Hardware trojan horse detection method based on few-state point analysis
A technology of hardware Trojan detection and point analysis, applied in the direction of platform integrity maintenance, etc., can solve the problems of insignificance, small hardware Trojan circuit scale, and non-negligible impact, and achieve the effects of strong applicability, low detection cost, and improved recognition efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
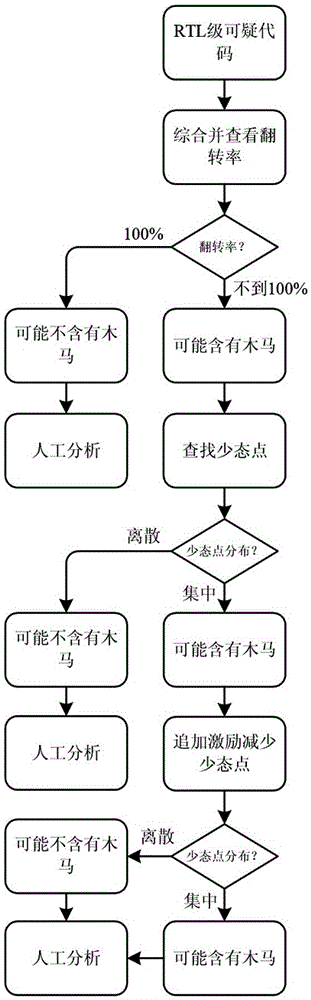
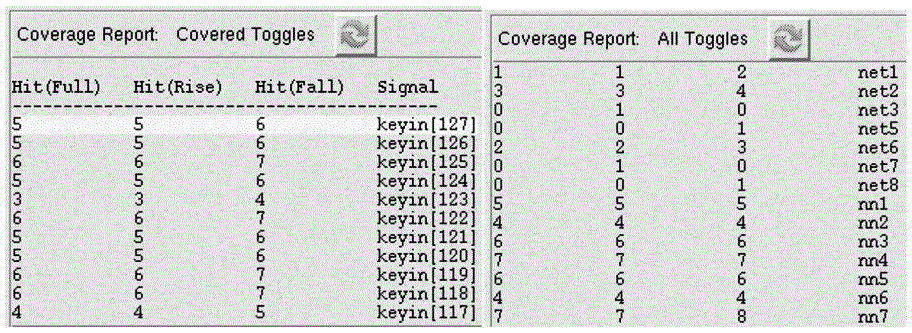
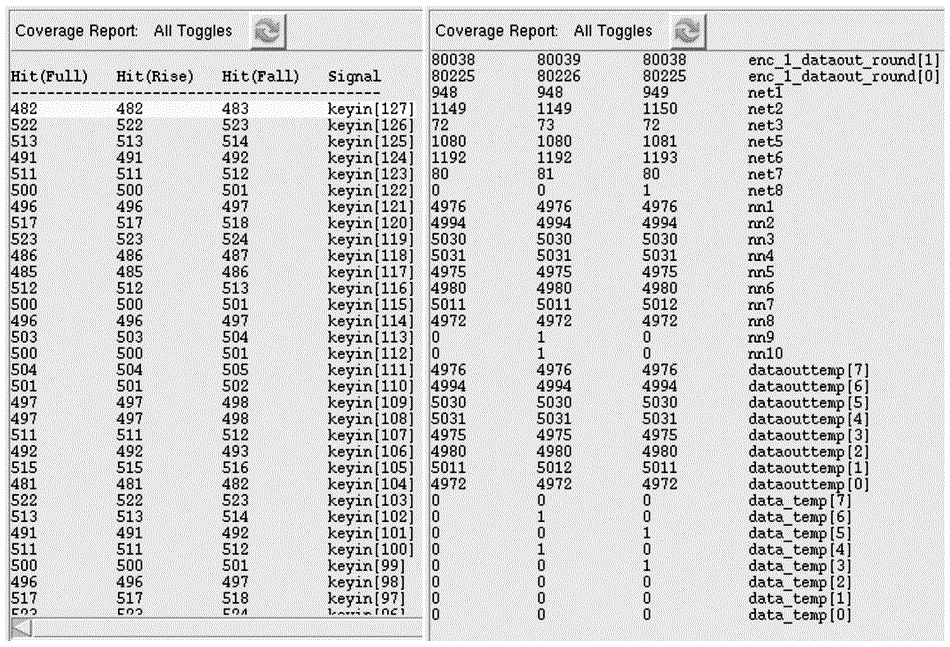
[0024] It has become one of the mainstream design methods to find the few state points in the circuit and use these few state points as the trigger logic hardware Trojan design method. Hardware Trojans often use fewer state points to attack during the design and implantation process, thereby increasing the probability of successful attack and concealment. And for the multi-point trigger technology, the functional logic of its hardware Trojan horse will not be activated when the circuit is working normally. That is to say, even if some designers will specially hide the Trojan horse circuit, the trigger point of its functional logic is not related to the entire function. Logic must be less stateful. Therefore, the present invention is based on the above principles, and analyzes the hardware Trojan horse attack by locating and statistic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com