Configuration system and methods including configuration inheritance and revisioning
a configuration system and configuration technology, applied in the field of computer network management, can solve the problems of difficult, if not impossible, for a network security administrator to know, monitor and change configurations in view of security threats, and ensure that the policy is properly implemented at all times on the network, and achieve the effect of effective configuration
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
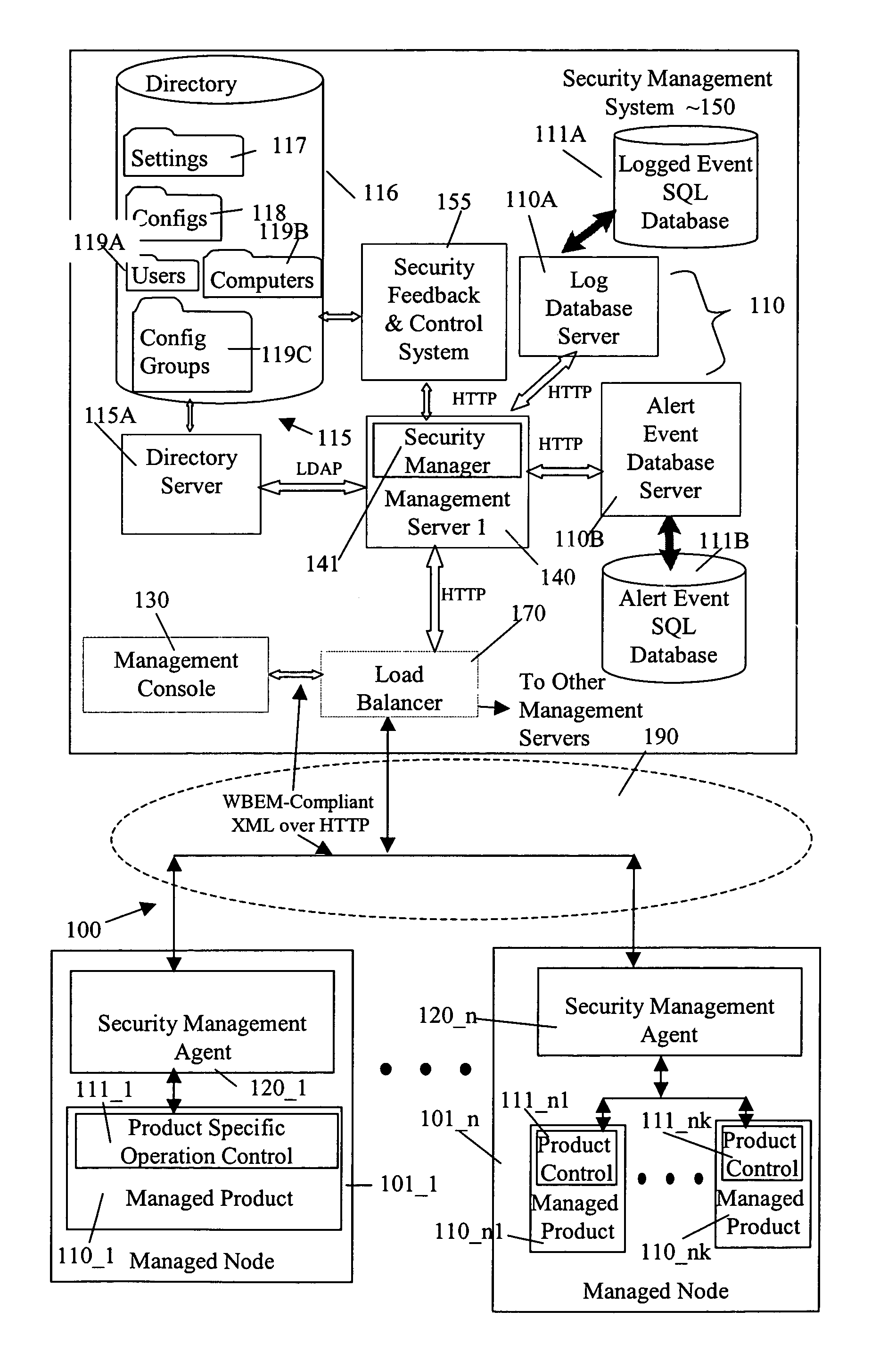
