Hiding method and system for signature of credible two-dimensional code
A two-dimensional code, reliable technology, applied in the field of two-dimensional code, can solve the problems of high requirements for decoding equipment, large amount of calculation, and inability to achieve watermark extraction.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
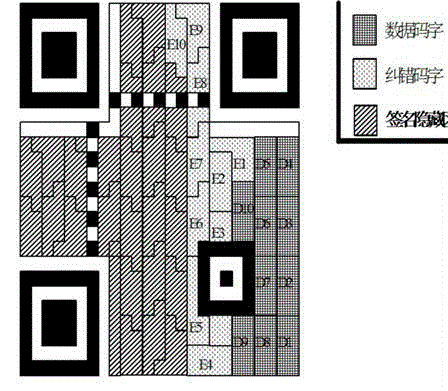
[0059] The invention discloses a method for hiding a signature in a credible two-dimensional code. The two-dimensional code is an effective carrier that can be used to publish information such as a website, a microblog account number, a business card, and the like.
[0060] Among the hidden methods of signing in trusted QR codes are:
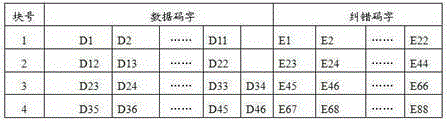
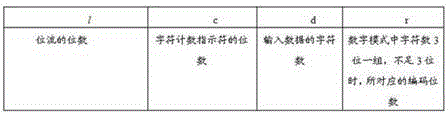
[0061] Signature hiding steps: h(m) is the message digest generated by the hash function of the information m released by the user, Ks and Kp are the effective private key and public key generated by the public key algorithm; use your own private key Ks to encrypt the message digest h( m) to obtain the signature D; according to the two-dimensional code coding rules, encode the information m and signature D issued by the user, and obtain the data bit stream Data of the information m respectively m and the data bit stream Data of signature D D , the data bit stream contains data codewords and error correction codewords; according to the two-dimen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com