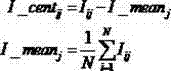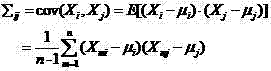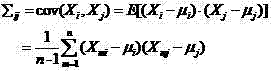Hardware Trojan horse recognition method based on neural network
A hardware Trojan and neural network technology, applied in the field of neural network-based hardware Trojan recognition, can solve the problems of large errors and low efficiency, and achieve the effect of overcoming defects and improving recognition efficiency and accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0012] A kind of hardware Trojan horse recognition method based on neural network described in this embodiment, the method comprises the following steps:
[0013] Step 1. For all the chips to be tested, perform data preprocessing on the side channel information to obtain a preprocessed side channel information matrix of all the chips to be tested;
[0014] Step 2, select a part of the chip to be detected as the anti-section chip, and other remaining chips to be detected are called test chips, and the reverse analysis is carried out to the anti-section chip to determine whether each anti-section chip contains a hardware Trojan horse;
[0015] Step 3, take out the side channel information corresponding to the anti-profile chip that does not contain the hardware Trojan horse determined by step 2 from the side channel information matrix described in step 1, and use this side channel information to establish the feature space of the chip;
[0016] Step 4, projecting the preprocesse...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com