Nondestructive detecting method of mixed activated hardware Trojan horse in integrated circuit
A technology of integrated circuits and hardware Trojan horses, applied in the field of detection of malicious circuit modules, can solve problems such as detection and killing, and achieve the effect of avoiding being attacked and ensuring safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
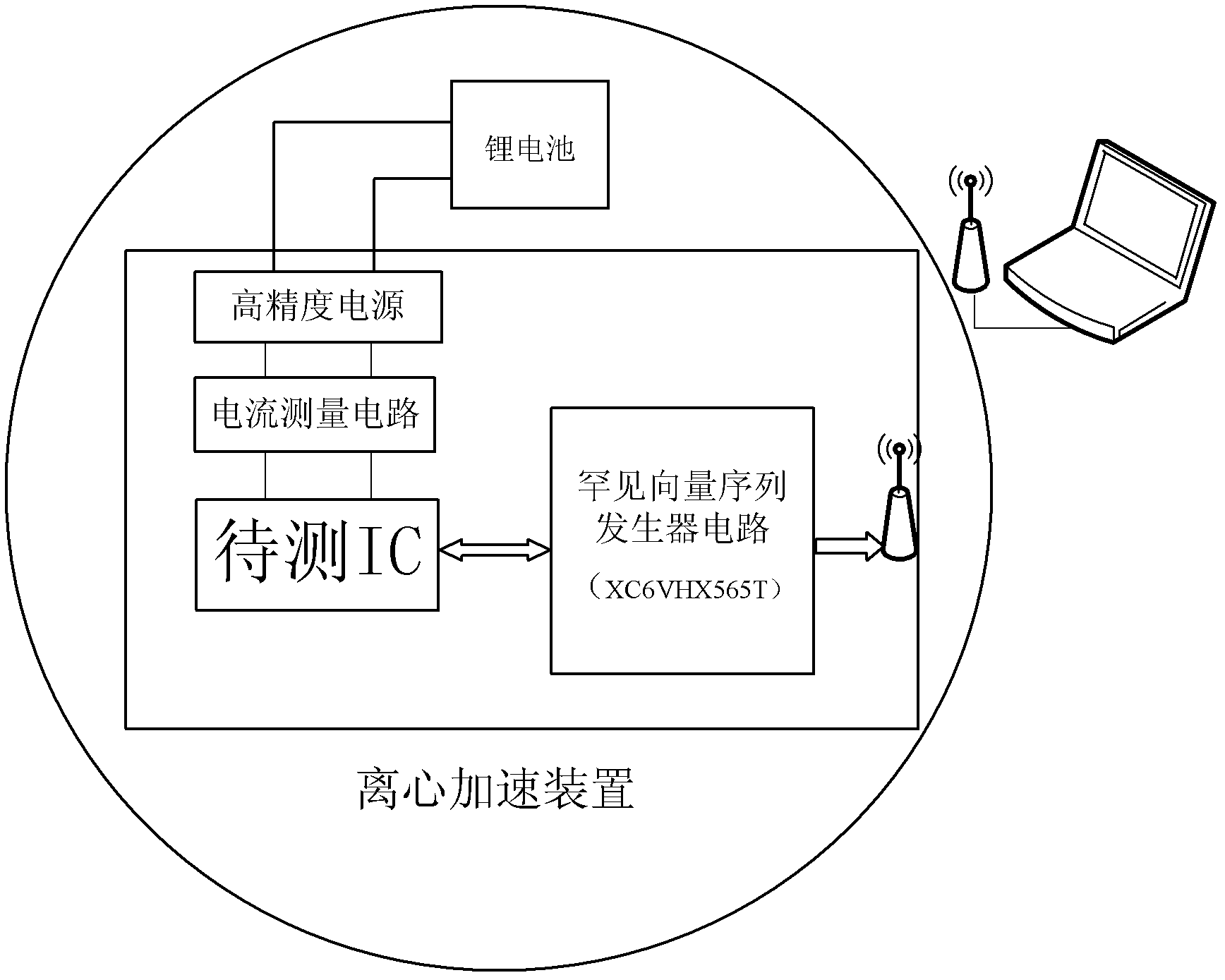
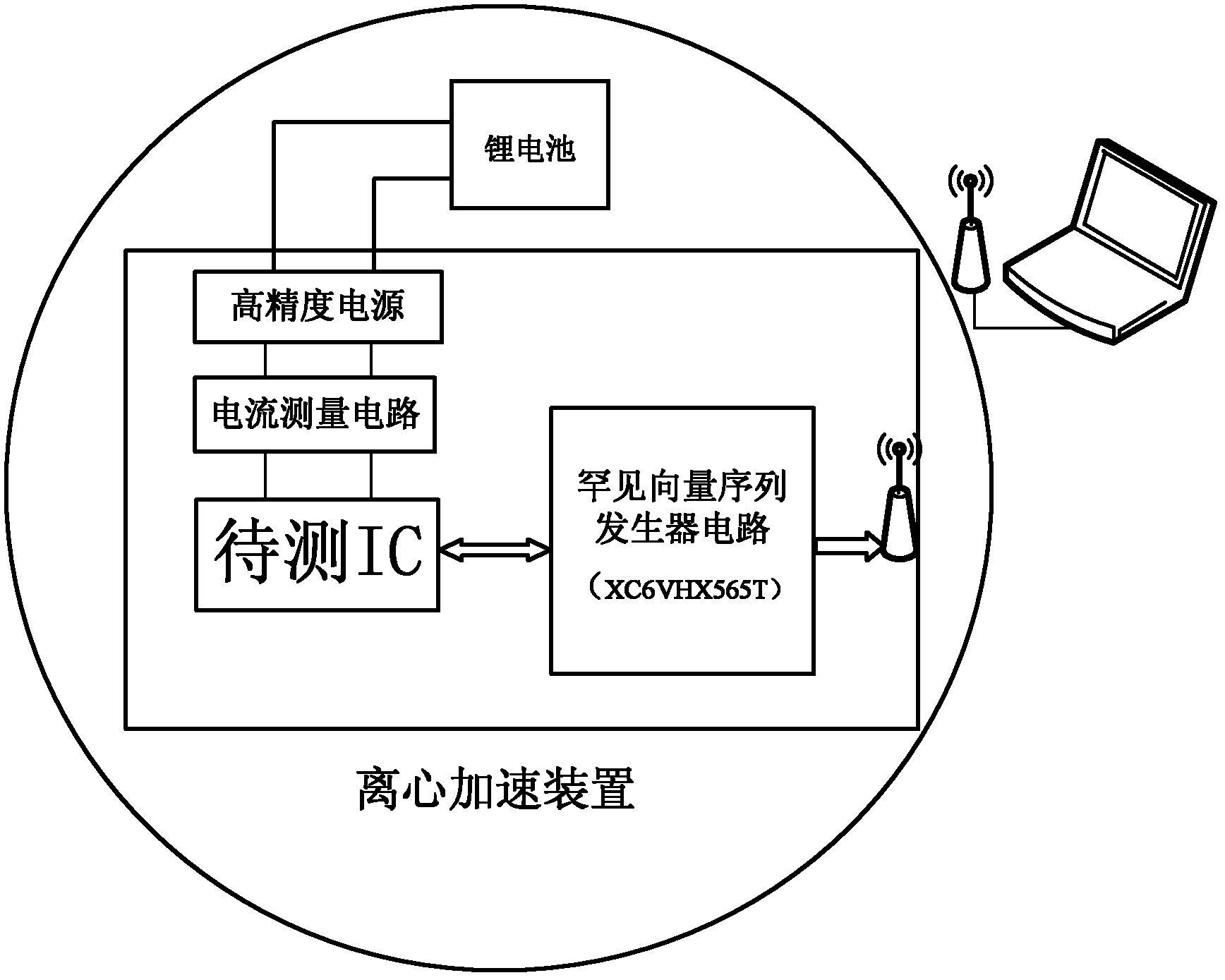
[0022] The integrated circuit tested in this example is the integrated circuit implanted by the research group into a hardware Trojan horse. This circuit features a MEMS acceleration sensor, serial data transmission and processing. The transmission speed of the circuit receiving data is 115kbps, the normal data is CRC check data, each frame of data is 7 data bits + 4 check bits, the normal working current consumption is less than 20uA, and the bit error rate is less than 0.1%.
[0023] The specific test method is: use the phase-locked loop embedded in Xilinx's XC6VHX565T to realize a high-precision test system clock. The circuit is powered independently and its current consumption and output port signal are monitored. The rare vector sequence generator is coded in verilog hardware description language, synthesized with Foundation ISE and downloaded to the XC6VHX565T structure for implementation, and is powered separately from the integrated circuit under test.
[0024] In th...
Embodiment 2
[0100] The circuit tested in this example is an integrated circuit implanted by the research group into a hardware Trojan. This circuit features a MEMS acceleration sensor, serial data transmission and processing. The transmission speed of the circuit receiving data is 115kbps, the normal data is CRC check data, each frame of data is 7 data bits + 4 check bits, the normal working current consumption is less than 20uA, and the bit error rate is less than 0.1%.
[0101] The specific test method is: use the phase-locked loop embedded in Xilinx's XC6VHX565T to realize a high-precision test system clock. The circuit is powered independently and its current consumption and output port signal are monitored. The rare vector sequence generator is coded in verilog hardware description language, synthesized with Foundation ISE and downloaded to the XC6VHX565T structure for implementation, and is powered separately from the integrated circuit under test.
[0102] In this example, the no...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com