Detecting method of combining infrared imagery and normal distribution analysis for hardware trojan horse
A hardware Trojan detection and infrared image technology, which is applied in image communication, radiation pyrometry, color TV parts, etc., can solve the problems of slow verification process, poor detection effect and high cost, and achieve low detection cost and high detection cost. high precision effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0056] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
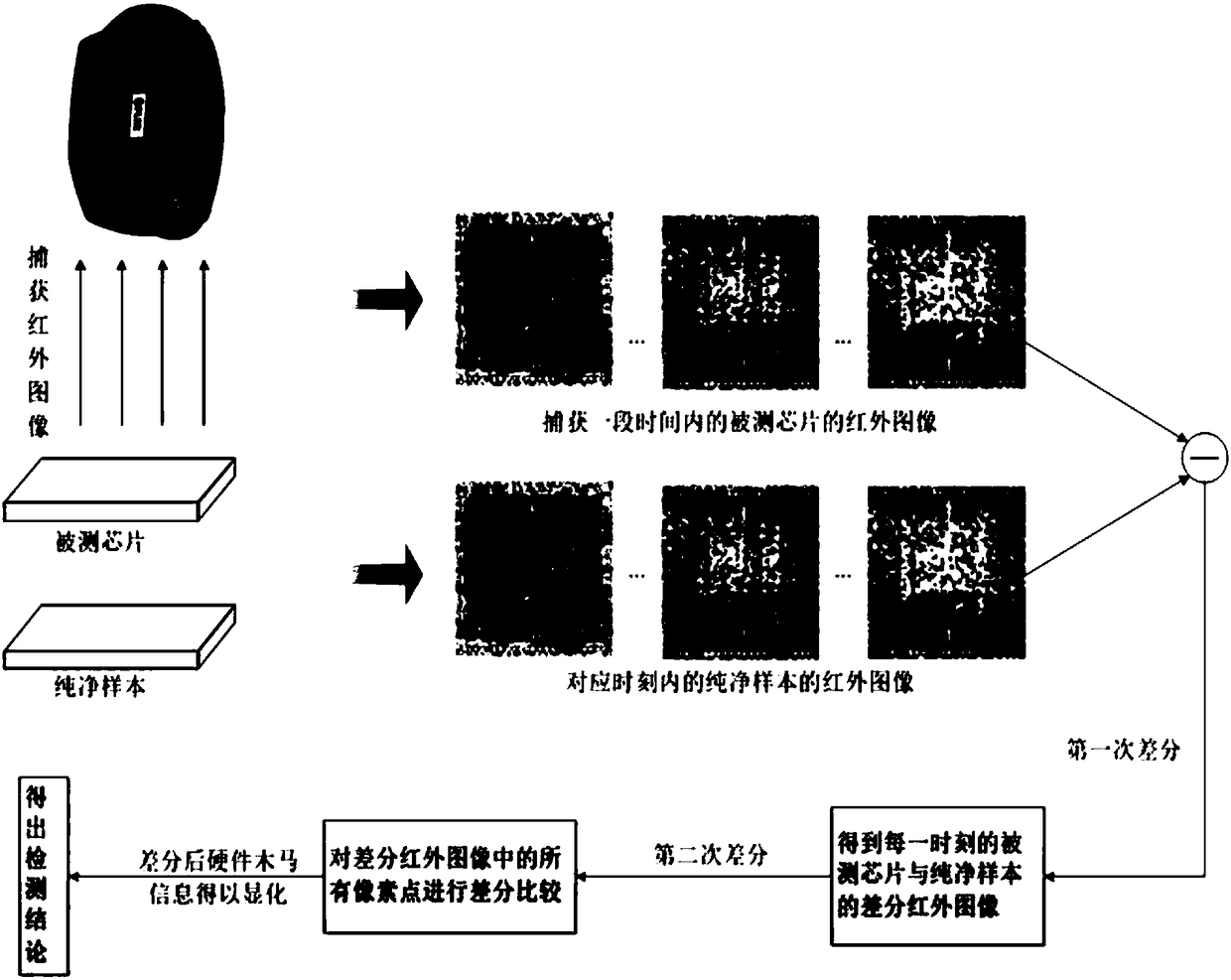
[0057] A hardware Trojan consists of two parts - the trigger part and the load part. The trigger part will always be in the working state, because it needs to monitor the state of the circuit and activate the load part to work at a specific moment. The active part of the trigger consumes energy, which generates heat and radiates it into space. This heat can be captured by an infrared camera, which is the change in the heat bypass information caused by the hardware Trojan horse, and the present invention utilizes the heat bypass information for detection.
