Method and system for monitoring Trojan Horse based on network communication behavior characteristic
A network communication and Trojan horse technology, applied in transmission systems, digital transmission systems, data exchange networks, etc., can solve problems such as occupying system resources, Trojan horse programs cannot be effectively prevented, and system performance is affected.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
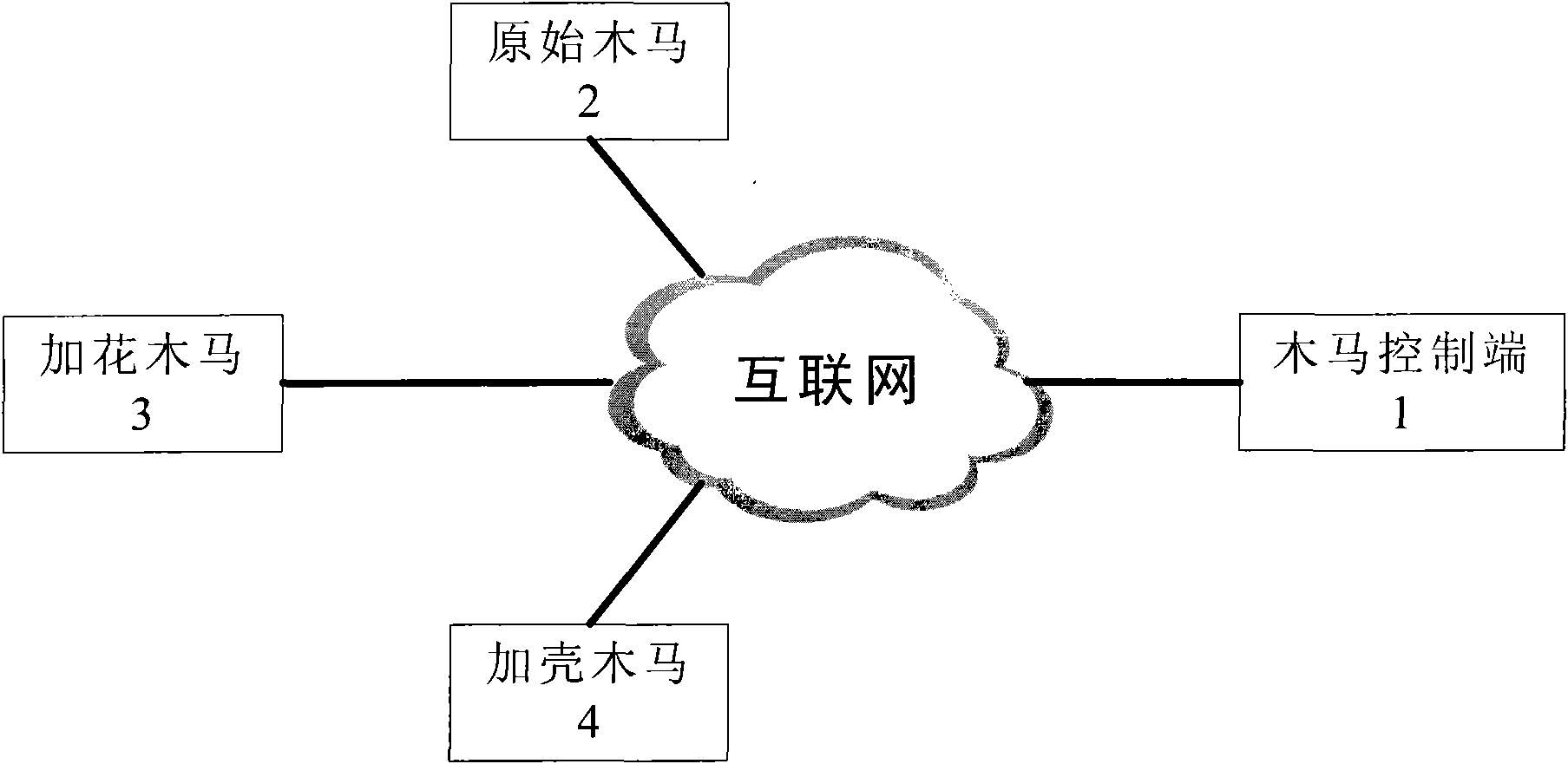
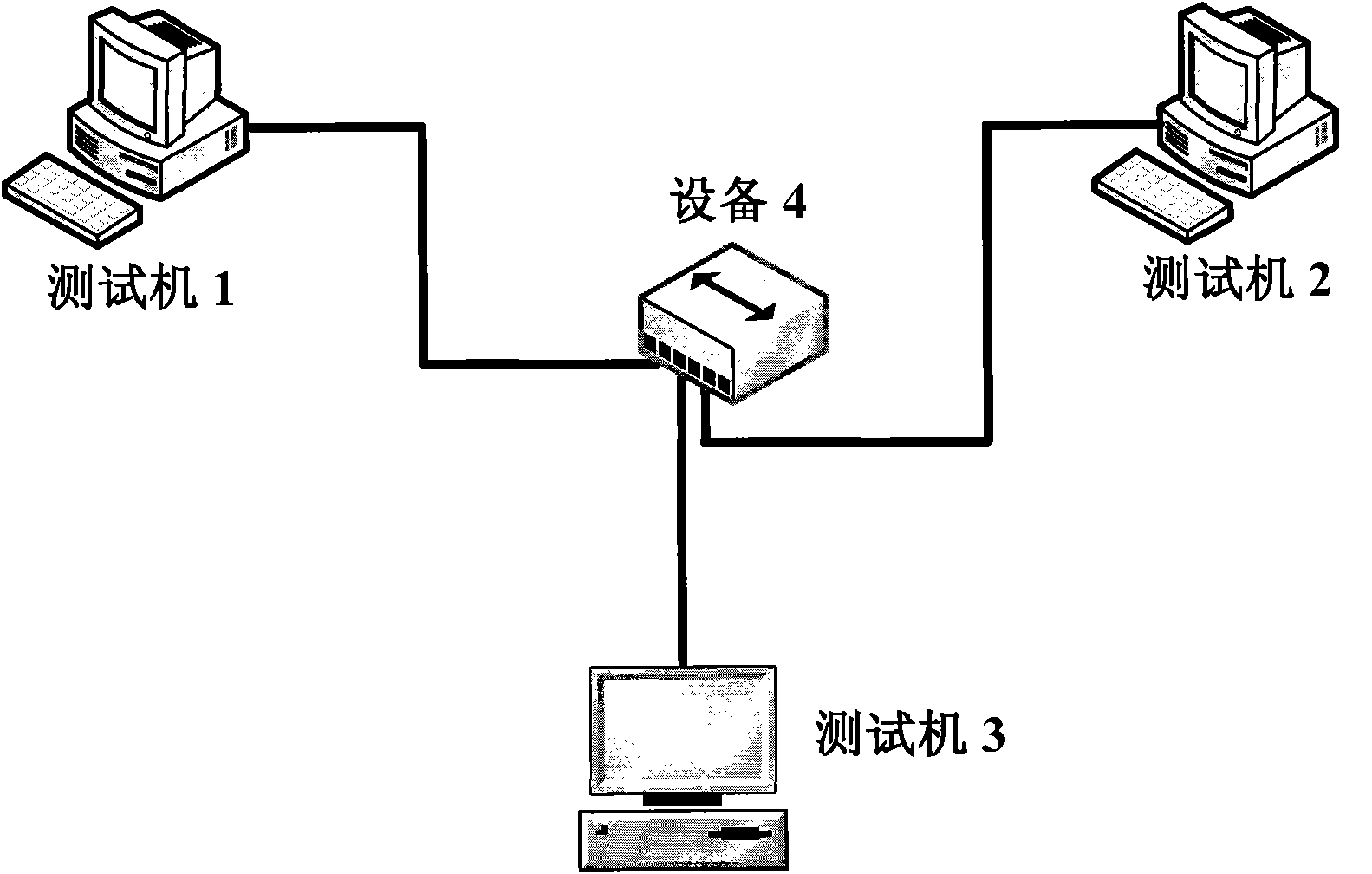
