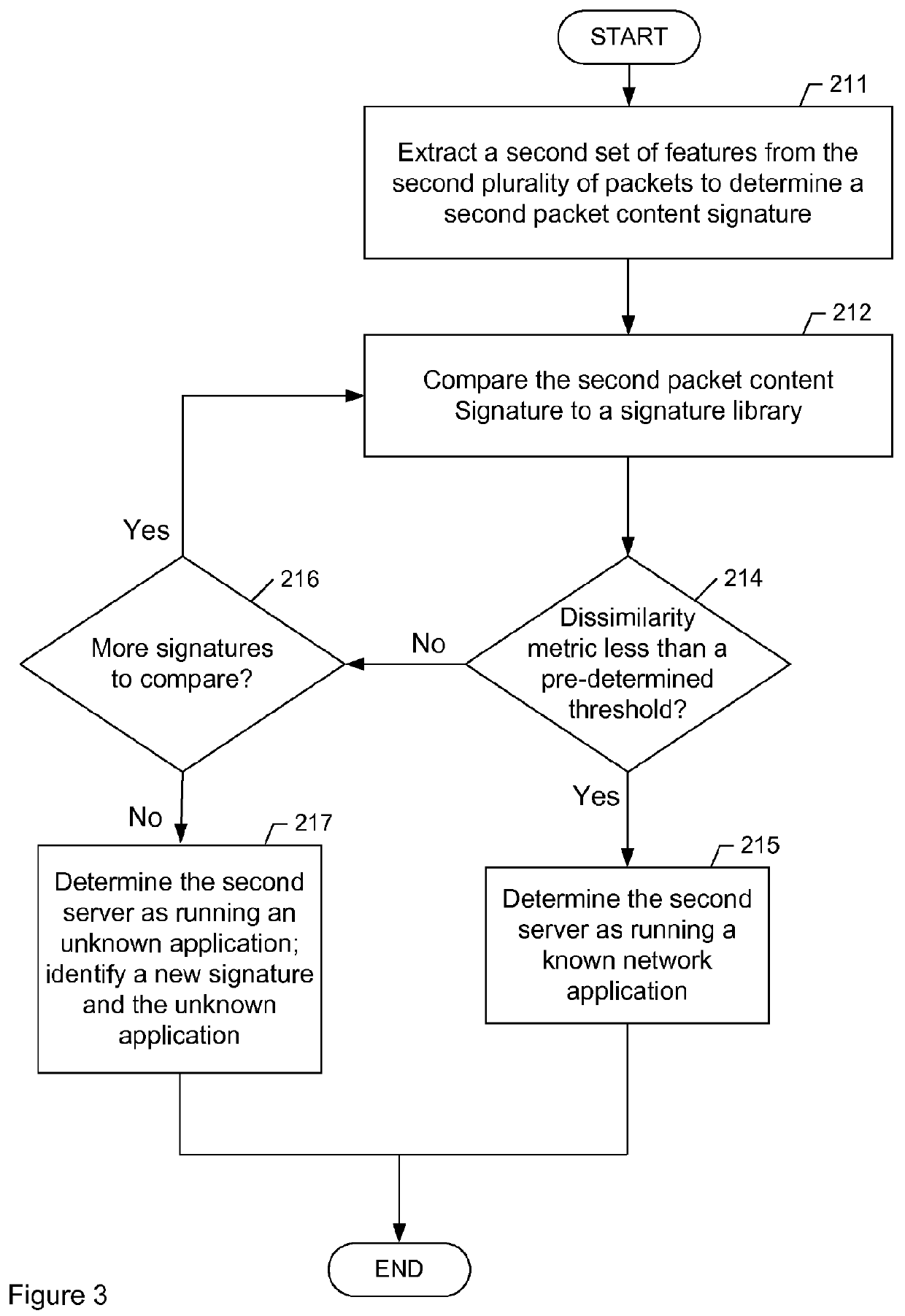
System and method for identifying network applications based on packet content signatures
ActiveUS8180916B1Bridging the gapWide applicabilityMultiple digital computer combinationsTransmissionData packBehavioral analytics
Embodiments of the invention provide a framework for traffic classification that bridges the gap between the packet content inspection and the flow-based behavioral analysis techniques. In particular, IP packets and / or IP flows are used as an input, network nodes are associated to specific network applications by leveraging information gathered from the web, and packet content signatures are extracted in an off-line fashion using clustering and signature extraction algorithms. The signatures learned are systematically exported to a traffic classifier that uses the newly available signatures to classify applications on-the-fly.
Owner:THE BOEING CO
Multifunctional input device for authentication and security applications
InactiveUS20120092127A1Small spacingElectric signal transmission systemsImage analysisHandwritingUser authentication
This disclosure provides systems, methods and apparatus for a combined sensor device. In some implementations, the combined sensor device may enable a single touchscreen to perform additional functions such as handwriting input and fingerprint recognition. In some implementations, these multiple features allow increased security through user authentication, and allow better capture of handwriting and a more interactive approach to user interfaces. A handheld mobile device such as a cell phone with the combined sensor device can enable an array of applications, such as using the mobile device as a gateway for user authentication to enable transactions and physical access; using the handwriting input function for signature recognition and transmittal for transaction applications; and / or using the handwriting input feature to automatically capture notes and other documents of students in an academic setting or employees in a corporate setting.
Owner:SNAPTRACK
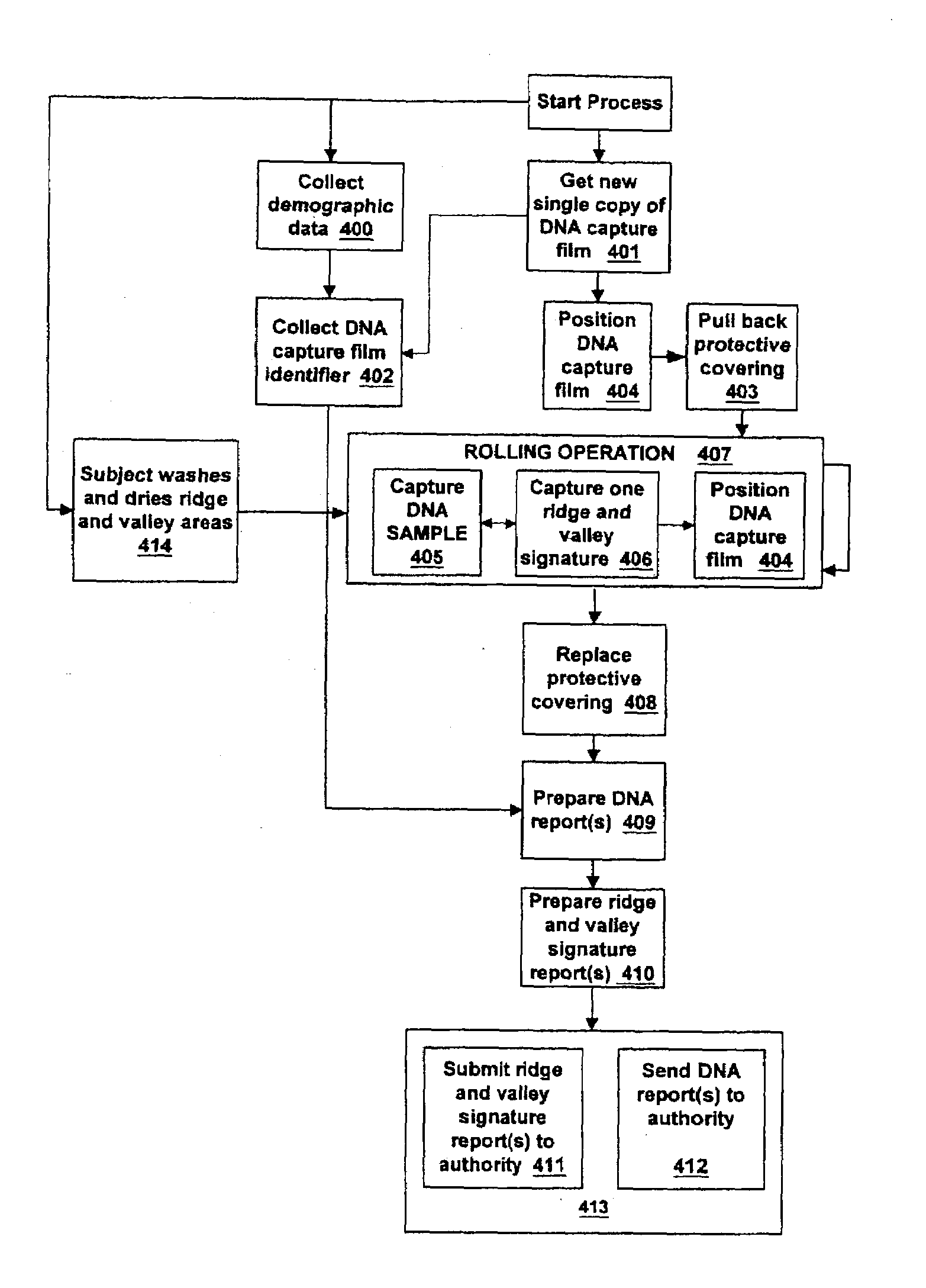
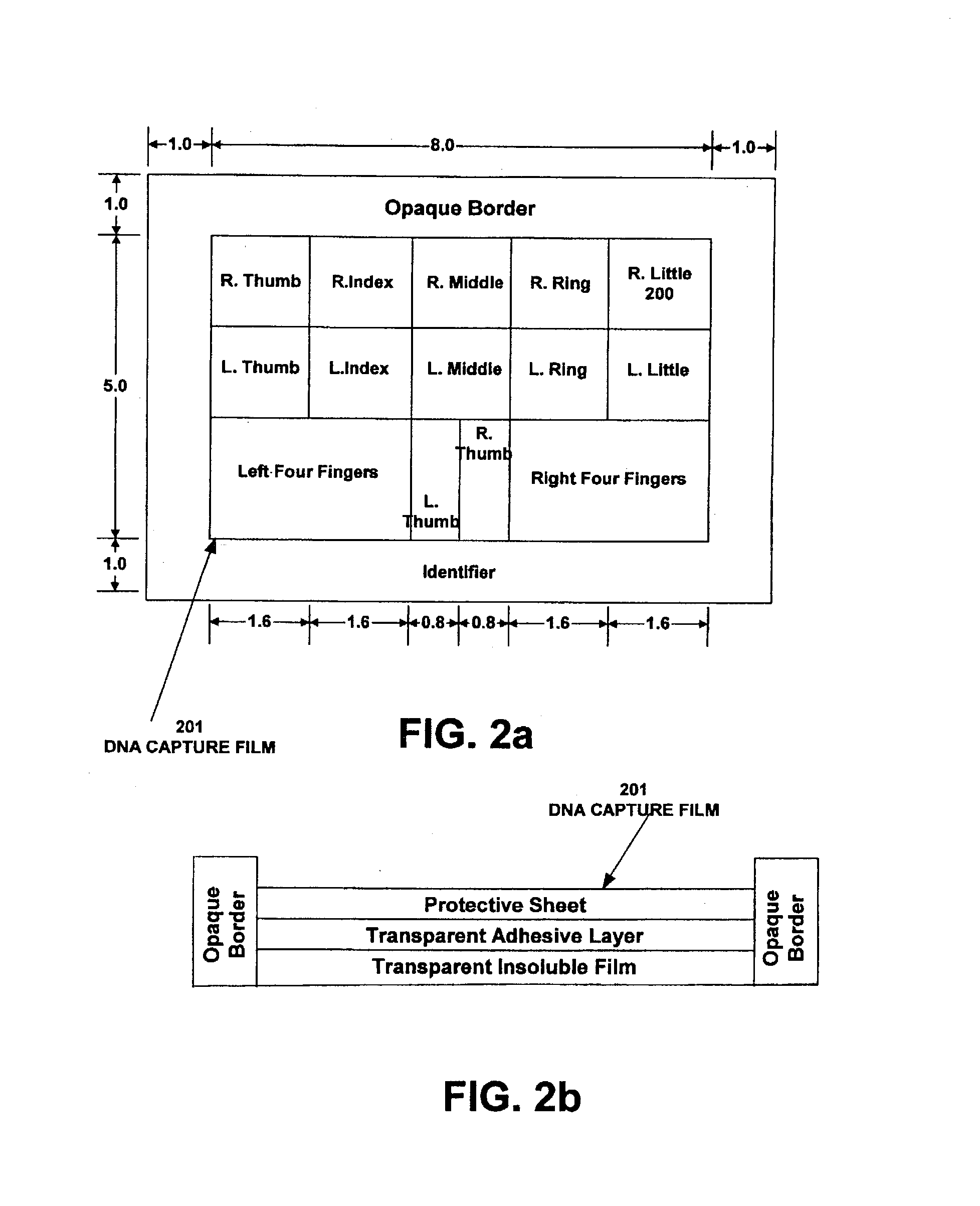
System and method for collecting DNA and fingerprints
ActiveUS7308123B2Efficient solutionIncrease valueWithdrawing sample devicesSurgical needlesBiologyDNA
A system and method is provided that simultaneously or consecutively collects DNA samples and ridge and valley signatures from the same subject during the same collection window that adds value to forensic data collection processes. The collection of the DNA samples and ridge and valley signatures occur during the same collection window to assured the DNA sample and ridge and valley signatures identify the same individual.
