Chip hardware Trojan horse detection method and system
A hardware Trojan detection and chip technology, which is applied in the electronic field, can solve the problems of difficult implementation of highly integrated chips, difficulty in detecting hardware Trojans, and high cost, and achieve the effect of improving automatic identification capabilities, reducing manual intervention, and strong detection capabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
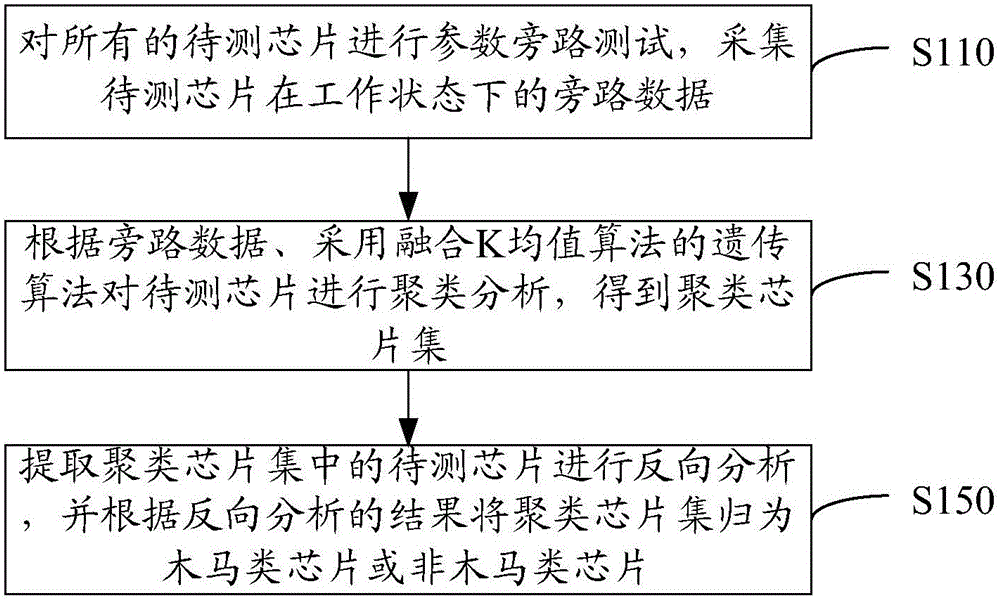
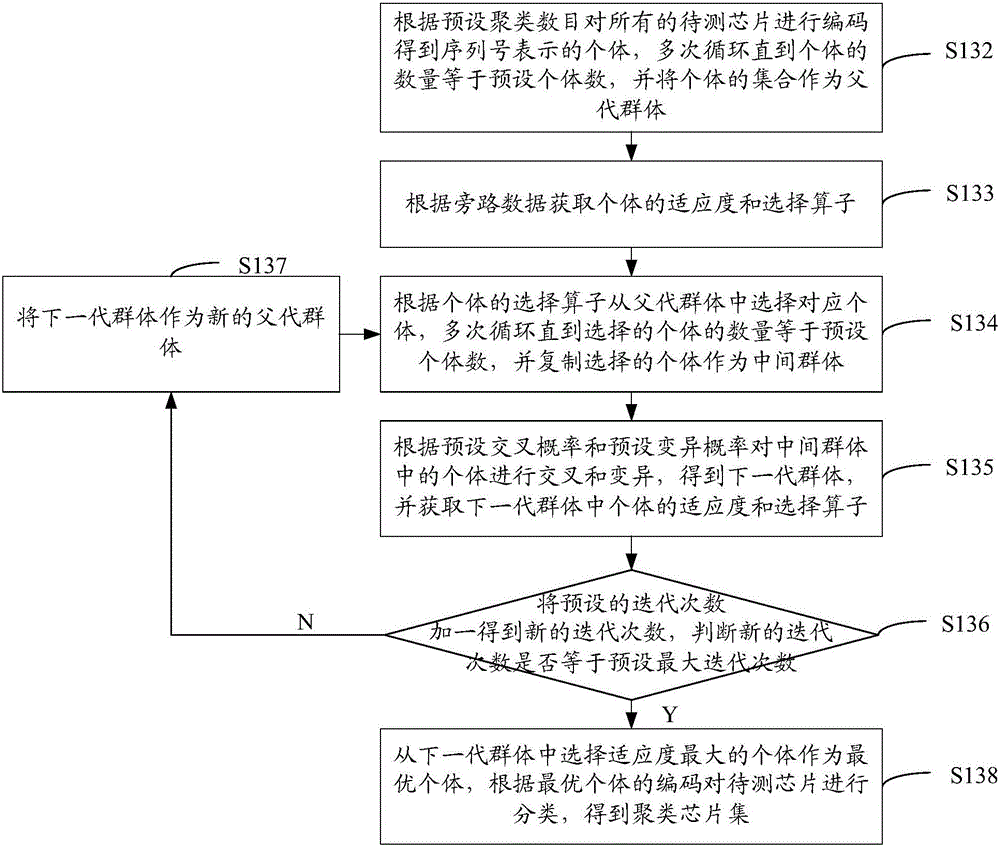
[0020] refer to figure 1 , the chip hardware Trojan detection method in one embodiment of the present invention, comprises the following steps.