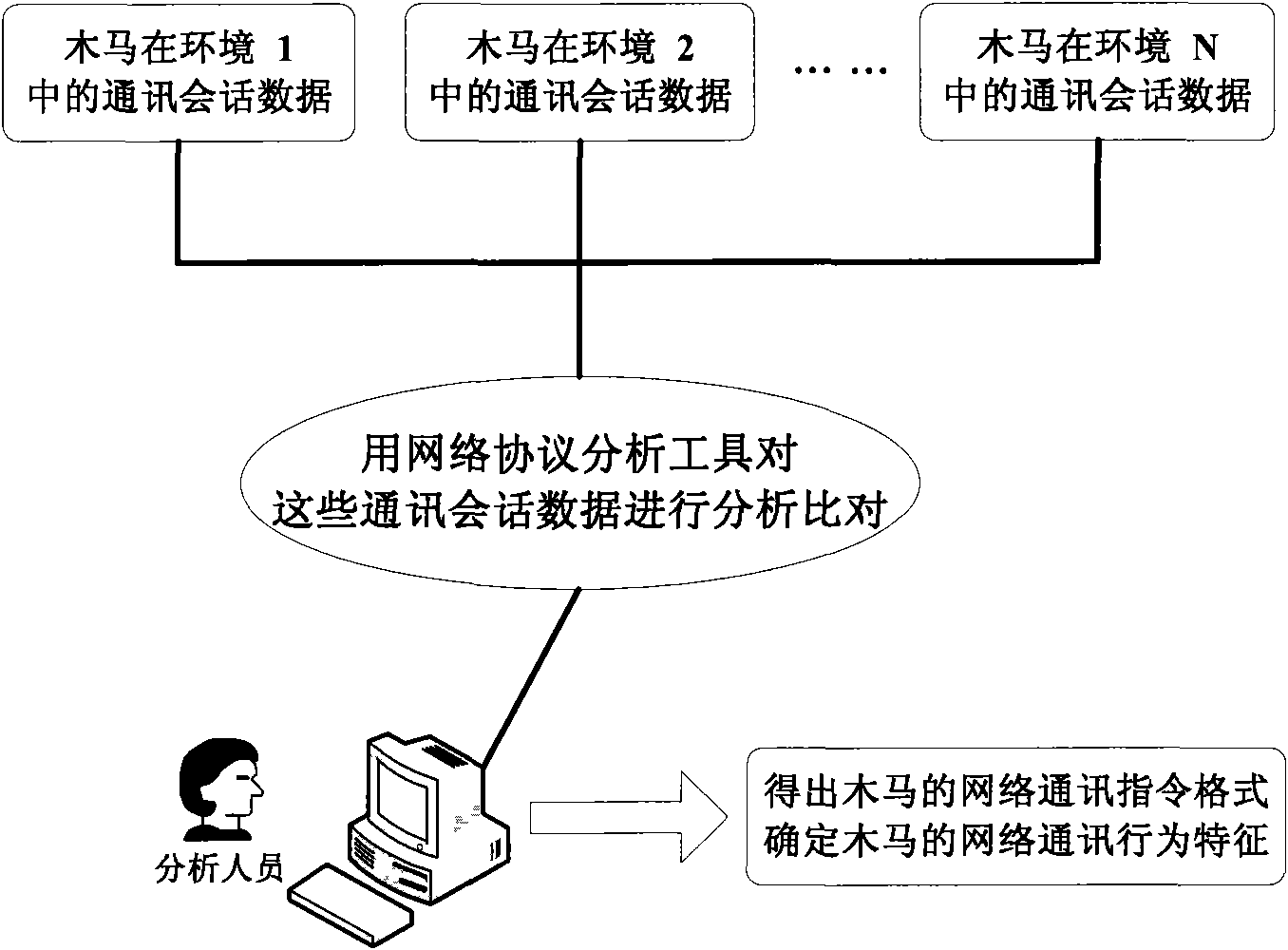
[0025] figure 1 It is a schematic diagram of monitoring Trojan horses in network data streams based on network communication behavior characteristics when Trojan horses are active.
[0026] Usually the Trojan horse program will be added various shells by hackers, or anti-kill processing for certain anti-virus software, so the Trojan horse program with the same function will produce files with completely different characteristics after being processed by adding flowers, packing or mutation. Storage, this is undoubtedly a nightmare for antivirus software that scans and kills files based on file signatures.
[0027] Although the Trojan horse carries out various forms of changes on its carrier - "file", such as adding flowers, packing or mutation, etc., the communication instruction format between the Trojan horse client and server of different versions of the same type is unchanged. That is, the application communication protocol of the Trojan horse itself will not be easily cha...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com