Hardware Trojan horse detection method and system based on bidirectional graph convolutional neural network
A convolutional neural network and hardware Trojan detection technology, applied in neural learning methods, biological neural network models, neural architectures, etc., can solve the problems of detecting and locating Trojan structure, low level of abstraction, and many design details, etc., to achieve detection efficiency The effect of high accuracy and high accuracy, avoiding difficult expansion, and getting rid of the burden of manual definition and feature extraction
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0053] The technical solution of the present invention will be specifically described below in conjunction with the accompanying drawings.
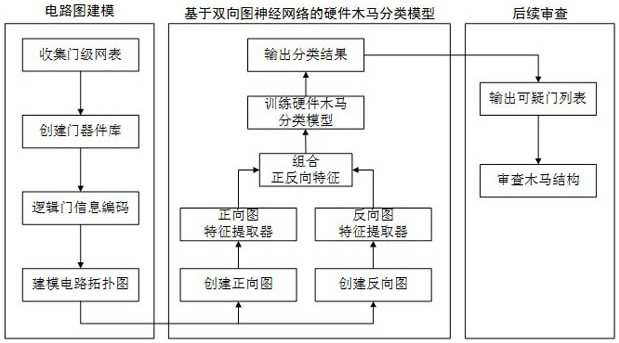
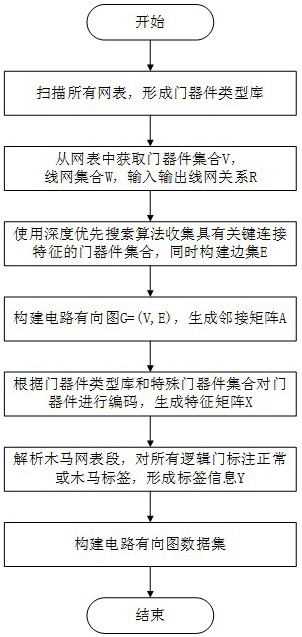
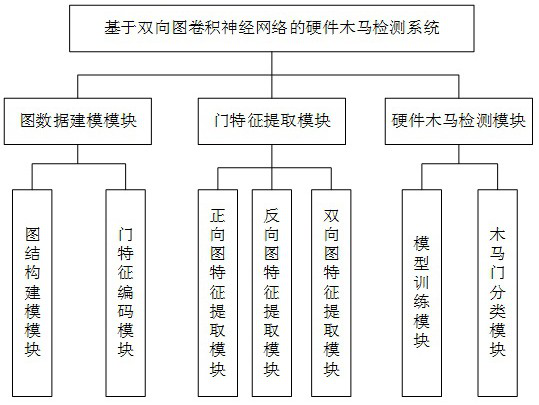
[0054] Such as Figure 1-2 As shown, the present invention provides a kind of hardware Trojan detection method based on two-way graph convolution neural network, comprises the following steps:
[0055] Step A, preprocess the collected netlist file, collect the gate device set V in the netlist, and generate the connection edge set E between devices, create a corresponding directed graph representation G=(V, E), and gate device The information is encoded as the feature representation X, and the hardware Trojan horse label Y is marked for each gate device, and the circuit directed graph data is constructed;
[0056] Step A1, collecting gate device types in all netlists to form a gate device type library;
[0057] Step A2, obtain the gate device set V={v from the netlist 0 ,v 1 ,...,v n-1} and net set W={w 0 ,w 1 ,...,w h}, and define...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com