hardware Trojan horse detection method based on path delay analysis
A hardware Trojan detection and path delay technology, applied in the protection of internal/peripheral computer components, instrument, platform integrity maintenance, etc., can solve problems such as increased pad consumption, increased area overhead, and Trojan detection fails to achieve the expected effect. , to achieve the effect of increasing difficulty and increasing credibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] The present invention will be described in further detail below in conjunction with specific examples, but the embodiments of the present invention are not limited thereto.
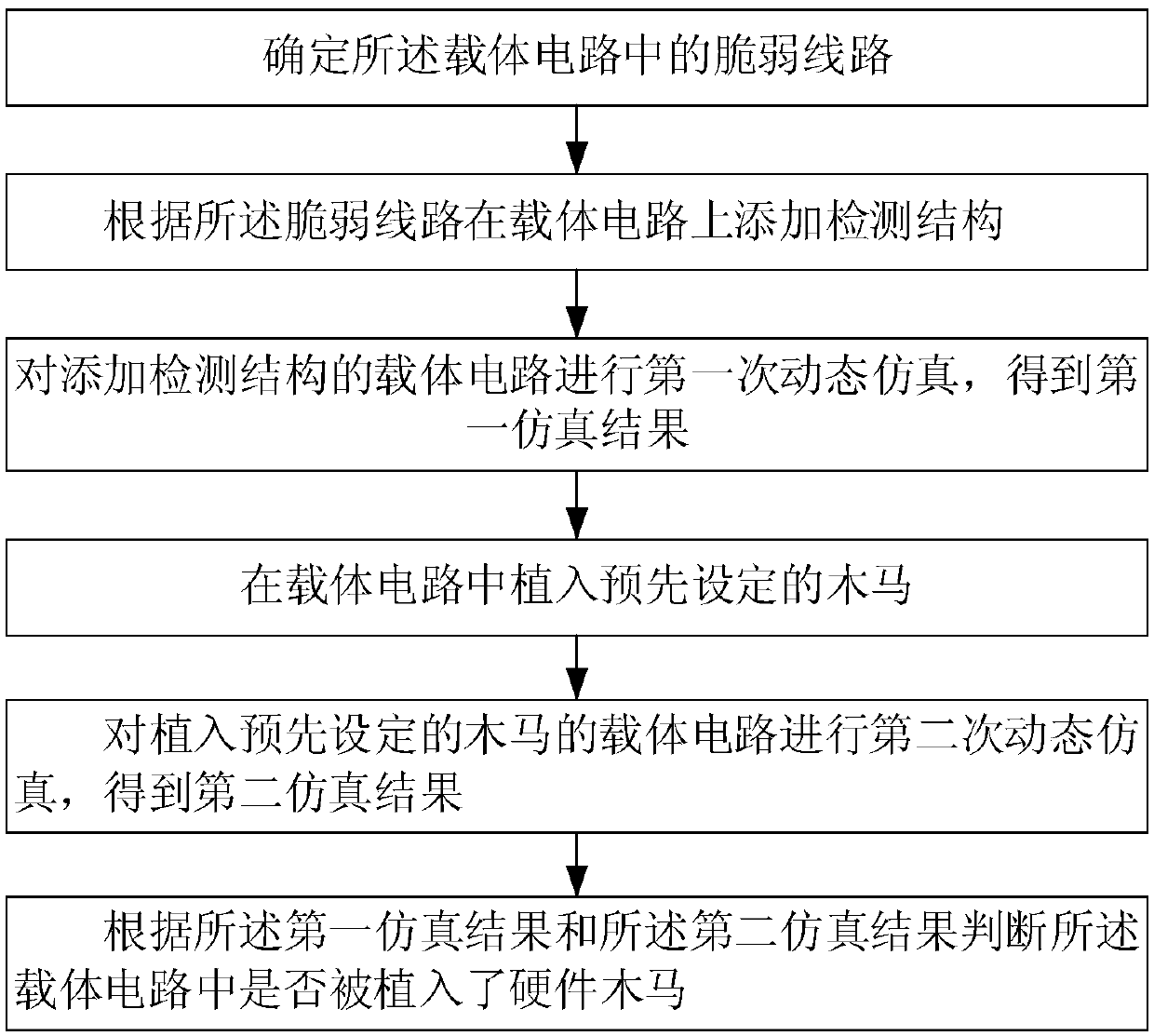
[0042] The embodiment of the present invention provides a hardware Trojan detection method based on path delay analysis, the method steps are as follows:
[0043] identifying vulnerable lines in said carrier circuit;
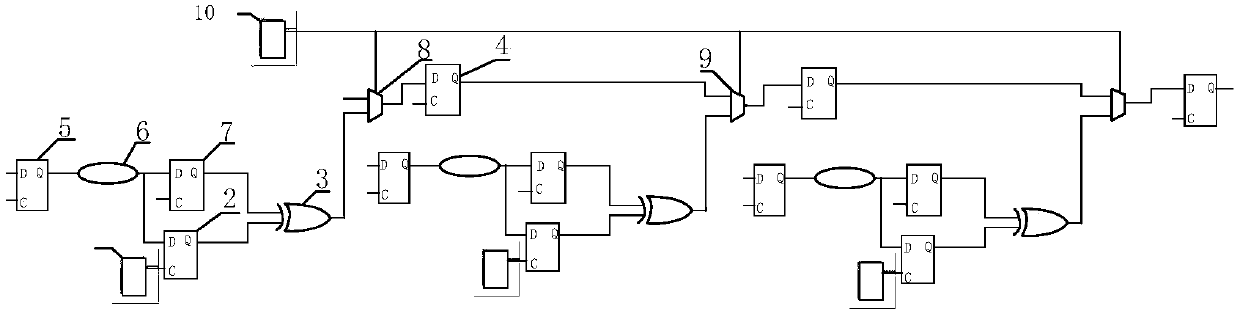
[0044] Adding a detection structure on the carrier circuit according to the vulnerable circuit;
[0045] Carrying out the first dynamic simulation on the carrier circuit with the detection structure added, and obtaining the first simulation result;
[0046] Implanting a preset Trojan horse in the carrier circuit;
[0047] Carrying out a second dynamic simulation of the carrier circuit implanted with the preset Trojan horse to obtain a second simulation result;
[0048] judging whether a hardware Trojan is implanted in the carrier circuit according to the first simulation result an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com