Owner:IDENTIFICATION INT
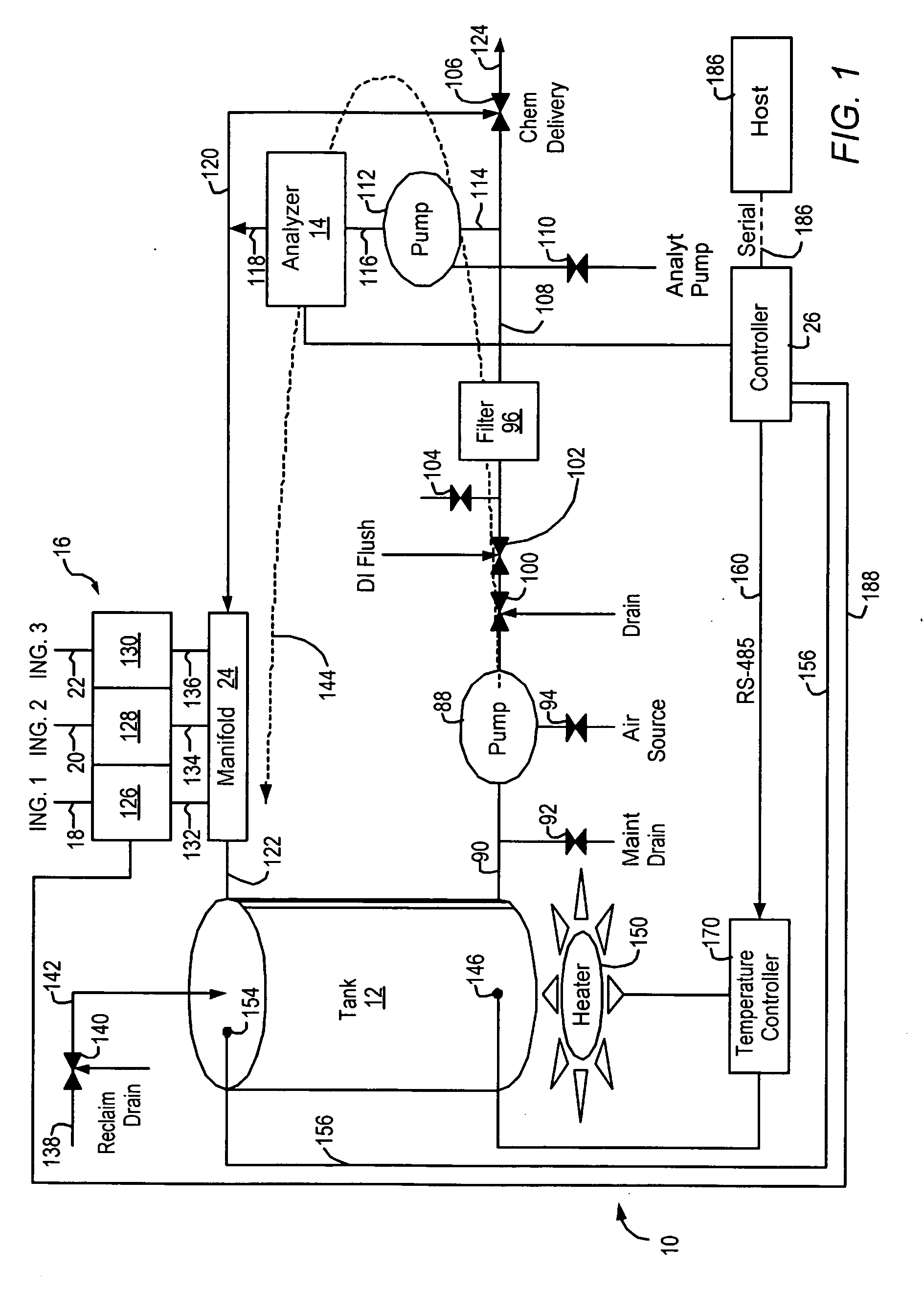
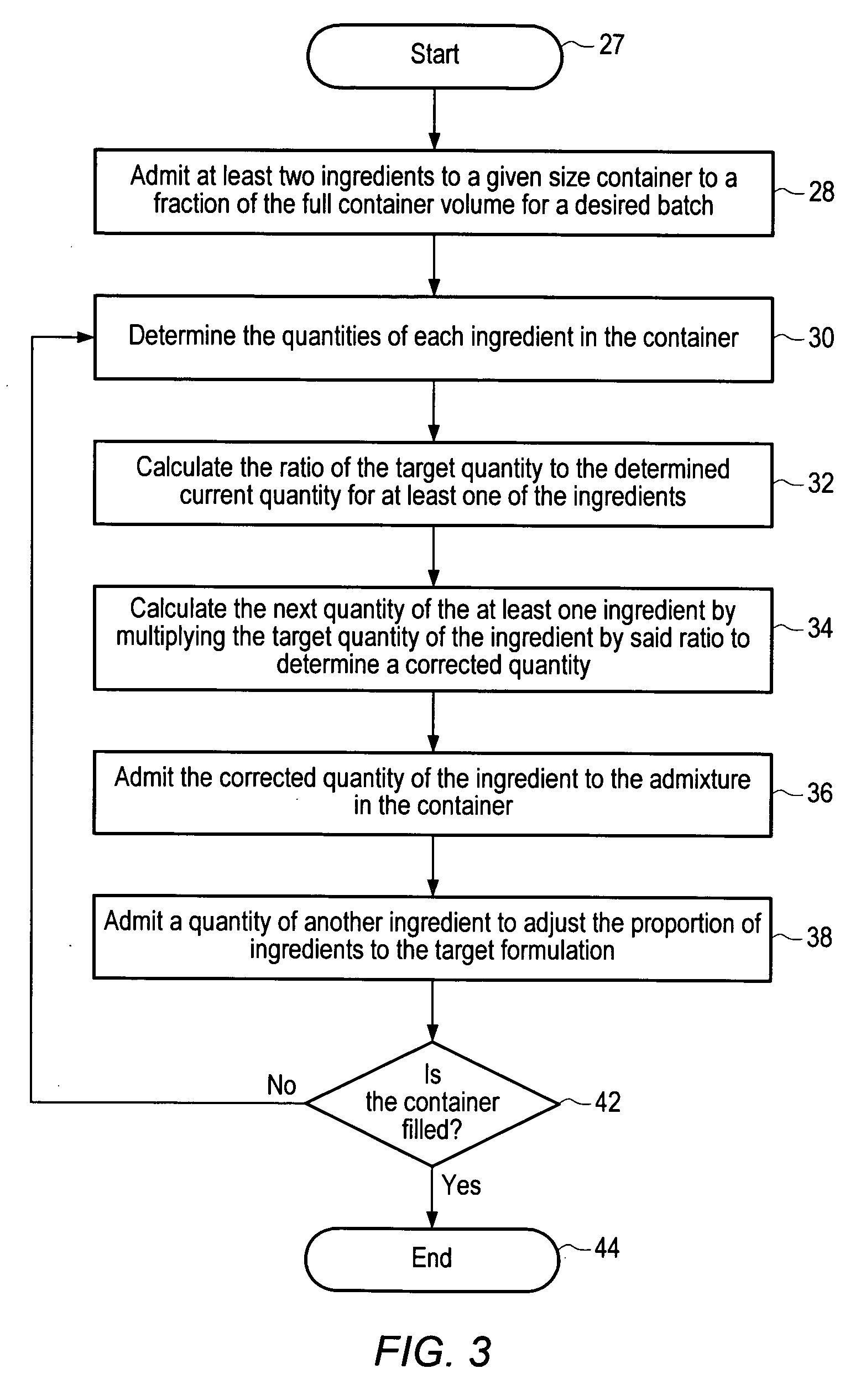
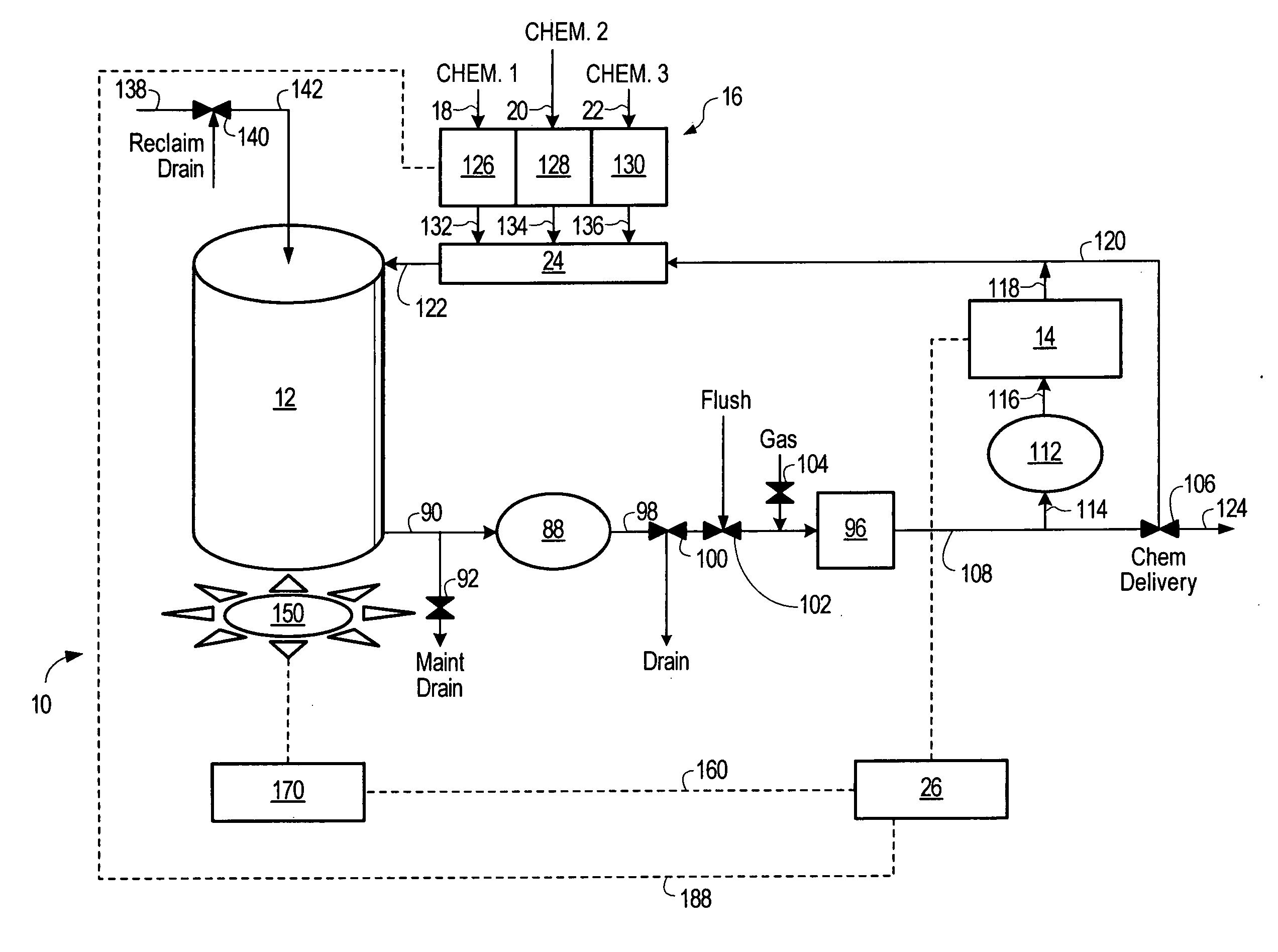
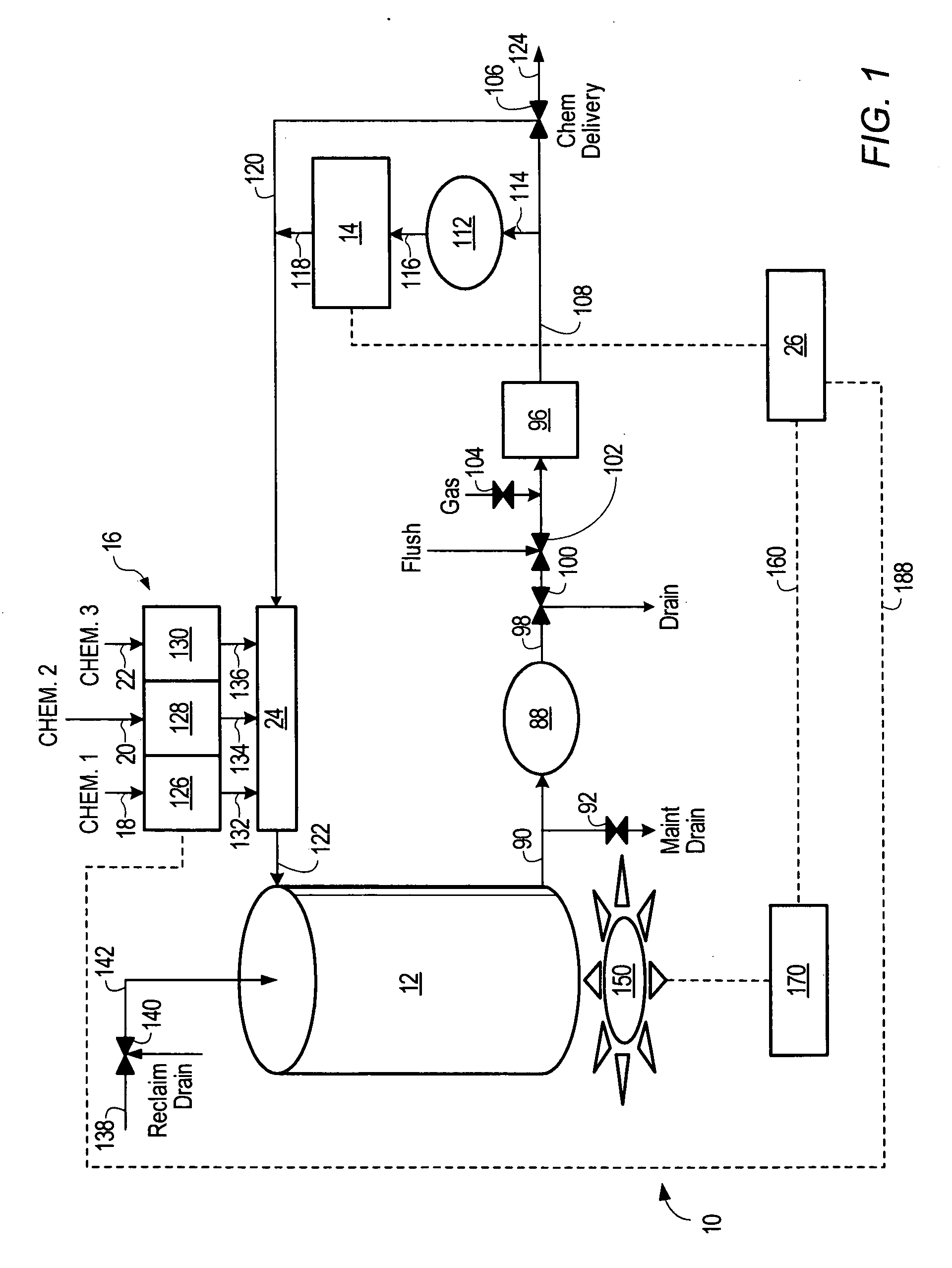
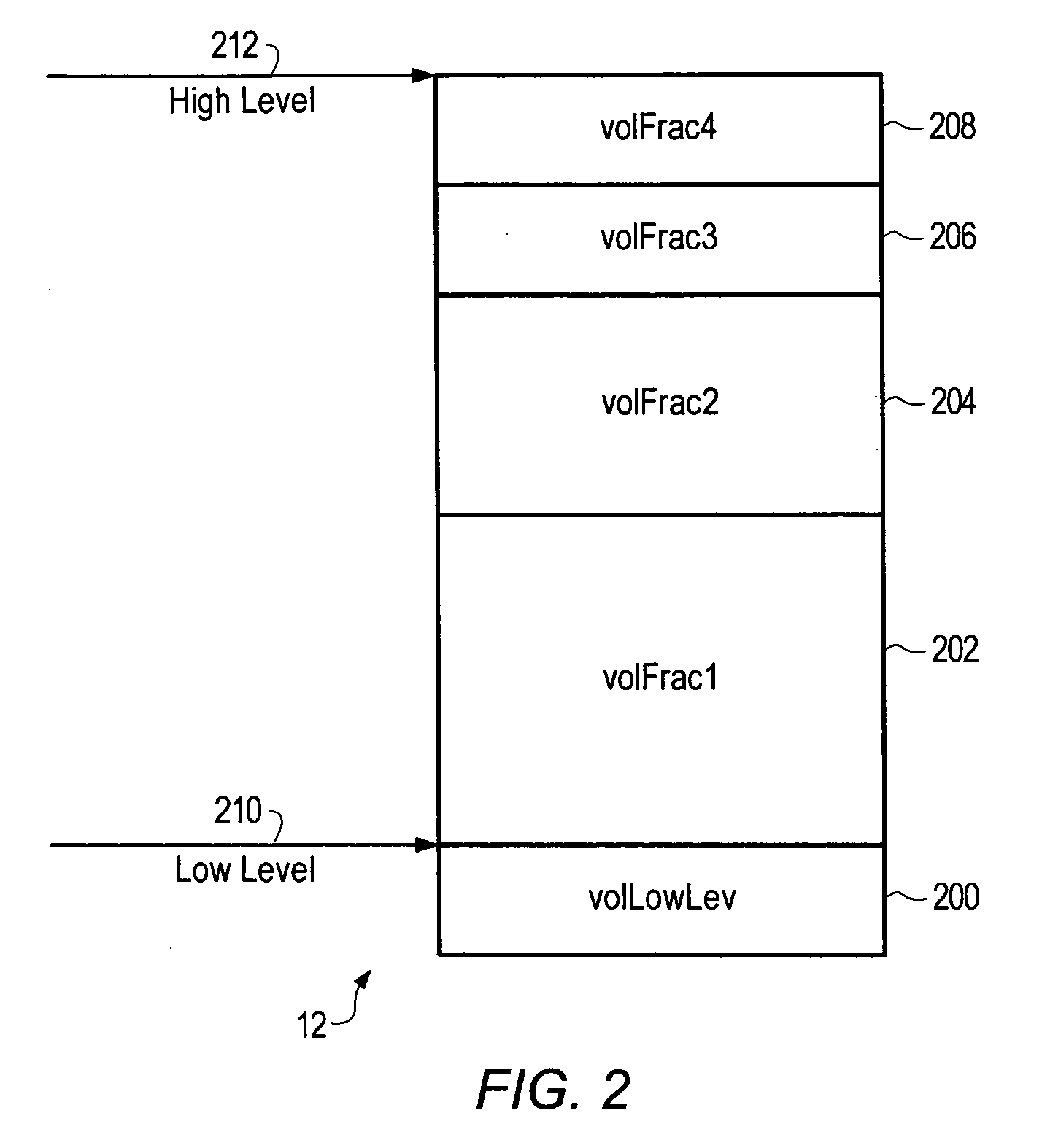
Chemical mixing apparatus, system and method
InactiveUS20060080041A1Transportation and packagingSemiconductor/solid-state device manufacturingOne passLoop control
There is disclosed a system and method of formulating a batch comprising at least two ingredients. An embodiment is disclosed wherein a feedforward algorithm can be used to control the target blend. Subsequently a feedback closed loop control loop algorithm is provided for a multivariant blend. Use of this approach allows for a continuously autoreplenished and controlled blend. Another enhancement disclosed is the ability to control via feedforward and feedback algorithms a fast responding control mode which allows for the elimination of a tank. This approach will allow for “one pass” blending with control. Feedback control can be provided via process indicators or through analytical or parametric methods. The controller implements an automated fault detection and correction system, thereby identifying necessary maintenance prior to failure. If failure does occur the signature recognition allows rapid analysis and correction thus maximizing tool availability.