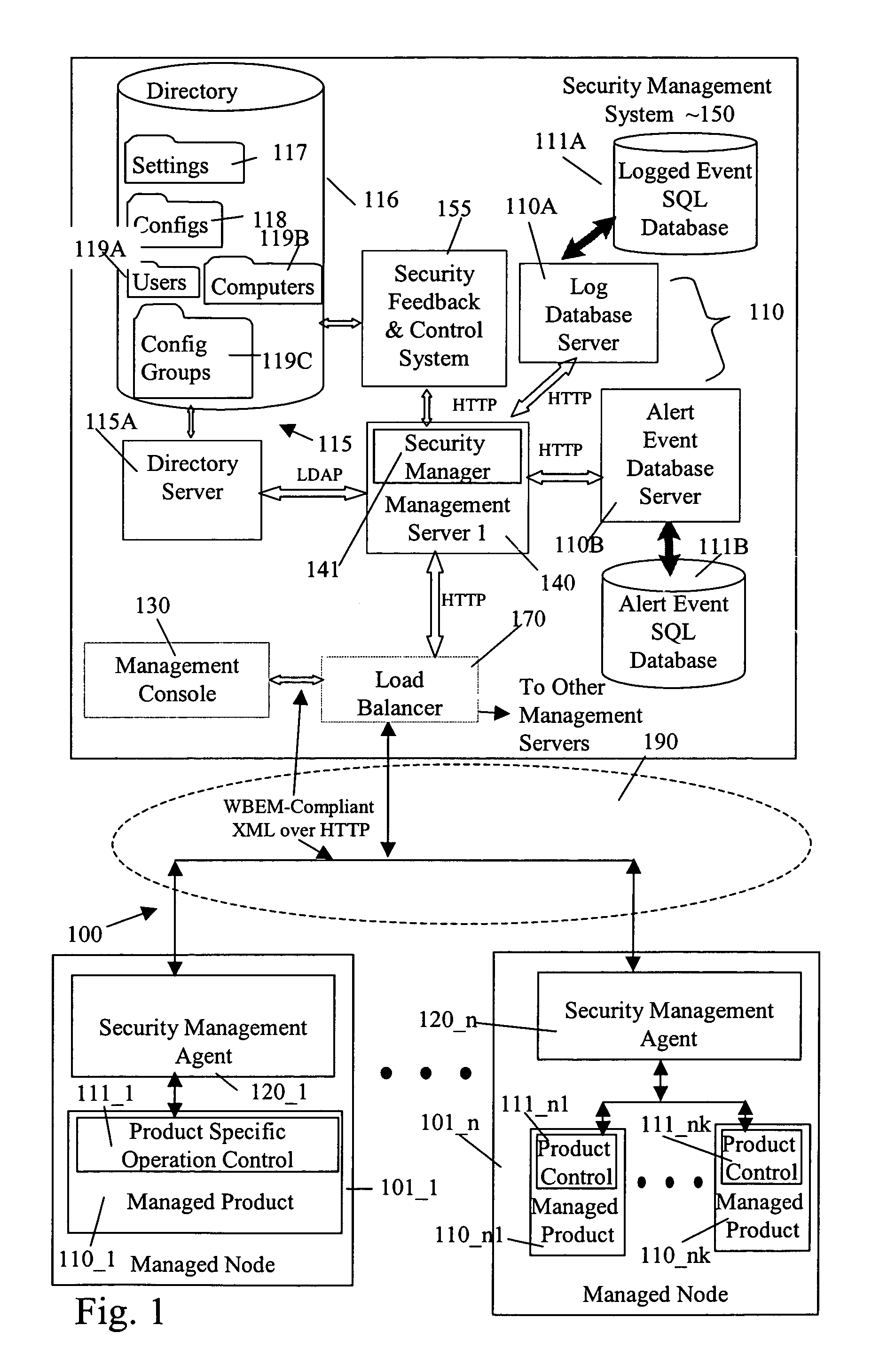
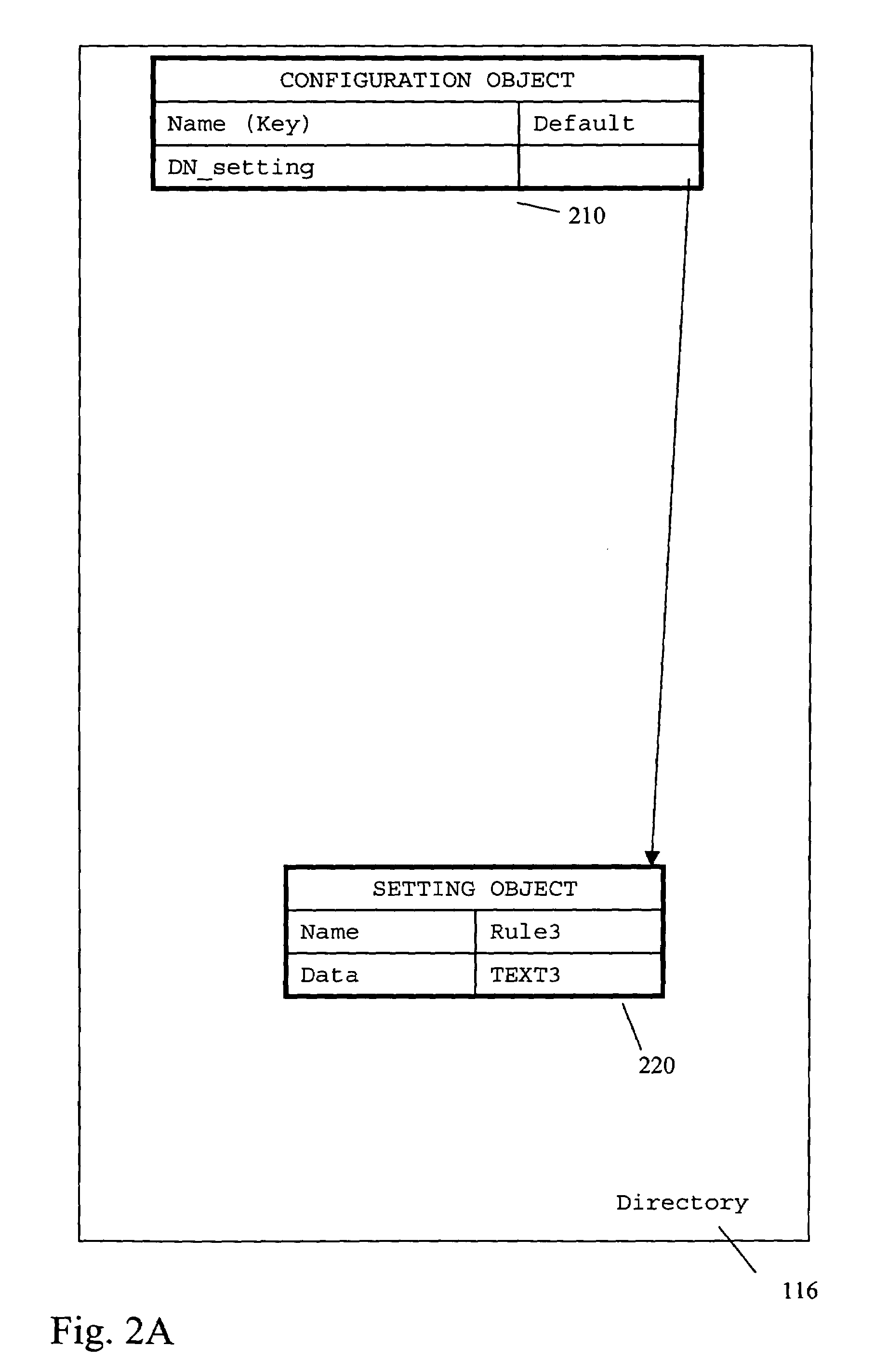
[0072]A system 100 (FIG. 1) includes a security management system 150 for a plurality of managed products 110_1 to 110—nk. Security management system 150 stores configuration data for managed products 110_1 to 110—nk in a directory 116. Configuration data is stored in directory 116 in the form of configuration objects 118 and setting objects 117, in one embodiment. In one embodiment, the operational parameters are included in one or more setting objects that are addressed by a configuration object, e.g., the configuration object includes pointers to the setting objects.
[0073]Configuration objects may be assigned to an entity in computers 119B, an entity in users 119A, or an entity in configuration groups 119C. As explained more completely below, each of a computer, a user, and a configuration group may be assigned one configuration object for a software feature of a managed product.
[0074]Inheritance between configuration objects 118 is supported. This allows an administrator to crea...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com