Hardware Trojan horse detection method based on information flow security verification
A hardware Trojan detection and security verification technology, applied in the field of information security, can solve the problems of inability to accurately locate the Trojan design, high design cost, and reveal the trigger mechanism of the Trojan, so as to avoid design overhead, improve efficiency, and achieve precise positioning.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0050] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
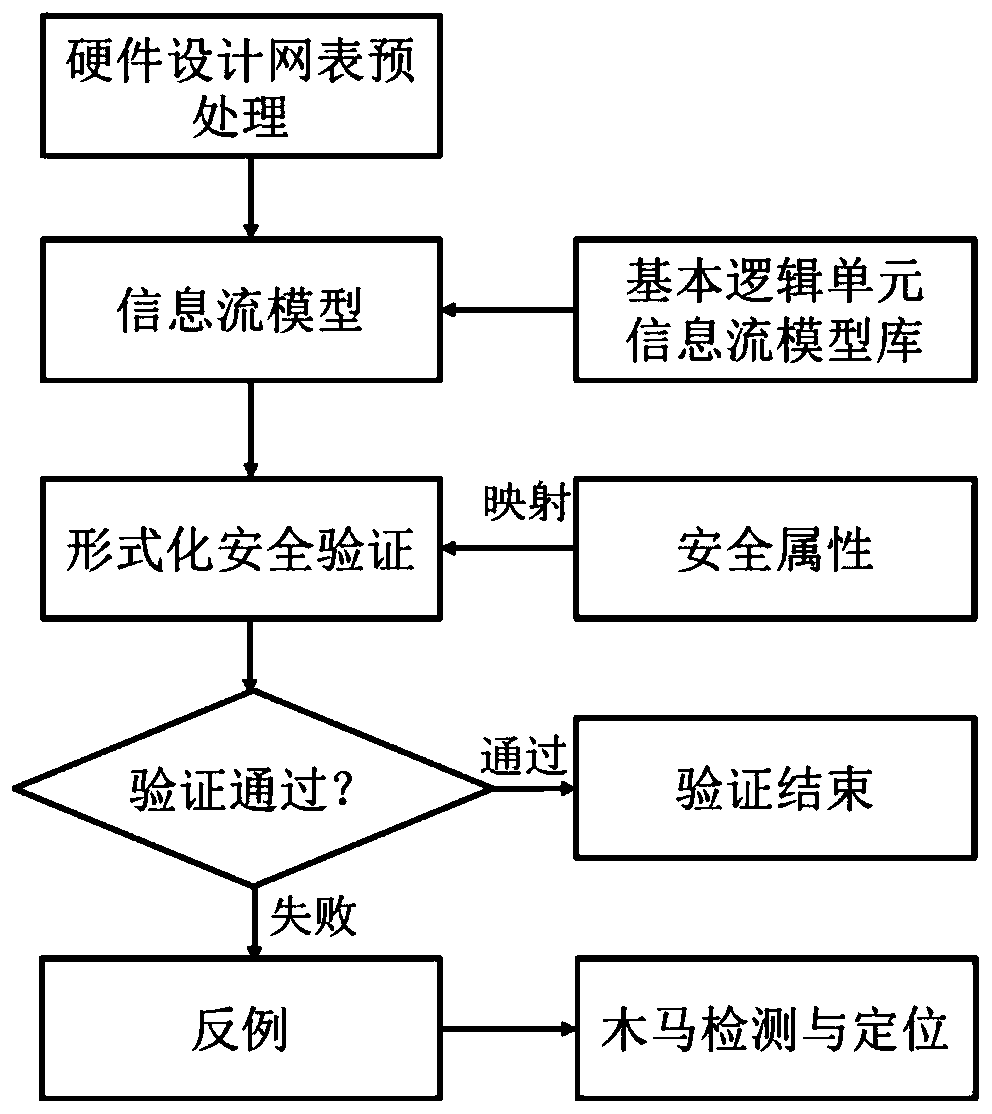
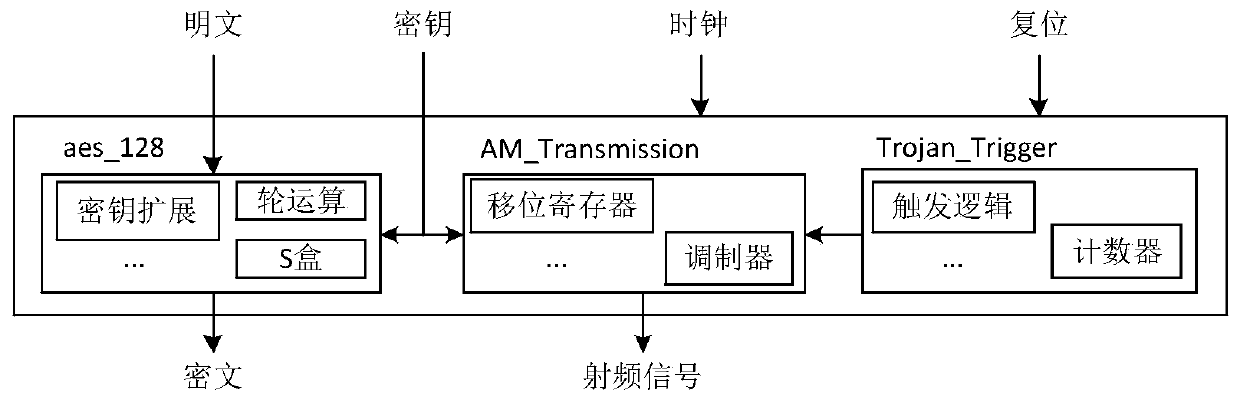
[0051] The invention proposes a Trojan horse detection method based on information flow security verification aiming at the potential hardware Trojan horse safety threat in integrated circuit hardware design whose design process is uncontrollable. The working principle of this method is: use the hardware information flow analysis method to construct the information flow model of the hardware design, describe the model by using the standard hardware design description language, and define the information flow security attributes that the hardware design needs to meet, such as confidentiality, integrity, etc. and isolation properties. Then, using the formal verification tools in the EDA tool chain, combined with the information flow model of the hardware design, the expected security properties are formally verified. When a violation of the security attr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com