Hardware Trojan horse detection method based on neural network
A hardware Trojan detection and neural network algorithm technology, applied in neural learning methods, biological neural network models, neural architecture, etc., can solve the problem of insignificant physical feature representation, insignificant influence of circuit bypass information, and bypass information of hardware Trojans. Problems such as difficult detection technology, to achieve the effect of universality, fast detection speed, and high recognition
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
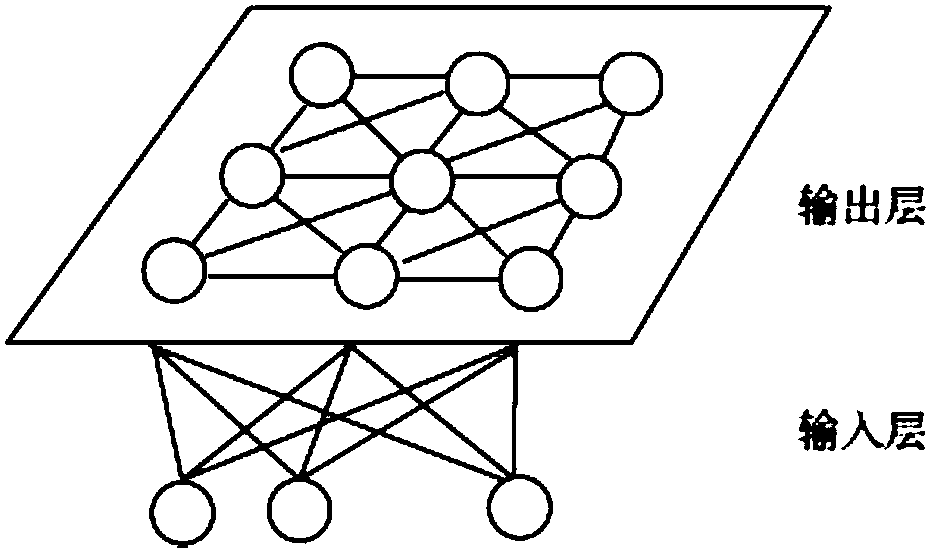
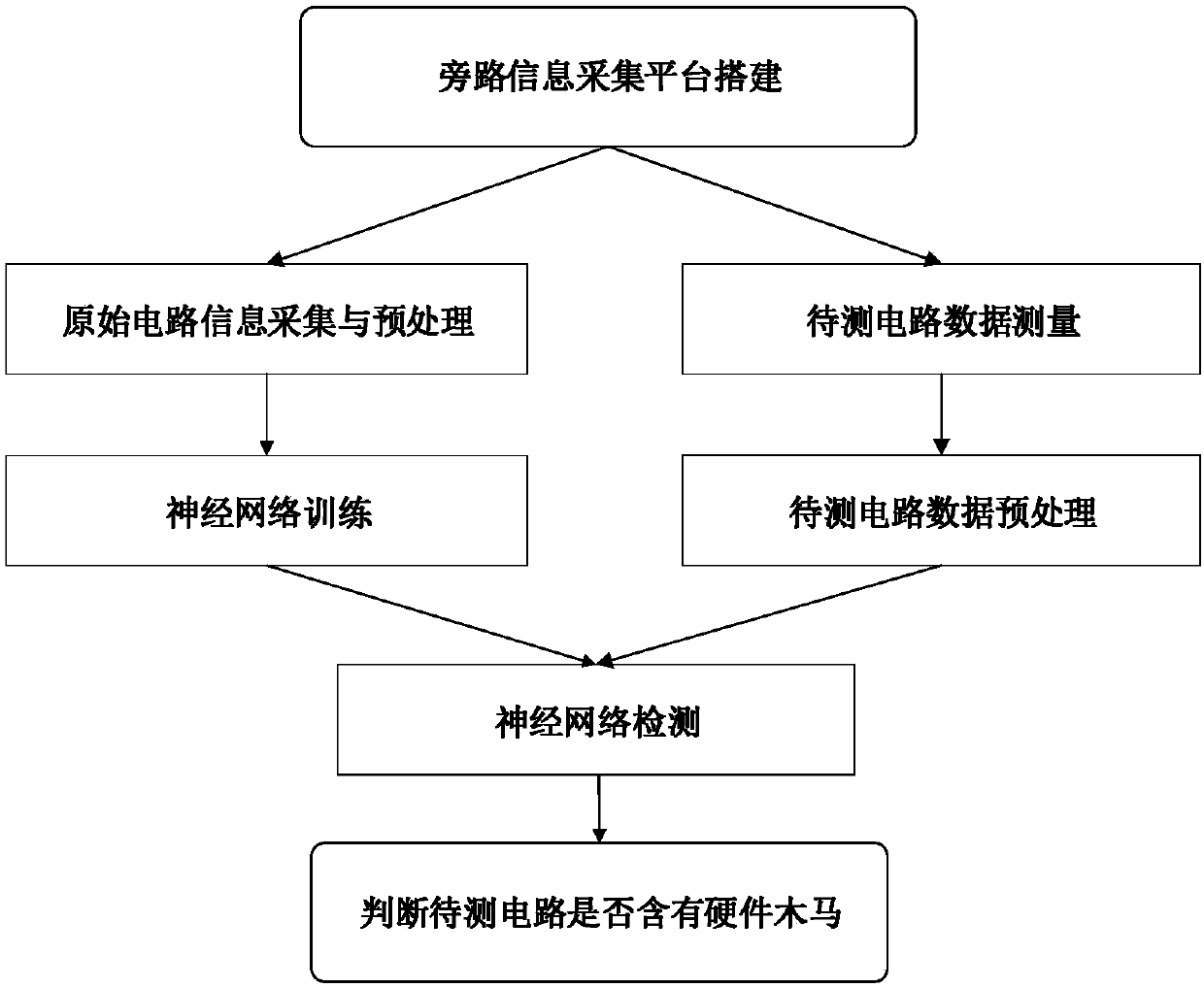
[0039]Due to the shrinking size of hardware Trojans, as well as the influence of process noise and test errors, the sensitivity of hardware Trojan bypass detection technology is affected, so that hardware Trojans that have little influence on circuit bypass information cannot be detected. In order to improve the detection efficiency of a hardware Trojan, the present invention proposes a method for detecting a hardware Trojan based on a neural network. The method collects the bypass information in the working process of the original circuit and the circuit to be tested, and processes the data through the neural network learning algorithm to realize the obvious distinction of the two types of circuit data, thereby realizing the detection of the hardware Trojan horse.
[0040] Regarding the detection of hardware Trojan horses, various countries have carried out a large number of researches. However, with the increase of the integrated circuit scale and the increasingly sophistica...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com