Hardware Trojan horse detection method and device
A technology of hardware Trojan detection and hardware Trojan, which is applied in the electronic field, can solve the problems of useless circuit side channel information timing, difficulty in detecting small Trojans, reducing detection practicability and reliability, etc., so as to avoid manual data processing and feature extraction , Reduce detection cost and time overhead, improve detection efficiency and accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0051] In order to make the above objects, features and advantages of the present invention more comprehensible, specific implementations of the present invention will be described in detail below in conjunction with the accompanying drawings.
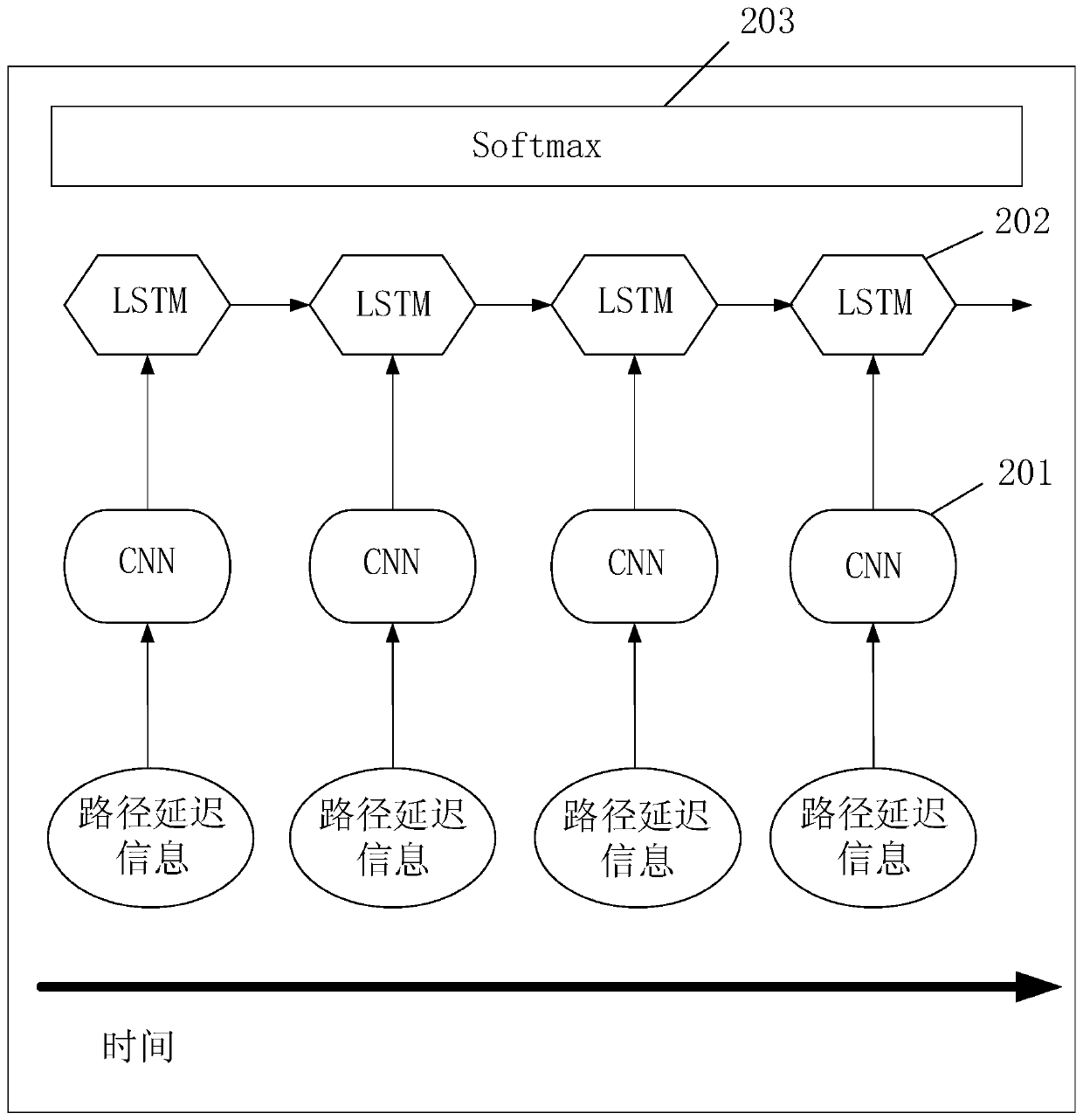