Owner:TRES ARK
Automated sourcing of substrate microfabrication defects using defects signatures
InactiveUS7229845B1Data processing applicationsSemiconductor/solid-state device testing/measurementWaferingAlgorithm
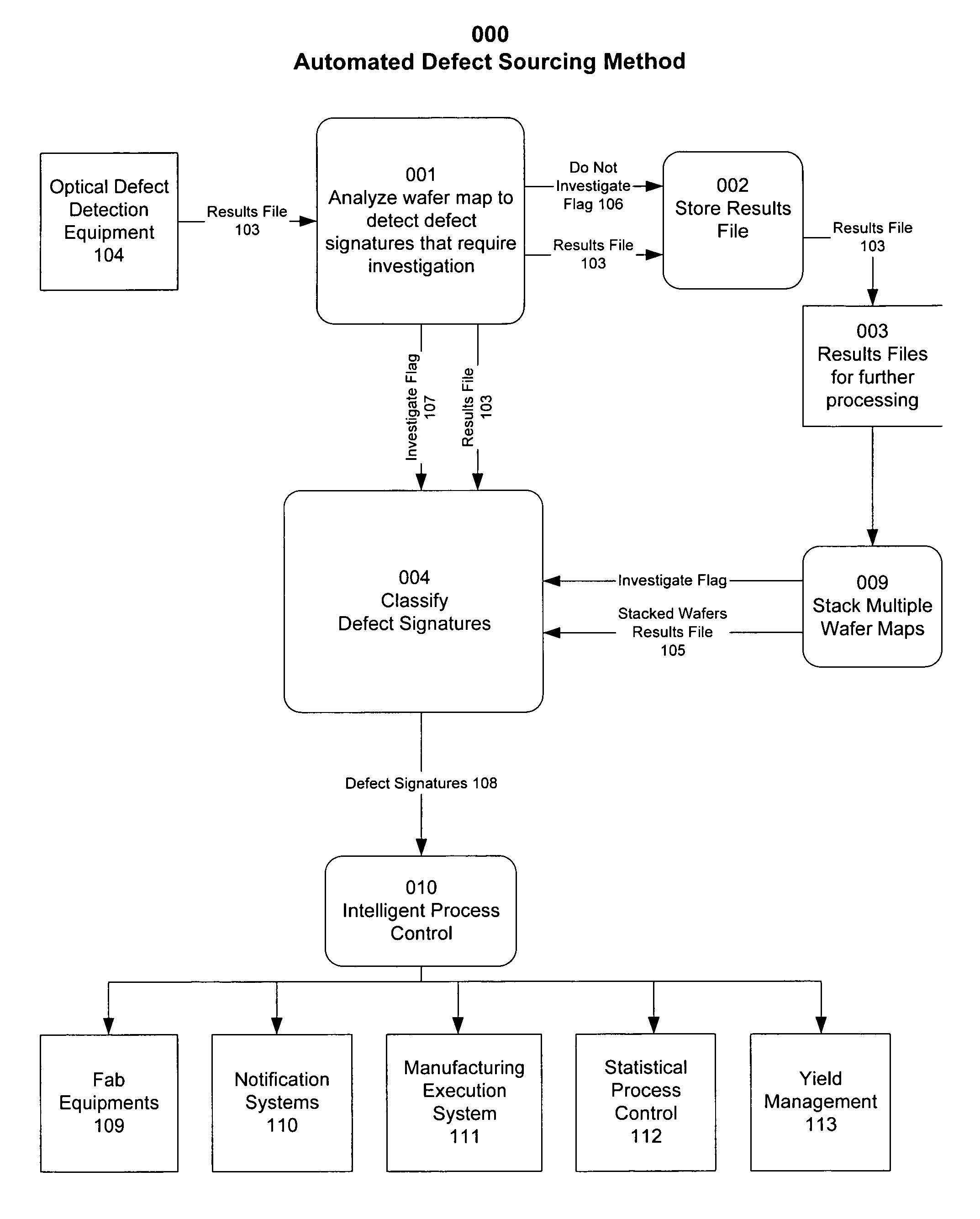
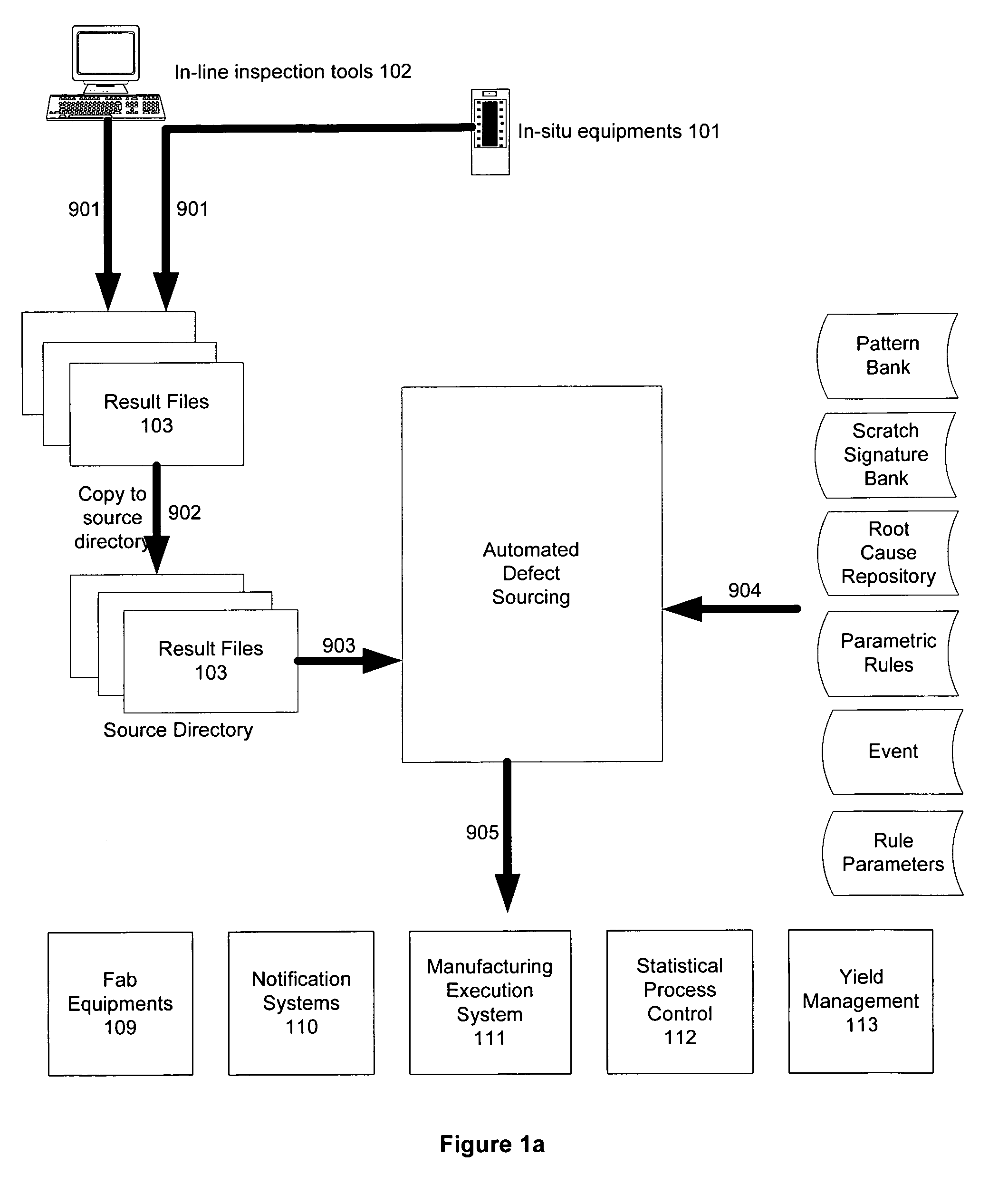
Automated defect sourcing system identifies root-causes of yield excursion due to contamination, process faults, equipment failure and / or handling in timely manner and provides accurate timely feedback to address and contain the sources of yield excursion. A signature bank stores known wafer surface manufacturing defects as defect signatures. The signature of a manufacturing defect pattern is associated with a type of equipment or process, and used to source the manufacturing defects and to provide process control for changing and / or stopping yield excursion during fabrication. A defect signature recognition engine matches wafer defects against the signature bank during wafer fabrication. Once the defect signature is detected during fabrication, handling and / or disposing the root-cause of the corresponding defect is facilitated using messages according to an event handling database. Optionally, a real-time process control for wafer fabrication is provided.
Owner:SIGLAZ +1
A method and apparatus for increasing synchronous detection precision
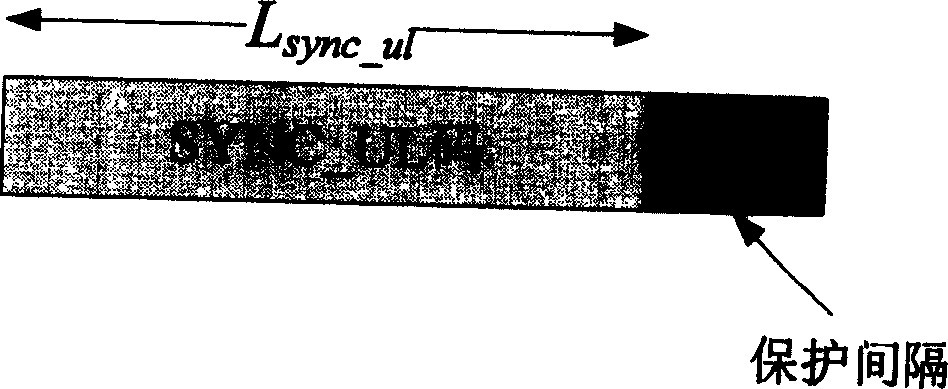
ActiveCN1595835AHigh precisionImprove performanceCode division multiplexRadio transmission for post communicationData segmentCode division multiple access
The invention is a method and device for improving synchronous detecting precision, used in synchronous detection based on ascending time gap in CDMA system, and its method includes the steps: antenna data segment obtaining to determine the data segment where the synchronous code exists; matching filtration: for detecting if there is ascending synchronous access at protective intervals and ascending guide frequency time gap intervals, firstly making shift relation between NSYNC_UL ascending synchronous codes and with antenna received data at protective intervals and ascending guide frequency time gas intervals and obtaining related power sequence; signature identification: detecting and judging the total related frequency sequence and only in the situation of meeting preset detecting conditions can it determine there is ascending synchronous access; fast physical access channel arrangement: making priority processing according to many ascending synchronous signatures in each subframe. It gives a multiple sampling-based method and device fro improving synchronous detecting precision, improving the synchronous detecting precision.
Owner:DATANG MOBILE COMM EQUIP CO LTD
Hiding method and system for signature of credible two-dimensional code
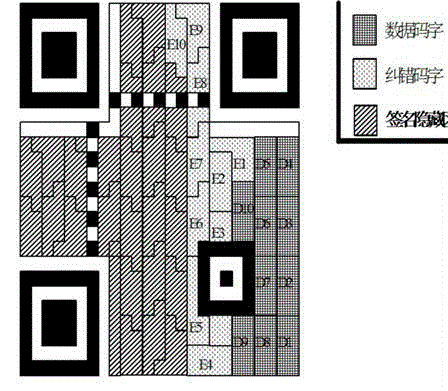
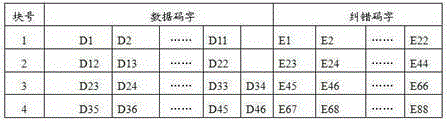
ActiveCN103605950AGuaranteed availabilityRecord carriers used with machinesSensing by electromagnetic radiationAlgorithmStream data
The invention provides a hiding method and system for a signature of a credible two-dimensional code. The hiding method comprises the signature hiding step that a message m passes through hash to obtain an h(m), Ks and Kp are a secrete key and a public key respectively, the Ks is used for encrypting the h(m) to obtain a signature D, the m and the D are encoded to obtain data bit streams Data m of the m and data bit streams Data D of the D, each data bit stream is composed of a data codeword and an error correction codeword, the Data m are arranged in areas of data codewords and error correction codewords, and the Data D are arranged in a signature hiding area; and the signature recognition step that an m0 is obtained when a stop character is scanned, the D is obtained by scanning data after the stop character, the Kp is used for decrypting the D to obtain the h(m), the hash is carried out on the m0 to obtain an h(m0), the h(m) is compared with the h(m0) to verify the credibility. The hiding method and system for the signature of the credible two-dimensional code have the advantages that the issued message is not interfered by credible measures, the usability of the credible two-dimensional code is ensured, and no special requirement for equipment exists.
Owner:SHENZHEN FULLY HOMOMORPHIC ENCRYPTION SCI & TECH CO LTD
Point-of-use mixing method with standard deviation homogeneity monitoring
InactiveUS20070043473A1Sampled-variable control systemsControlling ratio of multiple fluid flowsHybrid approachLoop control
Owner:TRES ARK
Fast application notification in a clustered computing system
ActiveUS7747717B2Resource allocationMultiple digital computer combinationsComputer networkService experience
With fast notification of changes to a clustered computing system, through which a number of events are published for system state changes, applications can quickly recover and sessions can quickly be rebalanced. When a resource associated with a service experiences a change in status, such as a termination or a start / restart, a notification event is immediately published. Notification events contain information to enable subscribers to identify, based on matching a session signature, the particular sessions that are affected by the change in status, and to respond accordingly. This allows sessions to be quickly aborted and ongoing processing to be quickly terminated when a resource fails, and allows fast rebalancing of work when a resource is restarted.
Owner:ORACLE INT CORP
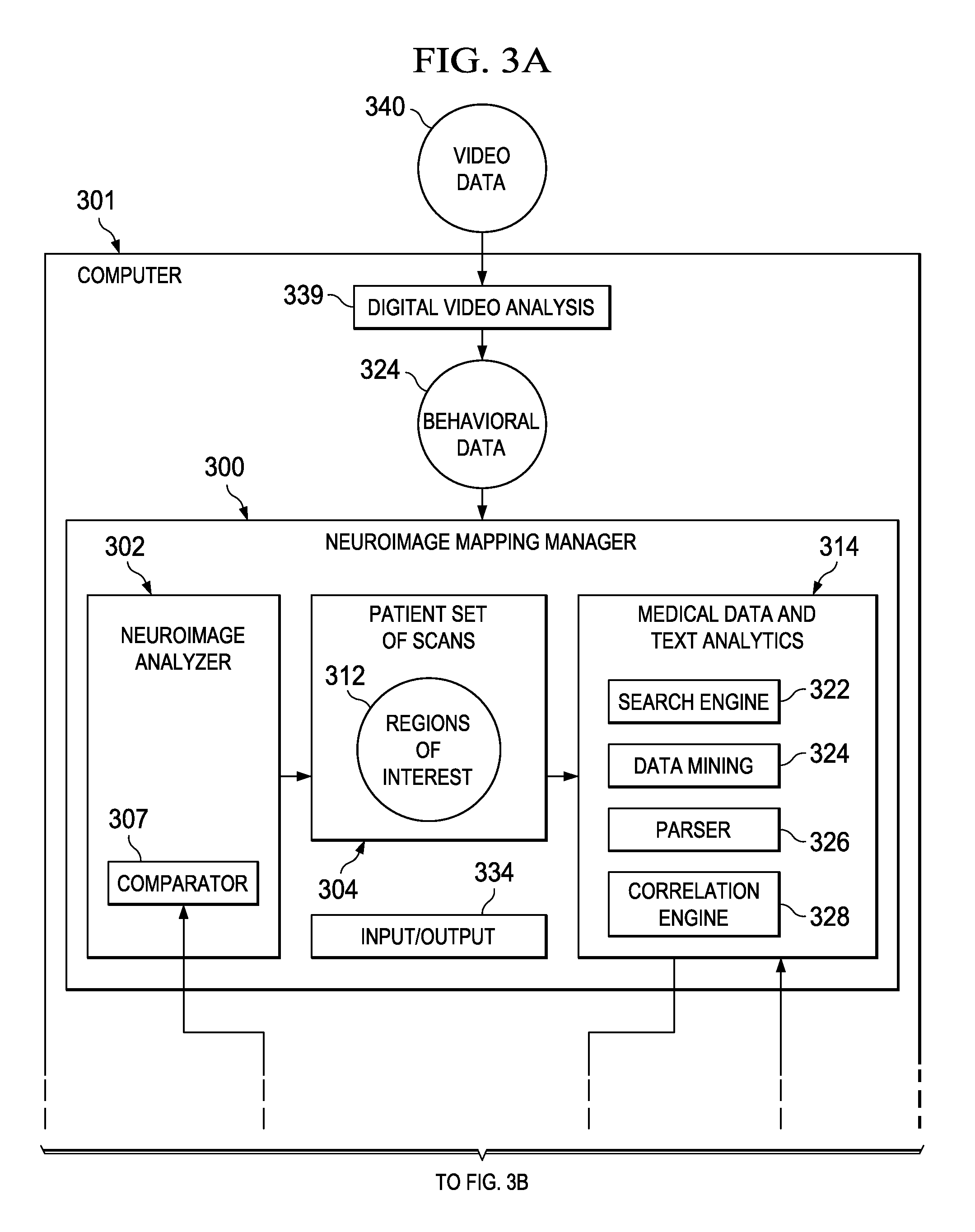
Differential diagnosis of neuropsychiatric conditions
A computer implemented method, apparatus, and computer program product for generating neuropsychiatric diagnoses. Quantitative information describing diagnostic characteristics associated with a patient is generated based on an analysis of a set of patient scans. The quantitative information comprises a set of indictors associated with regions of interest in the set of scans for the patient. The set of indicators of potential neuropsychiatric conditions is compared with a set of diagnostic signatures. A diagnostic signature comprises a set of indicators of a known neuropsychiatric condition. Matching signatures are identified. A matching signature is a diagnostic signature that corresponds to at least one indicator in the set of indicators to form a set of signatures. A diagnosis associated with each signature in the set of signatures is identified to form a set of potential diagnoses. The set of potential diagnoses is presented with links to relevant portion of the medical literature.