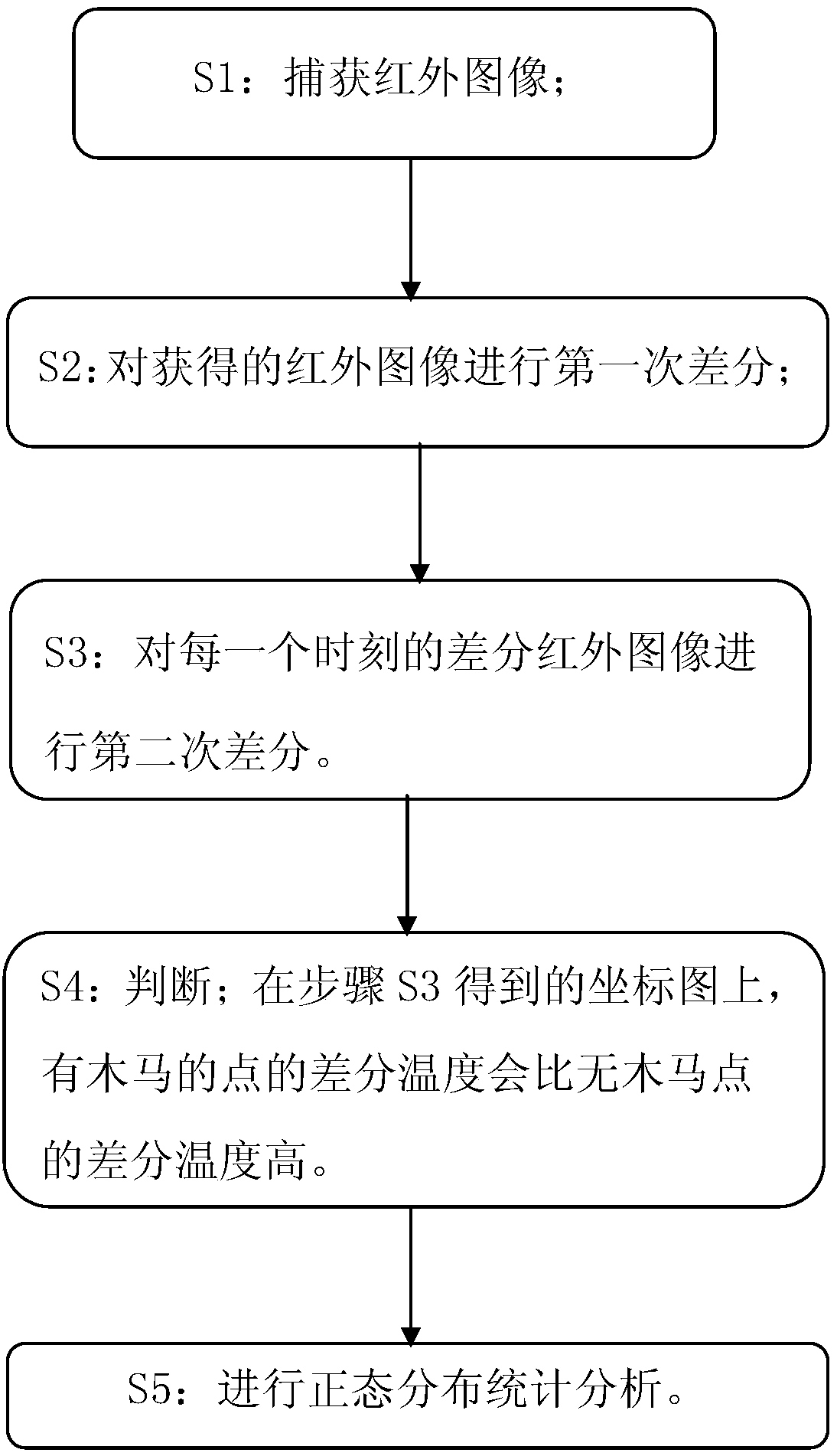
[0058] Such as figure 1 and figure 2 Shown, the hardware Trojan detection method that infrared image of the present invention combines with normal distribution analysis, its steps are:
[0059] S1: Capture an infrared image.
[0060] Let a pure chip sample without hardware Tro...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com