[0021] S110: Perform a parameter bypass test on all chips to be tested, and collect bypass data of the chips to be tested in a working state.
[0022] The parameter bypass test refers to the bypass signal analysis of the chip under test, and the collection of bypass data corresponding to the physical characteristic information leaked by the chip under test during operation.
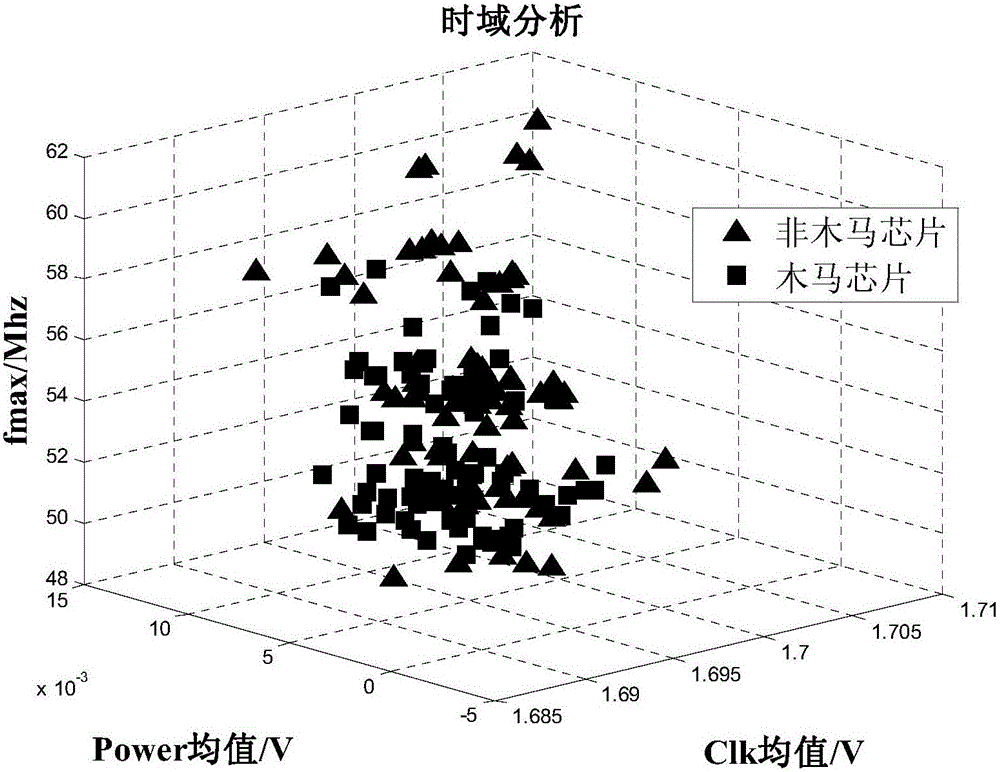
[0023] In this embodiment, the collected bypass data includes the average value of the global clock voltage, the average value of the dynamic power consumption voltage, and the output frequency of the ring oscillator. That is, each piece of bypass data is three-dimensional data including three kinds of information. In one of the specific embodiments, there are 160 chips to be tested, figure 2 It is the three-dimensional result graph of the global clock volta...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com