Owner:IBM CORP
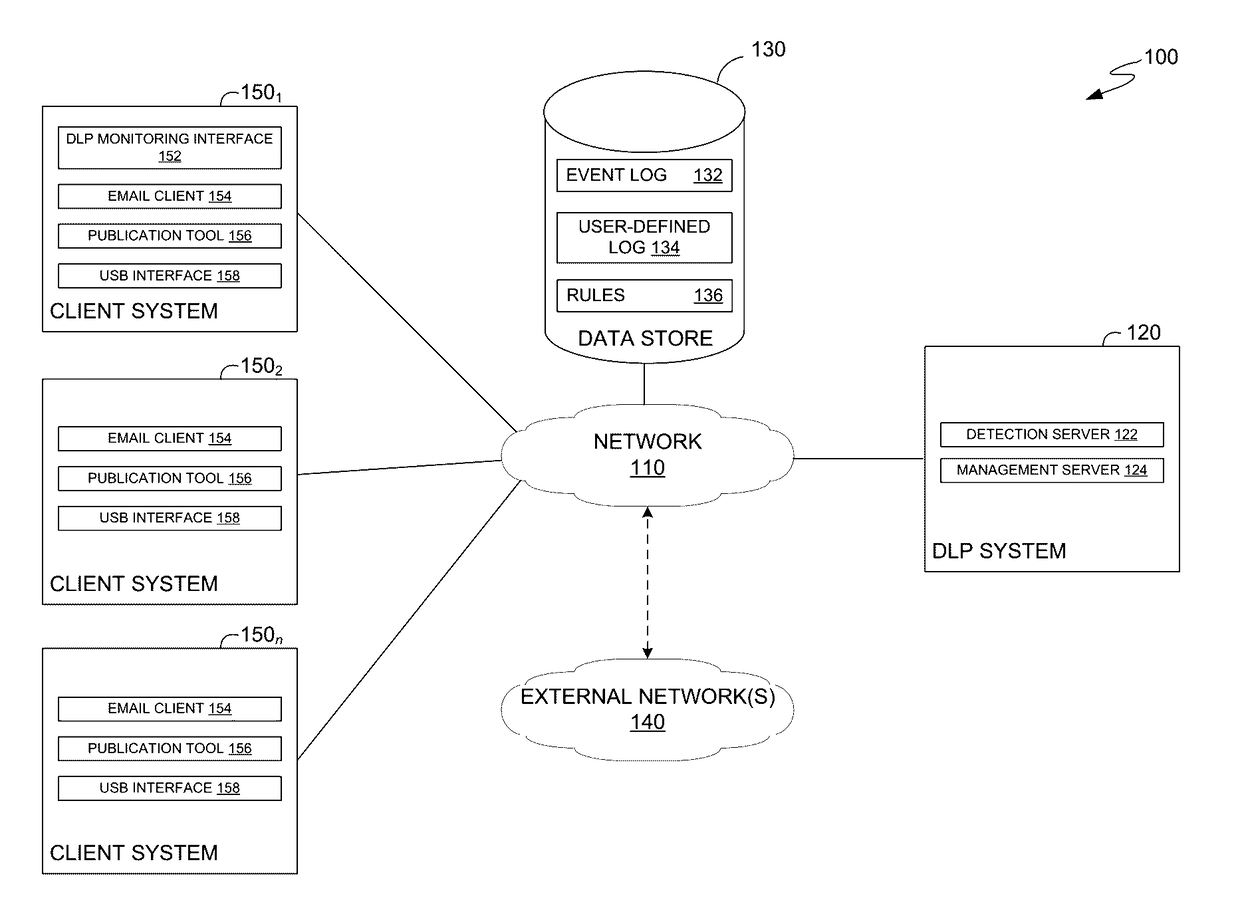
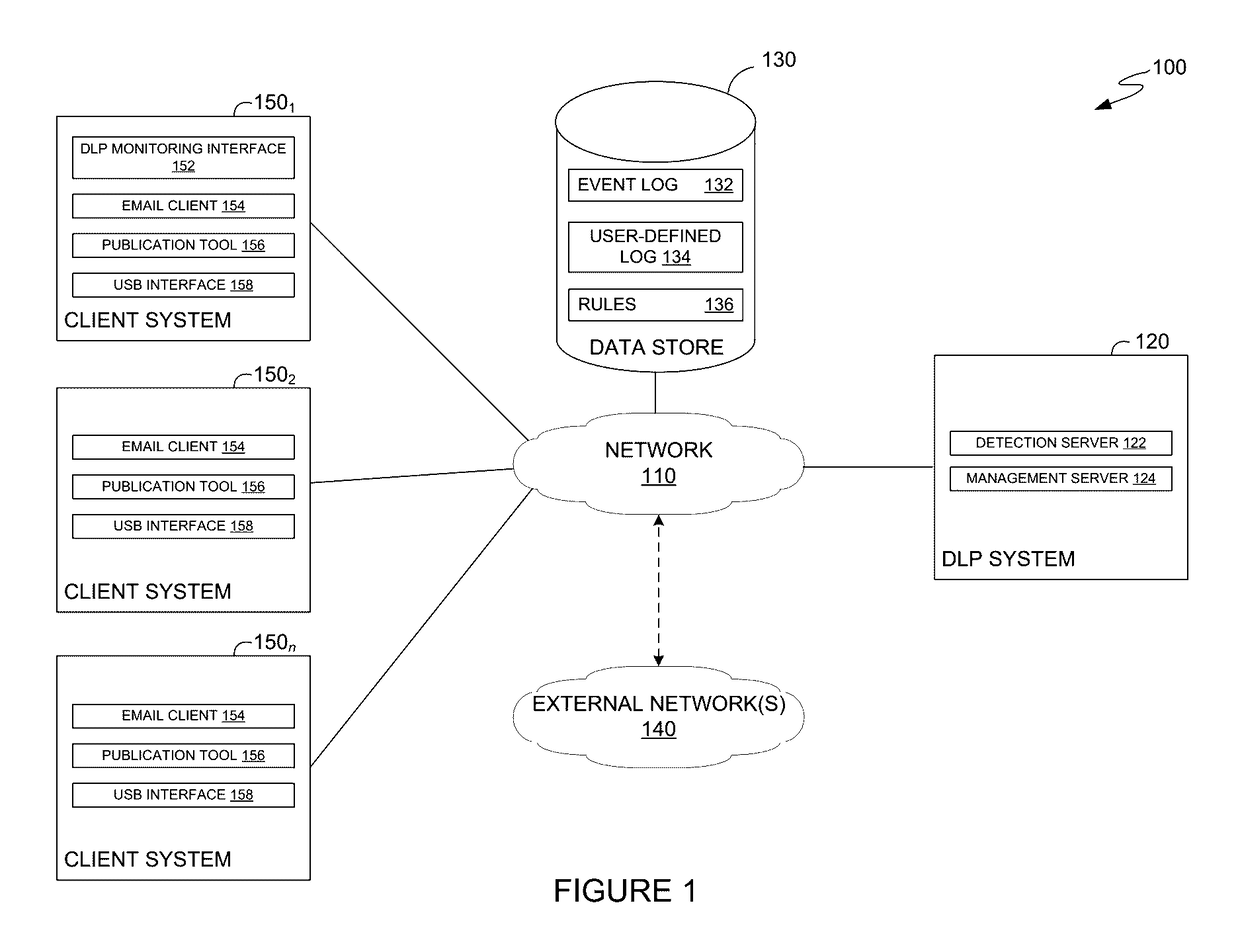
Match signature recognition for detecting false positive incidents and improving post-incident remediation
The present disclosure relates to using signatures in a data loss prevention system. According to one embodiment, a DLP system identifies an occurrence of a data loss prevention (DLP) incident triggered by content and a DLP rule. The DLP system generates a first signature representing the DLP incident based on a specific pattern inherent to the content which triggered the DLP incident. The DLP system compares the first signature to one or more second signatures generated from other DLP incidents associated with the DLP rule. Upon determining the first signature matches at least one of the second signatures, the DLP system assigns an event status of the second matching signature to the first signature.
Owner:CA TECH INC
Recognition method and recognition device based on biological characteristics
InactiveCN103218624AImprove recognition rateImprove signature recognition rateCharacter and pattern recognitionHandwritingDecomposition
The invention relates to a recognition method and a recognition device based on biological characteristics. According to the recognition method, wavelet packet multilayer decomposition characteristic parameters are used for generating new frequency characteristic quantities; due to the fact that wavelet coefficients have a large difference, energy of signals at all decomposition nodes not only can reflect energy distribution of the signals in all frequency bands, but also has translation invariance, as a result, the frequency characteristic quantities can highly reflect user characteristics and improve the recognition rate of user signatures; and further, fingerprint characteristics and handwritten signature characteristics are combined, fingerprint information is collected while a user gives a signature, and therefore a high recognition rate of fingerprints is used for making up for a low high recognition rate of handwritten signatures. Accordingly, a handwriting pen provided with a fingerprint collection module at the pen holding end in an inlaid mode is used, and therefore the fingerprint information of the user can be collected while the user gives the signature, namely two types of information can be collected at the time of one action. A biometric feature recognition system which combines the fingerprints and the handwritten signatures and is studied out according to the thinking is high in recognition rate and acceptability.
