Hardware trojan horse detection method based on waveform superposition
A hardware Trojan detection and hardware Trojan technology, applied in the direction of internal/peripheral computer component protection, etc., can solve the problems of high hardware Trojan detection cost, high implementation cost, and low detection efficiency, so as to reduce detection cost, improve recognition efficiency, and operate easy effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
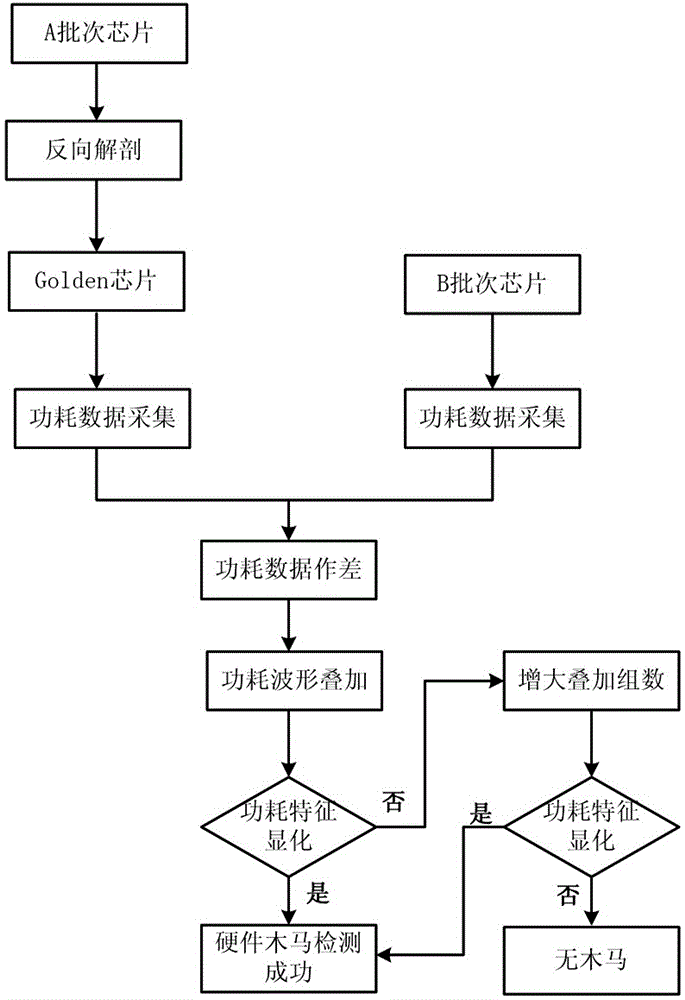
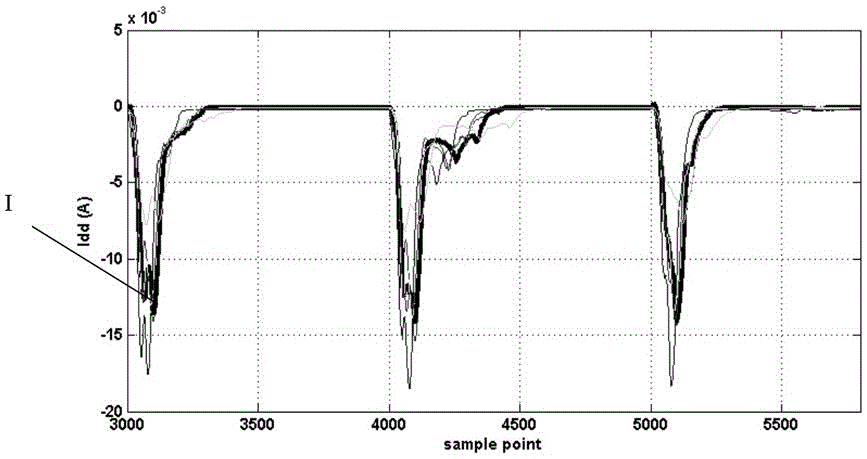
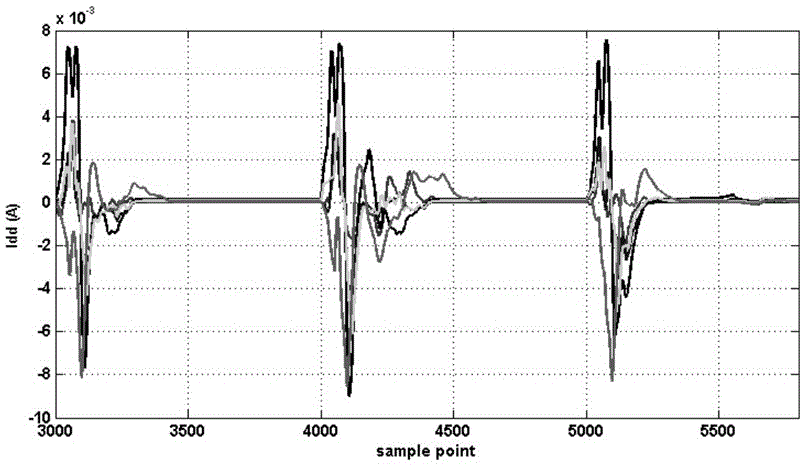
[0034] Such as figure 1 Shown, the hardware Trojan detection method based on waveform superposition of the present invention, its steps are:
[0035] S1: Obtain a clean chip as a reference;
[0036] That is, a clean chip (Golden chip) that does not contain hardware Trojan horse circuits can be obtained as a reference through the method of reverse dissection;
[0037] S2: Extract several chips from another batch as chips to be tested;
[0038] Since the chips in the same batch have the same security status, that is, all contain hardware Trojan horse circuits or are all normal chips, and there are process deviations between chips in different batches, in order to avoid process deviations from affecting the final judgment of whether the chip is safe or not, another Randomly select n chips from the batch of chips as the chips to be tes...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com