Testing vector generating method based on variation analysis for effectively activating hardware trojan horses
A technology of test vectors and hardware Trojan horses, applied in error detection/correction, instrumentation, electrical digital data processing, etc., can solve the problems of identifying hardware Trojan horses, flooding, and difficulty, and achieve high test efficiency, strong purpose, and methods mature effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
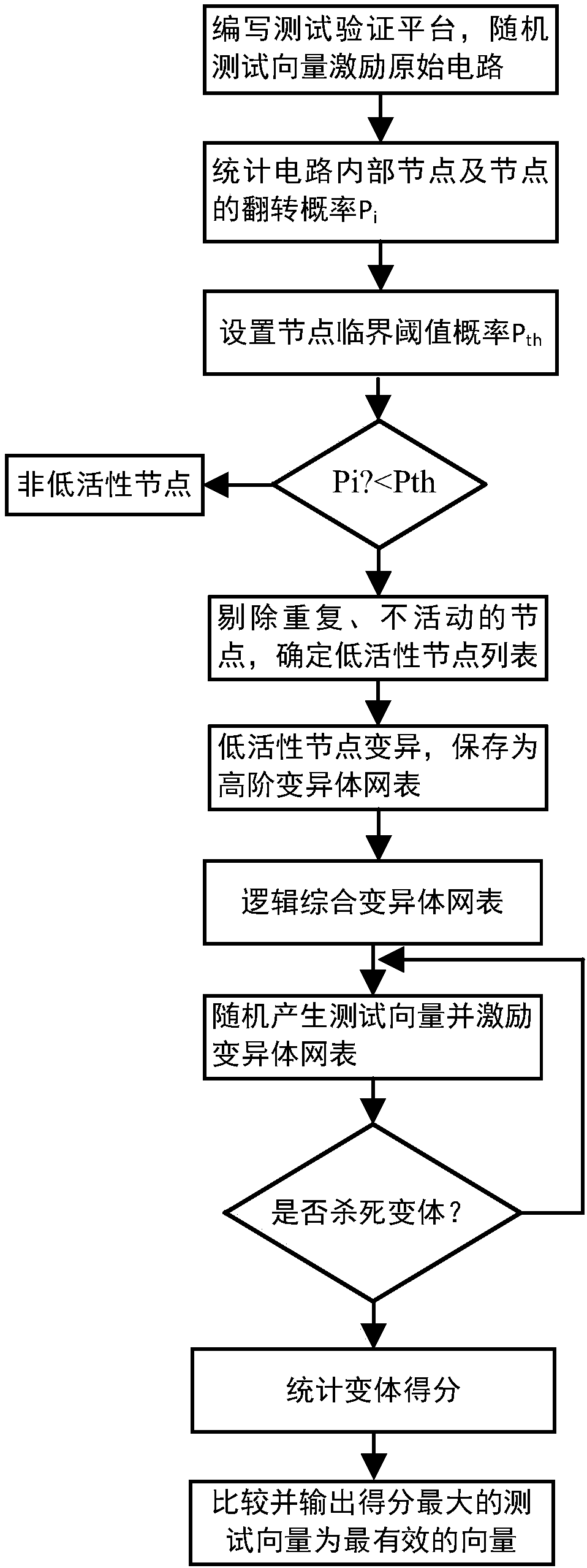
[0034] The present invention proposes a method for generating test vectors based on mutation analysis for effective activation of hardware Trojan horses, using methods of software testing and locating program loopholes to locate the implantation point of the hardware Trojan horse—the low-activity node, and targeting at the implantation point of the hardware Trojan horse Screening test vectors that can effectively activate hardware Trojan horses, this method has strong purpose, low test cost, high test efficiency, more streamlined test sequences, and more effective activation of hardware Trojan horses. The analysis has certain practical significance and reference value.
[0035] The present invention is on the basis of software testing, combined with the concealment characteristics of hardware Trojan horses, proposes a test vector generation method that utilizes mutation analysis to effectively activate hardware Trojan horses, analyzes the structural characteristics of the mothe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com