Owner:EAST CHINA UNIV OF SCI & TECH
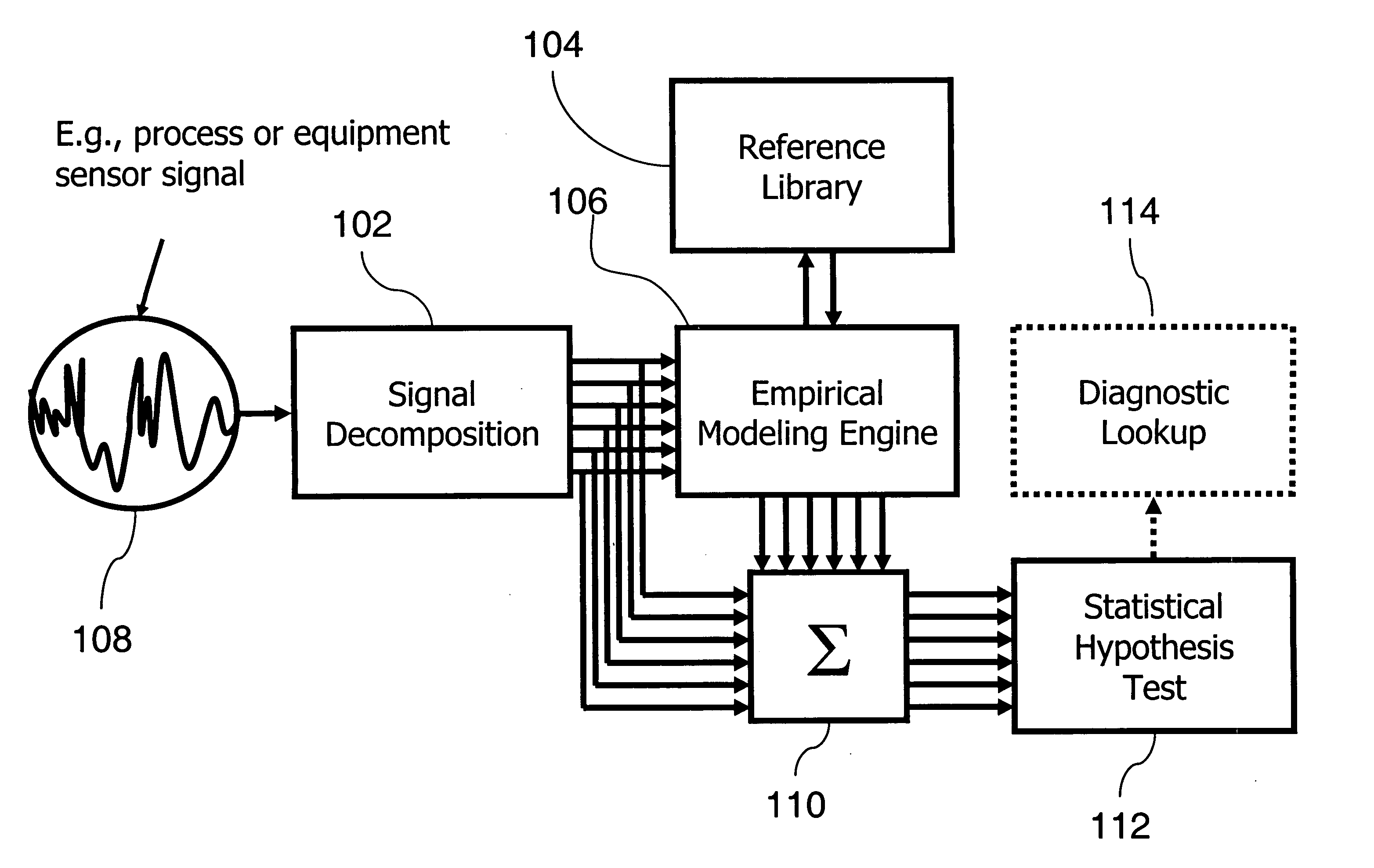
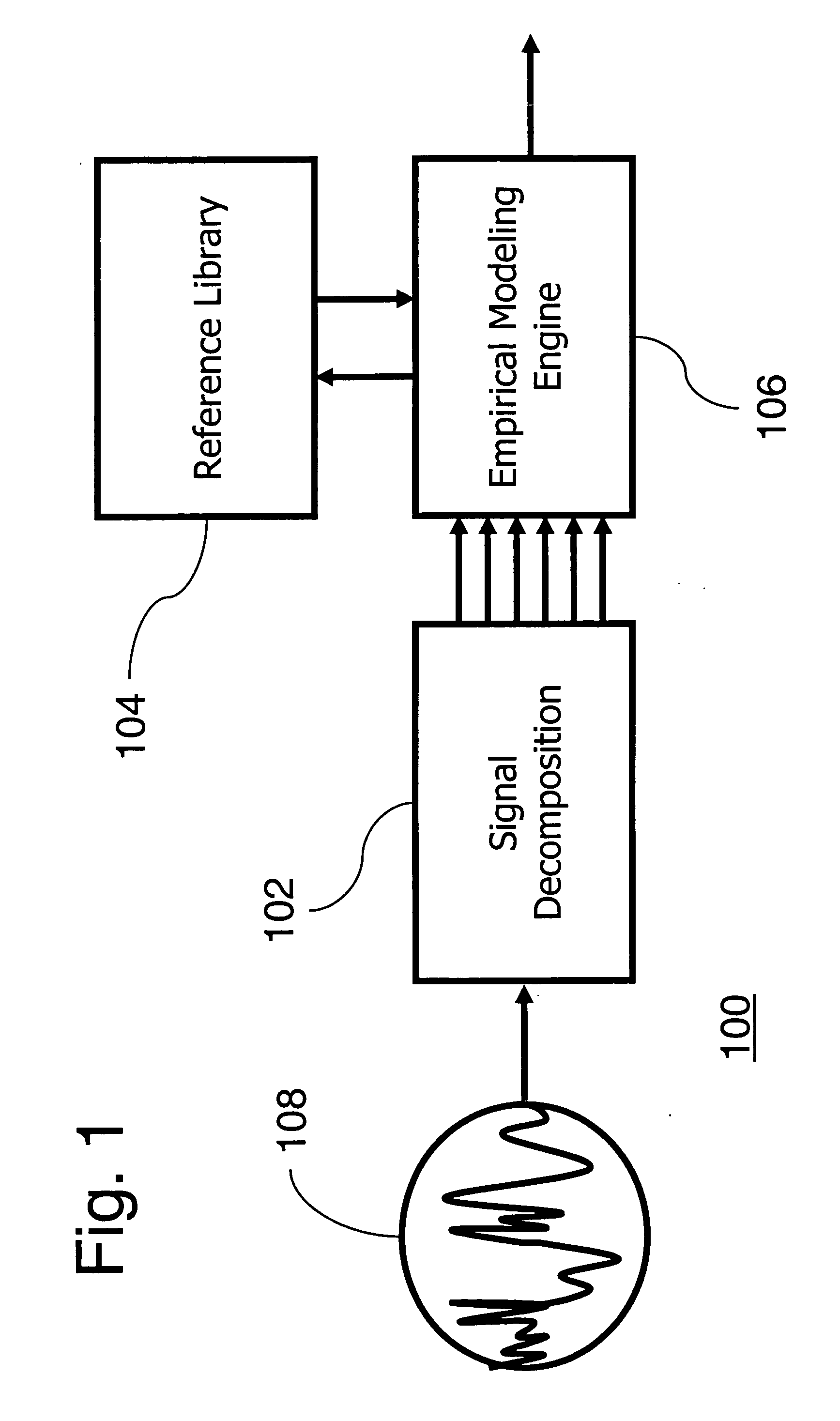
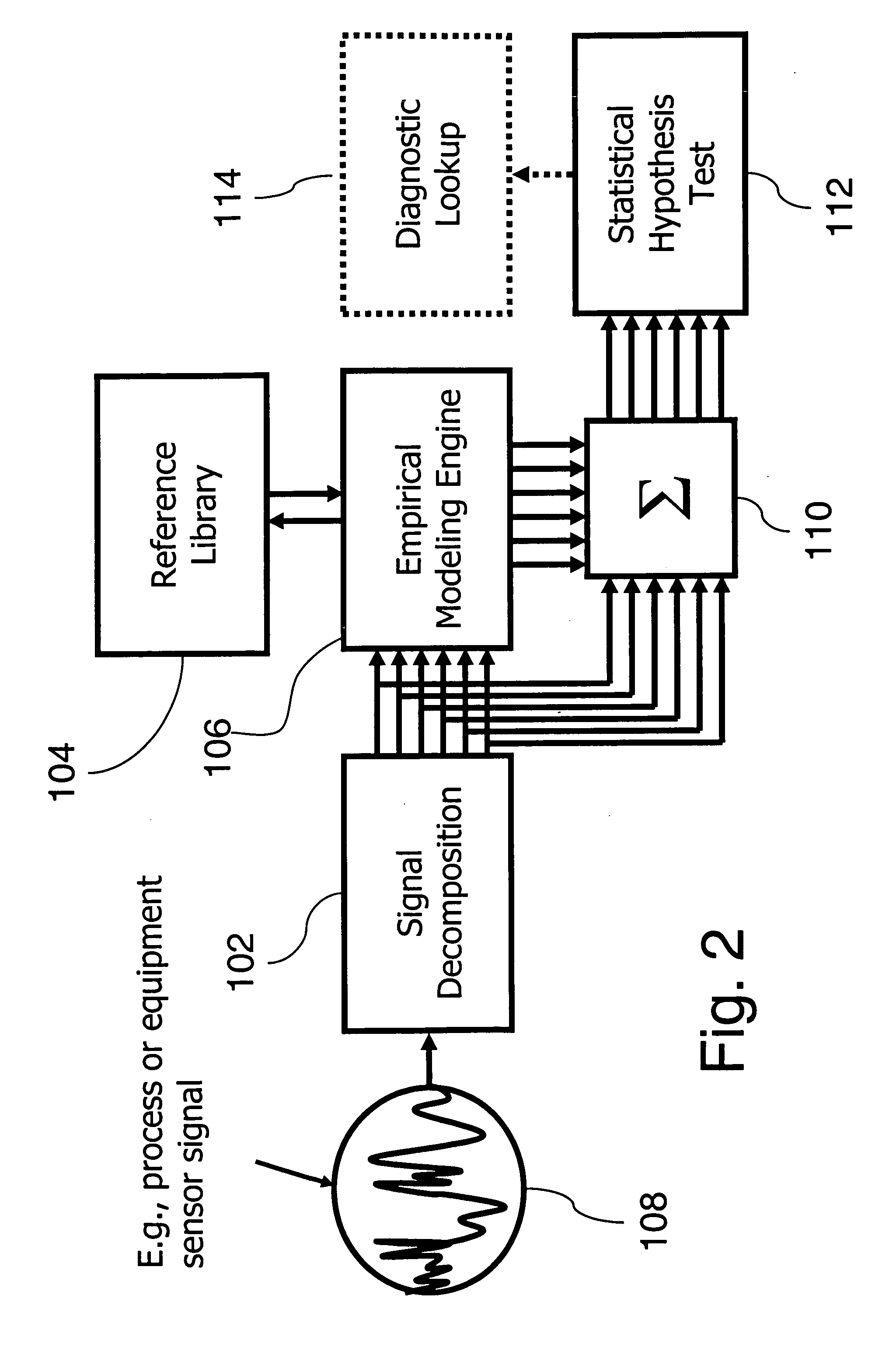
Complex signal decomposition and modeling
InactiveUS20060025970A1Improve accuracyOptimization rangeAmplifier modifications to reduce noise influenceElectric testing/monitoringEmpirical modellingHypothesis
A system, method and program product for monitoring a complex signal for ultrasensitive detection of state changes, or for signature recognition and classification is provided. A complex signal is decomposed periodically for empirical modeling. Wavelet analysis, frequency band filtering or other methods may be used to decompose the complex signal into components. A library of signature data may be referenced for selection of a recognized signature in the decomposed complex signal. The recognized signature may indicate data being carried in the complex signal. Estimated signal data may be generated for determination of an operational state of a monitored process or machine using a statistical hypothesis test with reference to the decomposed input signal.
Owner:SMARTSIGNAL CORP
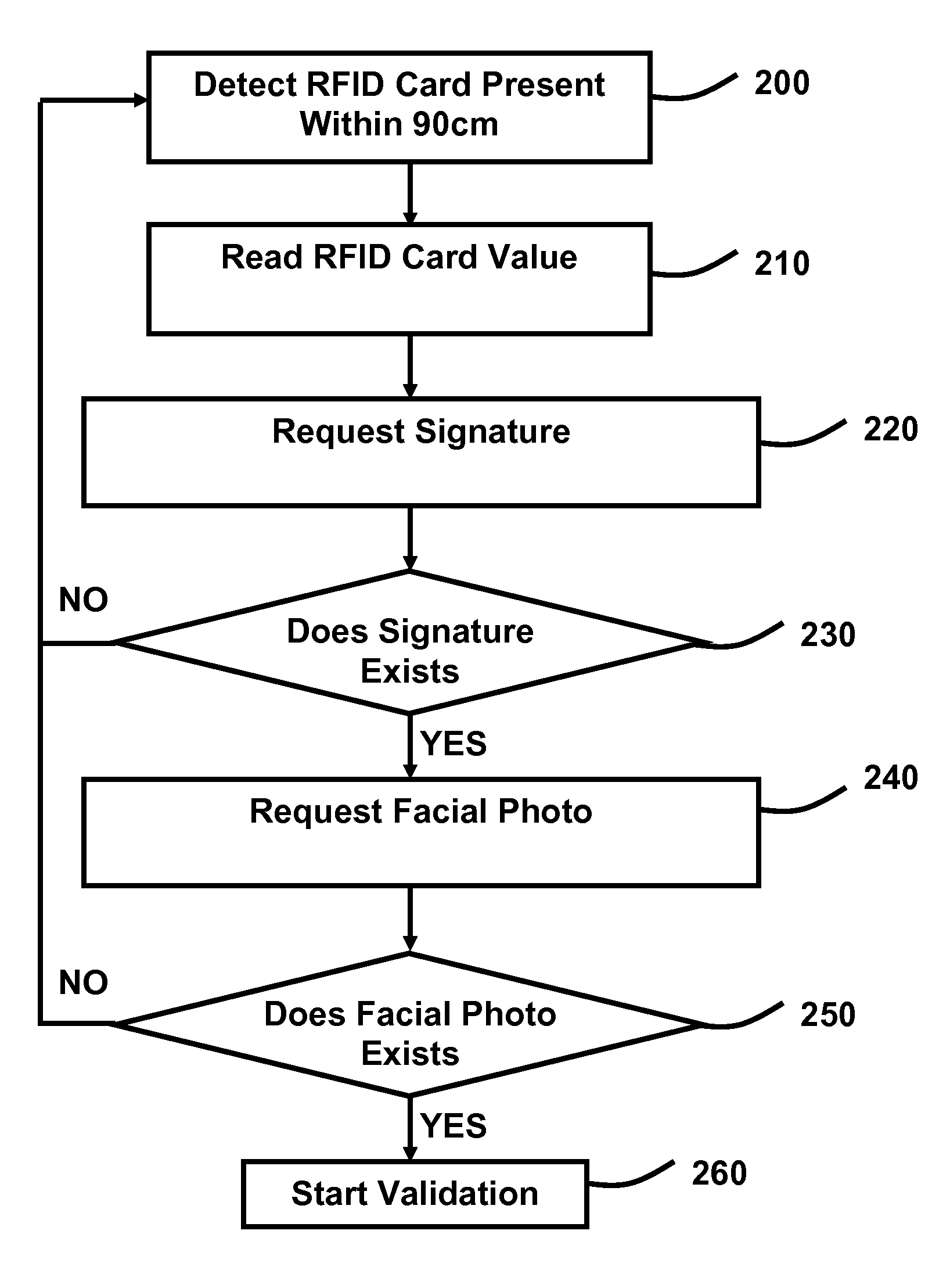
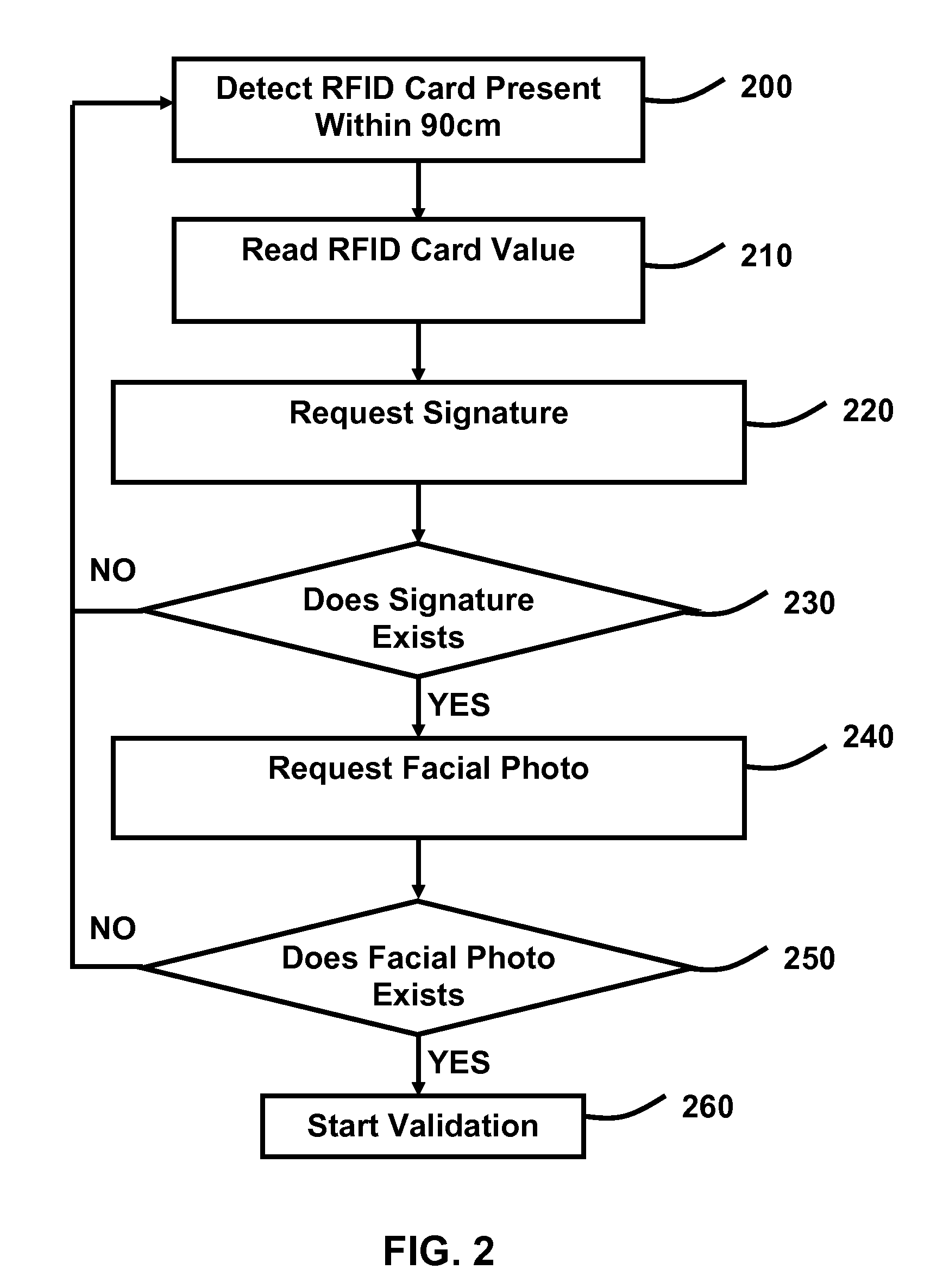
Method for authenticating a person's identity by using a RFID card, biometric signature recognition and facial recognition.
InactiveUS20110248851A1Individual entry/exit registersBurglar alarm by hand-portable articles removalThird partyFacial identity
A method is provided for validating an individual's identity by using a combination of a RFID card, signature captured by a touch screen computer, and a facial photo captured by a built-in camera of a touch screen computer. Using third party biometric signature recognition algorithms and facial recognition algorithms are preferred to differentiate the differences between a sample signature and facial photo referenced by a RFID card value.
