Hardware Trojan horse detection device and method based on weak same paths
A hardware Trojan detection, same-path technology, applied in computer security devices, internal/peripheral computer component protection, instruments, etc., can solve problems such as increased power consumption, many circuit paths, and complex processes, saving circuit area and reducing complexity the effect of improving the accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
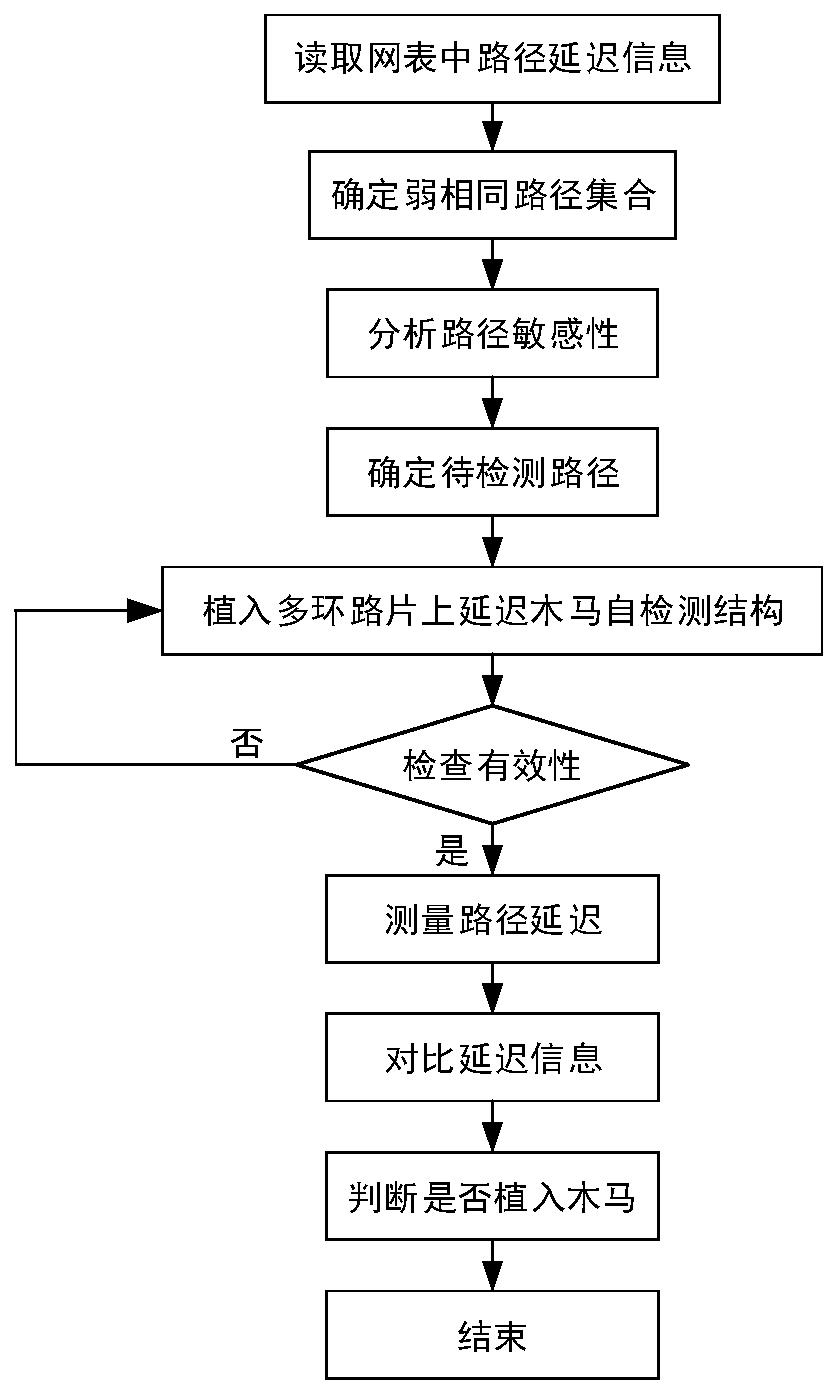
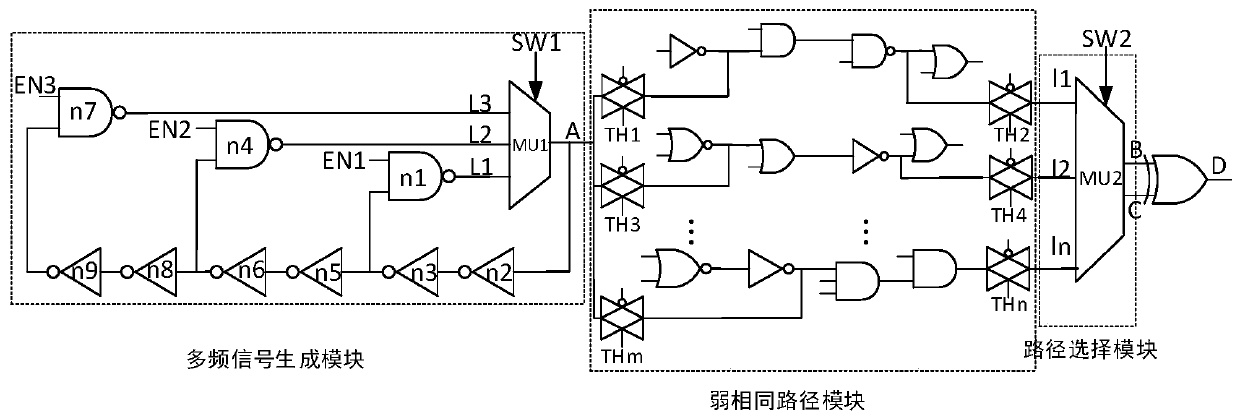
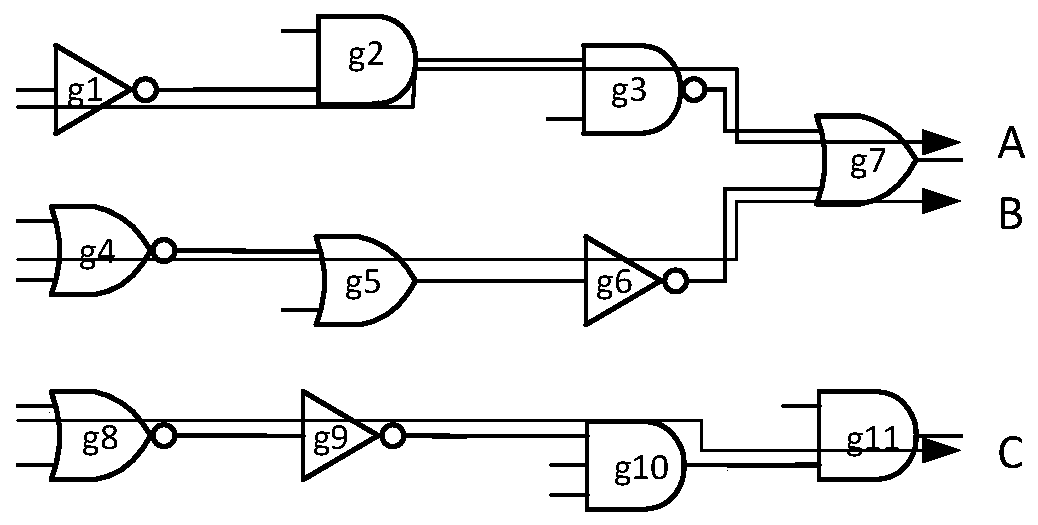
[0037] The traditional path-based hardware Trojan detection method needs to measure and compare the delay information of a large number of original circuits, the detection efficiency is low, the cost is high, and there are process deviations in the manufacturing process, resulting in a deviation between the actual value of the path delay and the theoretical value, which seriously reduces the improved the accuracy of Trojan horse detection. Aiming at the problem that Trojan horses are easily implanted in the chip manufacturing process, the present invention proposes a multi-loop on-chip delay Trojan horse self-detection structure based on weakly identical paths, which can quickly and effectively detect delay information on weakly identical paths. And compared with the simulation results, there is no need to establish a golden model, which reduces the complexity and cost of chip inspection. By comparing the difference in path delay, the influence of process deviation is removed. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com