Machine learning Trojan horse detection method based on structural feature screening and load expansion
A technology of machine learning and structural features, applied in machine learning, instruments, computer security devices, etc., can solve problems such as data imbalance, small number of Trojan horse nodes, increased power consumption, etc., to improve efficiency and accuracy, and reduce training time , the effect of improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
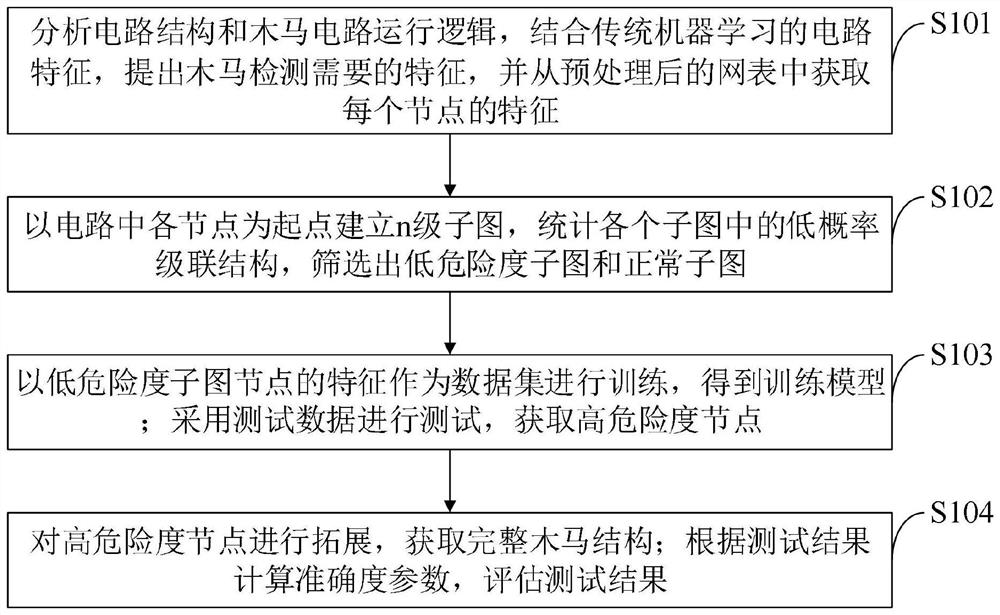
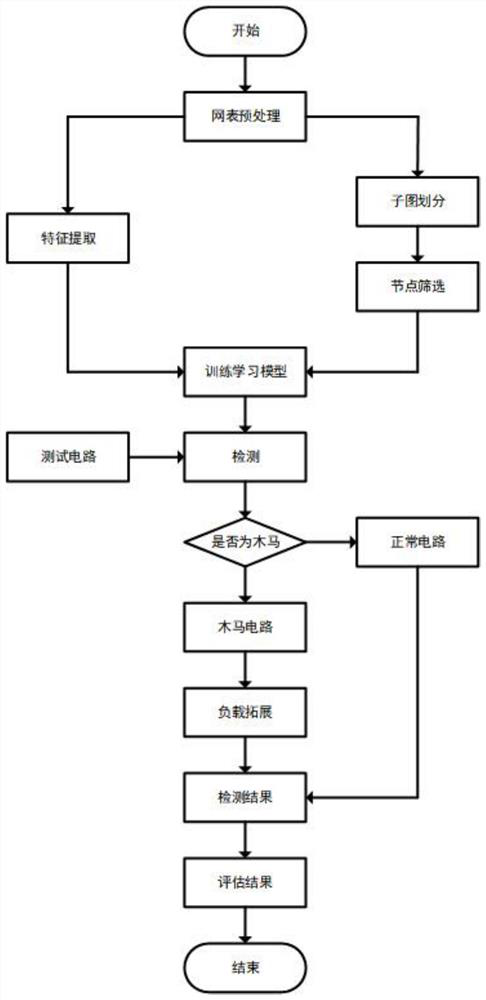
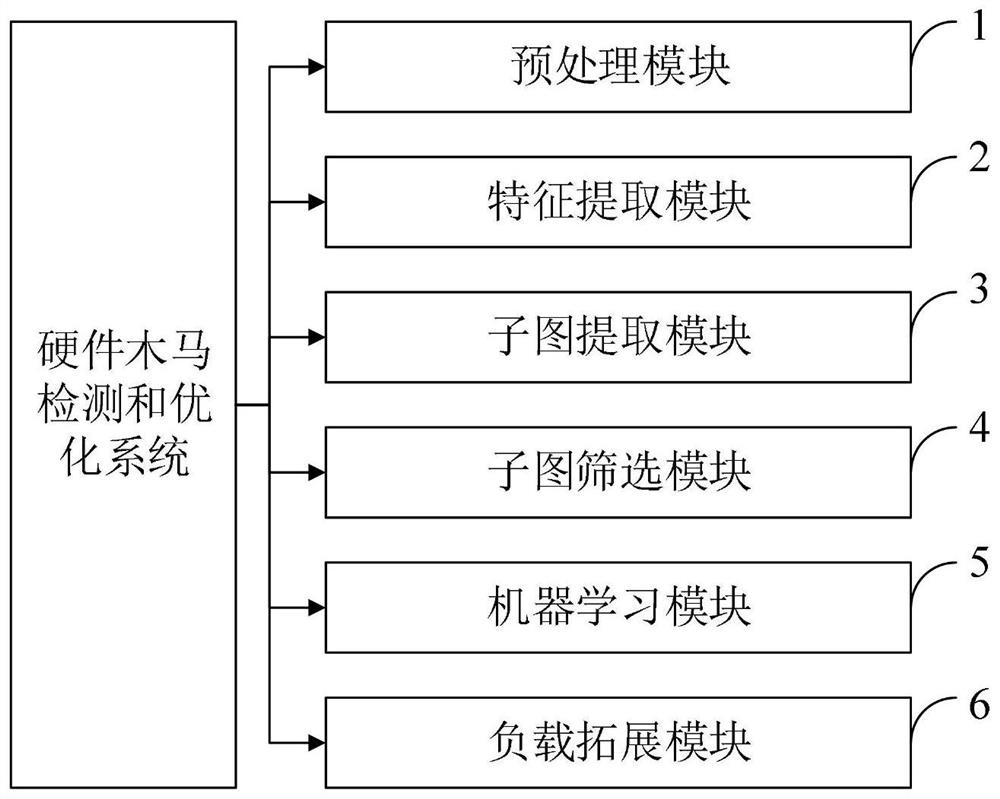
[0093] The invention provides a framework and optimization method based on netlist-level hardware Trojan detection. The implementation idea of the present invention is as follows: firstly, the netlist of the circuit is converted into a quantifiable mathematical model, and feature extraction is performed through mathematical methods based on the model. Then combined with hardware Trojan trigger structure characteristics, screening nodes to get a more balanced data set, combined with machine learning classification method for Trojan detection. Finally, according to the structural characteristics of the hardware Trojan horse, the Trojan horse node is expanded backwards to obtain a complete hardware Trojan horse circuit.
[0094] Realization of the present invention has adopted following technical scheme:
[0095] A framework and optimization method based on netlist-level hardware Trojan detection, comprising the following steps:
[0096] Step S1: preprocessing the gate-level ...
Embodiment 2
[0116] Such as figure 2 As shown, the machine learning Trojan horse detection method based on netlist level based on structural feature screening and load expansion provided by the embodiment of the present invention includes the following steps:
[0117] Step S1: Preprocessing the gate-level netlist to be tested, the specific operation is as follows:
[0118] S11: For a given gate-level netlist, first integrate all the modules in the netlist into a main module, and keep their connection relationship; in order to prevent the repetition of signal names and device names in different modules, the signal names and device names in name prefixed with the submodule name.
[0119] S12: traverse the entire gate-level circuit, extract the device names of all devices in the netlist, use each device as an independent node, and obtain the type of each node (INV, NOR, AND, OR, NAND, AOI, OAI, DFF, others ), obtain the input-output relationship of each node (which signals are input and wh...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com