Owner:PHAM THIEN VAN
Hand-wirte signature recognition program, method and device
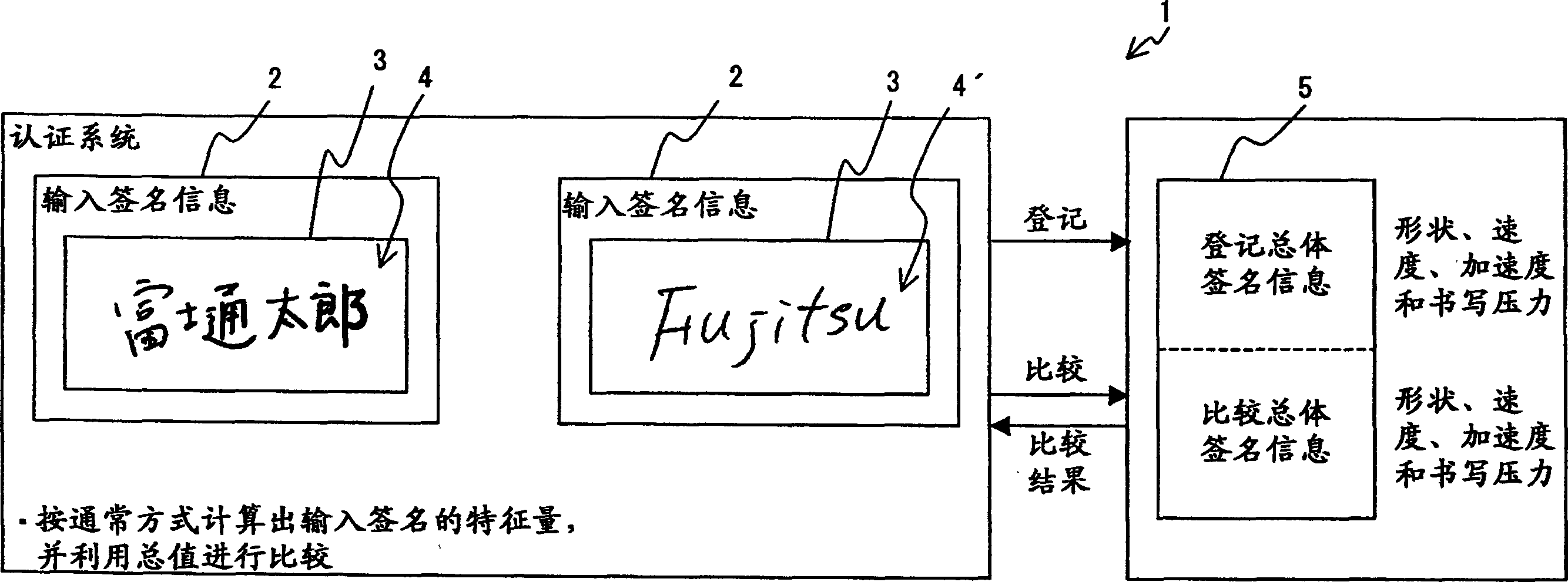
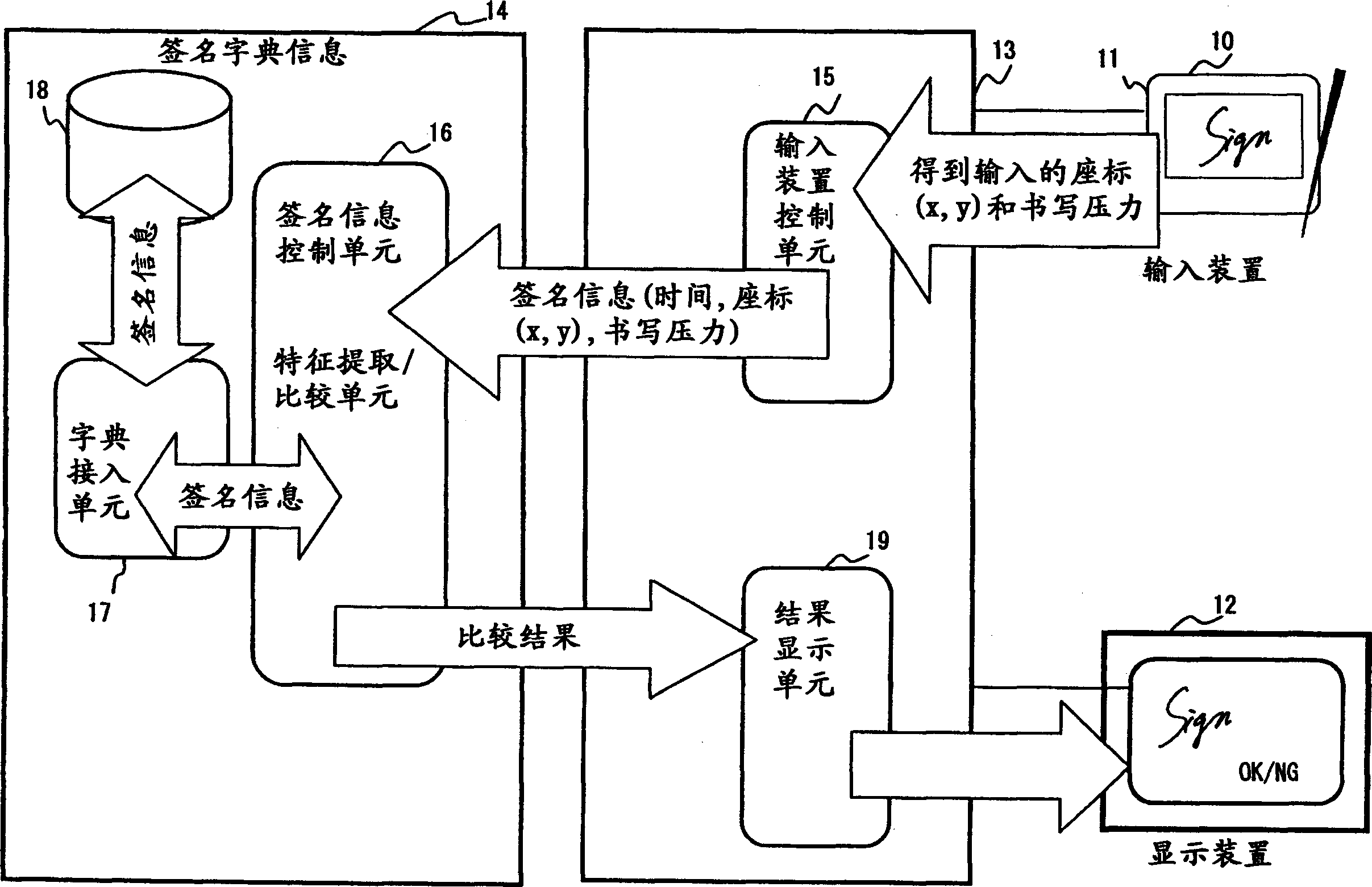
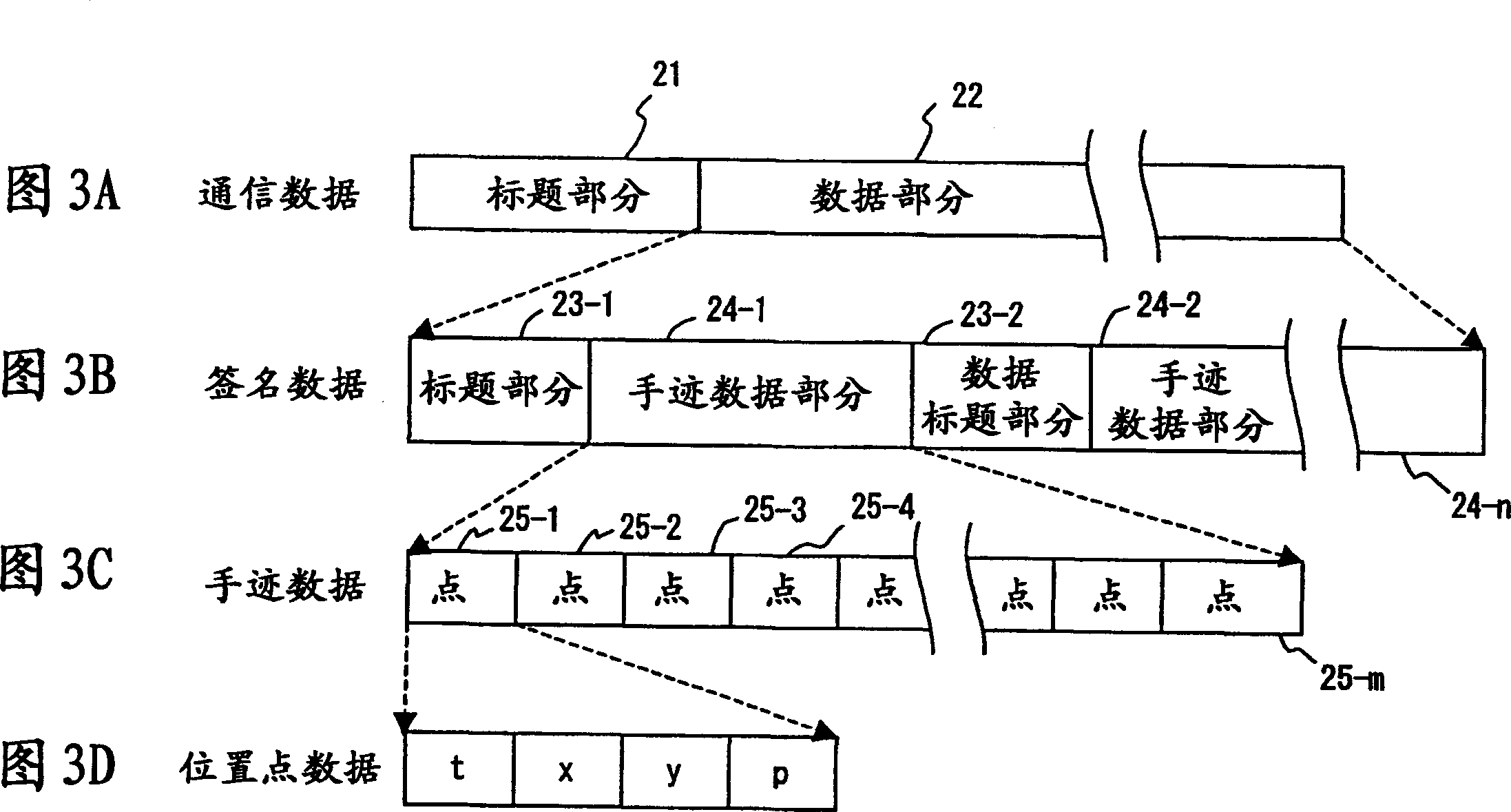
InactiveCN1445723AAvoid the authentication processAvoid false rejectionsImage analysisSpecial data processing applicationsHandwritingPattern recognition
The invention provides a handwritten signature authentication program, method and device. When registering a signature, input a Japanese signature such as "Fujitsu" ("Fujitsu") or an English signature such as "Fujitsu" n times through the input device of the input device of a signature authentication system, and calculate handwriting shape, writing speed, and writing acceleration and elements of writing pressure. Set the combination of nC2 for each element of the input data n times, get the inverse of each similarity, calculate the average value of the similarity of each element, determine the weight of each similarity according to the average value, and calculate the four elements and define it as the total similarity of the registered signatures. During the authentication process, the signature data to be compared is input / output m times. The total similarity of the signatures to be compared can be obtained in the same way.
Owner:FUJITSU LTD
Message-based exchange of access point pilot signature indicators
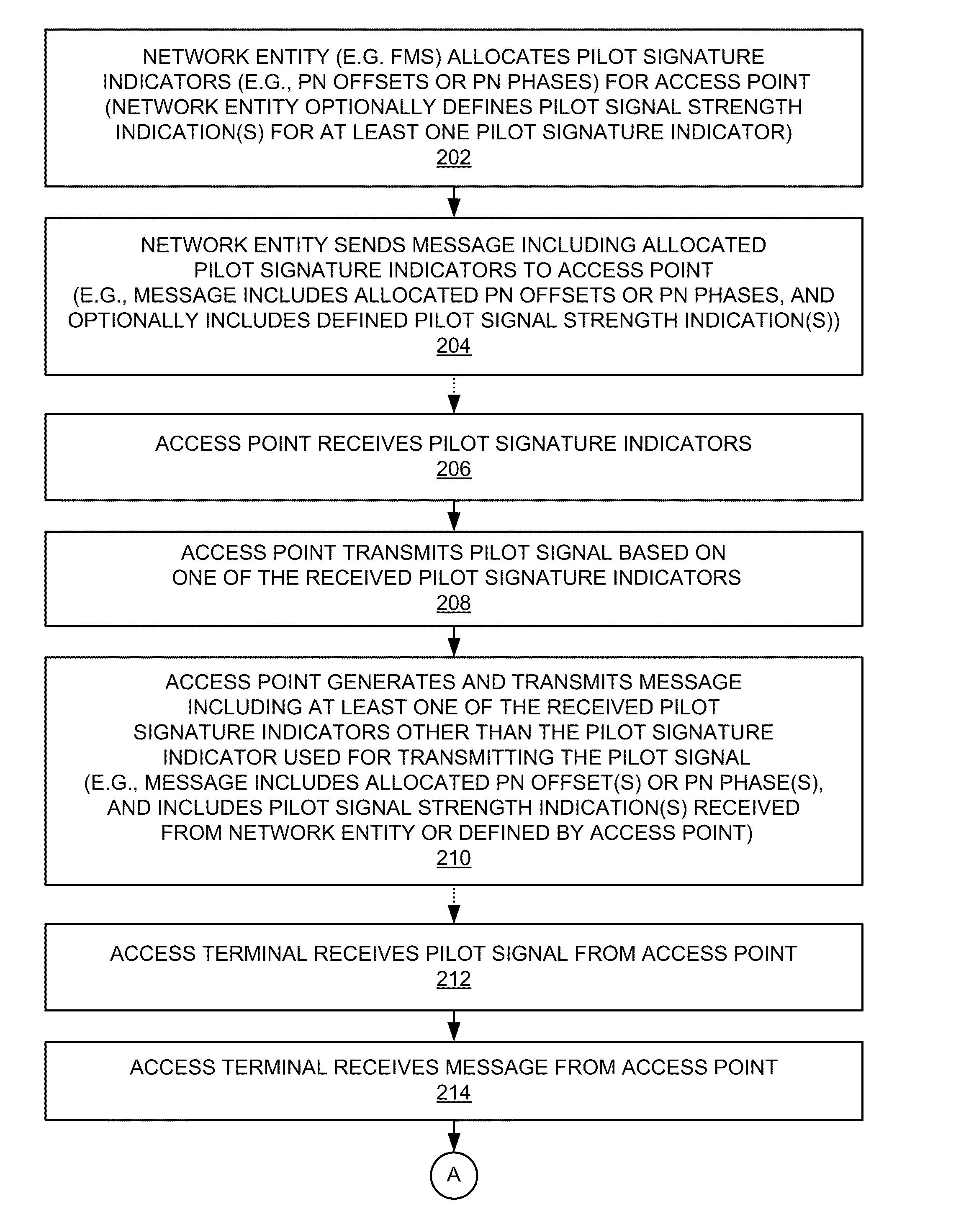
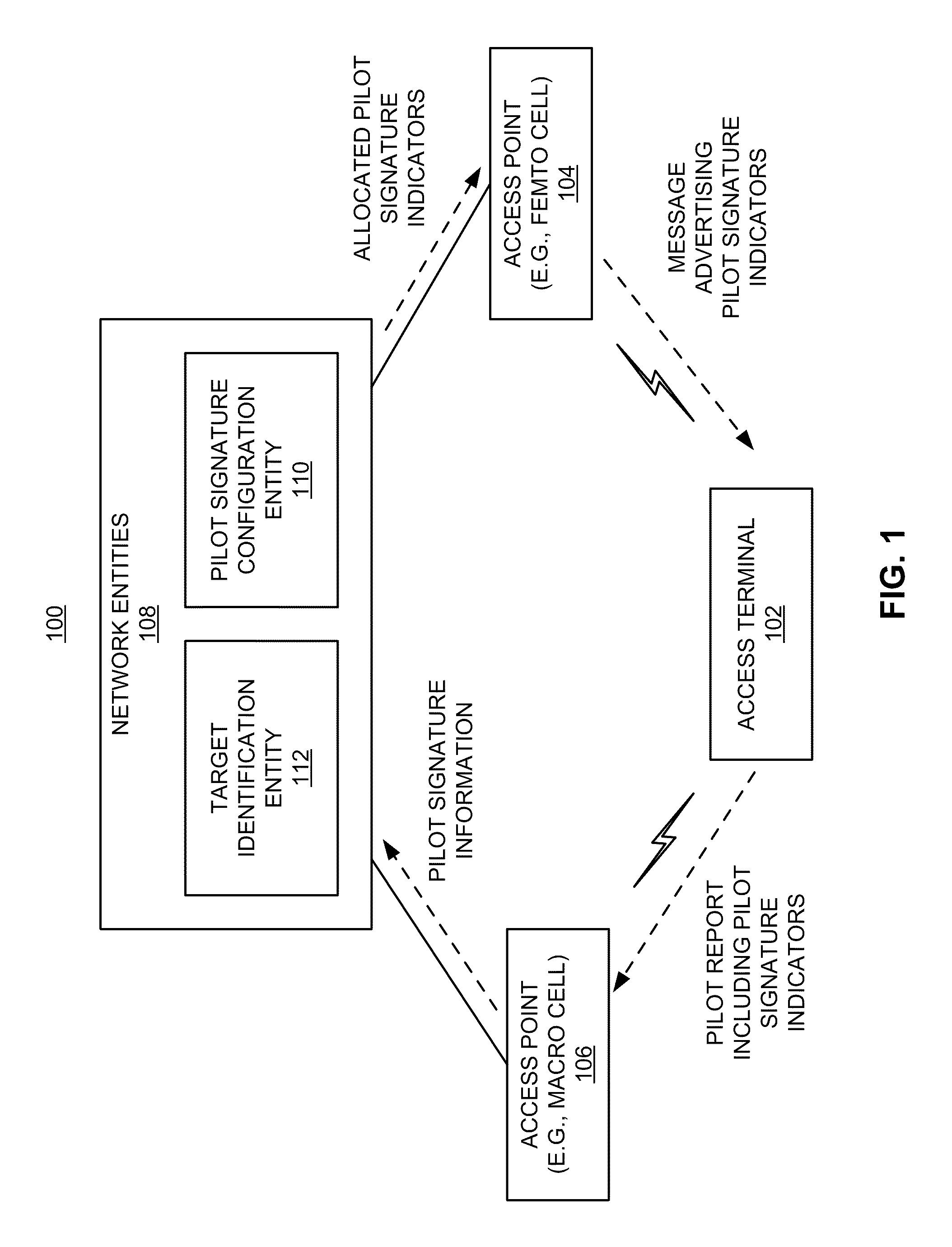
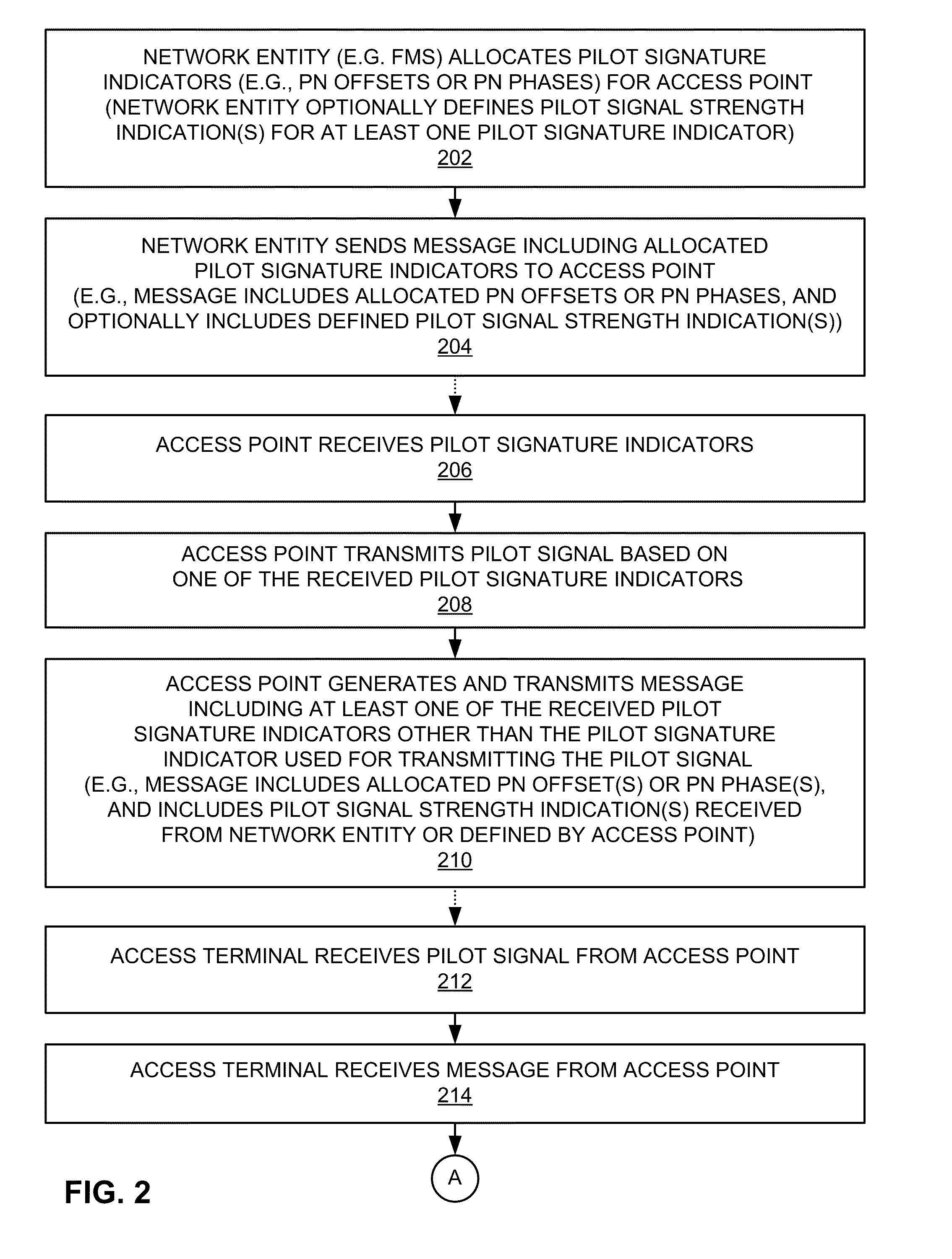
InactiveUS20110189986A1Accurate identificationAssess restrictionNetwork topologiesPilot reportBase exchange
An access point is identified based on a plurality of pilot signatures. Here, in addition to transmitting a pilot signal that is encoded (e.g., spread / scrambled) using a particular pilot signature, an access point transmits a message that includes at least one indication of at least one other pilot signature. For example, an access point may use one PN offset to generate a pilot signal and transmit a message that identifies at least one other PN offset. An access terminal that receives the pilot signal and the message may then generate a pilot report that identifies all of these pilot signatures. Upon receiving a handover message including this pilot-related information, a target network entity with knowledge of the pilot signatures assigned to that access point may then accurately identify the access point as a target for handover of the access terminal.