[0052] The present invention at first provides a kind of hardware Trojan detection method, as figure 1 shown, including:
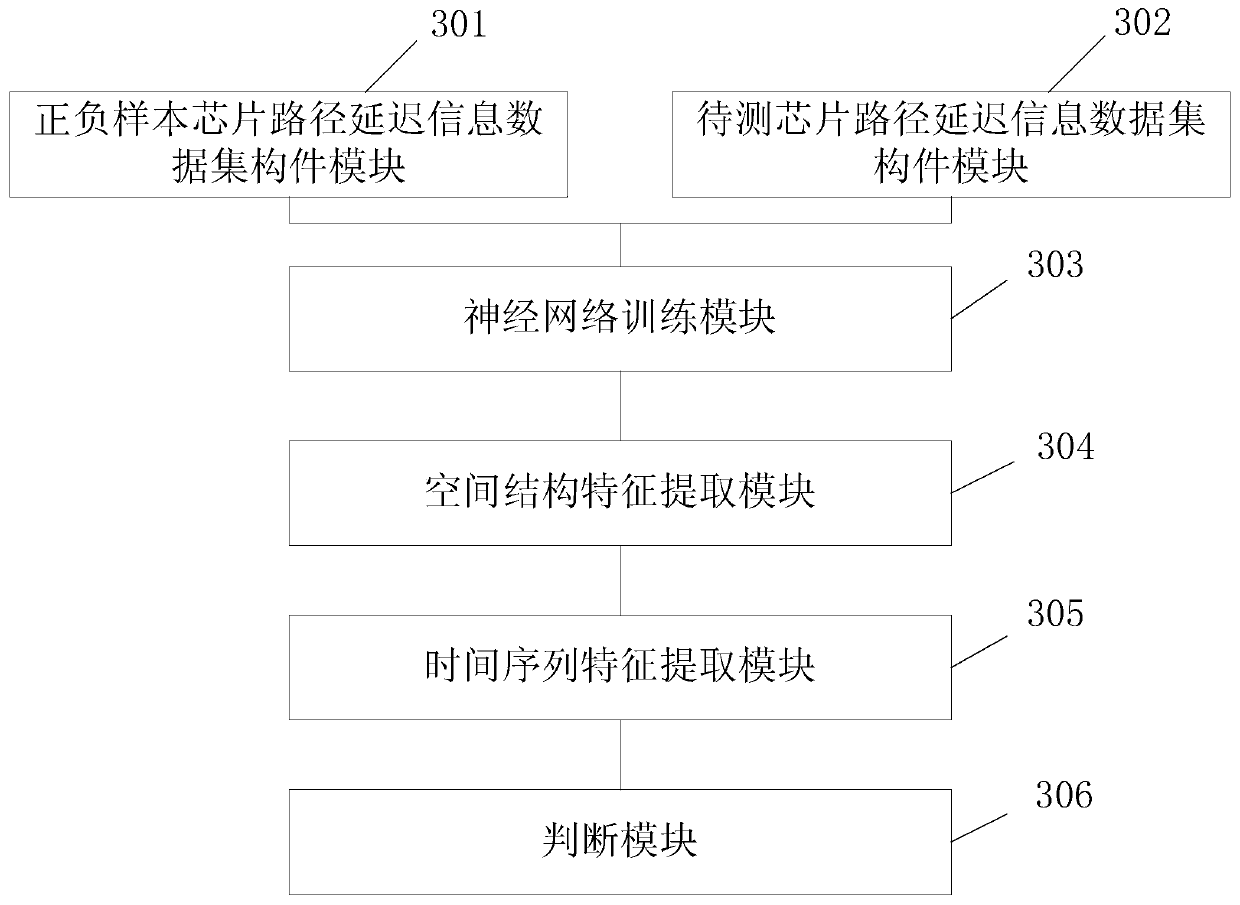
[0053] Step 101: Sampling the path delay information of the positive and negative sample chips, constructing the path delay information data set of the positive and negative sample chips; corresponding to the positive and negative sample chip path delay information data sets, sampling the path delay information of the chip to be tested, and constructing the chip to be tested path delay information dataset;
[0054] Step 102: sending the positive and negative sample chip path delay information data sets into the neural network to be trained for training, adjusting various parameters of the neural network according ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com