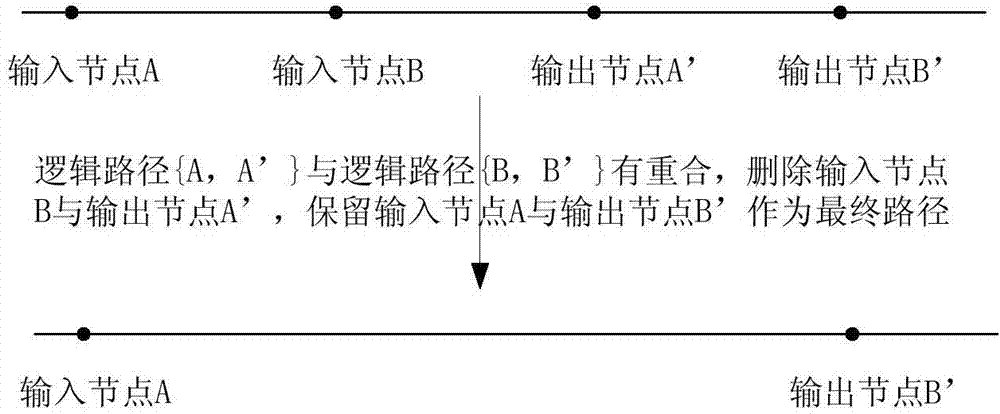
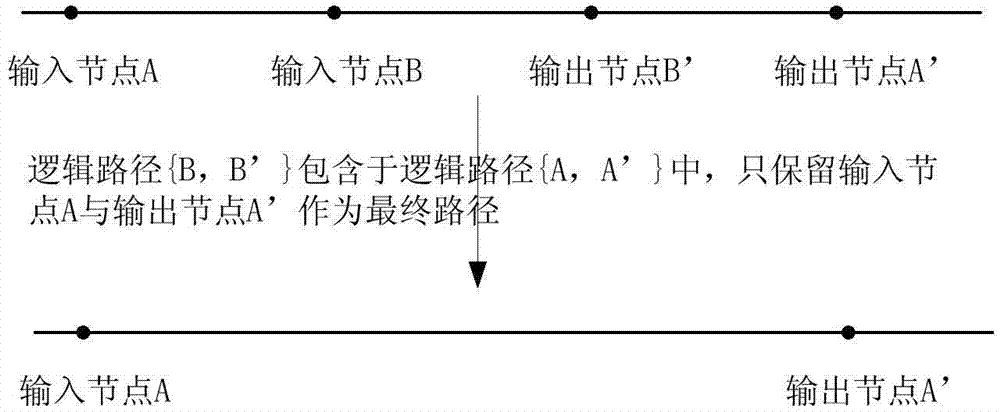
Circuit safety design method for defending against threat of hardware Trojan horse based on triple modular redundancy
A three-mode redundancy, hardware Trojan technology, applied in computing, electrical digital data processing, protection of internal/peripheral computer components, etc., can solve the problems of difficult detection of logic values, difficult to find trigger conditions, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] With the integration level of integrated circuits getting higher and higher and the scale getting bigger and bigger, it becomes extremely difficult to complete the design of 100% test coverage for the circuit within the specified time.
[0036] Whether it is functional test coverage or structural test (DFT) coverage, it is difficult to achieve 100%.
[0037] This means that after the circuit is manufactured, some circuit nodes inside the circuit cannot be tested, that is, the specific conditions of this part of the circuit nodes during the circuit working process cannot be predicted and grasped.
[0038] When this part of the circuit node is used as the attack object of the hardware Trojan, it is impossible to carry out any test to determine whether there is a potential threat in the circuit node. Or even if a functional failure occurs, it is impossible to trace and debug what caused it.
[0039] After the integrated circuit is implanted with a hardware Trojan horse du...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com