Owner:QUALCOMM INC
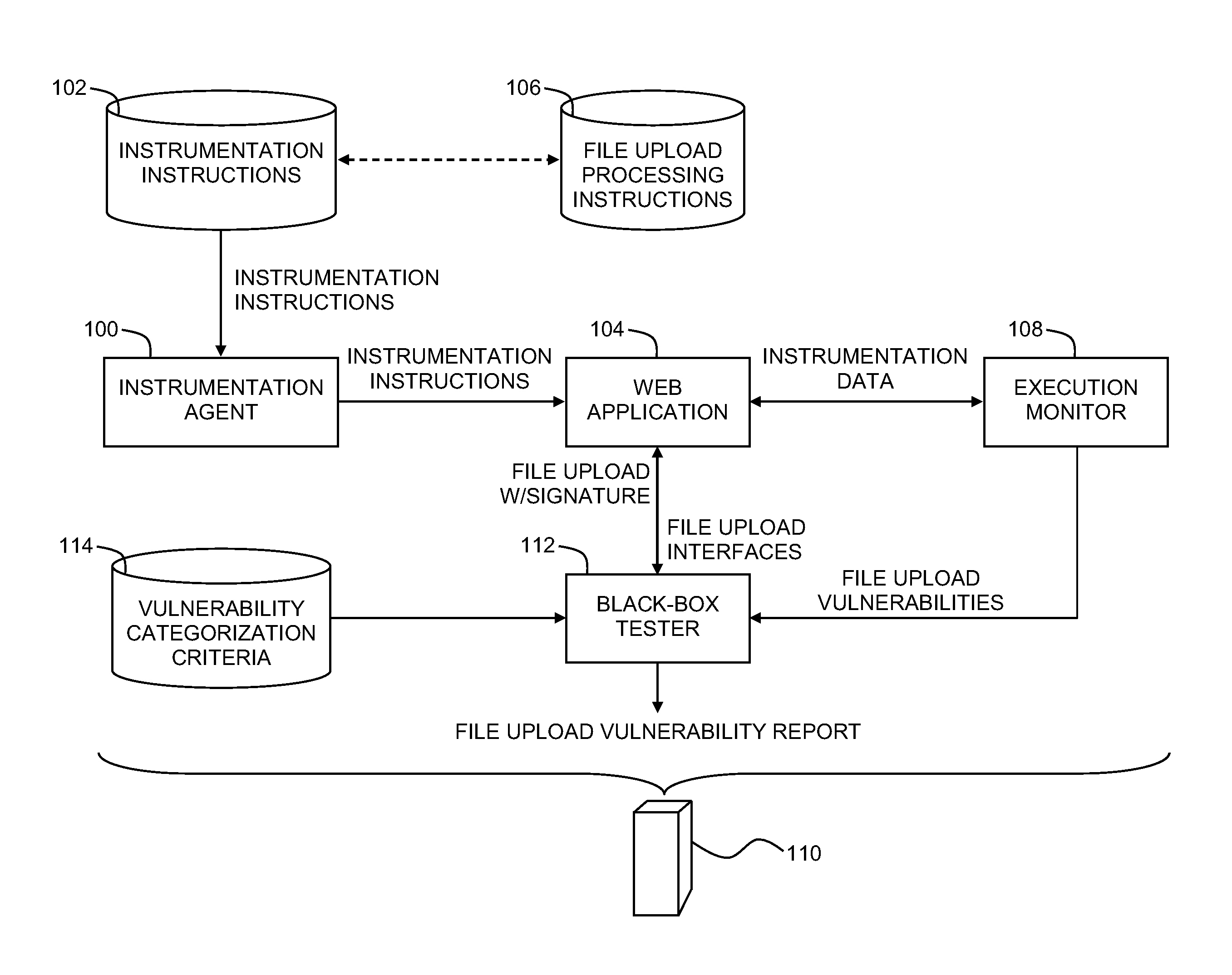
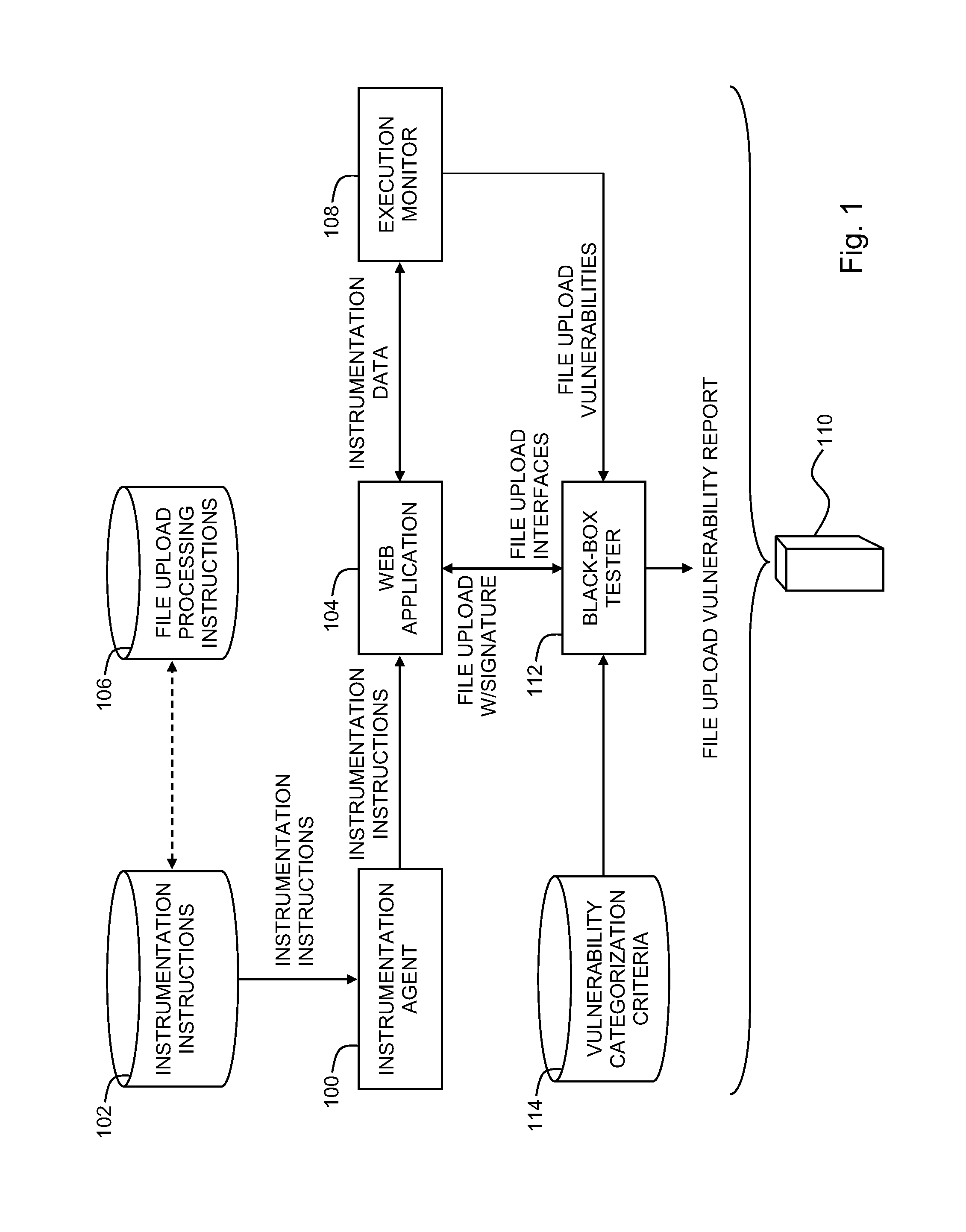
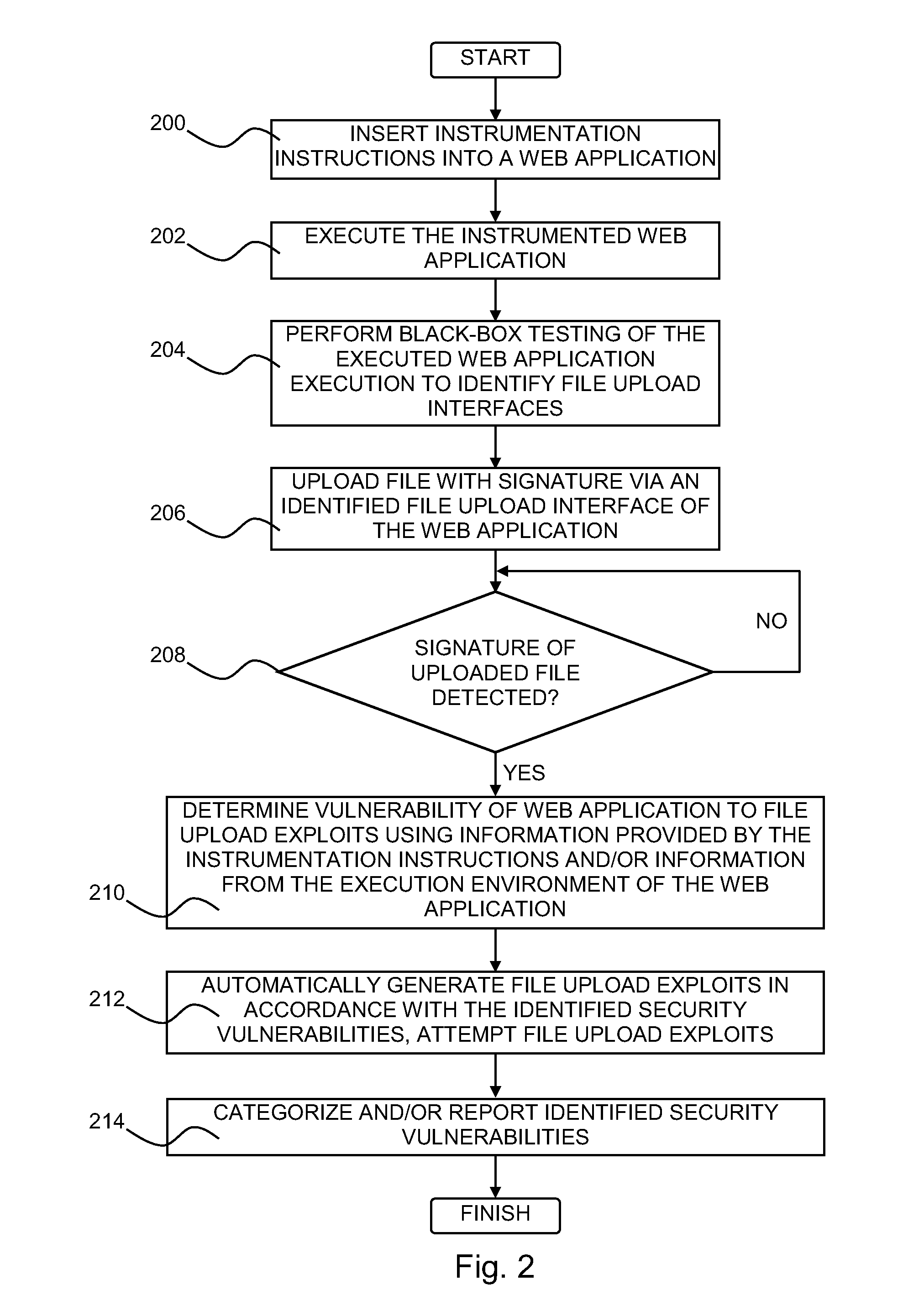
Testing web applications for file upload vulnerabilities
A system for detecting file upload vulnerabilities in web applications is provided. The system may include a black-box tester configured to upload, via a file upload interface exposed by a web application, a file together with a signature associated with the file. An execution monitor may be configured to receive information provided by instrumentation instructions within the web application during the execution of the web application. The execution monitor may be configured to recognize the signature of the uploaded file as indicating that the uploaded file was uploaded by the black-box tester. The execution monitor may also be configured to use any of the information to make at least one predefined determination assessing the vulnerability of the web application to a file upload exploit.
