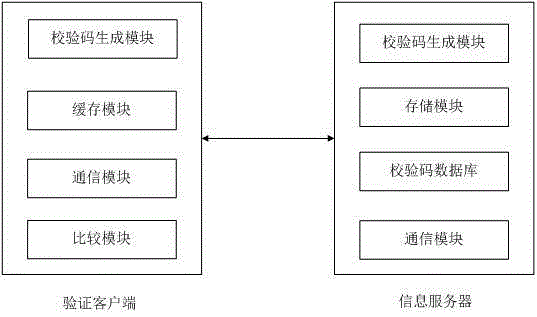
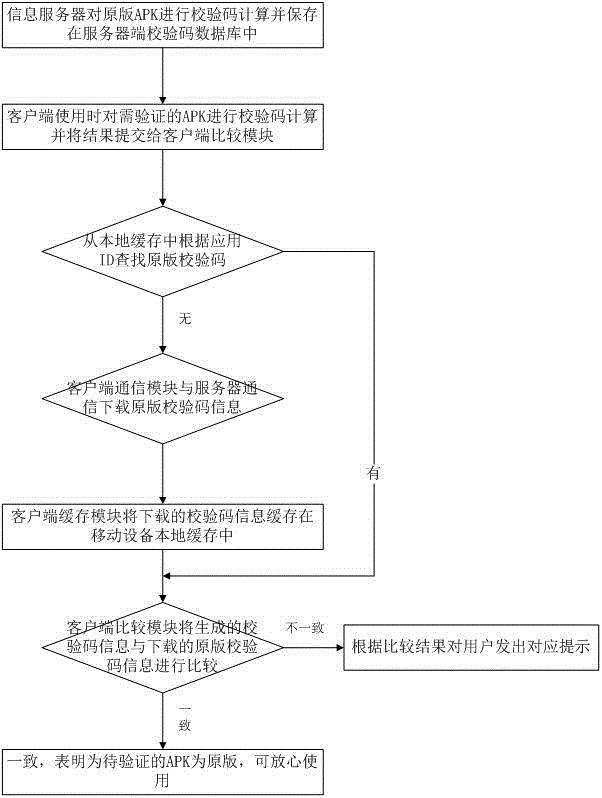
A system for authenticating mobile applications
A mobile application, the original technology, applied in the direction of transmission system, program/content distribution protection, telephone communication, etc., can solve the problems of lack of certificate management center and infeasibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0064] In this embodiment, it is assumed that the application program to be verified by the original version is a game application A (hereinafter referred to as application A) such as Fishing Daren, and the verification client has connected to the original version information server, and the client side of the verification client The caching module has downloaded all the verification codes of the original version of the application from the server and stored them in the local cache of the mobile device. The mobile terminal device in this example is a smart phone, and the algorithm for calculating the check code is the MD5 algorithm.
[0065] According to an embodiment of the present invention, when the user downloads the application A using the mobile phone, the verification client will verify the original version of the downloaded APK package of the application A. First, the MD5 algorithm is used to calculate the check code of the downloaded APK package to generate the check ...
Embodiment 2
[0067] In this embodiment, it is assumed that the application that needs to verify the original version is typesetting application B (hereinafter referred to as application B), and the verification client has connected to the original version information server. The mobile terminal device in this example is a smart phone, and the calculation algorithm of the verification code is SHA1 algorithm.
[0068] The user downloads application B through the mobile phone, and the file structure in the APK package of application B includes: lib folder, META-INF folder, res folder, AndroidManifest.xml, classes.dex and resources.arsc files.
[0069] First, the verification client uses the SHA1 algorithm to perform verification calculations on all files in the APK package of application B one by one, and generates verification codes corresponding to each file. The verification code generated by the classes.dex file is assumed to be A.sha11. Similarly, all files in the original APK package of...
Embodiment 3
[0071] In this embodiment, it is assumed that the application to be verified by the original version is application C of level games (hereinafter referred to as application C), and the verification client has downloaded the original verification code from the server. The mobile terminal device in this example is a tablet Computer, the algorithm for calculating the check code is the MD5 algorithm.
[0072] The user downloads application C, and verifies the original version of the APK during the installation process. The specific process is as follows:
[0073] First, the verification client uses the MD5 algorithm to calculate the check code of the downloaded APK package of application C and all files in the APK package (the file structure of the APK package is the same as that of the APK package in Embodiment 2). The verification client searches the corresponding APK original verification code (including the verification codes of the APK package and all files in the APK package...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com