Owner:IBM CORP
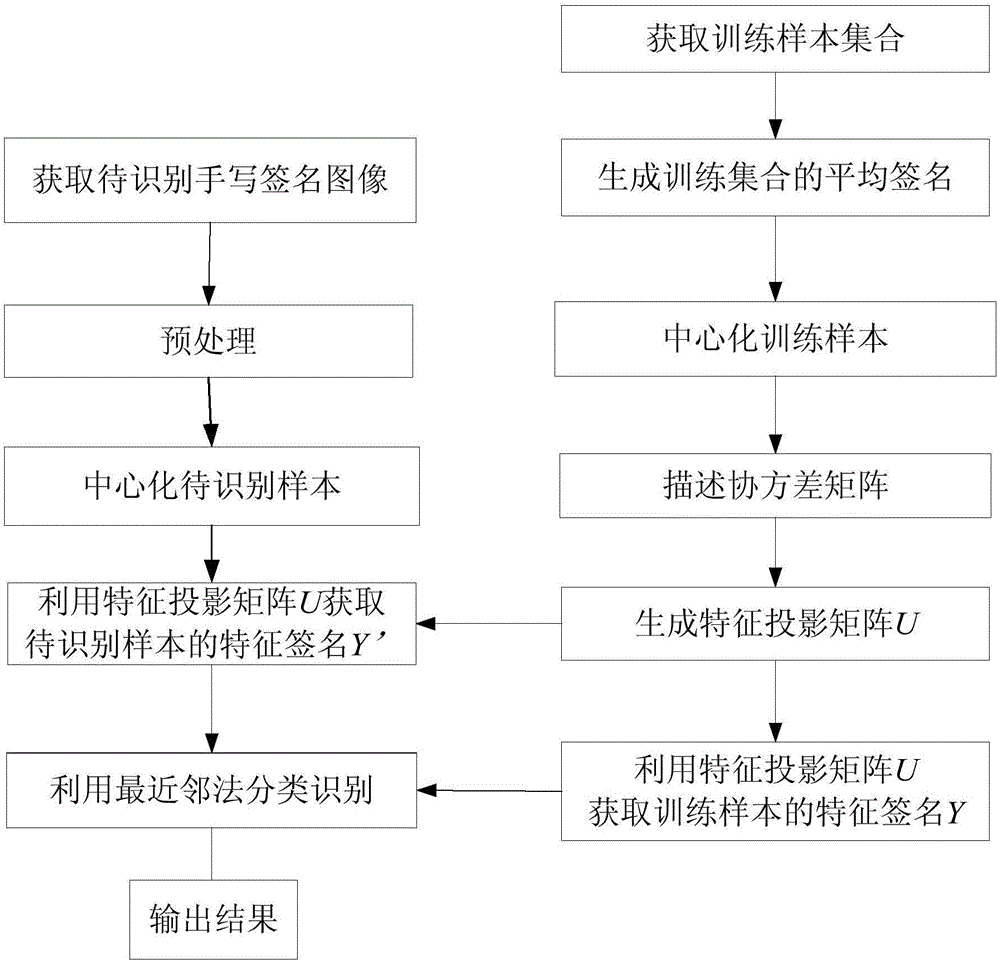
Hand-written signature identifying method based on PCA method
InactiveCN105893952AImprove recognition rateCharacter and pattern recognitionHat matrixFeature vector
The invention provides a hand-written signature identifying method based on a PCA method. The hand-written signature identifying method includes the steps of S1: obtaining original hand-written signatures, and storing the original hand-written signatures as signature images with uniform pixel format; S2: training the hand-written signature samples, taking the original signature images as an image training set, conducting gray processing for the images in the image training set and placing the processed images sequentially in a matrix, conducting special dimension reduction for images through the PCA method and extracting characteristic values and characteristic vectors to obtain the characteristic signature Y of the training sample set; S3:identifying a hand-written signature by using a nearest neighbor method, projecting the hand-written signature to be identified on a characteristic projection matrix U obtained from S2 to obtain a characteristic signature Y', comparing the characteristic signature Y' with the characteristic signature Y obtained from the training sample set through PCA projection, and selecting the minimal distance as a matching item. The recognition rate is high.
Owner:无锡度维智慧城市科技股份有限公司
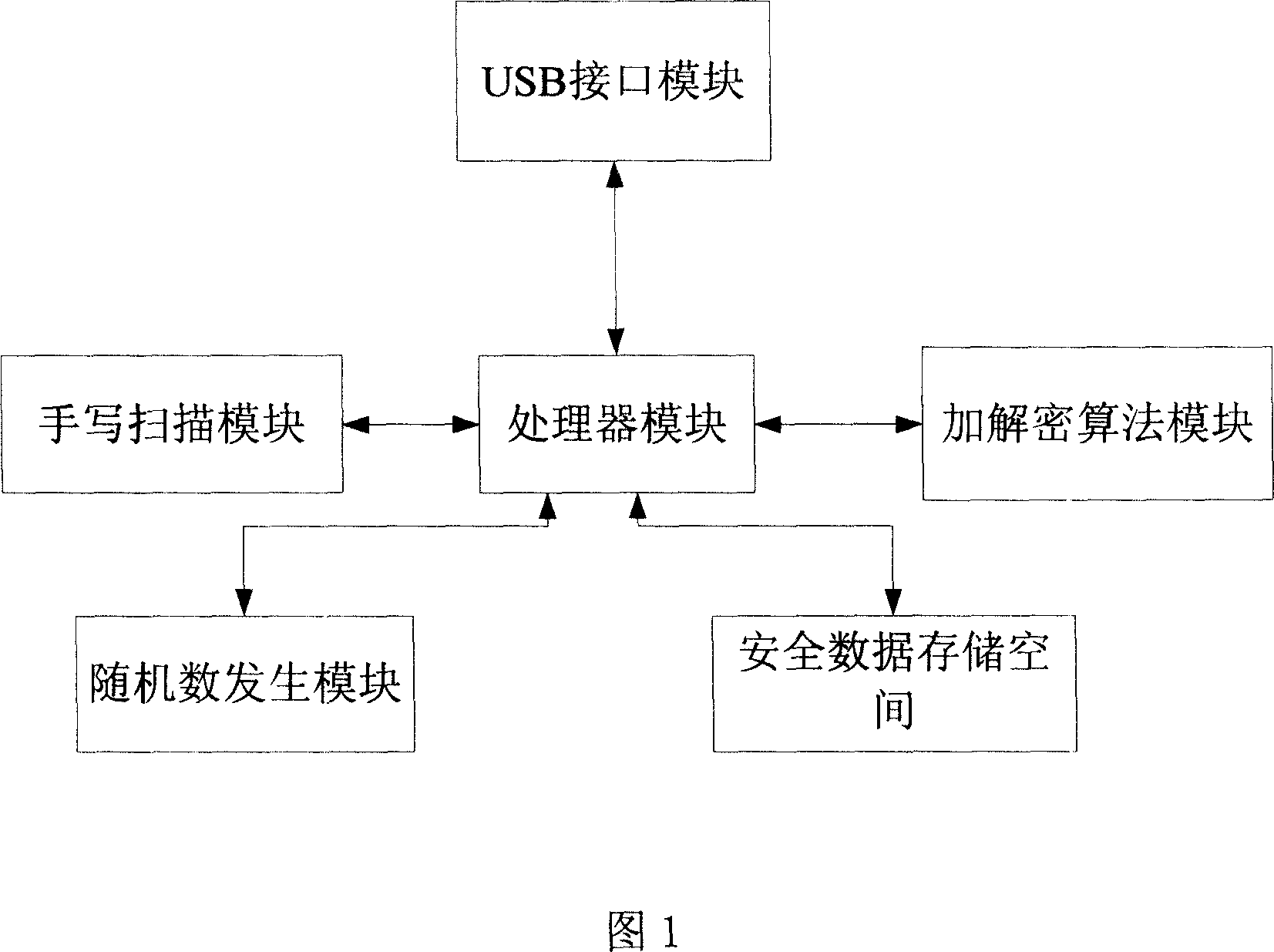
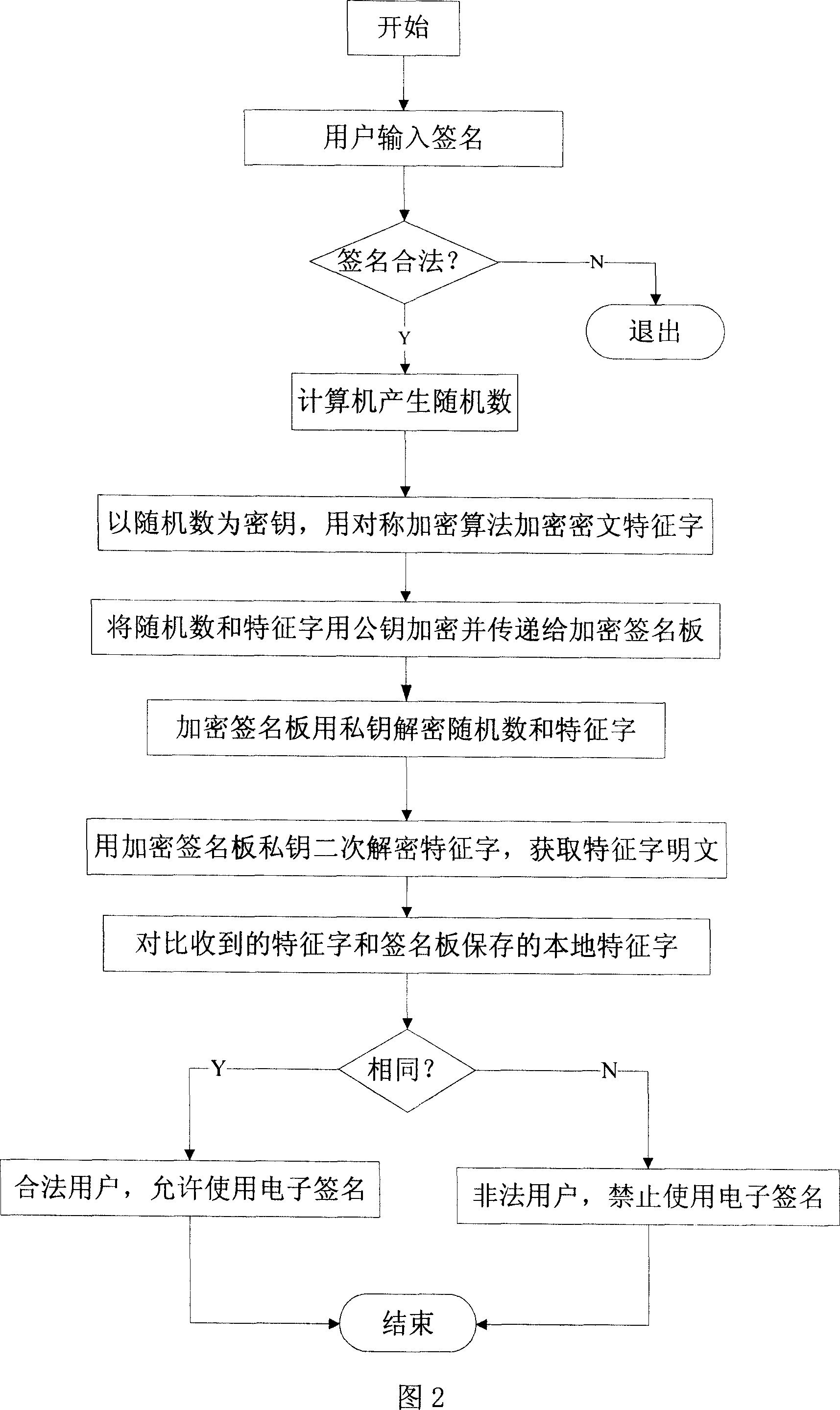
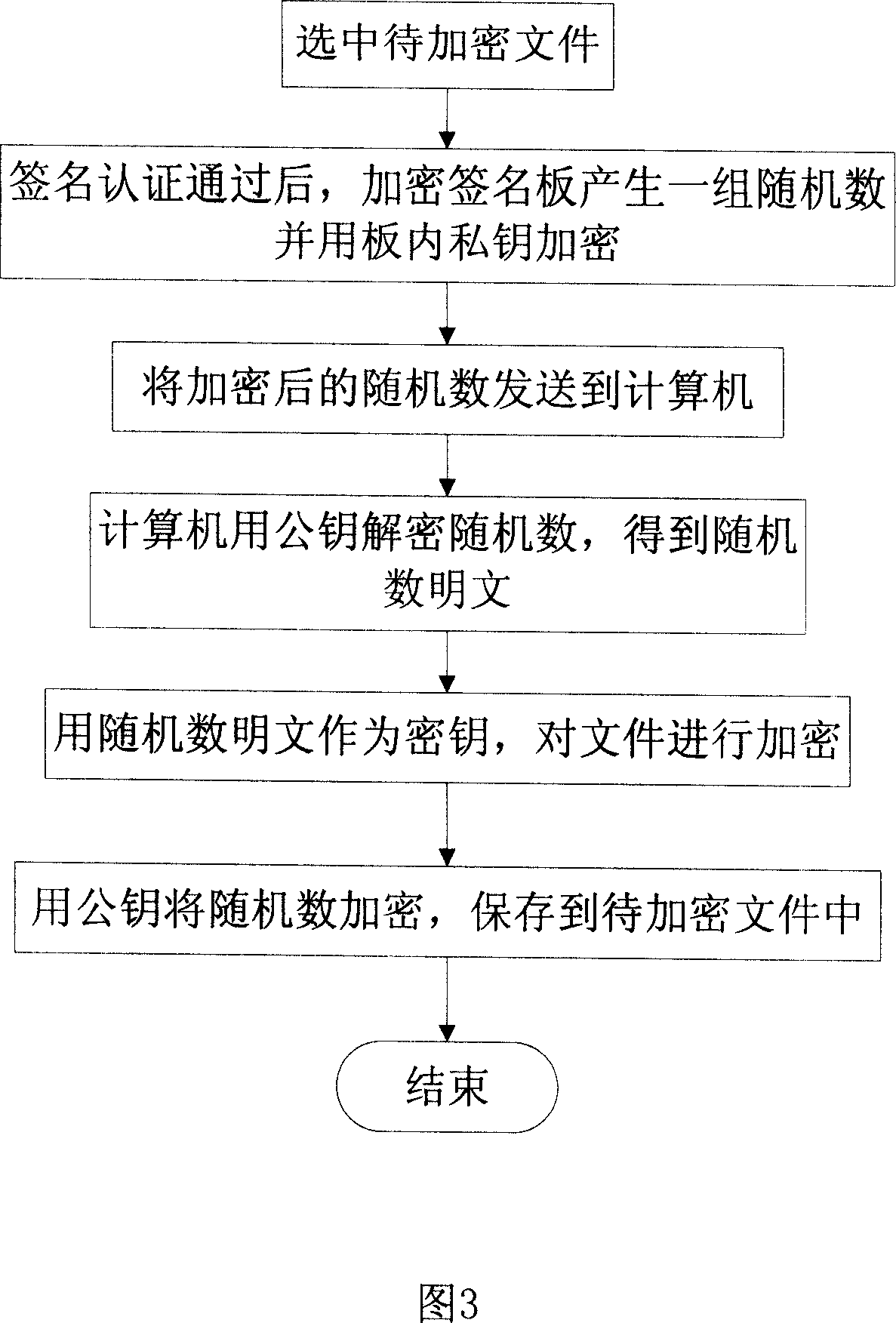
Enciphered sign board and composite encryption signing method
InactiveCN101145230AEasy to moveEnsure safetyUser identity/authority verificationDigital data authenticationSignature recognitionComputer users
A method for signature board encryption and encrypted signature composition belongs to the field of identity authentication. The technical proposal of the invention includes providing an encrypted signature board which has a processor module, a USB interface module, a hand-writing scanning module, an encryption / decryption algorithm module, a random number generating module and a safety storage space module, wherein private information of the user is stored in the module of the safety storage space. Connected to a computer, the invention identifies a written signature input by the user with a signature identifying software matched with the computer. The computer adopts public-key encrypted characteristic words, and the encrypted signature board adopts private-key encrypted characteristic words and performs comparison with the characteristic words stored in the safety storage space of the encrypted signature board to realize the protection of electronic signatures and the composite encryption of documents with the hardware encryption of the encrypted signature board and the software encryption of the computer. Mainly applied to the protection field of electronic signatures and personal information of computer users, the invention strengthens the safety and mobility of electronic signature carriers.
Owner:HANWANG MFG
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com